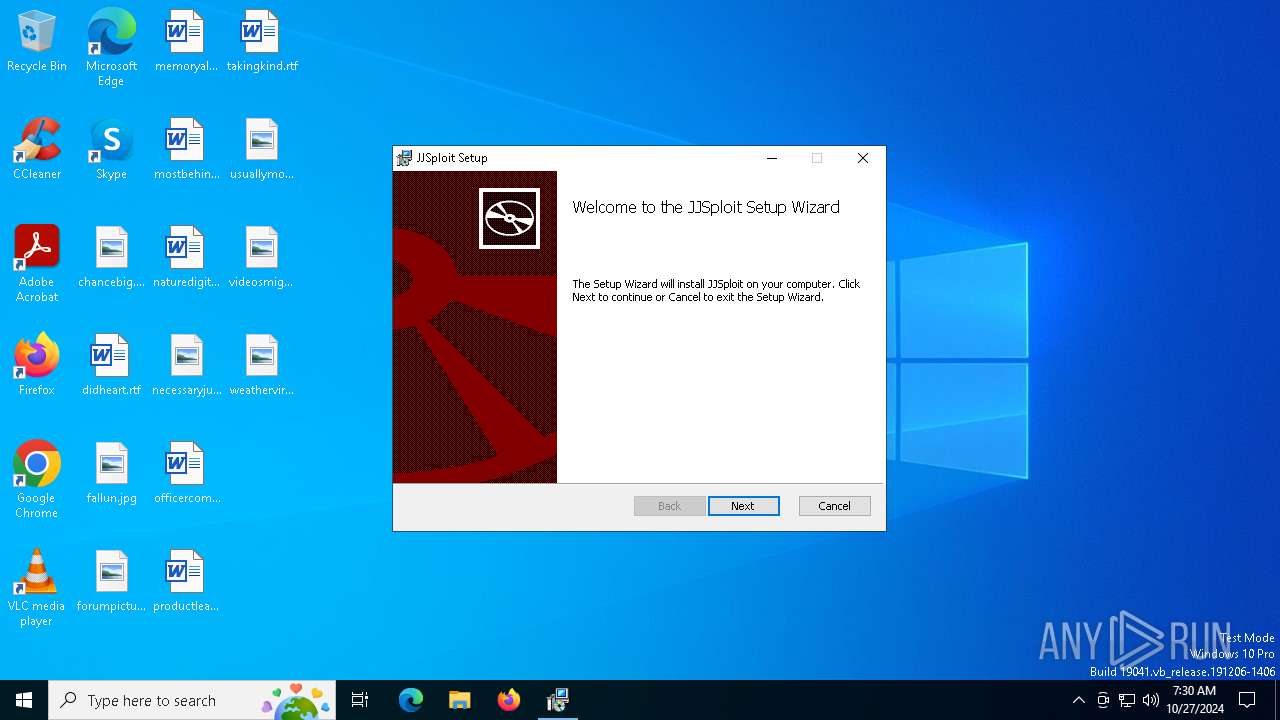
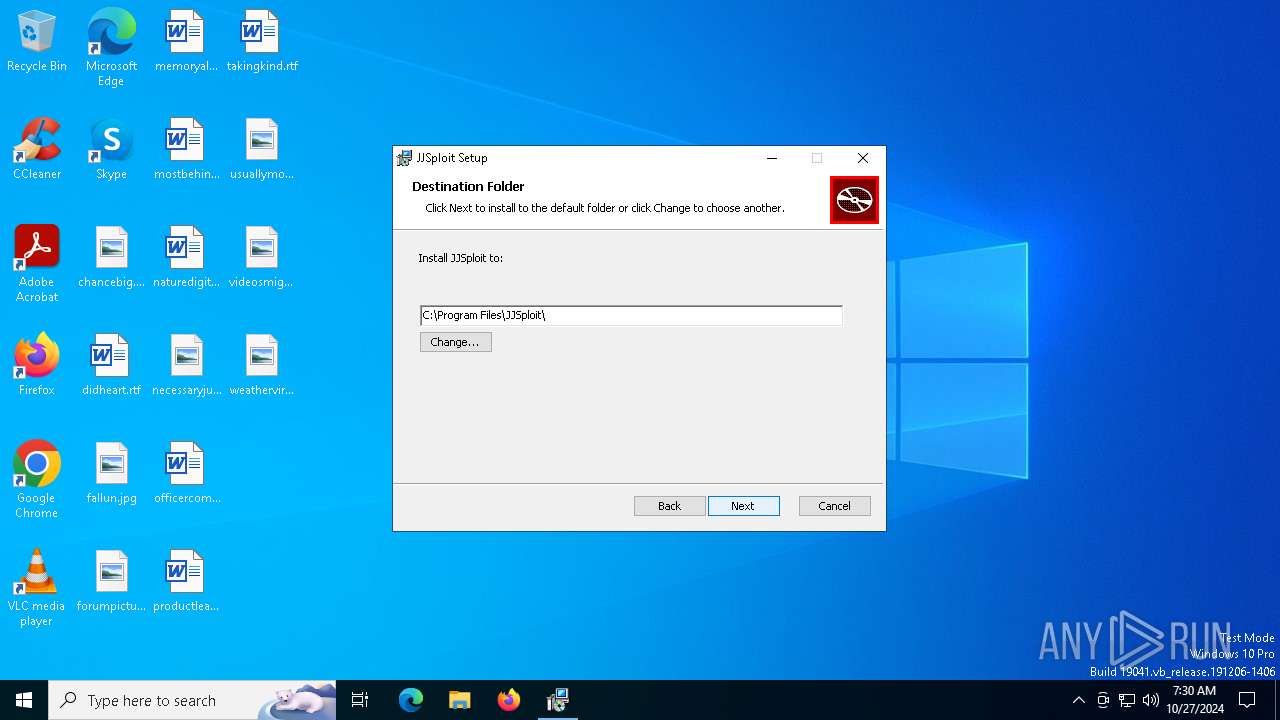
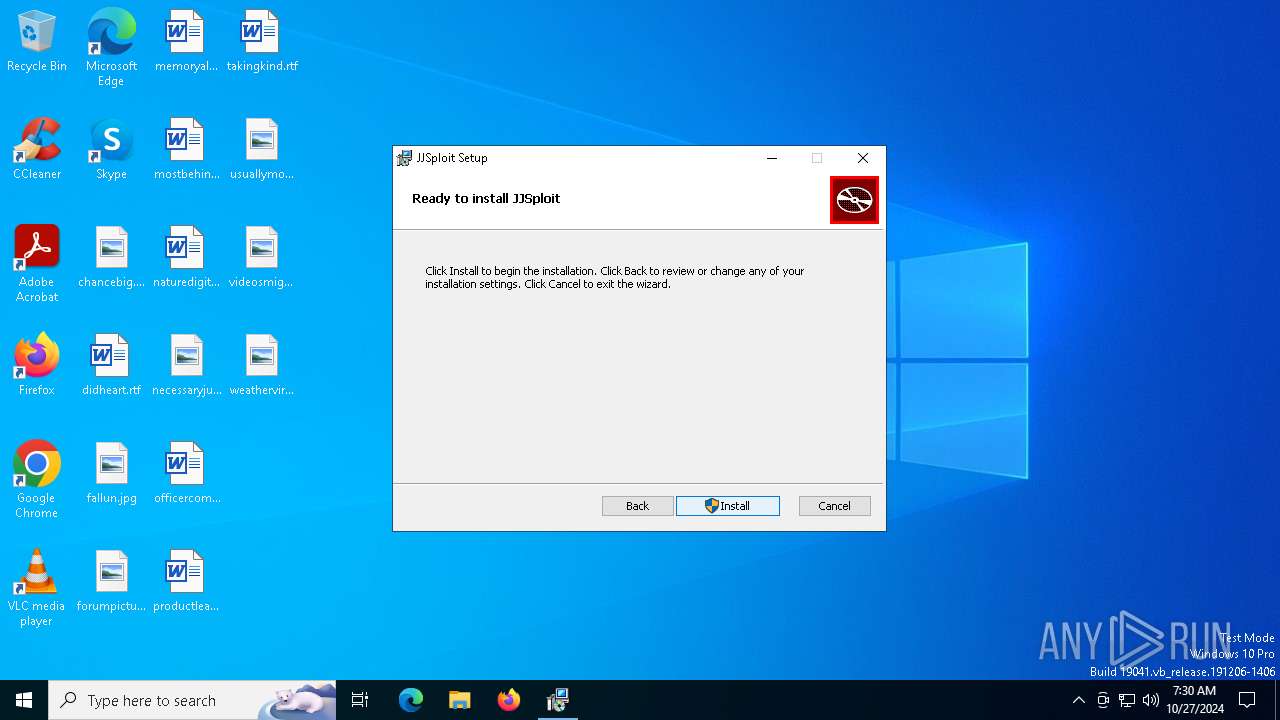
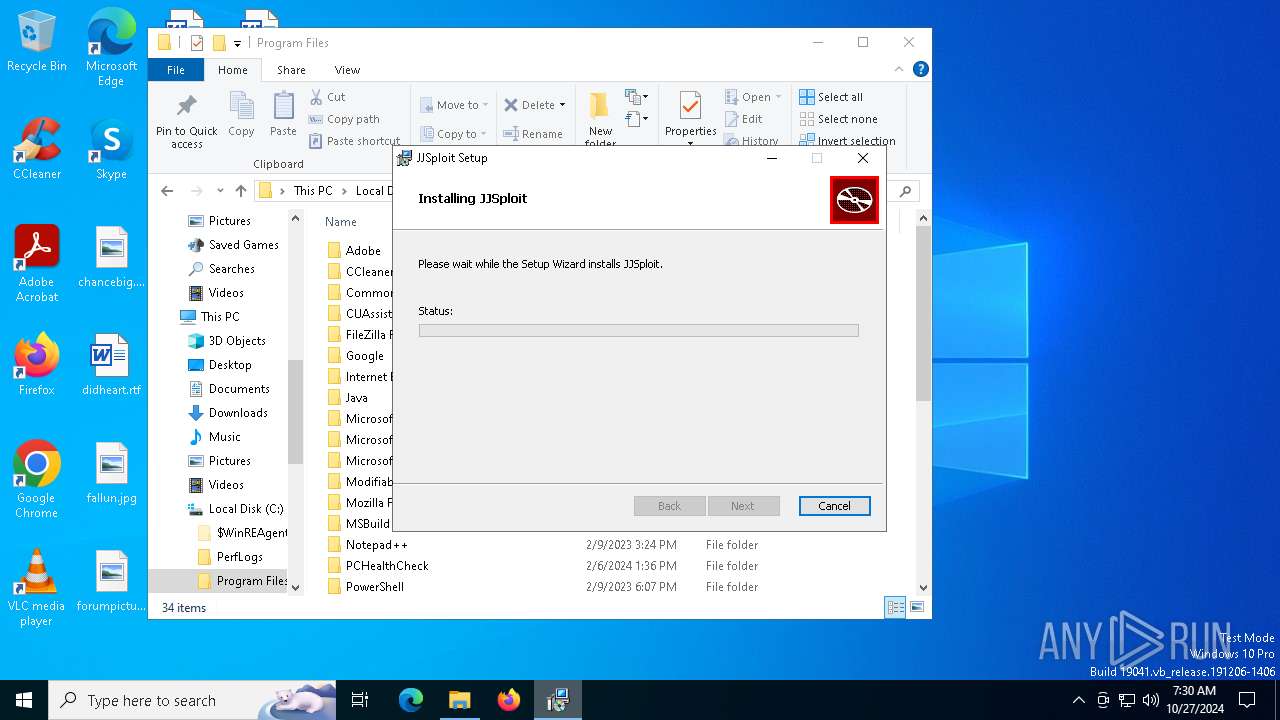
| File name: | JJSploit_8.10.10_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/8d7f33fa-c278-47f2-a732-8c34885c7717 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2024, 07:29:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: JJSploit, Author: wearedevs, Keywords: Installer, Comments: This installer database contains the logic and data required to install JJSploit., Template: x64;0, Revision Number: {283D1170-BF79-44E7-9EA0-801D93BD0365}, Create Time/Date: Thu Oct 24 12:44:38 2024, Last Saved Time/Date: Thu Oct 24 12:44:38 2024, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.14.1.8722), Security: 2 |
| MD5: | 8CB1E85B5723E3D186CC1742B6C71122 |
| SHA1: | F4638A9849B2BEA46C8120930C7727CFAE70B4D2 |
| SHA256: | F1DB224AF0F14B971BA8BE3E33482322B2F821695A4BBE2782B956217DA383AD |
| SSDEEP: | 98304:NFQ3rnqSHA2Z1hmyhQ+IO5aSXtTD2iZsUY2a5x2cddHEUGlGpX5fr1Hf/jNJJjbI:xbb/wxp71H |
MALICIOUS
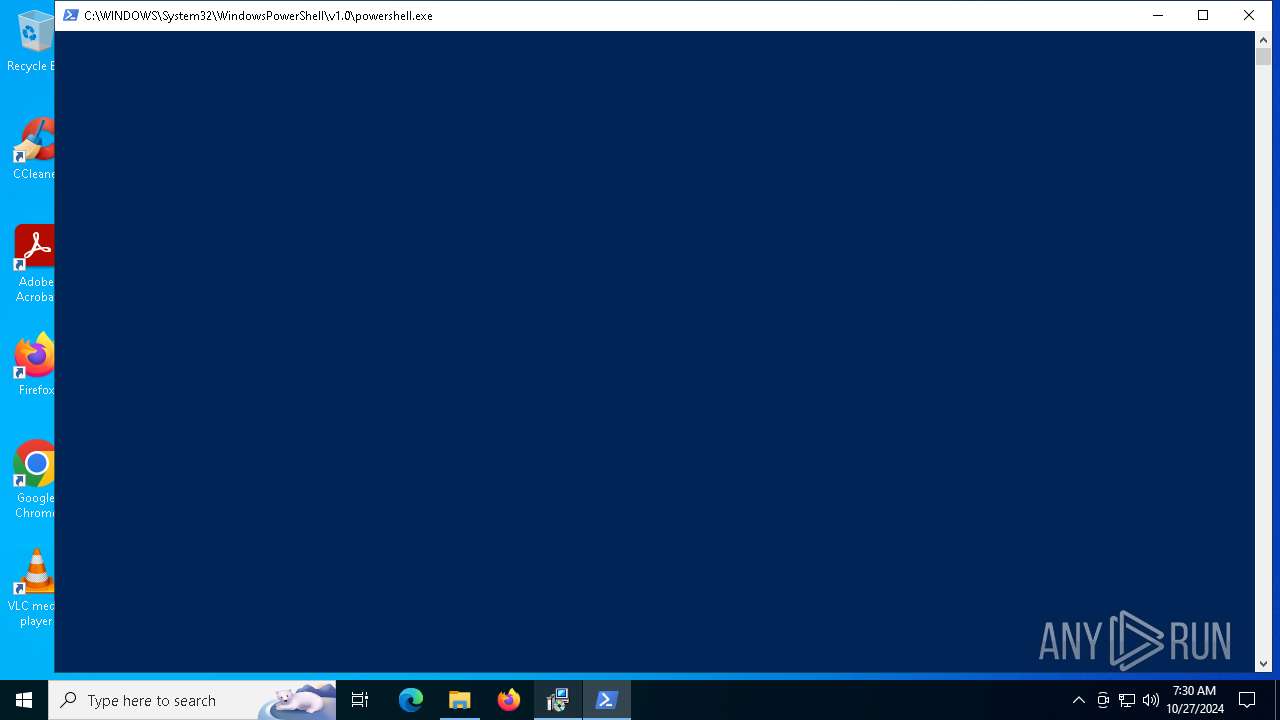
Run PowerShell with an invisible window
- powershell.exe (PID: 2864)
SUSPICIOUS
Manipulates environment variables
- powershell.exe (PID: 2864)
Starts process via Powershell
- powershell.exe (PID: 2864)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6684)
Downloads file from URI via Powershell
- powershell.exe (PID: 2864)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6684)
Executable content was dropped or overwritten
- powershell.exe (PID: 2864)
- MicrosoftEdgeWebview2Setup.exe (PID: 7256)
- MicrosoftEdgeUpdate.exe (PID: 7352)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 7256)
- MicrosoftEdgeUpdate.exe (PID: 7352)
Process drops legitimate windows executable
- powershell.exe (PID: 2864)
- MicrosoftEdgeWebview2Setup.exe (PID: 7256)
- MicrosoftEdgeUpdate.exe (PID: 7352)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 7352)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6684)
Executes as Windows Service
- VSSVC.exe (PID: 6336)
INFO
Reads the computer name
- msiexec.exe (PID: 6684)
- msiexec.exe (PID: 3076)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 7256)
An automatically generated document
- msiexec.exe (PID: 1732)
Checks supported languages
- msiexec.exe (PID: 6684)
- msiexec.exe (PID: 3076)
Manual execution by a user
- msedge.exe (PID: 7868)
Application launched itself
- msedge.exe (PID: 7868)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6684)
- msiexec.exe (PID: 1732)
Manages system restore points
- SrTasks.exe (PID: 6136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | JJSploit |
| Author: | wearedevs |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install JJSploit. |
| Template: | x64;0 |
| RevisionNumber: | {283D1170-BF79-44E7-9EA0-801D93BD0365} |
| CreateDate: | 2024:10:24 12:44:38 |
| ModifyDate: | 2024:10:24 12:44:38 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.14.1.8722) |
| Security: | Read-only recommended |
Total processes
174
Monitored processes
43
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3520 --field-trial-handle=2296,i,636641925282917021,12707159337043325554,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 1500 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4368 --field-trial-handle=2296,i,636641925282917021,12707159337043325554,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1732 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\JJSploit_8.10.10_x64_en-US.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3692 --field-trial-handle=2296,i,636641925282917021,12707159337043325554,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 2808 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6080 --field-trial-handle=2296,i,636641925282917021,12707159337043325554,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 2864 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3076 | C:\Windows\syswow64\MsiExec.exe -Embedding 42C08096CC7FB6C02489ED73BAF56385 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3952 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=5816 --field-trial-handle=2296,i,636641925282917021,12707159337043325554,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 4080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6108 --field-trial-handle=2296,i,636641925282917021,12707159337043325554,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
Total events
2 770
Read events
2 579
Write events
182
Delete events
9
Modification events
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000018FA83104228DB011C1A0000A0070000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000018FA83104228DB011C1A0000A0070000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000852DBD104228DB011C1A0000A0070000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000852DBD104228DB011C1A0000A0070000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000002B92BF104228DB011C1A0000A0070000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000D859C4104228DB011C1A0000A0070000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000004E8328114228DB011C1A0000A0070000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6684) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D2E62A114228DB011C1A0000241A0000E803000001000000000000000000000003ACF73A339A2E4E9DE28178F4710FC800000000000000000000000000000000 | |||
| (PID) Process: | (6336) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000A26234114228DB01C01800003C1A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
231
Suspicious files
351
Text files
78
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6684 | msiexec.exe | C:\Windows\Installer\92a8e.msi | — | |
MD5:— | SHA256:— | |||
| 1732 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIEA68.tmp | executable | |
MD5:CFBB8568BD3711A97E6124C56FCFA8D9 | SHA256:7F47D98AB25CFEA9B3A2E898C3376CC9BA1CD893B4948B0C27CAA530FD0E34CC | |||
| 6684 | msiexec.exe | C:\Windows\Installer\MSI2DF9.tmp | binary | |
MD5:24CC1ADBCA051D9D15A8F606BA955261 | SHA256:91B319ECEA070E6848A73F6512C24A7F54C9F40FCE2C46D0D2EABB2AE44F41C6 | |||
| 6684 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:8B816531C6084F044880BB95B4F2B18D | SHA256:1ECF651C2E588499FA0E3DD8D36F82904FEA687F08707DB052C582555F3A4FB9 | |||
| 6684 | msiexec.exe | C:\Windows\Temp\~DFE12ABC0B5FD14ADE.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6684 | msiexec.exe | C:\Program Files\JJSploit\resources\luascripts\animations\jumpland.lua | text | |
MD5:2899EC217AEF73B127C9328785012EEF | SHA256:7D4CA7B02C90B0B21D64C2BAA6E5940DCCE895DB5BC125D0E993A5A883186721 | |||
| 6684 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{3af7ac03-9a33-4e2e-9de2-8178f4710fc8}_OnDiskSnapshotProp | binary | |
MD5:A7ACFCEF67CE02A9834D4AB62EB3C1DB | SHA256:51ED85C94BCCDCE7C5093353D92FA1B1F97DE53CF470A15EEBB899CA6772631B | |||
| 6684 | msiexec.exe | C:\Windows\Temp\~DFCC9983F0FE8768EB.TMP | binary | |
MD5:8B816531C6084F044880BB95B4F2B18D | SHA256:1ECF651C2E588499FA0E3DD8D36F82904FEA687F08707DB052C582555F3A4FB9 | |||
| 6684 | msiexec.exe | C:\Program Files\JJSploit\resources\luascripts\general\teleportto.lua | text | |
MD5:CD719CA0E57C68FACFACEF67C2AAFE90 | SHA256:A22A6EF7A55035961C0A6F529C77D1100A333EC7A4CAA6384962E273C76CBA33 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
40
DNS requests
157
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | — | 199.232.210.172:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9929cff4-3487-4805-93f7-86acb813e26b?P1=1730619039&P2=404&P3=2&P4=kde8l%2f6wB7iC71IJjovdlRDjhgiOELXlAKkQ9MLg0FSvG6MYEoGtYfLNq7xctz7f4Ht7fDssmlPoS2KXTzOoLA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 304 | 2.18.161.41:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 304 | 195.138.255.18:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
7100 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7100 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5600 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potentially Bad Traffic | ET DNS Query for .cc TLD |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
— | — | Potentially Bad Traffic | ET DNS Query for .cc TLD |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |