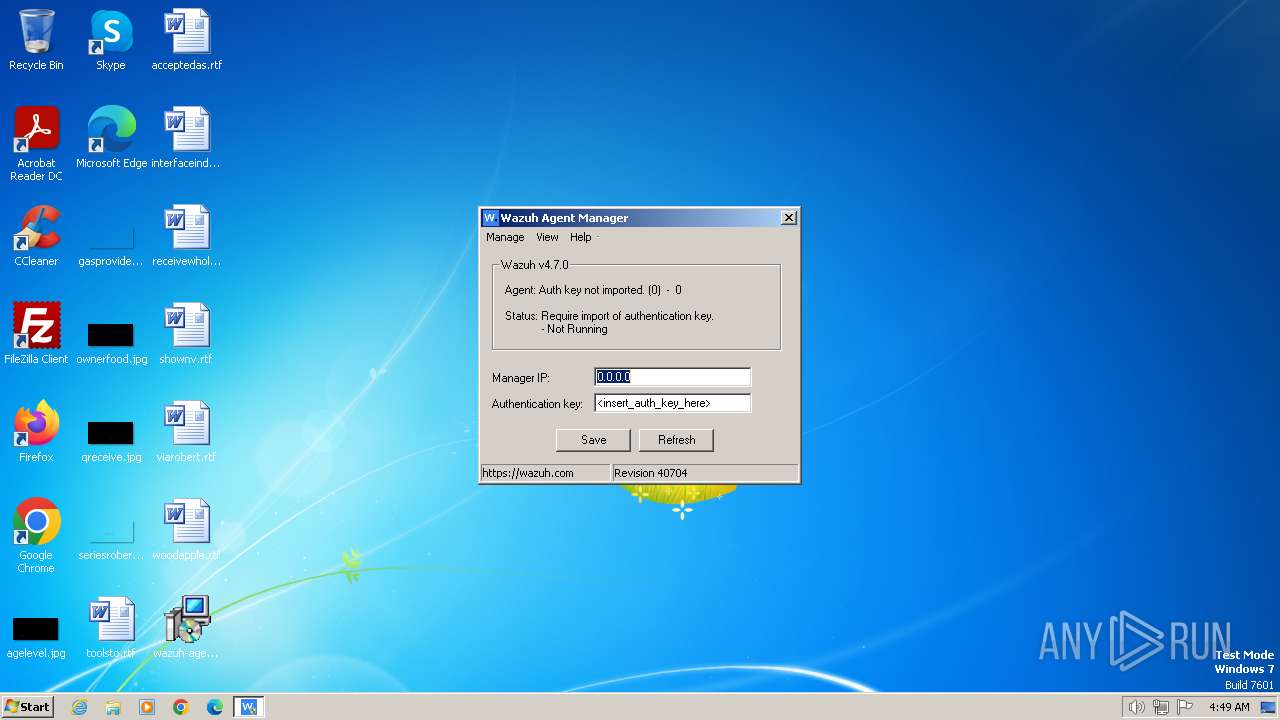
| File name: | wazuh-agent-4.7.0-1.msi |
| Full analysis: | https://app.any.run/tasks/7e72bbcb-05bd-4db0-a87b-1a1ad5afe02d |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2023, 04:48:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Wazuh helps you to gain security visibility into your infrastructure by monitoring hosts at an operating system and application level. It provides the following capabilities: log analysis, file integrity monitoring, intrusions detection and policy and compliance monitoring, Author: Wazuh, Inc., Keywords: Installer, Comments: wazuh-agent, Template: Intel;1033, Revision Number: {9C572392-011B-486A-9B3B-03EB76B02DCF}, Create Time/Date: Thu Nov 23 16:07:32 2023, Last Saved Time/Date: Thu Nov 23 16:07:32 2023, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | FD3DE1502C7D3D3AF83C576A4F2B4741 |
| SHA1: | 3B9FADC6A07E6D68D172AFEABB5768CA7FC639CB |
| SHA256: | F1E81D5E8C29176F72F4640804F60F926C7825138DA923C151EB65428184059C |
| SSDEEP: | 98304:pEZvya7eJ8unVFIDngaHQuBHVogWiH0lw3xeNs6ro7f3p3aFlhtrQSHeouwxxQF9:pGALesUF1nFffN |
MALICIOUS
Accesses system services(Win32_Service) via WMI (SCRIPT)
- msiexec.exe (PID: 1892)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1056)
Gets username (SCRIPT)
- msiexec.exe (PID: 2428)
Opens a text file (SCRIPT)
- msiexec.exe (PID: 2428)
Accesses environment variables (SCRIPT)
- msiexec.exe (PID: 2428)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 1392)
Checks Windows Trust Settings
- msiexec.exe (PID: 1056)
- win32ui.exe (PID: 3076)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- msiexec.exe (PID: 1892)
- msiexec.exe (PID: 2428)
Executes WMI query (SCRIPT)
- msiexec.exe (PID: 1892)
- msiexec.exe (PID: 2428)
The process creates files with name similar to system file names
- msiexec.exe (PID: 1056)
Writes binary data to a Stream object (SCRIPT)
- msiexec.exe (PID: 2428)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 2428)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 2428)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 2428)
Reads data from a binary Stream object (SCRIPT)
- msiexec.exe (PID: 2428)
Checks whether a specific file exists (SCRIPT)
- msiexec.exe (PID: 2428)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- msiexec.exe (PID: 2428)
Uses ICACLS.EXE to modify access control lists
- msiexec.exe (PID: 2428)
Accesses computer name via WMI (SCRIPT)
- msiexec.exe (PID: 2428)
Accesses current user name via WMI (SCRIPT)
- msiexec.exe (PID: 2428)
Reads the Internet Settings
- msiexec.exe (PID: 2524)
Reads settings of System Certificates
- win32ui.exe (PID: 3076)
Reads security settings of Internet Explorer
- win32ui.exe (PID: 3076)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 128)
Checks supported languages
- msiexec.exe (PID: 1056)
- msiexec.exe (PID: 1892)
- msiexec.exe (PID: 2428)
- msiexec.exe (PID: 2524)
- win32ui.exe (PID: 3076)
Reads the computer name
- msiexec.exe (PID: 1056)
- msiexec.exe (PID: 1892)
- msiexec.exe (PID: 2428)
- win32ui.exe (PID: 3076)
- msiexec.exe (PID: 2524)
Create files in a temporary directory
- msiexec.exe (PID: 128)
- msiexec.exe (PID: 1056)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1056)
- msiexec.exe (PID: 1892)
- msiexec.exe (PID: 2428)
- win32ui.exe (PID: 3076)
- msiexec.exe (PID: 2524)
Application launched itself
- msiexec.exe (PID: 1056)
Reads Environment values
- msiexec.exe (PID: 1892)
- msiexec.exe (PID: 2428)
Drops the executable file immediately after the start
- msiexec.exe (PID: 128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Wazuh helps you to gain security visibility into your infrastructure by monitoring hosts at an operating system and application level. It provides the following capabilities: log analysis, file integrity monitoring, intrusions detection and policy and compliance monitoring |
| Author: | Wazuh, Inc. |
| Keywords: | Installer |
| Comments: | wazuh-agent |
| Template: | Intel;1033 |
| RevisionNumber: | {9C572392-011B-486A-9B3B-03EB76B02DCF} |
| CreateDate: | 2023:11:23 16:07:32 |
| ModifyDate: | 2023:11:23 16:07:32 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
57
Monitored processes
13
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\wazuh-agent-4.7.0-1.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | "C:\Windows\System32\taskkill.exe" /f /im win32ui.exe | C:\Windows\System32\taskkill.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1056 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1392 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | "C:\Windows\System32\icacls.exe" "C:\Program Files\ossec-agent" /remove *S-1-5-32-545 /q | C:\Windows\System32\icacls.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | C:\Windows\system32\MsiExec.exe -Embedding D08543C2F5A85E27F3C0B7FCE9CFC0D7 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Windows\System32\icacls.exe" "C:\Program Files\ossec-agent" /inheritancelevel:d /q | C:\Windows\System32\icacls.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2428 | C:\Windows\system32\MsiExec.exe -Embedding 81426E27A4A57456362976035352A151 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | C:\Windows\system32\MsiExec.exe -Embedding A00F8C33817156E19D48B22434AF2AFC C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | "C:\Program Files\ossec-agent\win32ui.exe" | C:\Program Files\ossec-agent\win32ui.exe | — | msiexec.exe | |||||||||||
User: admin Company: Wazuh Inc. Integrity Level: MEDIUM Description: Wazuh Agent Exit code: 3221226540 Version: v4.7.0 Modules
| |||||||||||||||
Total events
14 285
Read events
14 209
Write events
70
Delete events
6
Modification events
| (PID) Process: | (128) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 73 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008543C5D72FB0D90164030000840D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 4000000000000000475C02D92FB0D90164030000840D0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 4000000000000000E57701DA2FB0D90164030000840D0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 4000000000000000E57701DA2FB0D90164030000840D0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
23
Suspicious files
14
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1056 | msiexec.exe | C:\Windows\Installer\e6c42.msi | — | |
MD5:— | SHA256:— | |||
| 1056 | msiexec.exe | C:\Program Files\ossec-agent\active-response\active-responses.log | — | |
MD5:— | SHA256:— | |||
| 1056 | msiexec.exe | C:\Windows\Installer\MSI78D5.tmp | binary | |
MD5:F6E85ADD6889005CE427515164EDE905 | SHA256:A507EFA980B6062497250F238EFD4DCCE733792EEAE4DC435B656500635A708A | |||
| 1056 | msiexec.exe | C:\Windows\Installer\MSI7964.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 1056 | msiexec.exe | C:\Windows\Installer\MSI7A20.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 1056 | msiexec.exe | C:\Windows\Installer\MSI7934.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 1056 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{a47d6fac-7d10-4f1c-867d-af200461f5ba}_OnDiskSnapshotProp | binary | |
MD5:1B4C528812752C71B990B5EAD38DF597 | SHA256:76D5462DA97BF62097F21CFB0E8ABB73854DBA2E1DCD906B659D7C724E5BBA1B | |||
| 1056 | msiexec.exe | C:\Windows\Installer\e6c43.ipi | binary | |
MD5:F27C688B988887EA78CCA1DBDD6C372A | SHA256:C0E5671ACECFE3CAF79EC49527033A9FF1BE0EC33AF784AB32026AA387D2CE44 | |||
| 1056 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFE74668C5E94B53FD.TMP | binary | |
MD5:0700536749E6501897F205A7525DB91C | SHA256:2889B8B16E1D1D8A5B926A770232678A18FC2841159B5BFBE082500F0EFF4369 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |