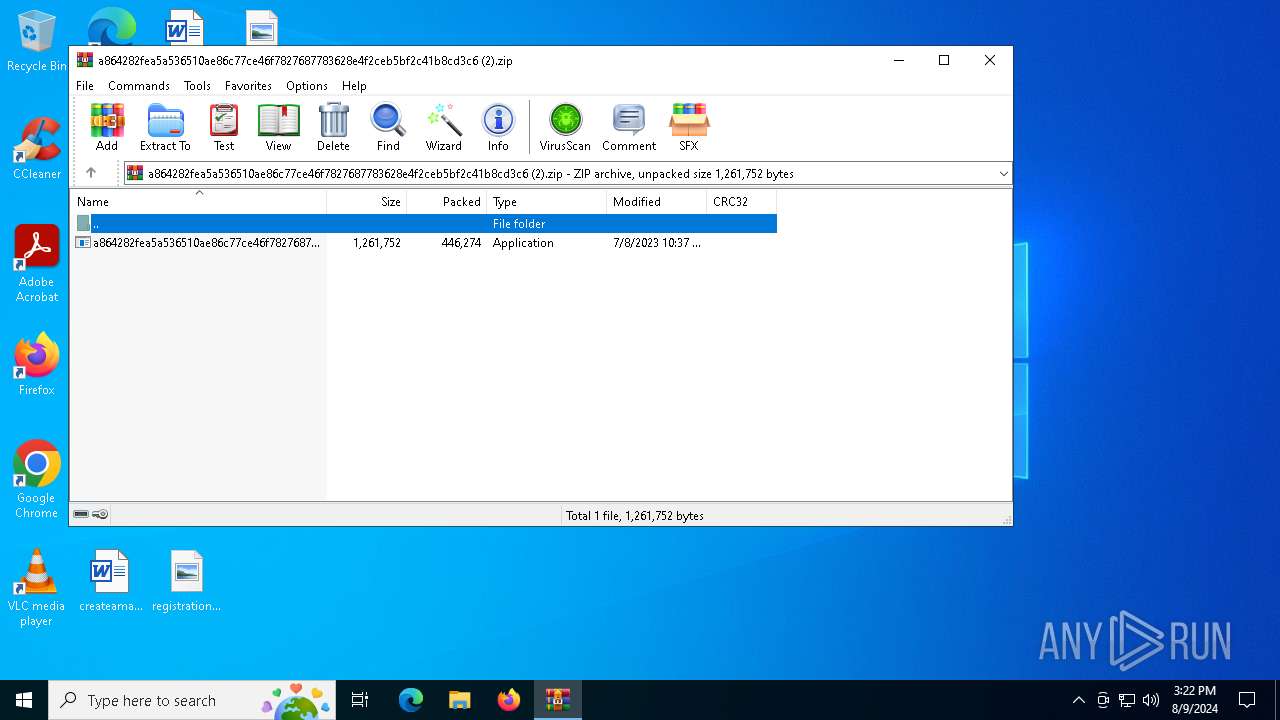
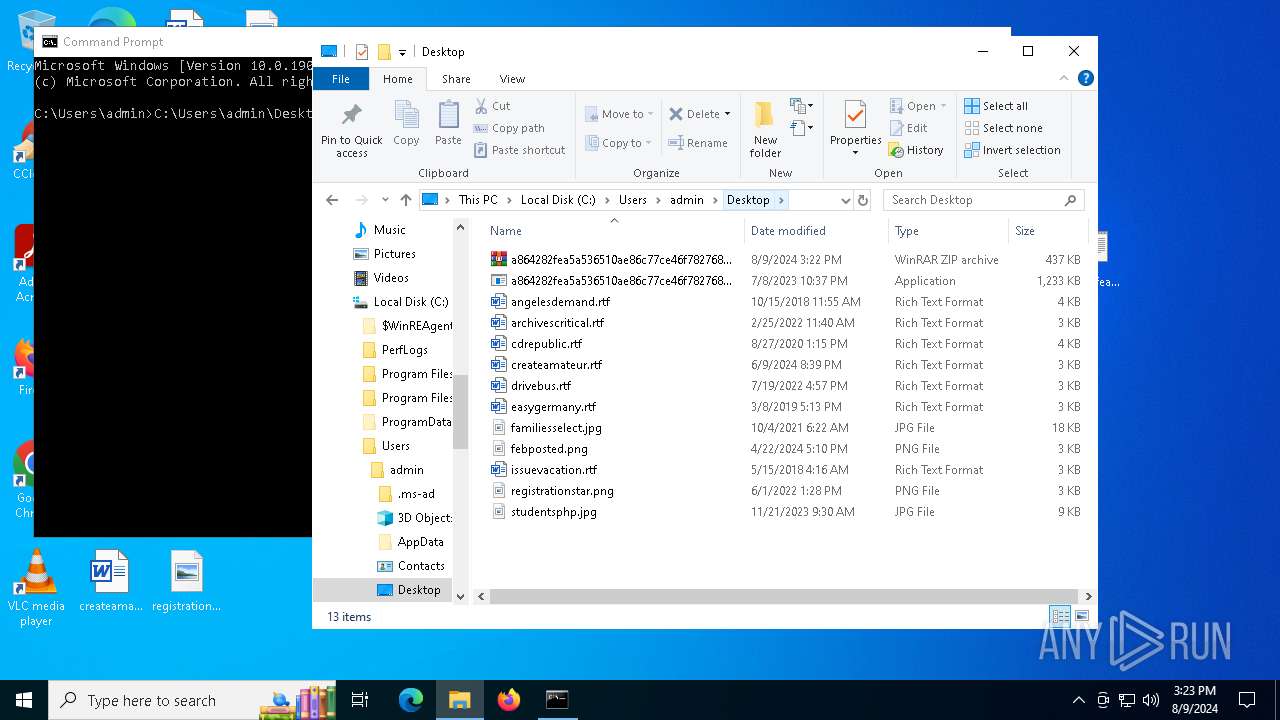
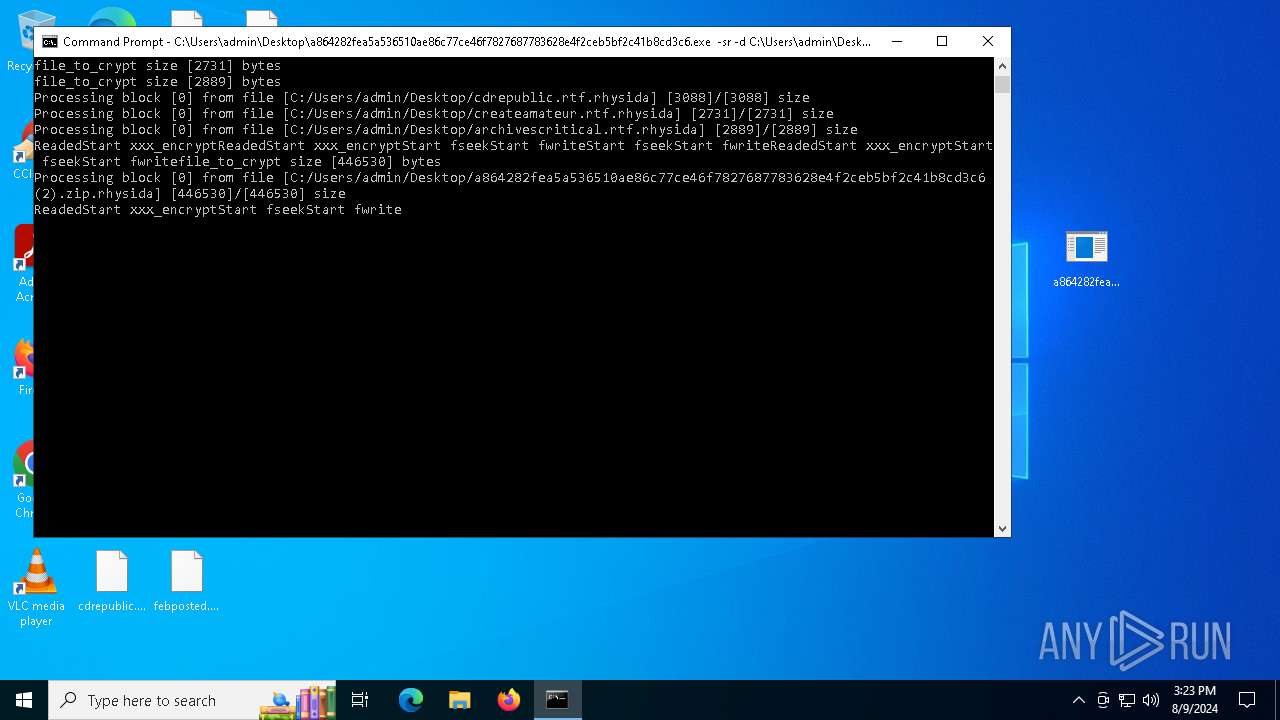
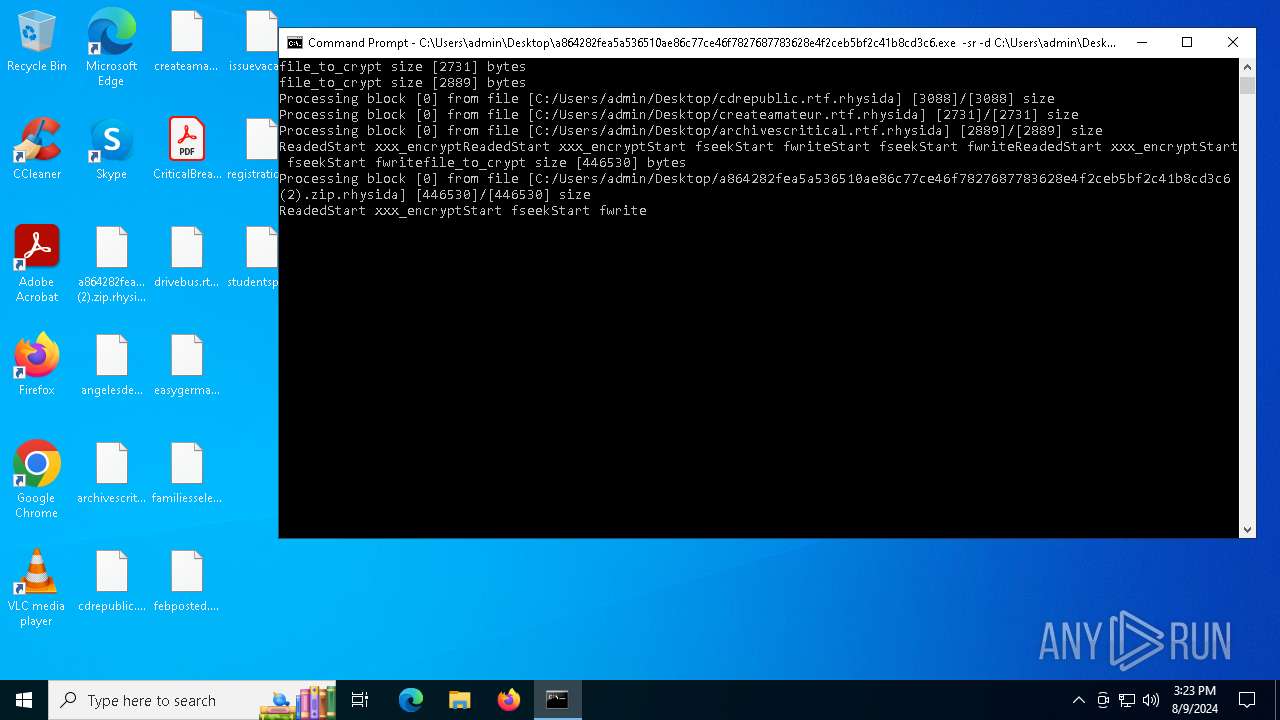
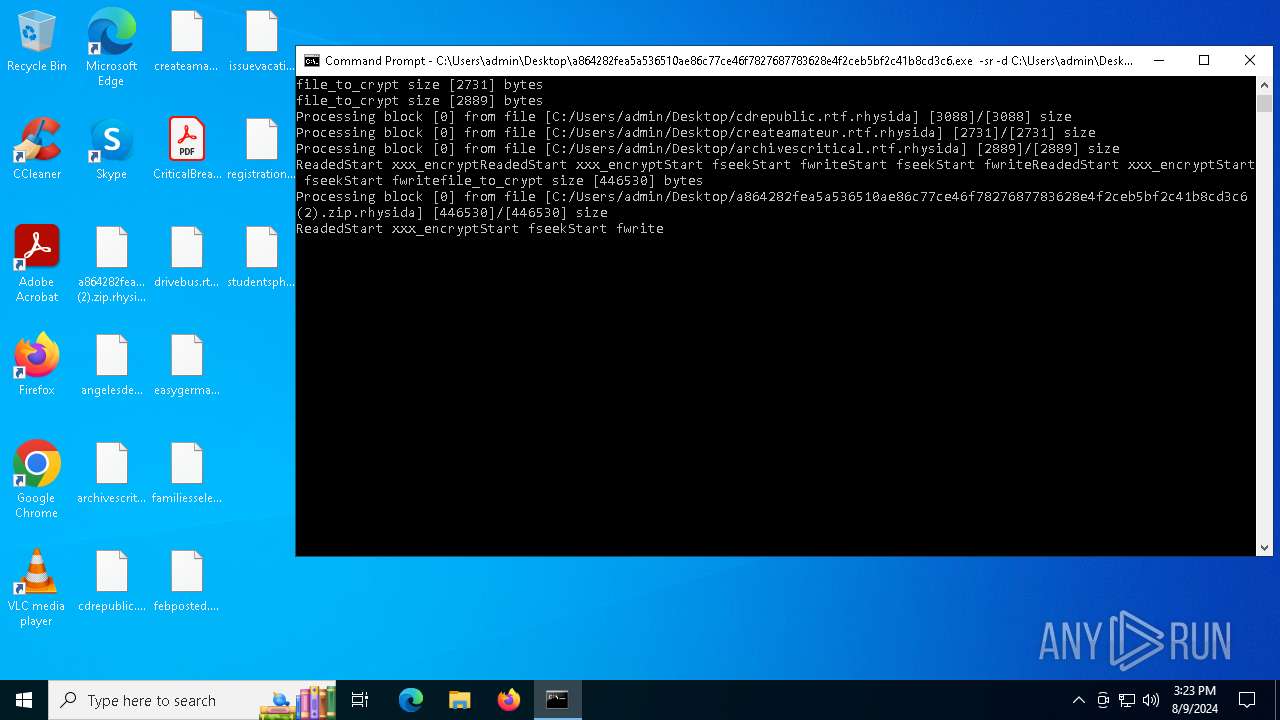
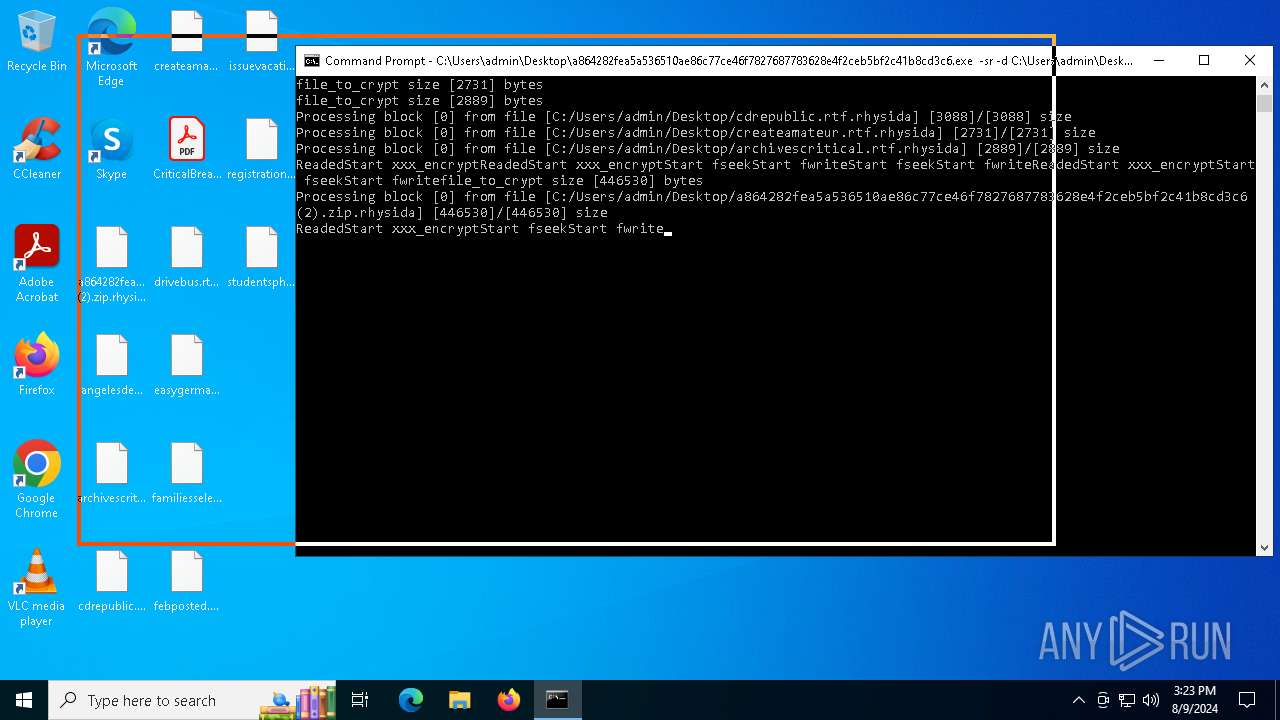
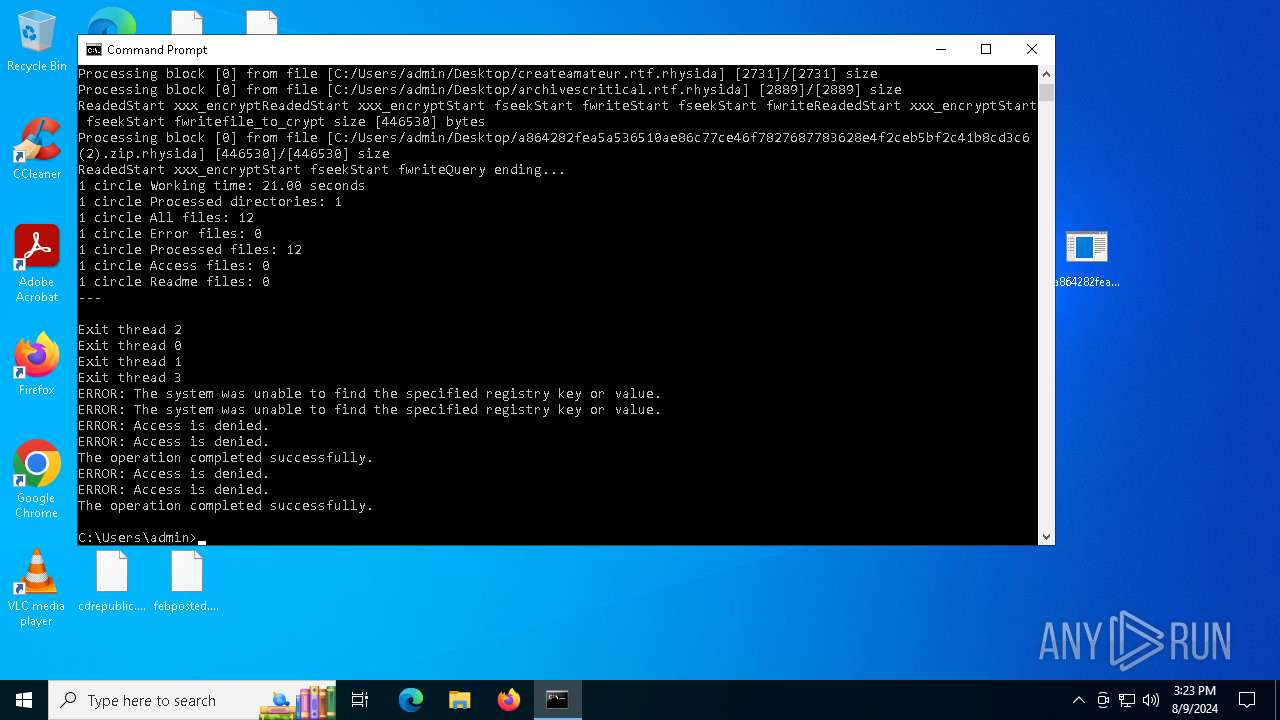
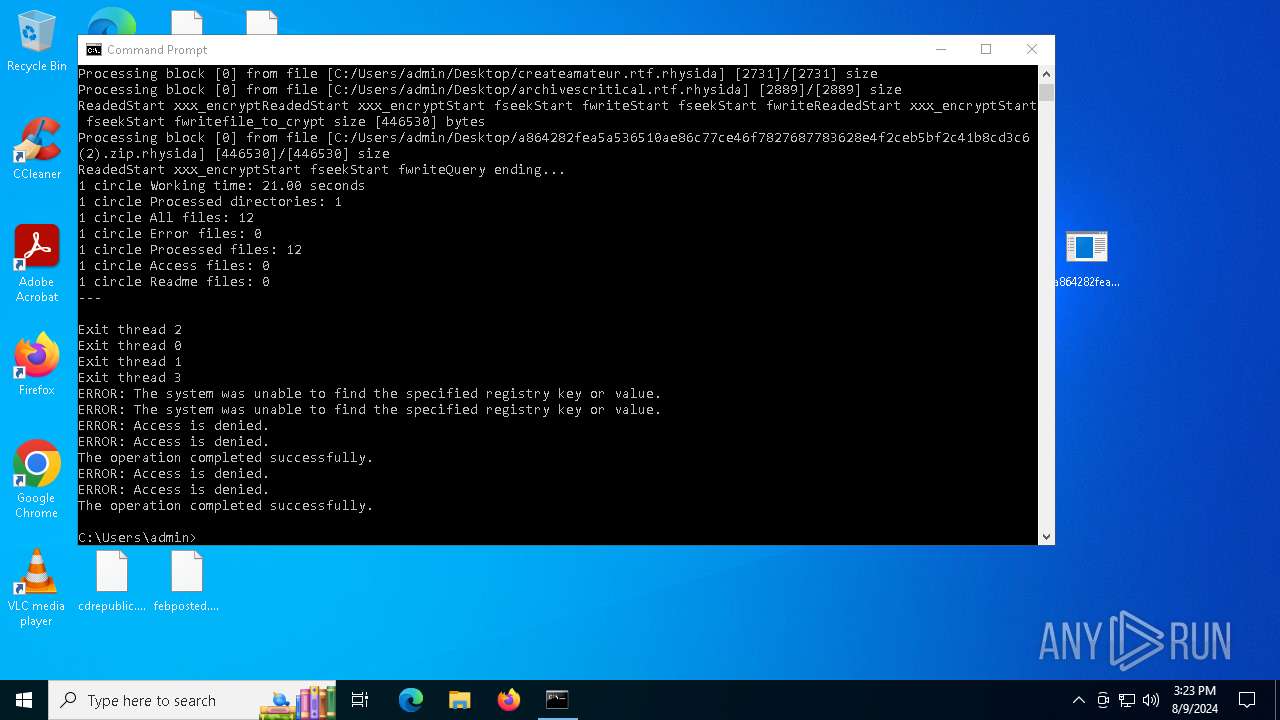
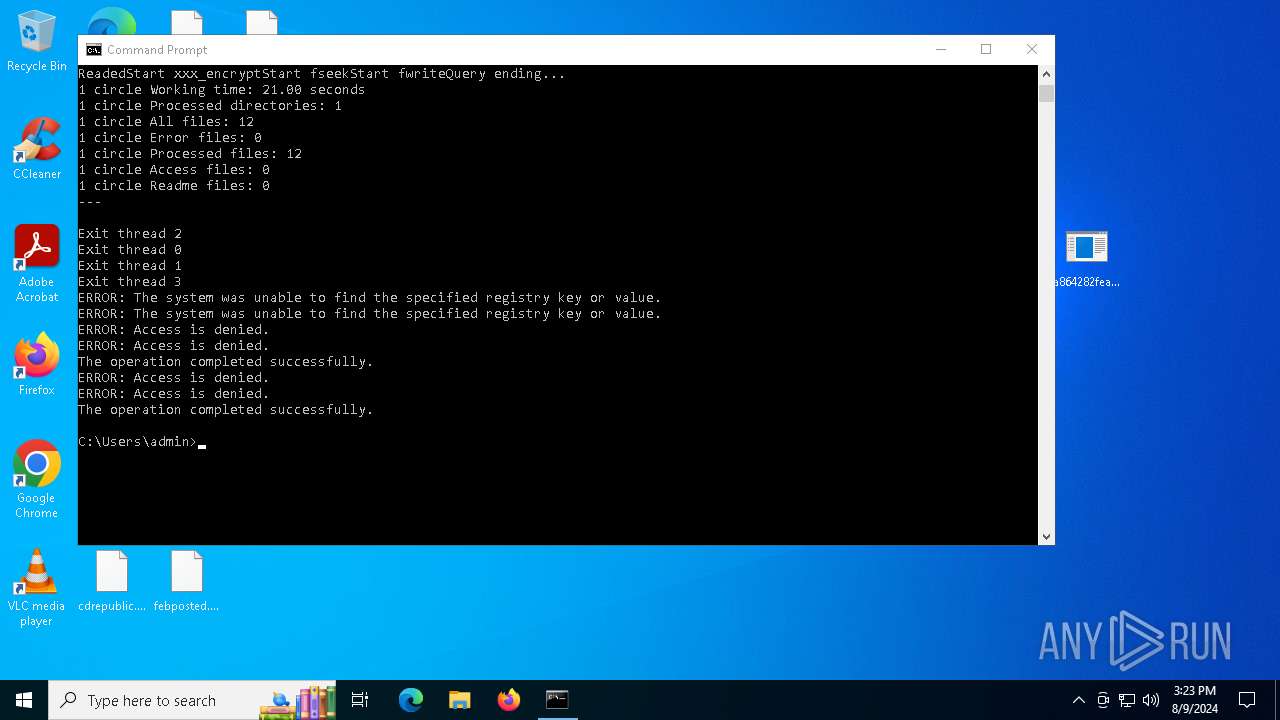
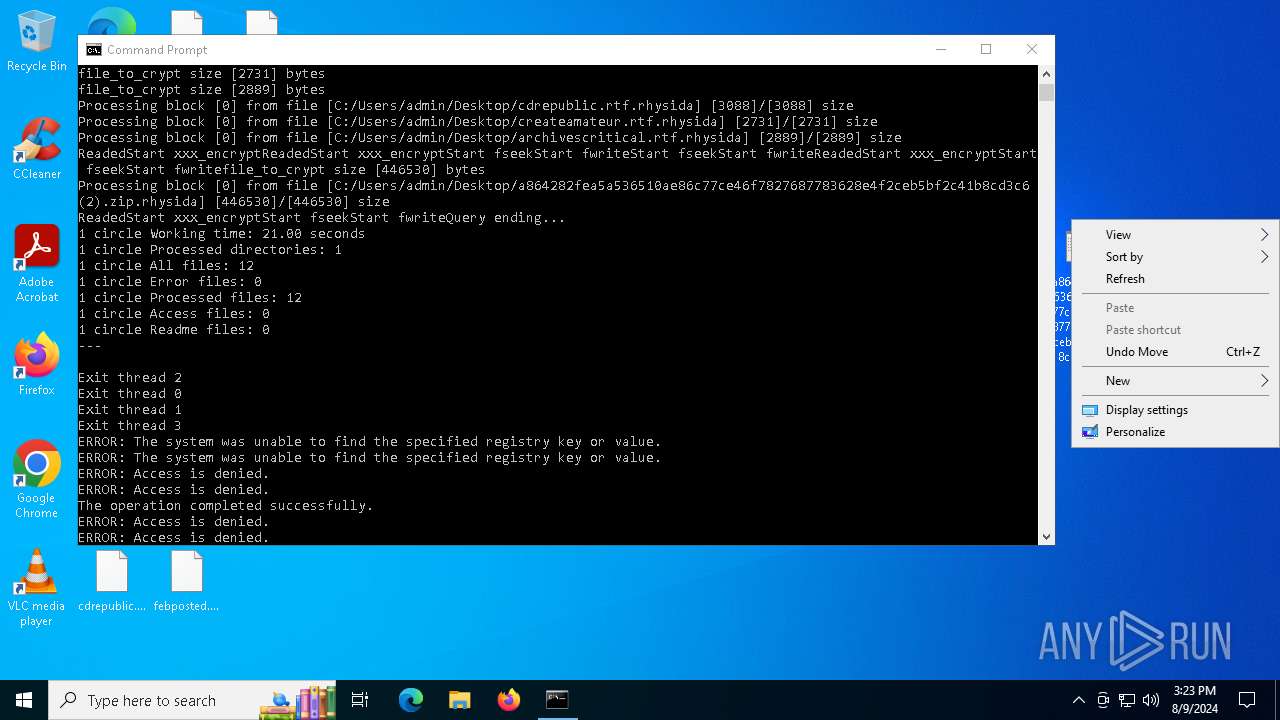
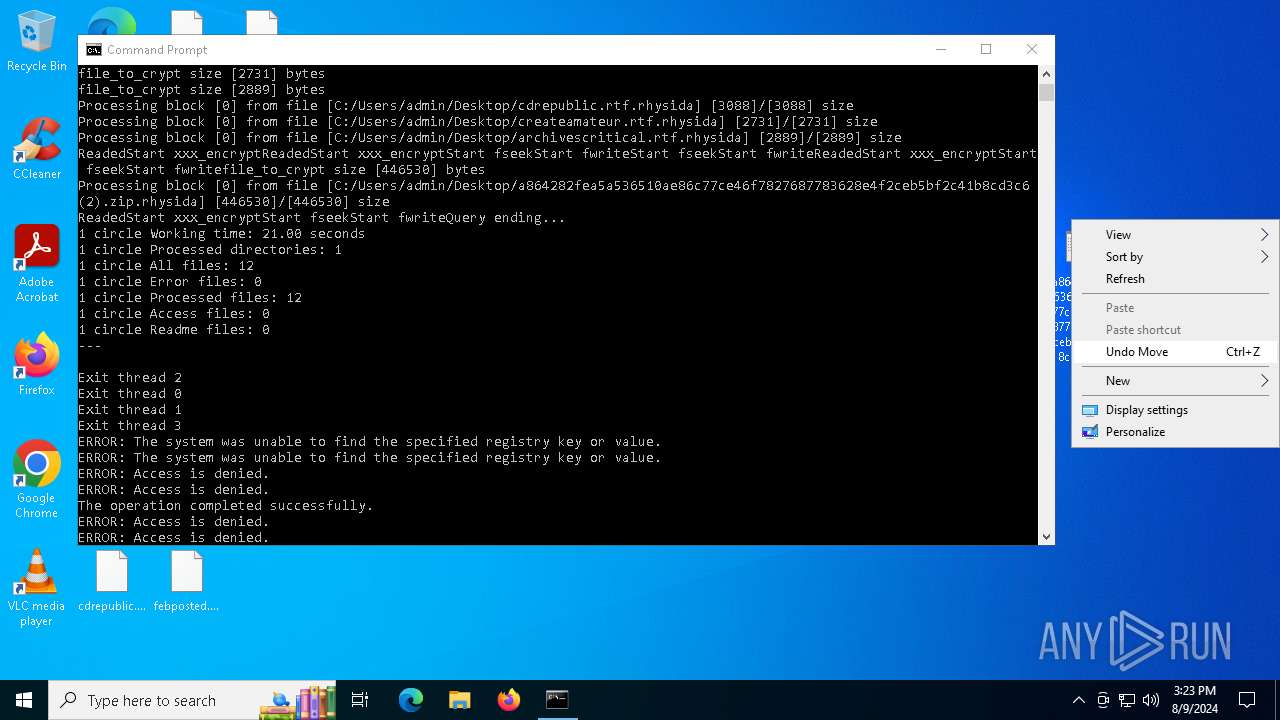
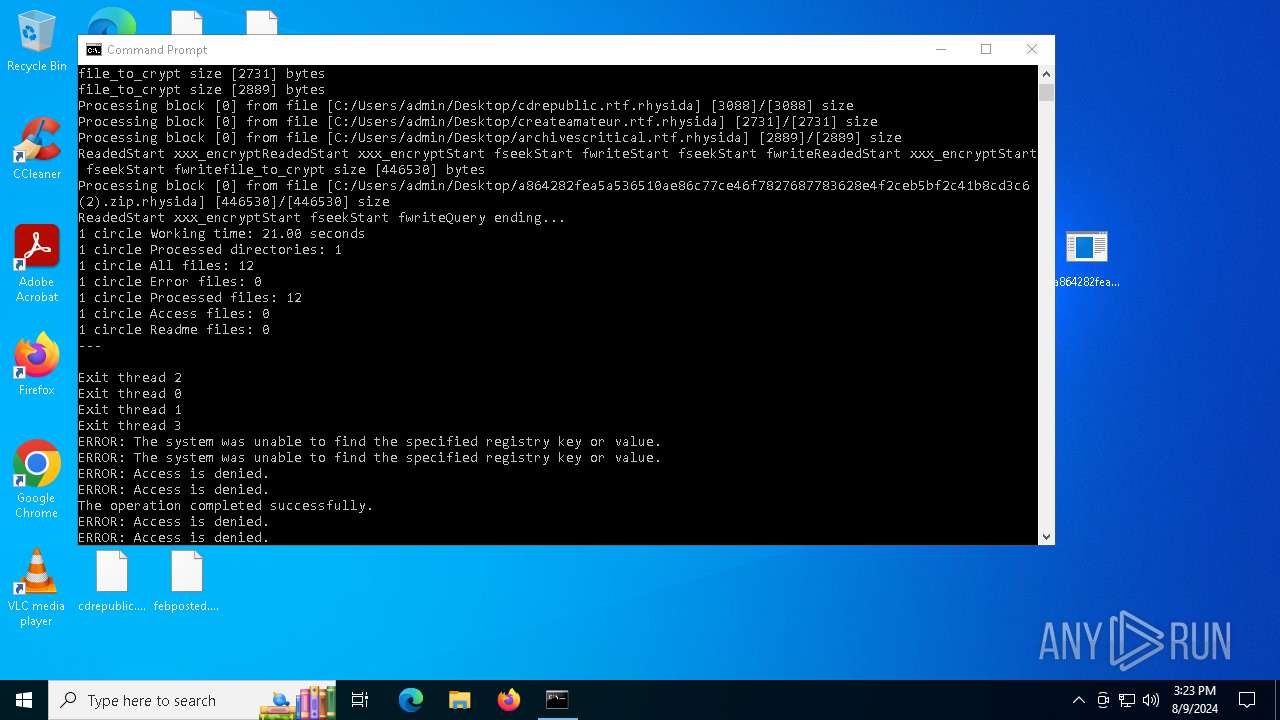
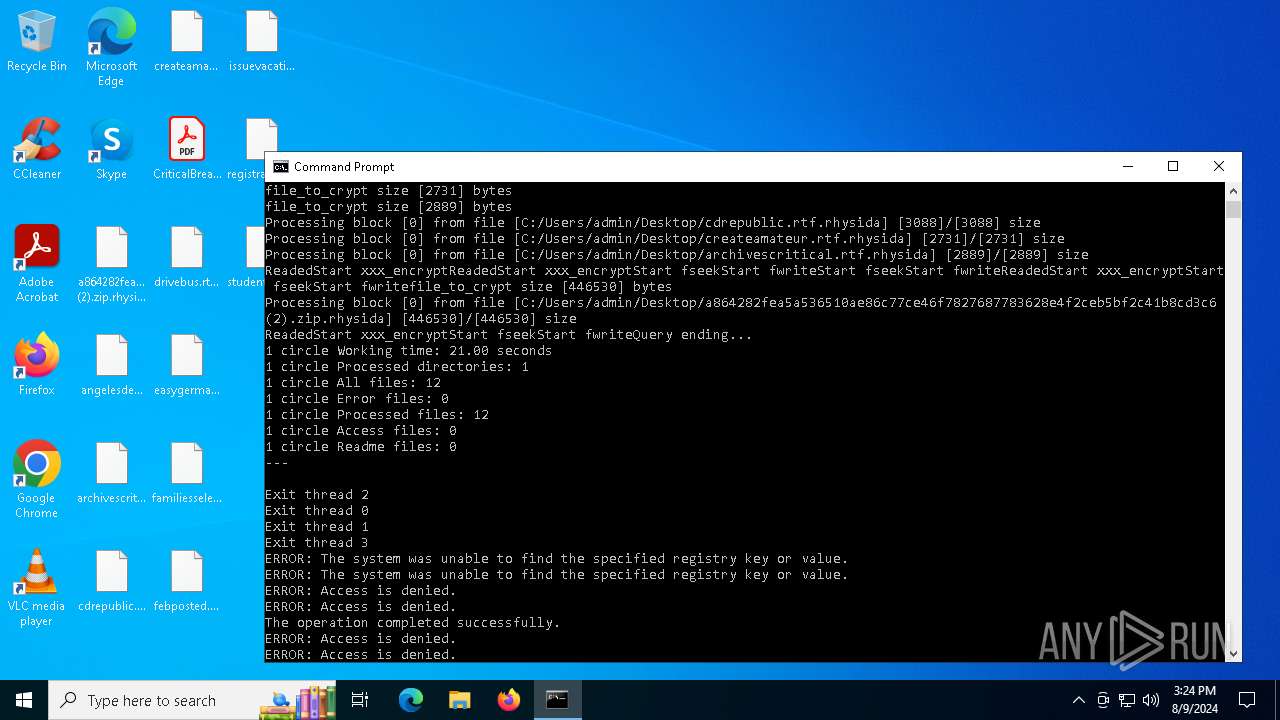
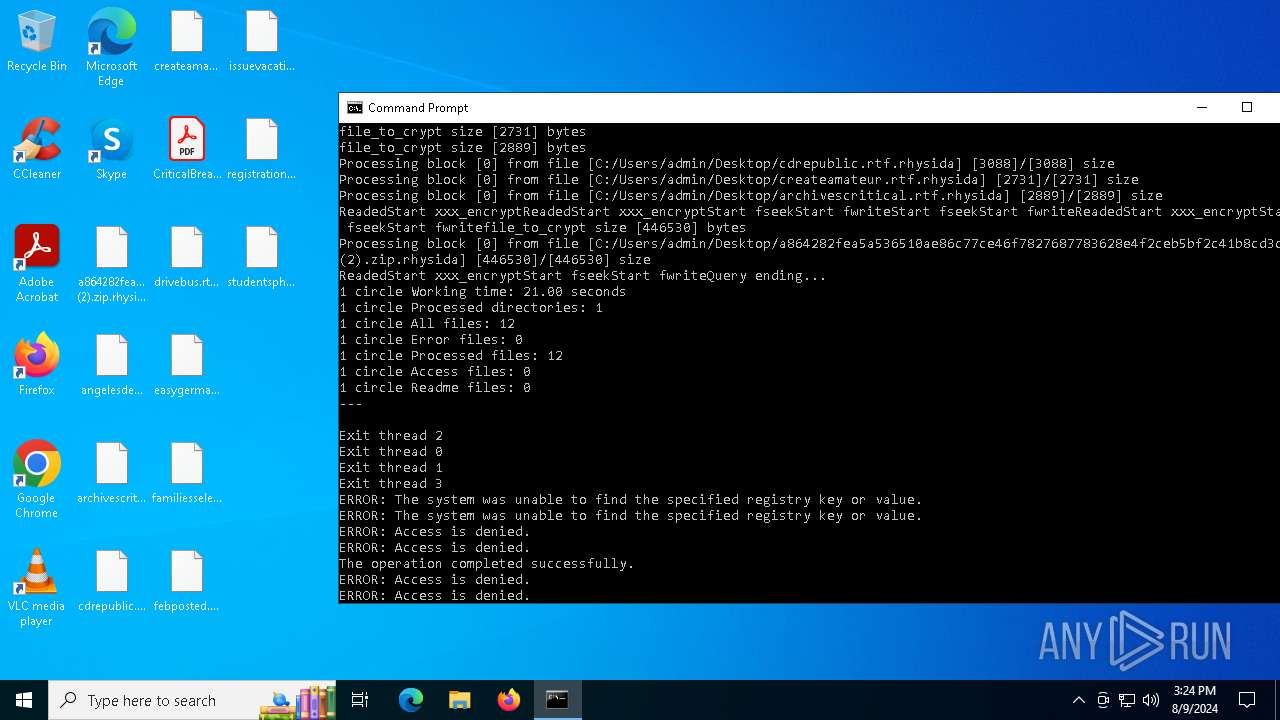
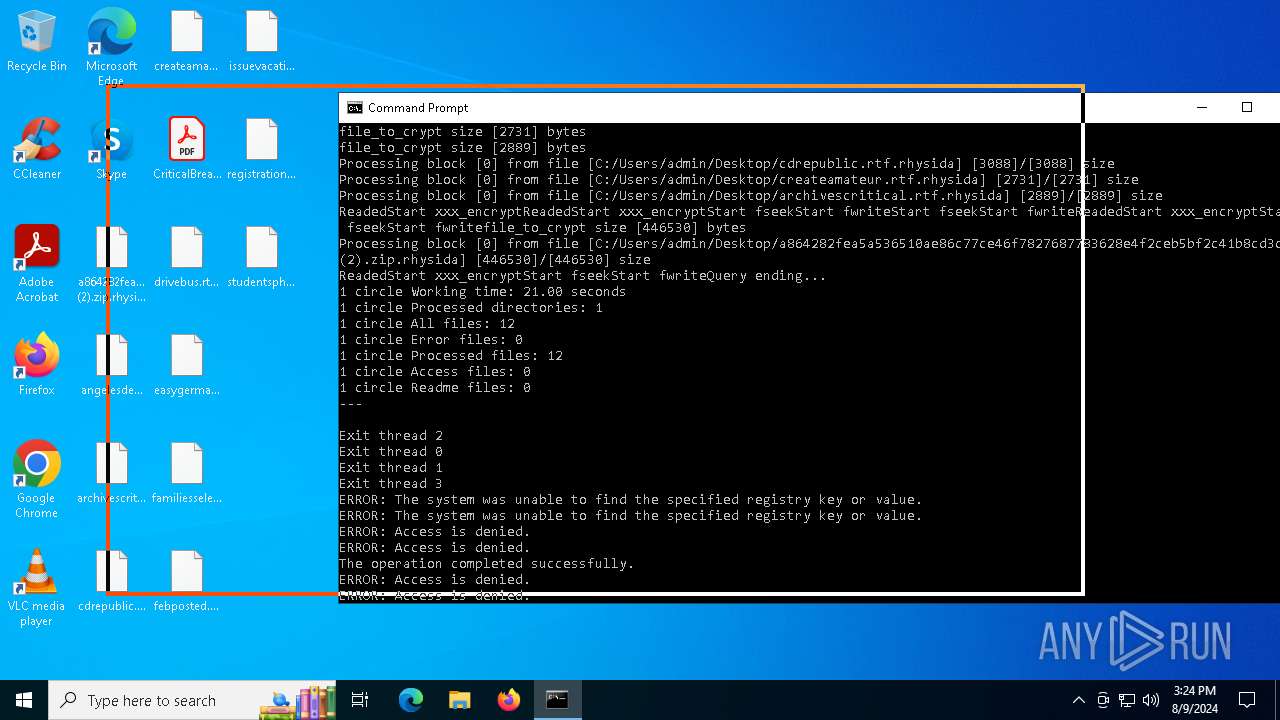
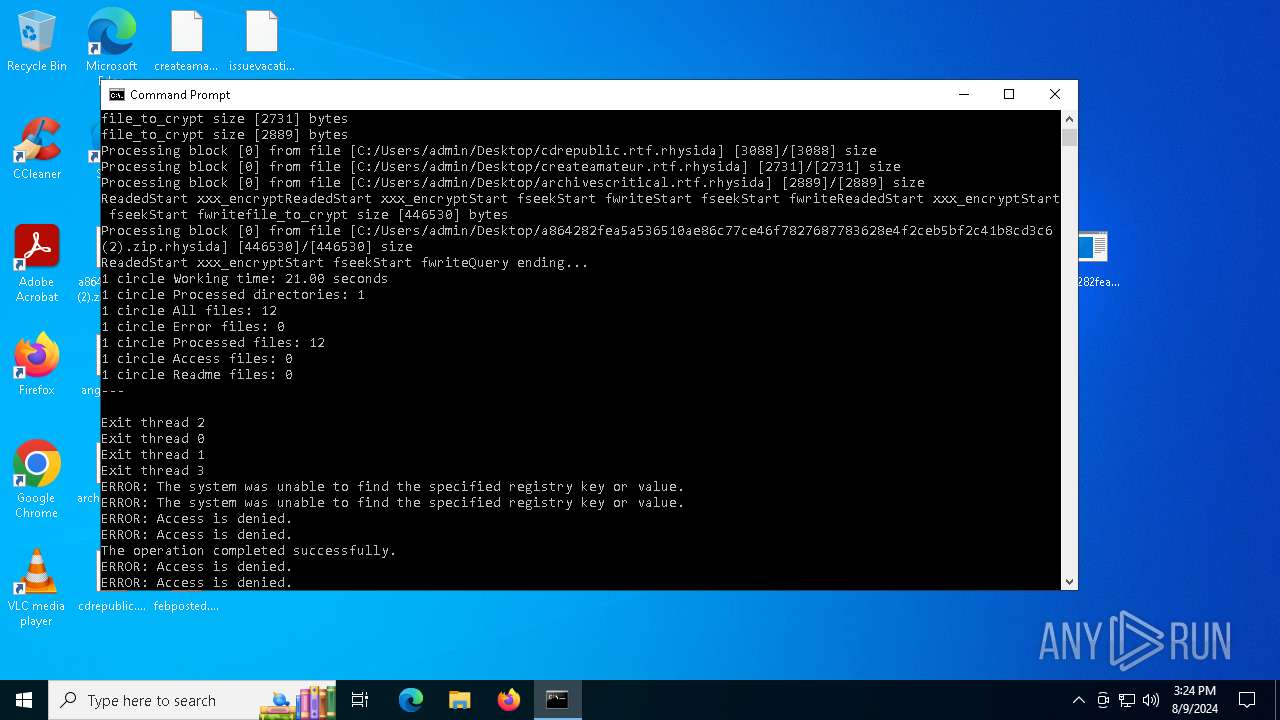
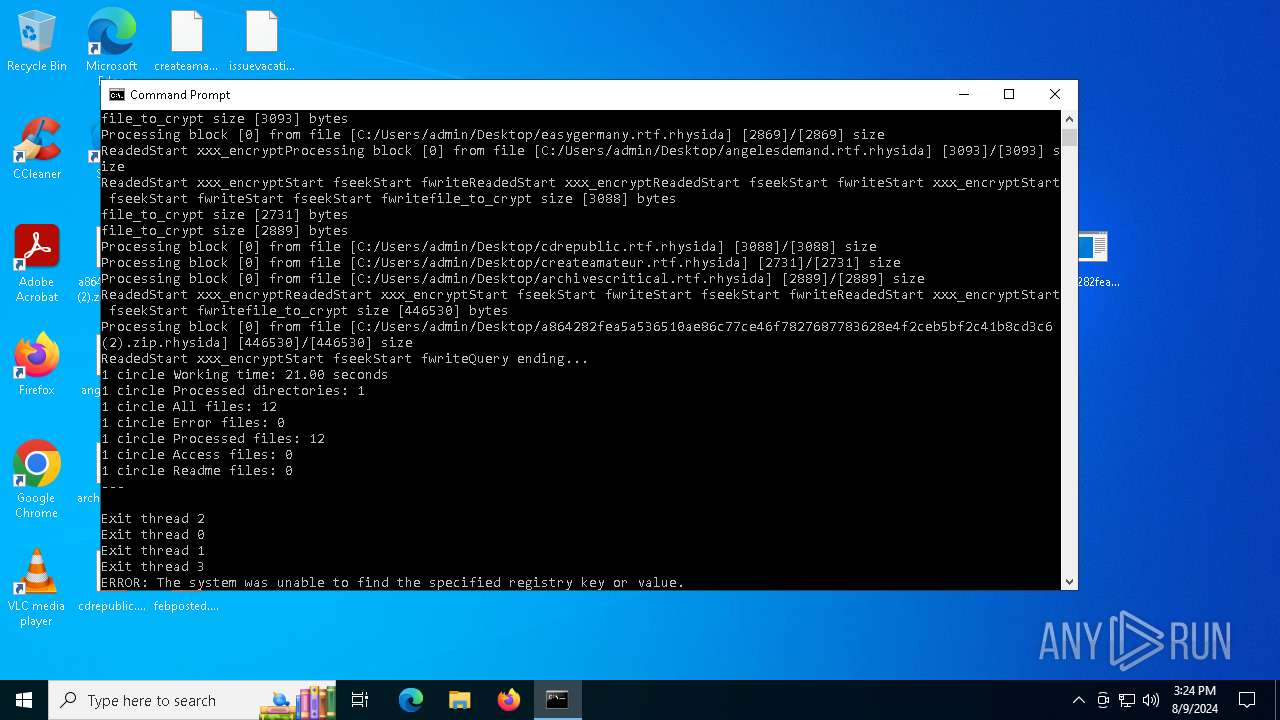
| File name: | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6 (2).zip |
| Full analysis: | https://app.any.run/tasks/d7601448-bbc0-4041-8d7d-38182675d7d0 |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2024, 15:22:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
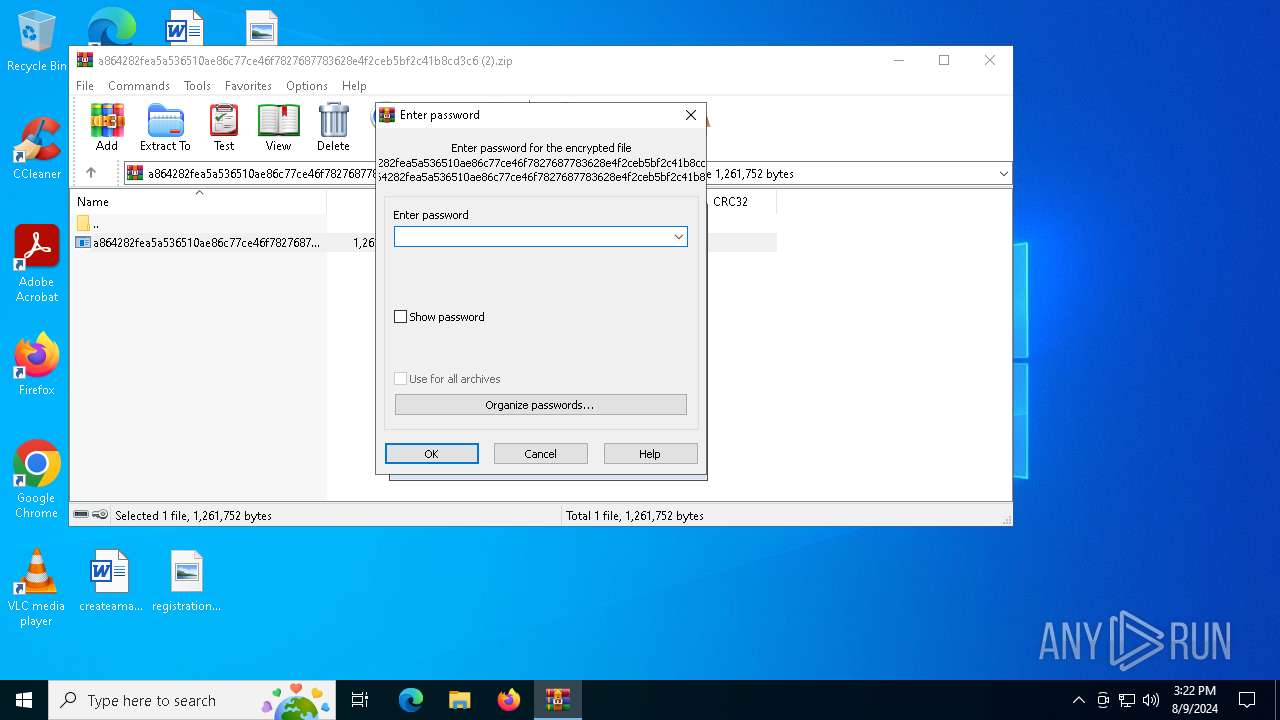
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 2C9E9F65F00363CD648D5C866483A6BB |
| SHA1: | CF5018D36363A5BDBEA4D8BAA768547F16B24483 |
| SHA256: | F1768C9F736C42332C9E195134E0DCCE7C762FD50B7BFC71CB55BF0C3E770A60 |
| SSDEEP: | 6144:OttWV7qEogQRPS8qq9vZbGYnc9+uLyOFfllOzAHnu5rojhPgfUTS5+xufl:OfGMPRTqYutL/hH4ojhxTK4ufl |
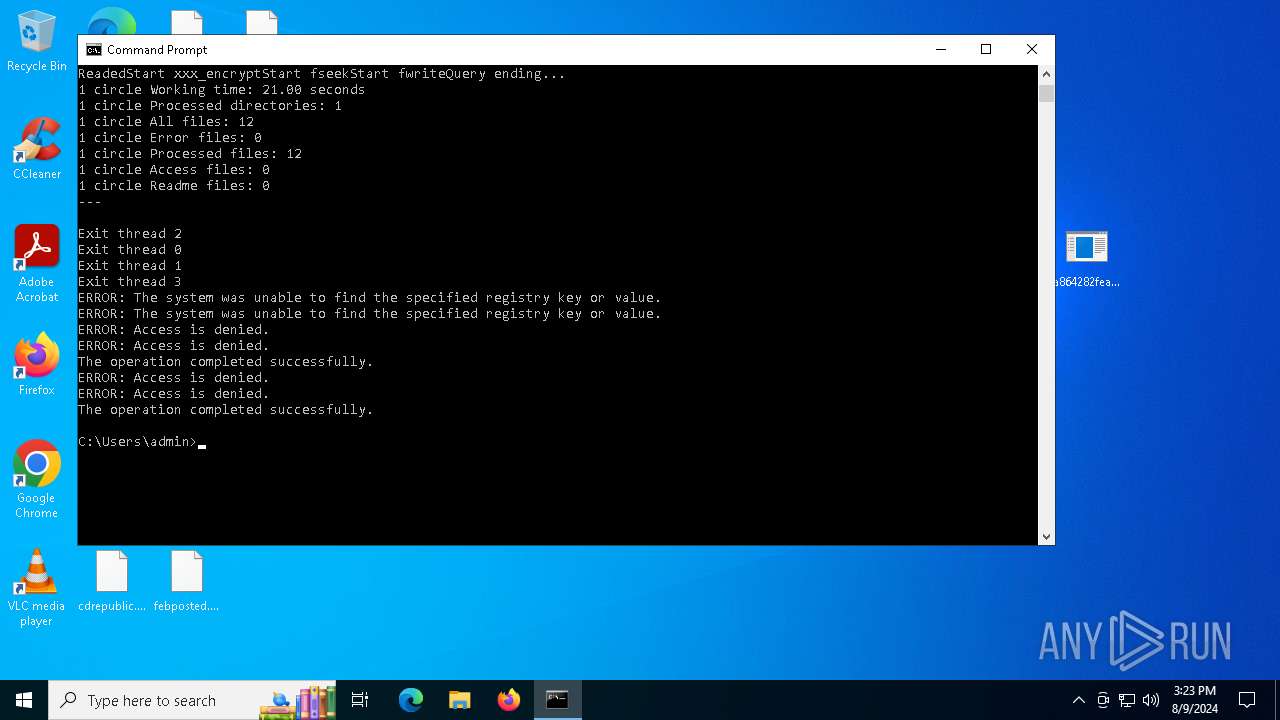
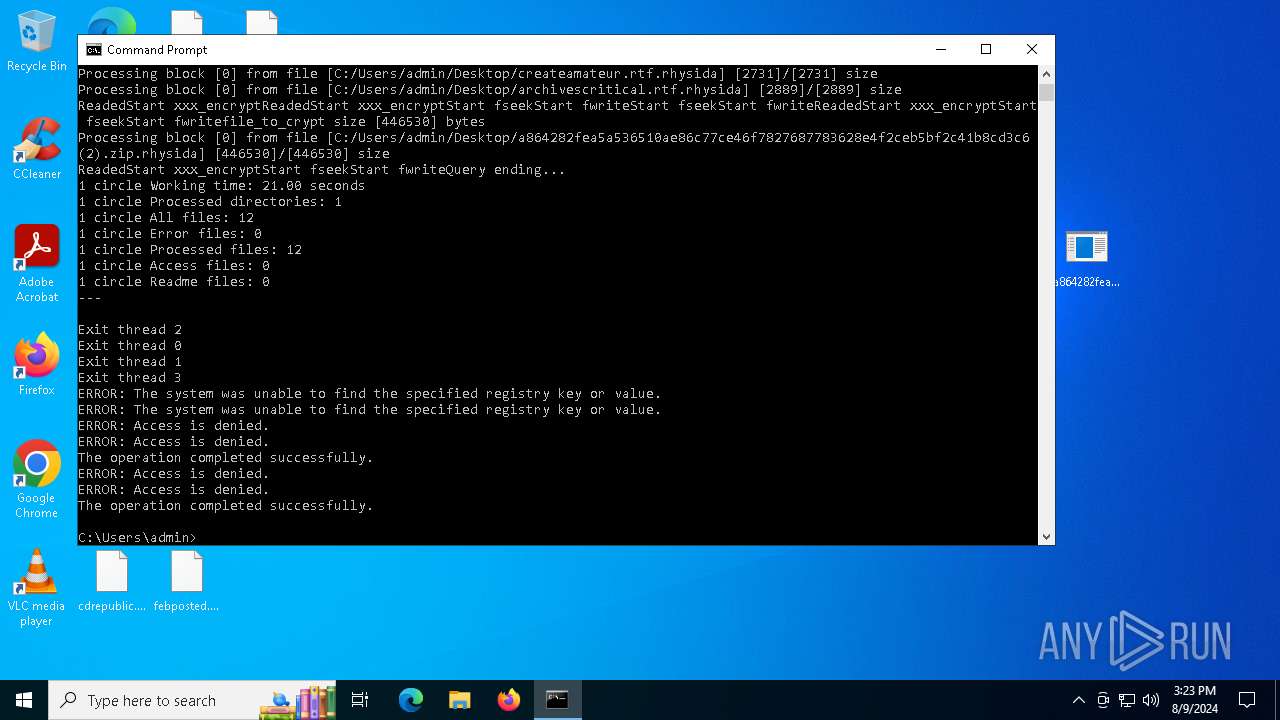
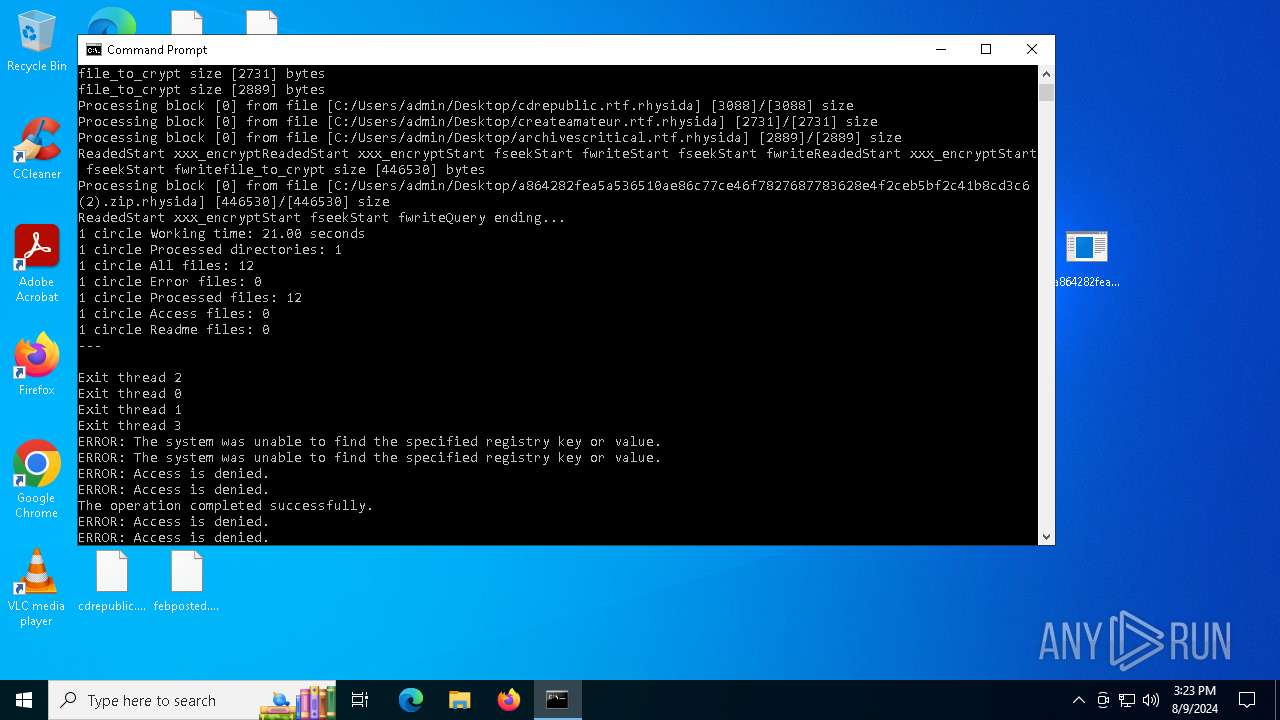
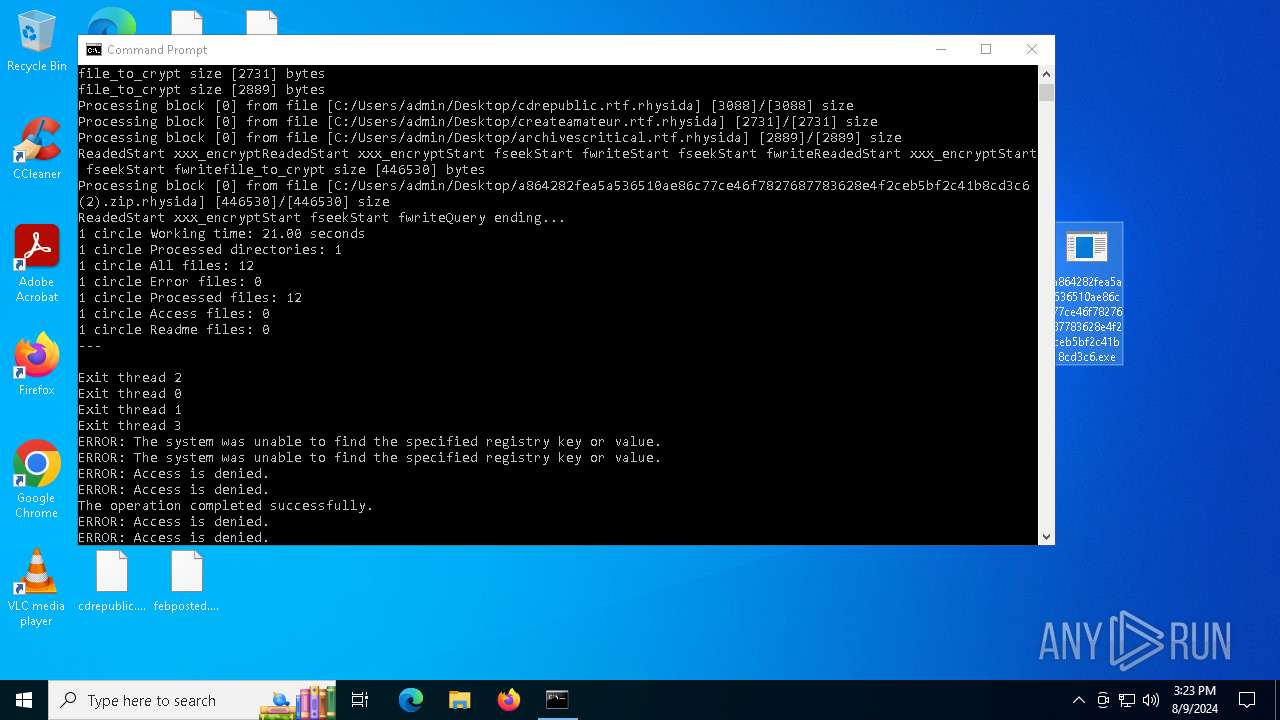
MALICIOUS
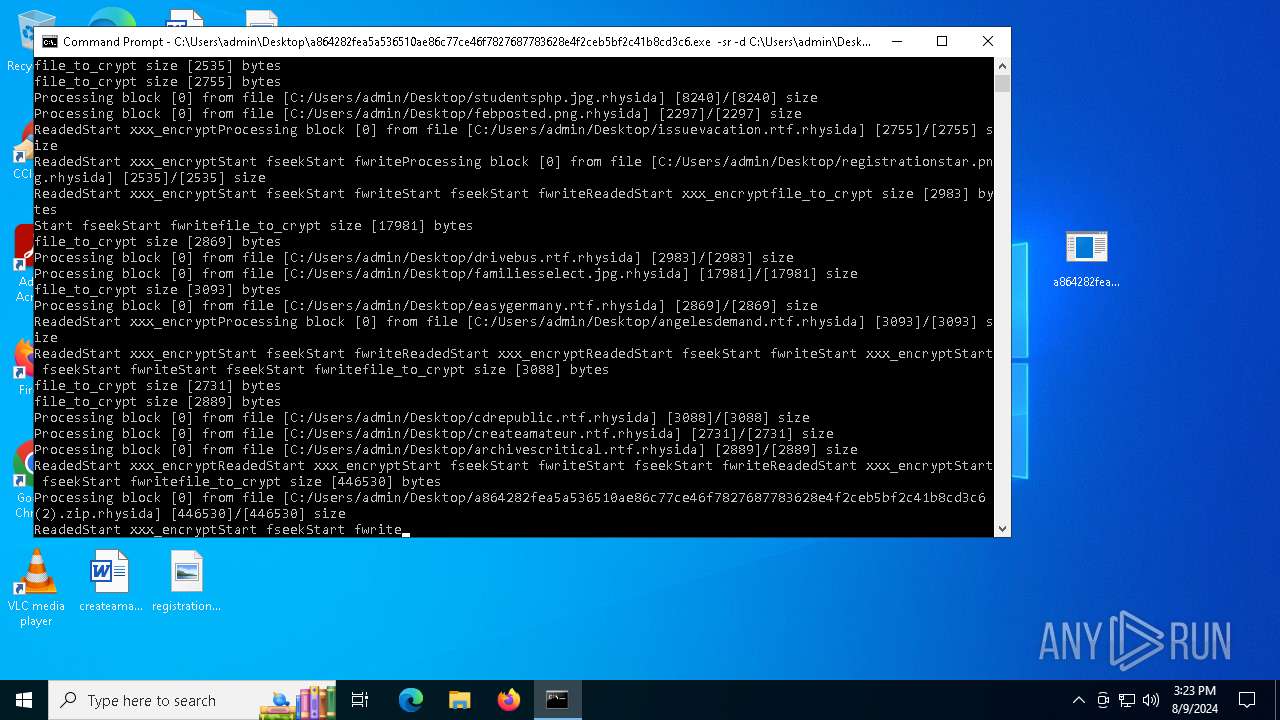
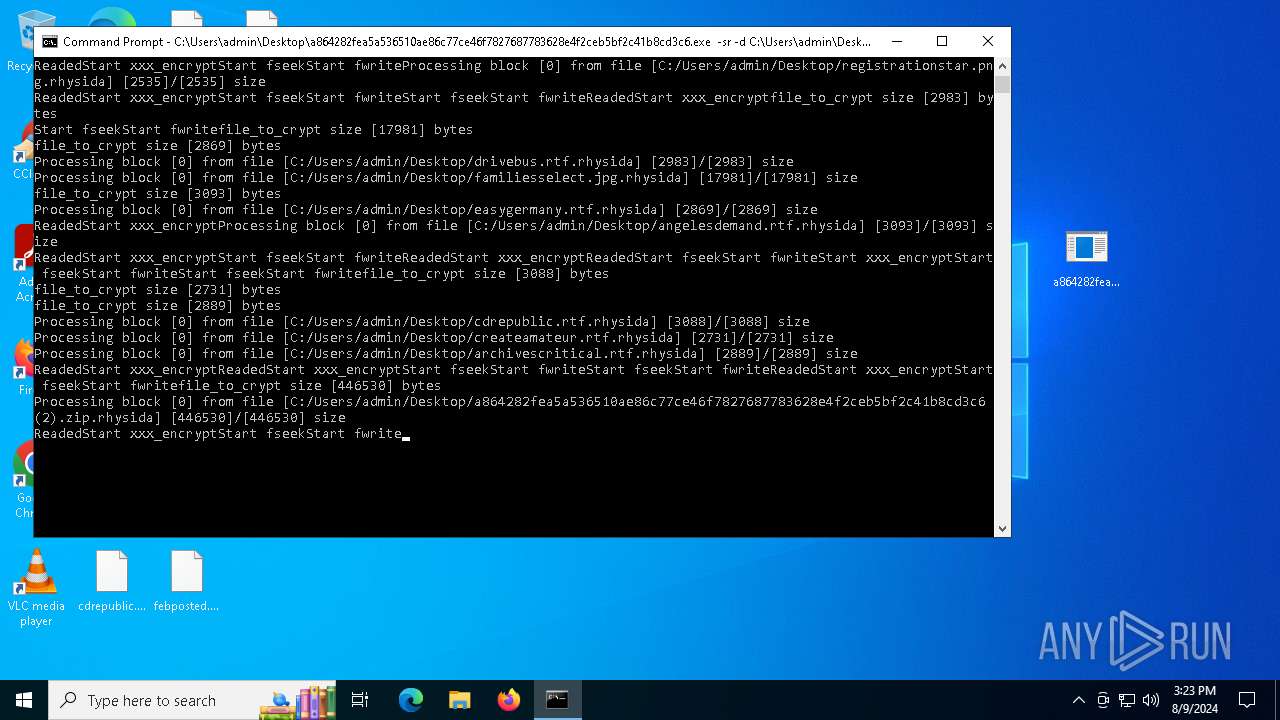
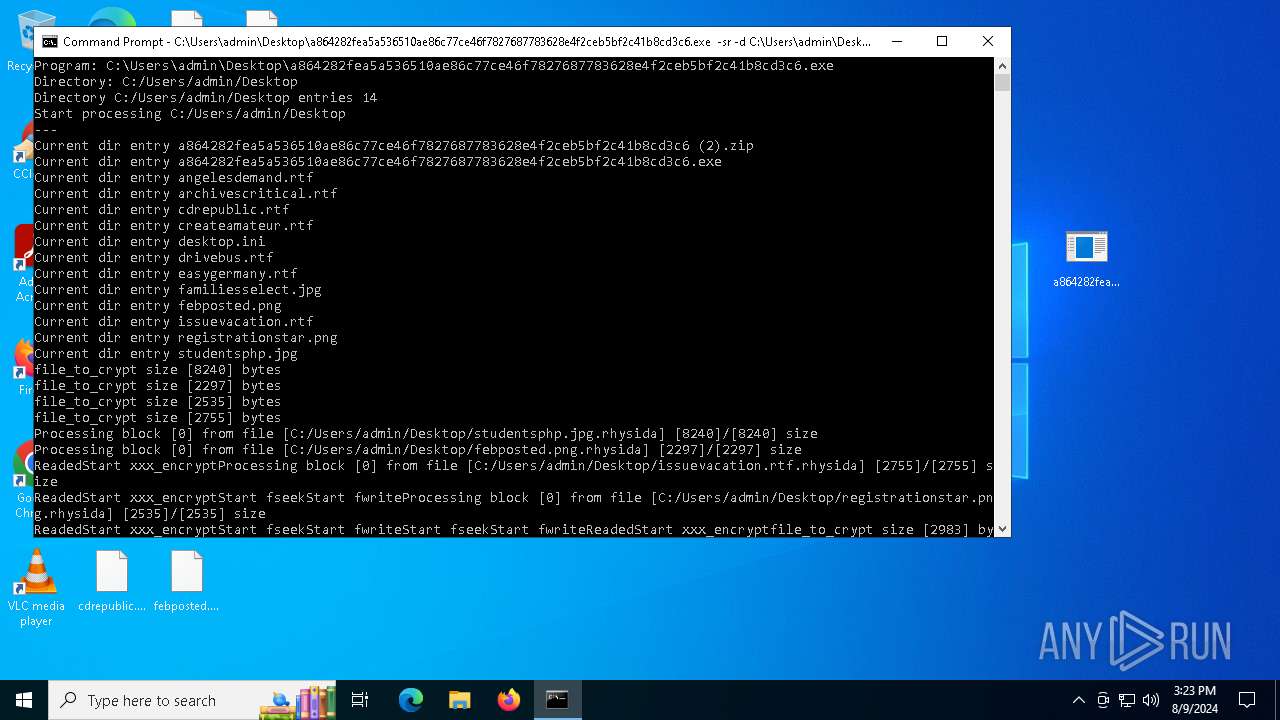
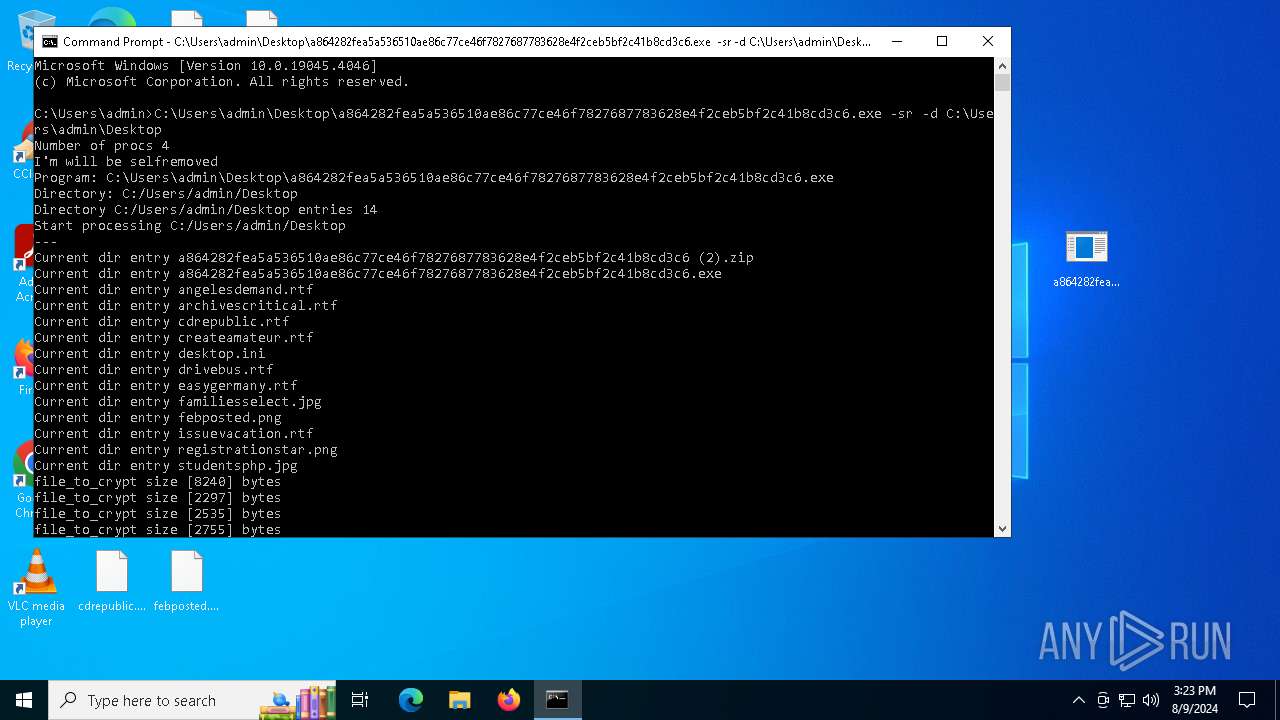
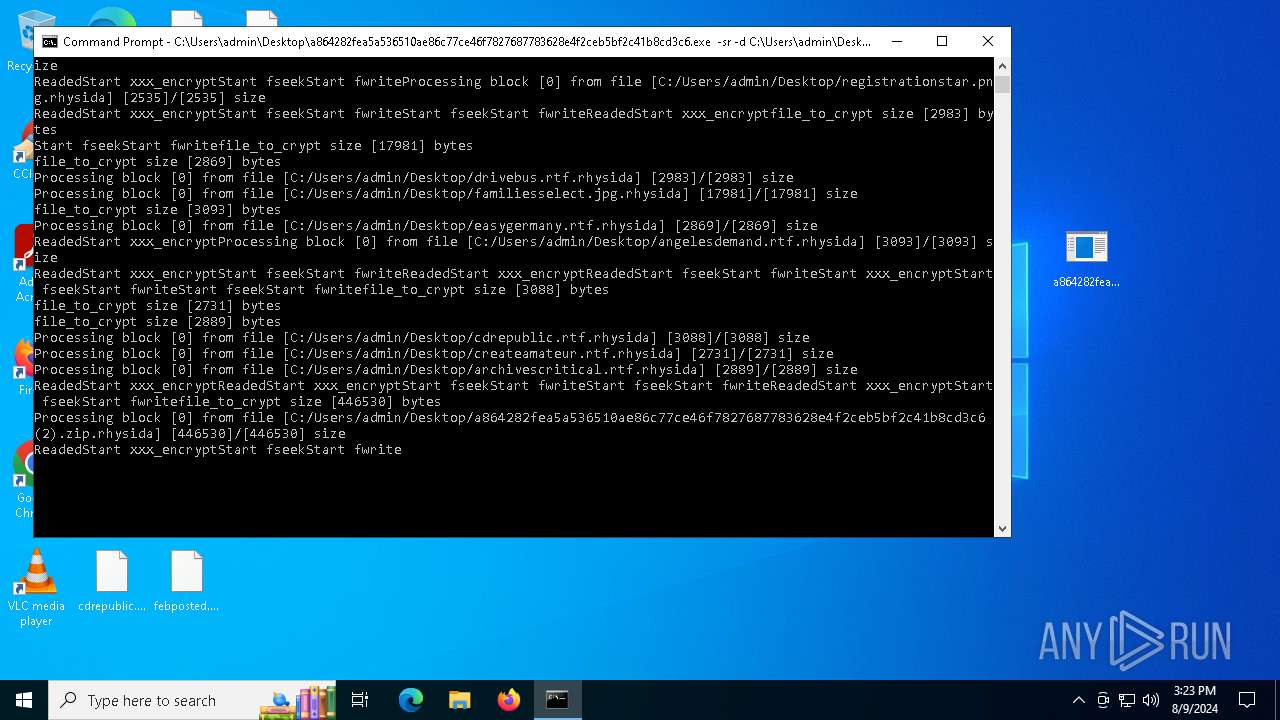
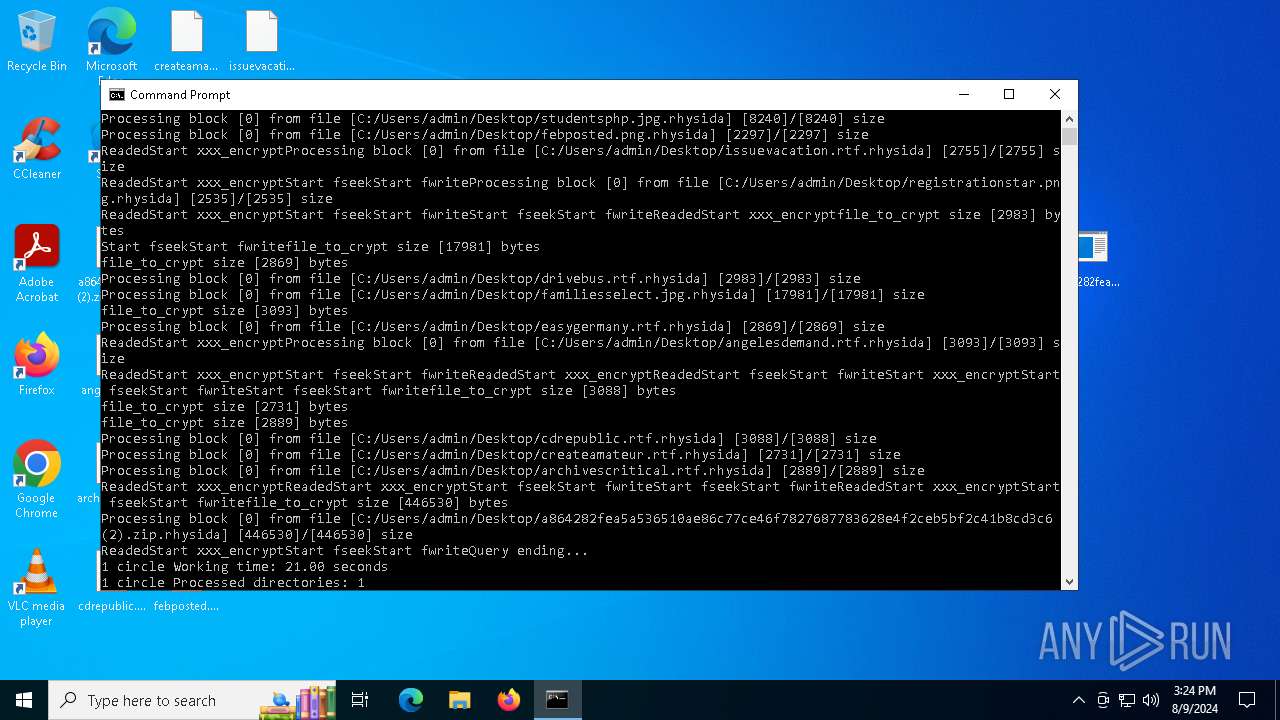
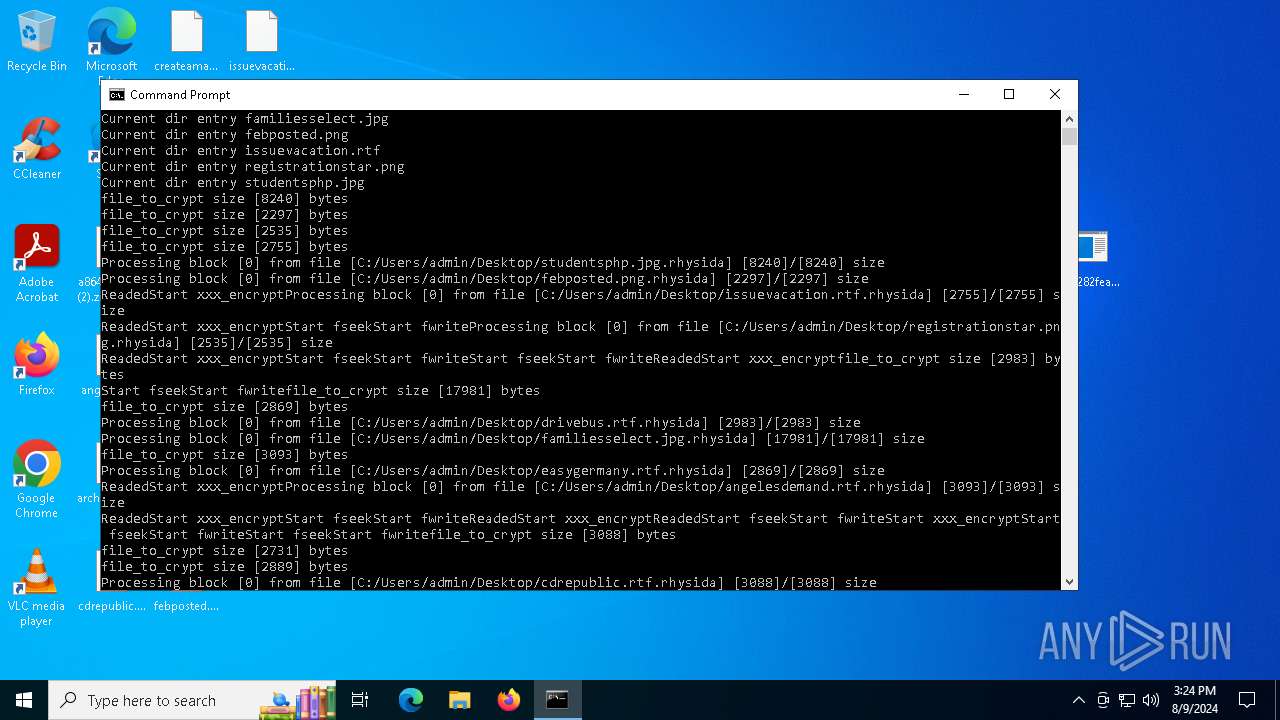
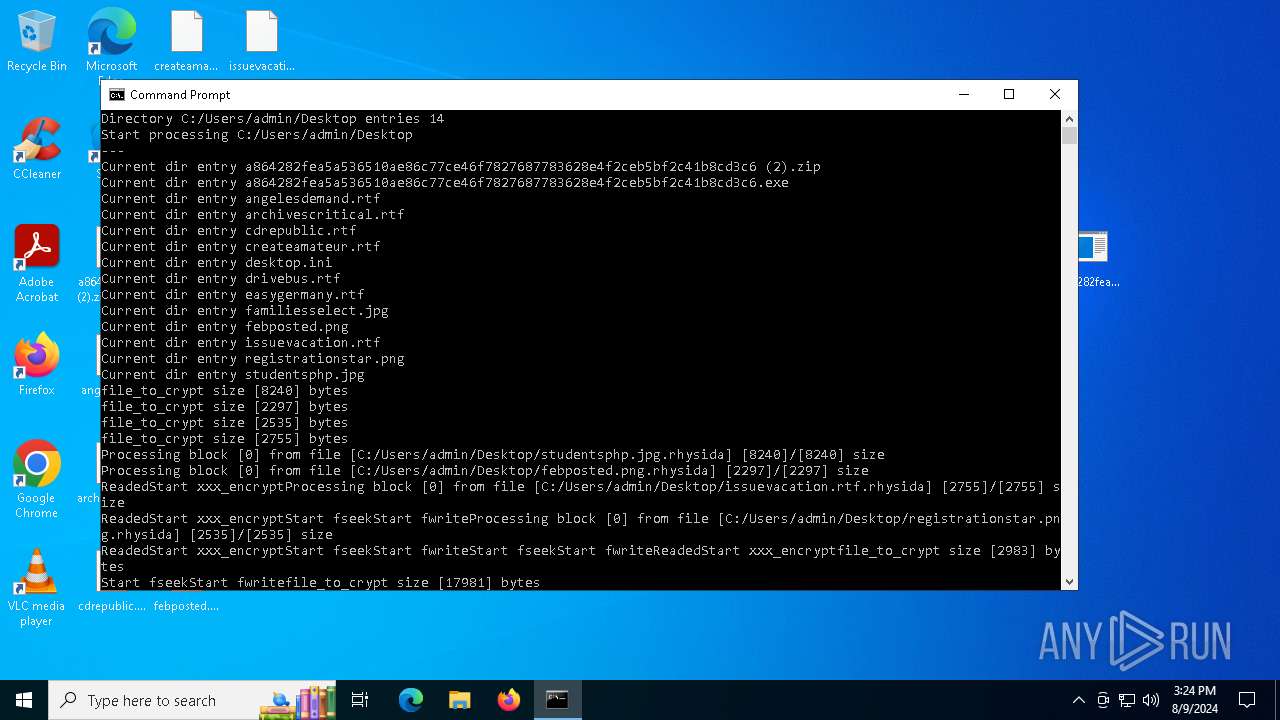
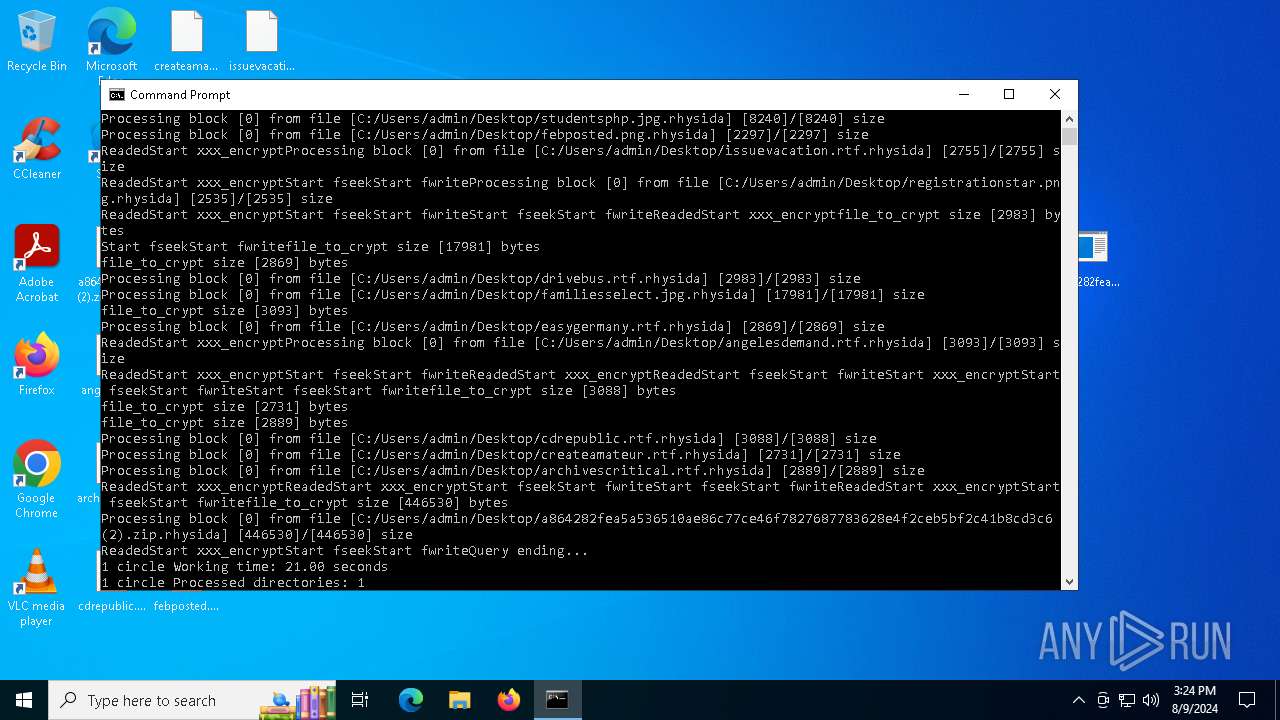
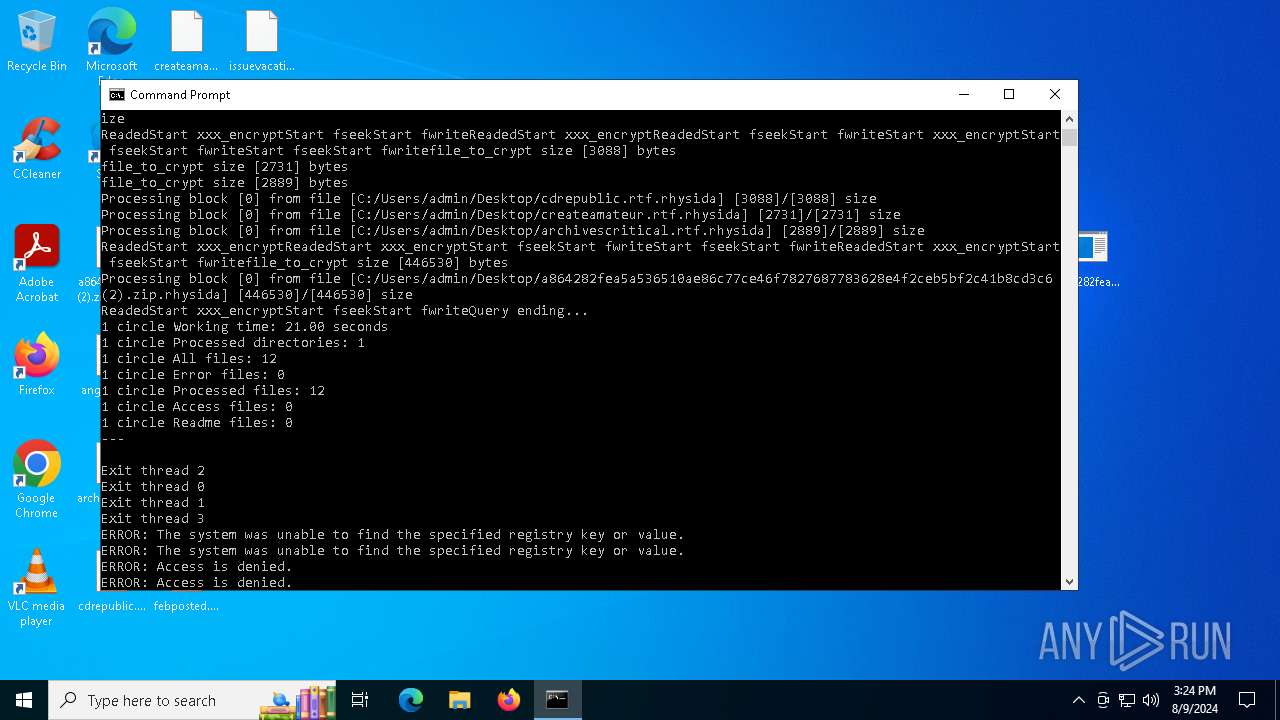
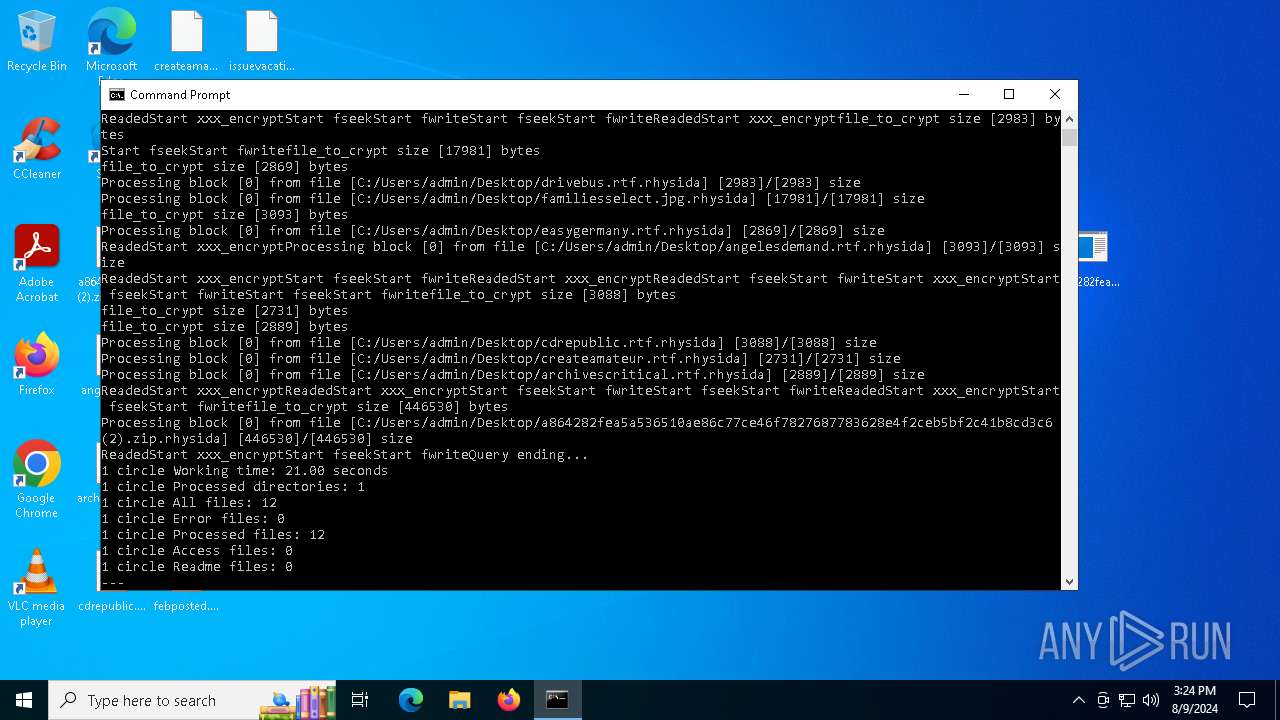
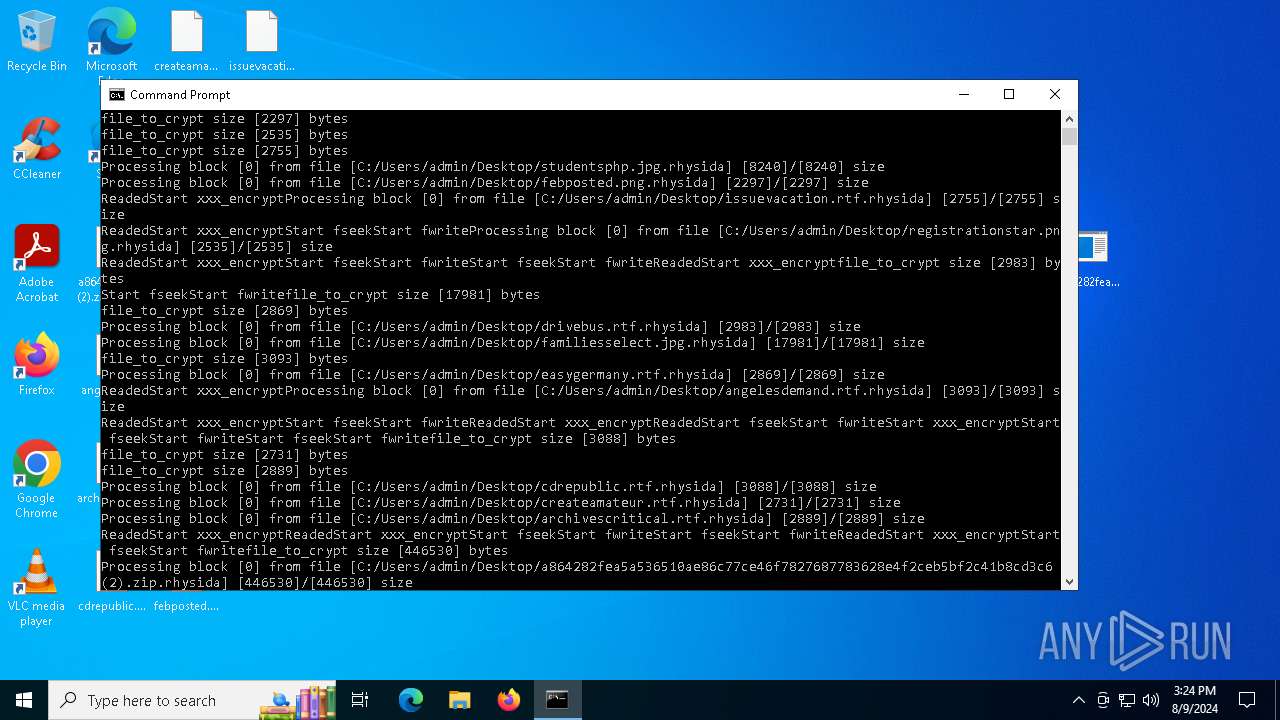
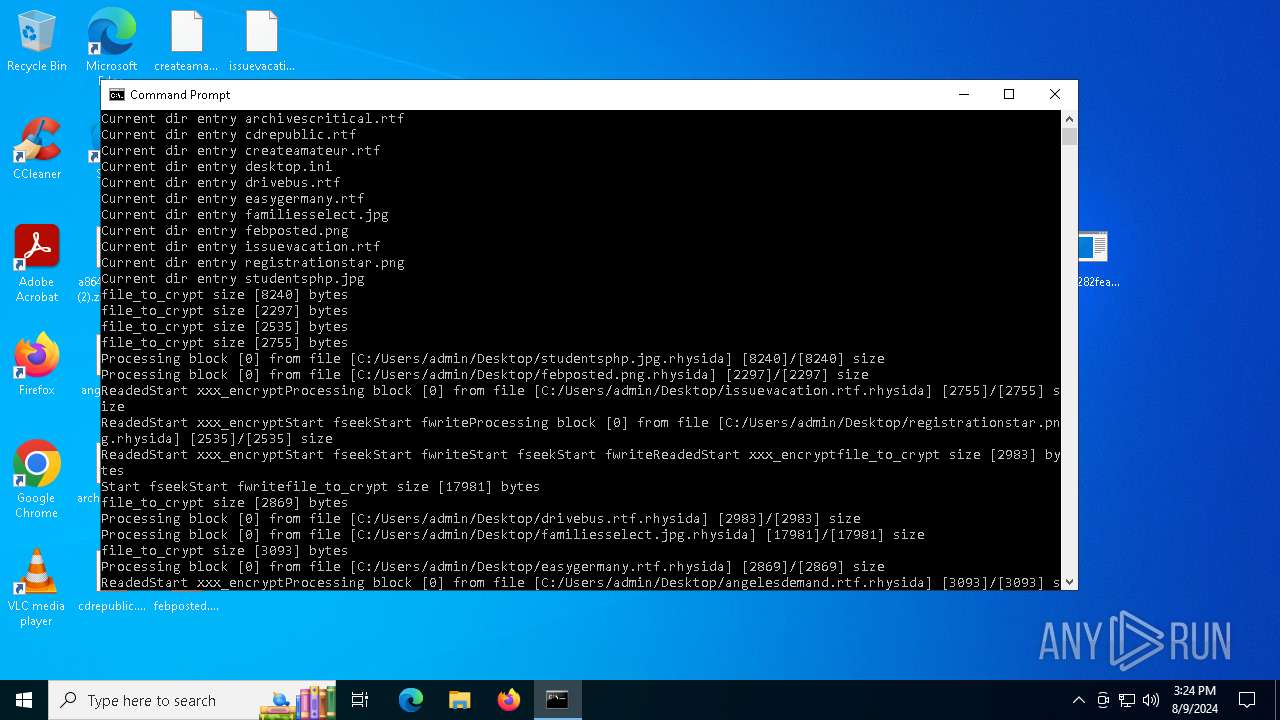
Renames files like ransomware
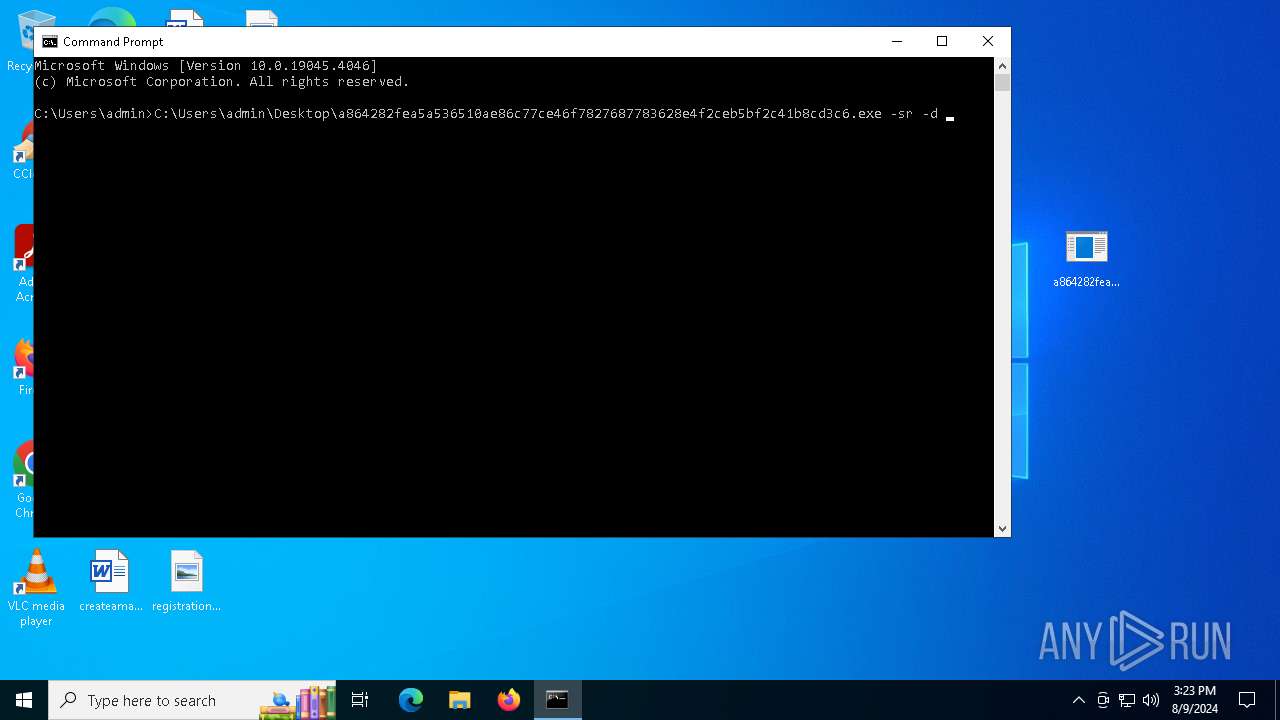
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6180)
Rhysida note has been found
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6180)
Run PowerShell with an invisible window
- powershell.exe (PID: 6596)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6436)
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6180)
Application launched itself
- cmd.exe (PID: 5984)
- cmd.exe (PID: 1216)
- cmd.exe (PID: 5900)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 7092)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 6688)
- cmd.exe (PID: 420)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1216)
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6180)
- cmd.exe (PID: 5984)
- cmd.exe (PID: 5900)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 7092)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 6688)
- cmd.exe (PID: 420)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6908)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 6944)
- cmd.exe (PID: 7036)
- cmd.exe (PID: 6992)
- cmd.exe (PID: 1420)
- cmd.exe (PID: 7096)
- cmd.exe (PID: 1452)
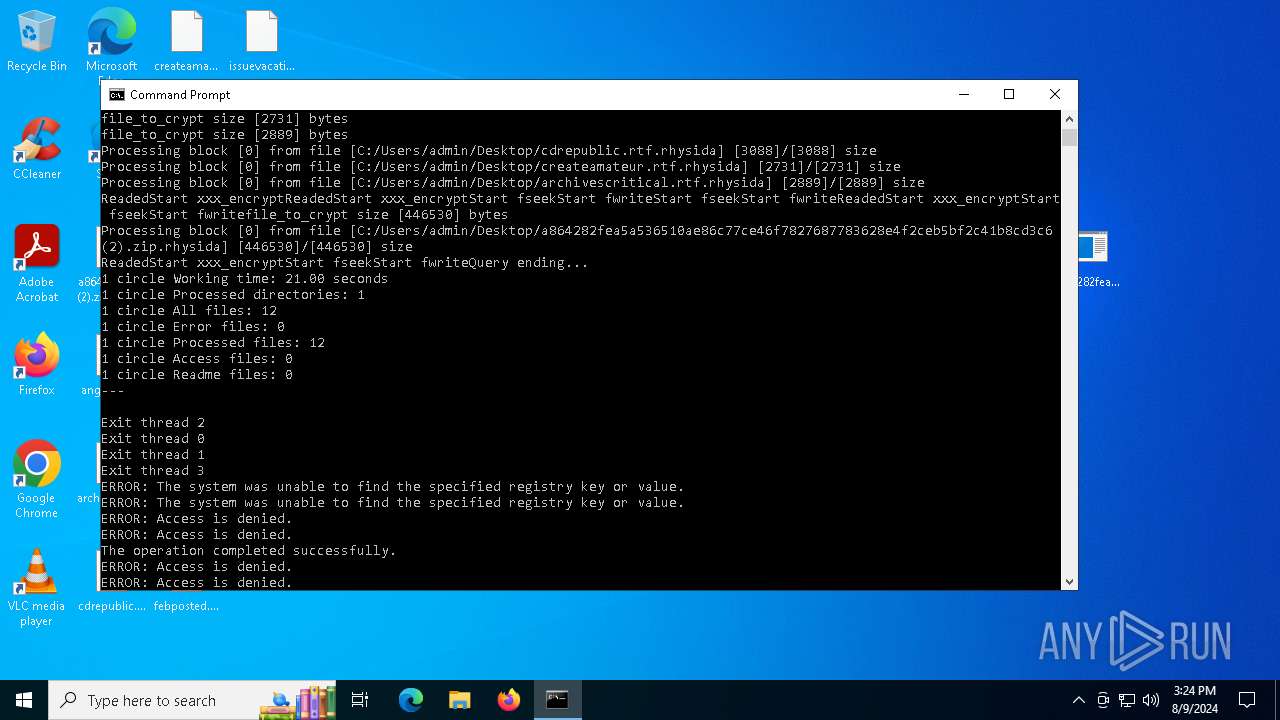
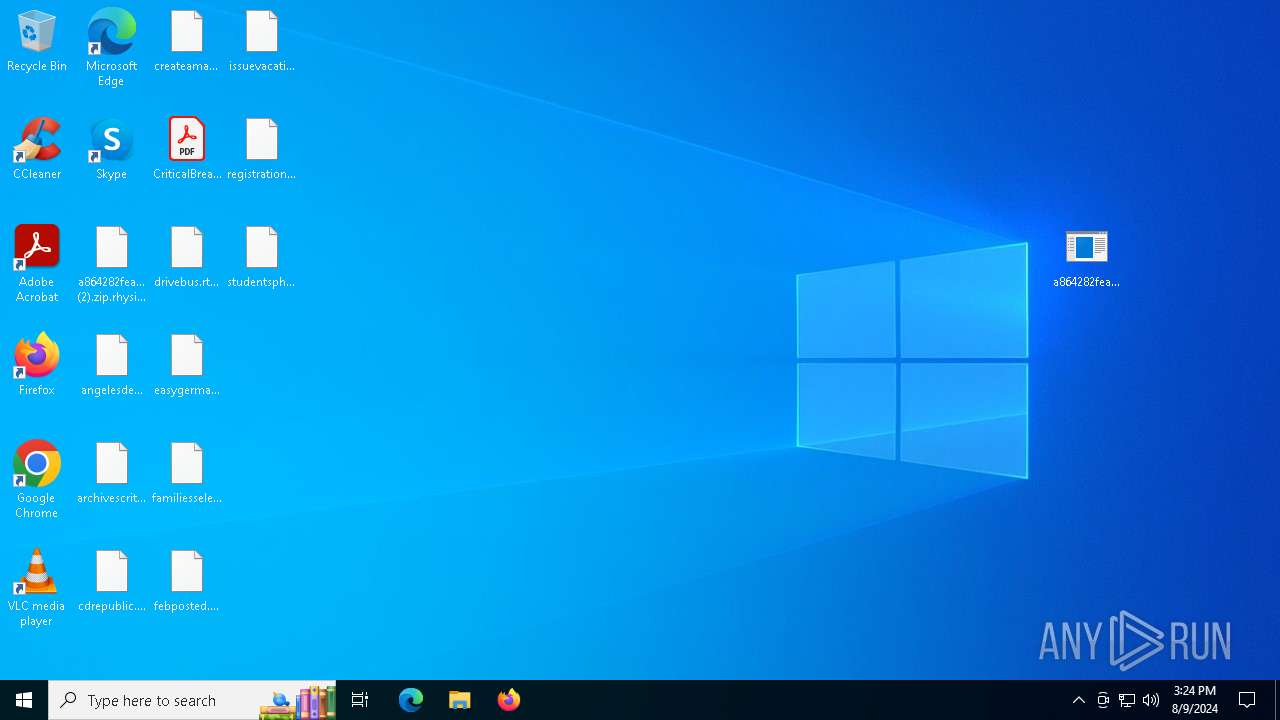
Changes the desktop background image
- reg.exe (PID: 6568)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 6988)
- cmd.exe (PID: 6992)
- reg.exe (PID: 6568)
- cmd.exe (PID: 7096)
- cmd.exe (PID: 7092)
- reg.exe (PID: 2464)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6624)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 6148)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6436)
Checks supported languages
- TextInputHost.exe (PID: 4104)
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6180)
Reads the computer name
- TextInputHost.exe (PID: 4104)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 6436)
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6180)
Manual execution by a user
- cmd.exe (PID: 6616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2023:07:08 22:37:08 |
| ZipCRC: | 0x7a7b5808 |
| ZipCompressedSize: | 446274 |
| ZipUncompressedSize: | 1261752 |
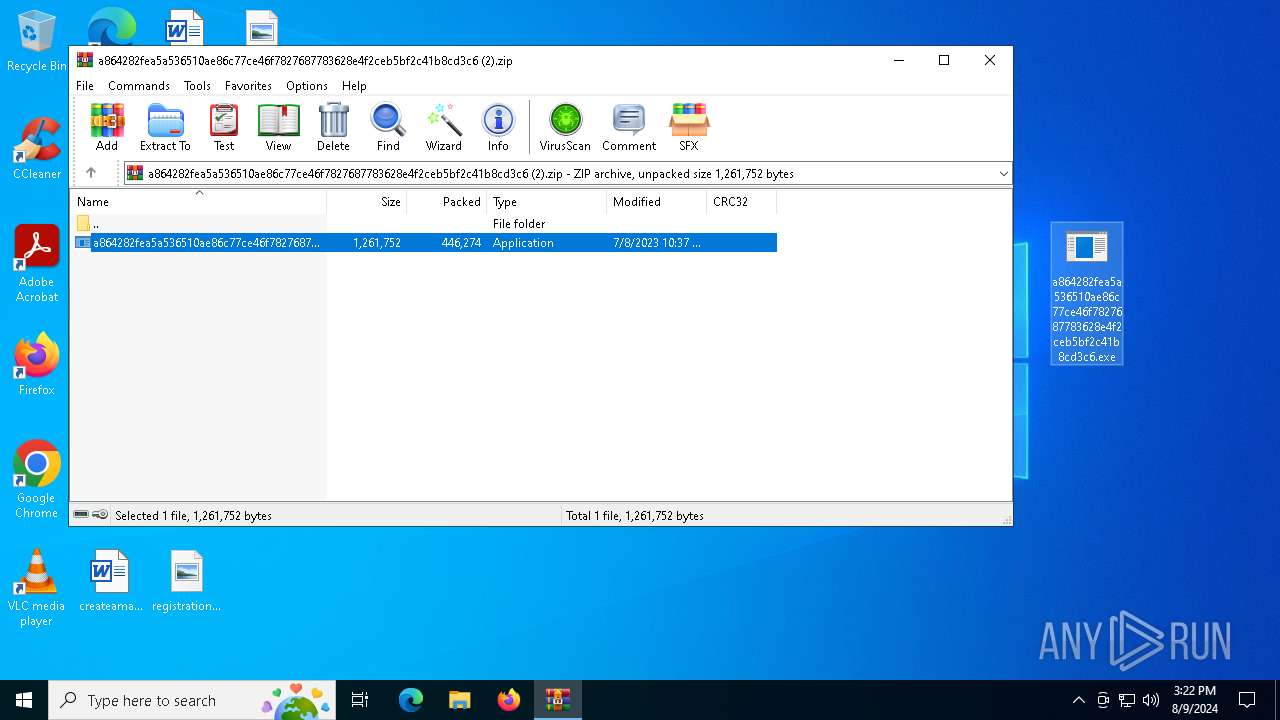
| ZipFileName: | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe |
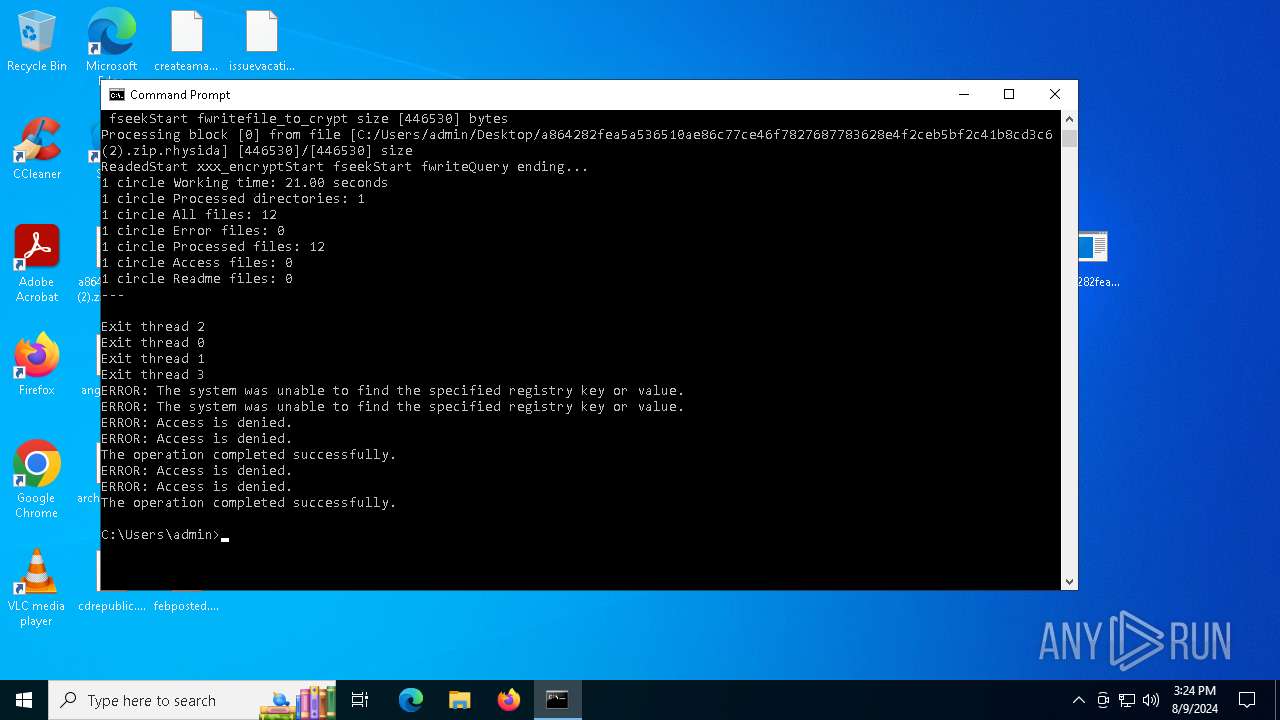
Total processes
156
Monitored processes
36
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | C:\WINDOWS\system32\cmd.exe /c cmd.exe /c reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v WallpaperStyle /t REG_SZ /d 2 /f | C:\Windows\System32\cmd.exe | — | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | C:\WINDOWS\system32\cmd.exe /c cmd.exe /c reg delete "HKCU\Conttol Panel\Desktop" /v Wallpaper /f | C:\Windows\System32\cmd.exe | — | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | reg delete "HKCU\Conttol Panel\Desktop" /v Wallpaper /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1420 | cmd.exe /c reg add "HKCU\Control Panel\Desktop" /v WallpaperStyle /t REG_SZ /d 2 /f | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | cmd.exe /c reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v WallpaperStyle /t REG_SZ /d 2 /f | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v Wallpaper /t REG_SZ /d "C:\Users\Public\bg.jpg" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 5084 | rundll32.exe user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5900 | C:\WINDOWS\system32\cmd.exe /c cmd.exe /c reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop" /v NoChangingWallPaper /t REG_SZ /d 1 /f | C:\Windows\System32\cmd.exe | — | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 756
Read events
13 734
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6 (2).zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
1
Suspicious files
15
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\febposted.png.rhysida | image | |
MD5:771A823FB058AD1ABF36CA62E48BE559 | SHA256:486AAC6AB83C3D75898AEE96A54A03E860F3F7D1061C9C197958BF9CF7A331CF | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6436.25127\a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | executable | |
MD5:0C8E88877383CCD23A755F429006B437 | SHA256:A864282FEA5A536510AE86C77CE46F7827687783628E4F2CEB5BF2C41B8CD3C6 | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\issuevacation.rtf.rhysida | text | |
MD5:ACC8D2C19EB5B1F637198CDF04938EFC | SHA256:FD32ACFBC1F0D89D18B7E399BD695AE1A7A4773E9FB21AE00F201F97F2B13C3B | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\drivebus.rtf.rhysida | text | |
MD5:2E6E6C2AEF8168125597AC3D5DE295C2 | SHA256:71FBDA66CF24100236A927F0BDC61C6805AF51C15CD688835C4600BB6A32C9FA | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\studentsphp.jpg.rhysida | image | |
MD5:E9940062927F8F1E456A66AD95A30CA9 | SHA256:C5E89E948C6EF1AAC1A3BFF7620BC03CD366AFA1AD047967B6F14875B6466C80 | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\easygermany.rtf.rhysida | text | |
MD5:A48BCDC82E7E58EF967C6190BEEBDC84 | SHA256:BA536312E38F5E28124F4FE7EB5E98F0D5E4EB03ECA560A7F07C4D492CAA7919 | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\cdrepublic.rtf.rhysida | text | |
MD5:07EAC1BB9C81F35C2B232E05362F4817 | SHA256:287EFA5B67206556DFEC271C2BDDA0B69A72B83A2D893A163D3EE09F0AC3EC6D | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\registrationstar.png.rhysida | image | |
MD5:1F6C81A5E4EDB6D807BE36D0A5E91218 | SHA256:783B0BA1ECC1B1A7553A2D25FBE794FAAC7518657F490B7CDE921FF273DB3D6C | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\familiesselect.jpg.rhysida | image | |
MD5:E19592AC2FAFC6546D013FF922C4239C | SHA256:317CC8048D66B842117F5FE9B5C0A25C16A3B0F3F2B0A33DF23BBC3A7E600D61 | |||
| 6180 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | C:\Users\admin\Desktop\angelesdemand.rtf.rhysida | text | |
MD5:0798EDD693AD814C017EDDC921CDECF5 | SHA256:AD52D1163DDD404E599C0FAF7B3128E54C4747B4AAB784B68F7AB6F820363063 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
32
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
532 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
532 | svchost.exe | 20.49.150.241:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
5336 | SearchApp.exe | 2.21.35.209:443 | www.bing.com | Akamai International B.V. | FR | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |