| File name: | Java Update.exe |
| Full analysis: | https://app.any.run/tasks/b42429ca-9387-4699-a9af-9cc09febc6ed |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 17:42:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9B7B0D390D90D53FE2534C652132742D |
| SHA1: | 99F7A8E7809A4DF46FC53138A0BCF33F21AB85CB |
| SHA256: | F1EC83C56AD5FF95B84588B2185C8097237B0E5D0074D8BEE020D28416C0FDA5 |
| SSDEEP: | 196608:ETYWRRrJhwPmtZuVbFQYbqexE8D7Zm3iQwzlq5DXVSEuMq1BUM7:1WblmKYvQEqgE8D7MQzC9uZjU |
MALICIOUS
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 2476)
- CCleaner.exe (PID: 1008)
Drops executable file immediately after starts
- CCleaner.exe (PID: 1008)
Loads dropped or rewritten executable
- CCleaner.exe (PID: 1008)
Changes settings of System certificates
- CCleaner.exe (PID: 1008)
SUSPICIOUS
Checks supported languages
- Java Update.exe (PID: 1432)
- CCleaner.exe (PID: 2476)
- CCleaner.exe (PID: 1008)
Reads Environment values
- CCleaner.exe (PID: 2476)
- CCleaner.exe (PID: 1008)
Drops a file with a compile date too recent
- CCleaner.exe (PID: 1008)
Creates files in the program directory
- CCleaner.exe (PID: 1008)
Reads internet explorer settings
- CCleaner.exe (PID: 1008)
Reads the computer name
- CCleaner.exe (PID: 2476)
- CCleaner.exe (PID: 1008)
Executed via Task Scheduler
- CCleaner.exe (PID: 1008)
Reads the date of Windows installation
- CCleaner.exe (PID: 1008)
Executable content was dropped or overwritten
- CCleaner.exe (PID: 1008)
Reads CPU info
- CCleaner.exe (PID: 1008)
Creates files in the user directory
- CCleaner.exe (PID: 1008)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 1008)
Adds / modifies Windows certificates
- CCleaner.exe (PID: 1008)
Searches for installed software
- CCleaner.exe (PID: 1008)
INFO
Manual execution by user
- CCleaner.exe (PID: 2476)
Reads the hosts file
- CCleaner.exe (PID: 1008)
Reads settings of System Certificates
- CCleaner.exe (PID: 1008)
Checks Windows Trust Settings
- CCleaner.exe (PID: 1008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x185f66f |
| UninitializedDataSize: | - |
| InitializedDataSize: | 265728 |
| CodeSize: | 104448 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| TimeStamp: | 2022:05:20 18:58:20+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-May-2022 16:58:20 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 20-May-2022 16:58:20 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000196D8 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.rdata | 0x0001B000 | 0x00006DF2 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.data | 0x00022000 | 0x000030C0 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.vmp0 | 0x008E2000 | 0x00004D9B | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.vmp1 | 0x00AD7000 | 0x002CB43D | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.vlizer | 0x008E7000 | 0x001F0000 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.vmp2 | 0x00DA3000 | 0x00ADAB60 | 0x00ADAC00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.98832 |
.rsrc | 0x0187E000 | 0x00004D9B | 0x00004E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.49018 |
Imports
KERNEL32.dll |
OLEAUT32.dll |
USER32.dll |
WTSAPI32.dll |
mscoree.dll |
ole32.dll |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
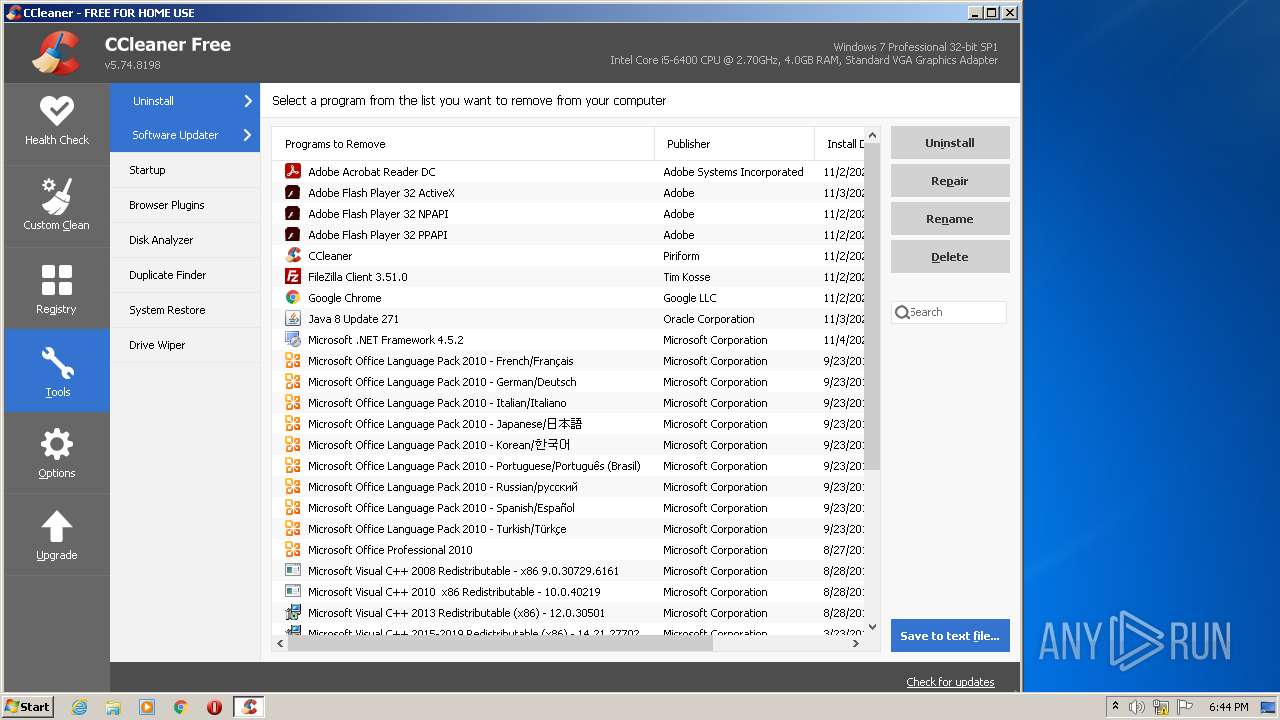
| 1008 | "C:\Program Files\CCleaner\CCleaner.exe" /TOOLS /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5.74.0.8198 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\AppData\Local\Temp\Java Update.exe" | C:\Users\admin\AppData\Local\Temp\Java Update.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3735929054 Modules
| |||||||||||||||
| 2476 | "C:\Program Files\CCleaner\CCleaner.exe" /TOOLS | C:\Program Files\CCleaner\CCleaner.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 5.74.0.8198 Modules
| |||||||||||||||
Total events
16 926
Read events
16 751
Write events
145
Delete events
30
Modification events
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 0 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | FTU |
Value: 02/11/2020|7|1 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1008) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
2
Suspicious files
10
Text files
6
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1008 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0E2R7T90DV36ZDMBV4C9.temp | binary | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\07VZIZXL.txt | text | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ed7a5cc3cca8d52a.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\HAYC0TBK.txt | ini | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\RLHC6L03.txt | text | |
MD5:— | SHA256:— | |||
| 1008 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\YVKJHZ0P.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
19
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1008 | CCleaner.exe | GET | 301 | 104.90.109.251:80 | http://www.ccleaner.com/auto?a=0&p=cc&v=5.74.8198&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-HZ8S&o=6.1W3&au=0&mx=97B7721C4994E2556FF6A439510F665DB0F235F172388ACE2A5D97D6A351F7CD&gd=19ce970b-f6c0-4a09-bae4-274b971730e0 | NL | — | — | whitelisted |
1008 | CCleaner.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
1008 | CCleaner.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDwQ9JNOs3IcArkp%2FBu7NbU | US | der | 472 b | whitelisted |
1008 | CCleaner.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
1008 | CCleaner.exe | GET | 200 | 92.123.194.99:80 | http://ncc.avast.com/ncc.txt | unknown | text | 26 b | whitelisted |
1008 | CCleaner.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
1008 | CCleaner.exe | GET | 200 | 8.248.117.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1f9c1682afaea59a | US | compressed | 4.70 Kb | whitelisted |
1008 | CCleaner.exe | GET | 200 | 8.248.117.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4ad50247a6c2d6b5 | US | compressed | 4.70 Kb | whitelisted |
1008 | CCleaner.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
1008 | CCleaner.exe | GET | 200 | 8.248.117.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e8b152a9340abcc5 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1008 | CCleaner.exe | 92.123.194.99:80 | ncc.avast.com | Akamai International B.V. | — | suspicious |
1008 | CCleaner.exe | 104.90.109.251:443 | www.ccleaner.com | Akamai Technologies, Inc. | NL | suspicious |
1008 | CCleaner.exe | 5.62.40.204:443 | analytics.ff.avast.com | AVAST Software s.r.o. | DE | malicious |
1008 | CCleaner.exe | 104.90.109.251:80 | www.ccleaner.com | Akamai Technologies, Inc. | NL | suspicious |
1008 | CCleaner.exe | 5.62.45.51:443 | ipm-provider.ff.avast.com | AVAST Software s.r.o. | US | unknown |
1008 | CCleaner.exe | 104.90.110.183:443 | license.piriform.com | Akamai Technologies, Inc. | NL | suspicious |
1008 | CCleaner.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1008 | CCleaner.exe | 104.90.181.175:443 | ipmcdn.avast.com | Akamai Technologies, Inc. | NL | suspicious |
1008 | CCleaner.exe | 142.250.181.232:443 | ssl.google-analytics.com | Google Inc. | US | suspicious |
1008 | CCleaner.exe | 142.250.185.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
license.piriform.com |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |
ipmcdn.avast.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1008 | CCleaner.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
Process | Message |
|---|---|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |