| File name: | Windows12.exe |
| Full analysis: | https://app.any.run/tasks/3ba3fced-922f-4ed6-9a18-7e7c0dc7c73a |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 04:55:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 3 sections |
| MD5: | 4948F35C6EFBF5F7003EE9D1E38B8326 |
| SHA1: | 22289A2FD963B6994C5ACCAD497895969BE87A71 |
| SHA256: | F196011831747A03C7B78B0884EE2DBC184383EFBD33F524CECF4A97466EA3FF |
| SSDEEP: | 6144:DdX1kAiUnAsHmmzifRsJ1LV425M/JuLt1azpqXrk3E6vHSvDcVfWN+81YPn5kDN/:ZXHiUnAsHx |
MALICIOUS
No malicious indicators.SUSPICIOUS
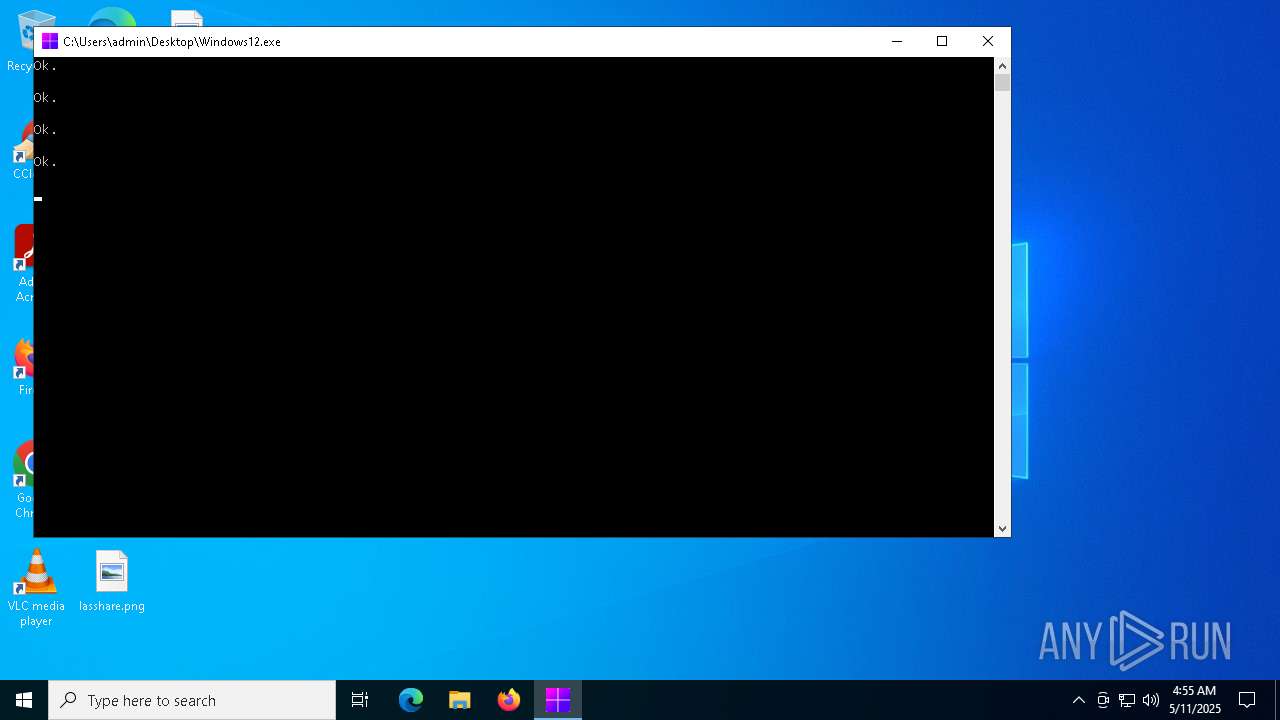
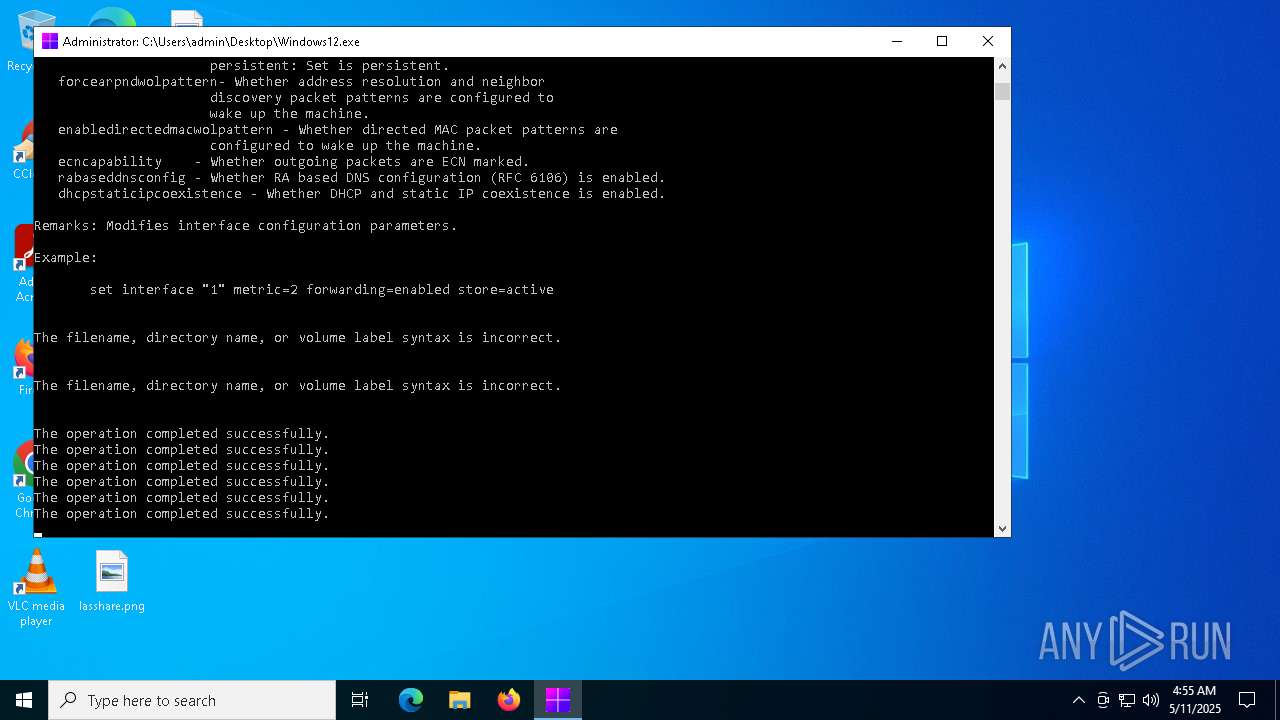
Executing commands from a ".bat" file
- Windows12.exe (PID: 5072)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7020)
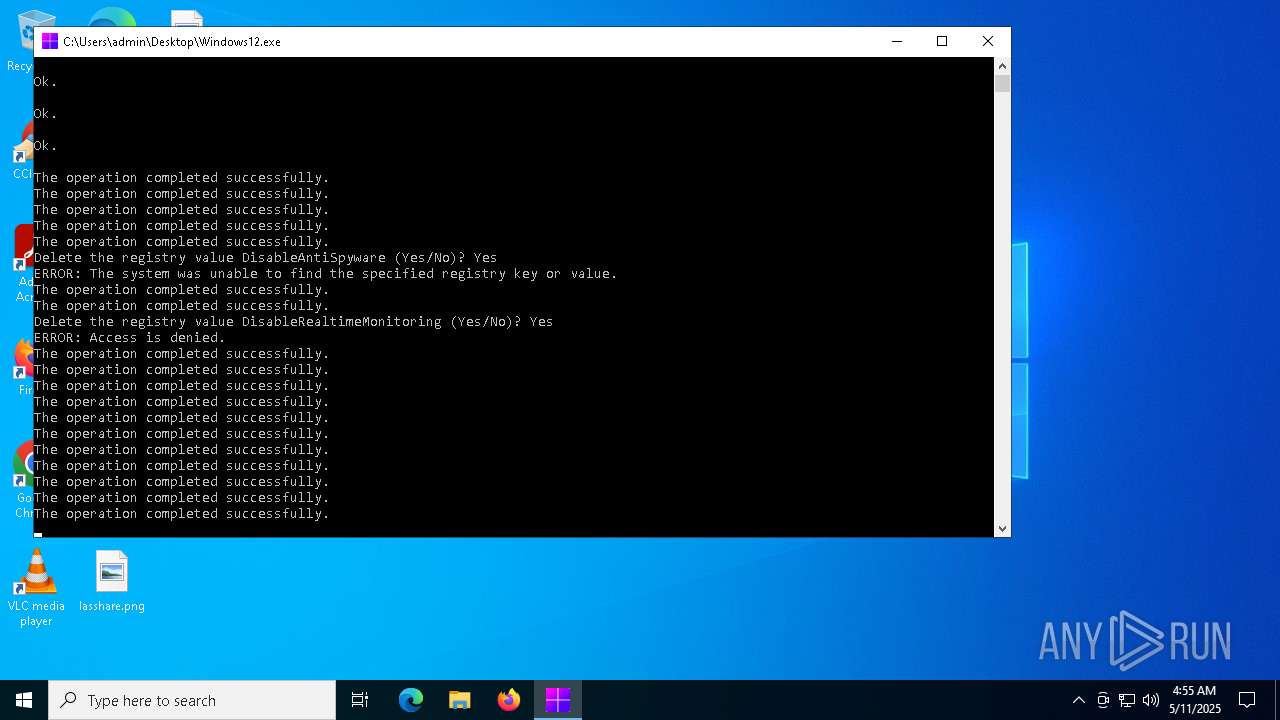
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7020)
Starts CMD.EXE for commands execution
- Windows12.exe (PID: 5072)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 7020)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7020)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 7020)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7020)
The process executes via Task Scheduler
- explorer.exe (PID: 7696)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 5324)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5324)
INFO
Create files in a temporary directory
- Windows12.exe (PID: 5072)
Checks supported languages
- Windows12.exe (PID: 5072)
- TextInputHost.exe (PID: 896)
- StartMenuExperienceHost.exe (PID: 5324)
- SearchApp.exe (PID: 3900)
UPX packer has been detected
- Windows12.exe (PID: 5072)
Reads mouse settings
- reg.exe (PID: 1164)
- reg.exe (PID: 1312)
- reg.exe (PID: 1324)
- reg.exe (PID: 5064)
Disables trace logs
- netsh.exe (PID: 7364)
- netsh.exe (PID: 7404)
- netsh.exe (PID: 7444)
- netsh.exe (PID: 7484)
- netsh.exe (PID: 7524)
- netsh.exe (PID: 7596)
- netsh.exe (PID: 7604)
- netsh.exe (PID: 7564)
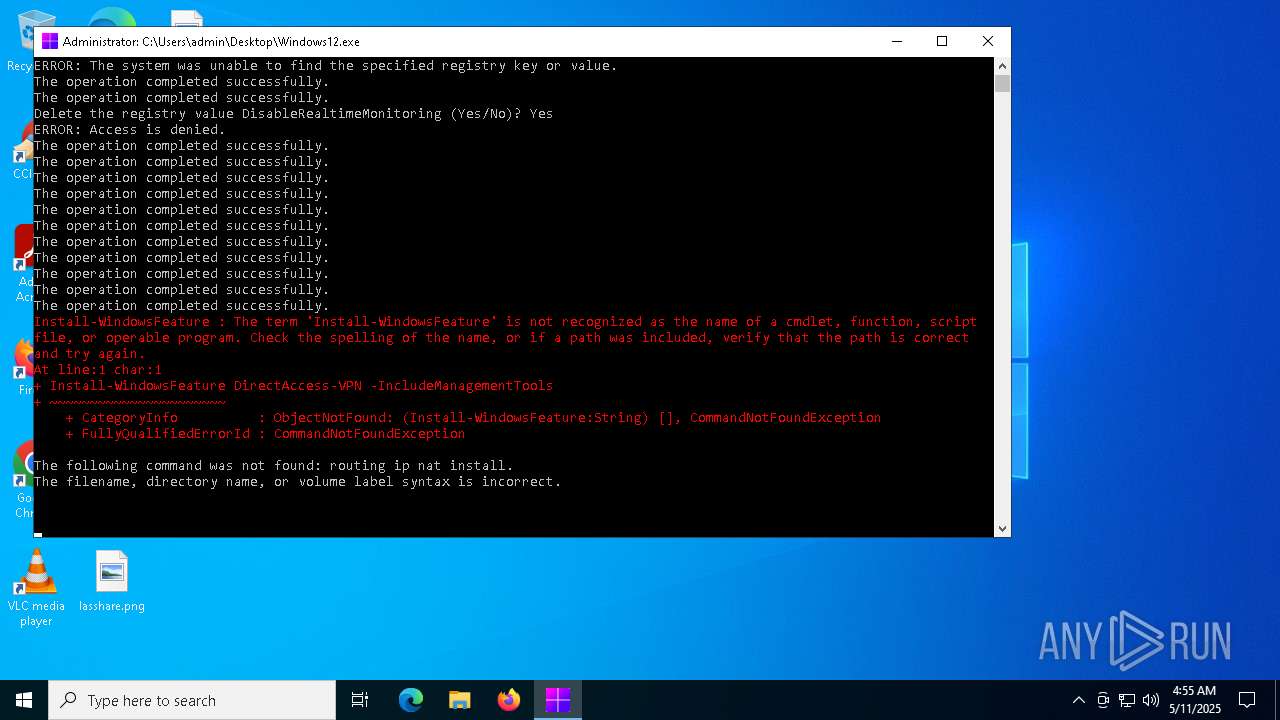
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4976)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7696)
Reads the computer name
- TextInputHost.exe (PID: 896)
- SearchApp.exe (PID: 3900)
- StartMenuExperienceHost.exe (PID: 5324)
Process checks computer location settings
- SearchApp.exe (PID: 3900)
- StartMenuExperienceHost.exe (PID: 5324)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 3900)
Checks proxy server information
- SearchApp.exe (PID: 3900)
- explorer.exe (PID: 7696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 61440 |
| InitializedDataSize: | 180224 |
| UninitializedDataSize: | 270336 |
| EntryPoint: | 0x50710 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
202
Monitored processes
69
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | reg add "HKCU\Control Panel\Desktop" /v "ScreenSaveTimeOut" /t REG_SZ /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 1164 | reg add "HKCU\Control Panel\Mouse" /v "MouseSensitivity" /t REG_SZ /d "40" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | reg add "HKCU\Control Panel\Mouse" /v "MouseSpeed" /t REG_SZ /d "5" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | reg add "HKCU\Control Panel\Mouse" /v "MouseThreshold1" /t REG_SZ /d "10" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | reg add "HKCU\Control Panel\Desktop" /v "ScreenRefreshRate" /t REG_SZ /d "144" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3020 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3300 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4172 | reg add "HKCU\Control Panel\Desktop" /v "DragFullWindows" /t REG_SZ /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 679
Read events
37 408
Write events
247
Delete events
24
Modification events
| (PID) Process: | (7692) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | delete value | Name: | DisableAntiSpyware |
Value: | |||
| (PID) Process: | (8128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\SmartScreen |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (8152) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SmartScreenEnabled |
Value: RequireAdmin | |||
| (PID) Process: | (7224) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | SubmitSamplesConsent |
Value: 2 | |||
| (PID) Process: | (4172) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | DragFullWindows |
Value: 1 | |||
| (PID) Process: | (5404) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | MenuShowDelay |
Value: 0 | |||
| (PID) Process: | (5156) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | ActiveWindowTracking |
Value: 1 | |||
| (PID) Process: | (2088) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | ScreenRefreshRate |
Value: 144 | |||
| (PID) Process: | (1164) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Mouse |
| Operation: | write | Name: | MouseSensitivity |
Value: 40 | |||
| (PID) Process: | (1324) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Mouse |
| Operation: | write | Name: | MouseThreshold1 |
Value: 10 | |||
Executable files
2
Suspicious files
51
Text files
131
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ihhgcecn.x0a.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_n02qugey.wr3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_grwisvzz.05y.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:A6F4468DB0FEF2C05CAF93F8DED52789 | SHA256:71424CED90589449B304953F7828F00622DA95EB1B5B7A4921825469B260DEC1 | |||
| 3900 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:B4DF24E28A75D8CE1ABC7B52FCA881BD | SHA256:8ADABFABD394F0A8240DB9C4FE2D23D3DE932E2603CDE0236CB667BA9BEACDED | |||
| 5072 | Windows12.exe | C:\Users\admin\AppData\Local\Temp\B817.tmp\B818.tmp\B819.bat | text | |
MD5:9BF0565C42F9C45A219EB46D40388D1D | SHA256:04CE073EC6E5DBDB45F39EA20816BB3CE6EFCC9ADE04F1569DF92B18FC48DB9D | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1eef1oun.ya2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3900 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:E73AB8DAB300130CDAD89A4EF8D8A2D2 | SHA256:4C18266A57918C4BC5E9250B81C1596F0367F6E99EE86CA78EE9D8B98D0D5E67 | |||
| 3900 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:E0DD745BCF597D40116DC0D32B6DCC29 | SHA256:23205CBBAAAE8DBDEA2FC67B41835CCB26151CC6B1B494C1FE7ECD007B443937 | |||
| 5892 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:101732AE8879EF766E33560EC23D9C03 | SHA256:0039EBF5450E781D69FD6843AE1BA3149CA1D5CAC886A24320C4AD025827F4D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3900 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3900 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6100 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6100 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |