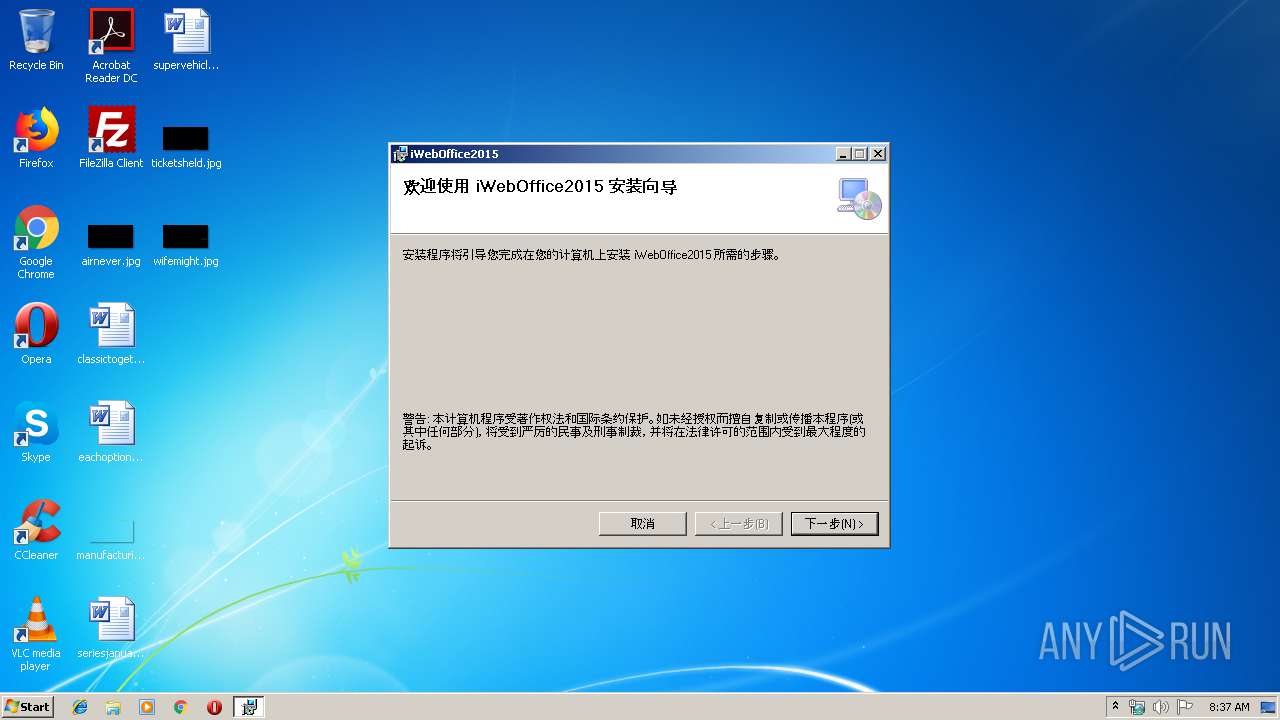
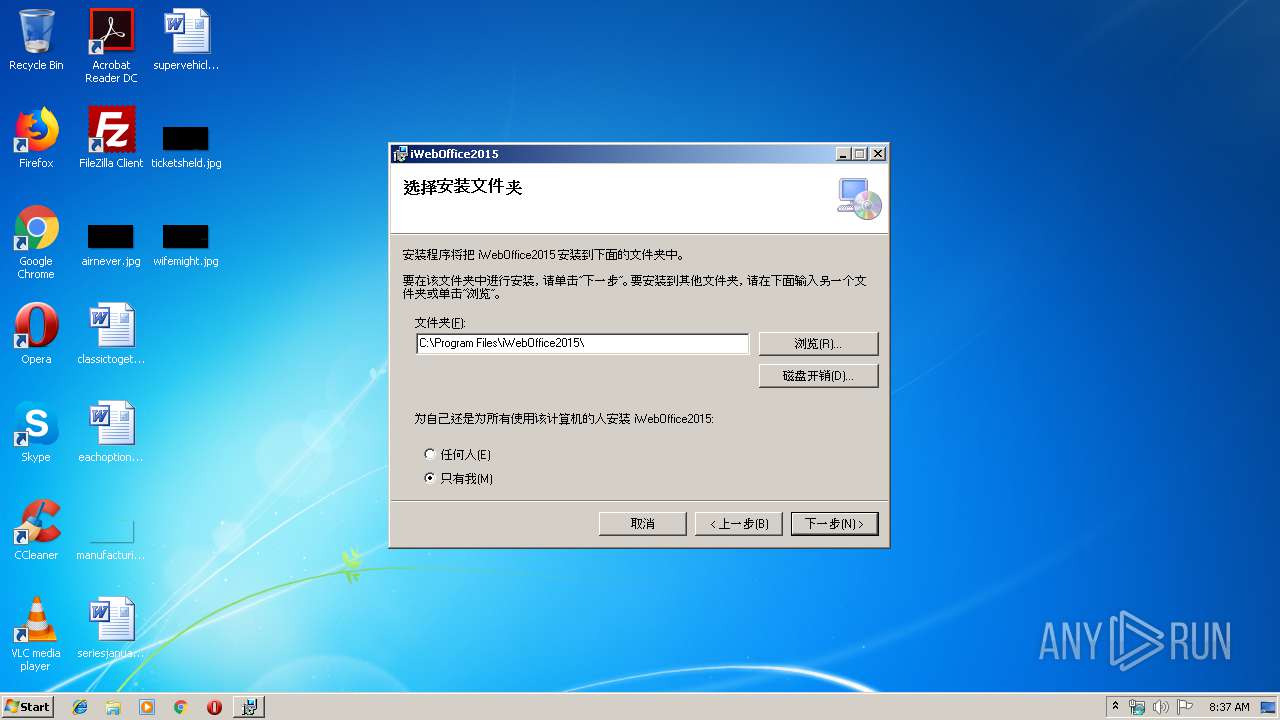
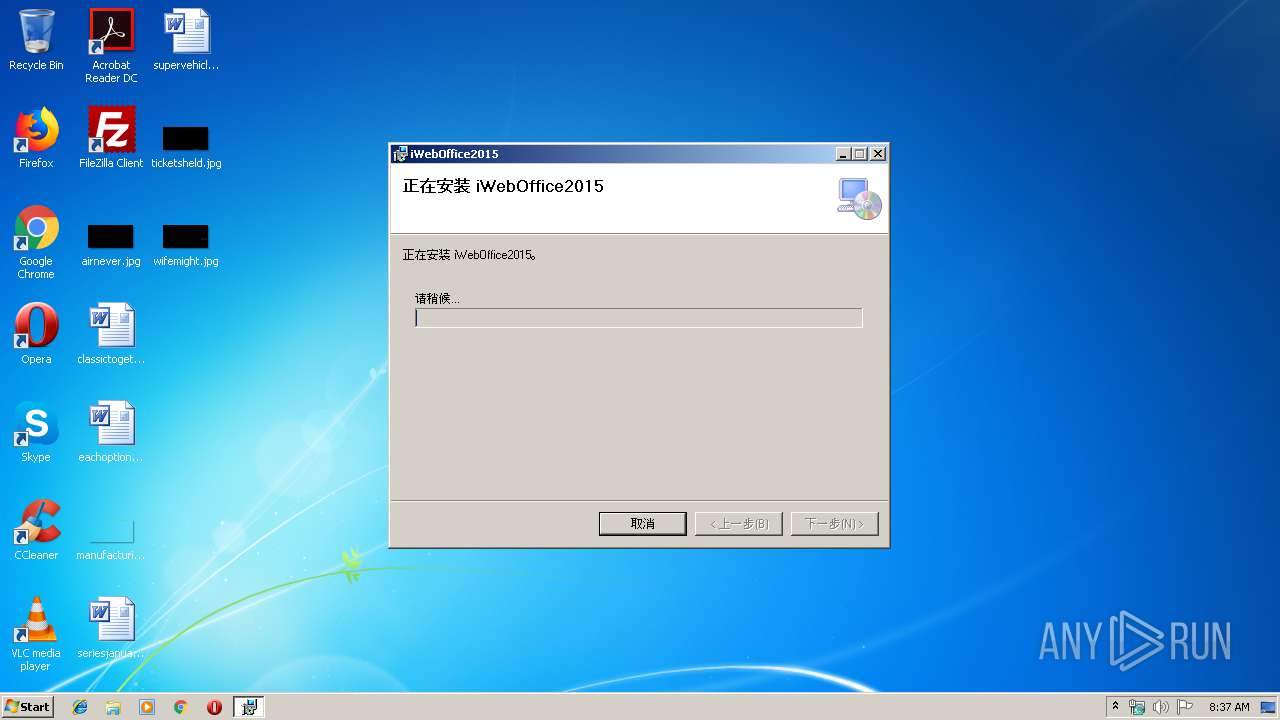
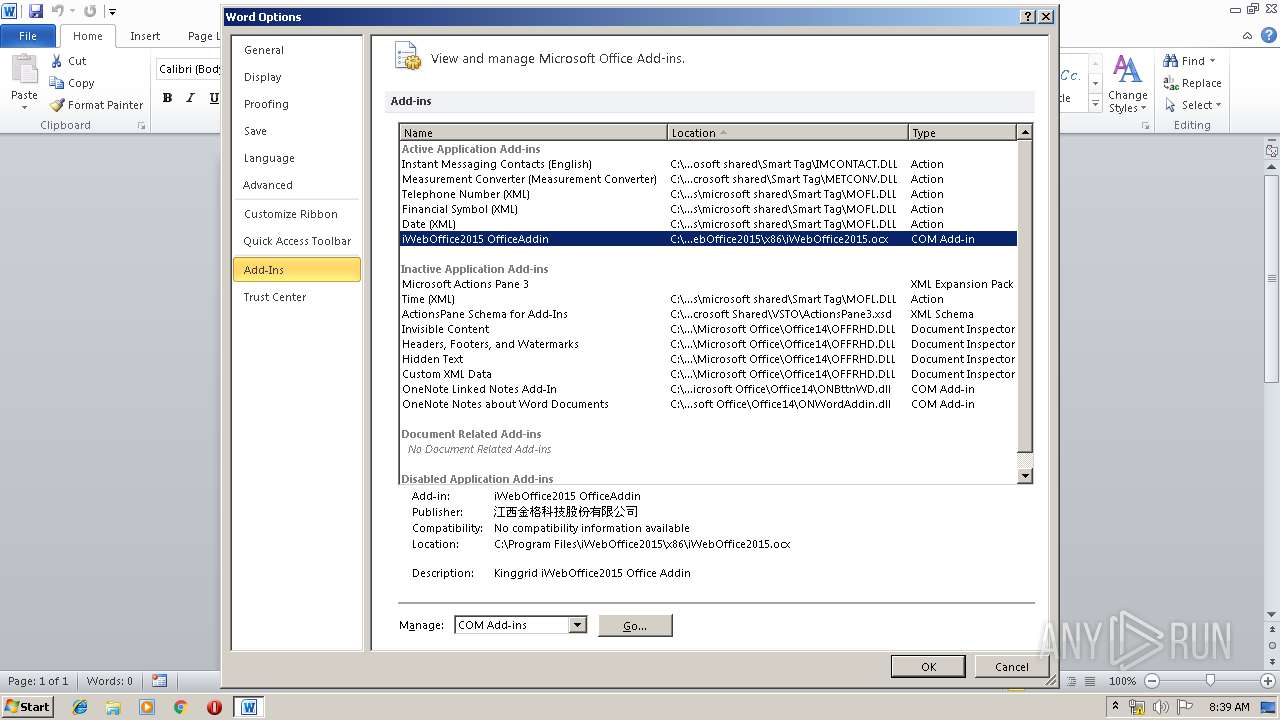
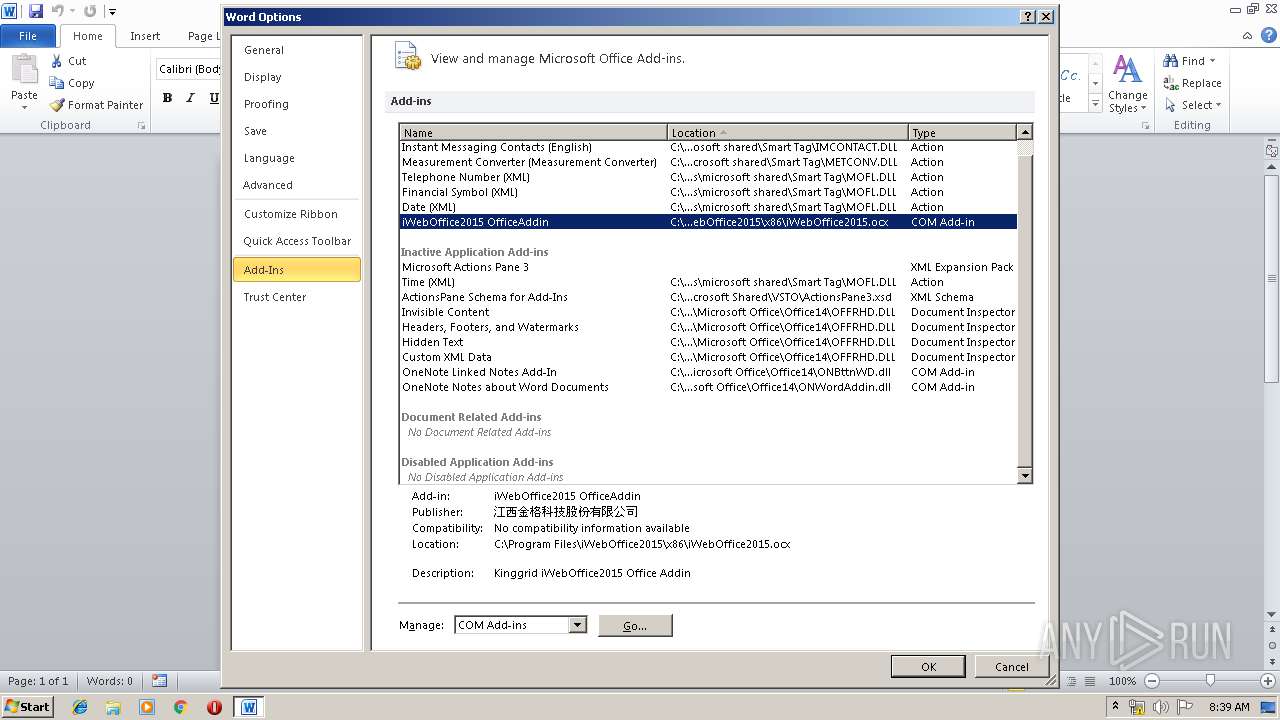
| File name: | iWebOffice2015.msi |
| Full analysis: | https://app.any.run/tasks/c8509274-73ba-4cfc-bab7-89ba7facc7aa |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2019, 07:37:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Create Time/Date: Mon Jun 21 08:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 936, Template: Intel;2052, Number of Pages: 200, Revision Number: {1F6ACC01-1111-4276-8D5F-8A9BA216A620}, Title: iWebOffice2015, Keywords: V12.6.0.744, Comments: V12.6.0.744, Number of Words: 2, Last Saved Time/Date: Thu Jul 11 11:52:58 2019, Last Printed: Thu Jul 11 11:52:58 2019 |
| MD5: | E7F5E854005E3F96421E888F5AD1C5AE |
| SHA1: | 68A1891A43187521FAB956164A2585CE4391B25C |
| SHA256: | F185771252C20DA90C8E97886E75292A727BF3EB5A970A7472BDD17EAD31B852 |
| SSDEEP: | 196608:jz4VlZeuI0MN6RQkQF+pVXOYlYAqpLOqkqZXtAo0/+L68s/jrMAxotU6jwYvIqK:f4lTMN4Qb+/XYzt8/+u8s/n0aXp |
MALICIOUS
Application was dropped or rewritten from another process
- ProcessCheck.exe (PID: 4048)
- FixShortCut.exe (PID: 3176)
- KGChromePluginSetup.exe (PID: 3704)
- SetIEAdmin.exe (PID: 2388)
- LoadNTDriver.exe (PID: 2976)
- CtrlRunReg.exe (PID: 2396)
- cmd.exe (PID: 2956)
- svchost.exe (PID: 2964)
- KGPMService.exe (PID: 2308)
- KGPM_32.exe (PID: 3580)
- cmd.exe (PID: 2996)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 3744)
Loads dropped or rewritten executable
- FixShortCut.exe (PID: 3176)
- SetIEAdmin.exe (PID: 2388)
- ProcessCheck.exe (PID: 4048)
- KGChromePluginSetup.exe (PID: 3704)
- LoadNTDriver.exe (PID: 2976)
- CtrlRunReg.exe (PID: 2396)
- regsvr32.exe (PID: 3188)
- regsvr32.exe (PID: 2944)
- regsvr32.exe (PID: 2228)
- regsvr32.exe (PID: 2720)
- KGPM_32.exe (PID: 3580)
- regsvr32.exe (PID: 2692)
- KGPMService.exe (PID: 2308)
- WINWORD.EXE (PID: 2856)
- regsvr32.exe (PID: 3268)
- regsvr32.exe (PID: 848)
- regsvr32.exe (PID: 980)
- regsvr32.exe (PID: 3844)
- regsvr32.exe (PID: 2764)
- regsvr32.exe (PID: 1952)
- regsvr32.exe (PID: 2420)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3948)
- cmd.exe (PID: 2996)
Starts NET.EXE for service management
- svchost.exe (PID: 2964)
SUSPICIOUS
Executed as Windows Service
- vssvc.exe (PID: 3532)
- KGPMService.exe (PID: 2308)
Executed via COM
- DrvInst.exe (PID: 2760)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3476)
- KGChromePluginSetup.exe (PID: 3704)
- cmd.exe (PID: 2956)
Creates files in the user directory
- KGChromePluginSetup.exe (PID: 3704)
Starts CMD.EXE for commands execution
- KGChromePluginSetup.exe (PID: 3704)
- CtrlRunReg.exe (PID: 2396)
- mshta.exe (PID: 3236)
Creates files in the program directory
- KGChromePluginSetup.exe (PID: 3704)
Creates executable files which already exist in Windows
- cmd.exe (PID: 2956)
Creates files in the Windows directory
- cmd.exe (PID: 2956)
Creates COM task schedule object
- regsvr32.exe (PID: 2944)
- regsvr32.exe (PID: 2720)
- regsvr32.exe (PID: 2692)
Starts SC.EXE for service management
- svchost.exe (PID: 2964)
Starts MSHTA.EXE for opening HTA or HTMLS files
- cmd.exe (PID: 3744)
- cmd.exe (PID: 2956)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 3532)
Searches for installed software
- msiexec.exe (PID: 3476)
Creates a software uninstall entry
- msiexec.exe (PID: 3476)
Creates files in the program directory
- msiexec.exe (PID: 3476)
Manual execution by user
- WINWORD.EXE (PID: 2856)
- cmd.exe (PID: 2996)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2856)
Creates files in the user directory
- WINWORD.EXE (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Simplified Chinese (PRC, Singapore) |
| Template: | Intel;2052 |
| Pages: | 200 |
| RevisionNumber: | {1F6ACC01-1111-4276-8D5F-8A9BA216A620} |
| Title: | iWebOffice2015 |
| Subject: | - |
| Author: | ?????????Ƽ??ɷ?????˾ |
| Keywords: | V12.6.0.744 |
| Comments: | V12.6.0.744 |
| Words: | 2 |
| ModifyDate: | 2019:07:11 10:52:58 |
| LastPrinted: | 2019:07:11 10:52:58 |
Total processes
88
Monitored processes
43
Malicious processes
8
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | net start KGPMSYS | C:\Windows\System32\net.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | regsvr32.exe "C:\Program Files\iWebOffice2015\X86\npiwebplugin.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | regsvr32.exe "C:\Program Files\iWebOffice2015\X64\StockVBAs.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 980 | regsvr32.exe "C:\Program Files\iWebOffice2015\X64\npiwebplugin.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1344 | regsvr32.exe "C:\Program Files\iWebOffice2015\X64\iWebRevisionII_x64.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1952 | regsvr32.exe "C:\Program Files\iWebOffice2015\X86\StockVBAs.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1952 | regsvr32.exe "C:\Program Files\iWebOffice2015\X64\FuncExtModule.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | regsvr32.exe "C:\Program Files\iWebOffice2015\x64\iWebOffice2015.ocx" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2228 | regsvr32.exe "C:\Program Files\iWebOffice2015\X64\npiwebplugin.dll" /s | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2308 | "C:\Program Files\KGChromePlugin\KGPMService.exe" | C:\Program Files\KGChromePlugin\KGPMService.exe | services.exe | ||||||||||||
User: SYSTEM Company: 江西金格科技股份有限公司 Integrity Level: SYSTEM Description: KGPMService Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
Total events
3 058
Read events
2 067
Write events
954
Delete events
37
Modification events
| (PID) Process: | (3856) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3476) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000068C13824066AD501940D0000F80C0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3476) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000068C13824066AD501940D0000F80C0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3476) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 24 | |||
| (PID) Process: | (3476) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000C45A9324066AD501940D0000F80C0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3476) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000001EBD9524066AD501940D0000B40B0000E8030000010000000000000000000000D890AEBEF5D04E4FB4E57F4F03263EB20000000000000000 | |||
| (PID) Process: | (3532) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000086469F24066AD501CC0D0000E0040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3532) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000086469F24066AD501CC0D0000300C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3532) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000086469F24066AD501CC0D00006C080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3532) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000086469F24066AD501CC0D0000000C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
54
Suspicious files
11
Text files
167
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3476 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Windows\Installer\170be7.msi | — | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF5CD5C4C6ECFC1078.TMP | — | |
MD5:— | SHA256:— | |||
| 3532 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Windows\Installer\MSI128E.tmp | binary | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Program Files\iWebOffice2015\Help\images\004.png | image | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Program Files\iWebOffice2015\Help\Faq003.html | html | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Program Files\iWebOffice2015\x86\languages\iweboffice_tw.xml | xml | |
MD5:— | SHA256:— | |||
| 3476 | msiexec.exe | C:\Program Files\iWebOffice2015\KGChromePlugin\KG360ChromeStarter.ico | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
KGPMService.exe | My Sample Service: Main: Entry |
KGPMService.exe | My Sample Service: ServiceMain: Entry |
KGPMService.exe | My Sample Service: ServiceMain: Performing Service Start Operations |
KGPMService.exe | My Sample Service: ServiceMain: Waiting for Worker Thread to complete |
KGPMService.exe | My Sample Service: ServiceWorkerThread: Entry |
KGPMService.exe | FindProcessByName
|
KGPM_32.exe | jxh [KGPM] InitInstance() pszCmdLineW = "C:\Program Files\KGChromePlugin\X86\KGPM_32.exe"
|
KGPM_32.exe | jxh [KGPM] argc = 1
|
KGPM_32.exe | jxh [KGPM] FindProcessByNameAndKillThemAll
|
KGPM_32.exe | jxh [KGPM] DeActiveMonitor start
|