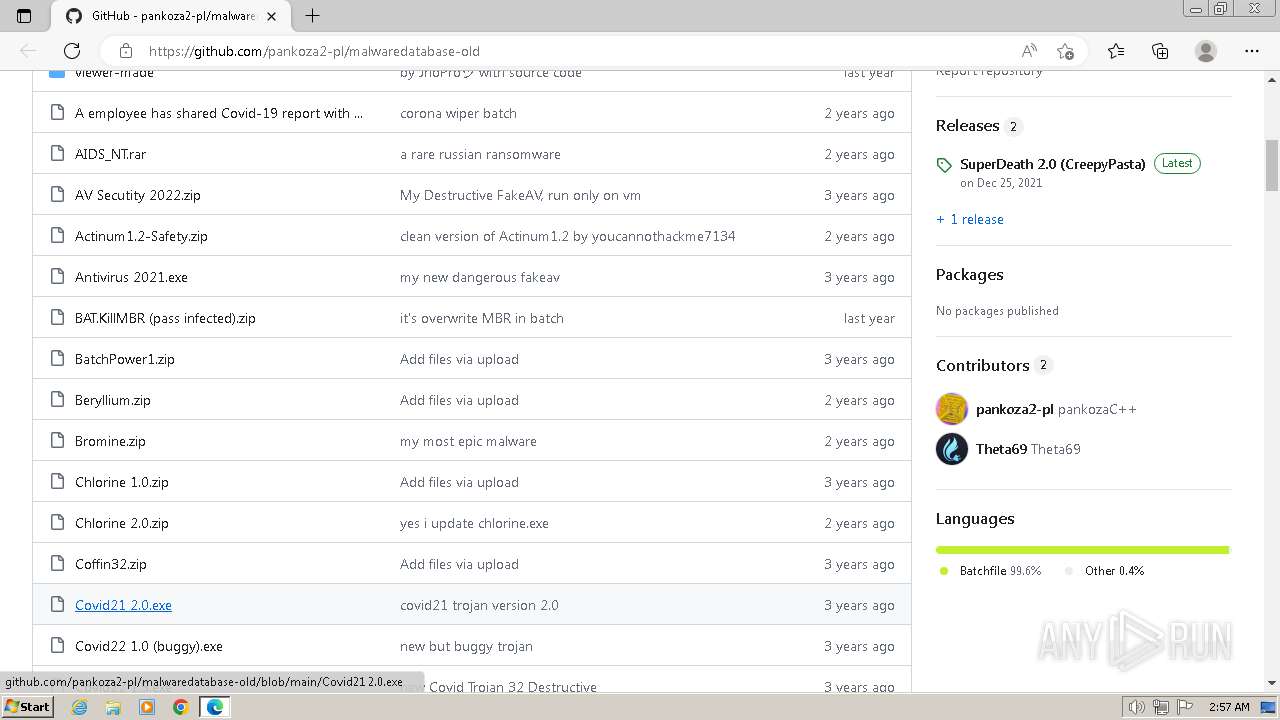
| URL: | https://github.com/pankoza2-pl/malwaredatabase-old |
| Full analysis: | https://app.any.run/tasks/54ee757f-c59d-4de3-83ac-cdae7972d69b |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2024, 01:57:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 89EF704FE9FCD9DEC53369122D727921 |
| SHA1: | D7A8E3B1E57F5AFCD06E7C58F7FAFC0D303E0F52 |
| SHA256: | F1917B1442611BC18DF396D71113C5BA1D83BB84899D5071668670CB6F21C758 |
| SSDEEP: | 3:N8tEdlELlf3VJIcKR0y:2uoLFlSxb |
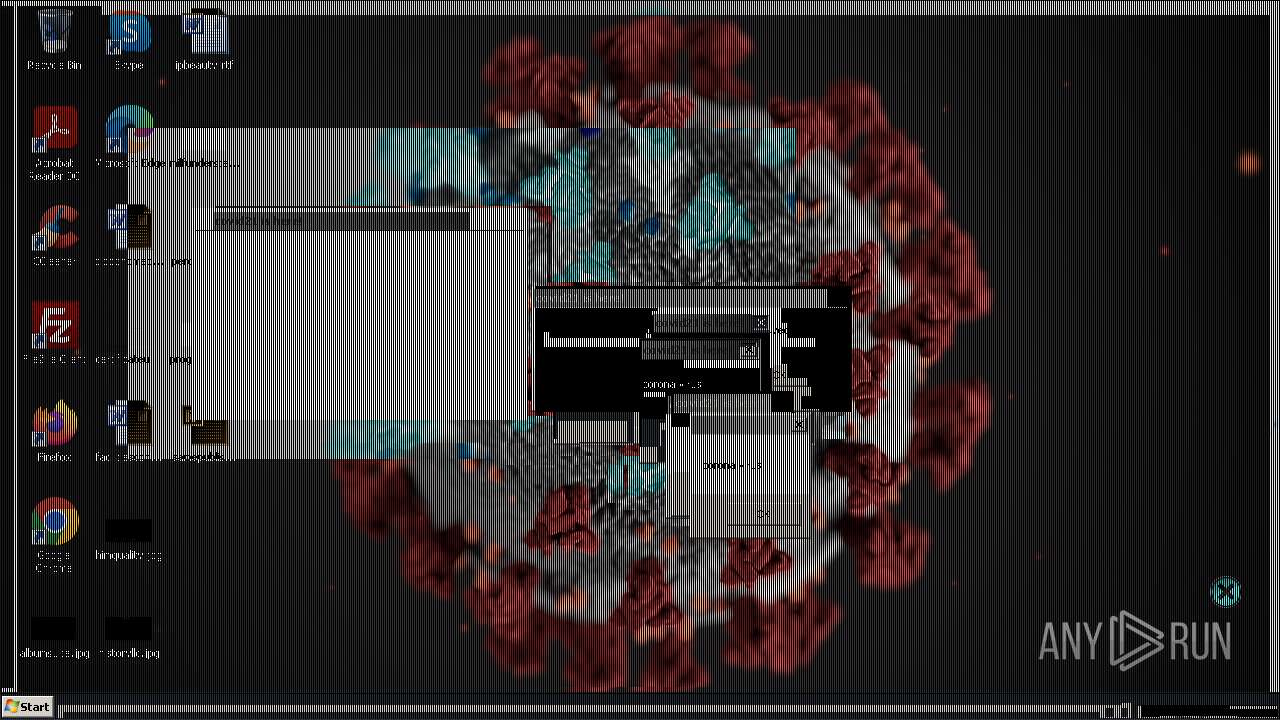
MALICIOUS
Drops the executable file immediately after the start
- Covid21 2.0.exe (PID: 3792)
- Covid21 2.0.exe (PID: 348)
- cmd.exe (PID: 832)
Disables Windows Defender
- reg.exe (PID: 1392)
Changes the autorun value in the registry
- PayloadMBR.exe (PID: 2736)
SUSPICIOUS
Reads the Internet Settings
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
- cmd.exe (PID: 832)
Executable content was dropped or overwritten
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
- cmd.exe (PID: 832)
Executing commands from a ".bat" file
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
- cmd.exe (PID: 832)
Starts CMD.EXE for commands execution
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
- cmd.exe (PID: 832)
Reads security settings of Internet Explorer
- Covid21 2.0.exe (PID: 3792)
- Covid21 2.0.exe (PID: 348)
The process executes VB scripts
- cmd.exe (PID: 3784)
- cmd.exe (PID: 832)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 832)
The executable file from the user directory is run by the CMD process
- CLWCP.exe (PID: 2708)
- inv.exe (PID: 2672)
- z.exe (PID: 3568)
- icons.exe (PID: 1680)
- PayloadMBR.exe (PID: 2736)
- screenscrew.exe (PID: 660)
Application launched itself
- cmd.exe (PID: 832)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 832)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 832)
INFO
Application launched itself
- msedge.exe (PID: 3392)
Checks supported languages
- Covid21 2.0.exe (PID: 3792)
- Covid21 2.0.exe (PID: 348)
- Corona.exe (PID: 2268)
- inv.exe (PID: 2672)
- icons.exe (PID: 1680)
- CLWCP.exe (PID: 2708)
- screenscrew.exe (PID: 660)
- PayloadMBR.exe (PID: 2736)
- z.exe (PID: 3568)
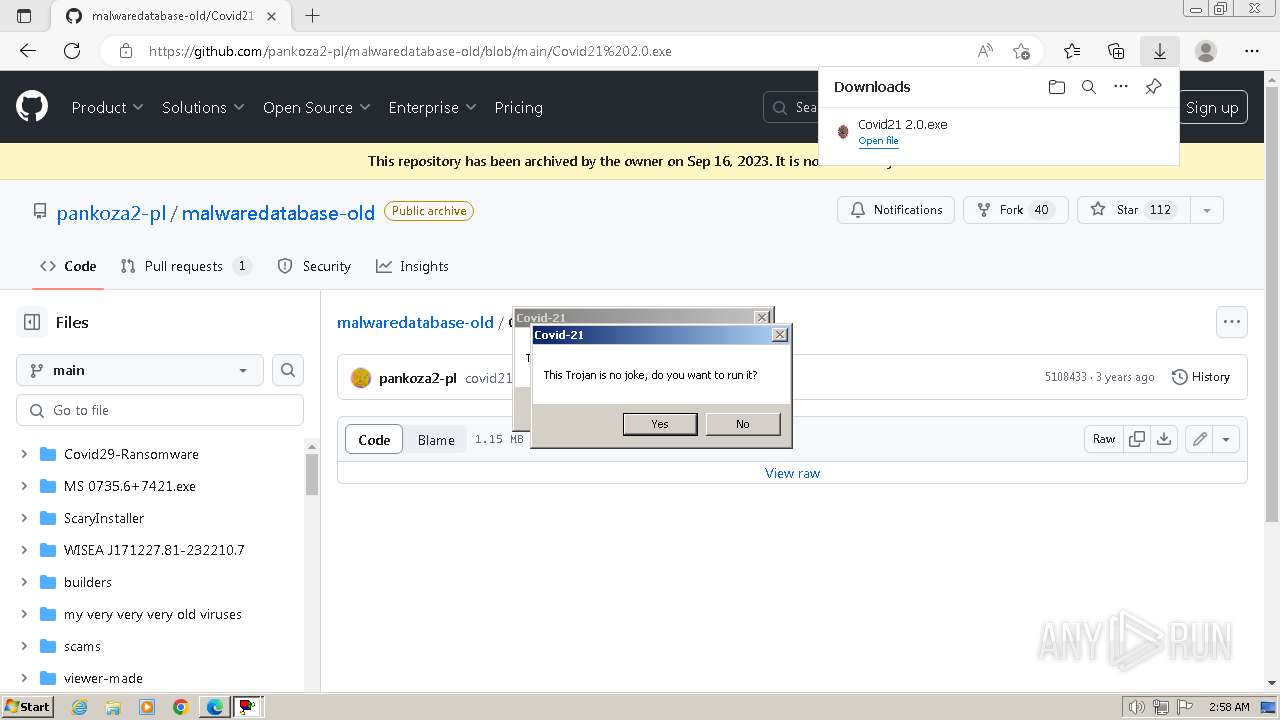
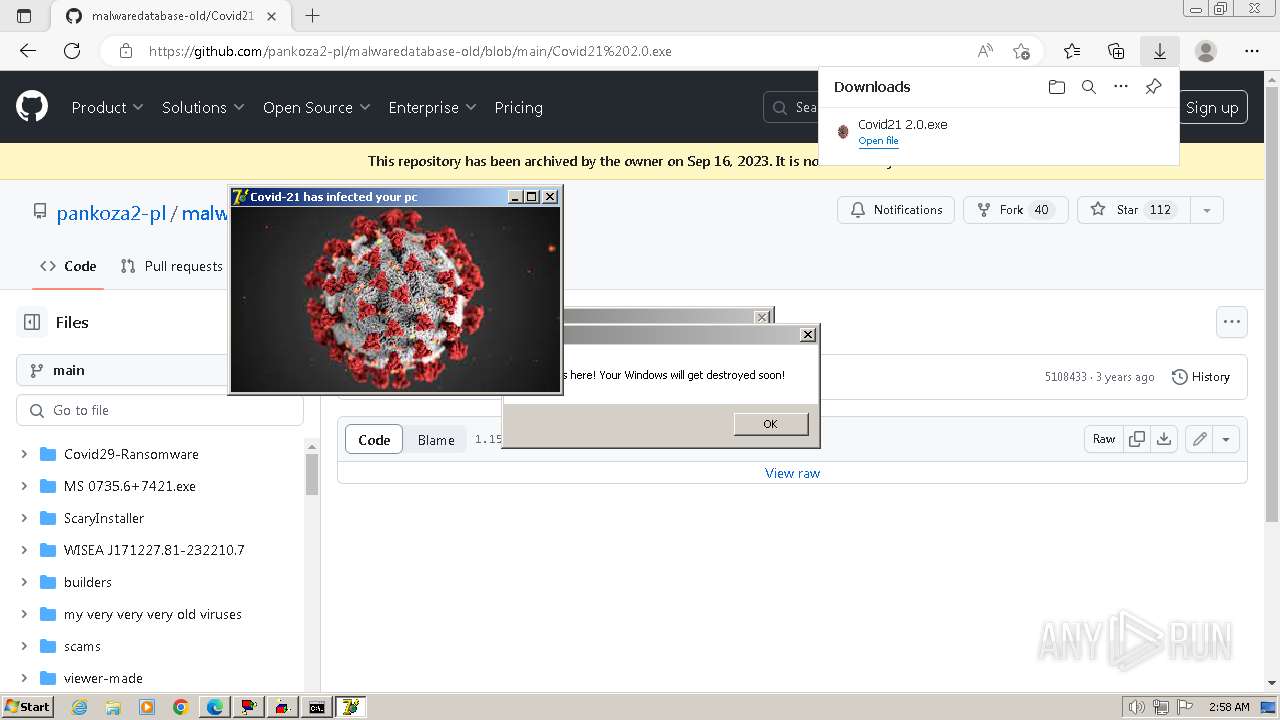
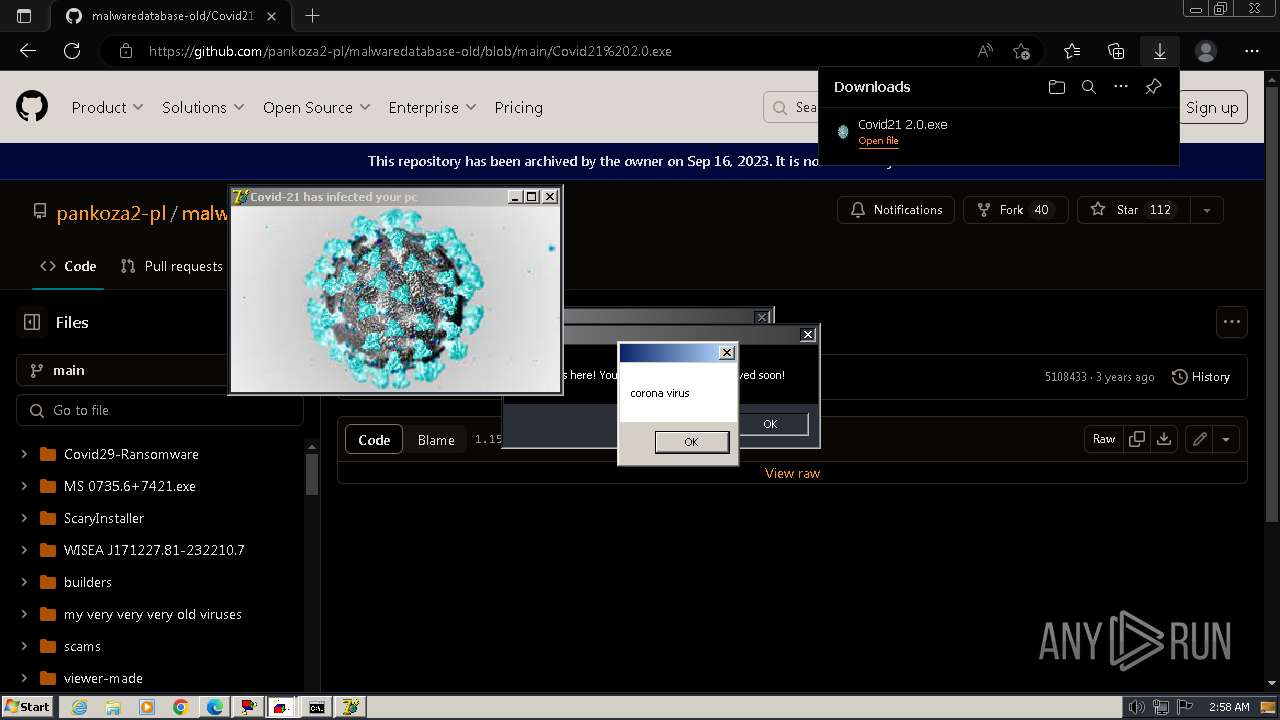
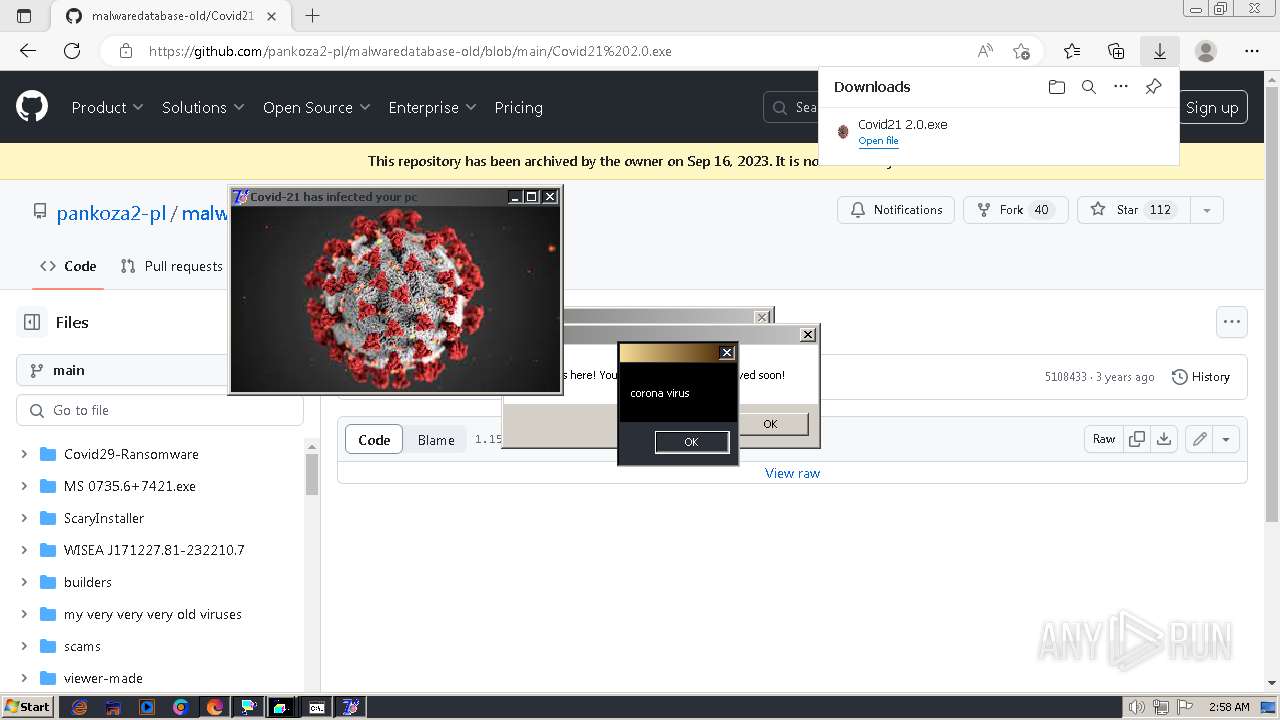
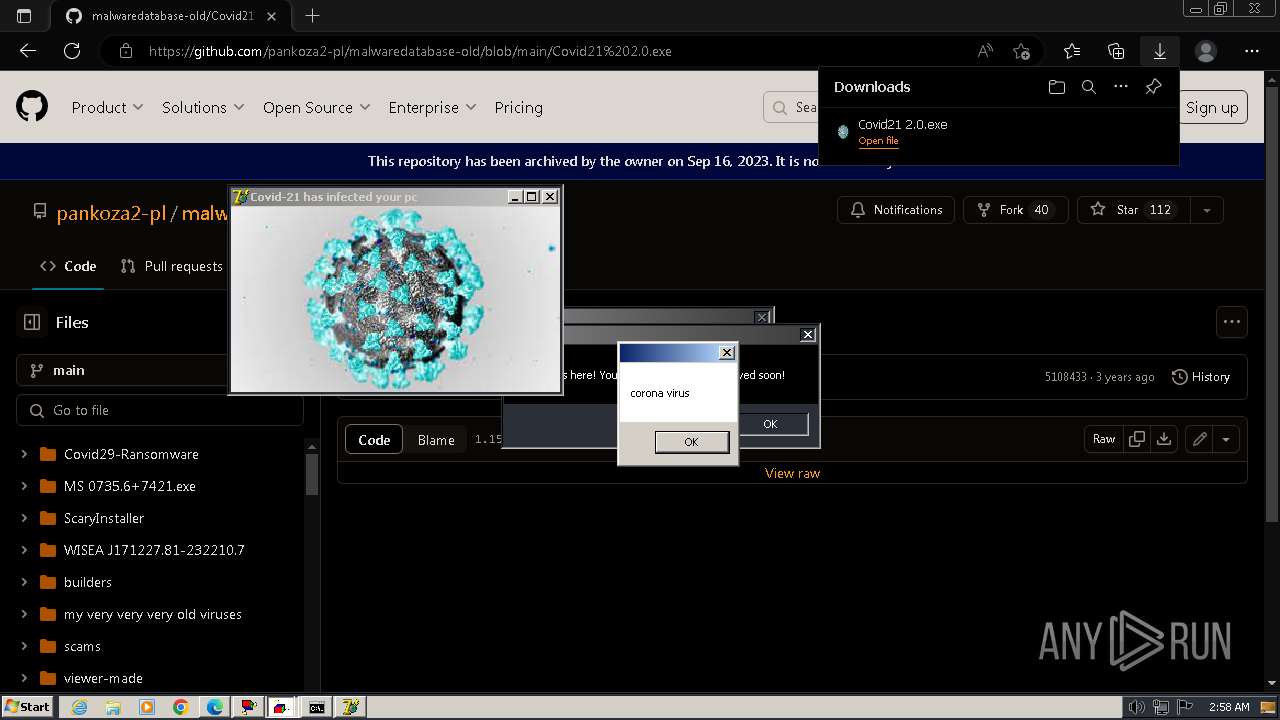
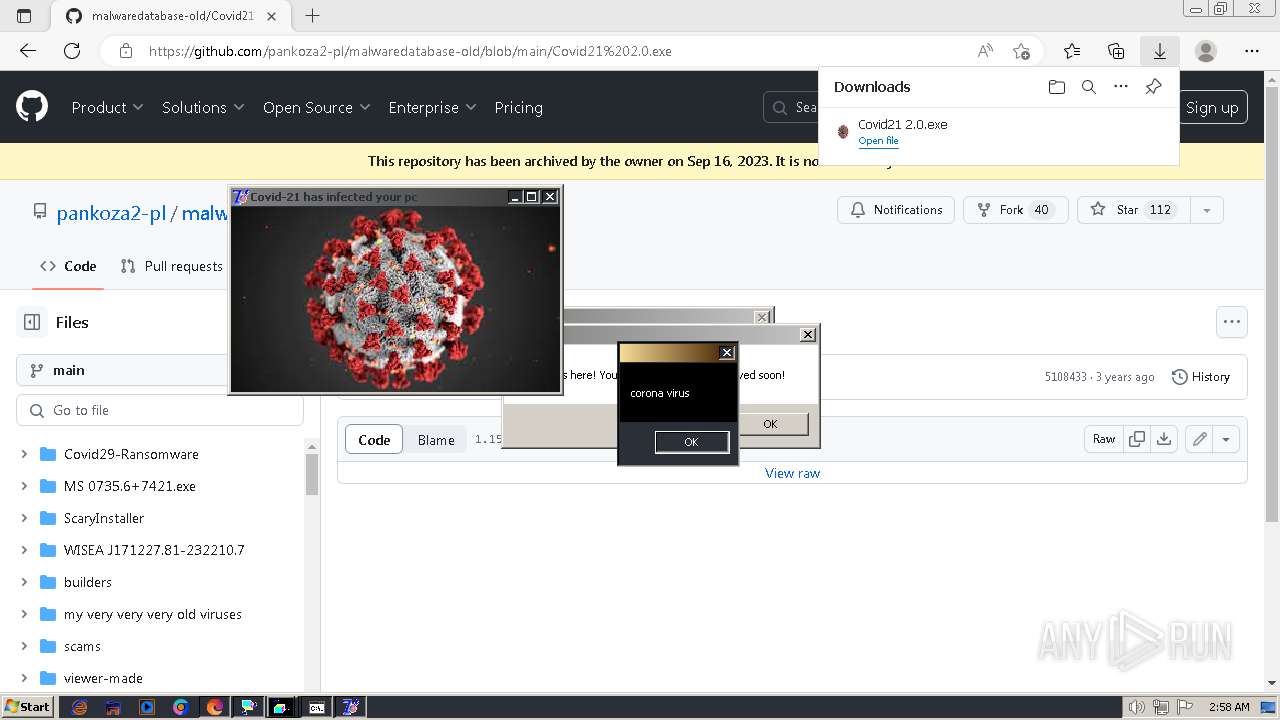
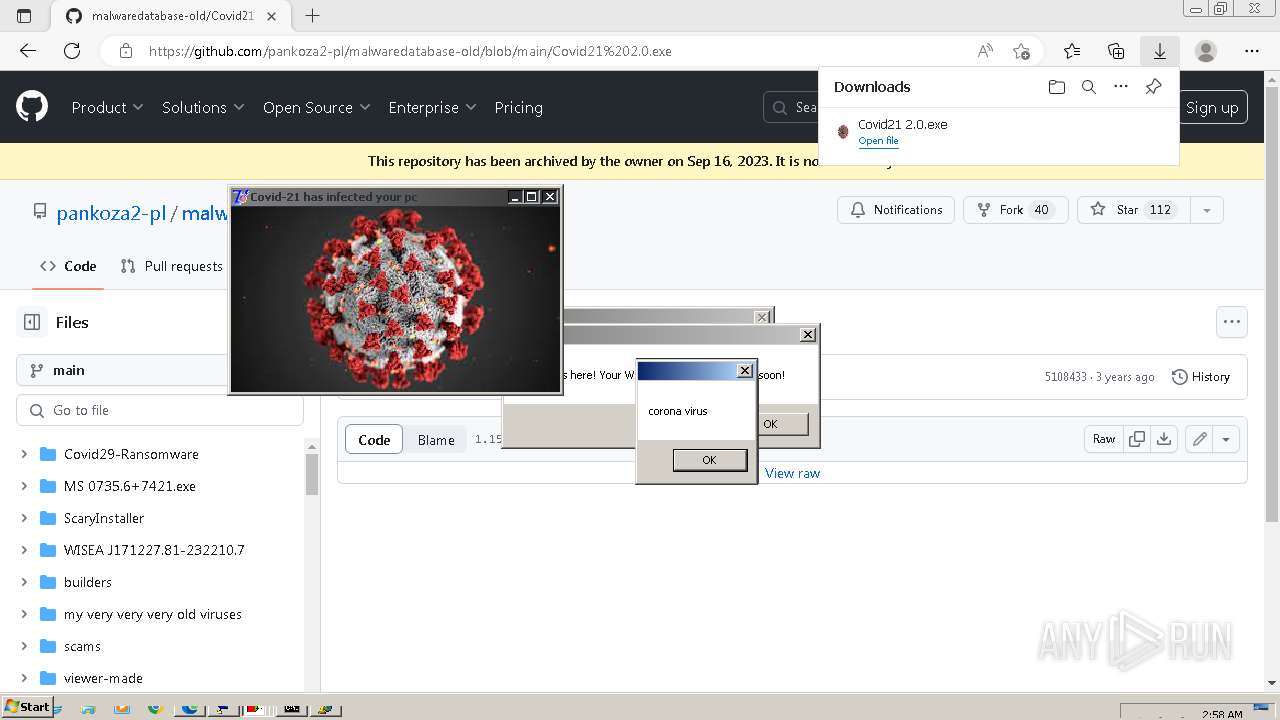
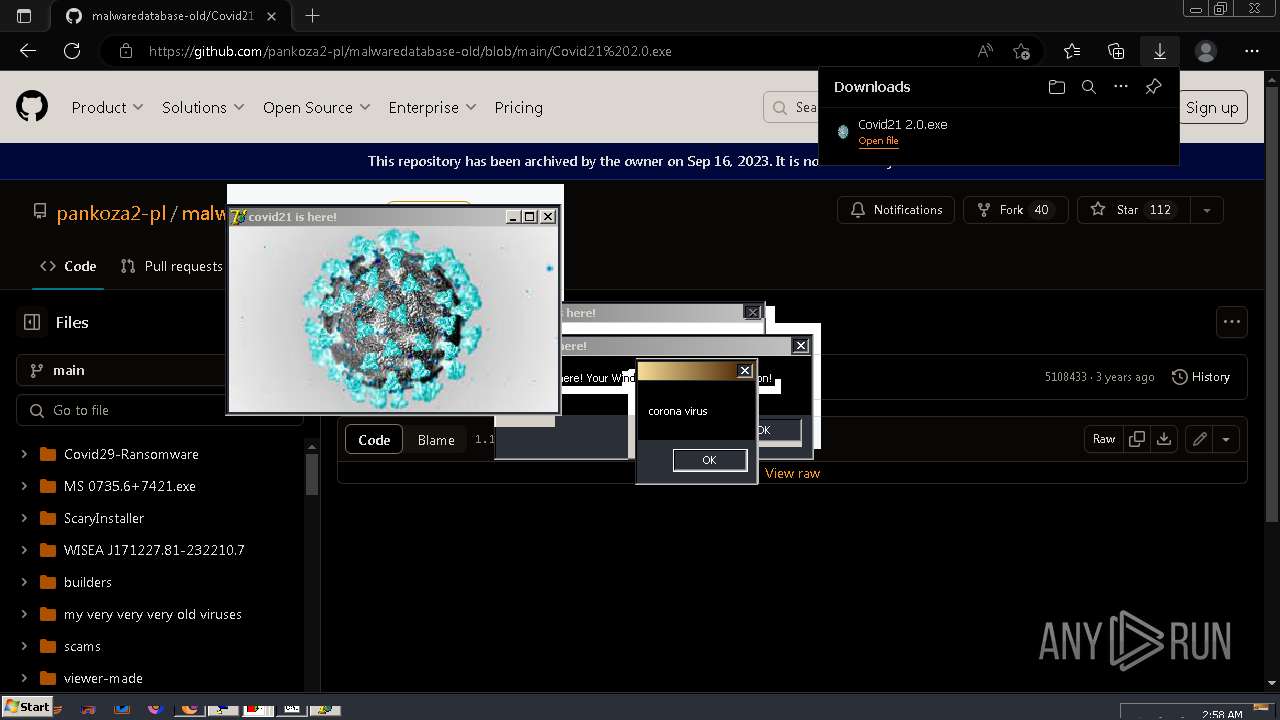
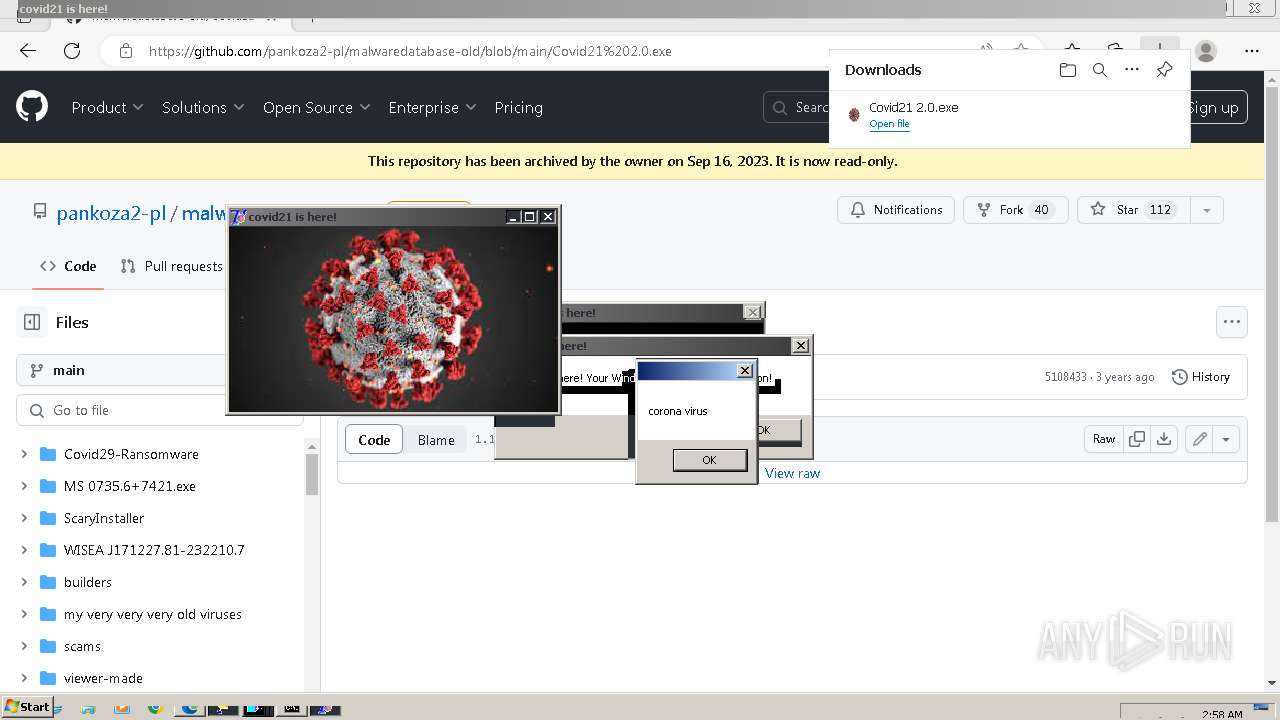
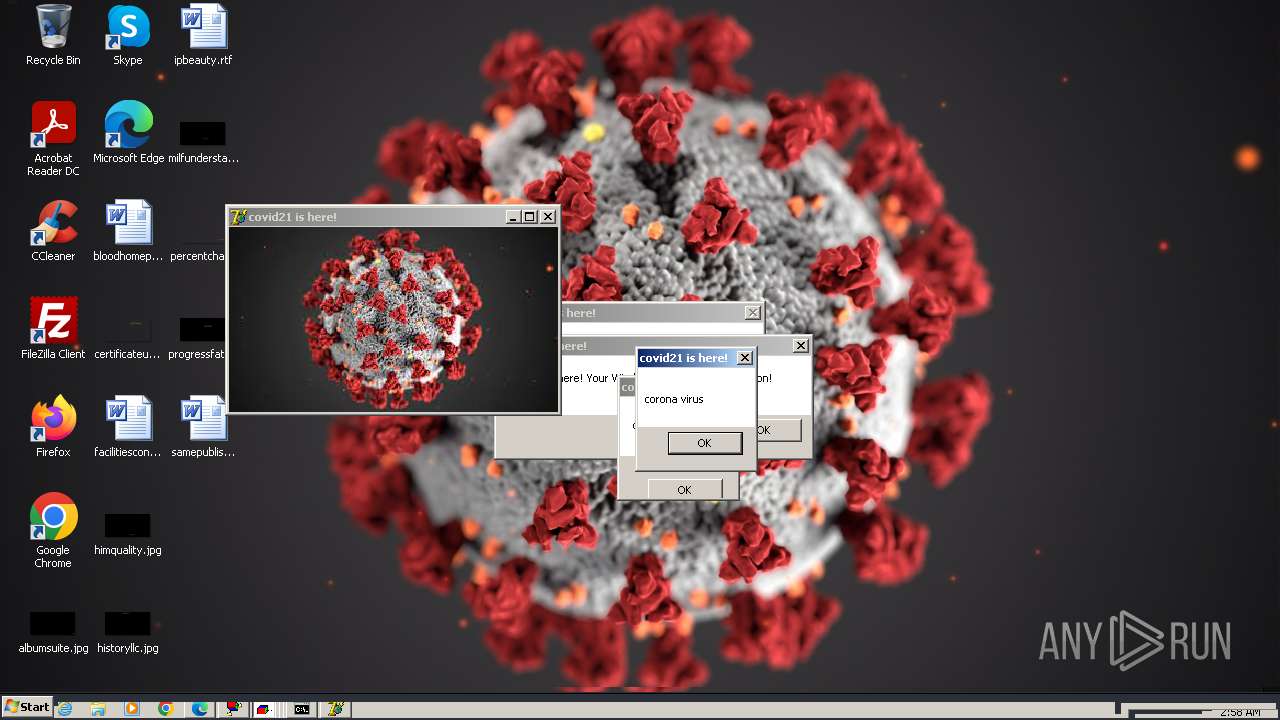
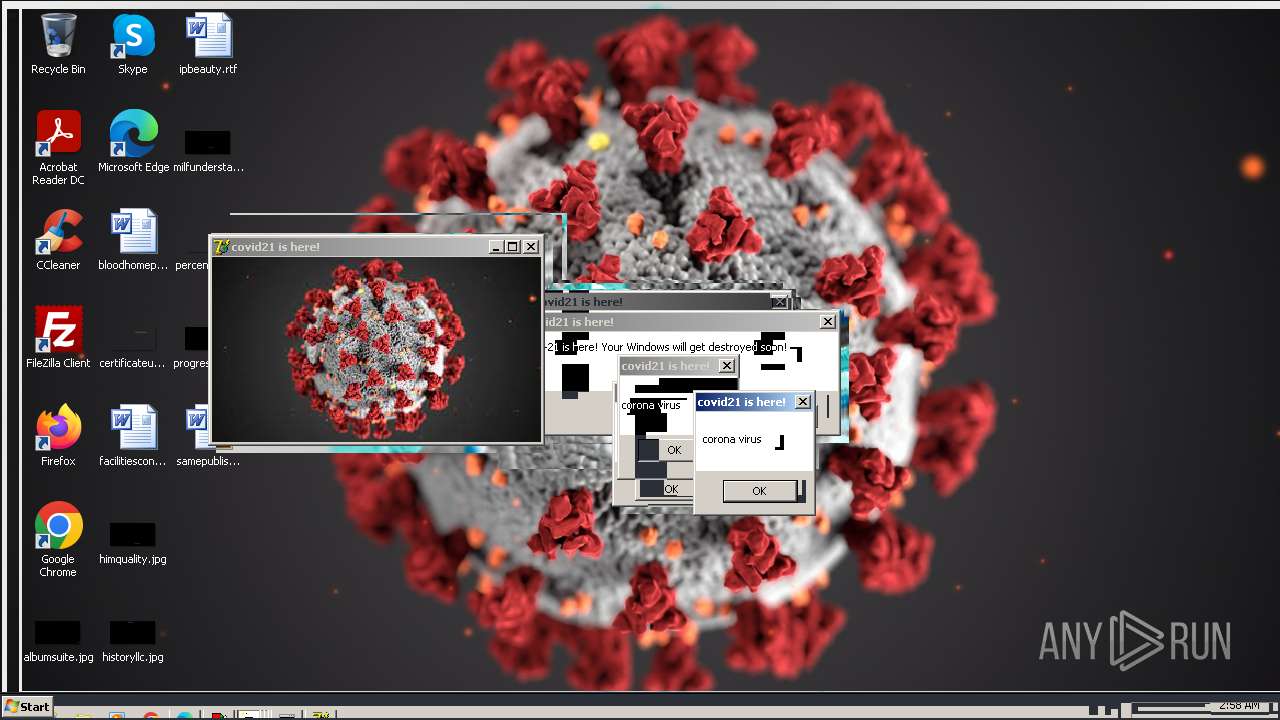
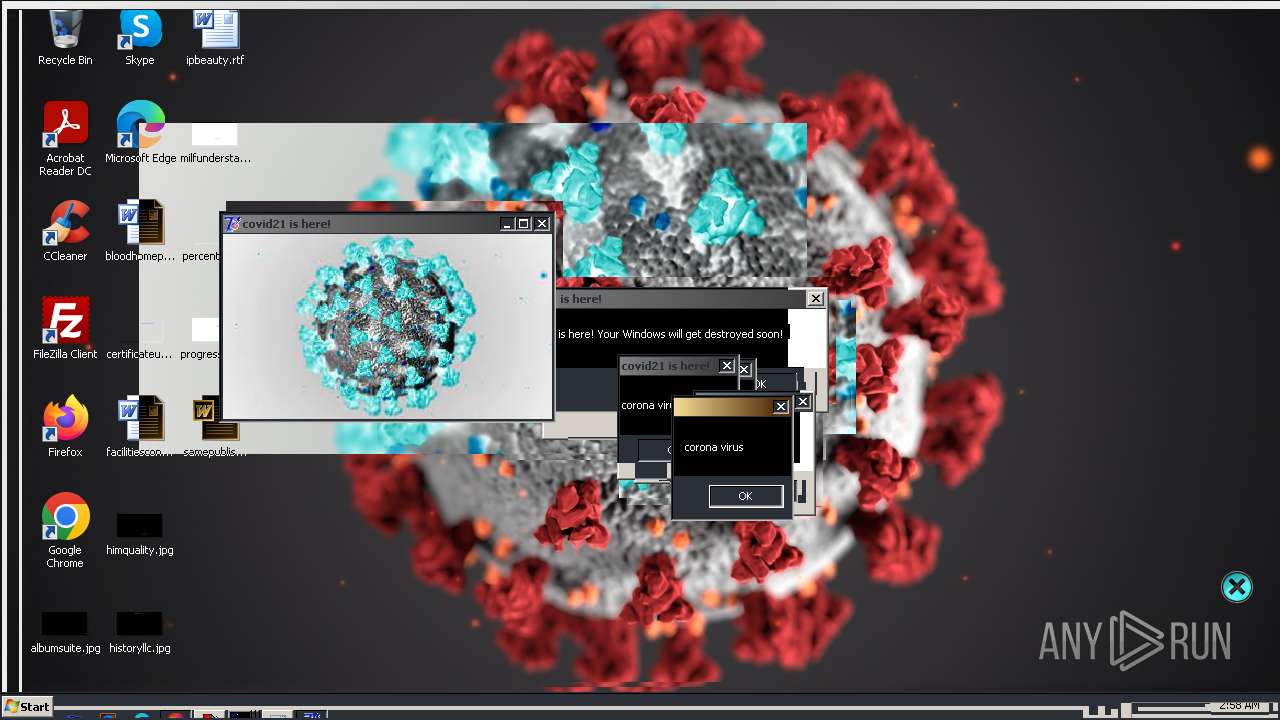
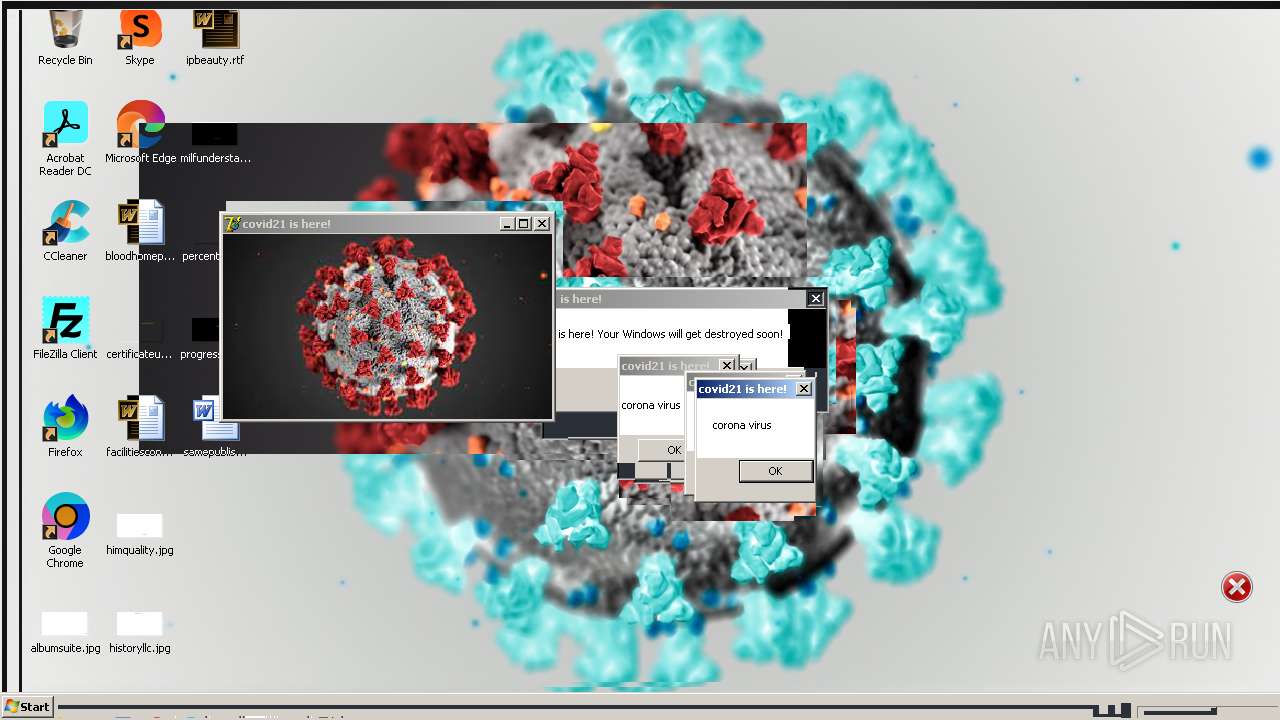
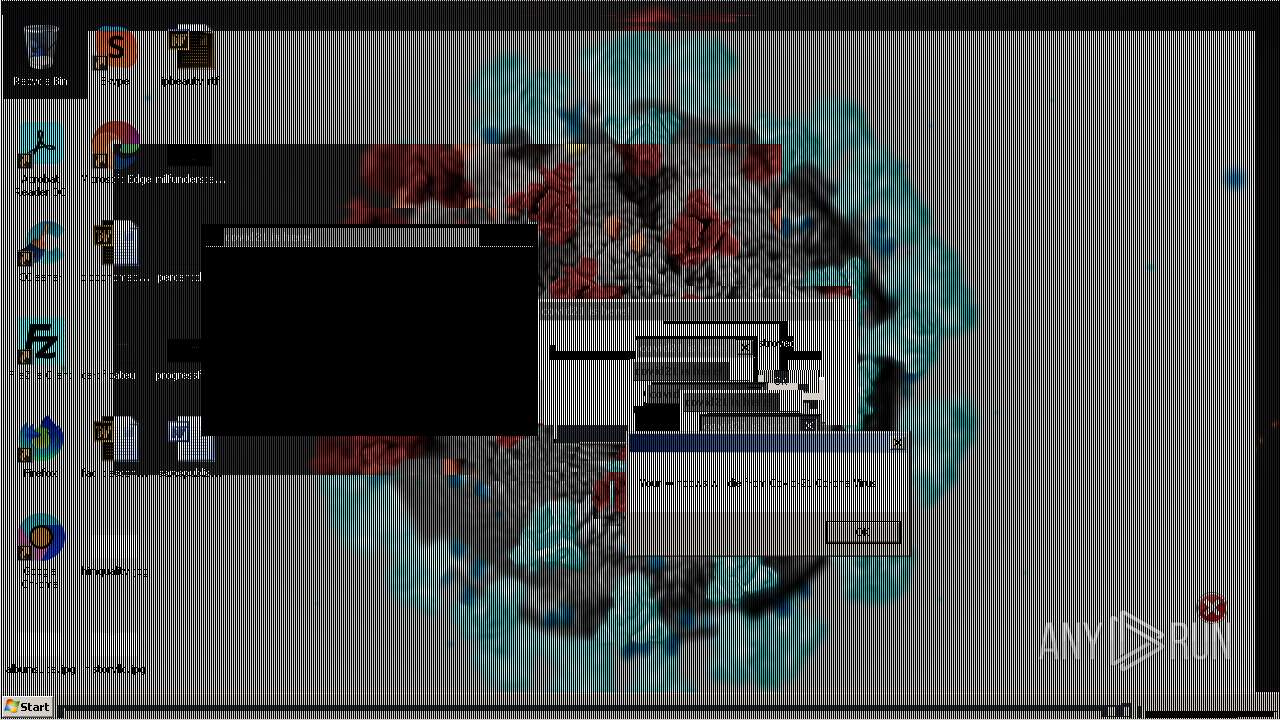
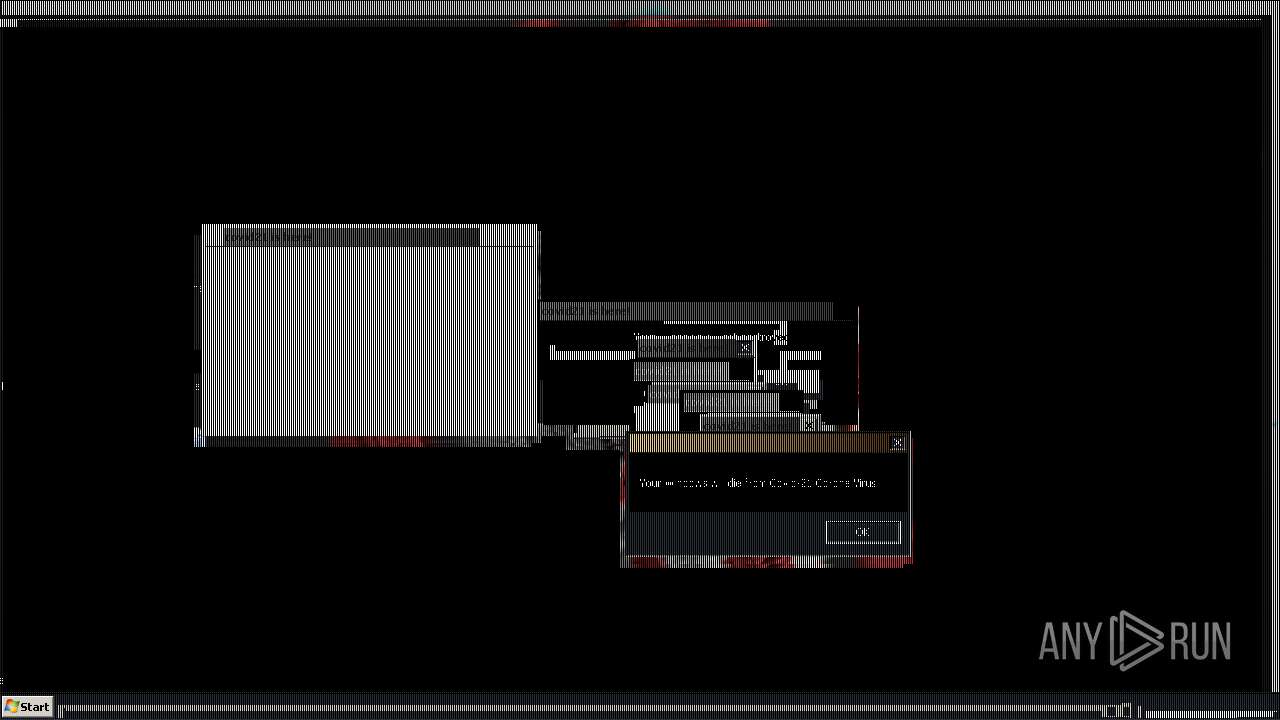
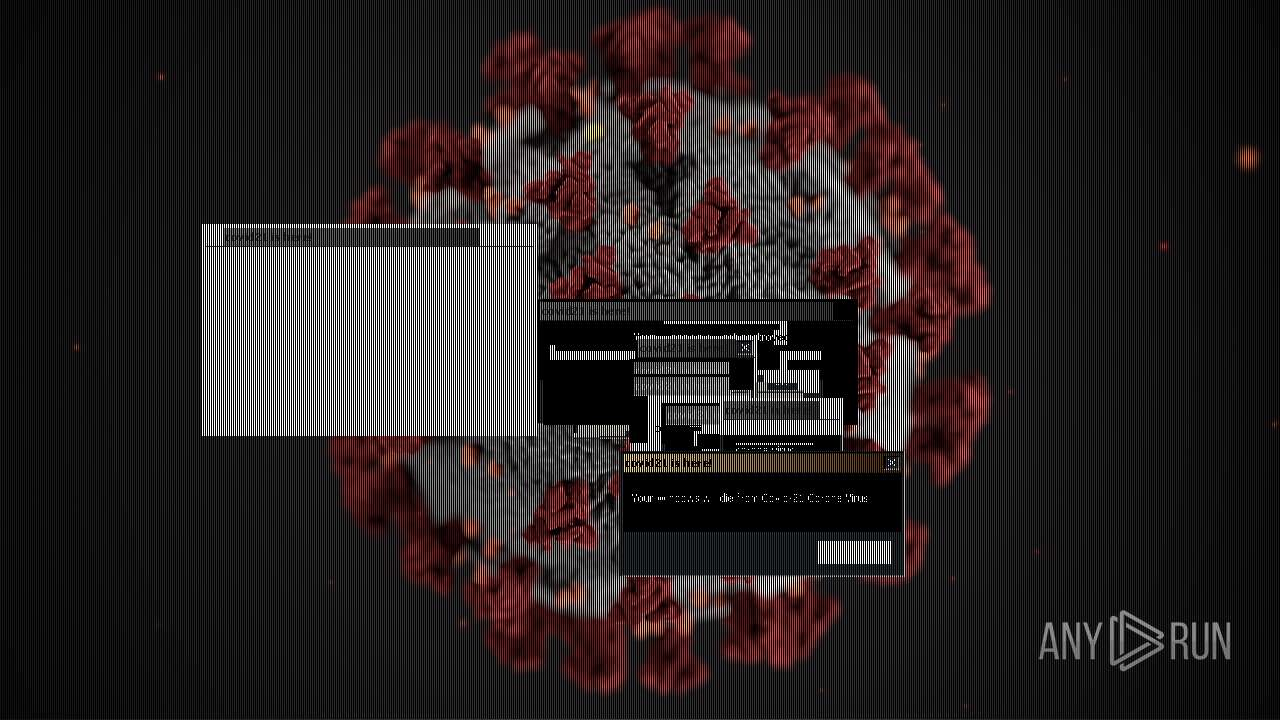
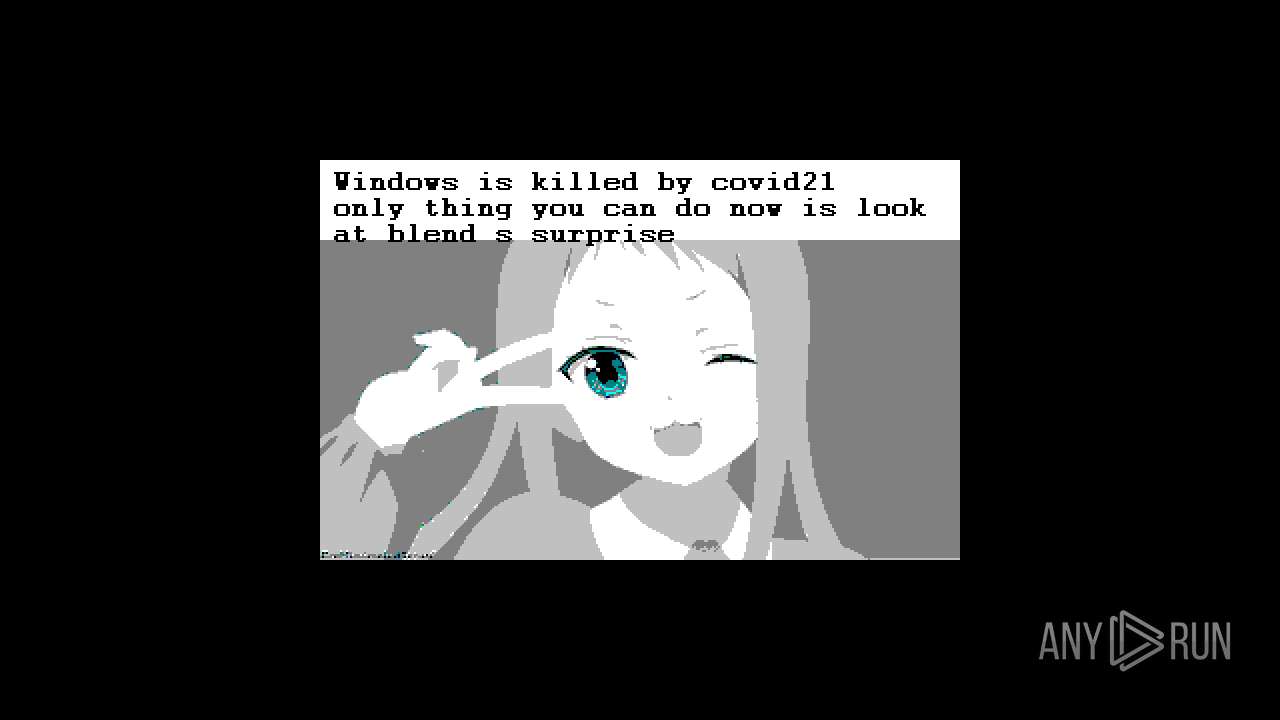
Drops a (possible) Coronavirus decoy
- Covid21 2.0.exe (PID: 348)
- msedge.exe (PID: 3392)
- Covid21 2.0.exe (PID: 3792)
- cmd.exe (PID: 832)
The process uses the downloaded file
- msedge.exe (PID: 3392)
- msedge.exe (PID: 3140)
Executable content was dropped or overwritten
- msedge.exe (PID: 3392)
- msedge.exe (PID: 2940)
Drops the executable file immediately after the start
- msedge.exe (PID: 3392)
- msedge.exe (PID: 2940)
Create files in a temporary directory
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
Reads the computer name
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2828)
- cscript.exe (PID: 2412)
UPX packer has been detected
- Covid21 2.0.exe (PID: 3792)
- Covid21 2.0.exe (PID: 348)
Aspack has been detected
- Covid21 2.0.exe (PID: 348)
- Covid21 2.0.exe (PID: 3792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
100
Monitored processes
54
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | timeout 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | "C:\Users\admin\Downloads\Covid21 2.0.exe" | C:\Users\admin\Downloads\Covid21 2.0.exe | msedge.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 660 | screenscrew.exe | C:\Users\admin\AppData\Local\Temp\3B99.tmp\screenscrew.exe | — | cmd.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: HIGH Description: Screws with your screen :) Version: 1.0.0.0 Modules
| |||||||||||||||
| 724 | bcdedit /delete {current} | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 832 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\3B99.tmp\Covid21.bat" " | C:\Windows\System32\cmd.exe | Covid21 2.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1164 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\3B99.tmp\y.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1196 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\3B99.tmp\t.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1324 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\3B99.tmp\y.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1392 | Reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\3B99.tmp\y.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
27 928
Read events
27 746
Write events
140
Delete events
42
Modification events
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: AA3FB6451B7A2F00 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
21
Suspicious files
167
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF4e4de.TMP | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF4e4ee.TMP | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF4e55b.TMP | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3700 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Platform Notifications\LOG.old~RF4e636.TMP | text | |
MD5:93B76D13B273BF917AB2B451BC904403 | SHA256:4080C22F68EC4545FC075C08CD3C8AEF8946444329C307F7BA54C134F75E901A | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF4e4de.TMP | text | |
MD5:646FEFDB4D82709E3056F5C71953783C | SHA256:7B83D8689750F64D31016F1E8AC2A4EB9D7DB406E4C9C66211D4ED17DEBFEAD9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
33
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.72.36.98:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.22.57.219:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3392 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2940 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
2940 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2940 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2940 | msedge.exe | 185.199.110.154:443 | github.githubassets.com | FASTLY | US | unknown |
2940 | msedge.exe | 185.199.108.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
collector.github.com |
| whitelisted |
api.github.com |
| whitelisted |