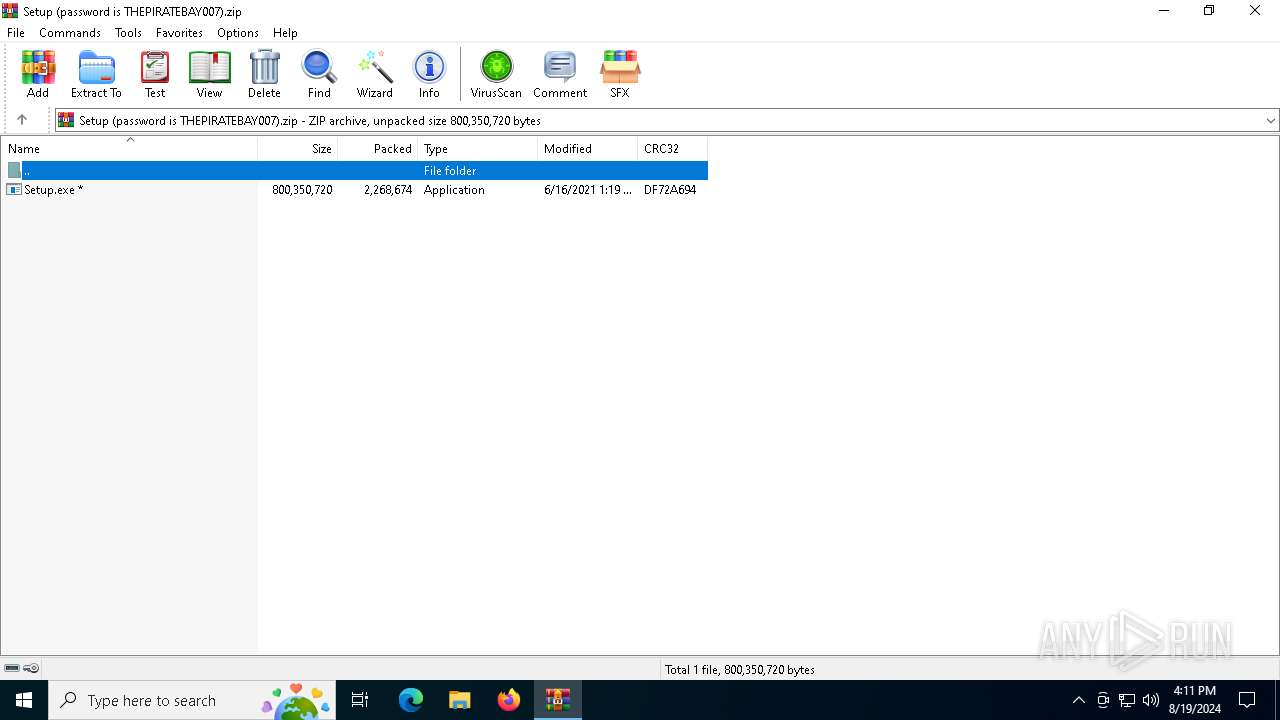
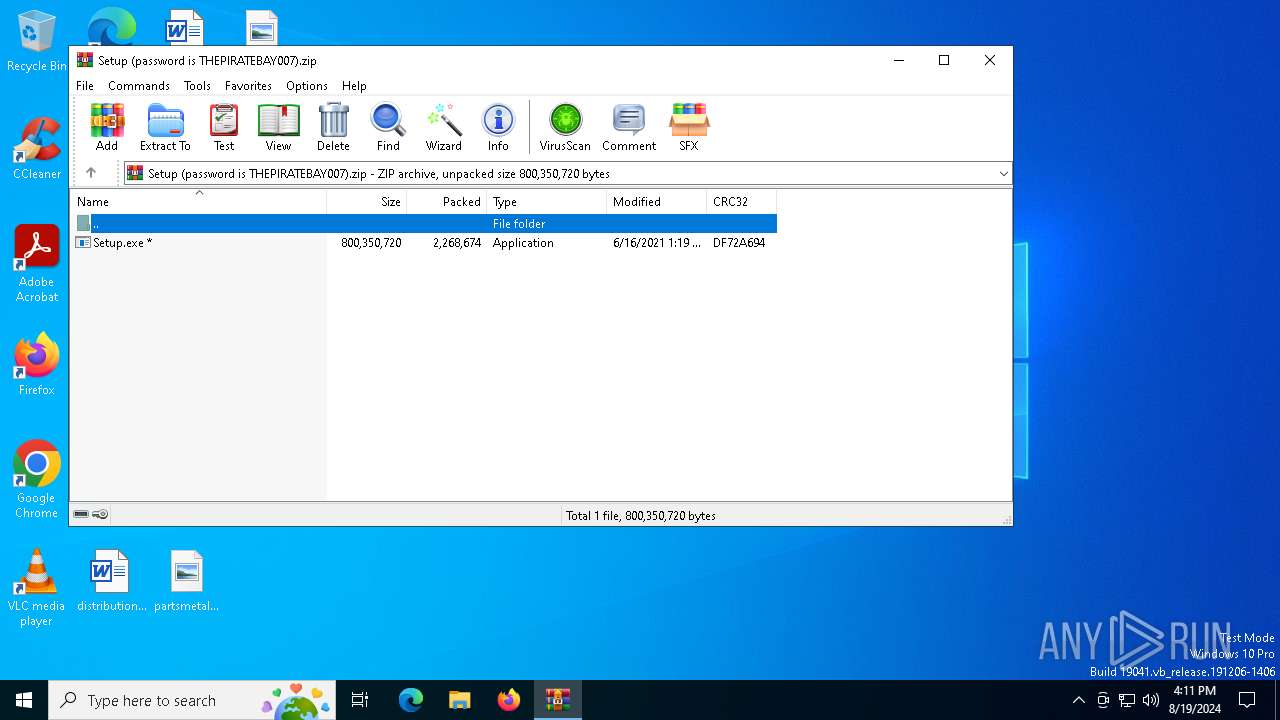
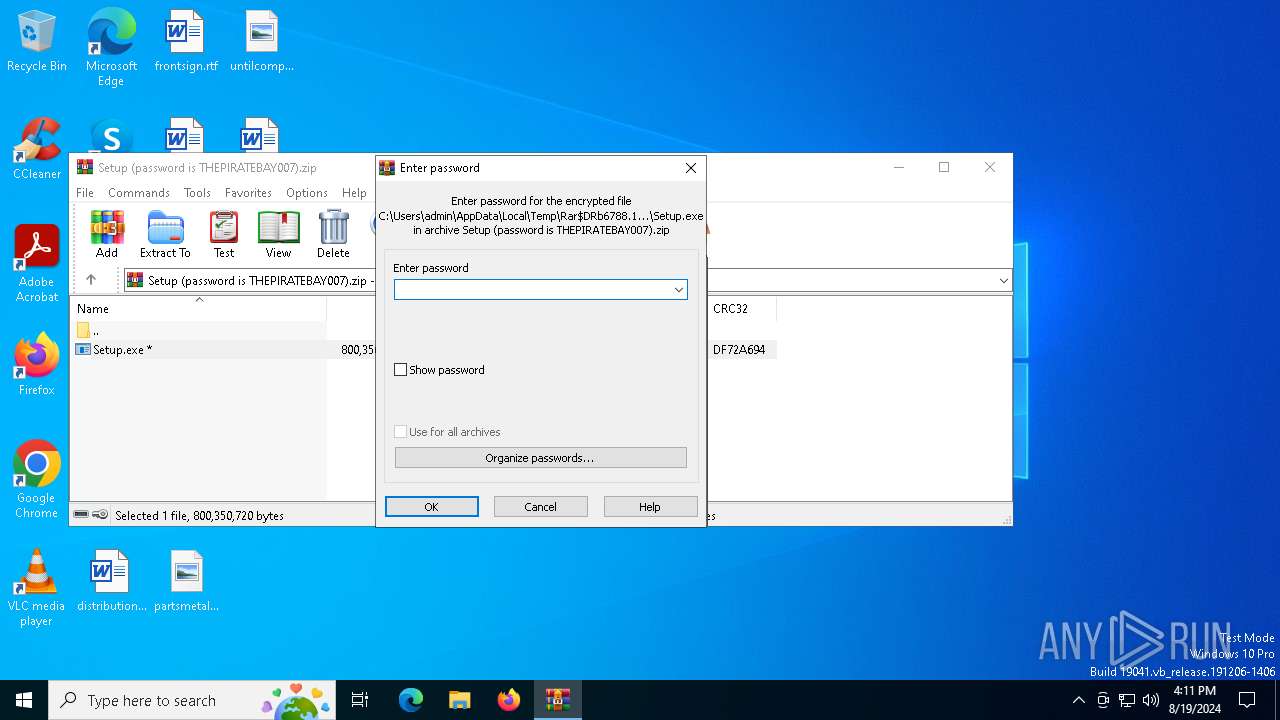
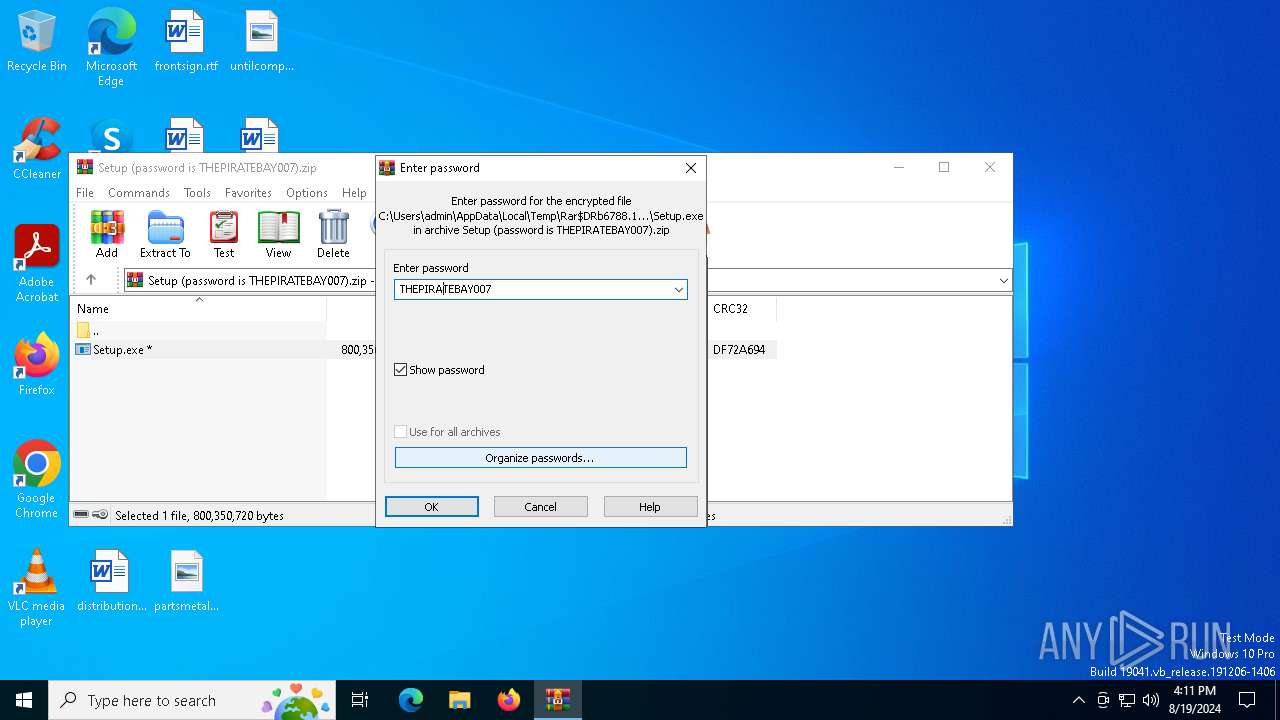
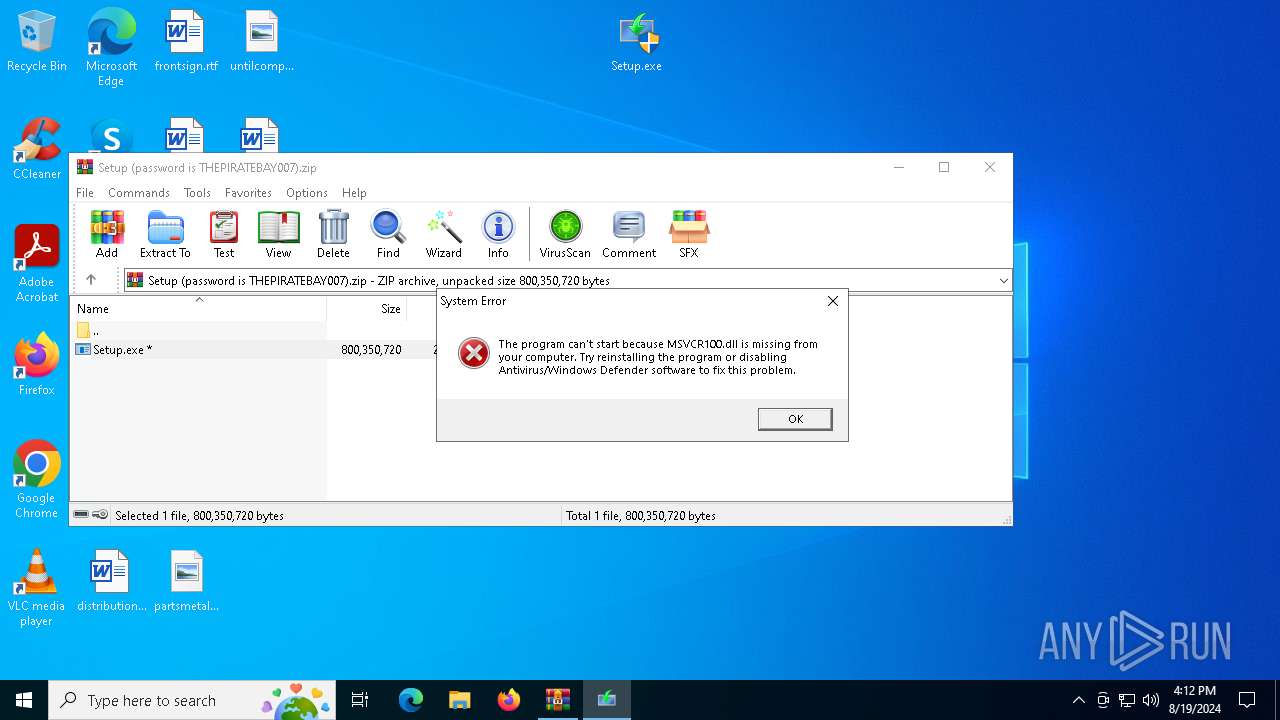
| File name: | Setup (password is THEPIRATEBAY007).zip |
| Full analysis: | https://app.any.run/tasks/71051f7a-4976-47a1-af6b-0e50536ce23e |
| Verdict: | Malicious activity |
| Analysis date: | August 19, 2024, 16:11:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 12F5F2F6C310B9A6052D4498AE5022EC |
| SHA1: | 0EE6DAAA2F312CEB7AB5E9296EE4B2E72D847BCC |
| SHA256: | F22DE84D68E75355BAEC827AF60B994090AFBBDAC4BF0ED1F487FA6E59755268 |
| SSDEEP: | 98304:FxKqGhwkRJ83S5+sKf5HDkYkOw1zvT/UoVy00dfoHHBEWbDzGtK3APy6MWn4J+Yw:9f12G |
MALICIOUS
Scans artifacts that could help determine the target
- Setup.exe (PID: 6720)
SUSPICIOUS
Creates file in the systems drive root
- Setup.exe (PID: 4248)
Reads security settings of Internet Explorer
- Setup.exe (PID: 6720)
Application launched itself
- Setup.exe (PID: 4248)
Potential Corporate Privacy Violation
- Setup.exe (PID: 6720)
Checks for external IP
- Setup.exe (PID: 6720)
INFO
Manual execution by a user
- Setup.exe (PID: 4248)
- Setup.exe (PID: 6536)
Checks supported languages
- Setup.exe (PID: 4248)
- Setup.exe (PID: 6720)
Creates files in the program directory
- Setup.exe (PID: 6720)
Creates files or folders in the user directory
- Setup.exe (PID: 6720)
Checks proxy server information
- Setup.exe (PID: 6720)
Reads the computer name
- Setup.exe (PID: 6720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:06:16 04:19:28 |
| ZipCRC: | 0xdf72a694 |
| ZipCompressedSize: | 2268674 |
| ZipUncompressedSize: | 800350720 |
| ZipFileName: | Setup.exe |
Total processes
134
Monitored processes
4
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4248 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: NVIDIA Corporation Integrity Level: HIGH Description: NVIDIA Package Launcher Exit code: 0 Version: 1.0.11 Modules
| |||||||||||||||
| 6536 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: NVIDIA Corporation Integrity Level: MEDIUM Description: NVIDIA Package Launcher Exit code: 3221226540 Version: 1.0.11 Modules
| |||||||||||||||
| 6720 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | Setup.exe | ||||||||||||
User: admin Company: NVIDIA Corporation Integrity Level: HIGH Description: NVIDIA Package Launcher Version: 1.0.11 Modules
| |||||||||||||||
| 6788 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Setup (password is THEPIRATEBAY007).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 746
Read events
5 726
Write events
20
Delete events
0
Modification events
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Setup (password is THEPIRATEBAY007).zip | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6788) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (6720) Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6788.19436\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 6720 | Setup.exe | C:\ProgramData\krosqm.txt | text | |
MD5:10C0D2B178F9DCE7033AB04E783317BD | SHA256:F26D3FF392906DC8A5B63B6AADEA43325FCDF9EE93454E6090601C060EEEA9C0 | |||
| 6720 | Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\KLMAL93U.txt | text | |
MD5:10C0D2B178F9DCE7033AB04E783317BD | SHA256:F26D3FF392906DC8A5B63B6AADEA43325FCDF9EE93454E6090601C060EEEA9C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
34
DNS requests
13
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7164 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2796 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4820 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6720 | Setup.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/?format=xml | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5880 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1020 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2796 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2796 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7164 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6720 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup (ipify .org) |
6720 | Setup.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |