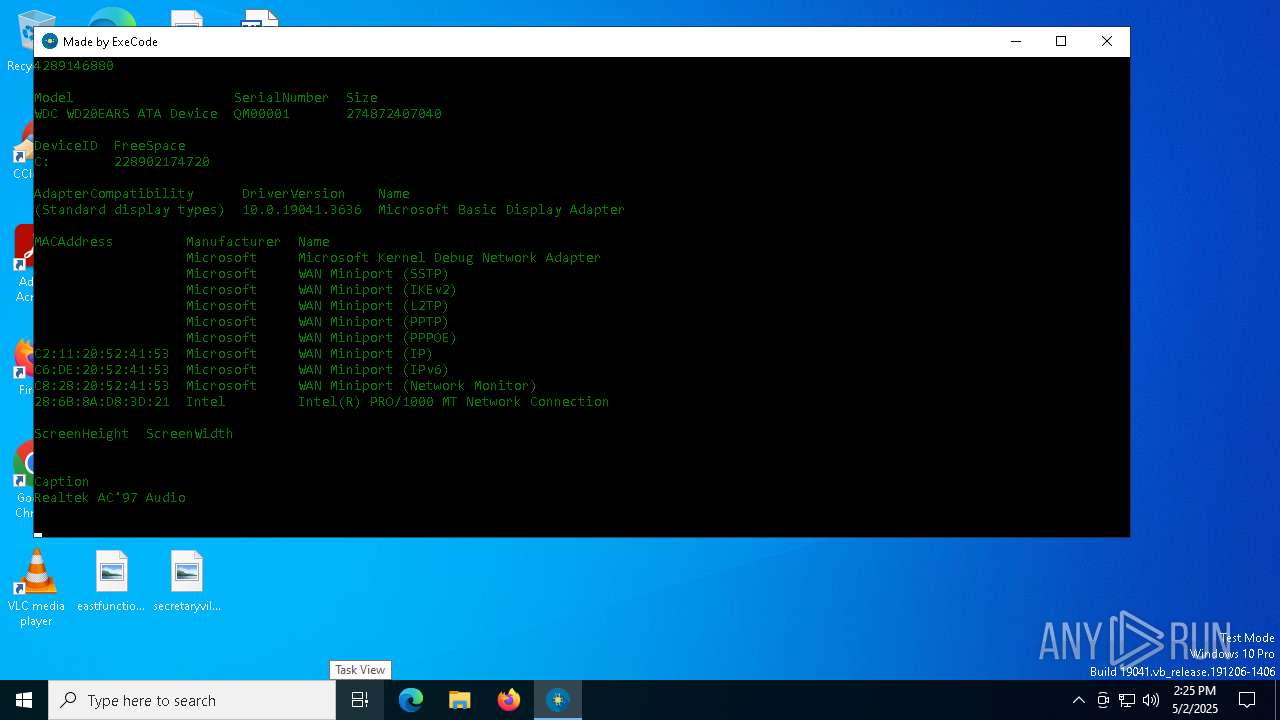
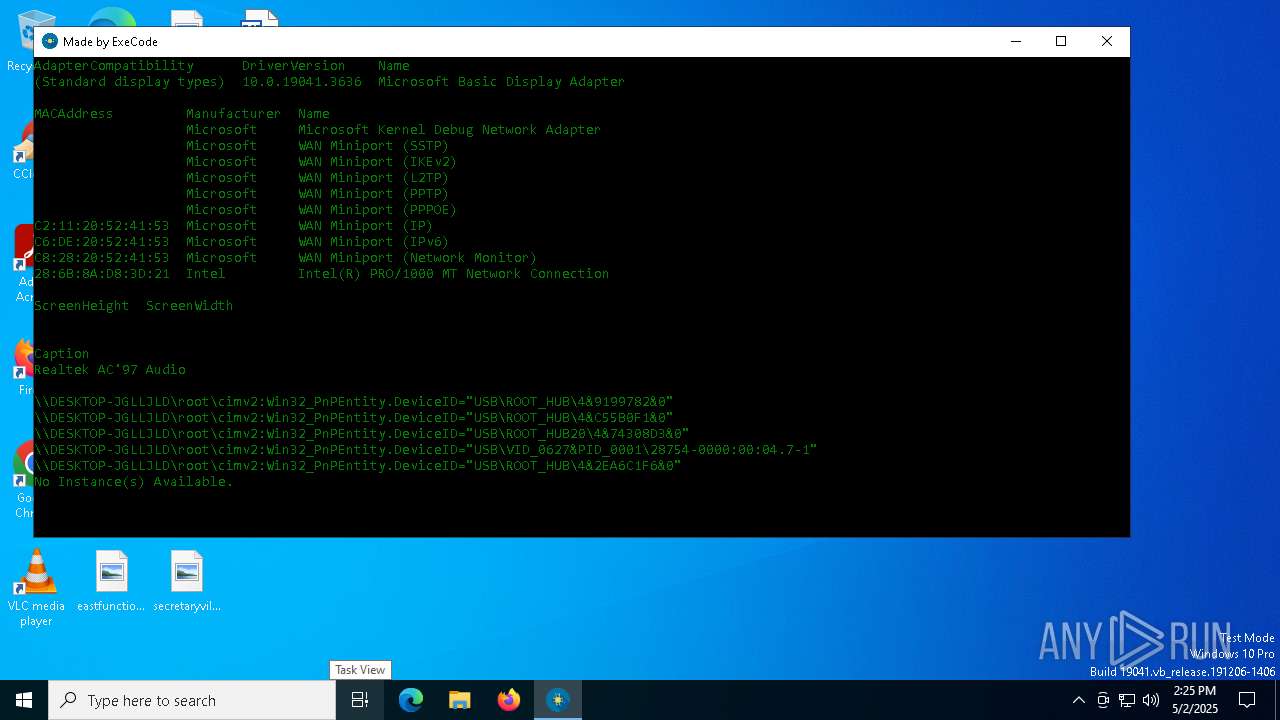
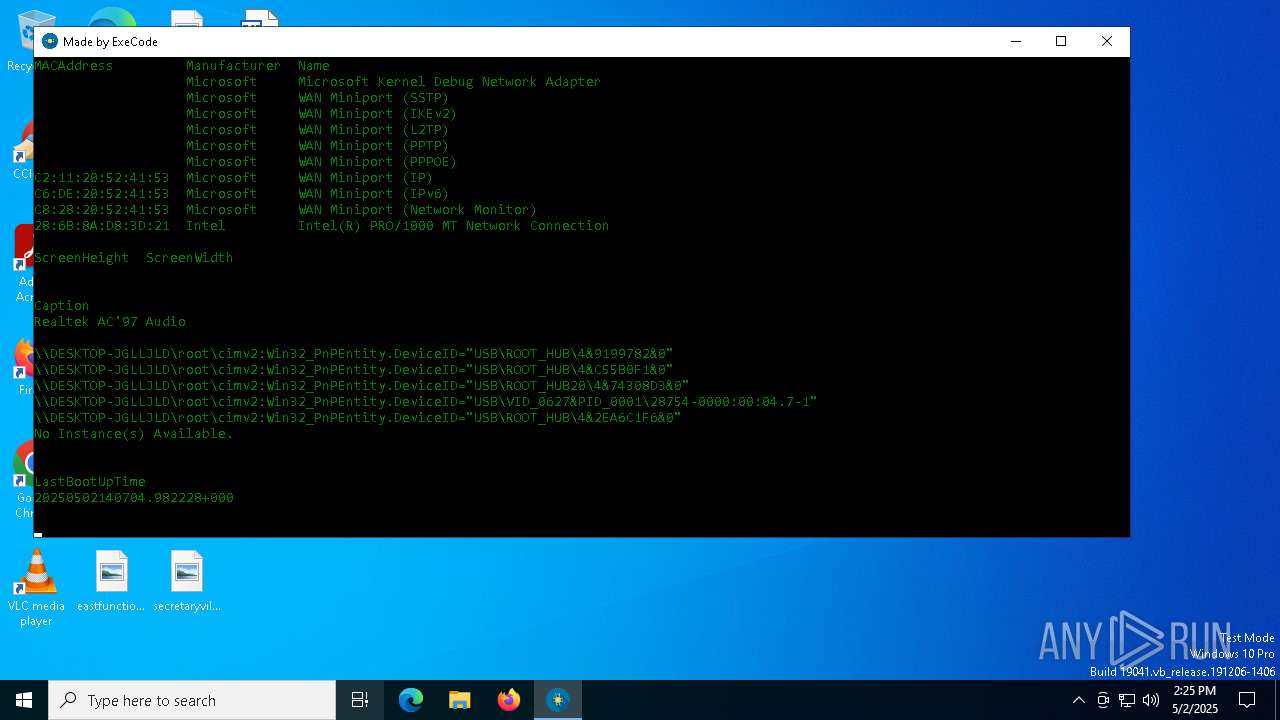
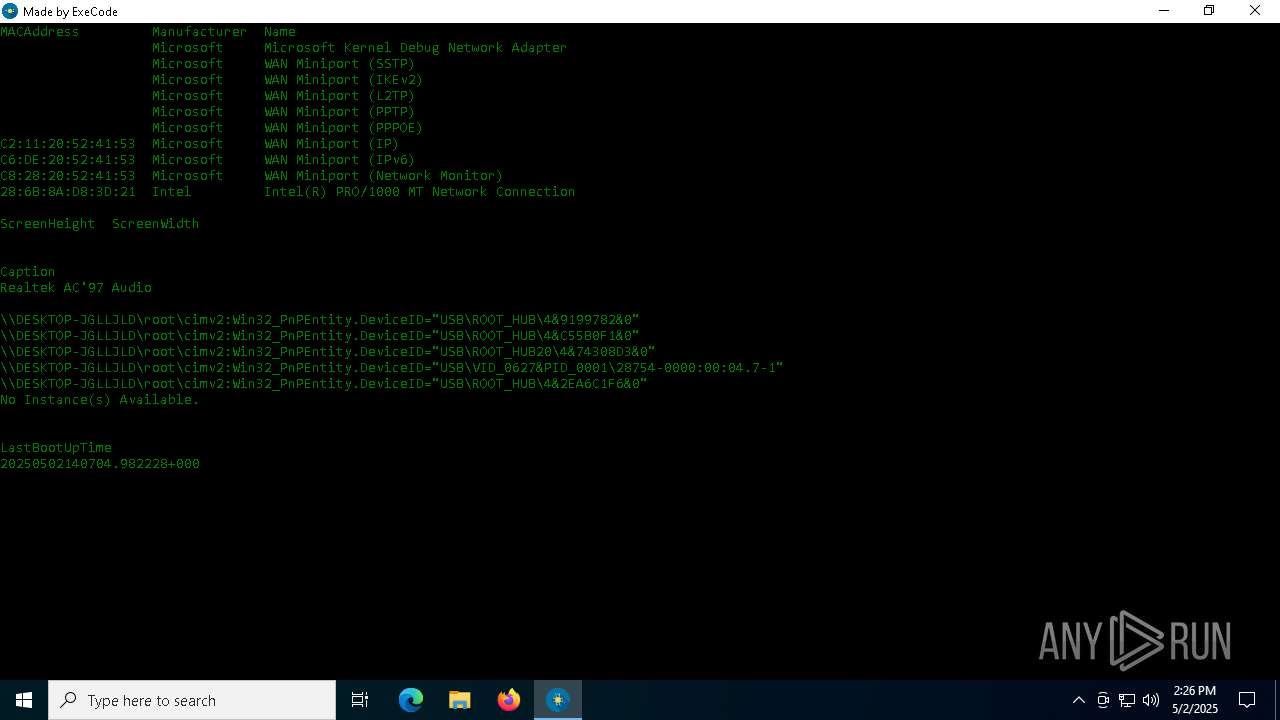
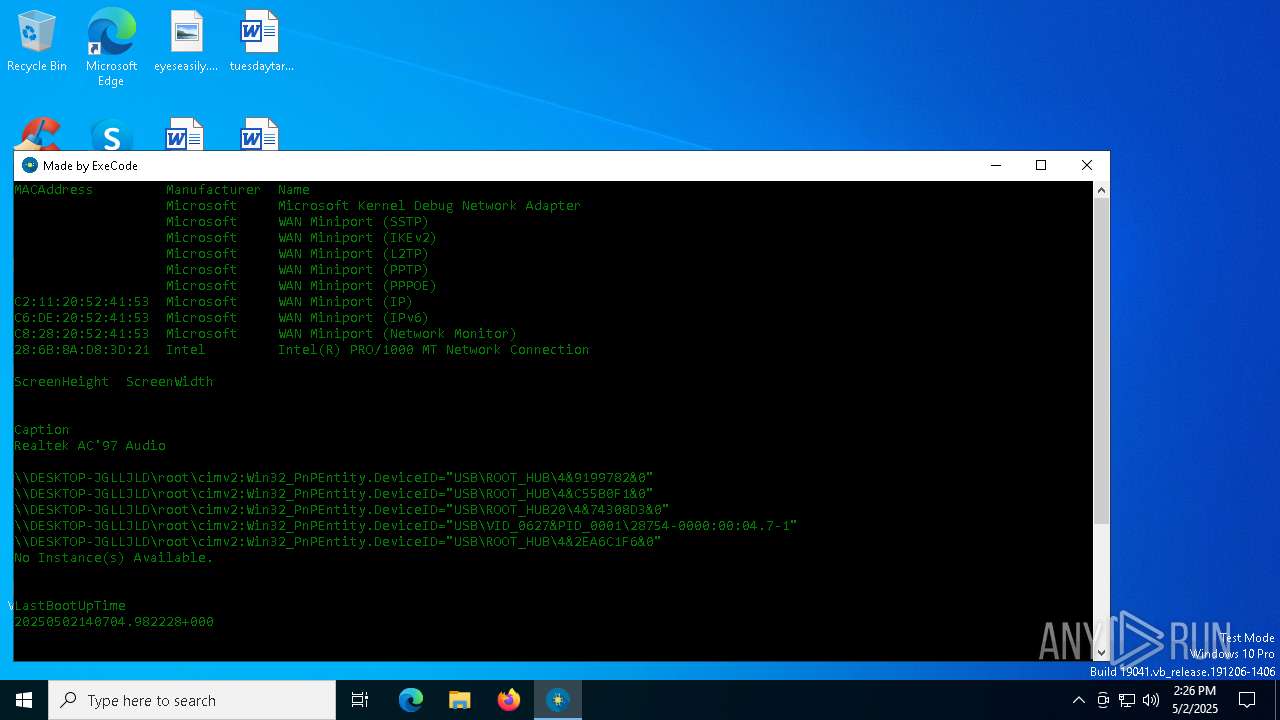
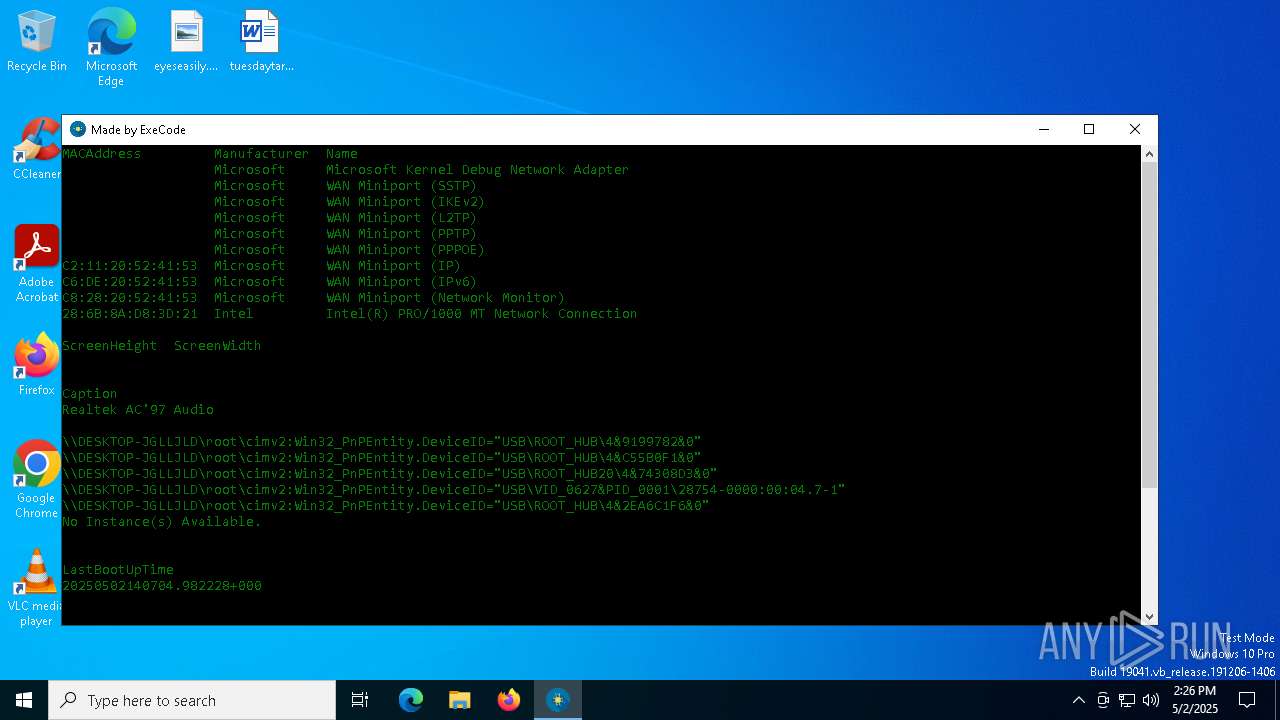
| File name: | HWID Lookup V 2.0_[unknowncheats.me]_.exe |
| Full analysis: | https://app.any.run/tasks/33281ce7-55bf-4981-8ea3-5d41b039da0c |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2025, 14:25:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 60A4BD9E3584D859E7F0A2A33AD8D8F0 |
| SHA1: | EA478C22C2D4F3E07CBF9EE1C40BEFD1CB47EADE |
| SHA256: | F1975B74F9EC508DC5EFFC624B627E9AE62A8D02D12B0A6B5FB72D8442F9A6ED |
| SSDEEP: | 3072:t/25jvDSgsqsb5Uh28vAbTV1WW69B9VjMdxPedN9ug0z9TBfFSmsdRe:Atzsb5Uh28+V1WW69B9VjMdxPedN9uge |
MALICIOUS
No malicious indicators.SUSPICIOUS
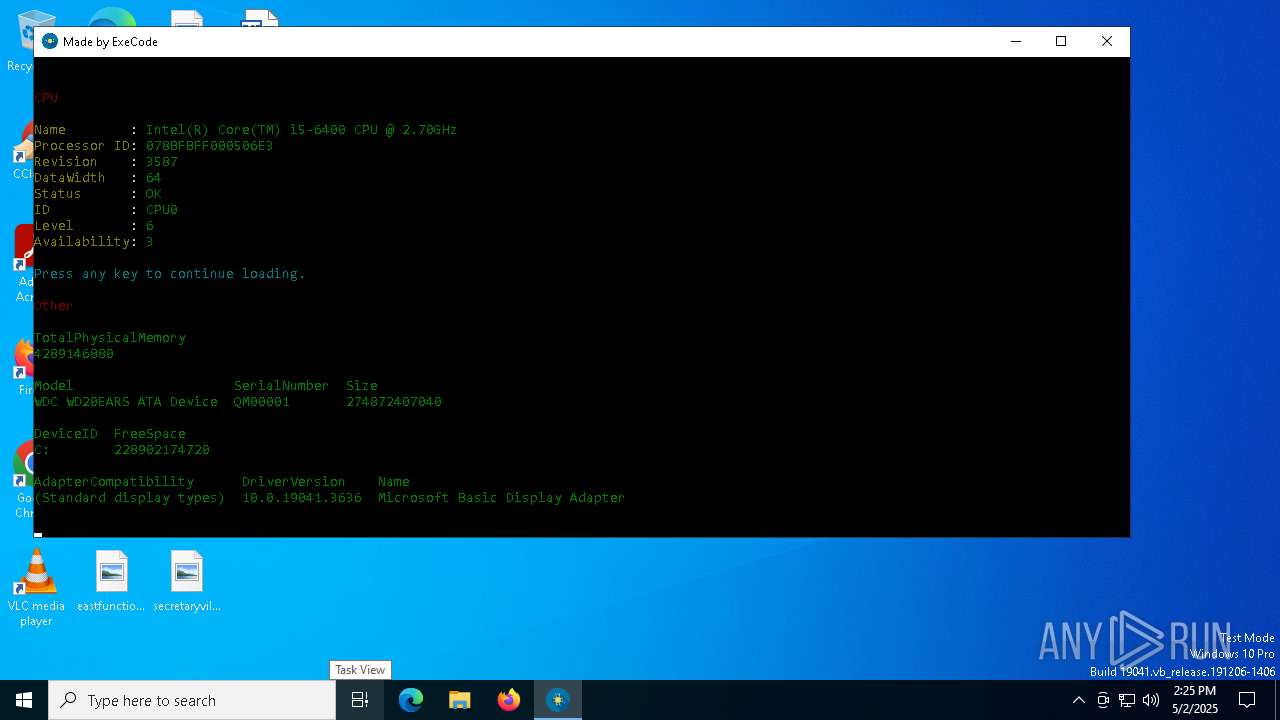
Accesses computer name via WMI (SCRIPT)
- WMIC.exe (PID: 7604)
- WMIC.exe (PID: 5968)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 7996)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7864)
Starts CMD.EXE for commands execution
- HWID Lookup V 2.0_[unknowncheats.me]_.exe (PID: 7364)
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain system information
- cmd.exe (PID: 7588)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 7464)
- cmd.exe (PID: 7420)
Executing commands from a ".bat" file
- HWID Lookup V 2.0_[unknowncheats.me]_.exe (PID: 7364)
Application launched itself
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 7480)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 8056)
Uses WMIC.EXE to obtain local storage devices information
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain information about the network interface controller
- cmd.exe (PID: 7420)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 8084)
Uses WMIC.EXE to obtain desktop monitor information
- cmd.exe (PID: 7420)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7420)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7420)
Sets XML DOM element text (SCRIPT)
- WMIC.exe (PID: 5968)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7420)
Uses WMIC.EXE to obtain Sound Devices data
- cmd.exe (PID: 7420)
Uses WMIC.EXE
- cmd.exe (PID: 7420)
INFO
Create files in a temporary directory
- HWID Lookup V 2.0_[unknowncheats.me]_.exe (PID: 7364)
Checks supported languages
- HWID Lookup V 2.0_[unknowncheats.me]_.exe (PID: 7364)
- mode.com (PID: 7440)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7604)
- WMIC.exe (PID: 7880)
- WMIC.exe (PID: 7664)
- WMIC.exe (PID: 7480)
- WMIC.exe (PID: 7728)
- WMIC.exe (PID: 7792)
- WMIC.exe (PID: 5968)
- WMIC.exe (PID: 7284)
- WMIC.exe (PID: 3008)
- WMIC.exe (PID: 4464)
- WMIC.exe (PID: 7624)
- WMIC.exe (PID: 8012)
- WMIC.exe (PID: 8072)
- WMIC.exe (PID: 8144)
- WMIC.exe (PID: 7904)
- WMIC.exe (PID: 8008)
- WMIC.exe (PID: 8084)
- WMIC.exe (PID: 8056)
- WMIC.exe (PID: 8180)
- WMIC.exe (PID: 7652)
- WMIC.exe (PID: 7864)
- WMIC.exe (PID: 6080)
- WMIC.exe (PID: 7248)
- WMIC.exe (PID: 5968)
- WMIC.exe (PID: 7284)
Starts MODE.COM to configure console settings
- mode.com (PID: 7440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 102912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
180
Monitored processes
50
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | C:\WINDOWS\system32\cmd.exe /c wmic cpu get processorid | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\system32\cmd.exe /c wmic cpu get level | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | wmic cpu get level | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4464 | wmic cpu get processorid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | C:\WINDOWS\system32\cmd.exe /c wmic cpu get datawidth | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | wmic cpu get datawidth | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | wmic path Win32_USBControllerDevice get Dependent | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6080 | wmic os get LastBootUpTime | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6156 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | findstr /B /C:"Betriebssystemname" /C:"Betriebssystemversion" /C:"Installiertes Patch" /C:"Systemtyp" /C:"Registrierte Benutzerorganisation" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 841
Read events
9 839
Write events
2
Delete events
0
Modification events
| (PID) Process: | (7176) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31177582 | |||
| (PID) Process: | (7176) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 475614093 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7176 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:5589B840A2F52690ECC792282E3E1E5B | SHA256:4A757C1DD8B39ED1E1E0B41F2870730C604FCAE3FEAABA00B095A4786DABF892 | |||
| 7364 | HWID Lookup V 2.0_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\F389.tmp\F39A.tmp\F39B.bat | text | |
MD5:B2E826C35CD955D297BD0CCC47270D16 | SHA256:D77E9A07F98D9361A8627449341EE8B47B078D47E6C4D5B9F241CAF6380E7472 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 23.59.18.102:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 23.59.18.102:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.43:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2568 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |