| download: | 1531865034 |
| Full analysis: | https://app.any.run/tasks/b19f2bf3-d4df-4390-a523-cf9040bbf3c9 |
| Verdict: | No threats detected |
| Analysis date: | July 17, 2018, 22:05:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | CAB01BDE8D4F37A19724BB2964475FF9 |
| SHA1: | C066575A8D891AC3D8EDA3C240A77F784F79797D |
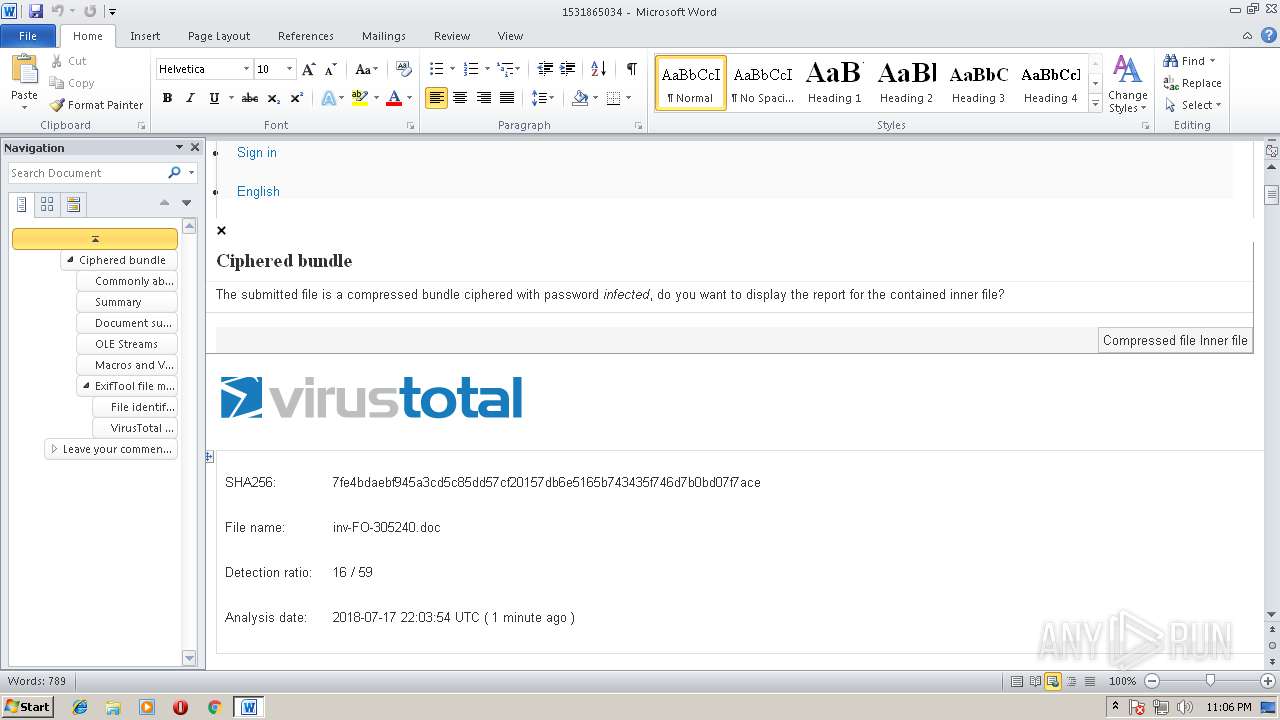
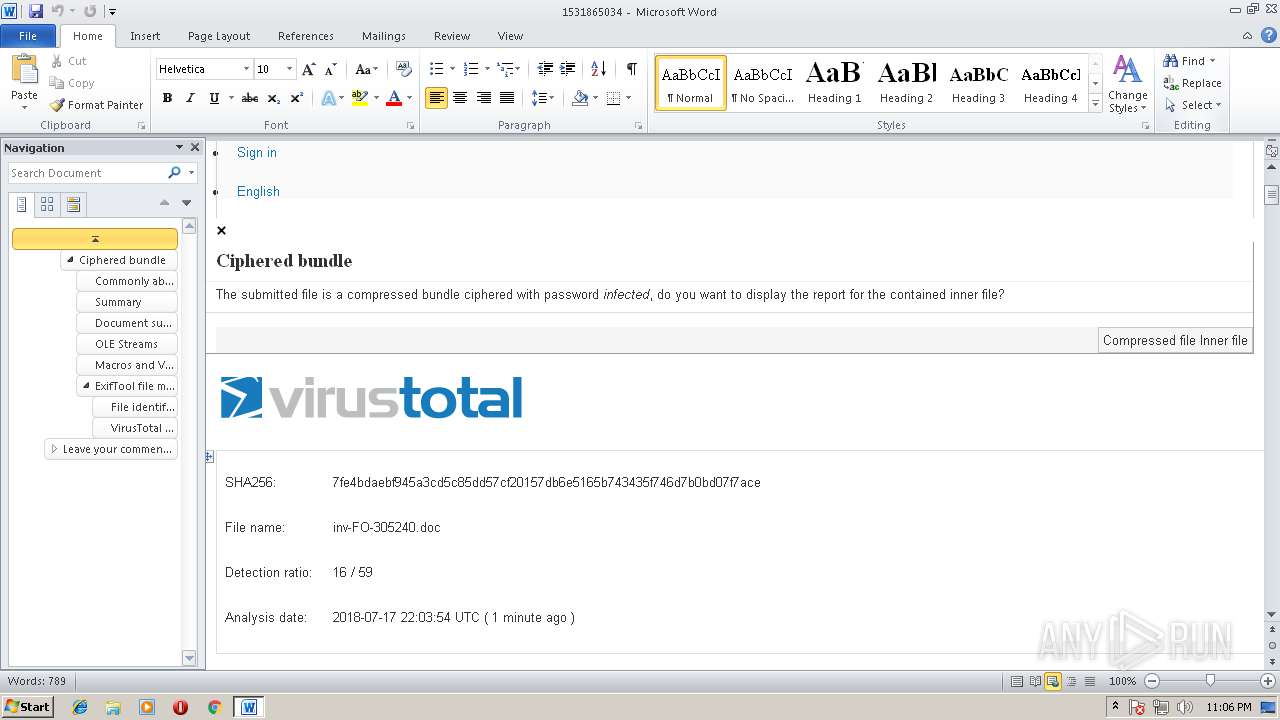
| SHA256: | F1E3C4F6E44EBB9611F0F1523A4B46EAD52241DD778483277D0091810826D4E0 |
| SSDEEP: | 768:HlSYe7gBYo8o7DOvO9s0wZLewmty6MuWlMbi3nu:HlFe7gBYoTOvOFwZLewmOu4M4nu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Microsoft Office Application
- rundll32.exe (PID: 2200)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3856)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| Title: | Antivirus scan for 7fe4bdaebf945a3cd5c85dd57cf20157db6e5165b743435f746d7b0bd07f7ace at 2018-07-17 22:03:54 UTC - VirusTotal |
|---|---|
| ContentType: | text/html; charset=utf-8 |
| Pragma: | no-store |
| Expires: | -1 |
| Keywords: | virustotal, antivirus, infected, free, scan, online, malware, malicious, scanner |
| googleSiteVerification: | Id8gKYyQBVmhsuWOE1SDkhDhAU5QW9pREnc-RO9lPLQ |
| Description: | VirusTotal's antivirus scan report for the file with MD5 805e39bfbc0cb2d008d9adcc68d48132 at 2018-07-17 22:03:54 UTC. 16 out of 59 antivirus detected the file as malicious. Some of the detections were: VB.EmoDldr.5.Gen, W97M/Downloader.cqw, type-unsupported, Trojan ( 00536d111 ), Trojan ( 00536d111 ), type-unsupported, Trojan.Ole2.Vbs-heuristic.druvzi, Heur.Macro.Generic.Gen.f, type-unsupported, HEUR_VBA.O.ELBP, BehavesLike.Downloader.dg, type-unsupported, Troj/DocDl-OWH, type-unsupported, VBA/Agent.JLD!tr.dldr, type-unsupported, VB.EmoDldr.5.Gen, TrojanDownloader:O97M/Dornoe.B!ams, Suspicious/W97M.Obfus.Gen, malware (ai score=85), type-unsupported, Probably W97Obfuscated, type-unsupported, type-unsupported, type-unsupported, virus.office.qexvmc.1100 |
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2200 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\1531865034 | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3856 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\1531865034" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 344
Read events
1 911
Write events
427
Delete events
6
Modification events
| (PID) Process: | (2200) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2200) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2200) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\53\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 8:& |
Value: 383A2600100F0000010000000000000000000000 | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1290862610 | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1290862667 | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1290862668 | |||
| (PID) Process: | (3856) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Shared Tools\Outlook\Journaling\Microsoft Word |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
0
Suspicious files
24
Text files
5
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4A18.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{4E7480BC-F086-4150-BE98-7CA55DB14826} | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{4D5B5F49-F8E7-4694-92A6-3ED61223908B} | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso513E.tmp | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1F931F8C.wmf | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EA1A9733.wmf | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3F92FF98.wmf | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C2258AB9.wmf | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5D3EC166.wmf | — | |
MD5:— | SHA256:— | |||
| 3856 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A034762F.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3856 | WINWORD.EXE | 172.217.168.20:443 | virustotalcloud.appspot.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
virustotalcloud.appspot.com |
| whitelisted |