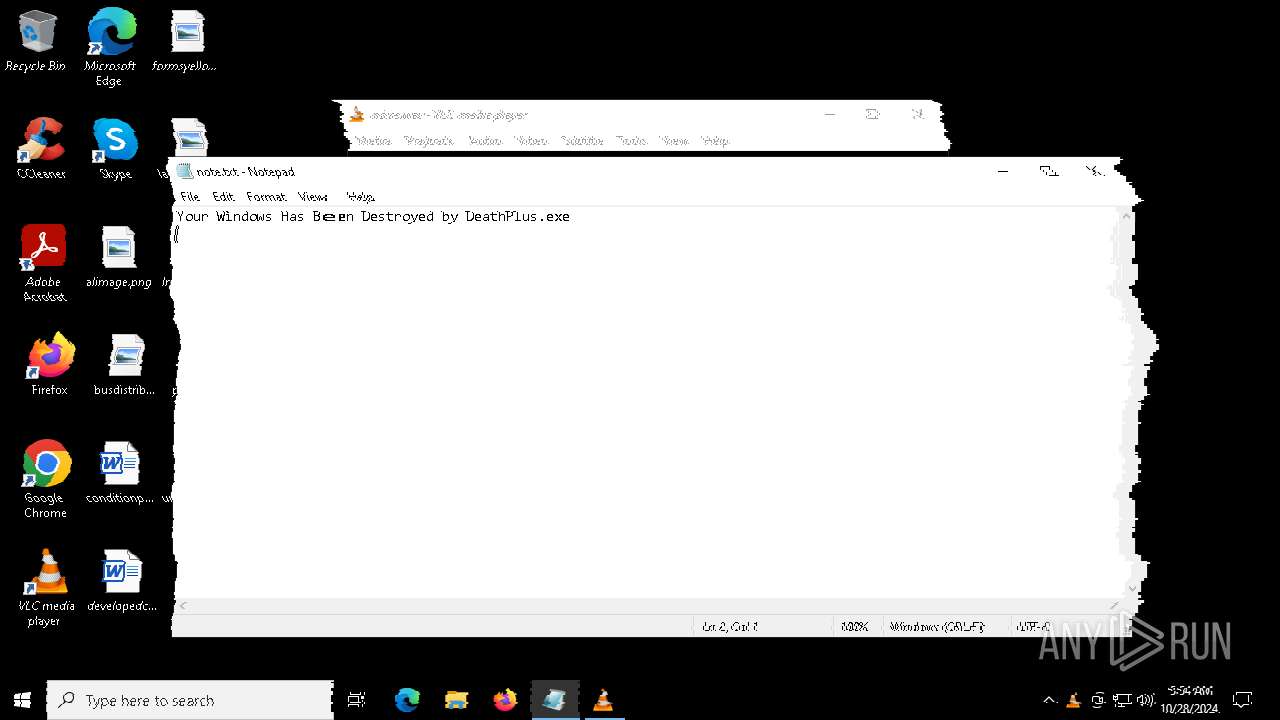
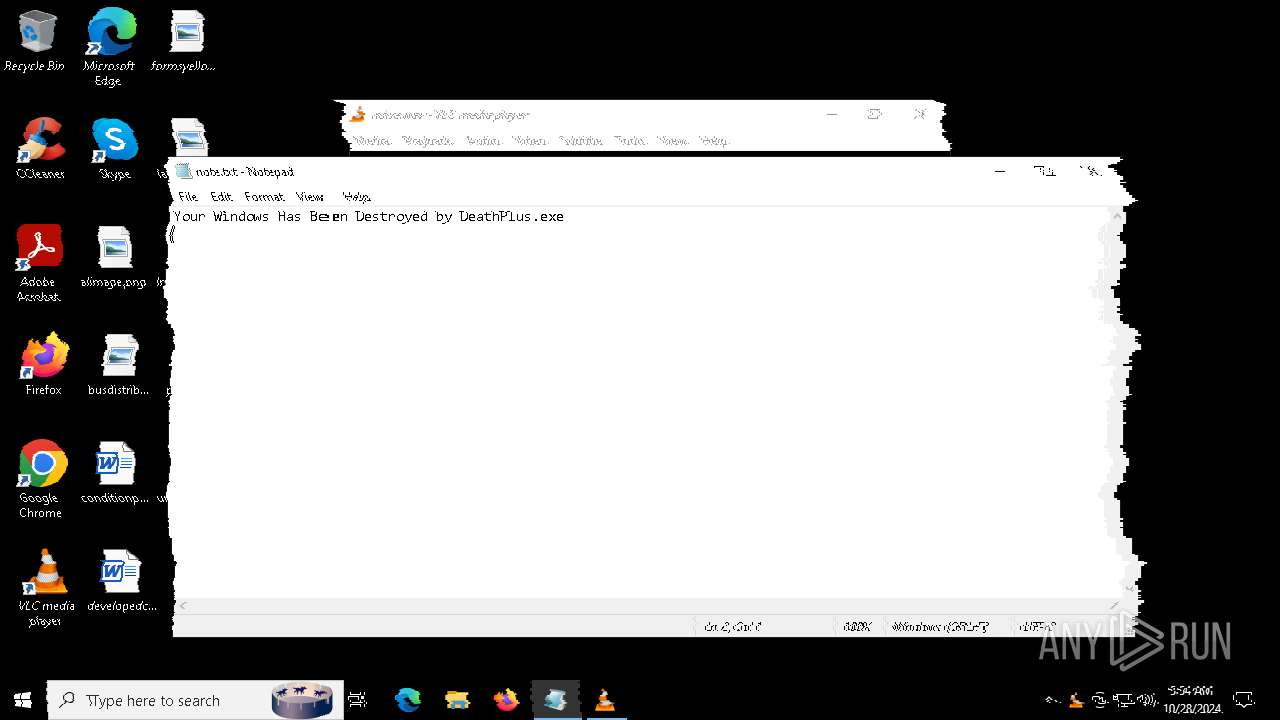
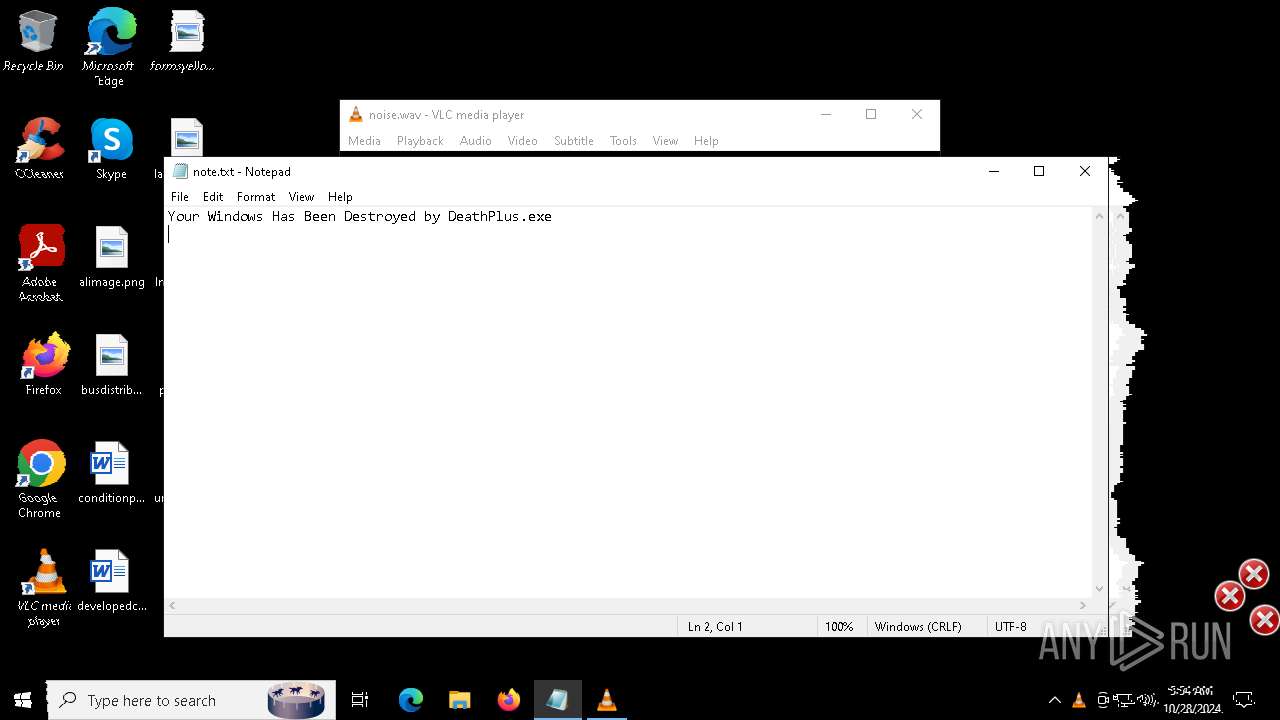
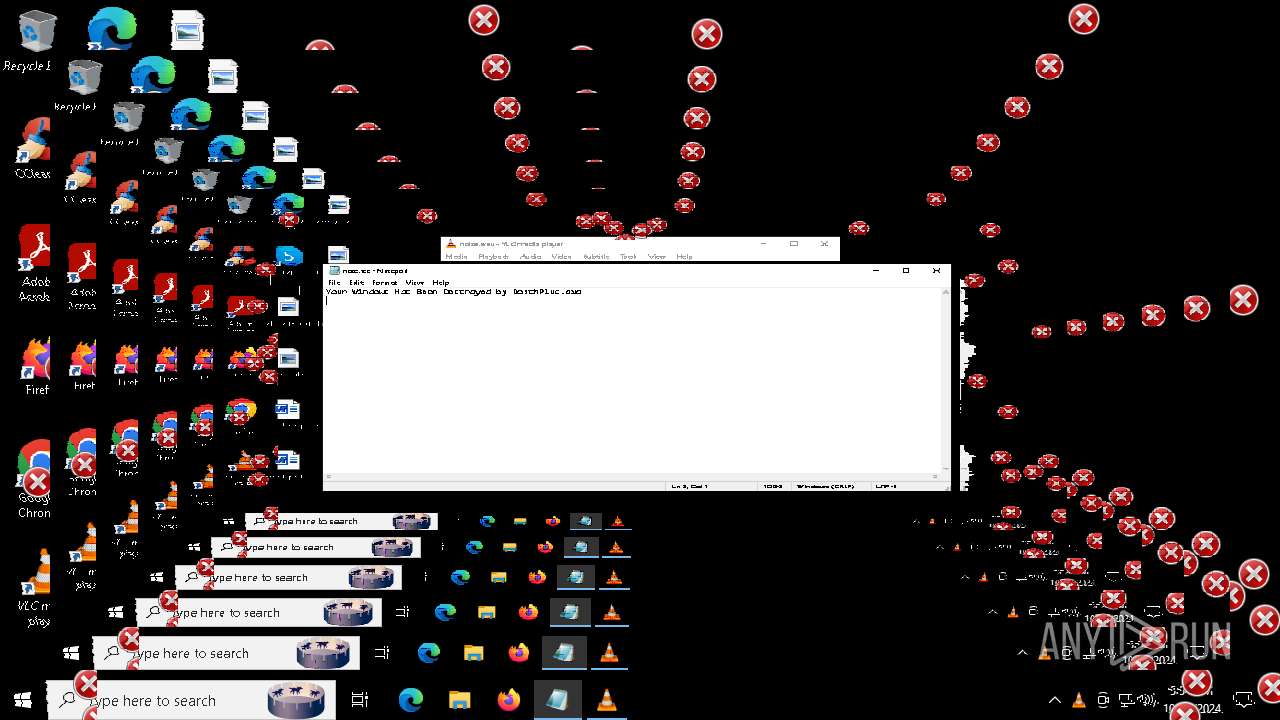
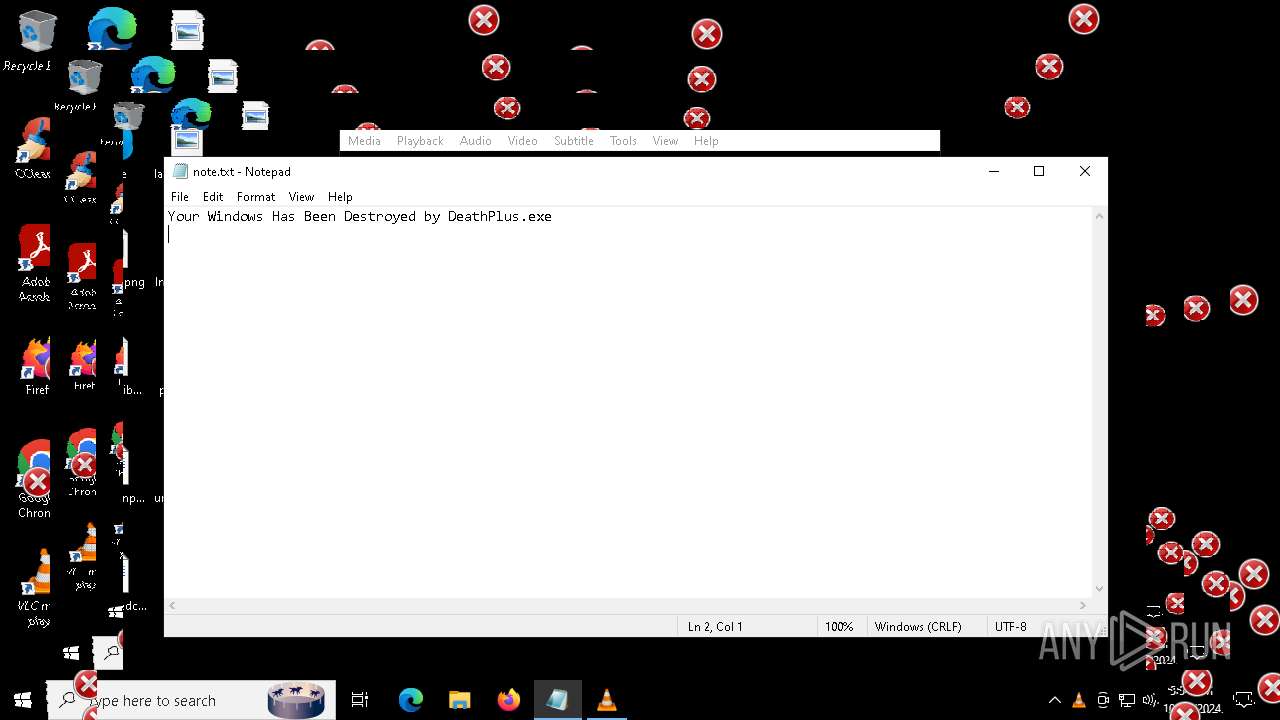
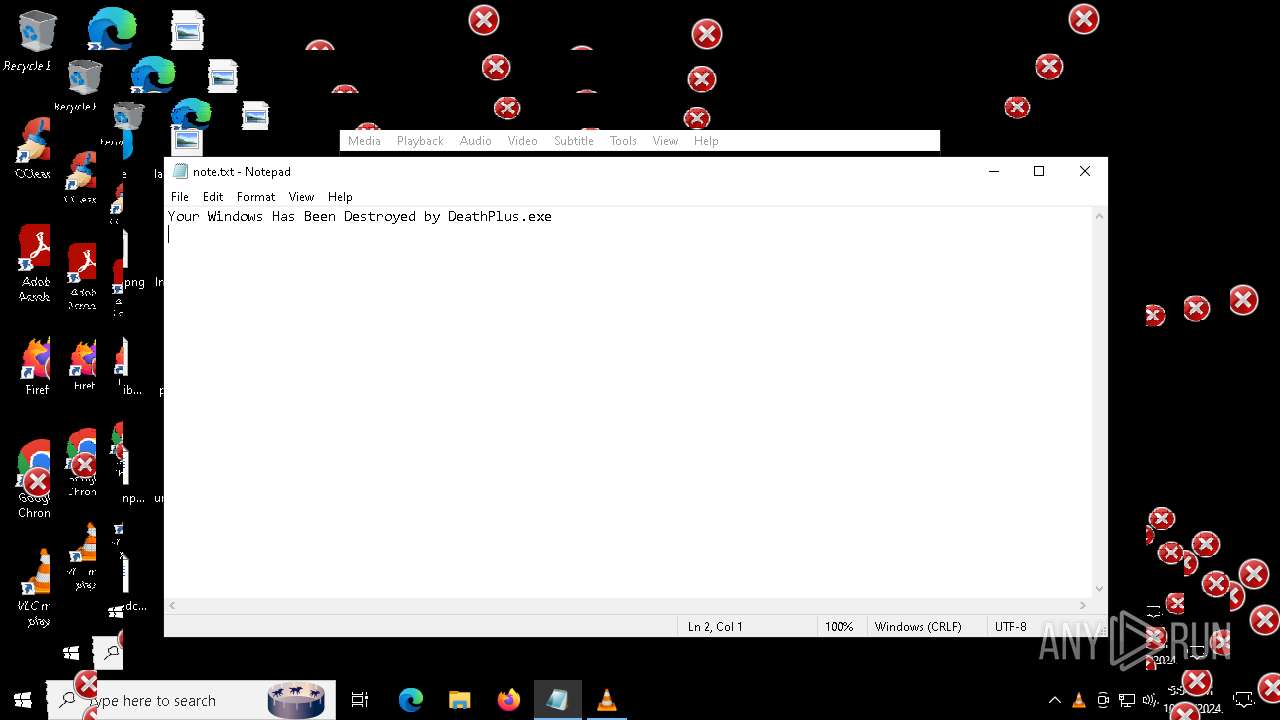
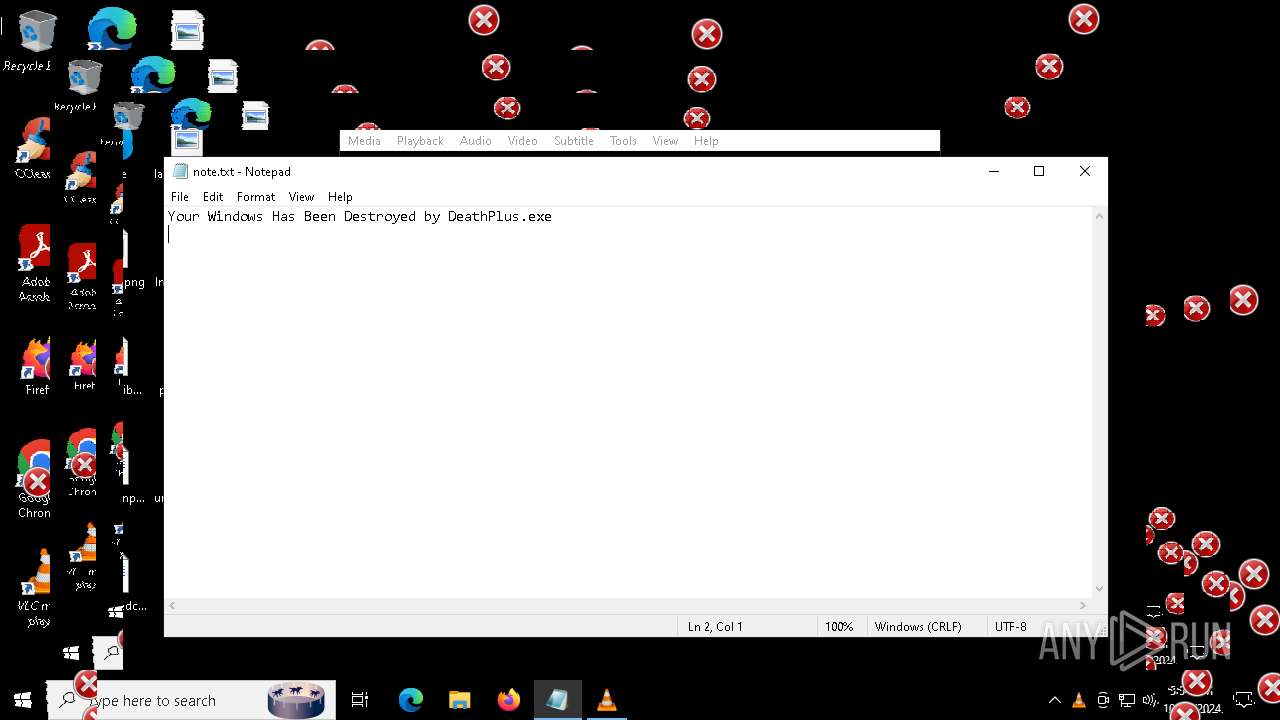
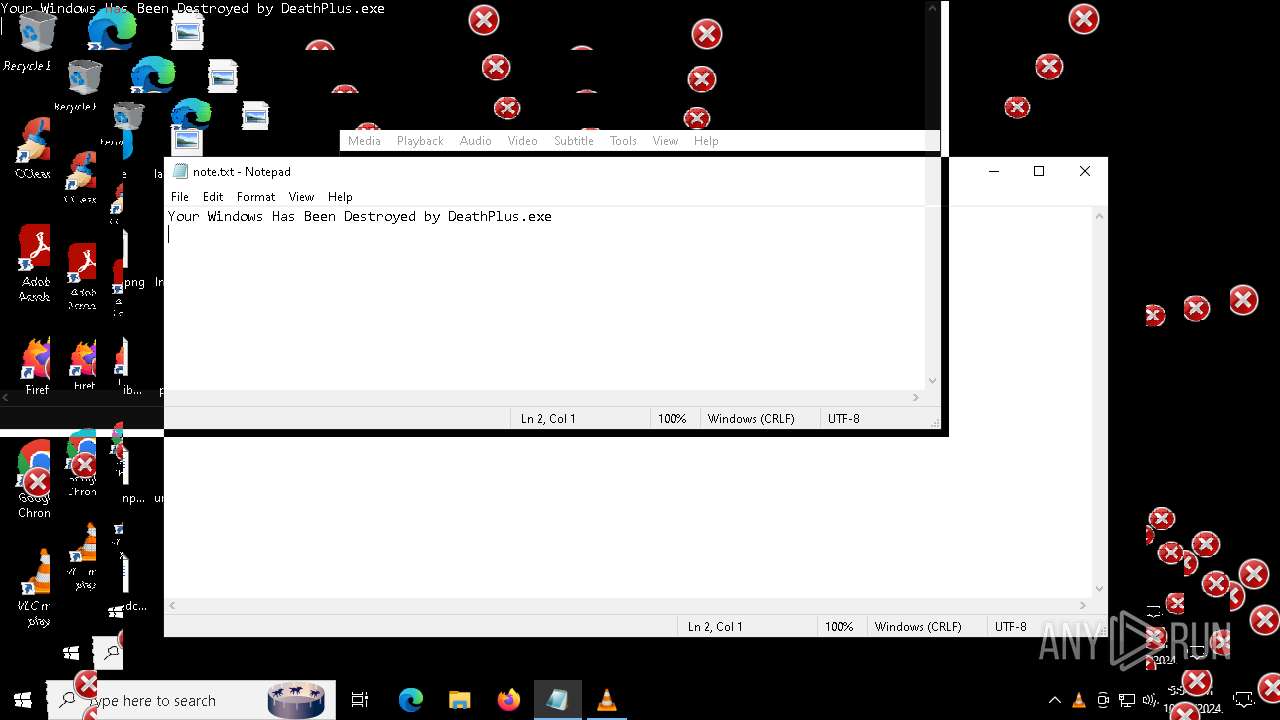
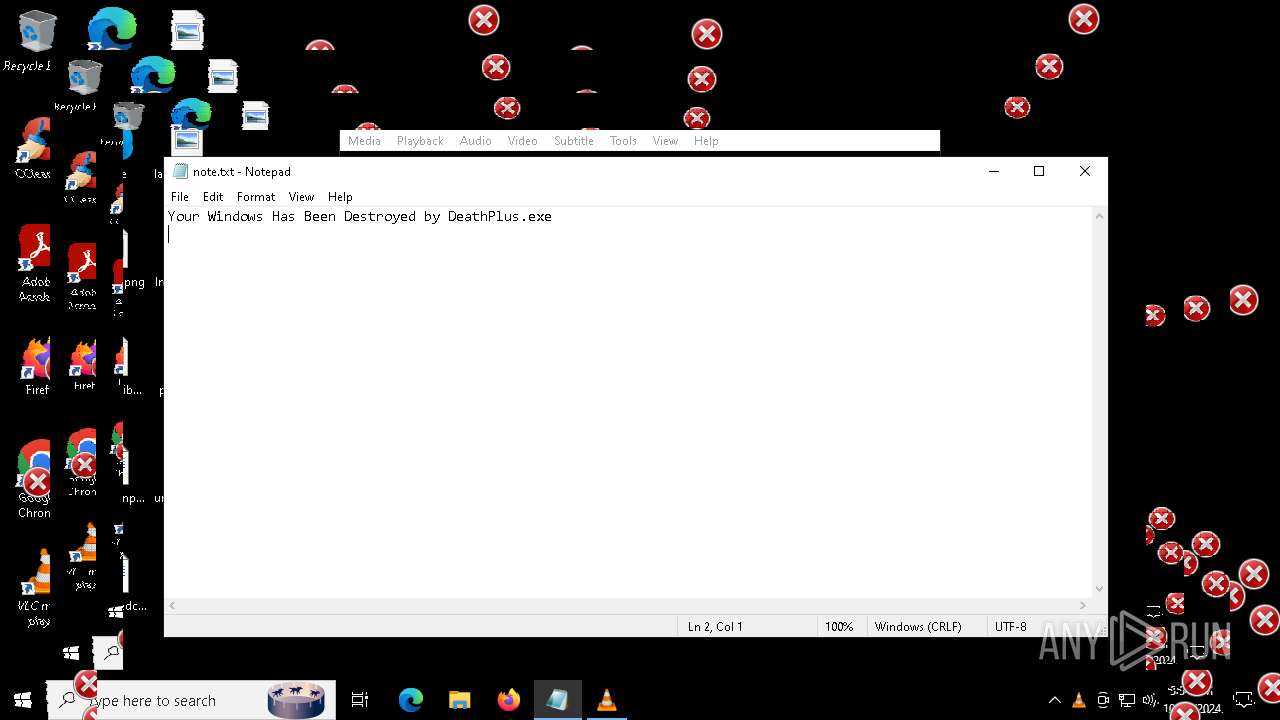
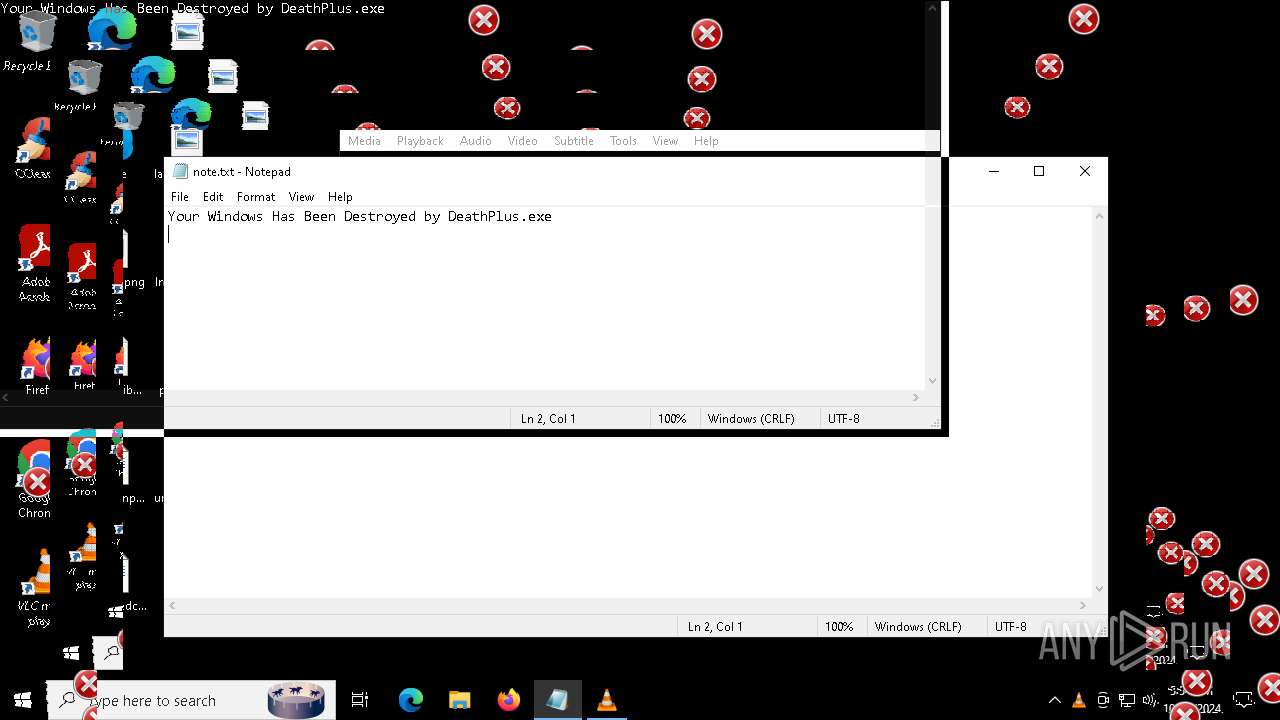
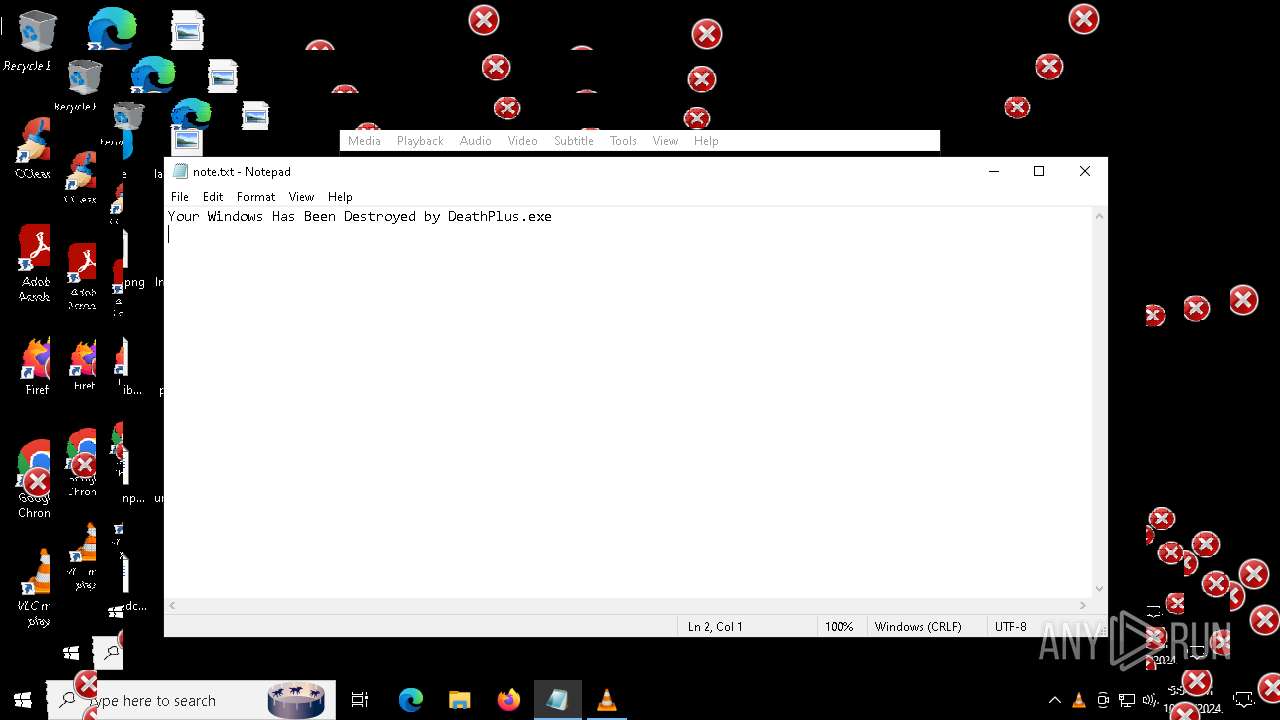
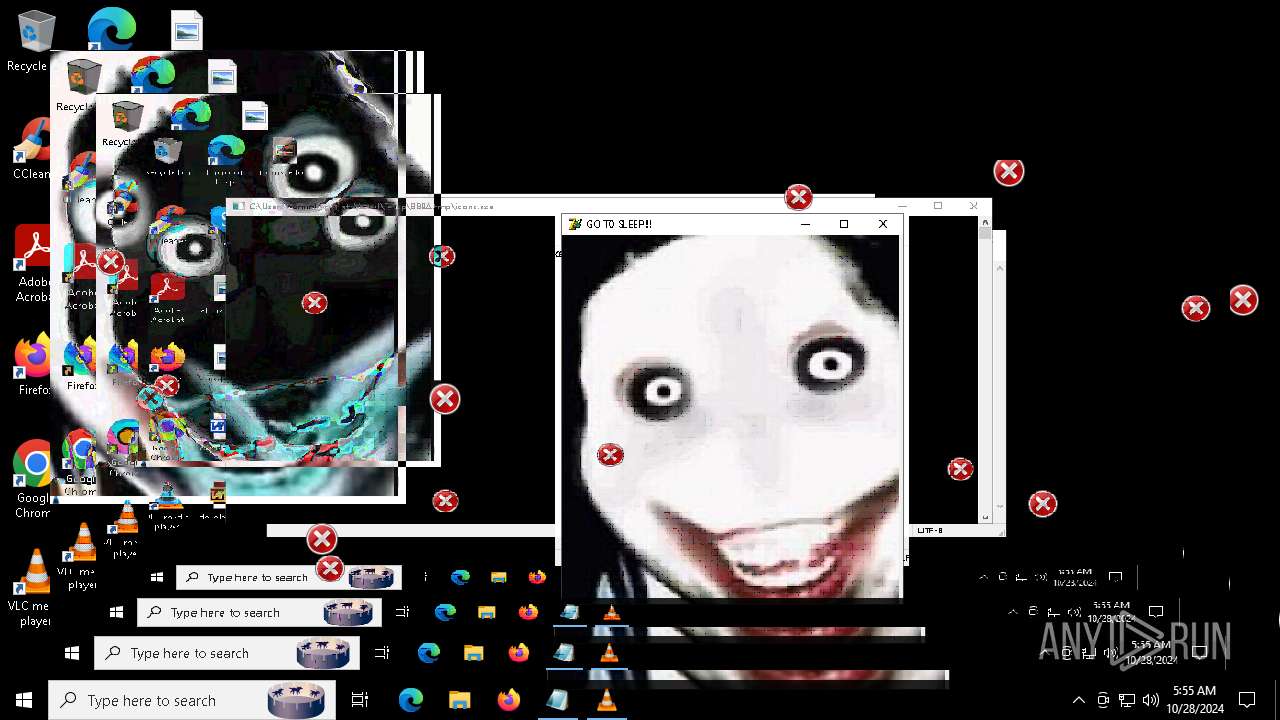
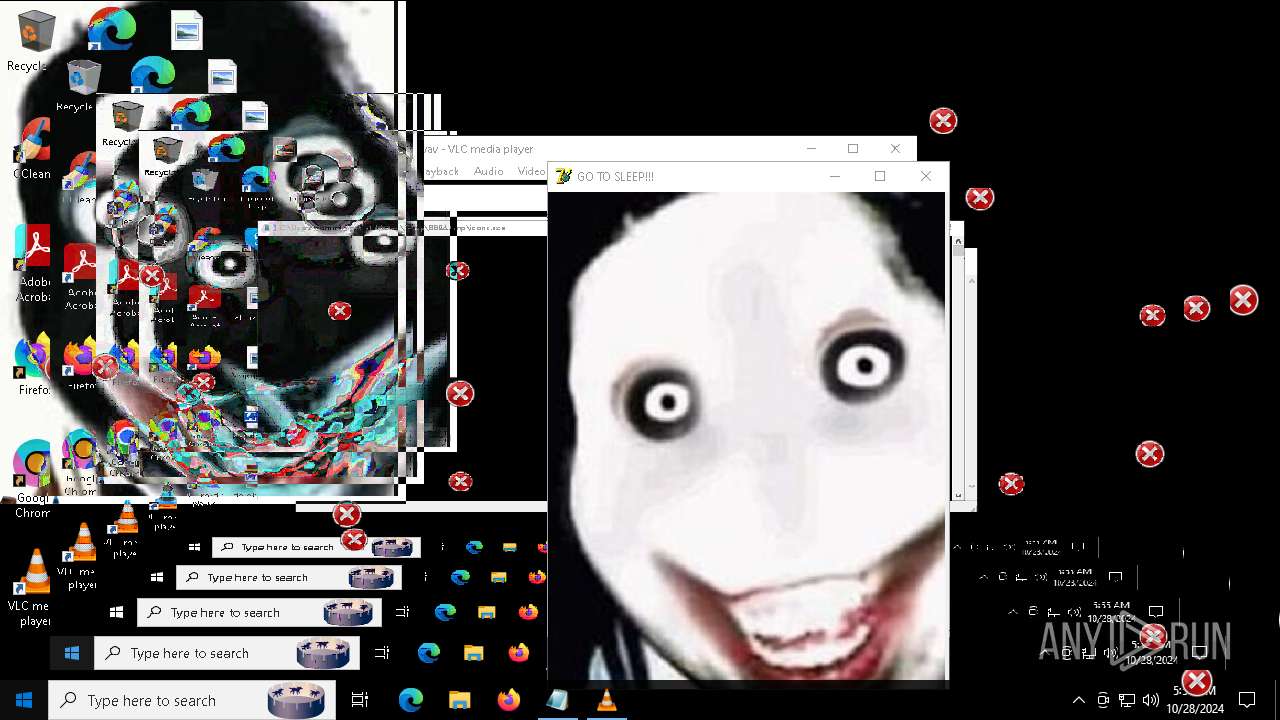
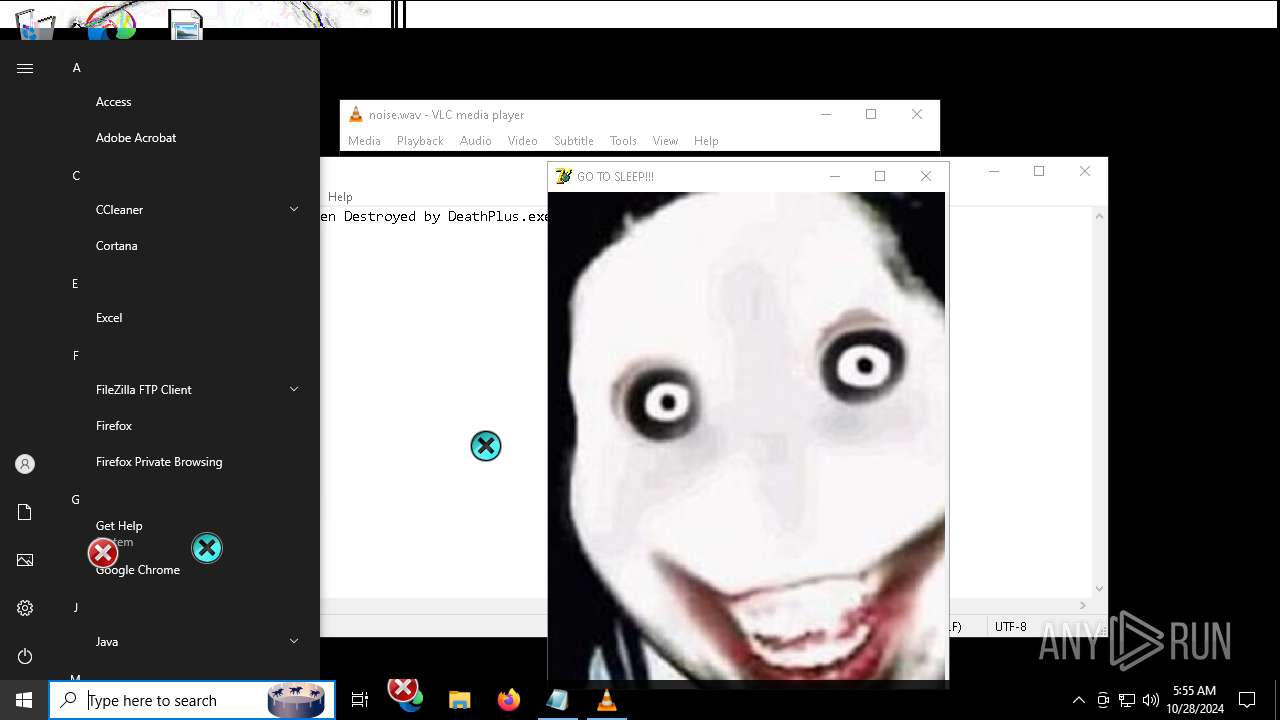
| File name: | Halloween.exe |
| Full analysis: | https://app.any.run/tasks/75c2d25b-4c29-4031-928c-6859747adcab |
| Verdict: | Malicious activity |
| Analysis date: | October 28, 2024, 05:54:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | F0ECDCCB410A0F4E01CD6D41A52D56B2 |
| SHA1: | 23D1452A0FA794D6EE03B786DD4CF9EC189904CE |
| SHA256: | F23233BFFB08FCBBDA8237FECE95003BEA1453466150BE0EB0B2F0860A34B72E |
| SSDEEP: | 98304:TgTYVfYa4uckN1T6ZbyeC/xij1A+LEew5/19SOGqSWqlz1Ymh5uC7o+vIeKJVJ:aNickN1T6Fyx/g/E75/19SOGLWqlBNhE |
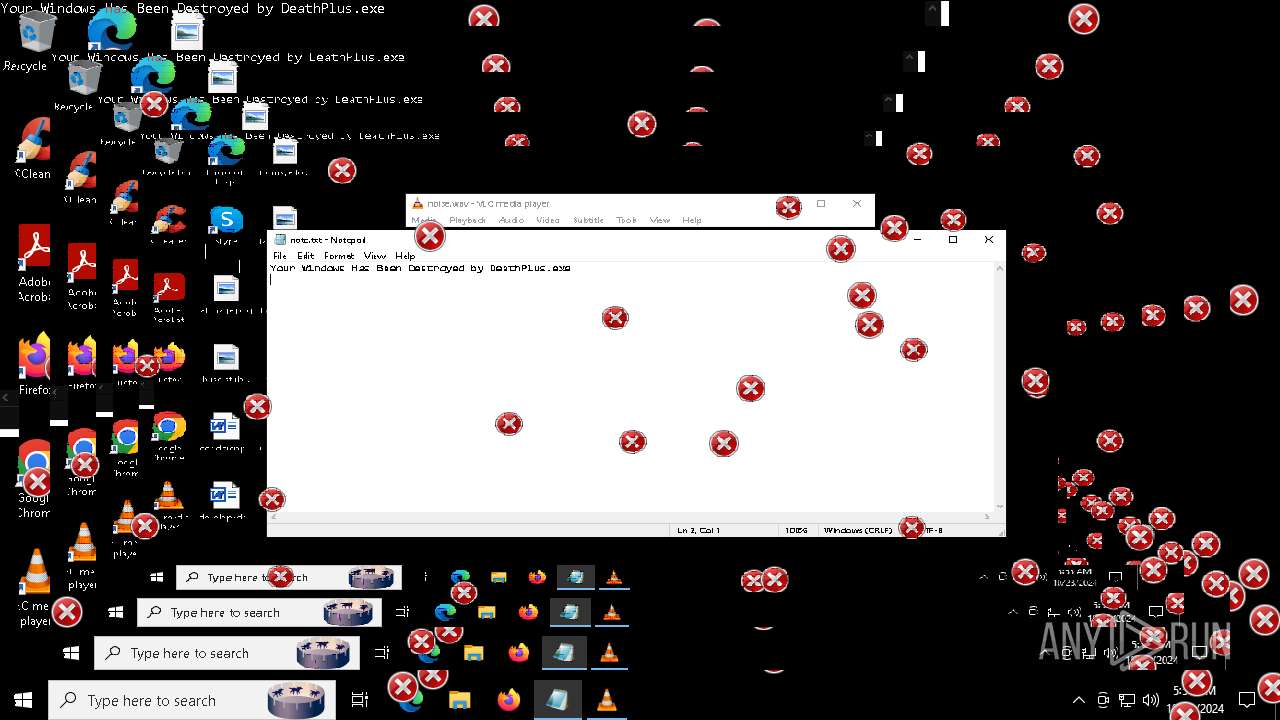
MALICIOUS
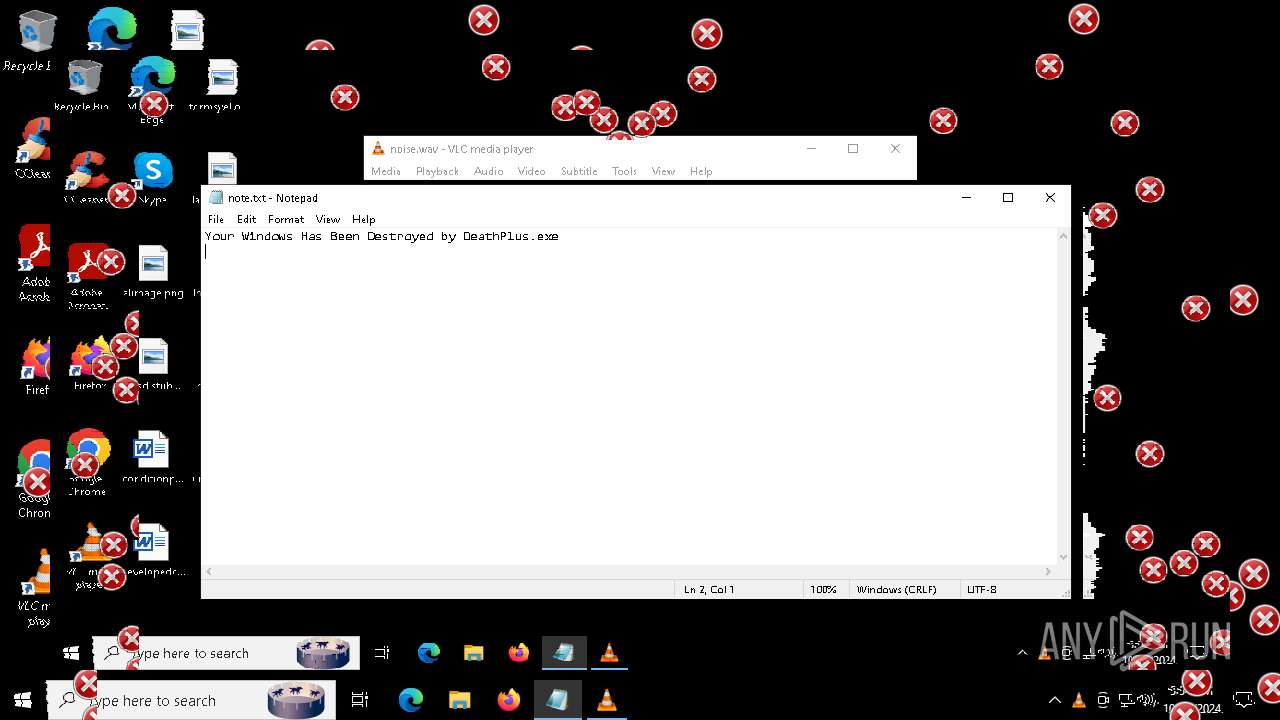
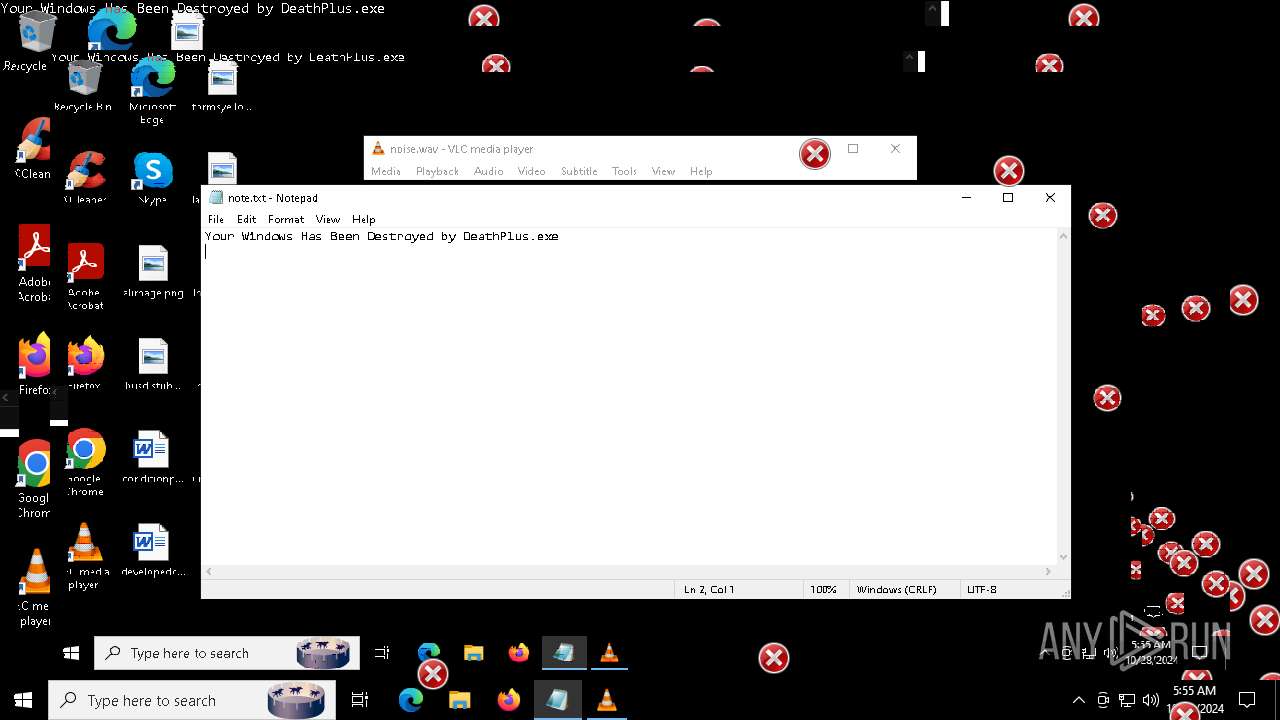
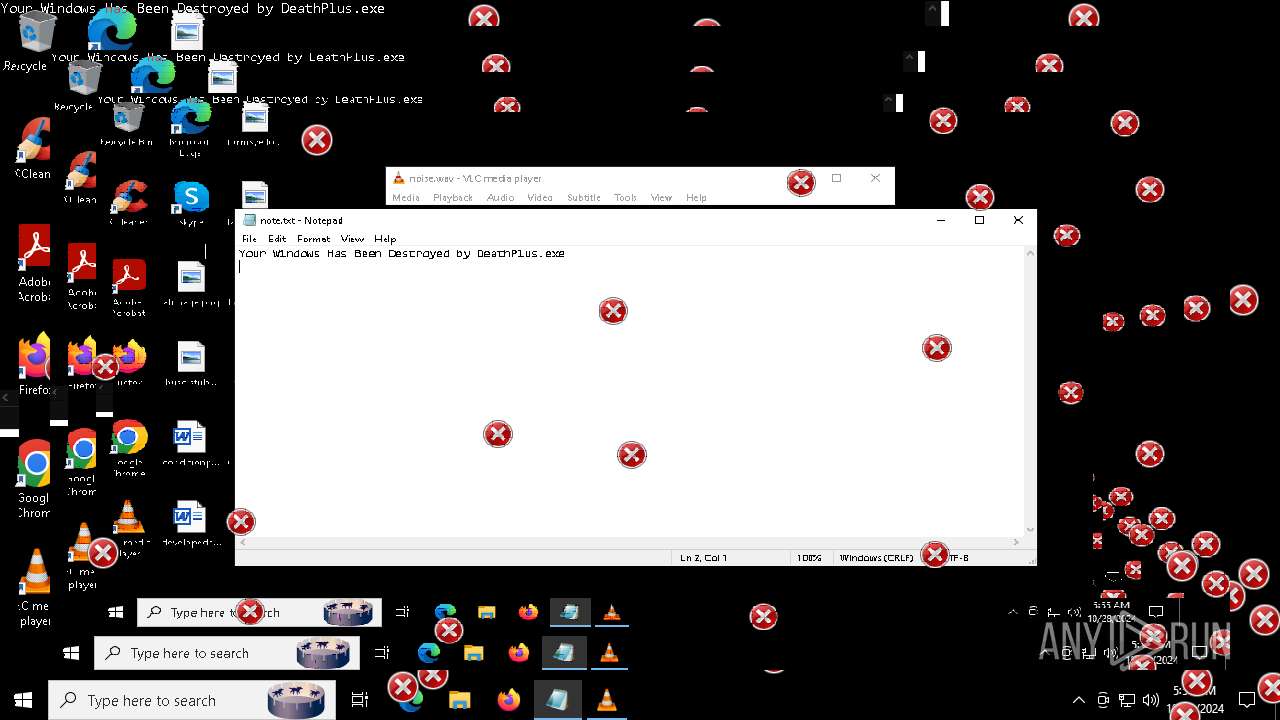
Uses Task Scheduler to run other applications
- MBRKiller.exe (PID: 6740)
Changes the autorun value in the registry
- MBRKiller.exe (PID: 6740)
SUSPICIOUS
Reads security settings of Internet Explorer
- Halloween.exe (PID: 1732)
Executable content was dropped or overwritten
- Halloween.exe (PID: 1732)
The executable file from the user directory is run by the CMD process
- MBRKiller.exe (PID: 6740)
- CLWCP.exe (PID: 1372)
- waves.exe (PID: 5324)
- tunnel.exe (PID: 5952)
- icons.exe (PID: 6340)
- tunnel.exe (PID: 7000)
- BitBlt.exe (PID: 6556)
- icons.exe (PID: 1588)
- CLWCP.exe (PID: 6336)
- scream.exe (PID: 612)
- scream.exe (PID: 3852)
- scream.exe (PID: 6504)
- scream.exe (PID: 6364)
- scream.exe (PID: 5736)
- scream.exe (PID: 6556)
- scream.exe (PID: 2432)
- scream.exe (PID: 2808)
- scream.exe (PID: 2084)
- scream.exe (PID: 6552)
- scream.exe (PID: 2124)
- scream.exe (PID: 6644)
- scream.exe (PID: 2196)
- scream.exe (PID: 4836)
- scream.exe (PID: 2464)
- scream.exe (PID: 6456)
- scream.exe (PID: 2184)
- scream.exe (PID: 7164)
- scream.exe (PID: 528)
- scream.exe (PID: 6384)
- BitBlt.exe (PID: 6832)
- tunnel.exe (PID: 7096)
- CLWCP.exe (PID: 1588)
- icons.exe (PID: 5524)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6708)
Executing commands from a ".bat" file
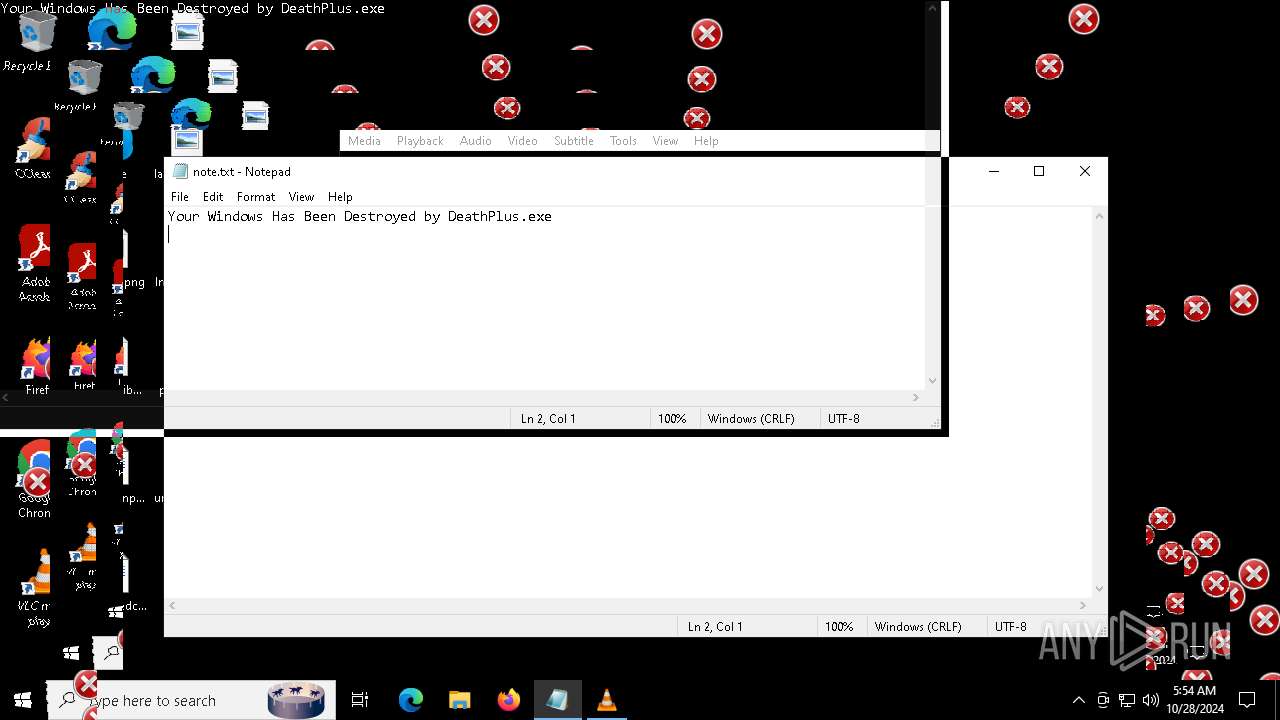
- Halloween.exe (PID: 1732)
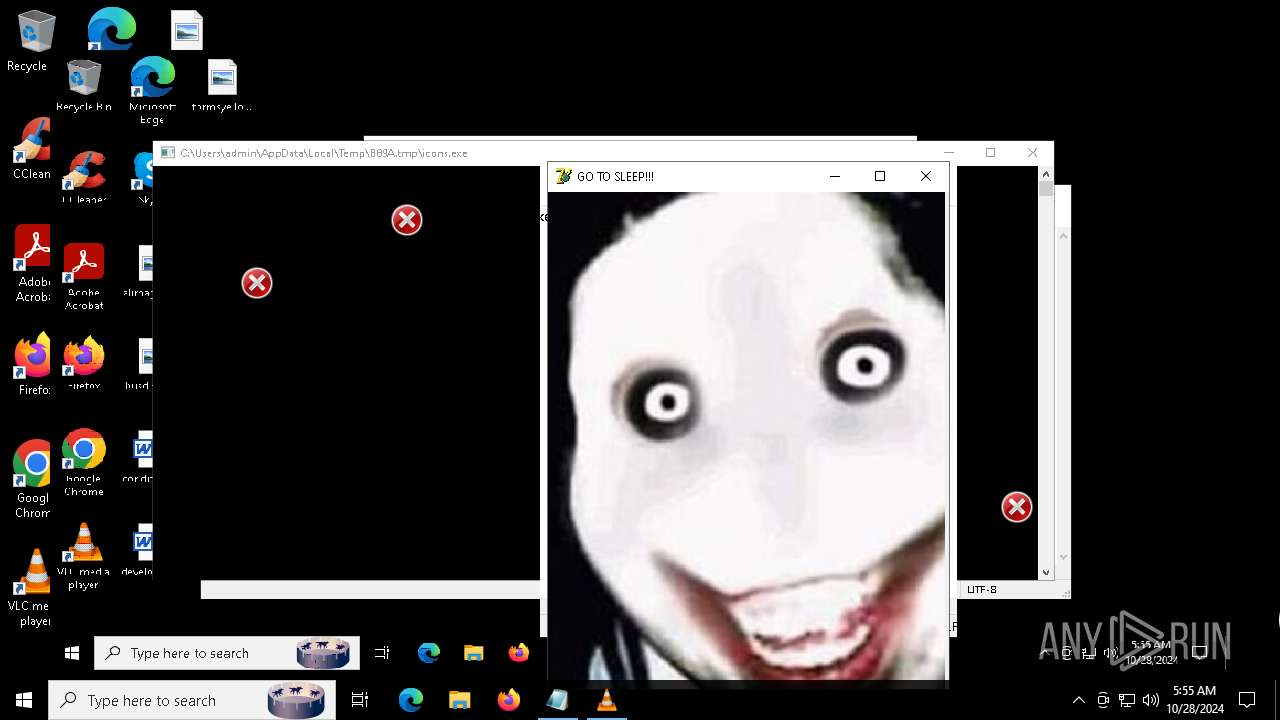
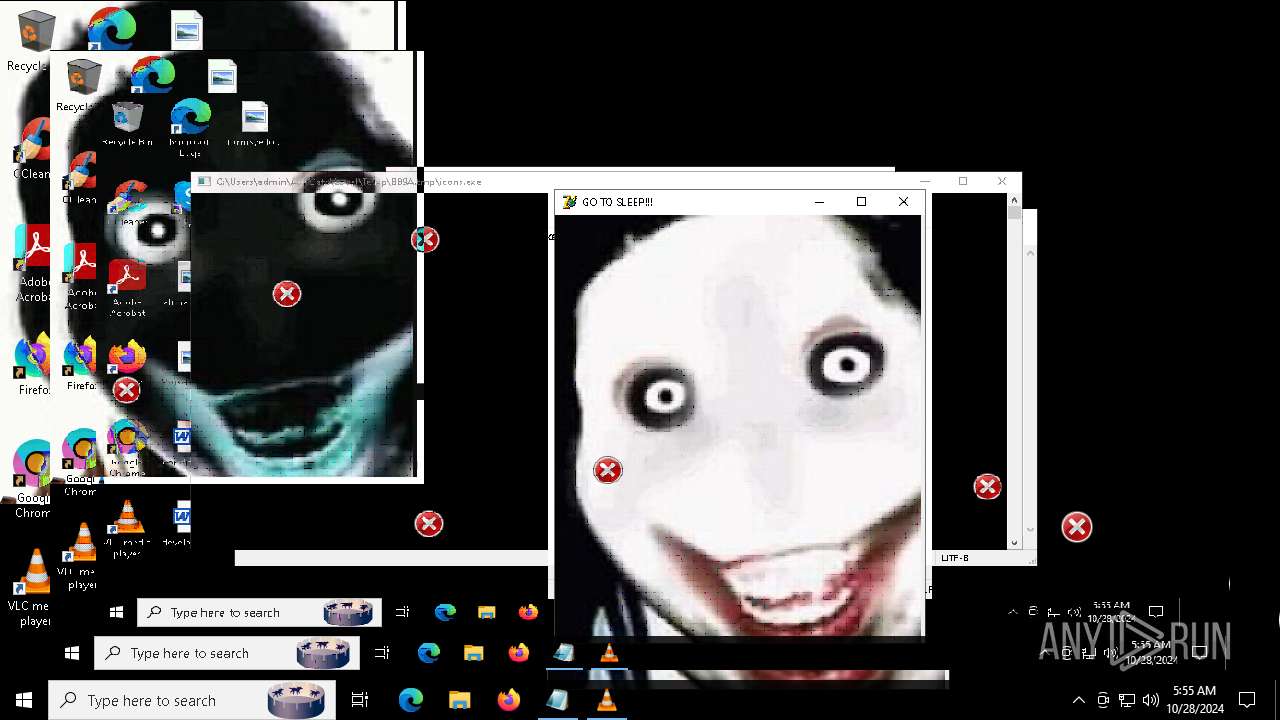
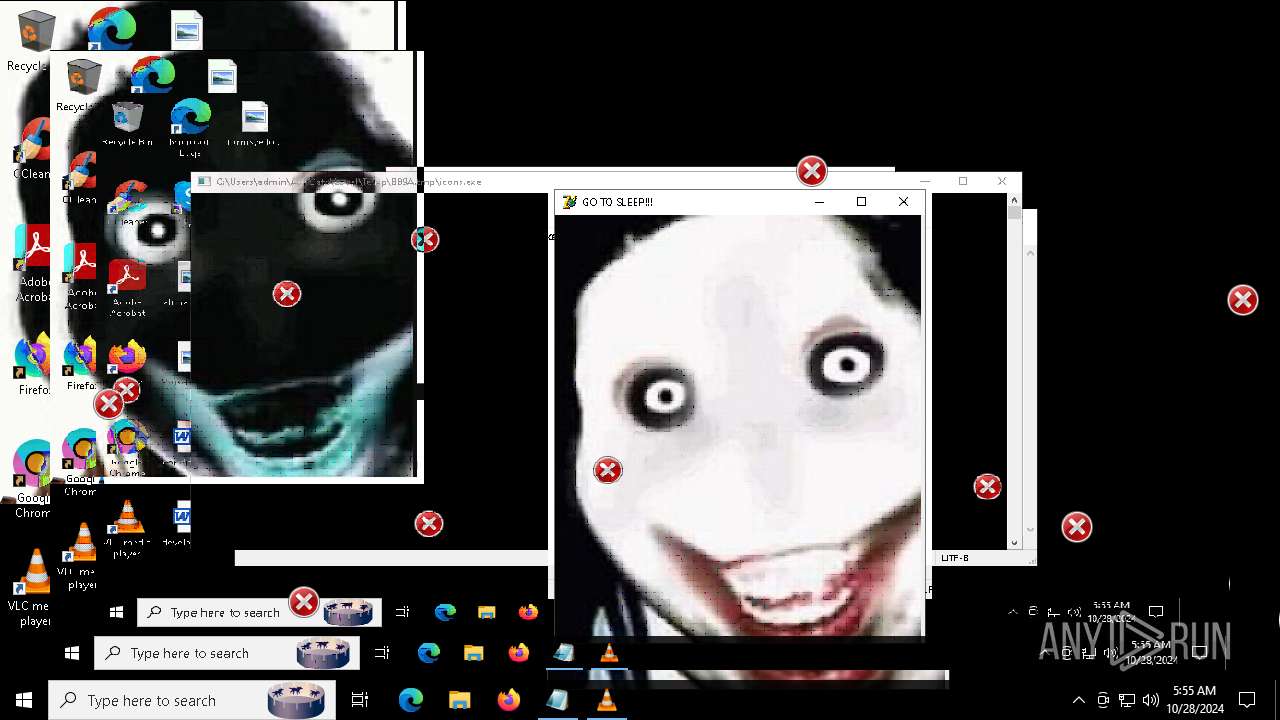
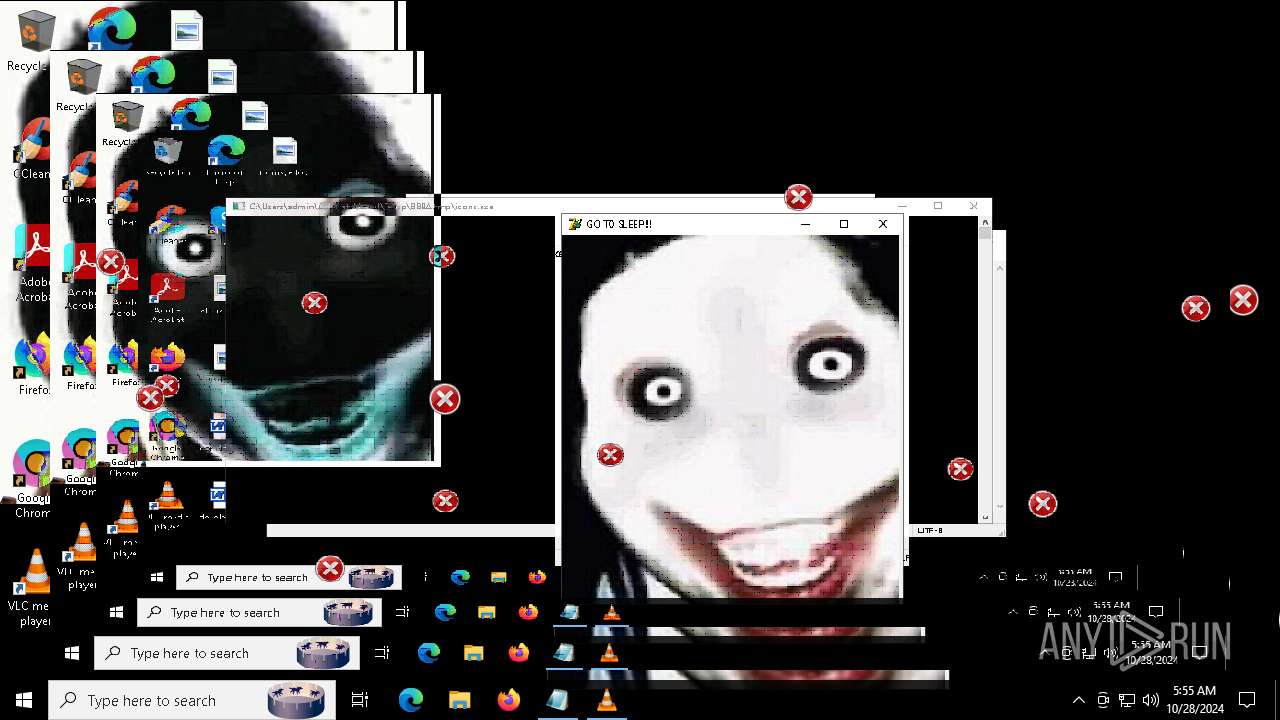
Probably fake Windows Update
- schtasks.exe (PID: 6300)
Starts CMD.EXE for commands execution
- Halloween.exe (PID: 1732)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6708)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6708)
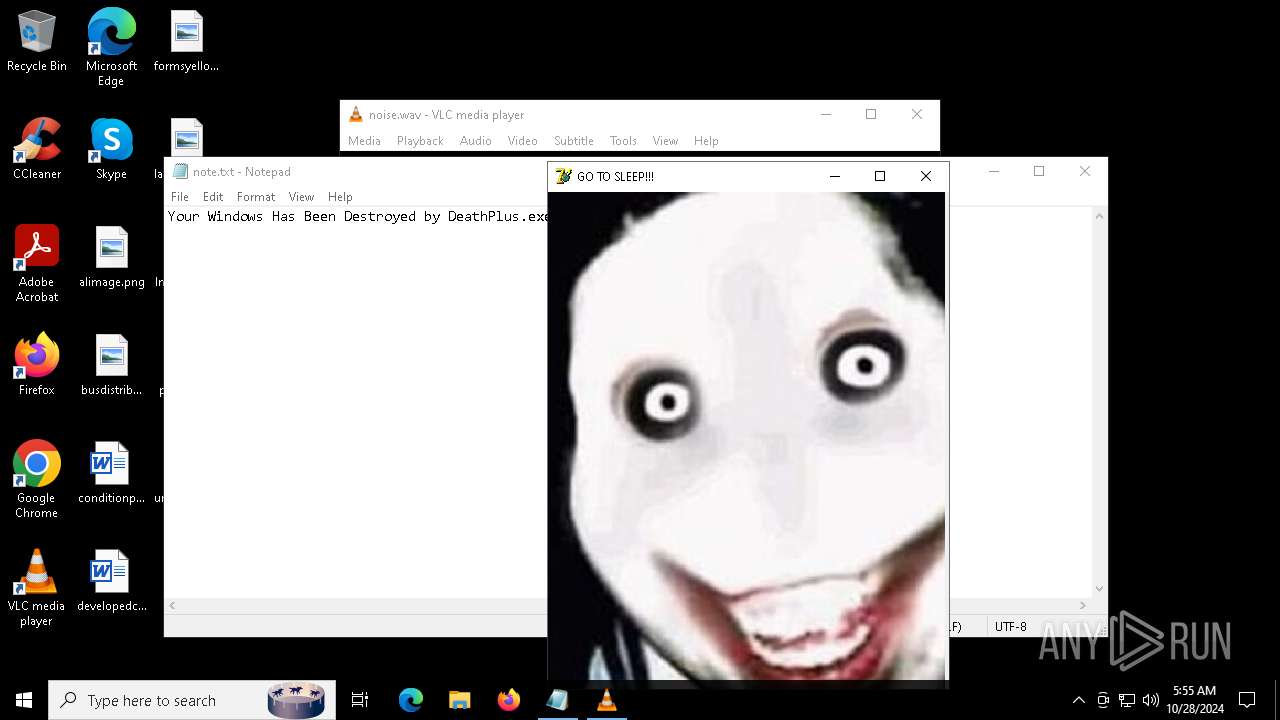
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 4224)
INFO
Create files in a temporary directory
- Halloween.exe (PID: 1732)
Reads the computer name
- Halloween.exe (PID: 1732)
- vlc.exe (PID: 4224)
Checks supported languages
- Halloween.exe (PID: 1732)
- MBRKiller.exe (PID: 6740)
- vlc.exe (PID: 4224)
- CLWCP.exe (PID: 1372)
The process uses the downloaded file
- Halloween.exe (PID: 1732)
- cmd.exe (PID: 6708)
Process checks computer location settings
- Halloween.exe (PID: 1732)
Sends debugging messages
- vlc.exe (PID: 4224)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6828)
The process uses Lua
- vlc.exe (PID: 4224)
UPX packer has been detected
- Halloween.exe (PID: 1732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 5767168 |
| InitializedDataSize: | 200704 |
| UninitializedDataSize: | 29433856 |
| EntryPoint: | 0x2191930 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
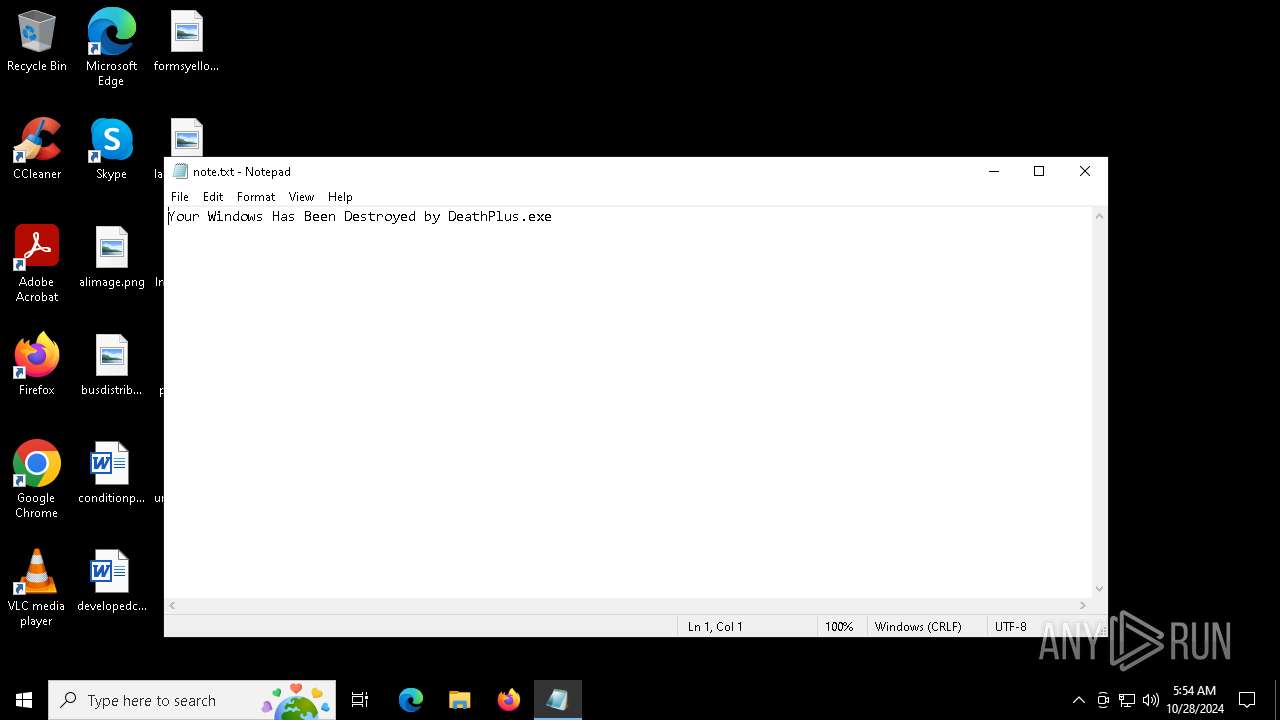
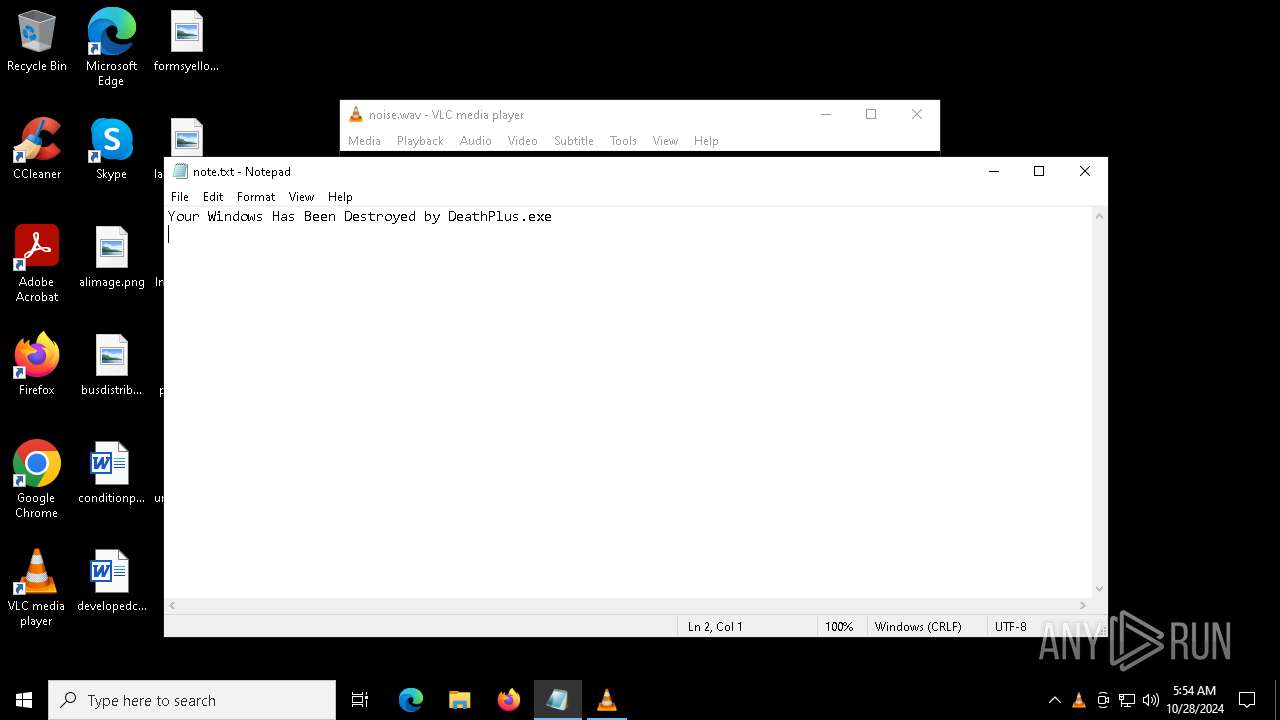
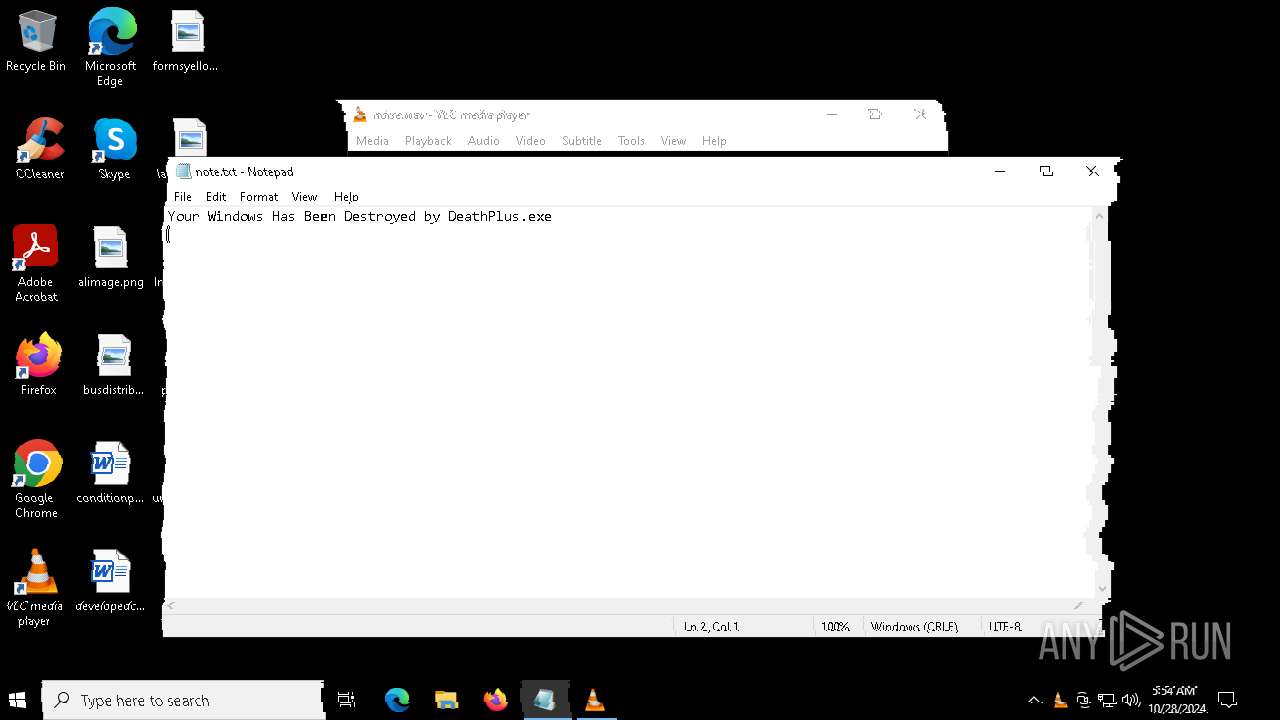
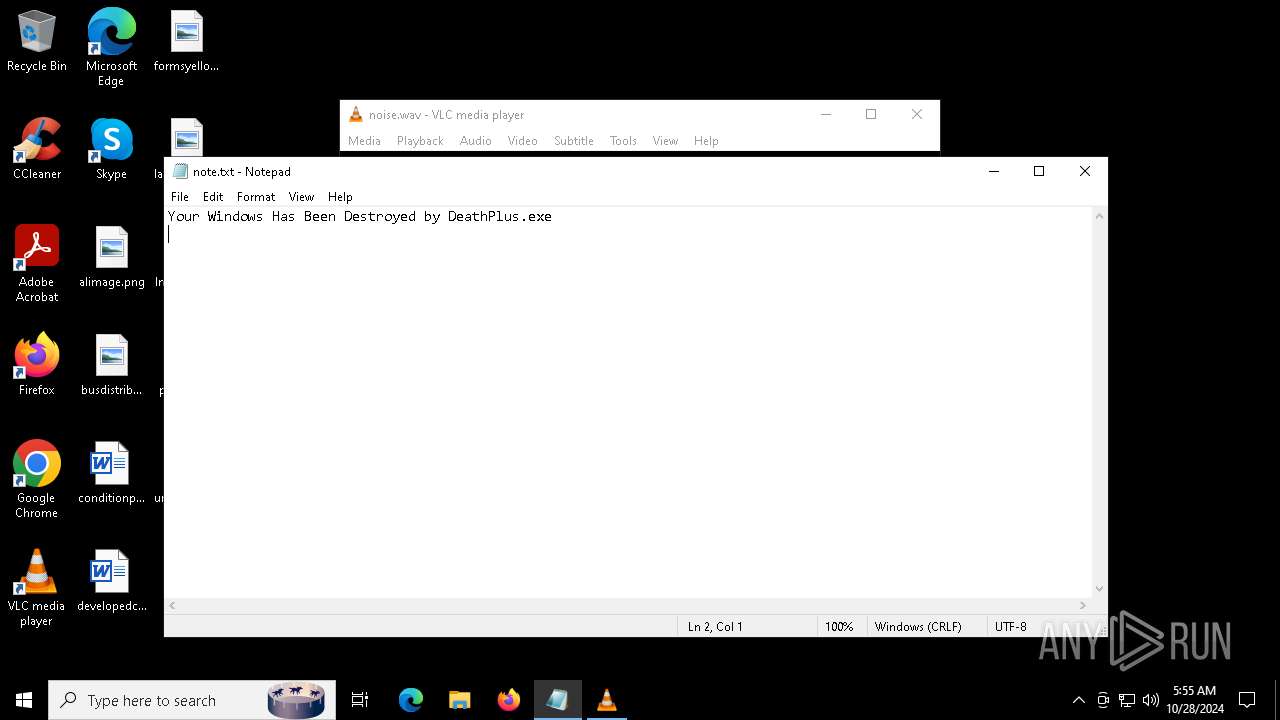
| FileDescription: | Do not run this on Real PC |
| FileVersion: | 1,0,0,0 |
| ProductName: | DeathPlus |
| ProductVersion: | 1,0,0,0 |
Total processes
208
Monitored processes
72
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | scream.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 612 | scream.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tunnel.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tunnel.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\AppData\Local\Temp\Halloween.exe" | C:\Users\admin\AppData\Local\Temp\Halloween.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1068 | timeout 10 /nobreak | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | clwcp clown.bmp | C:\Users\admin\AppData\Local\Temp\B89A.tmp\CLWCP.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1396 | timeout 10 /nobreak | C:\Windows\SysWOW64\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1440 | taskkill /f /im taskmgr.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1588 | icons.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\icons.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
Total events
5 029
Read events
5 021
Write events
6
Delete events
2
Modification events
| (PID) Process: | (6708) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.wav\OpenWithProgids |
| Operation: | write | Name: | VLC.wav |
Value: | |||
| (PID) Process: | (6692) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (6740) MBRKiller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Windows Update |
Value: | |||
| (PID) Process: | (6740) MBRKiller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Update |
Value: C:\Users\admin\AppData\Local\Temp\B89A.tmp\MBRKiller.exe | |||
| (PID) Process: | (6740) MBRKiller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Windows Update |
Value: C:\Users\admin\AppData\Local\Temp\B89A.tmp\MBRKiller.exe | |||
| (PID) Process: | (6708) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {E46787A1-4629-4423-A693-BE1F003B2742} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 0100000000000000850ABBCEFD28DB01 | |||
| (PID) Process: | (6708) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
Executable files
12
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\fnaf.bmp | — | |
MD5:— | SHA256:— | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\clown.bmp | — | |
MD5:— | SHA256:— | |||
| 6740 | MBRKiller.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\waves.exe | executable | |
MD5:D8E680AE1D2EDD79FC67B784B3A47921 | SHA256:DF6DCAEF3930C089873E74F85EC7F6BF390F84BB173BE3323D0B79262C4EE6D4 | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\DeathPlus.bat | text | |
MD5:892F11B37E59D1BB0D8ACCD66402E12D | SHA256:AB473B1B6AE32BCB465DDDBD0A8079A12611BD7A2AF5DF45367A0AA6764E3E8A | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\noise.wav | binary | |
MD5:6FB3826CE933E7748E14CB31D1E50A74 | SHA256:81EB82AC1911503143BBAA44646CFEDE618A0807E9DCCCEF09F1DEB4D8700CE4 | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\scare.mp4 | binary | |
MD5:17042B9E5FC04A571311CD484F17B9EB | SHA256:A9B0F1F849E0B41924F5E80B0C4948E63FC4B4F335BBDF0F997B03A3AFF55424 | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\tunnel.exe | executable | |
MD5:7DAE1FB2E3A65E8DD594B021A6923E24 | SHA256:732ADADB4C7167E61F0F5763C2C01E43FB01369683D23C9652AEA99F6C42C810 | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\skulls.bmp | image | |
MD5:F39D3B06F62B88D02D4DC93B4BED0E3C | SHA256:C85F12ED323E9AA3A943777CD23F4549697D5FF517D1EF2E2A887E7D165170F5 | |||
| 1732 | Halloween.exe | C:\Users\admin\AppData\Local\Temp\B89A.tmp\icons.exe | executable | |
MD5:3CA1D5768C2944D4284B1541653823C7 | SHA256:4172C6120F8F98685698365D6DD52C80EB2080203CDDE479009BF8F4FA770AF0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
42
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4692 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4692 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6172 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6908 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: opening config file (C:\Users\admin\AppData\Roaming\vlc\vlcrc)
|