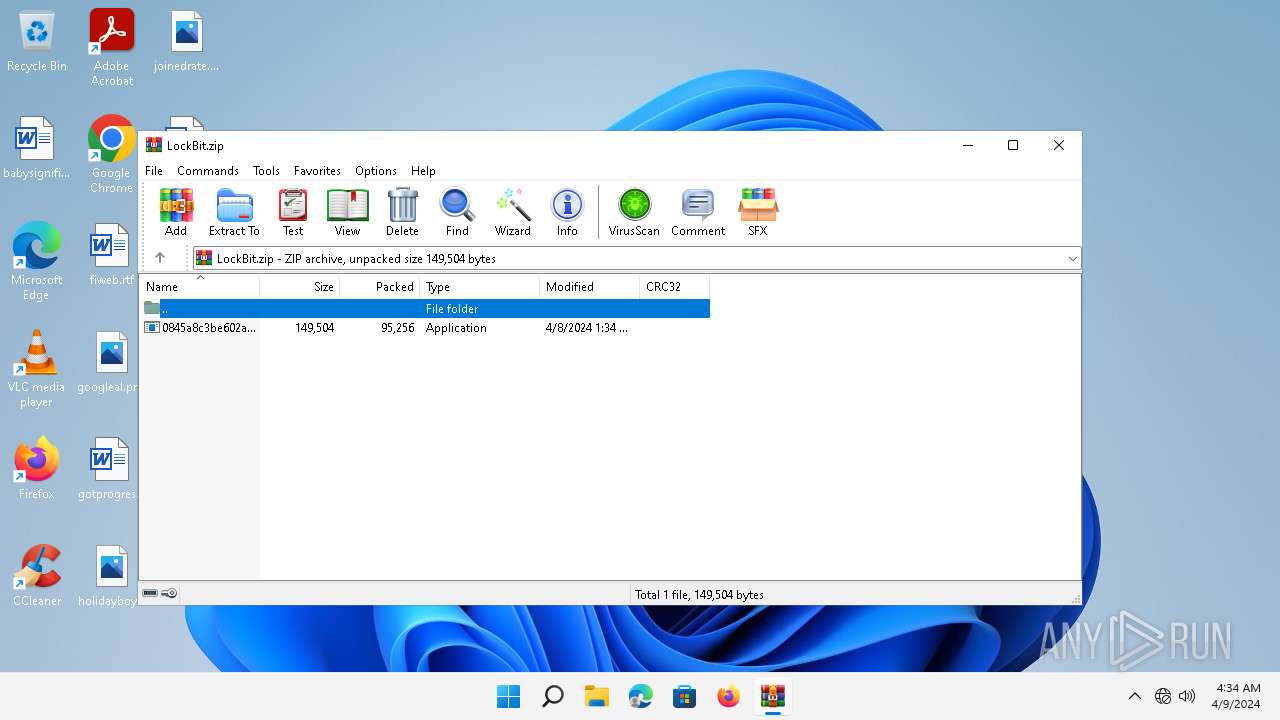
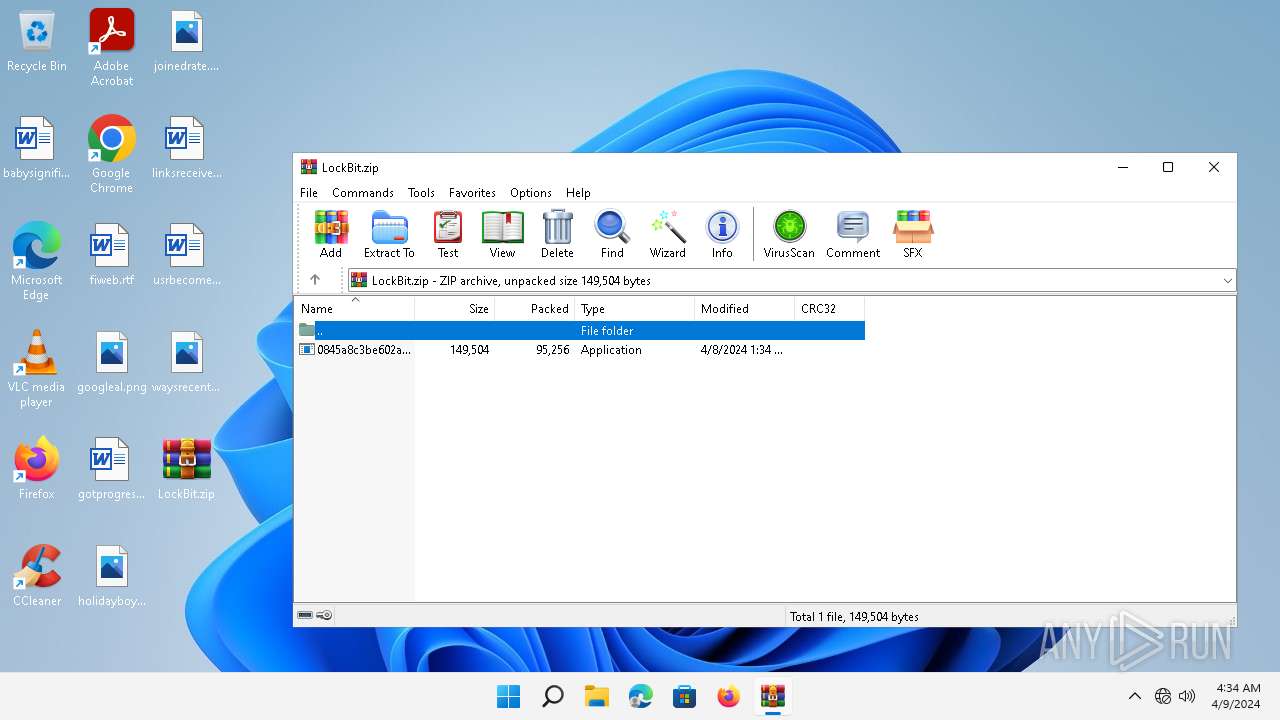
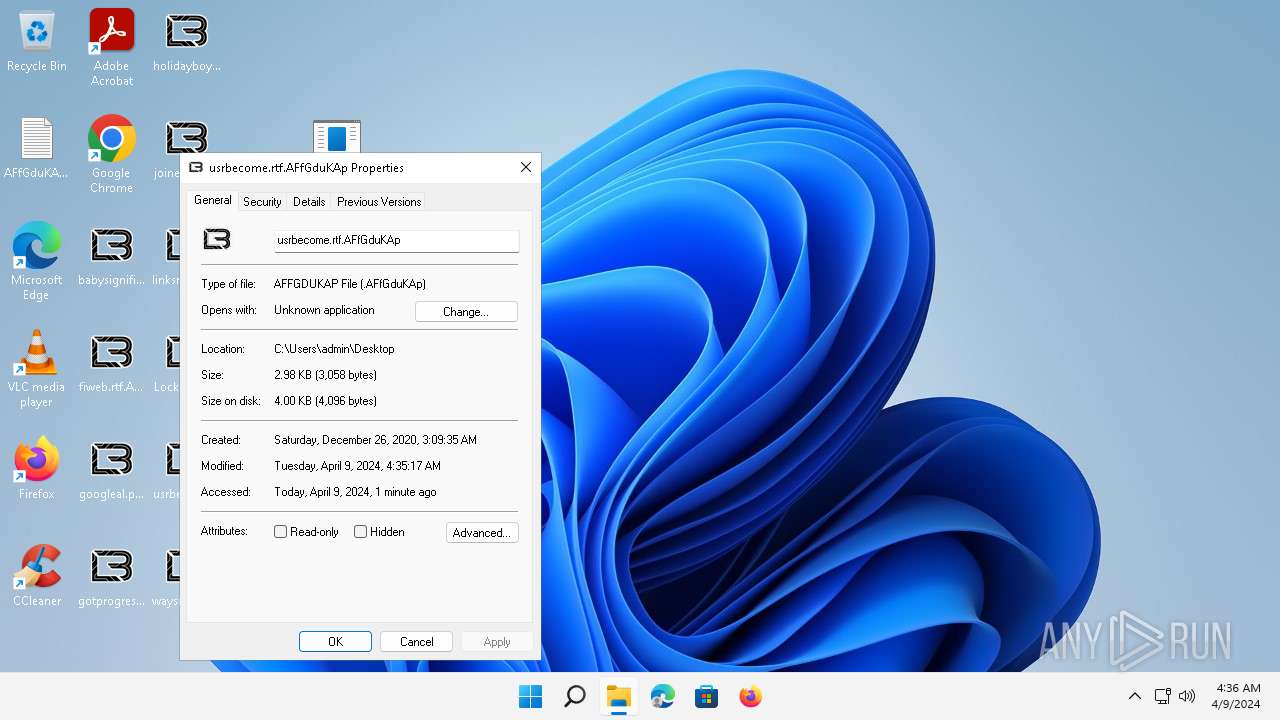
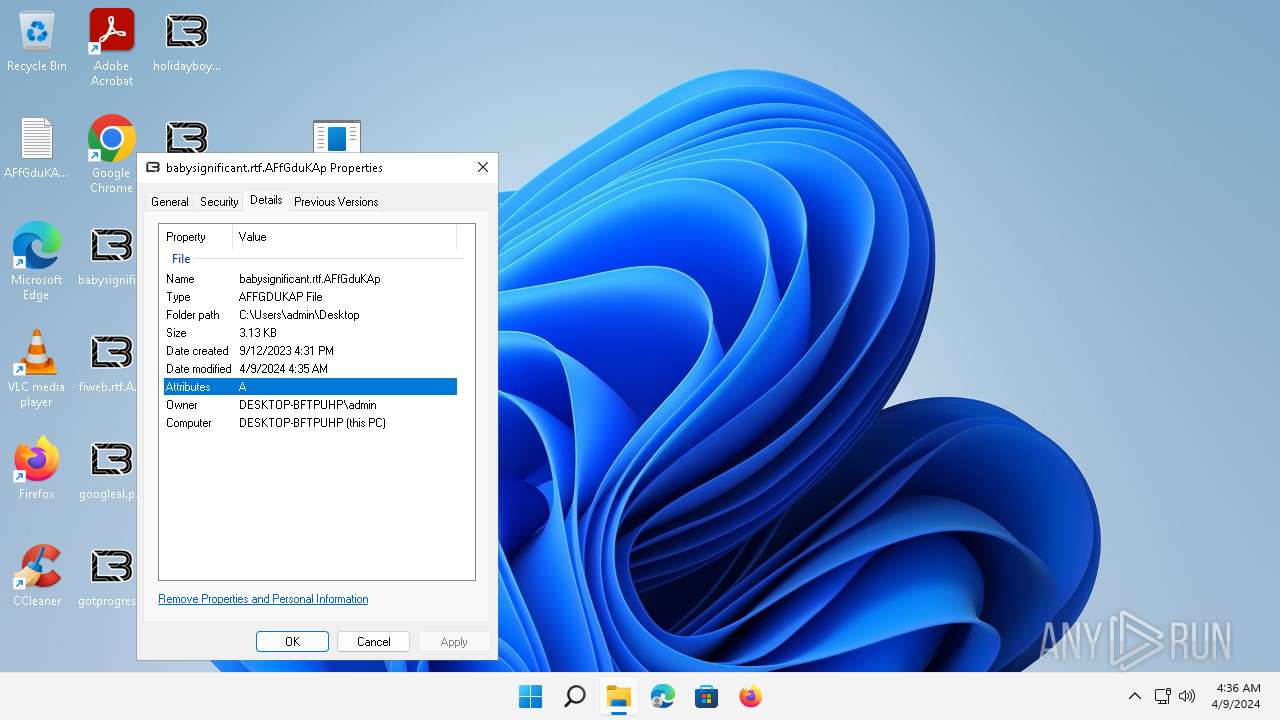
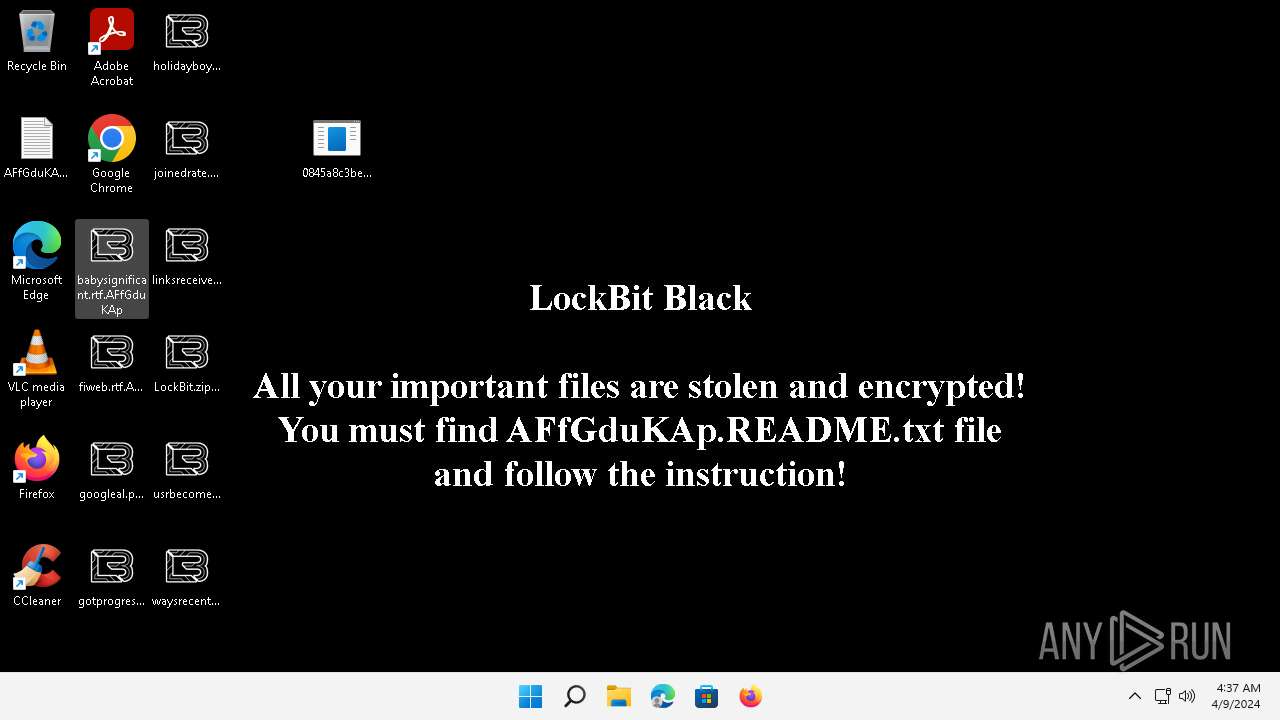
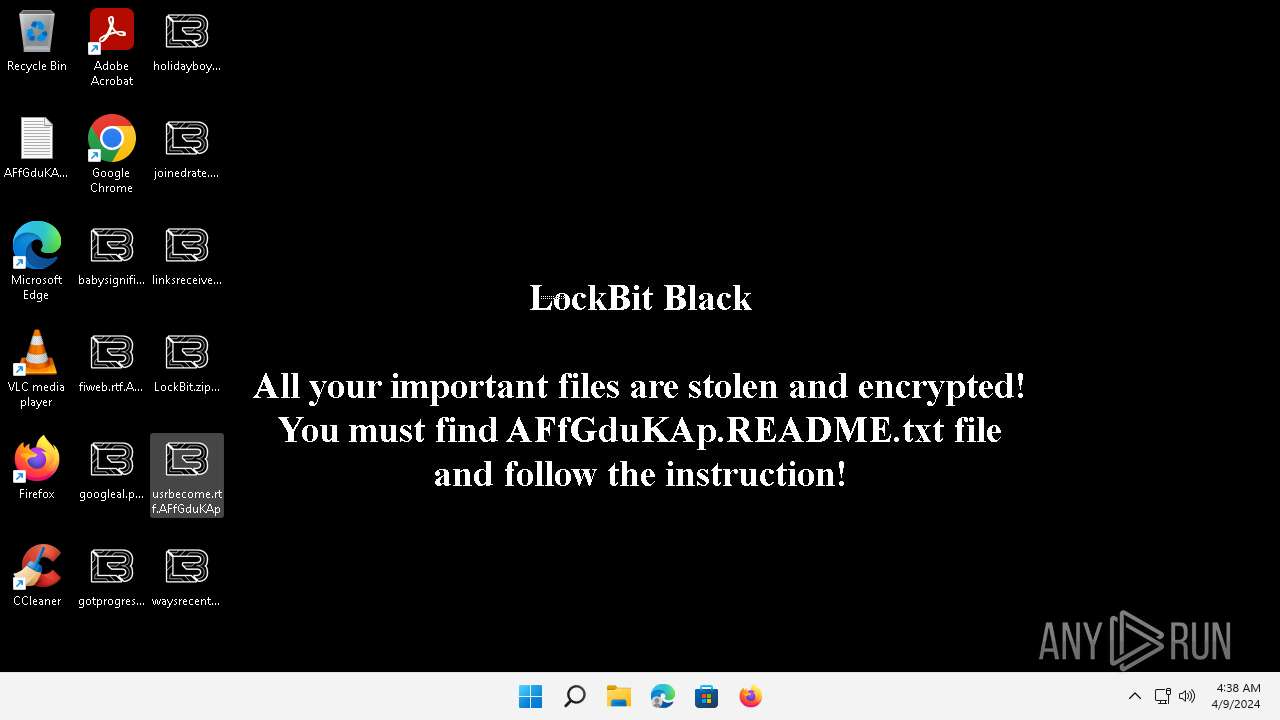
| File name: | LockBit.zip |
| Full analysis: | https://app.any.run/tasks/4b2cc7b2-106c-479d-859b-3a8afc3ce6f6 |
| Verdict: | Malicious activity |
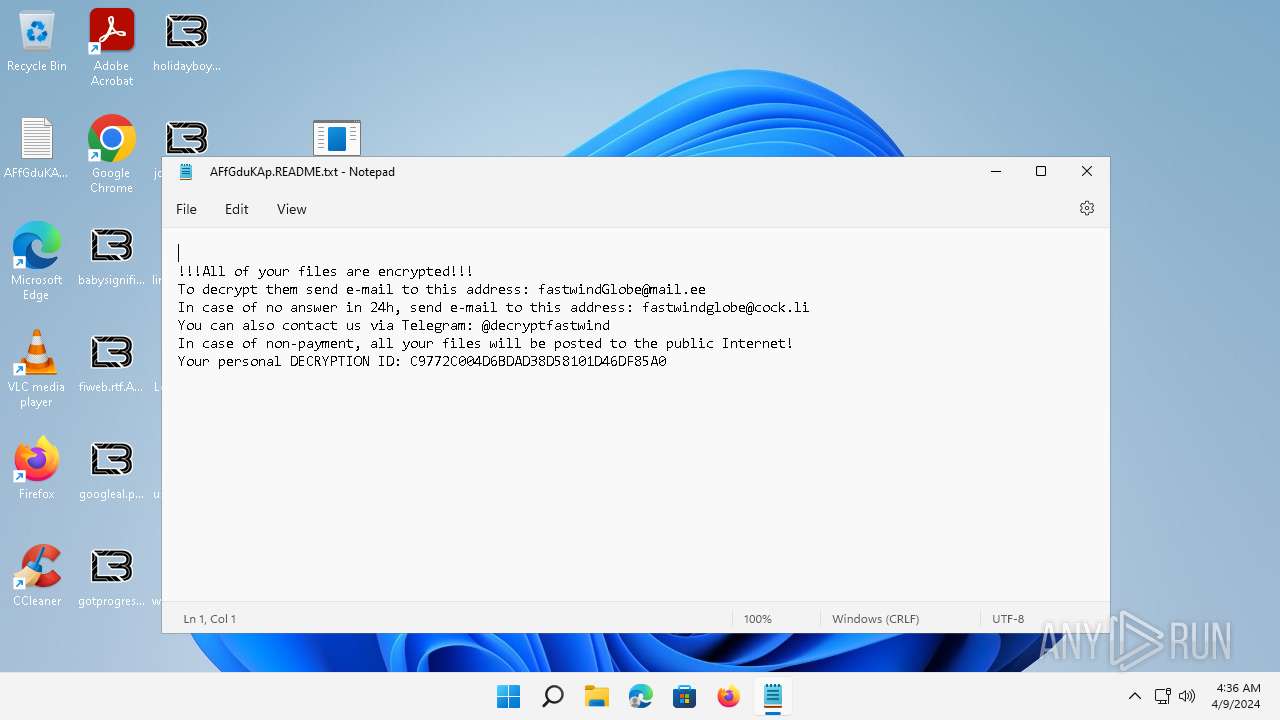
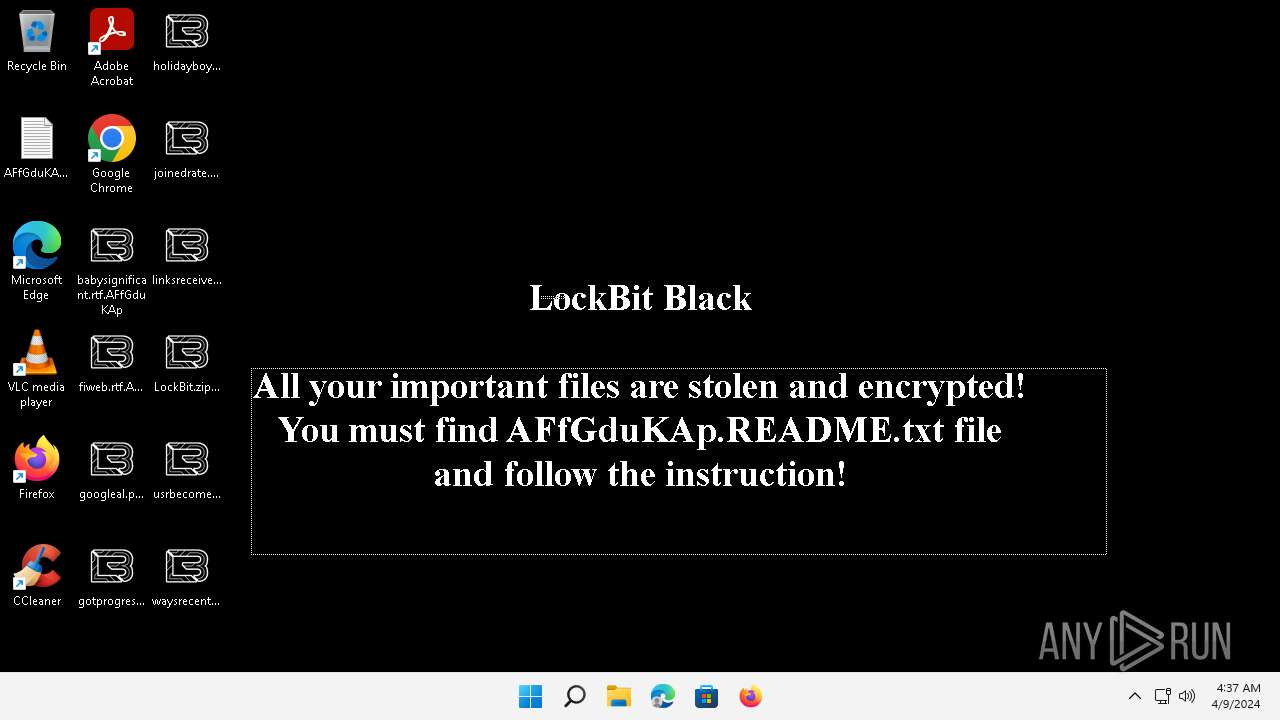
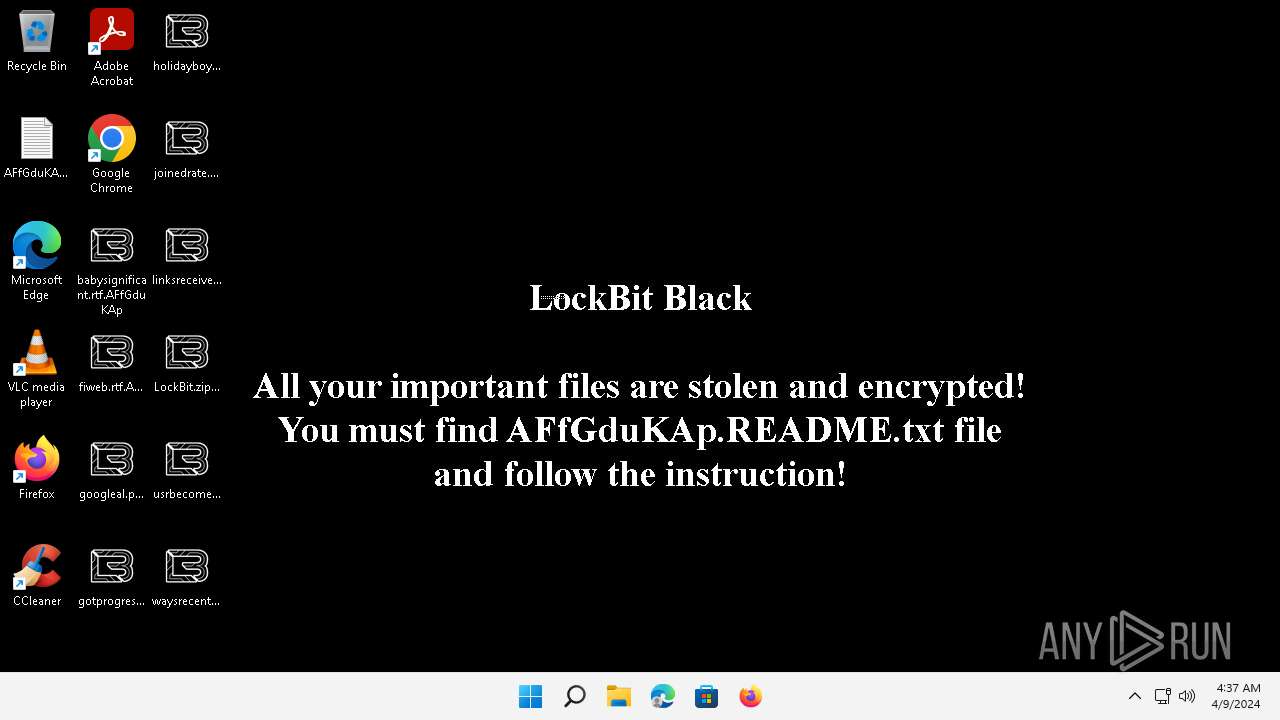
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | April 09, 2024, 04:33:52 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
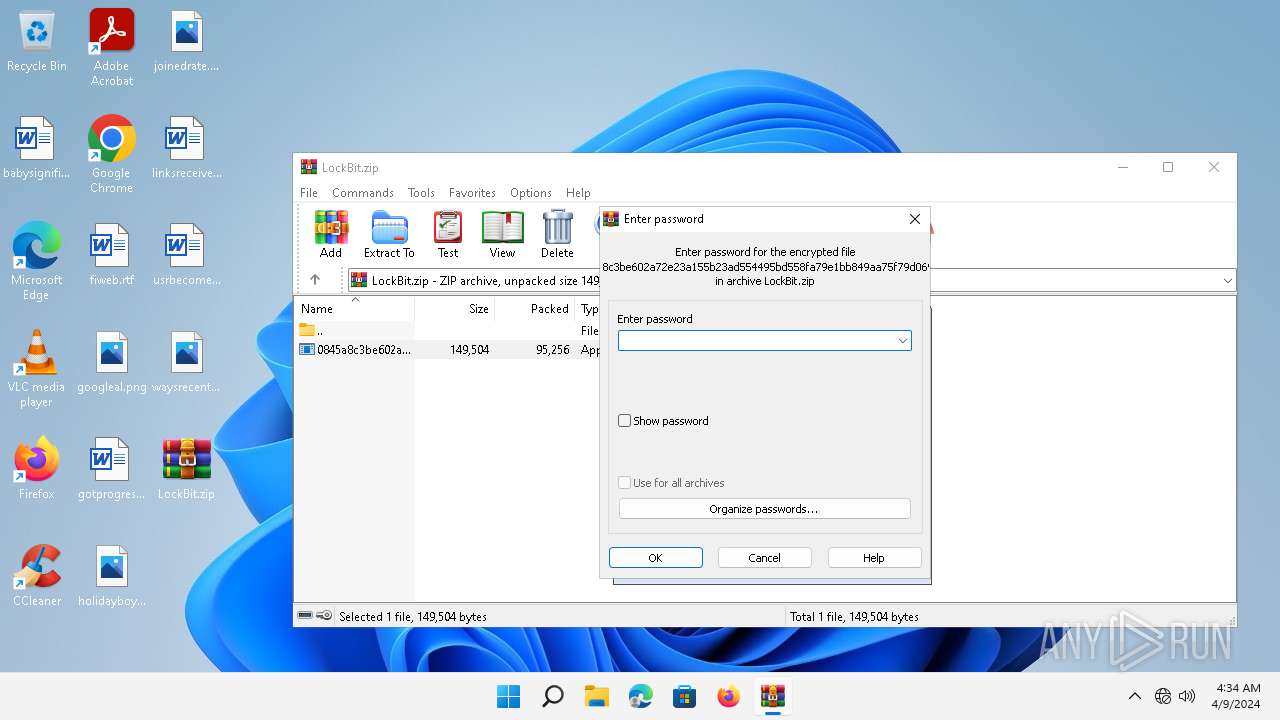
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 87739F580B661ADE6070F82DA99A8DF8 |
| SHA1: | CF824C94022C38B7905CDFCBBCA92DA61EFE4899 |
| SHA256: | F2301A1B3D390E3709AC6B19D0C00EFE2829110AD22641A00B1D94C586203F27 |
| SSDEEP: | 3072:pfY8SsjgU0E+VRzICygikLVSnAUvMohBMQ47cqiYf5wHH:5Y8NjF+/IzgikLVO1NbMHcuf5W |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5068)
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Known privilege escalation attack
- dllhost.exe (PID: 1200)
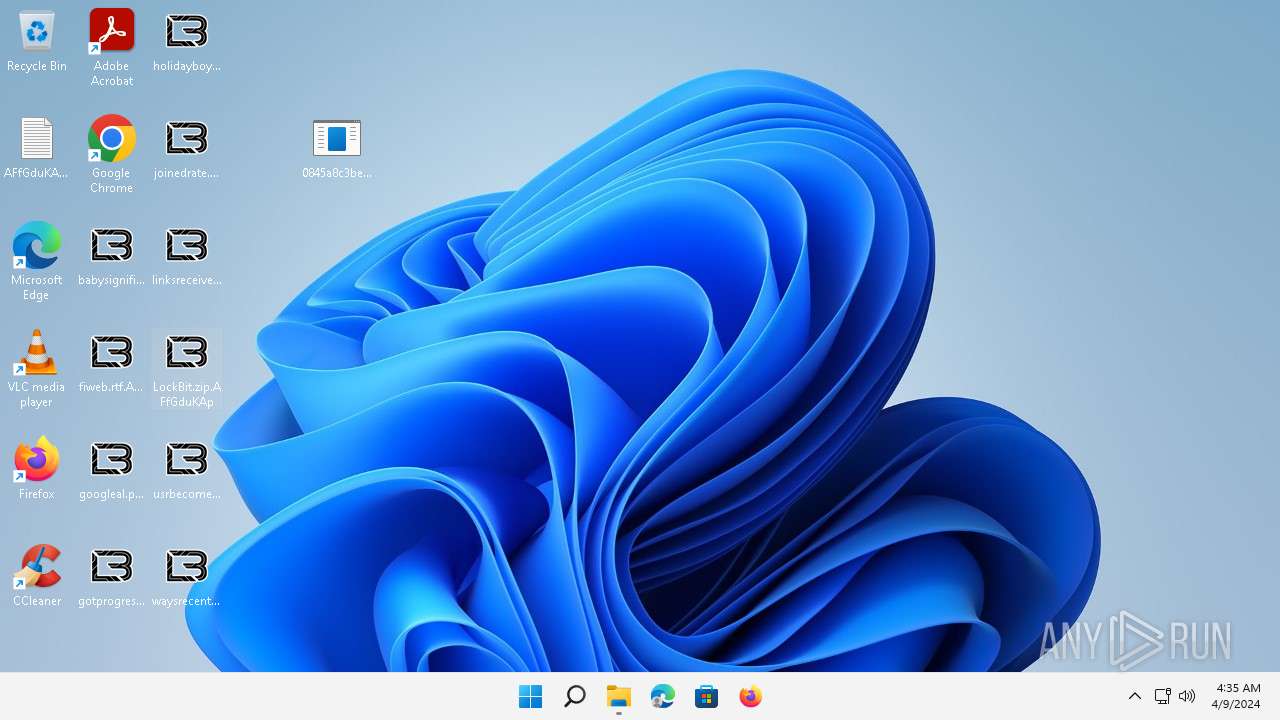
Renames files like ransomware
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
[YARA] LockBit is detected
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Steals credentials from Web Browsers
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Actions looks like stealing of personal data
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
SUSPICIOUS
Creates file in the systems drive root
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Non-standard symbols in registry
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Reads security settings of Internet Explorer
- Notepad.exe (PID: 2596)
- Notepad.exe (PID: 3976)
- A740.tmp (PID: 3504)
Reads the Internet Settings
- Notepad.exe (PID: 2596)
- A740.tmp (PID: 3504)
- Notepad.exe (PID: 3976)
Write to the desktop.ini file (may be used to cloak folders)
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
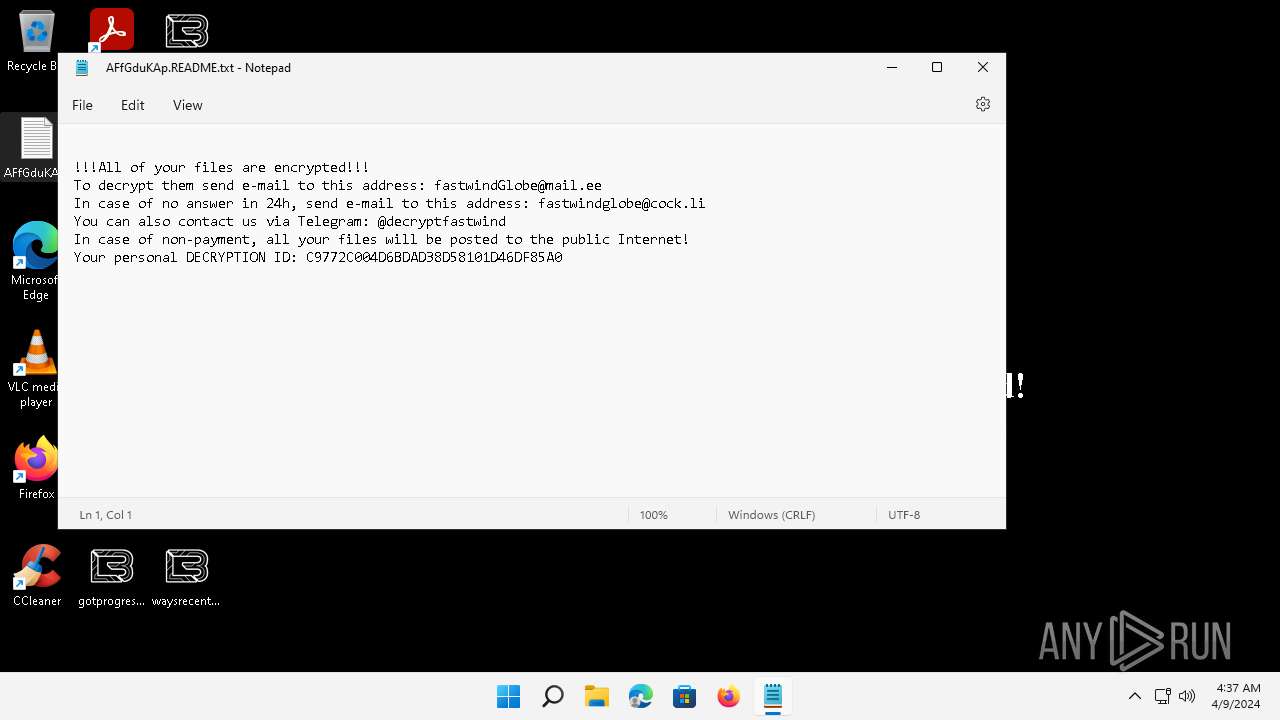
Creates files like ransomware instruction
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Executable content was dropped or overwritten
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Starts CMD.EXE for commands execution
- A740.tmp (PID: 3504)
Hides command output
- cmd.exe (PID: 3440)
Changes the desktop background image
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Starts application with an unusual extension
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Reads the date of Windows installation
- A740.tmp (PID: 3504)
INFO
Checks supported languages
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 3580)
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
- Notepad.exe (PID: 2596)
- Notepad.exe (PID: 3976)
- A740.tmp (PID: 3504)
Reads the computer name
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 3580)
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
- Notepad.exe (PID: 2596)
- A740.tmp (PID: 3504)
- Notepad.exe (PID: 3976)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 1200)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5068)
Reads the machine GUID from the registry
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 3580)
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Manual execution by a user
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 3580)
- Notepad.exe (PID: 2596)
- Notepad.exe (PID: 3976)
Dropped object may contain TOR URL's
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Creates files in the program directory
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Creates files or folders in the user directory
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Create files in a temporary directory
- 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe (PID: 6092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:04:08 13:34:56 |
| ZipCRC: | 0x9b0f71d4 |
| ZipCompressedSize: | 95256 |
| ZipUncompressedSize: | 149504 |
| ZipFileName: | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe |
Total processes
123
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | C:\Windows\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\Windows\system32\DllHost.exe" /Processid:{9F156763-7844-4DC4-B2B1-901F640F5155} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe" "C:\Users\admin\Desktop\AFfGduKAp.README.txt" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2860 | "C:\Windows\system32\DllHost.exe" /Processid:{9F156763-7844-4DC4-B2B1-901F640F5155} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | "C:\Windows\system32\DllHost.exe" /Processid:{B41DB860-64E4-11D2-9906-E49FADC173CA} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3440 | "C:\Windows\System32\cmd.exe" /C DEL /F /Q C:\PROGRA~3\A740.tmp >> NUL | C:\Windows\SysWOW64\cmd.exe | — | A740.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3504 | "C:\ProgramData\A740.tmp" | C:\ProgramData\A740.tmp | — | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3580 | "C:\Users\admin\Desktop\0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe" | C:\Users\admin\Desktop\0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3976 | "C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe" "C:\Users\admin\Desktop\AFfGduKAp.README.txt" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4236 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 868
Read events
13 478
Write events
2 365
Delete events
25
Modification events
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B050005B00125378ADA01 | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\LockBit.zip | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5068) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1D01000098000000DD0400007B020000 | |||
Executable files
27
Suspicious files
883
Text files
2 347
Unknown types
695
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5068 | WinRAR.exe | C:\USERS\ADMIN\APPDATA\ROAMING\WINRAR\VERSION.DAT | binary | |
MD5:— | SHA256:— | |||
| 5068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5068.23488\0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | executable | |
MD5:— | SHA256:— | |||
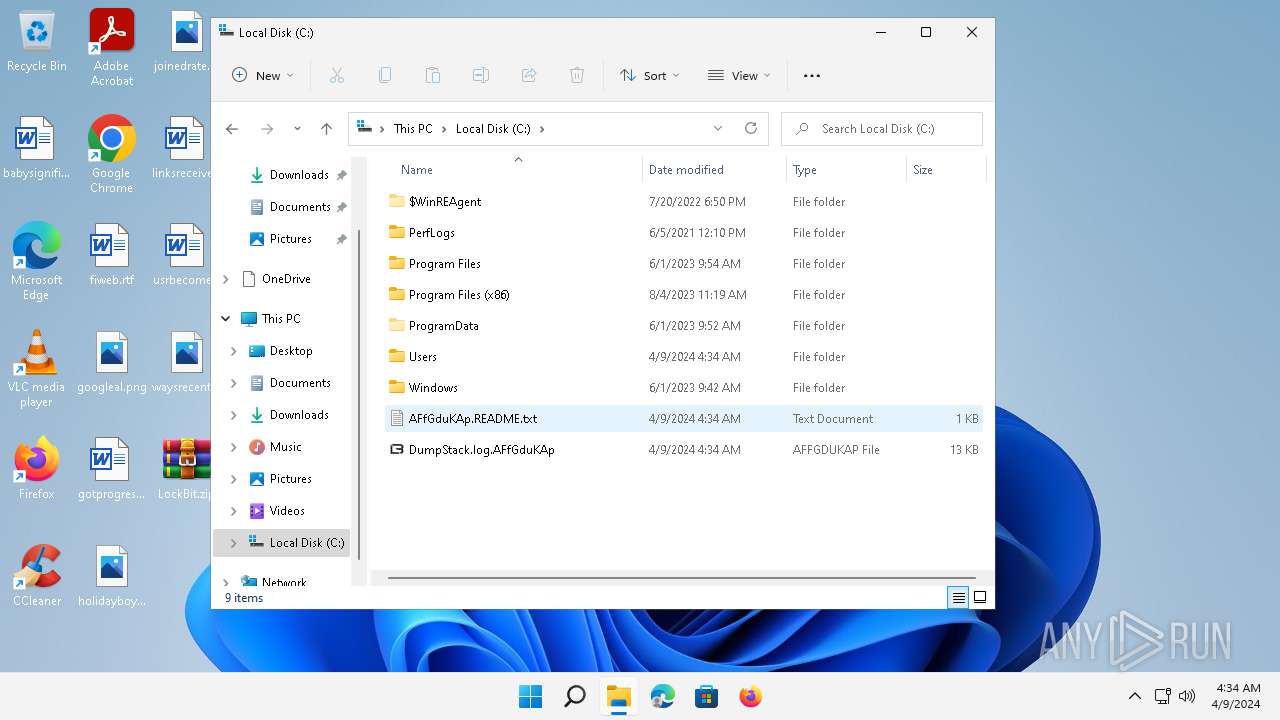
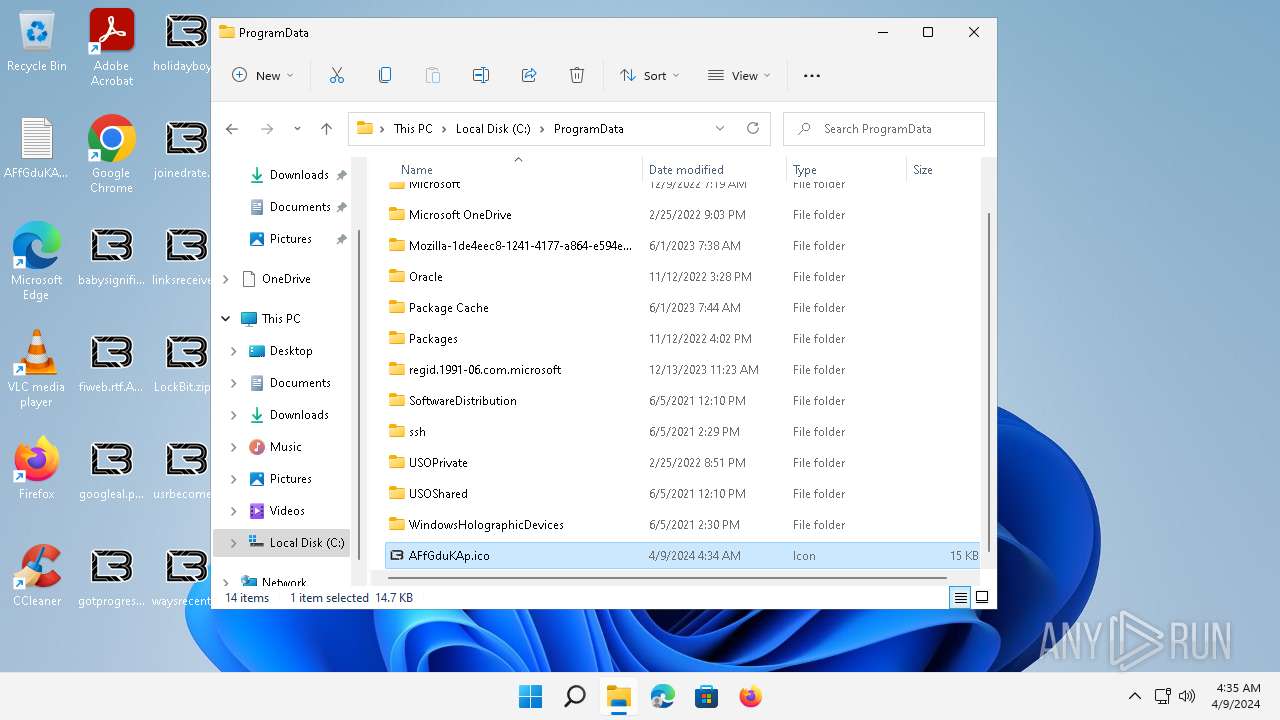
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\ProgramData\AFfGduKAp.ico | image | |
MD5:— | SHA256:— | |||
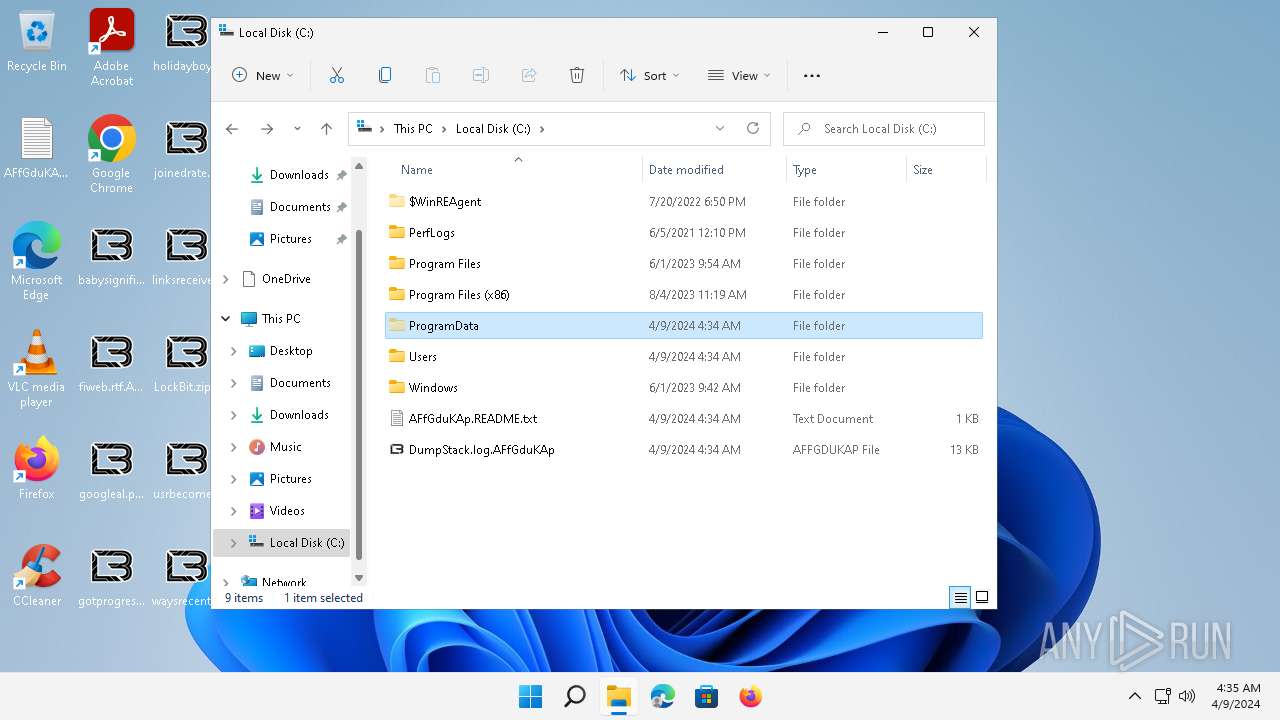
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\AFfGduKAp.README.txt | text | |
MD5:— | SHA256:— | |||
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\$Recycle.Bin\S-1-5-18\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\$Recycle.Bin\S-1-5-18\AAAAAAAAAAA | — | |
MD5:— | SHA256:— | |||
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\DumpStack.log.AFfGduKAp | binary | |
MD5:— | SHA256:— | |||
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | — | |
MD5:— | SHA256:— | |||
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\$Recycle.Bin\S-1-5-18\CCCCCCCCCCC | — | |
MD5:— | SHA256:— | |||
| 6092 | 0845a8c3be602a72e23a155b23ad554495bd558fa79e1bb849aa75f79d069194.exe | C:\Users\AFfGduKAp.README.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
26
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1412 | svchost.exe | GET | 200 | 2.16.164.42:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | unknown |
3752 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b1d3162992d7bb9c | unknown | — | — | unknown |
3752 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.251:5353 | — | — | — | unknown |
1412 | svchost.exe | 2.16.164.99:80 | — | Akamai International B.V. | NL | unknown |
5944 | svchost.exe | 2.19.244.127:443 | — | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4588 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
1412 | svchost.exe | 2.16.164.42:80 | — | Akamai International B.V. | NL | unknown |
3752 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3752 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3752 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5948 | taskhostw.exe | 20.82.217.86:443 | cs.dds.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
v20.events.data.microsoft.com |
| whitelisted |
cs.dds.microsoft.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
config.edge.skype.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1412 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |