| URL: | https://github.com/pankoza2-pl/malwaredatabase-old |
| Full analysis: | https://app.any.run/tasks/081d9a1c-3ce7-4dfe-ac56-d4dccd5c8e47 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2024, 21:57:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 89EF704FE9FCD9DEC53369122D727921 |
| SHA1: | D7A8E3B1E57F5AFCD06E7C58F7FAFC0D303E0F52 |
| SHA256: | F1917B1442611BC18DF396D71113C5BA1D83BB84899D5071668670CB6F21C758 |
| SSDEEP: | 3:N8tEdlELlf3VJIcKR0y:2uoLFlSxb |
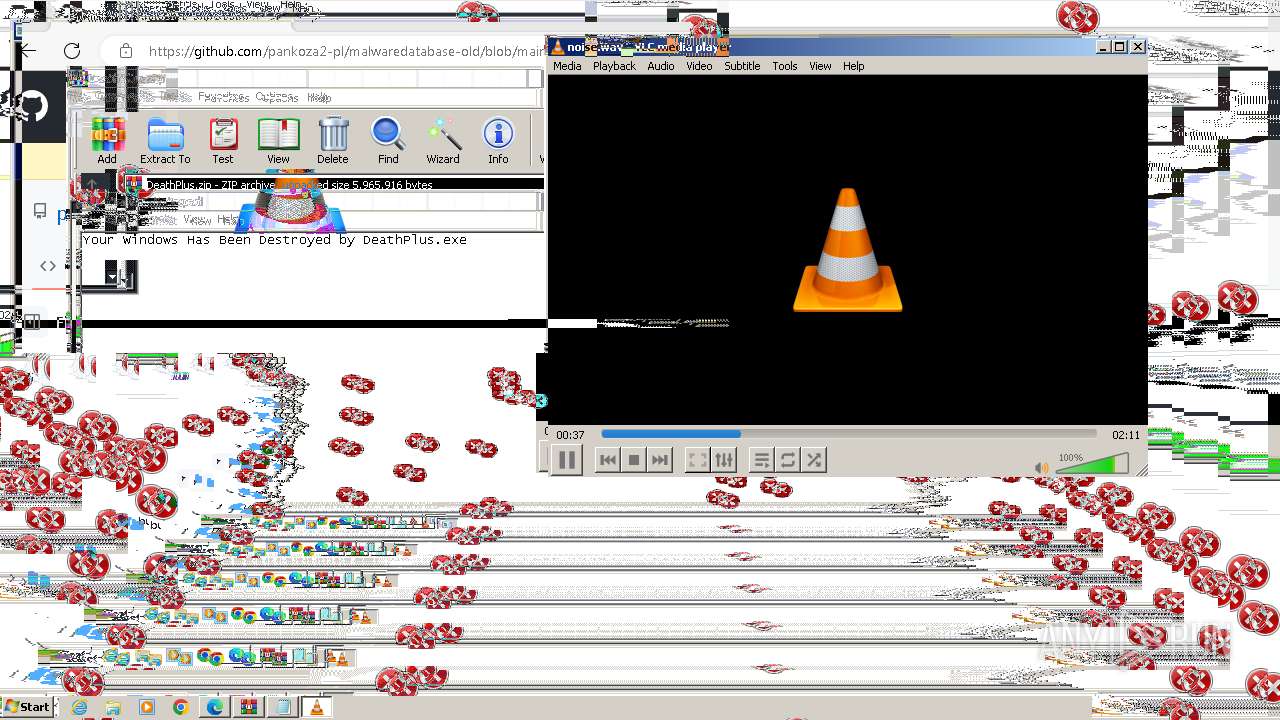
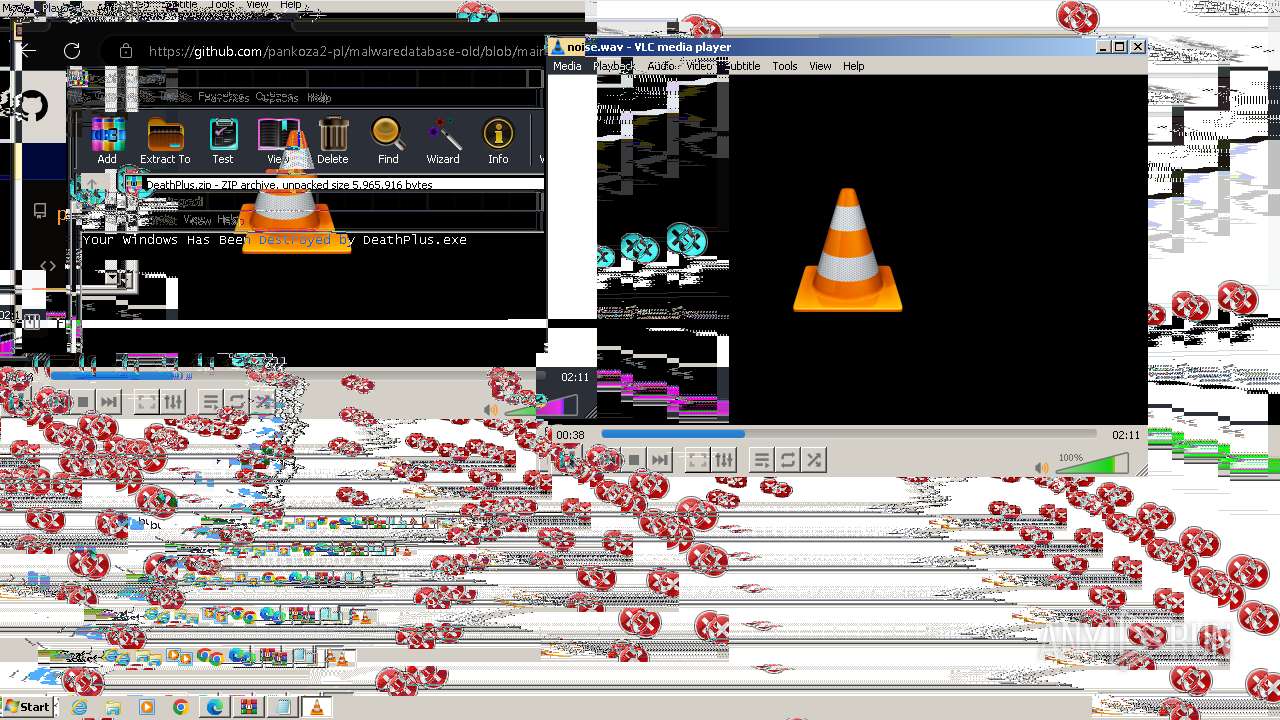
MALICIOUS
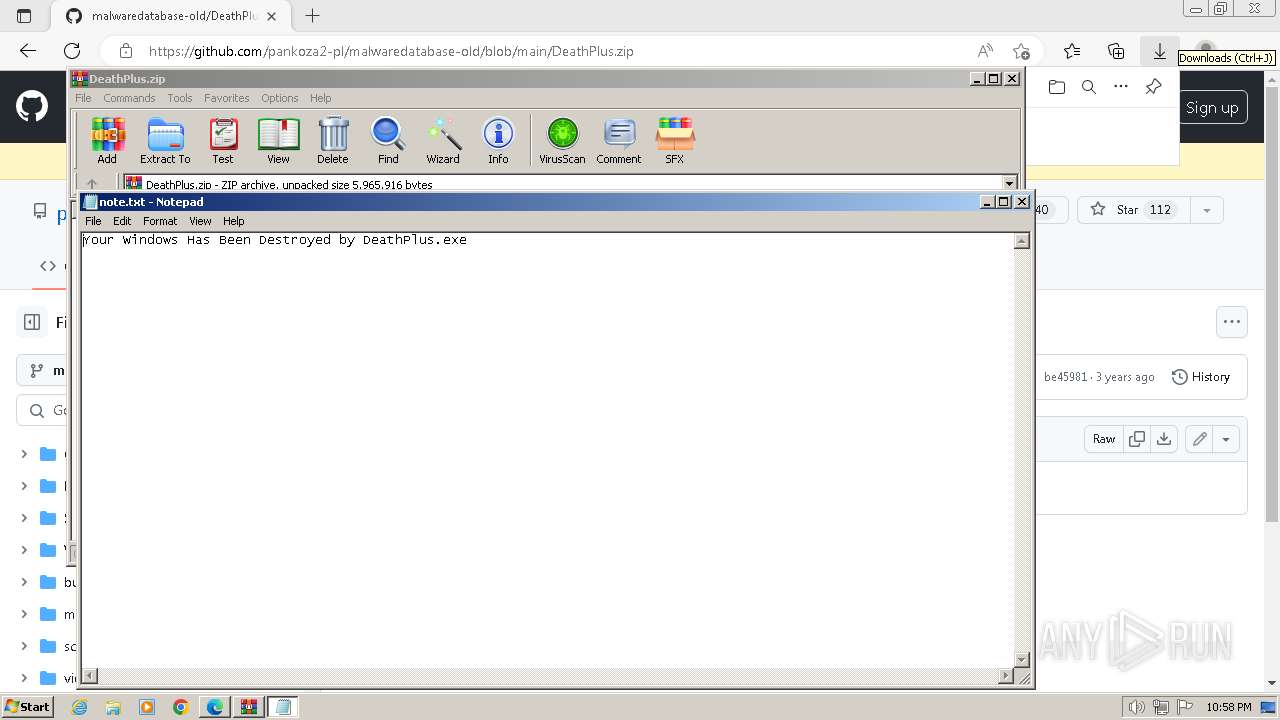
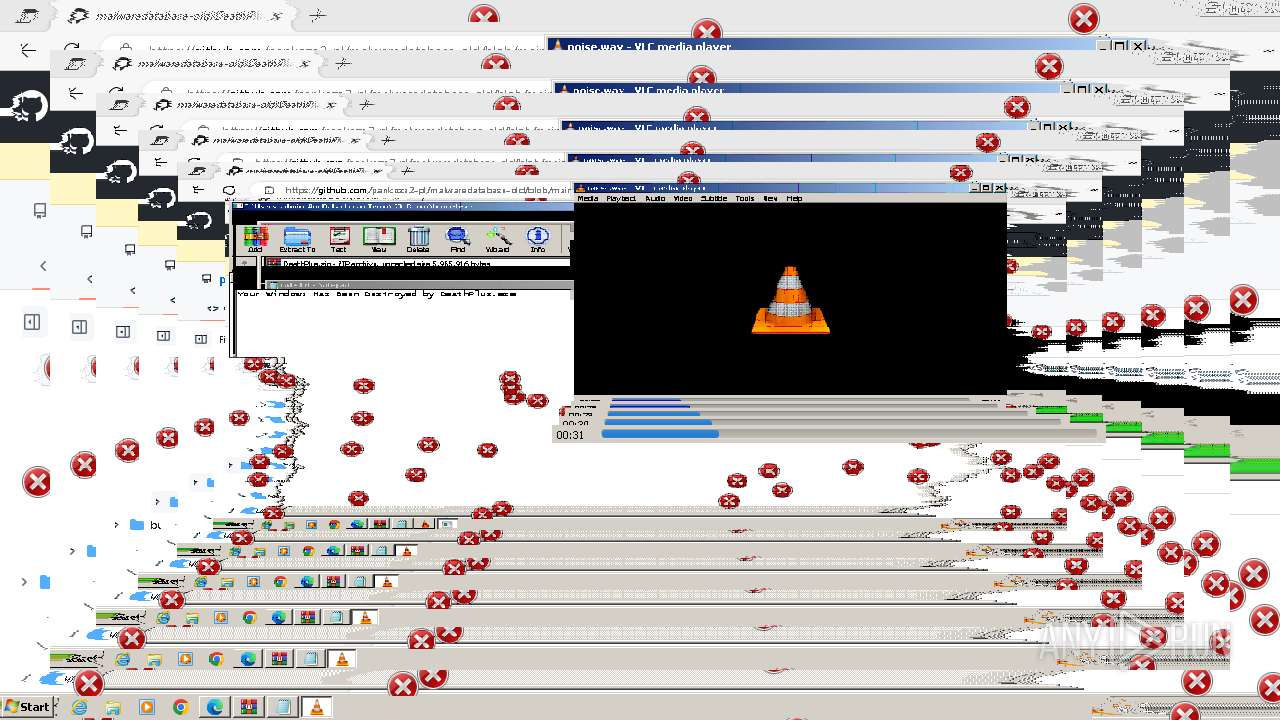
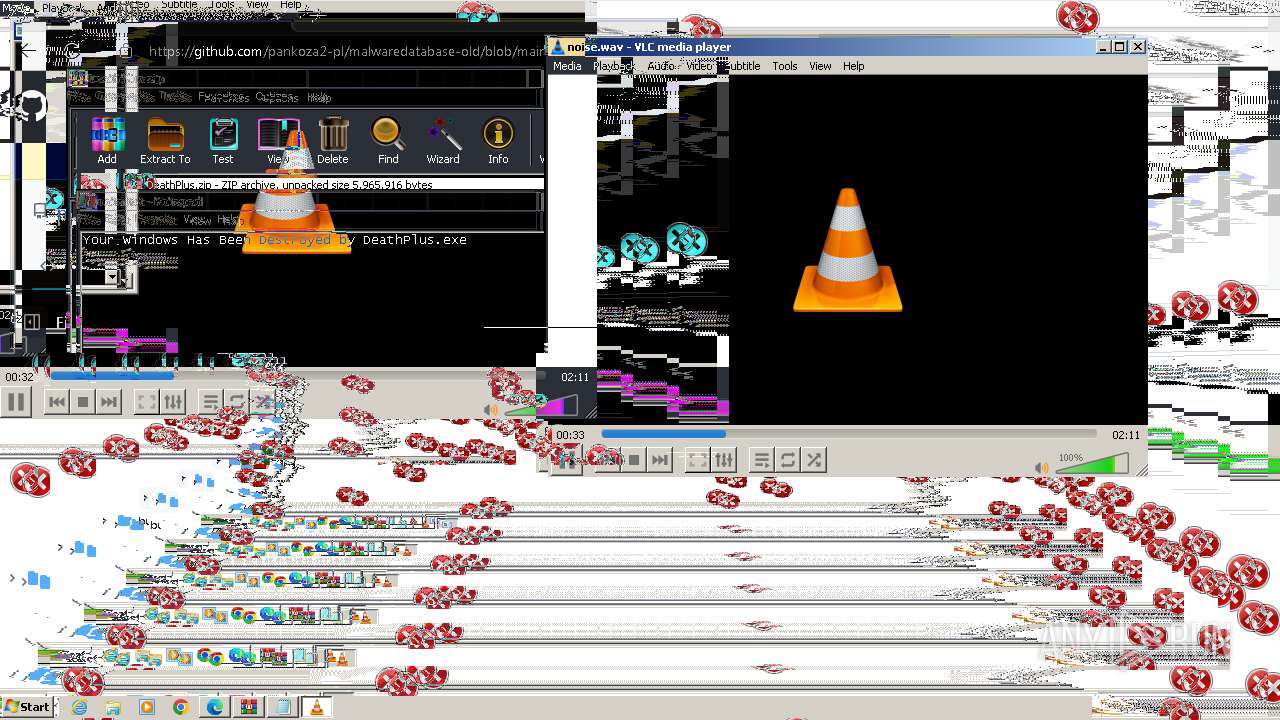
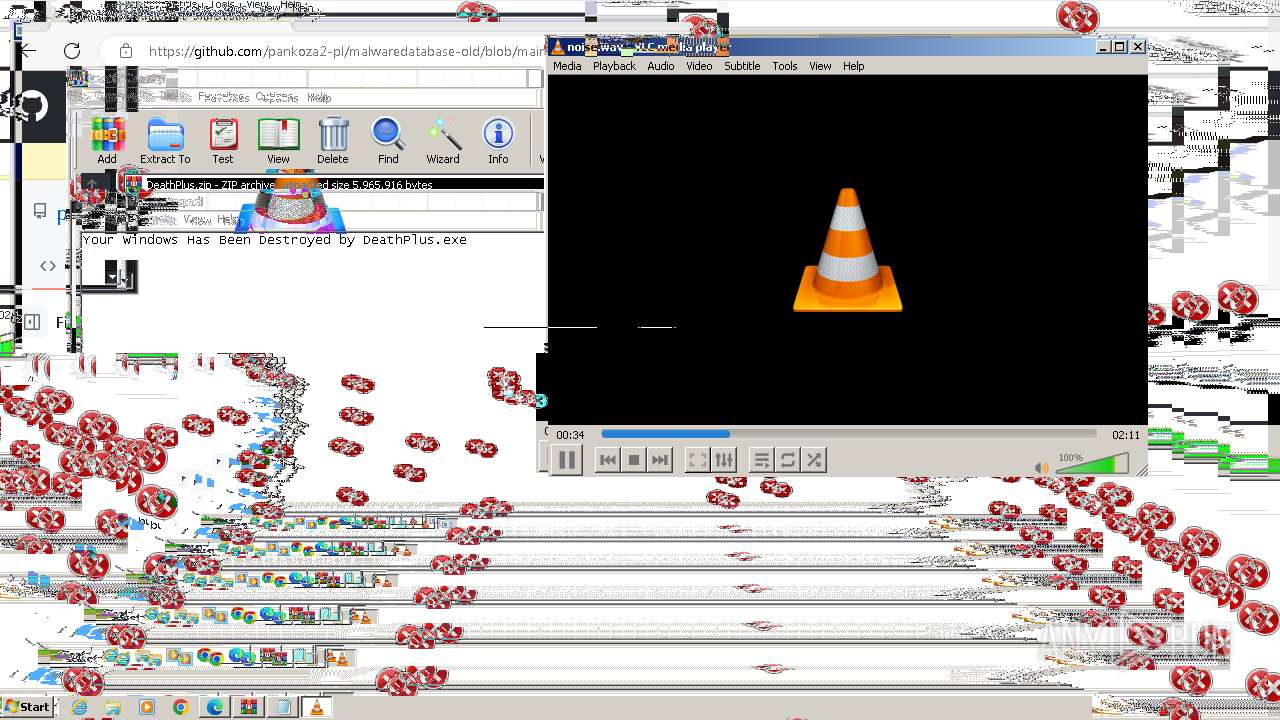
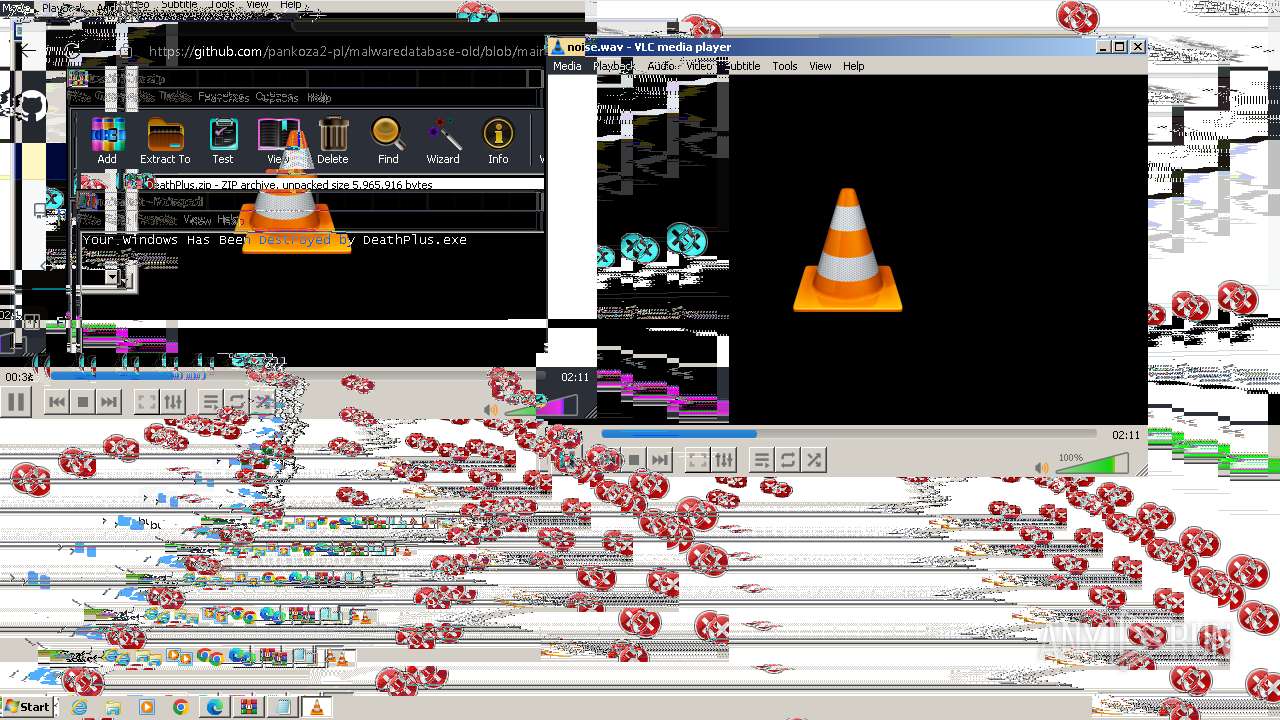
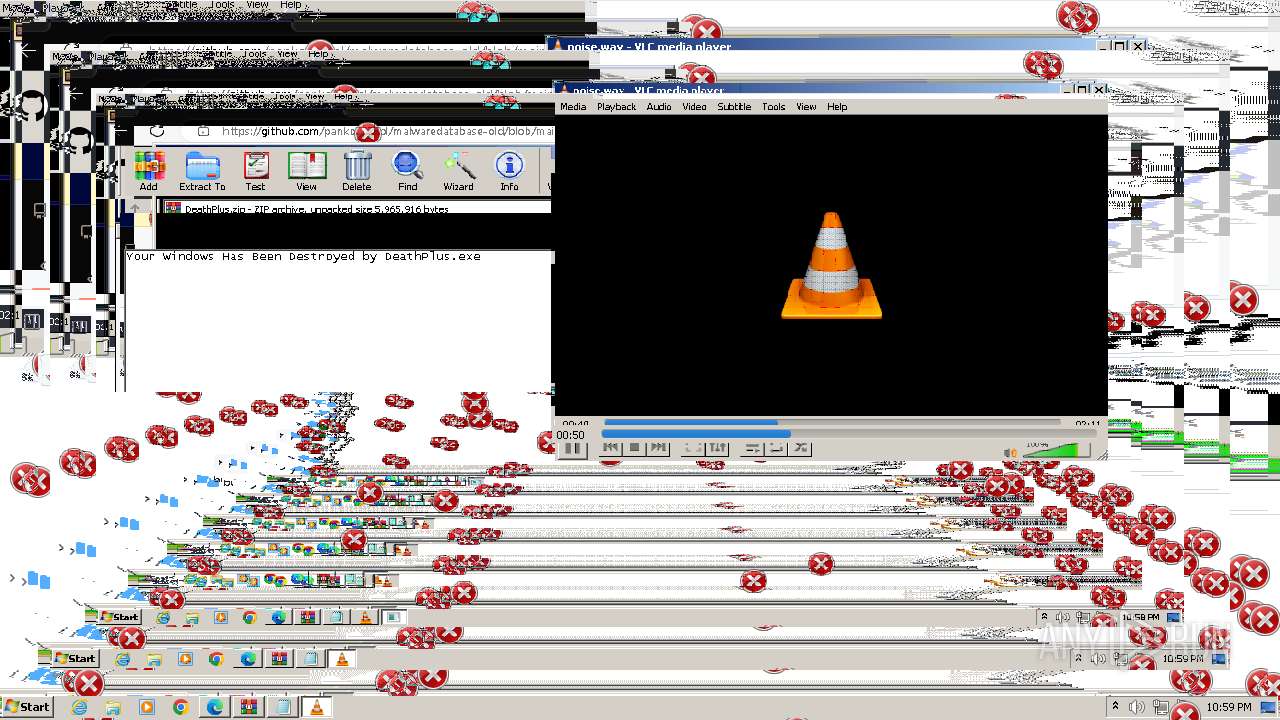
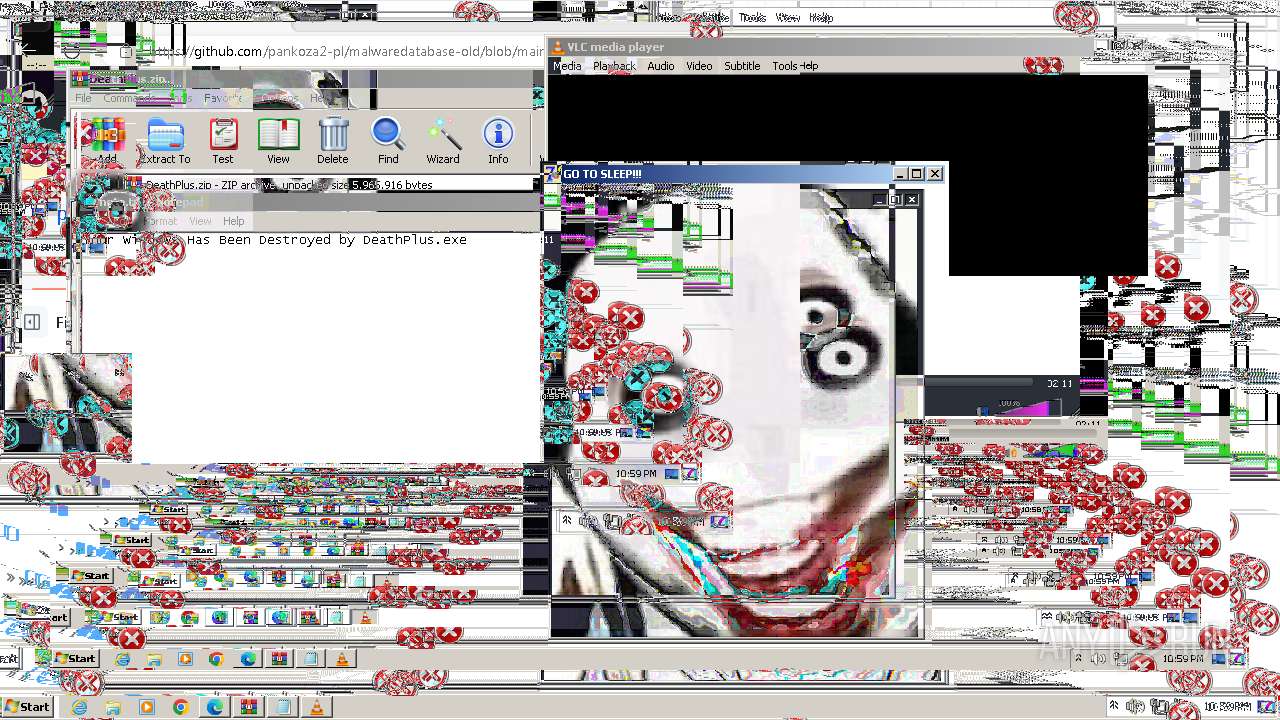
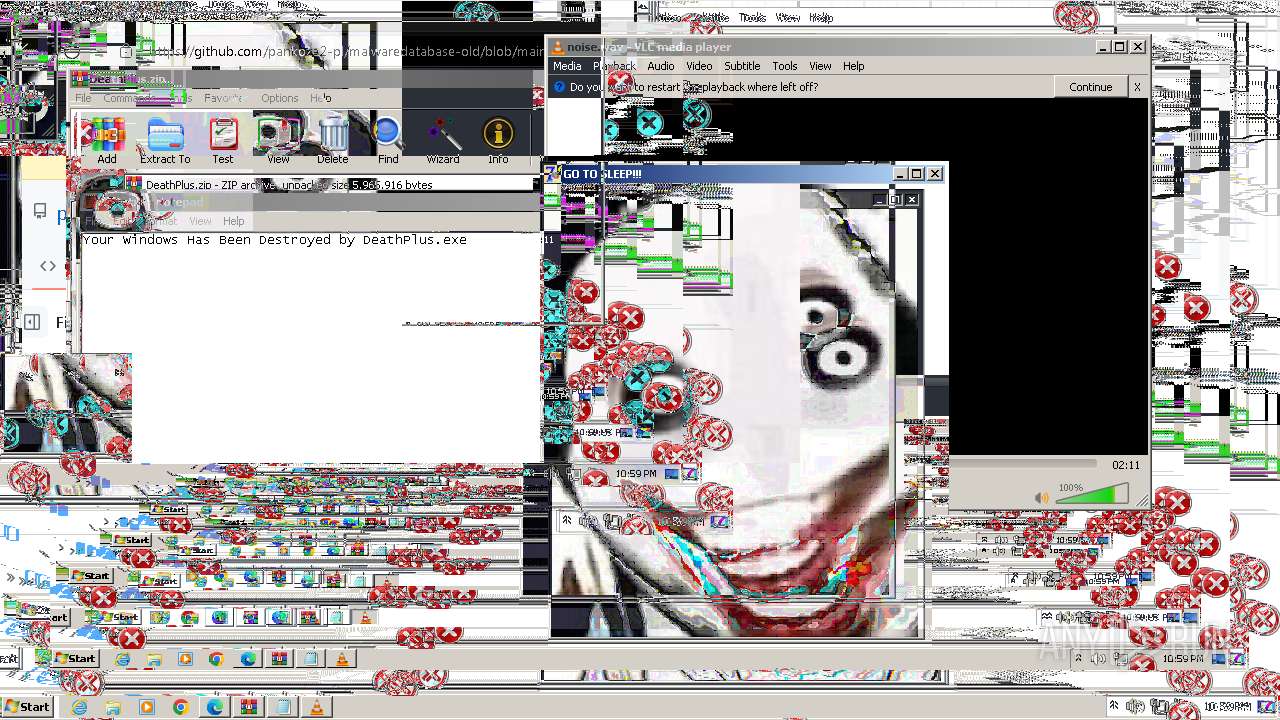
Drops the executable file immediately after the start
- DeathPlus.exe (PID: 2888)
Uses Task Scheduler to run other applications
- MBRKiller.exe (PID: 3808)
Changes the autorun value in the registry
- MBRKiller.exe (PID: 3808)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2016)
- DeathPlus.exe (PID: 2888)
Executable content was dropped or overwritten
- DeathPlus.exe (PID: 2888)
Executing commands from a ".bat" file
- DeathPlus.exe (PID: 2888)
Reads the Internet Settings
- DeathPlus.exe (PID: 2888)
- mshta.exe (PID: 1876)
- cmd.exe (PID: 684)
The executable file from the user directory is run by the CMD process
- MBRKiller.exe (PID: 3808)
- CLWCP.exe (PID: 1588)
- waves.exe (PID: 3436)
- icons.exe (PID: 3484)
- BitBlt.exe (PID: 1164)
- tunnel.exe (PID: 764)
- icons.exe (PID: 3940)
- scream.exe (PID: 2704)
- scream.exe (PID: 3352)
- scream.exe (PID: 1412)
- scream.exe (PID: 1104)
- scream.exe (PID: 1796)
- scream.exe (PID: 2696)
- scream.exe (PID: 2400)
- CLWCP.exe (PID: 1488)
- tunnel.exe (PID: 3616)
- scream.exe (PID: 1916)
- scream.exe (PID: 2712)
- scream.exe (PID: 3356)
- scream.exe (PID: 2872)
- scream.exe (PID: 1284)
- scream.exe (PID: 1404)
- scream.exe (PID: 2992)
- scream.exe (PID: 1216)
- scream.exe (PID: 368)
- CLWCP.exe (PID: 1588)
- BitBlt.exe (PID: 3624)
- icons.exe (PID: 3228)
- tunnel.exe (PID: 1788)
- inv.exe (PID: 1268)
- scream.exe (PID: 1280)
- scream.exe (PID: 2908)
- scream.exe (PID: 2904)
- scream.exe (PID: 2708)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 684)
Starts CMD.EXE for commands execution
- DeathPlus.exe (PID: 2888)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 684)
Probably fake Windows Update
- schtasks.exe (PID: 832)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 684)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 684)
INFO
Drops the executable file immediately after the start
- msedge.exe (PID: 2092)
- WinRAR.exe (PID: 2016)
- msedge.exe (PID: 3380)
Application launched itself
- msedge.exe (PID: 3380)
The process uses the downloaded file
- msedge.exe (PID: 2832)
- WinRAR.exe (PID: 2016)
Checks supported languages
- DeathPlus.exe (PID: 2888)
- MBRKiller.exe (PID: 3808)
- CLWCP.exe (PID: 1588)
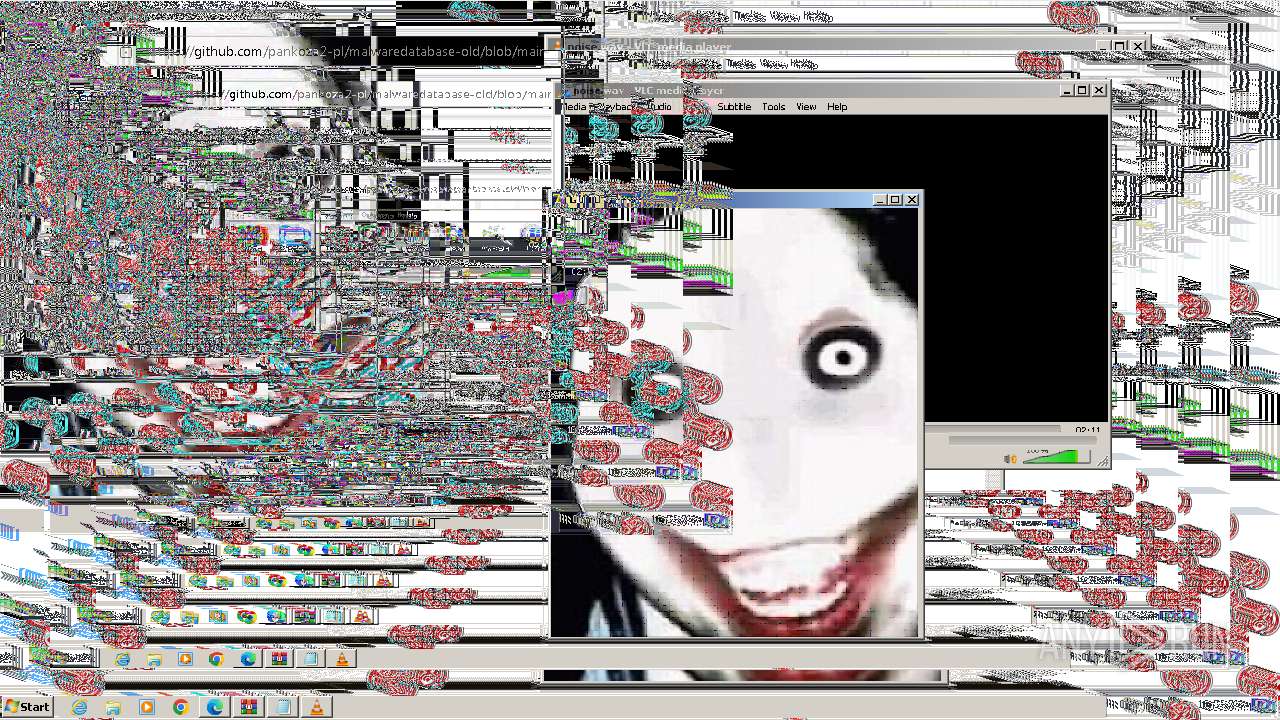
- vlc.exe (PID: 1228)
- waves.exe (PID: 3436)
- icons.exe (PID: 3484)
- tunnel.exe (PID: 764)
- BitBlt.exe (PID: 1164)
- icons.exe (PID: 3940)
- CLWCP.exe (PID: 1488)
- tunnel.exe (PID: 3616)
- scream.exe (PID: 3352)
- scream.exe (PID: 1412)
- scream.exe (PID: 2704)
- scream.exe (PID: 1104)
- scream.exe (PID: 2400)
- scream.exe (PID: 1796)
- scream.exe (PID: 2696)
- scream.exe (PID: 1916)
- scream.exe (PID: 2712)
- scream.exe (PID: 1280)
- scream.exe (PID: 1284)
- scream.exe (PID: 2904)
- scream.exe (PID: 2872)
- scream.exe (PID: 1404)
- scream.exe (PID: 2908)
- scream.exe (PID: 2992)
- scream.exe (PID: 1216)
- scream.exe (PID: 368)
- CLWCP.exe (PID: 1588)
- vlc.exe (PID: 3024)
- BitBlt.exe (PID: 3624)
- tunnel.exe (PID: 1788)
- inv.exe (PID: 1268)
- icons.exe (PID: 3228)
- vlc.exe (PID: 2220)
- scream.exe (PID: 2708)
- scream.exe (PID: 3356)
Reads the computer name
- DeathPlus.exe (PID: 2888)
- vlc.exe (PID: 1228)
Create files in a temporary directory
- DeathPlus.exe (PID: 2888)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2016)
UPX packer has been detected
- DeathPlus.exe (PID: 2888)
Reads Internet Explorer settings
- mshta.exe (PID: 1876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
146
Monitored processes
97
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | taskkill /f /im icons.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3664 --field-trial-handle=1324,i,2107990750088796087,11337592523546047010,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 368 | scream.exe | C:\Users\admin\AppData\Local\Temp\501B.tmp\scream.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 684 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\501B.tmp\DeathPlus.bat" " | C:\Windows\System32\cmd.exe | — | DeathPlus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 724 | timeout 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | taskkill /f /im BitBlt.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4176 --field-trial-handle=1324,i,2107990750088796087,11337592523546047010,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 764 | tunnel.exe | C:\Users\admin\AppData\Local\Temp\501B.tmp\tunnel.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 764 | taskkill /f /im explorer.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | schtasks.exe /Create /TN "Windows Update" /ru SYSTEM /SC ONSTART /TR "C:\Users\admin\AppData\Local\Temp\501B.tmp\MBRKiller.exe" | C:\Windows\System32\schtasks.exe | — | MBRKiller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
45 864
Read events
45 713
Write events
108
Delete events
43
Modification events
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 9A8867EB177A2F00 | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3380) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
14
Suspicious files
186
Text files
32
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF4e859.TMP | — | |
MD5:— | SHA256:— | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF4e878.TMP | — | |
MD5:— | SHA256:— | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF4e887.TMP | — | |
MD5:— | SHA256:— | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF4e8b6.TMP | — | |
MD5:— | SHA256:— | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3424 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3380 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF4e878.TMP | text | |
MD5:646FEFDB4D82709E3056F5C71953783C | SHA256:7B83D8689750F64D31016F1E8AC2A4EB9D7DB406E4C9C66211D4ED17DEBFEAD9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
40
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 200 | 213.155.157.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 213.155.157.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.40.125.183:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 213.155.157.155:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3380 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2092 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
2092 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2092 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2092 | msedge.exe | 185.199.110.154:443 | github.githubassets.com | FASTLY | US | unknown |
2092 | msedge.exe | 185.199.108.133:443 | avatars.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
collector.github.com |
| whitelisted |
api.github.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_concat_plugin.dll
|