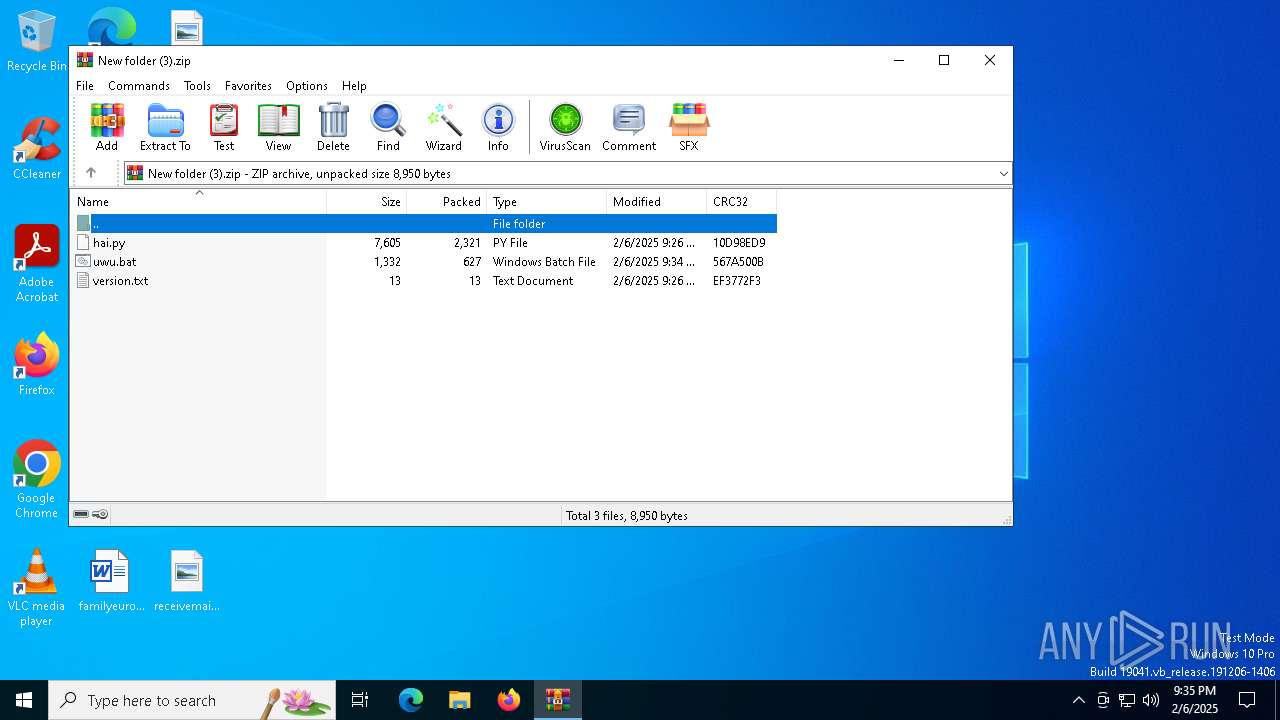
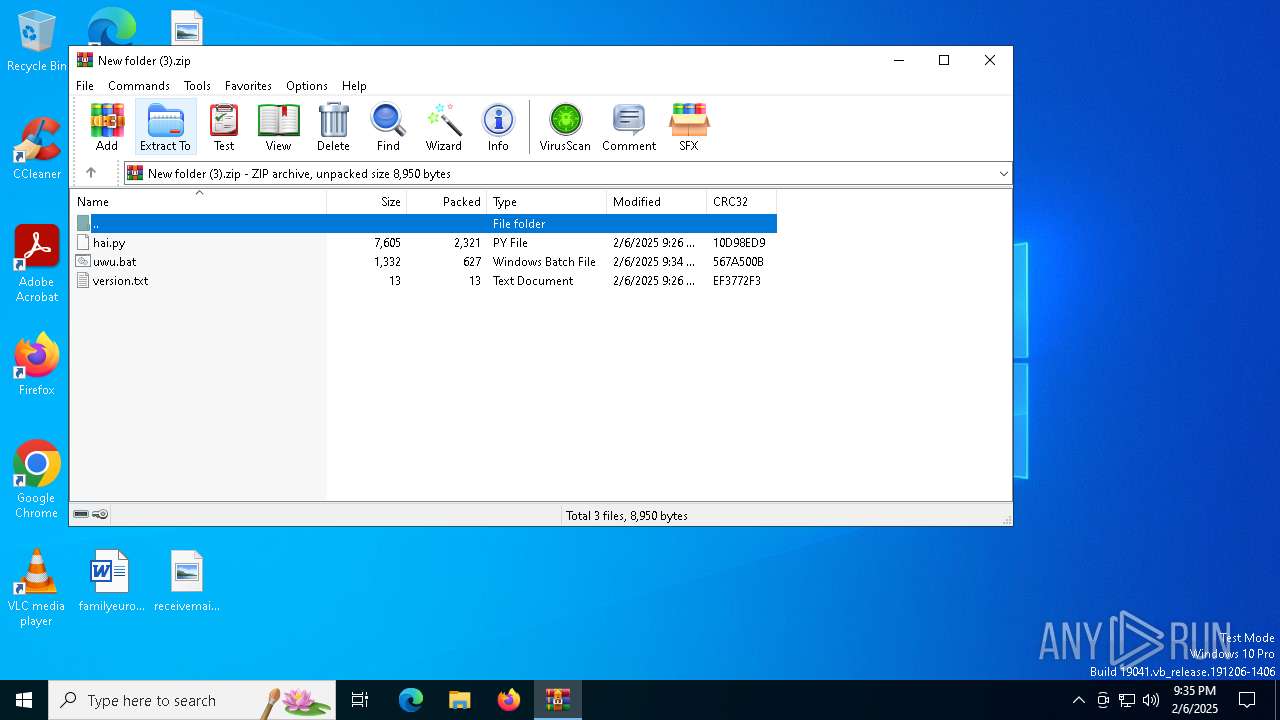
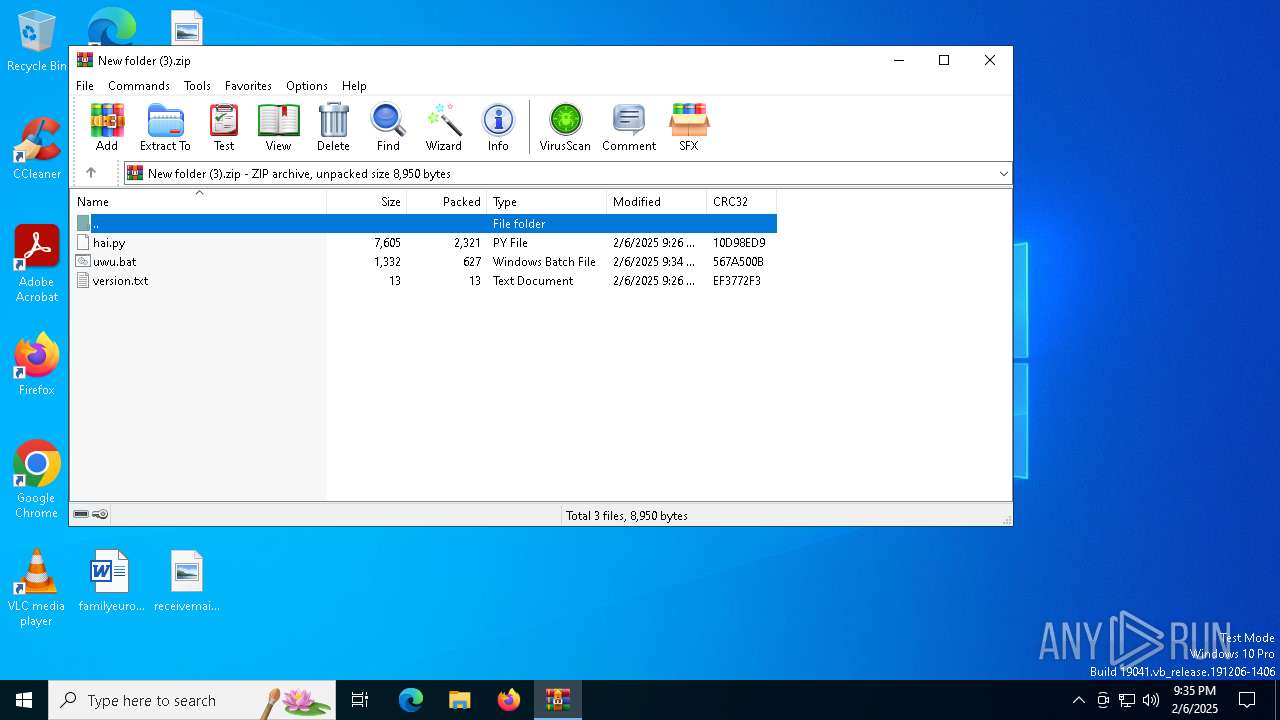
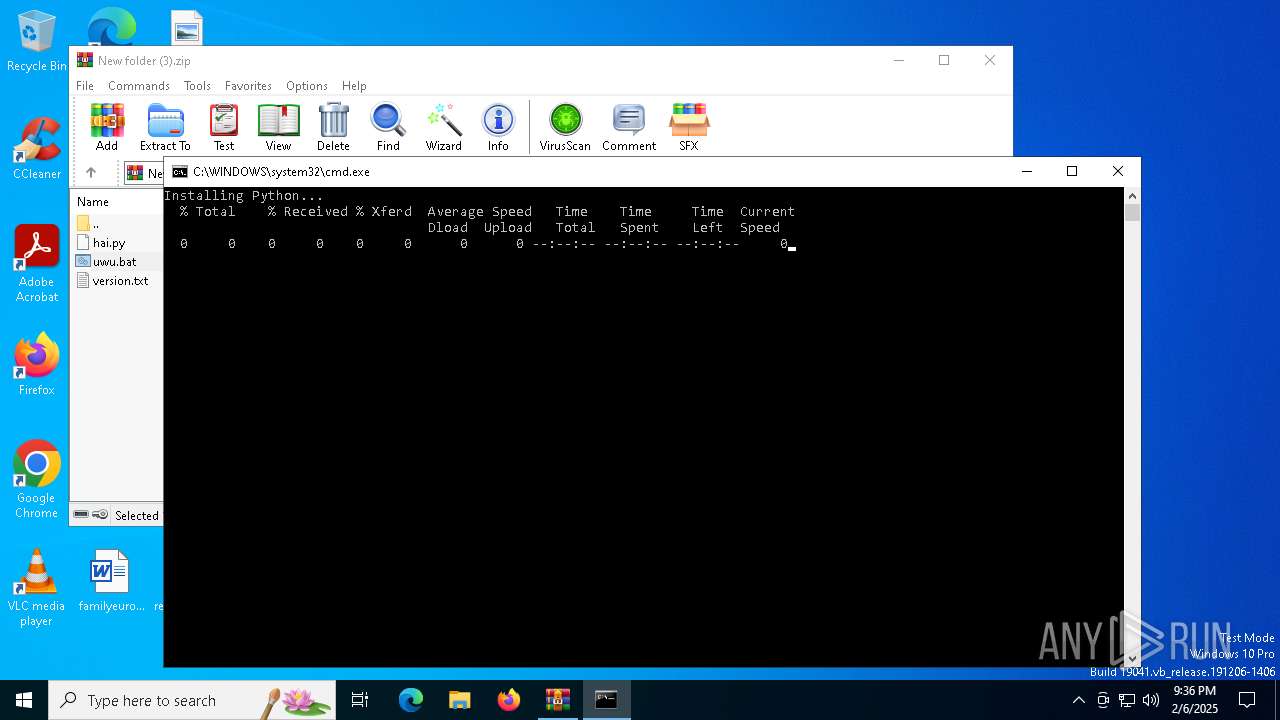
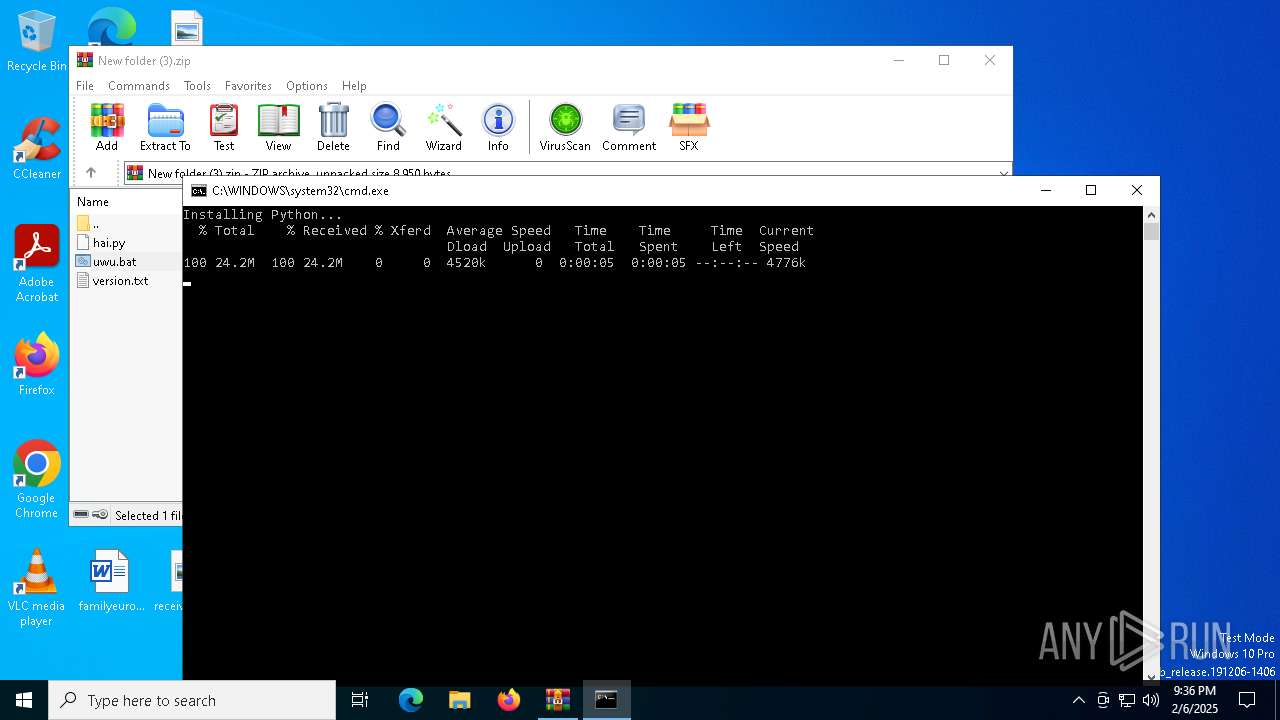
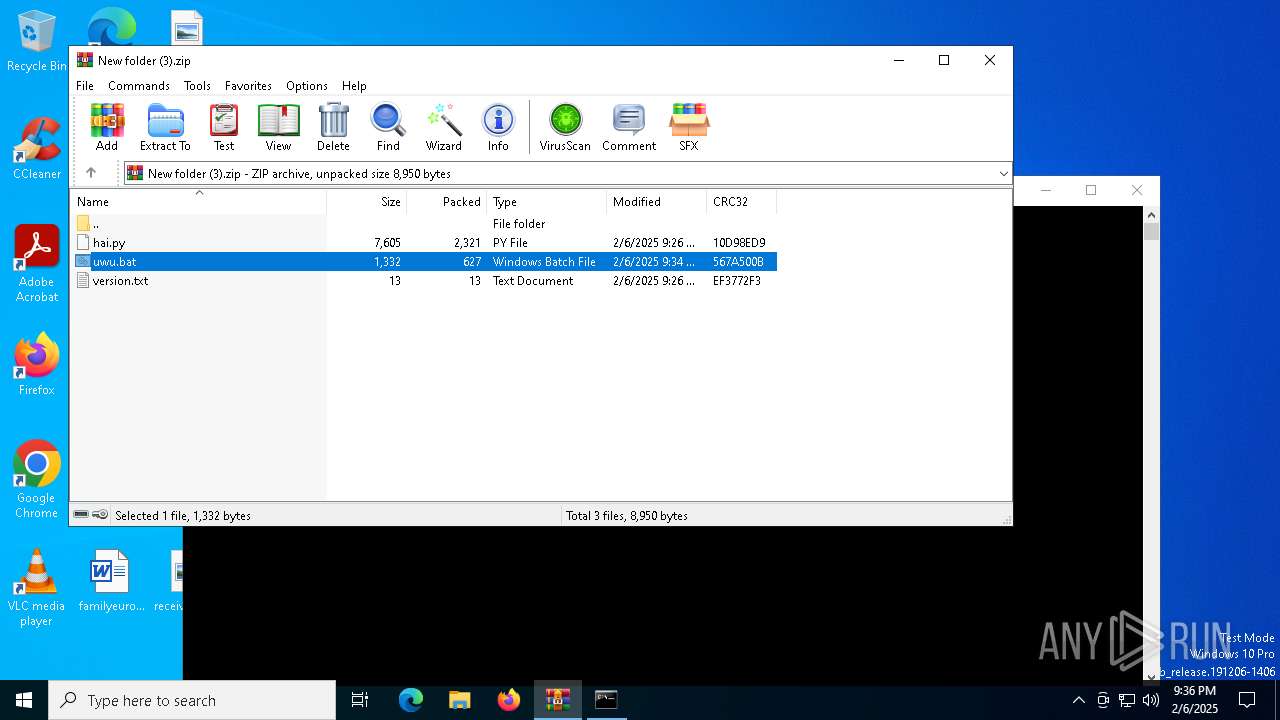
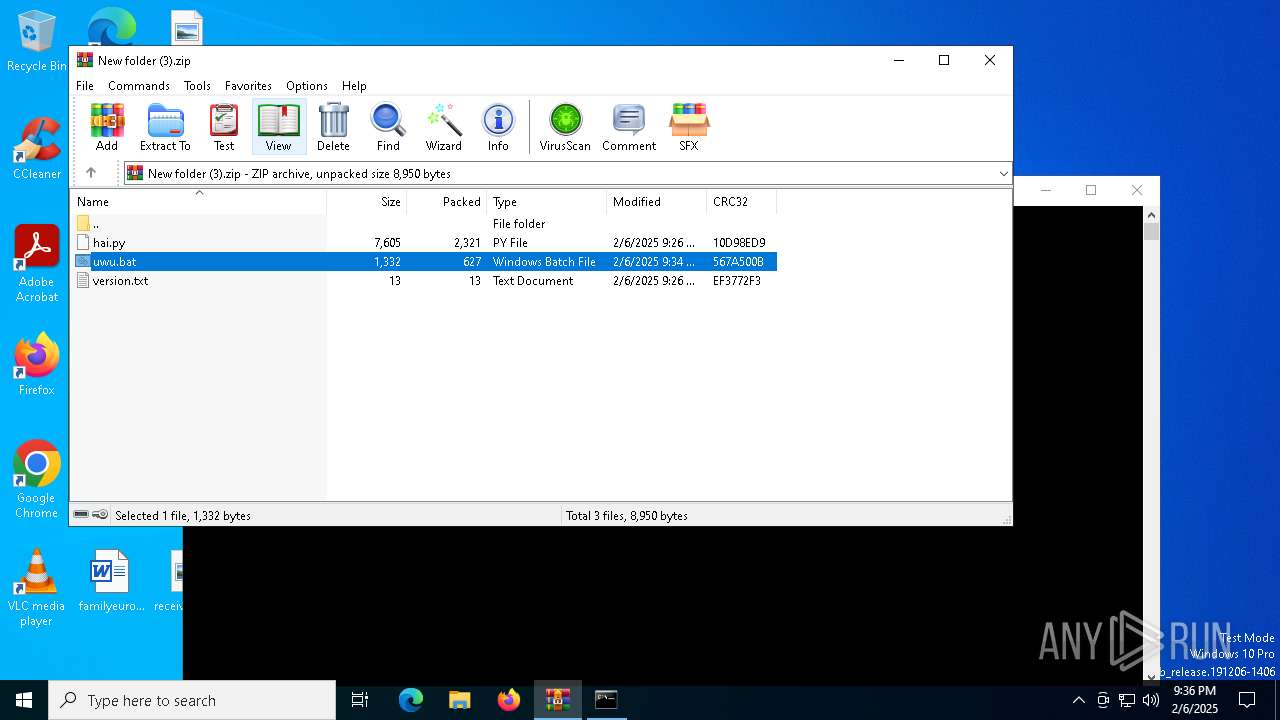
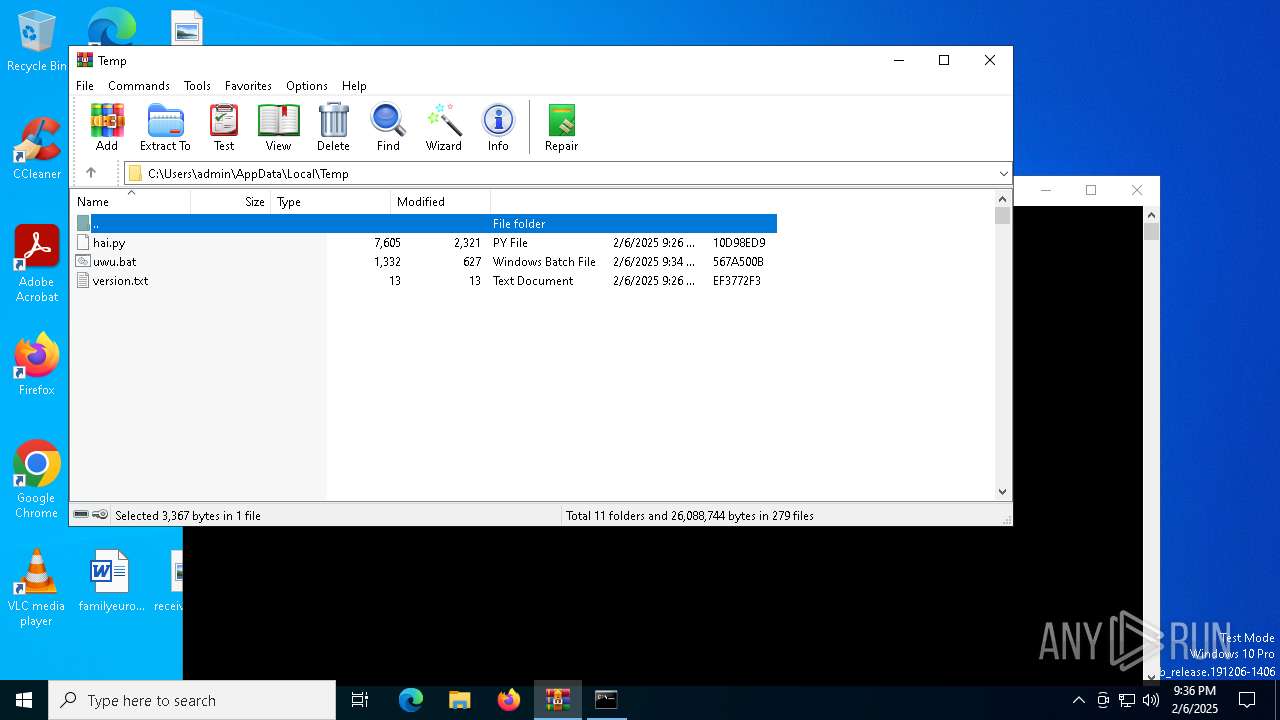
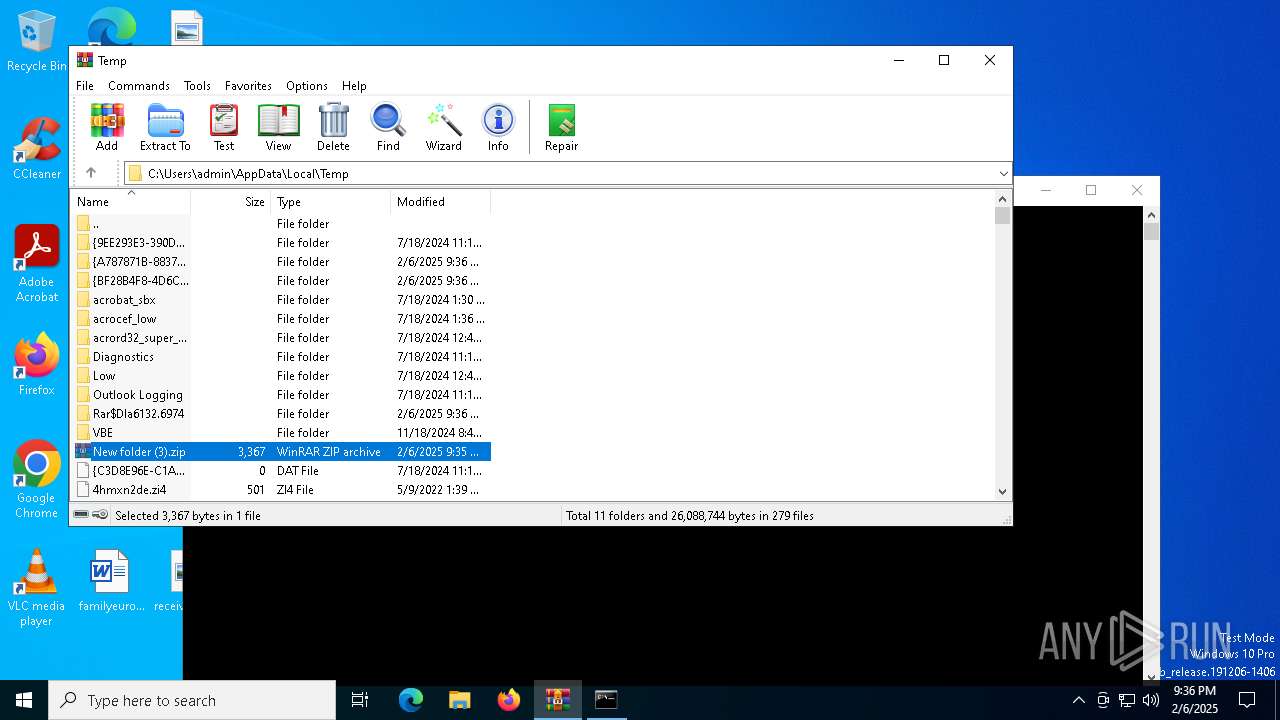
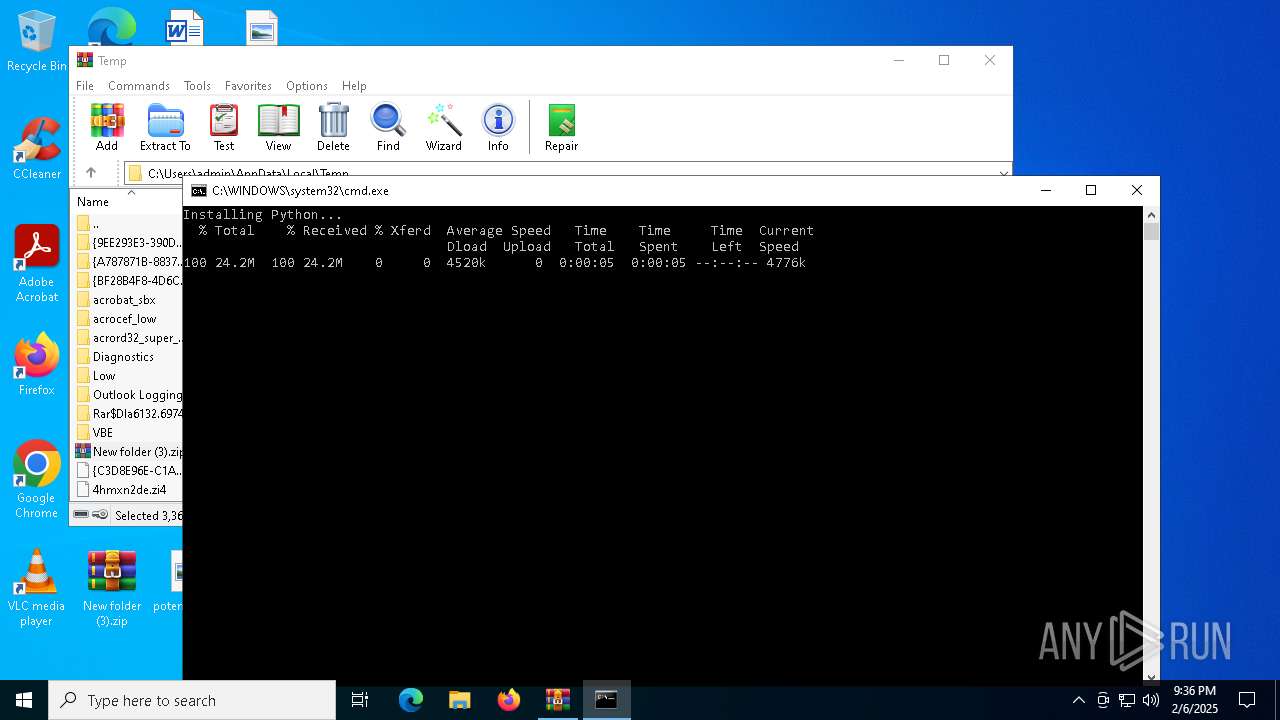
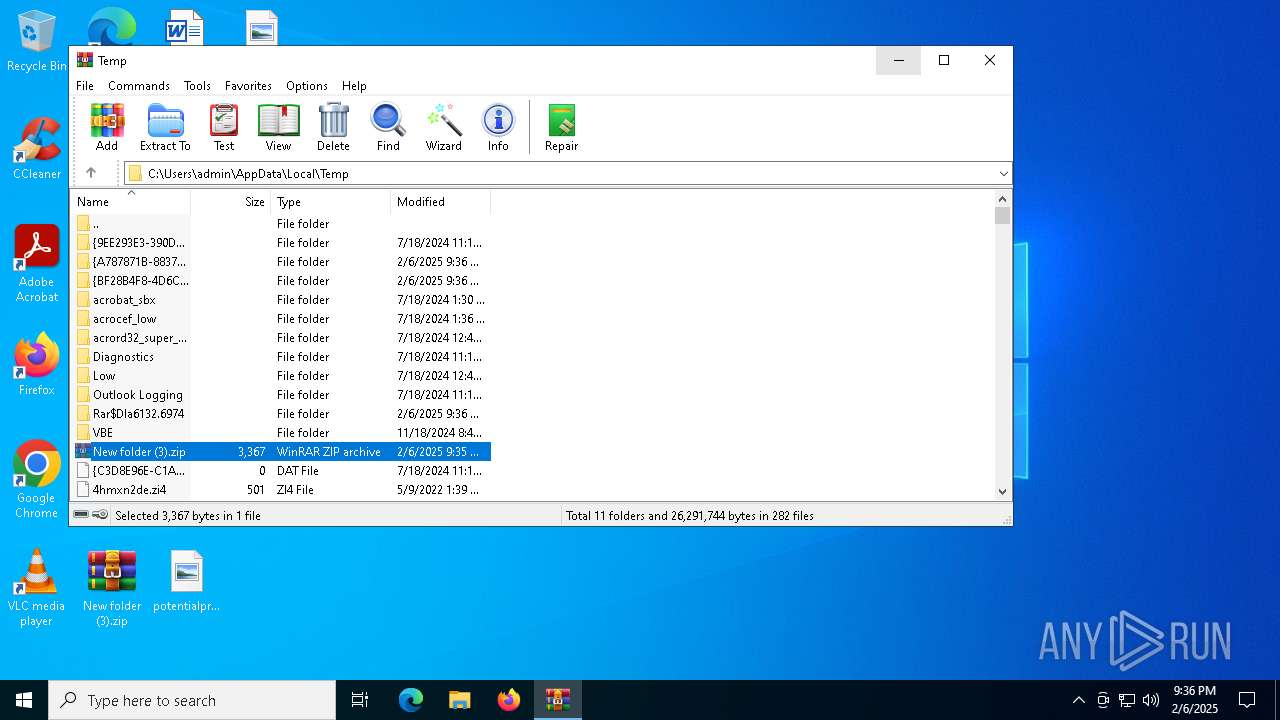
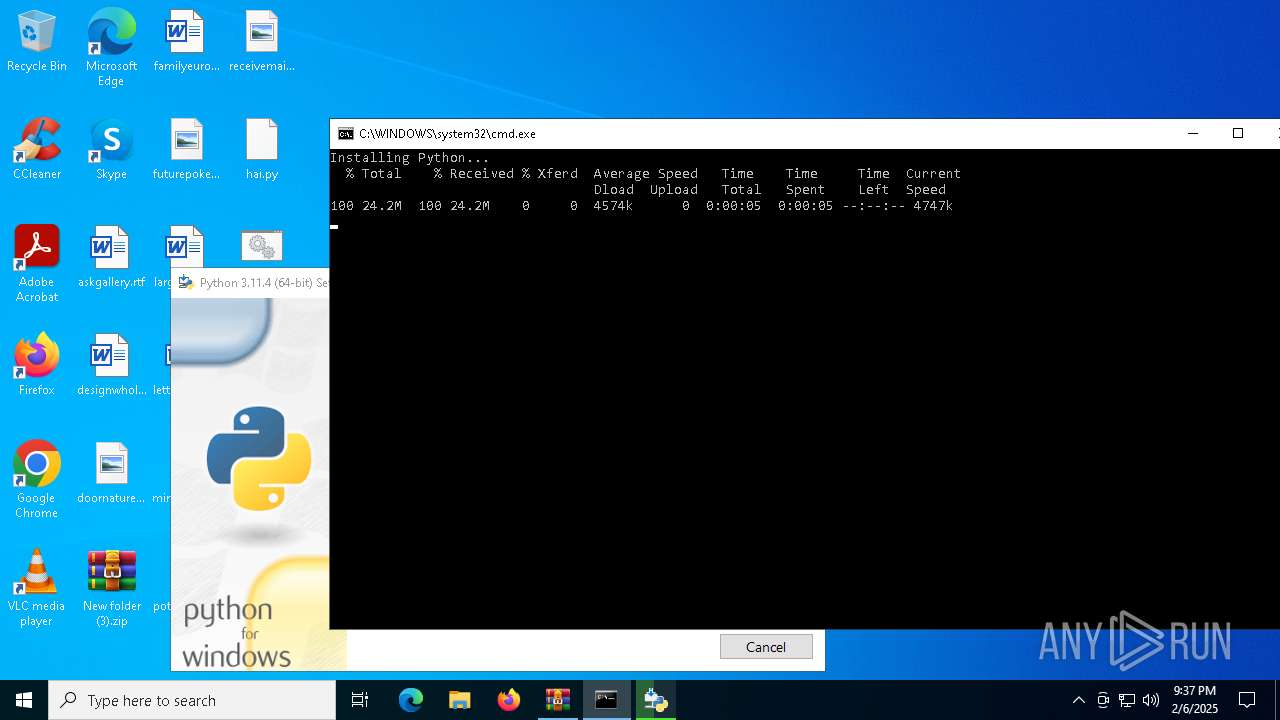
| File name: | New folder (3).zip |
| Full analysis: | https://app.any.run/tasks/45a31430-94e5-4d5d-9d31-004ed795d5fb |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2025, 21:35:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v6.3 to extract, compression method=lzma |
| MD5: | C43F97D22CC25702DBE755715C53B99B |
| SHA1: | C3A9BA628CCBC5BB447D148BF365D092F1C8458F |
| SHA256: | F180F879D36094B518FBB1A93A1162D7D019388A40B9E7091B648431CF6F0410 |
| SSDEEP: | 96:LRFXqSAfnztgL+DH1+ow5LpXRMNmtdD/nfAcw8gMtVsOgtjtSJ:Lr1AhN13cLjtdD/nfQUVsOwjt0 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6132)
Changes the autorun value in the registry
- python_installer.exe (PID: 7012)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 6220)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6132)
- python_installer.exe (PID: 7012)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 6220)
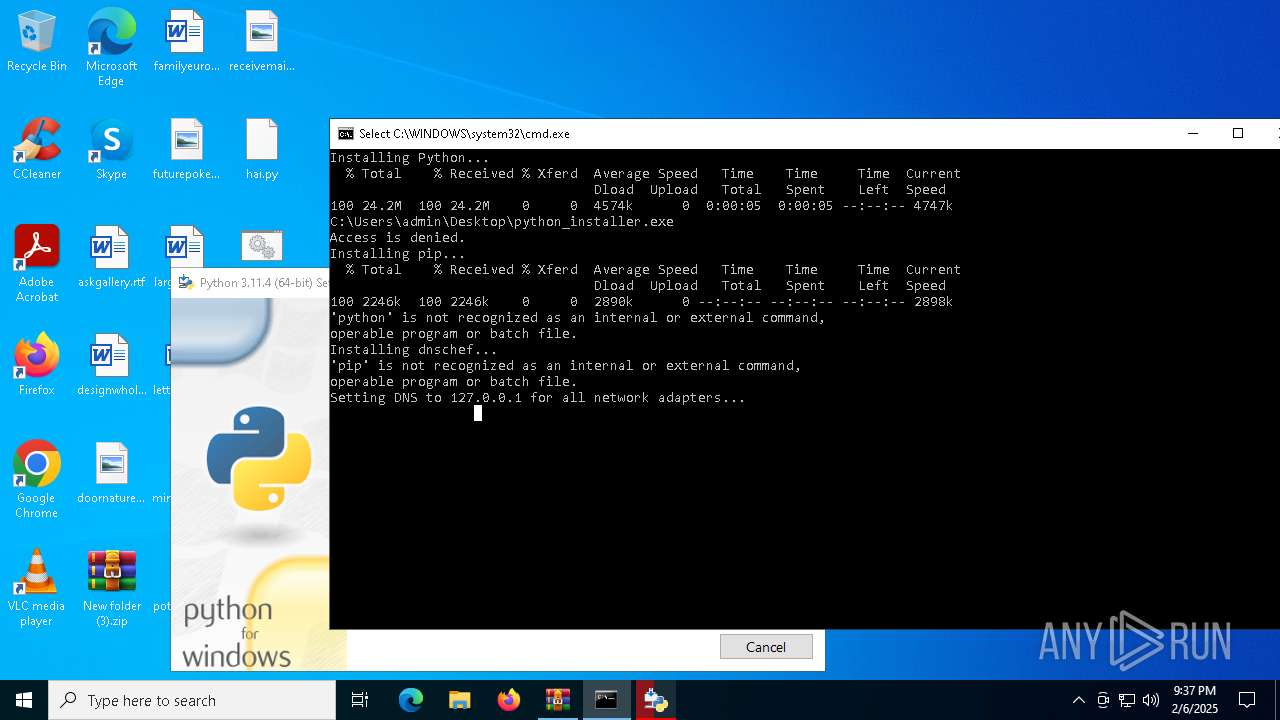
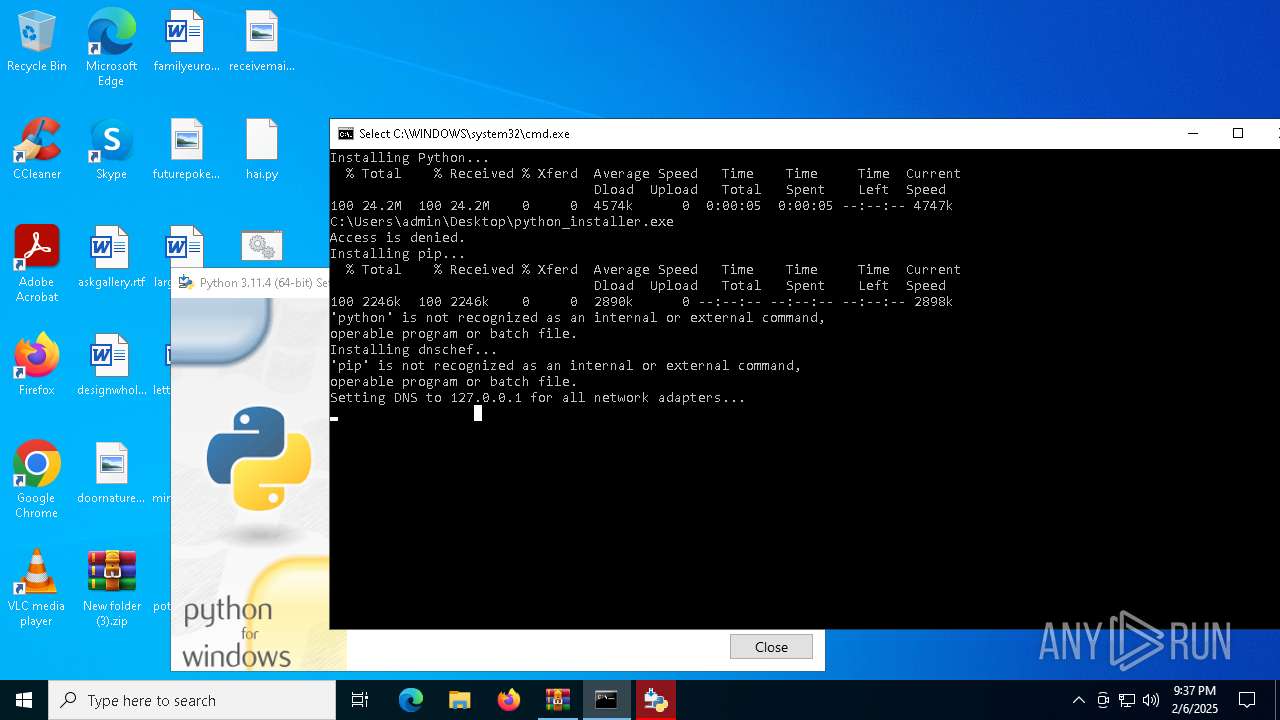
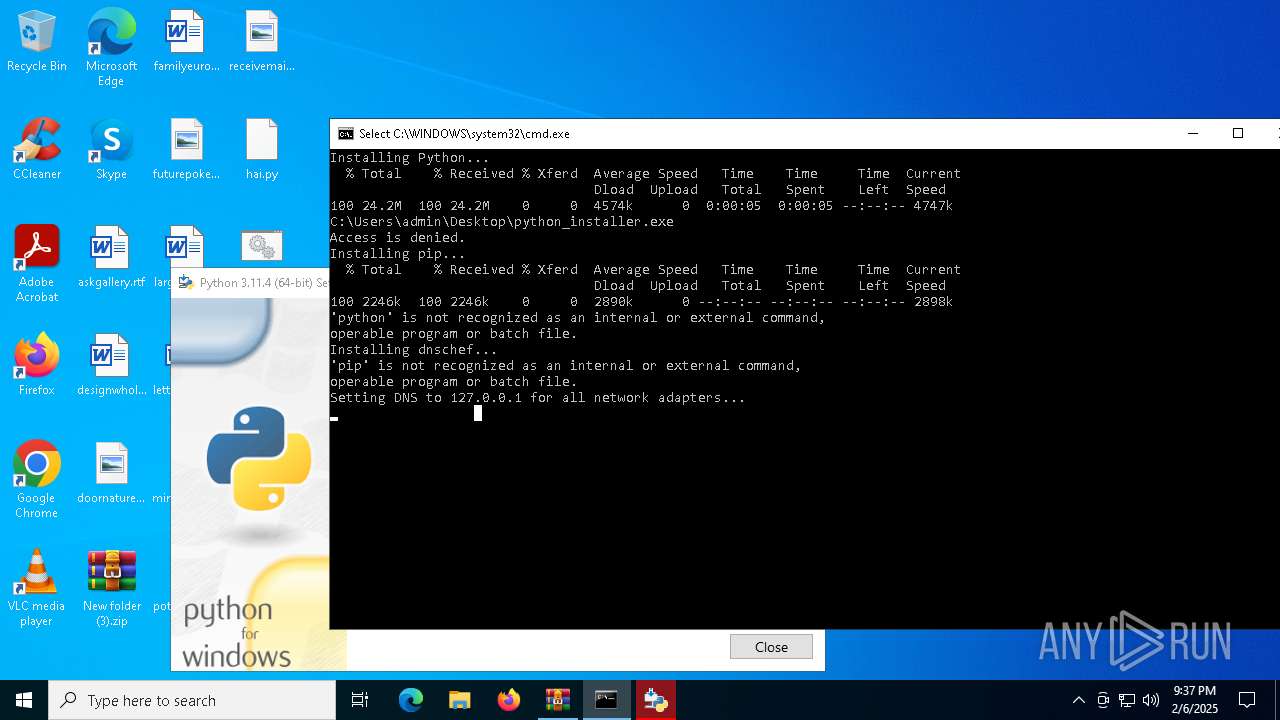
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6132)
The executable file from the user directory is run by the CMD process
- python_installer.exe (PID: 6940)
Executable content was dropped or overwritten
- curl.exe (PID: 6292)
- python_installer.exe (PID: 6940)
- python_installer.exe (PID: 7012)
- python-3.11.4-amd64.exe (PID: 7108)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 2216)
- python_installer.exe (PID: 5680)
- python_installer.exe (PID: 6220)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6132)
Starts itself from another location
- python_installer.exe (PID: 7012)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 6220)
Executes as Windows Service
- VSSVC.exe (PID: 6196)
Searches for installed software
- dllhost.exe (PID: 5488)
- python_installer.exe (PID: 7012)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 6220)
Loads Python modules
- python_installer.exe (PID: 7012)
The process drops C-runtime libraries
- python-3.11.4-amd64.exe (PID: 7108)
- python_installer.exe (PID: 7012)
- msiexec.exe (PID: 6516)
- python_installer.exe (PID: 6220)
Process drops legitimate windows executable
- python-3.11.4-amd64.exe (PID: 7108)
- python_installer.exe (PID: 7012)
- msiexec.exe (PID: 6516)
- python_installer.exe (PID: 6220)
Creates a software uninstall entry
- python_installer.exe (PID: 7012)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 6220)
Checks Windows Trust Settings
- msiexec.exe (PID: 6516)
Process drops python dynamic module
- msiexec.exe (PID: 6516)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6516)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7092)
Found IP address in command line
- powershell.exe (PID: 7048)
Process uses powershell cmdlet to discover network configuration
- cmd.exe (PID: 7092)
INFO
Execution of CURL command
- cmd.exe (PID: 6224)
- cmd.exe (PID: 7092)
Reads the computer name
- curl.exe (PID: 6292)
- python-3.11.4-amd64.exe (PID: 7108)
- python_installer.exe (PID: 7012)
- msiexec.exe (PID: 6516)
- curl.exe (PID: 2996)
- python_installer.exe (PID: 5092)
- python-3.11.4-amd64.exe (PID: 3724)
- python_installer.exe (PID: 6220)
Create files in a temporary directory
- curl.exe (PID: 6292)
- python_installer.exe (PID: 6940)
- python_installer.exe (PID: 7012)
Checks supported languages
- curl.exe (PID: 6292)
- python_installer.exe (PID: 6940)
- python_installer.exe (PID: 7012)
- python-3.11.4-amd64.exe (PID: 7108)
- msiexec.exe (PID: 6516)
- curl.exe (PID: 2996)
- python_installer.exe (PID: 2216)
- python_installer.exe (PID: 5092)
- python-3.11.4-amd64.exe (PID: 3724)
- python_installer.exe (PID: 5680)
- python_installer.exe (PID: 6220)
- python-3.11.4-amd64.exe (PID: 1684)
The sample compiled with english language support
- curl.exe (PID: 6292)
- python_installer.exe (PID: 6940)
- python_installer.exe (PID: 7012)
- python-3.11.4-amd64.exe (PID: 7108)
- msiexec.exe (PID: 6516)
- python_installer.exe (PID: 2216)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 5680)
- python_installer.exe (PID: 6220)
Manages system restore points
- SrTasks.exe (PID: 6460)
Process checks computer location settings
- python_installer.exe (PID: 7012)
- python_installer.exe (PID: 5092)
- python_installer.exe (PID: 6220)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6516)
Creates files in the program directory
- python-3.11.4-amd64.exe (PID: 7108)
Mutex for Python MSI log
- python-3.11.4-amd64.exe (PID: 7108)
- msiexec.exe (PID: 6516)
- python-3.11.4-amd64.exe (PID: 3724)
- python-3.11.4-amd64.exe (PID: 1684)
Reads the machine GUID from the registry
- python-3.11.4-amd64.exe (PID: 7108)
- msiexec.exe (PID: 6516)
- python-3.11.4-amd64.exe (PID: 3724)
- python_installer.exe (PID: 6220)
- python-3.11.4-amd64.exe (PID: 1684)
Creates files or folders in the user directory
- python_installer.exe (PID: 7012)
- msiexec.exe (PID: 6516)
Manual execution by a user
- cmd.exe (PID: 7092)
- WinRAR.exe (PID: 5920)
- python_installer.exe (PID: 5680)
Reads the software policy settings
- msiexec.exe (PID: 6516)
Creates a software uninstall entry
- msiexec.exe (PID: 6516)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7048)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 63 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | LZMA (EFS) |
| ZipModifyDate: | 2025:02:06 13:26:24 |
| ZipCRC: | 0x10d98ed9 |
| ZipCompressedSize: | 2321 |
| ZipUncompressedSize: | 7605 |
| ZipFileName: | hai.py |
Total processes
165
Monitored processes
26
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1684 | "C:\Users\admin\AppData\Local\Temp\{747BA0F6-A9C9-4802-8B8D-7E08C3499348}\.be\python-3.11.4-amd64.exe" -q -burn.elevated BurnPipe.{D88BF0B9-4347-4261-8E53-9D530B0ABC14} {6D67DC17-9256-4A9B-B545-184E9C0B6070} 6220 | C:\Users\admin\AppData\Local\Temp\{747BA0F6-A9C9-4802-8B8D-7E08C3499348}\.be\python-3.11.4-amd64.exe | python_installer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python 3.11.4 (64-bit) Version: 3.11.4150.0 Modules
| |||||||||||||||
| 2216 | python_installer.exe /quiet InstallAllUsers=1 PrependPath=1 | C:\Users\admin\Desktop\python_installer.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.11.4 (64-bit) Exit code: 1618 Version: 3.11.4150.0 Modules
| |||||||||||||||
| 2996 | curl -L "https://www.python.org/ftp/python/3.11.4/python-3.11.4-amd64.exe" -o python_installer.exe | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 3724 | "C:\Users\admin\AppData\Local\Temp\{CF96EF45-C2D3-4FA2-A2FE-10B713A07EFB}\.be\python-3.11.4-amd64.exe" -q -burn.elevated BurnPipe.{9E35B52A-28BF-4FB6-8065-26F32B0A6E40} {5D05333E-2102-4C3B-8E70-289D8AC1A017} 5092 | C:\Users\admin\AppData\Local\Temp\{CF96EF45-C2D3-4FA2-A2FE-10B713A07EFB}\.be\python-3.11.4-amd64.exe | python_installer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python 3.11.4 (64-bit) Exit code: 1618 Version: 3.11.4150.0 Modules
| |||||||||||||||
| 4648 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5092 | "C:\Users\admin\AppData\Local\Temp\{5B413407-086D-41CA-B9DD-4A7DBD2F5751}\.cr\python_installer.exe" -burn.clean.room="C:\Users\admin\Desktop\python_installer.exe" -burn.filehandle.attached=704 -burn.filehandle.self=660 /quiet InstallAllUsers=1 PrependPath=1 | C:\Users\admin\AppData\Local\Temp\{5B413407-086D-41CA-B9DD-4A7DBD2F5751}\.cr\python_installer.exe | python_installer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.11.4 (64-bit) Exit code: 1618 Version: 3.11.4150.0 Modules
| |||||||||||||||
| 5240 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5488 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5680 | "C:\Users\admin\Desktop\python_installer.exe" | C:\Users\admin\Desktop\python_installer.exe | explorer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.11.4 (64-bit) Version: 3.11.4150.0 Modules
| |||||||||||||||
| 5728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
39 665
Read events
36 977
Write events
2 628
Delete events
60
Modification events
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\New folder (3).zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7108) python-3.11.4-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000039758C22DF78DB01C41B0000C81B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5488) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000FC46E222DF78DB017015000030180000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
101
Suspicious files
90
Text files
1 023
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5488 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Temp\{BF28B4F8-4D6C-4D4A-A538-10E2514CBA72}\lib_AllUsers | — | |
MD5:— | SHA256:— | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Temp\{BF28B4F8-4D6C-4D4A-A538-10E2514CBA72}\doc_AllUsers | — | |
MD5:— | SHA256:— | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Package Cache\{3d45edf4-44bb-483f-9e08-43c38c81e118}\state.rsm | binary | |
MD5:D17DF135DE713931CA2551AD404860D6 | SHA256:05133C5E8071F0A17B5092AFFEB9C19E870A6333693F48F0701A1DAE90C16913 | |||
| 6292 | curl.exe | C:\Users\admin\AppData\Local\Temp\python_installer.exe | executable | |
MD5:E4413BB7448CD13B437DFFFFBA294CA0 | SHA256:47BE821C0F1825D90FC40F83A3EE3D3A691A3E16C8E21AC0CD56371362AAAD50 | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Temp\{BF28B4F8-4D6C-4D4A-A538-10E2514CBA72}\.be\python-3.11.4-amd64.exe | executable | |
MD5:73084CDC98F16F144AEAA7CE8966A76A | SHA256:6846E876B507121739C7325D83C6CEF655748113F0EF1CB61759552DD76C9DB4 | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Temp\{BF28B4F8-4D6C-4D4A-A538-10E2514CBA72}\.ba\Default.thm | xml | |
MD5:4A006BB0FD949404E628D26F833C994B | SHA256:BE2BAED45BCFB013E914E9D5BF6BC7C77A311F6F1723AFBB7EB1FAA7DA497E1B | |||
| 5488 | dllhost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{d074a17a-dd22-4cf0-b4cc-2a34953876ac}_OnDiskSnapshotProp | binary | |
MD5:2574E863384985817760F87D044B3516 | SHA256:DDF5E0823CAE04902E90214B55782E22D51F03CC9C93F9827ABEEA71AEA62C7D | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Temp\{BF28B4F8-4D6C-4D4A-A538-10E2514CBA72}\dev_AllUsers | executable | |
MD5:AF3C0810DA0AEDE9C90102A52F5A64E3 | SHA256:38738C01263514CB029B94E2DEFE67FFD115D22C8EEAC603430BB65FDA6ABEBF | |||
| 7012 | python_installer.exe | C:\Users\admin\AppData\Local\Package Cache\{3d45edf4-44bb-483f-9e08-43c38c81e118}\python-3.11.4-amd64.exe | executable | |
MD5:73084CDC98F16F144AEAA7CE8966A76A | SHA256:6846E876B507121739C7325D83C6CEF655748113F0EF1CB61759552DD76C9DB4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 151.101.194.133:80 | http://ocsp2.globalsign.com/rootr3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEQCATgA6JyvFGONNpLH8m3gz | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6004 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6004 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6688 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6516 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6516 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.21.65.157:443 | — | Akamai International B.V. | NL | unknown |
880 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6292 | curl.exe | 151.101.192.223:443 | www.python.org | FASTLY | US | whitelisted |
760 | lsass.exe | 151.101.194.133:80 | ocsp2.globalsign.com | FASTLY | US | whitelisted |
3976 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.python.org |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |