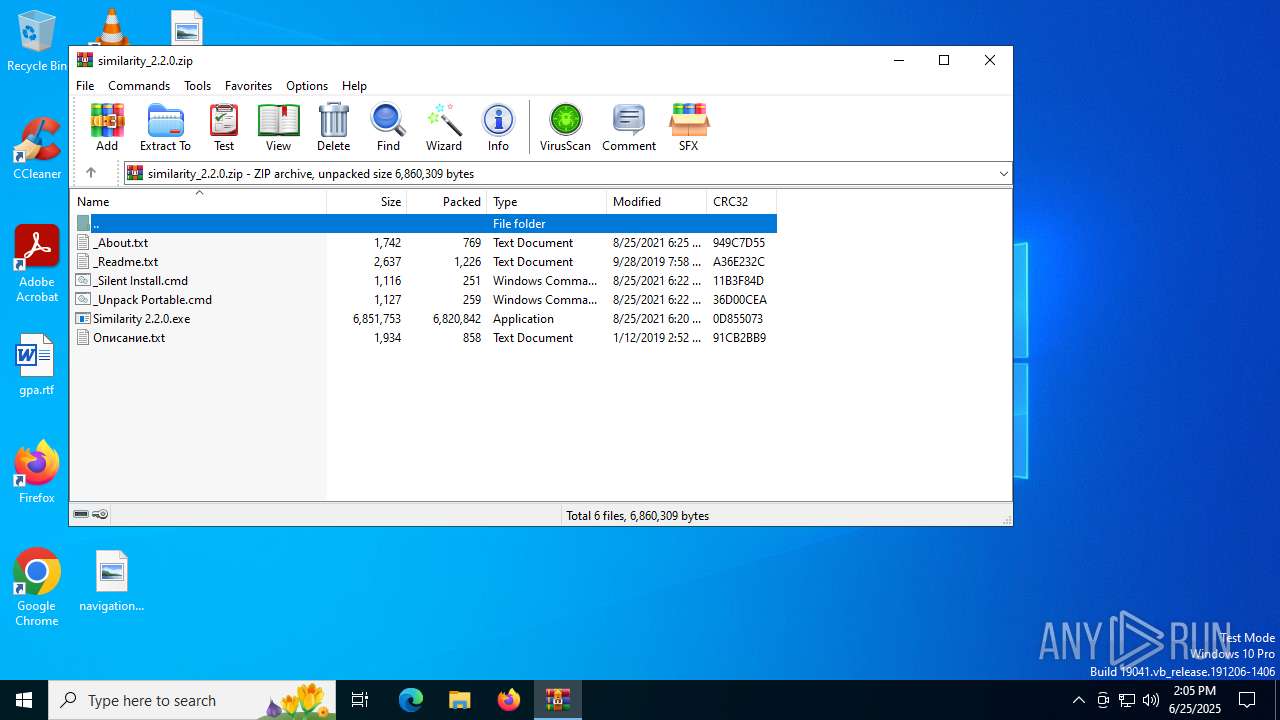
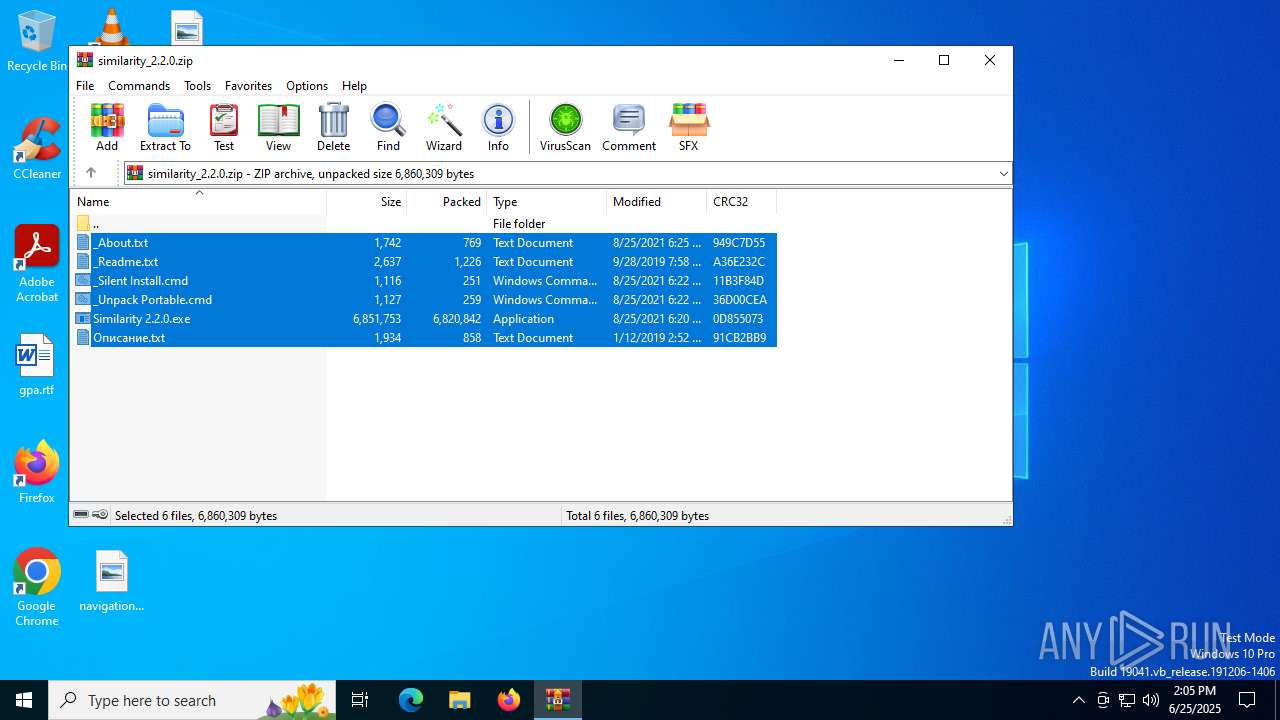
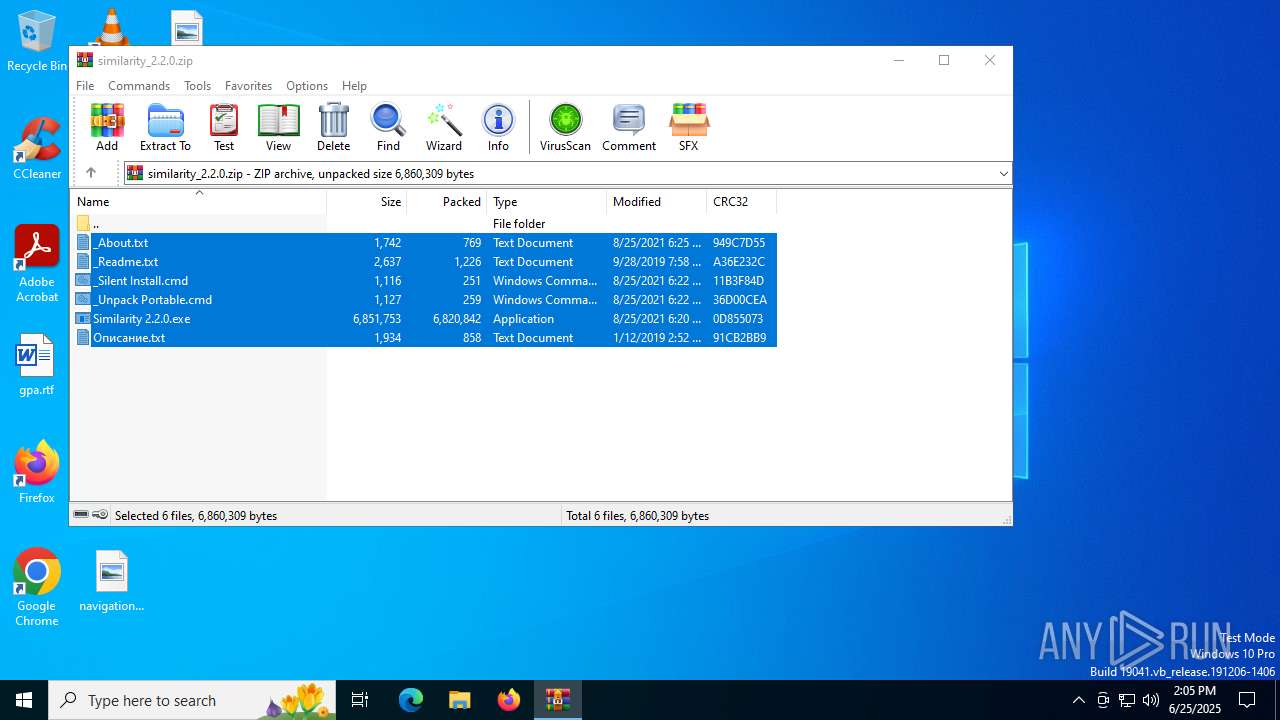
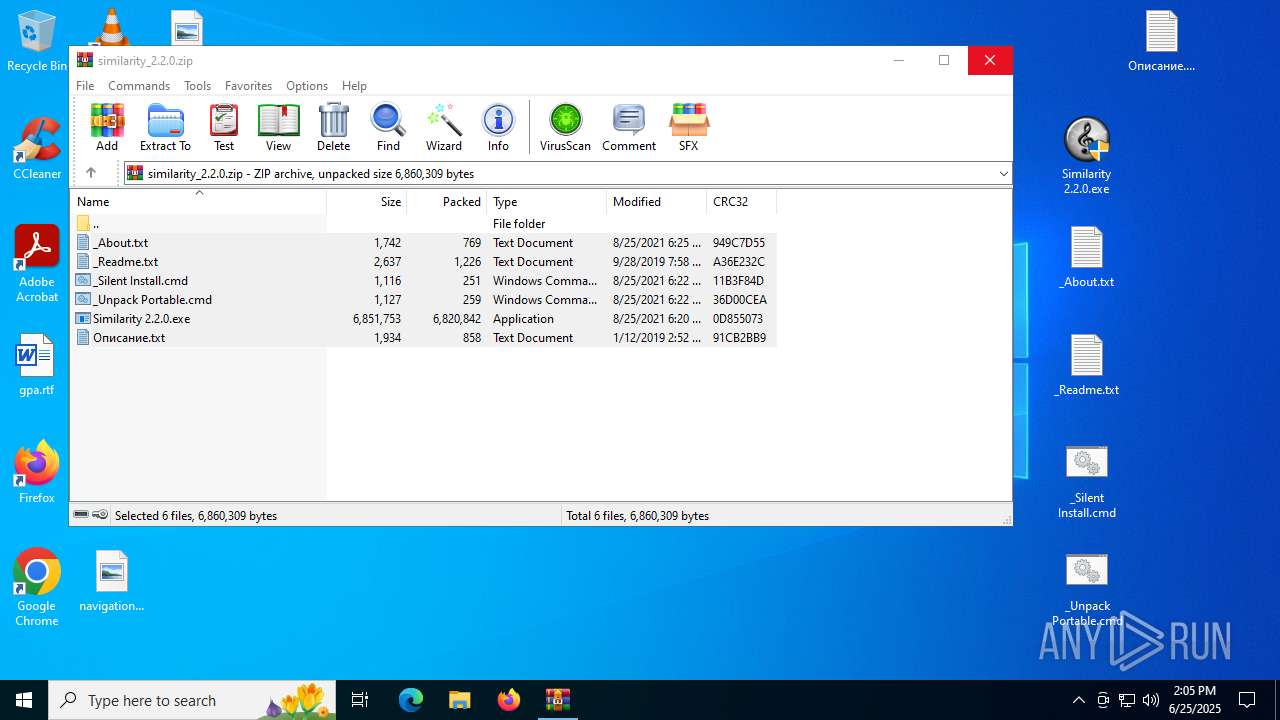
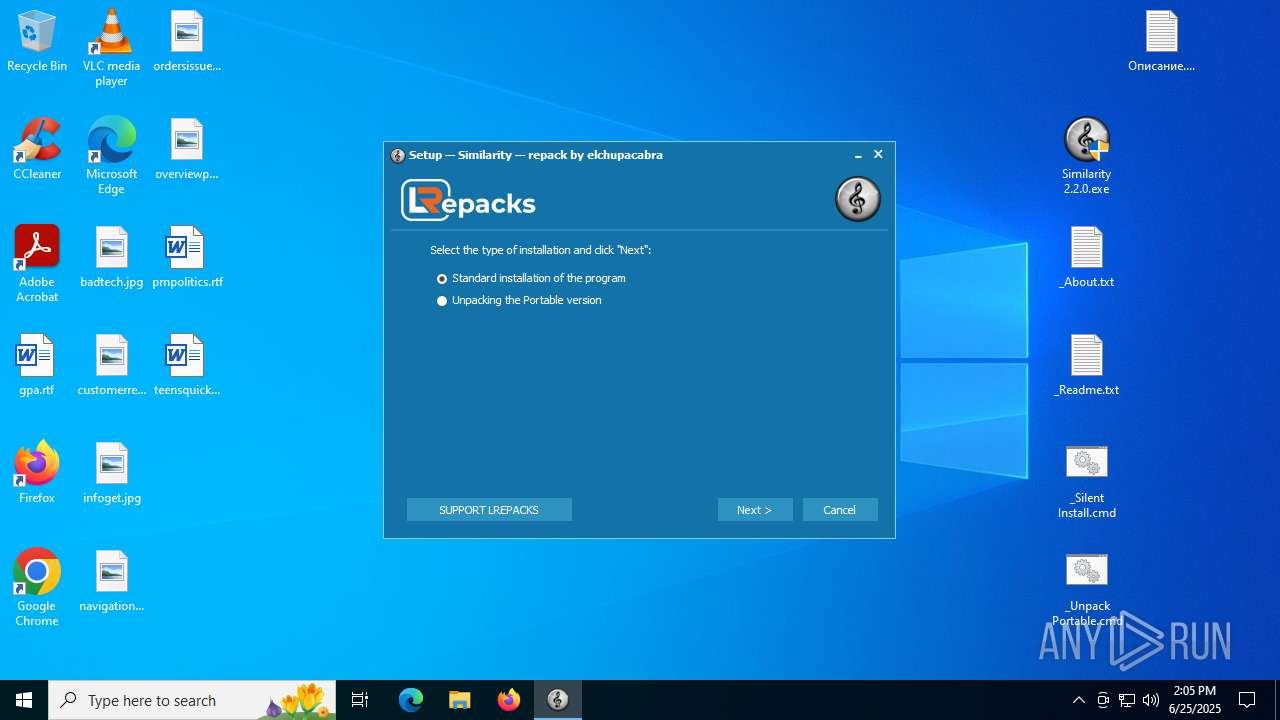
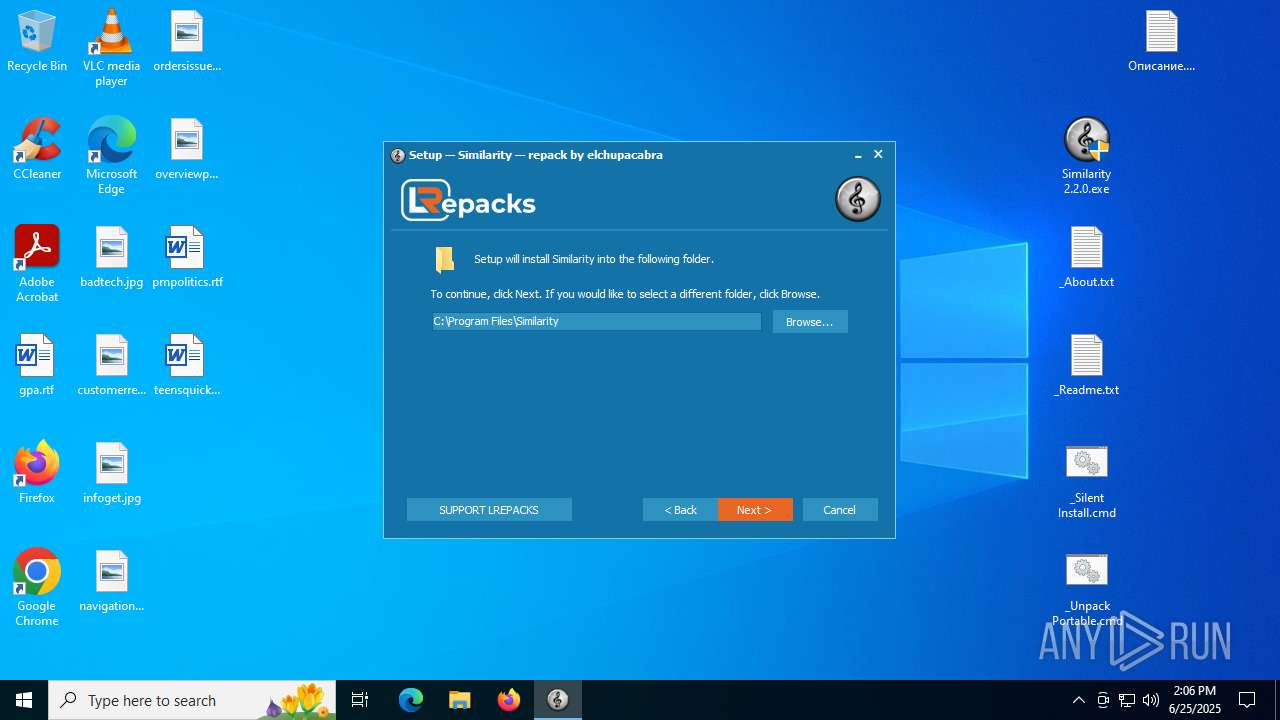
| File name: | similarity_2.2.0.zip |
| Full analysis: | https://app.any.run/tasks/43efc0ec-27bc-4351-a0ae-0bf2adae38e7 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2025, 14:05:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AB2D8EF48CD6689BEA33CE51AE14A70B |
| SHA1: | 36C766BBD3B22C2862EB90AAE033F5EEA537C25E |
| SHA256: | F1CD918C07BDAA207180EA60C0FD2F1BB164FA16A185BA9314237062D6338C61 |
| SSDEEP: | 98304:LsuDy9BonqqtdHTOrJ76KT4VUNOue1qqhOXCOSb0K0Obqnof8ct+Yb0N26GgA5bn:V08MrK1HxFncWhRAi |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5080)
SUSPICIOUS
Process drops legitimate windows executable
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
Executable content was dropped or overwritten
- Similarity 2.2.0.exe (PID: 4088)
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.exe (PID: 7412)
- Similarity 2.2.0.tmp (PID: 7396)
Reads the Windows owner or organization settings
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
Uses REG/REGEDIT.EXE to modify registry
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
Reads security settings of Internet Explorer
- Similarity 2.2.0.tmp (PID: 4880)
Searches for installed software
- Similarity 2.2.0.tmp (PID: 7396)
INFO
Manual execution by a user
- Similarity 2.2.0.exe (PID: 4088)
- Similarity 2.2.0.exe (PID: 6128)
- msedge.exe (PID: 2404)
- cmd.exe (PID: 6372)
- Similarity.exe (PID: 2128)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5080)
Reads the computer name
- Similarity 2.2.0.tmp (PID: 4880)
- identity_helper.exe (PID: 7432)
- identity_helper.exe (PID: 8132)
- Similarity 2.2.0.tmp (PID: 7396)
- Similarity.exe (PID: 2128)
Checks supported languages
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.exe (PID: 4088)
- SearchApp.exe (PID: 5328)
- identity_helper.exe (PID: 7432)
- identity_helper.exe (PID: 8132)
- Similarity 2.2.0.tmp (PID: 7396)
- Similarity.exe (PID: 2128)
- Similarity 2.2.0.exe (PID: 7412)
The sample compiled with english language support
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
The sample compiled with russian language support
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
Detects InnoSetup installer (YARA)
- Similarity 2.2.0.exe (PID: 4088)
- Similarity 2.2.0.tmp (PID: 4880)
Creates files in the program directory
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
Create files in a temporary directory
- Similarity 2.2.0.exe (PID: 4088)
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.exe (PID: 7412)
- Similarity 2.2.0.tmp (PID: 7396)
Creates files or folders in the user directory
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
- Similarity.exe (PID: 2128)
Compiled with Borland Delphi (YARA)
- Similarity 2.2.0.tmp (PID: 4880)
Creates a software uninstall entry
- Similarity 2.2.0.tmp (PID: 4880)
- Similarity 2.2.0.tmp (PID: 7396)
Reads the software policy settings
- SearchApp.exe (PID: 5328)
Process checks computer location settings
- SearchApp.exe (PID: 5328)
Application launched itself
- msedge.exe (PID: 7108)
- msedge.exe (PID: 2404)
- msedge.exe (PID: 7584)
- msedge.exe (PID: 1336)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5328)
- Similarity.exe (PID: 2128)
Reads Environment values
- identity_helper.exe (PID: 7432)
- identity_helper.exe (PID: 8132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:08:25 09:25:24 |
| ZipCRC: | 0x949c7d55 |
| ZipCompressedSize: | 769 |
| ZipUncompressedSize: | 1742 |
| ZipFileName: | _About.txt |
Total processes
194
Monitored processes
48
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2204,i,10265539032504591775,8600092936384181499,262144 --variations-seed-version --mojo-platform-channel-handle=2628 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
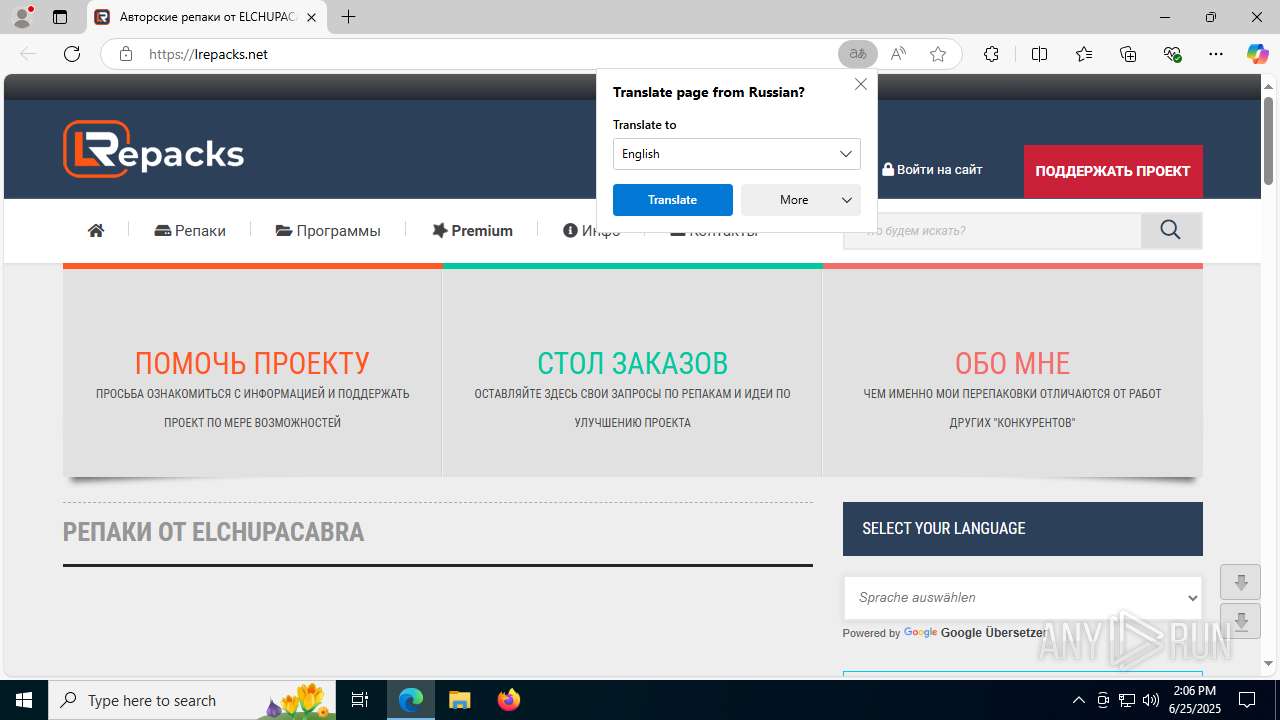
| 1336 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch --single-argument https://lrepacks.net/ | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2032 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2228,i,4045242395499670509,6487733397461340730,262144 --variations-seed-version --mojo-platform-channel-handle=2332 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
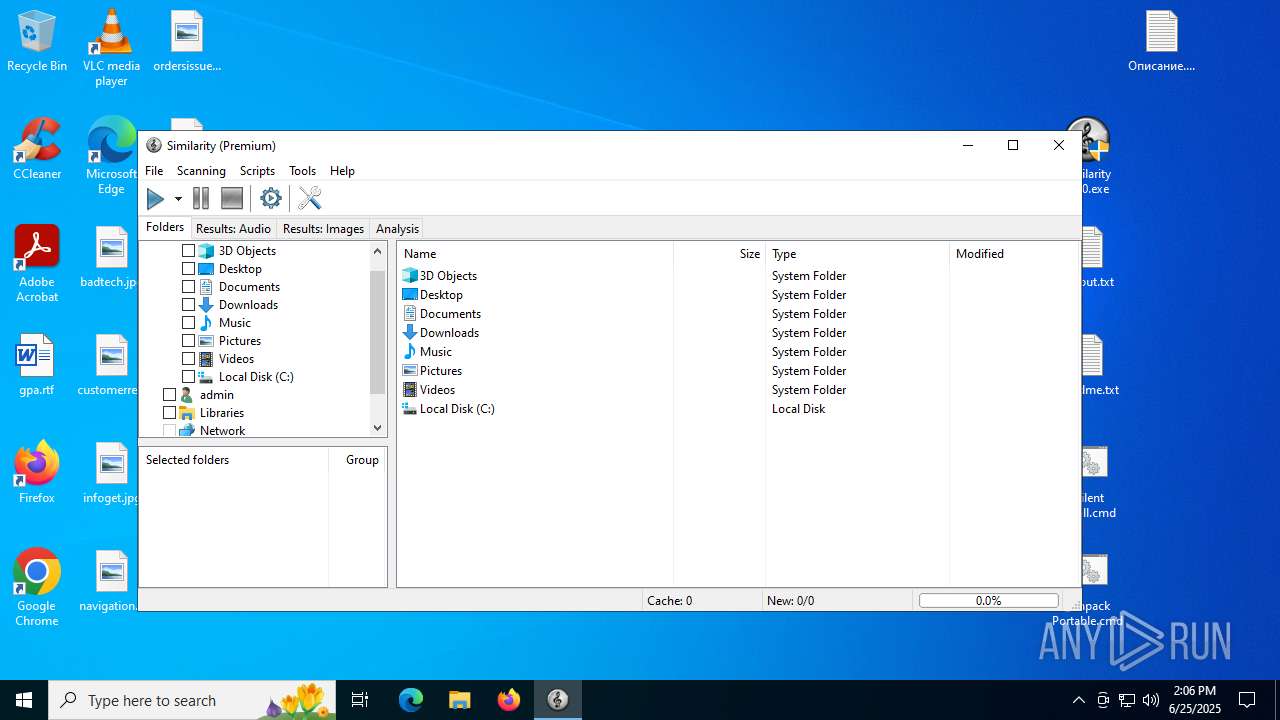
| 2128 | "C:\Program Files\Similarity\Similarity.exe" | C:\Program Files\Similarity\Similarity.exe | — | explorer.exe | |||||||||||
User: admin Company: © 2007-2016 GAR Software Integrity Level: MEDIUM Description: Similarity Exit code: 1 Version: 2.2.0.2204 Modules
| |||||||||||||||
| 2388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3552,i,10265539032504591775,8600092936384181499,262144 --variations-seed-version --mojo-platform-channel-handle=3684 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2404 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --disable-quic --flag-switches-end --do-not-de-elevate --single-argument https://lrepacks.net/ | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2468 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2696,i,10265539032504591775,8600092936384181499,262144 --variations-seed-version --mojo-platform-channel-handle=2788 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | "C:\Users\admin\Desktop\Similarity 2.2.0.exe" | C:\Users\admin\Desktop\Similarity 2.2.0.exe | explorer.exe | ||||||||||||
User: admin Company: LRepacks Integrity Level: HIGH Description: Similarity Setup Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
Total events
19 371
Read events
19 197
Write events
166
Delete events
8
Modification events
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\similarity_2.2.0.zip | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
37
Suspicious files
132
Text files
278
Unknown types
46
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.15890\_About.txt | text | |
MD5:80BF52FA51C70E1843C747F21B096CC8 | SHA256:C7D1CAD25195ADA8000DFF608270856B240C4692473C7F662B12306B9796AE1B | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.15890\_Silent Install.cmd | text | |
MD5:3A2600CD4B69BF034A2C07273FCDB6E9 | SHA256:FB95526878F2B8C8E5C3DAC6DC9EB780B6A4D6581956005E1309229D9B09CA17 | |||
| 4880 | Similarity 2.2.0.tmp | C:\Users\admin\AppData\Local\Temp\is-C4FUQ.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.15890\_Readme.txt | text | |
MD5:E47086C20C0E69016CC95CDE52BAA6DF | SHA256:D8DF425FB7E6C412736632D3AE3A3521309CE41E6149790533348C71B9F81954 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.15890\Similarity 2.2.0.exe | executable | |
MD5:8A71DF1CB5AB1DE9458A3BF9282593AB | SHA256:F36BB85D451661DA55225975C5756891BAA026475047C1D62A56428A6BF3343A | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.15890\Описание.txt | text | |
MD5:5883858BB398A317BEA876BB9D2DFC74 | SHA256:4F0A794F78EE501CABEECD8128FC061C54BC598C51226D8A903D38050E9C0C90 | |||
| 5080 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5080.15890\_Unpack Portable.cmd | text | |
MD5:BBF685574D49905A31BEC42447738DB6 | SHA256:8D340031F510DE0669BFAA171BD9D9B63ABC7B517339388D20691B784F381DF4 | |||
| 4880 | Similarity 2.2.0.tmp | C:\Users\admin\AppData\Local\Temp\is-C4FUQ.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 4880 | Similarity 2.2.0.tmp | C:\Users\admin\AppData\Local\Temp\is-C4FUQ.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 4880 | Similarity 2.2.0.tmp | C:\Users\admin\AppData\Local\Temp\is-C4FUQ.tmp\VclStylesInno.dll | executable | |
MD5:B0CA93CEB050A2FEFF0B19E65072BBB5 | SHA256:0E93313F42084D804B9AC4BE53D844E549CFCAF19E6F276A3B0F82F01B9B2246 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
116
DNS requests
112
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
420 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6164 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6164 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1052 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:SZ6LQGN_4dD7SccMU05wUTjdMrm-3UT__RSNkZcoZRo&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4512 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
420 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
420 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|