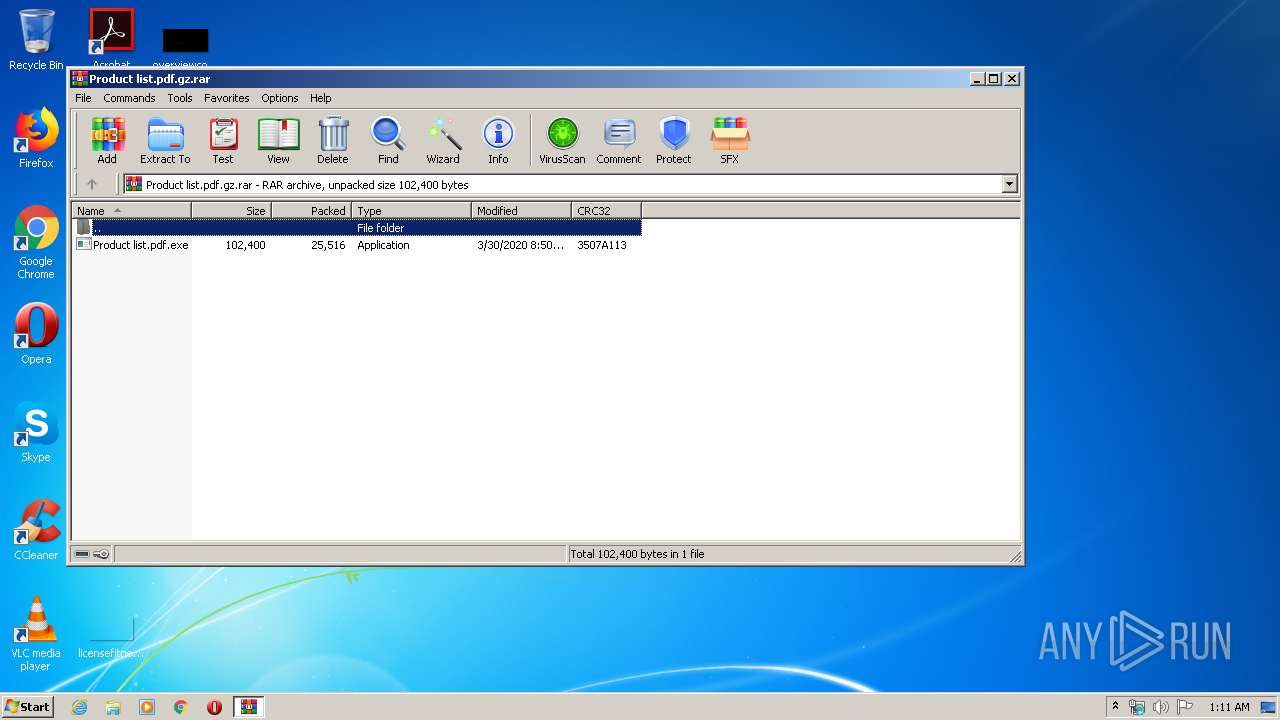
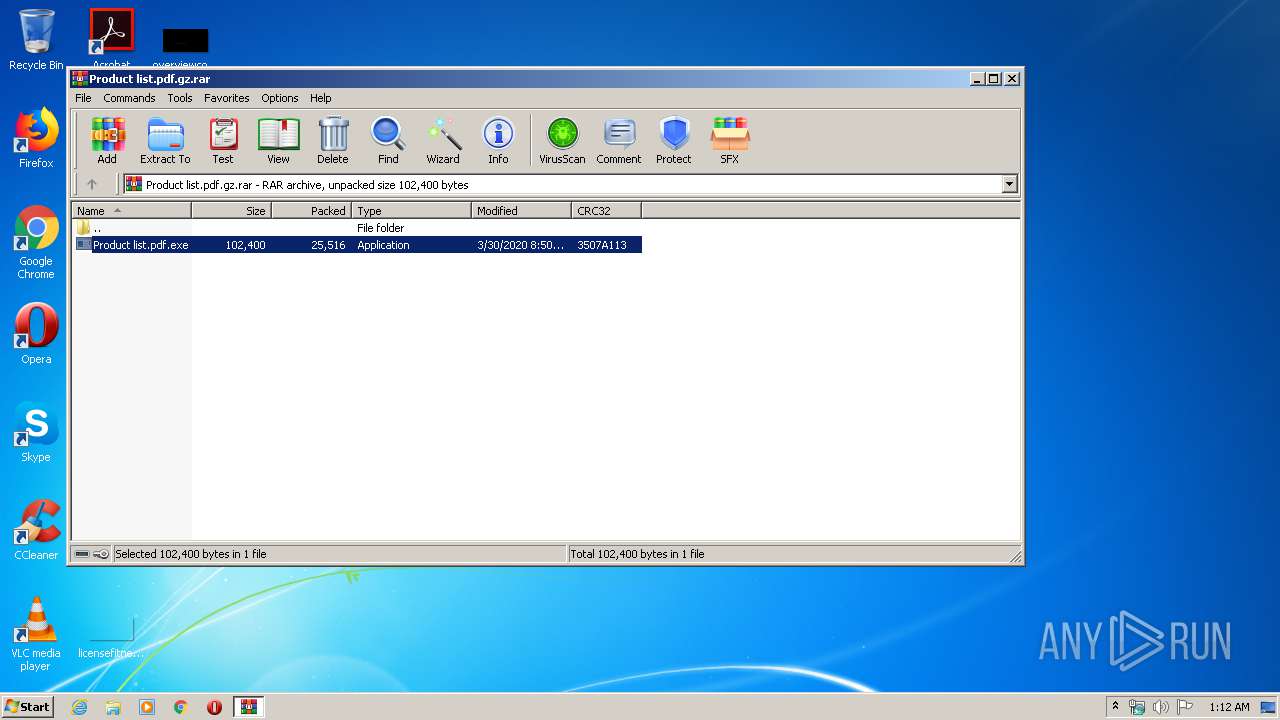
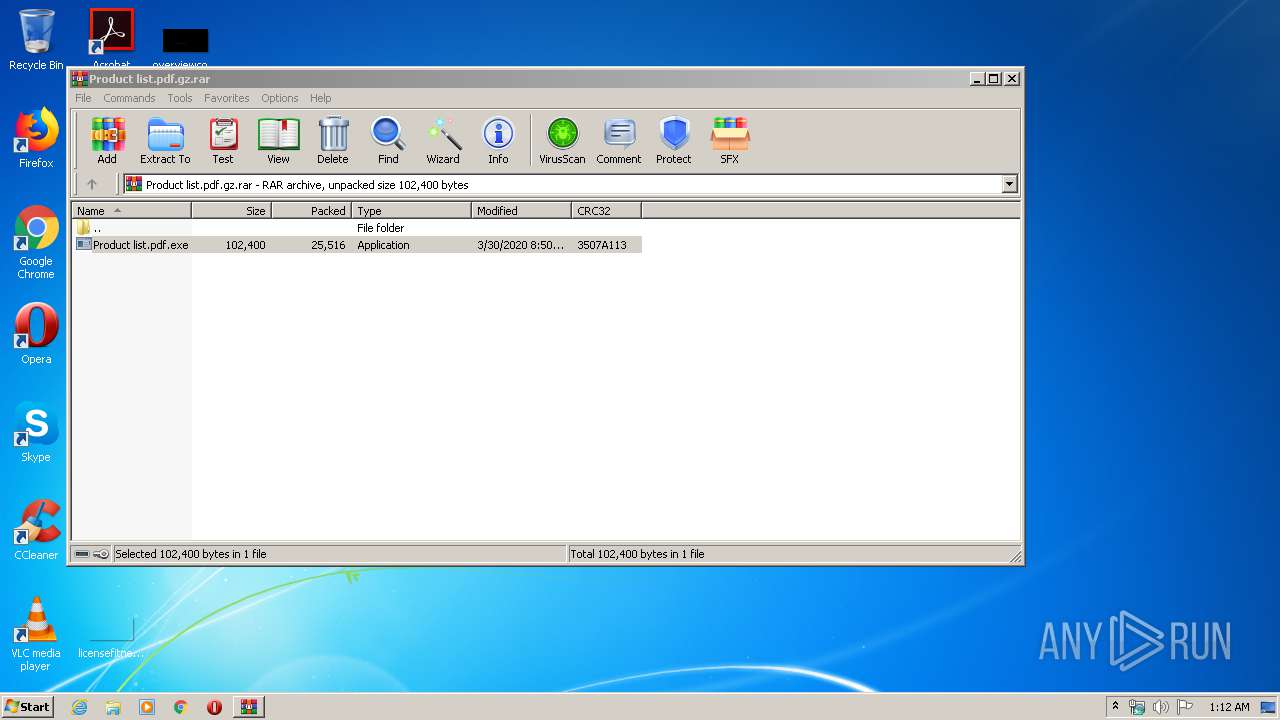
| File name: | Product list.pdf.gz |
| Full analysis: | https://app.any.run/tasks/a1b4df7c-22d8-46f7-94c0-02498b066fa6 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 00:11:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5476D7E612541522C4EBBC17654C169B |
| SHA1: | 7C11B4E31721F2EF61E85C3E8291281DD8A5A7A3 |
| SHA256: | F1CC7BCFCE852A007B51FBDFC19292619461715999C2C619ED91DBAAFA579D7B |
| SSDEEP: | 384:zfczVl3LvPOJsSDgq/w48OJmKzaO3RfhqduY5m8hu02nepIXKtkIs4MUivV:zUV1vPusmnQO4eJh6mnv6tkIs4nivV |
MALICIOUS
Application was dropped or rewritten from another process
- Product list.pdf.exe (PID: 3612)
- Product list.pdf.exe (PID: 4056)
Actions looks like stealing of personal data
- Product list.pdf.exe (PID: 4056)
Changes settings of System certificates
- Product list.pdf.exe (PID: 4056)
SUSPICIOUS
Creates files in the user directory
- Product list.pdf.exe (PID: 4056)
Application launched itself
- Product list.pdf.exe (PID: 3612)
Reads Internet Cache Settings
- Product list.pdf.exe (PID: 4056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2820)
Adds / modifies Windows certificates
- Product list.pdf.exe (PID: 4056)
INFO
Reads settings of System Certificates
- Product list.pdf.exe (PID: 4056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
36
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2820 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Product list.pdf.gz.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3612 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2820.34846\Product list.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2820.34846\Product list.pdf.exe | — | WinRAR.exe | |||||||||||
User: admin Company: WONderware Integrity Level: MEDIUM Description: Stiklings Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 4056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2820.34846\Product list.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2820.34846\Product list.pdf.exe | Product list.pdf.exe | ||||||||||||
User: admin Company: WONderware Integrity Level: MEDIUM Description: Stiklings Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
4 436
Read events
481
Write events
2 639
Delete events
1 316
Modification events
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Product list.pdf.gz.rar | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2820) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
4
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\Local\Temp\CabEC9A.tmp | — | |
MD5:— | SHA256:— | |||
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\Local\Temp\TarEC9B.tmp | — | |
MD5:— | SHA256:— | |||
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_C9FB72B5AE80778A08024D8B0FDECC6F | binary | |
MD5:— | SHA256:— | |||
| 2820 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2820.34846\Product list.pdf.exe | executable | |
MD5:— | SHA256:— | |||
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_D9817BD5013875AD517DA73475345203 | der | |
MD5:— | SHA256:— | |||
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_D9817BD5013875AD517DA73475345203 | binary | |
MD5:— | SHA256:— | |||
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_C9FB72B5AE80778A08024D8B0FDECC6F | der | |
MD5:— | SHA256:— | |||
| 4056 | Product list.pdf.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\TXVRE35Z.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
4
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4056 | Product list.pdf.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
4056 | Product list.pdf.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4056 | Product list.pdf.exe | 13.107.42.12:443 | 4apotw.bn.files.1drv.com | Microsoft Corporation | US | suspicious |
4056 | Product list.pdf.exe | 212.227.15.142:587 | smtp.1and1.es | 1&1 Internet SE | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
ocsp.digicert.com |
| whitelisted |
4apotw.bn.files.1drv.com |
| whitelisted |
smtp.1and1.es |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4056 | Product list.pdf.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |