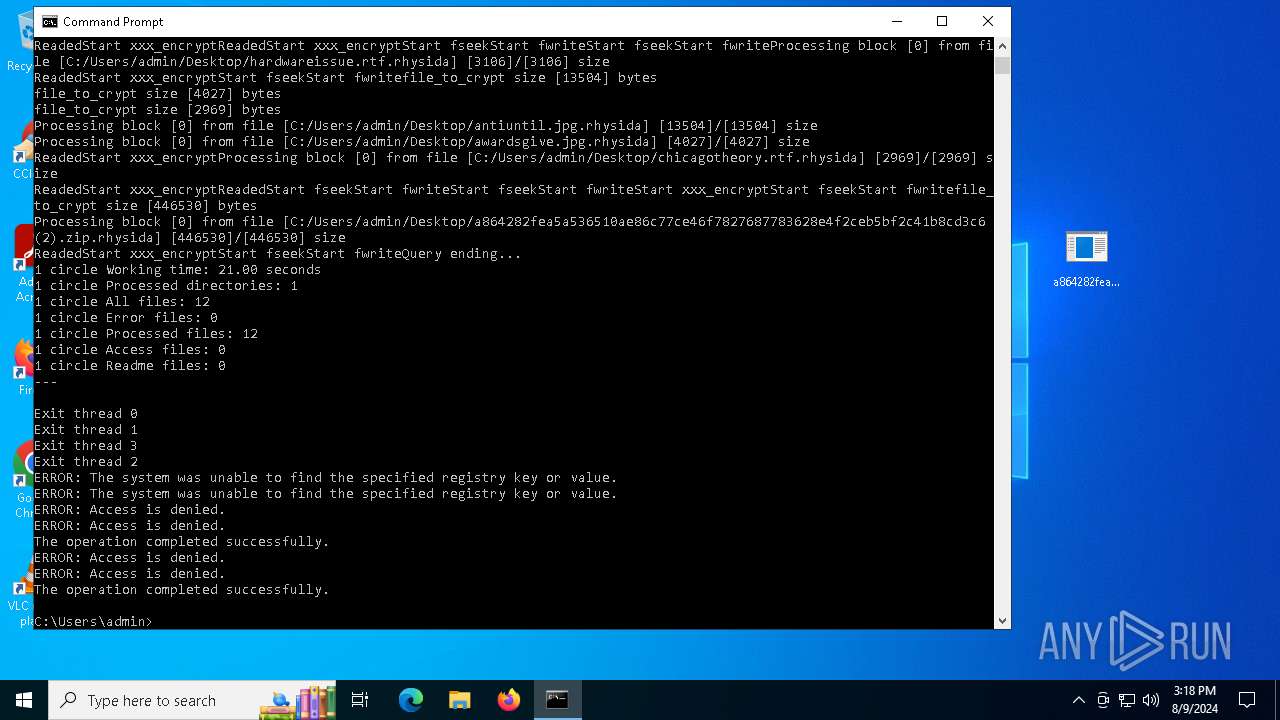
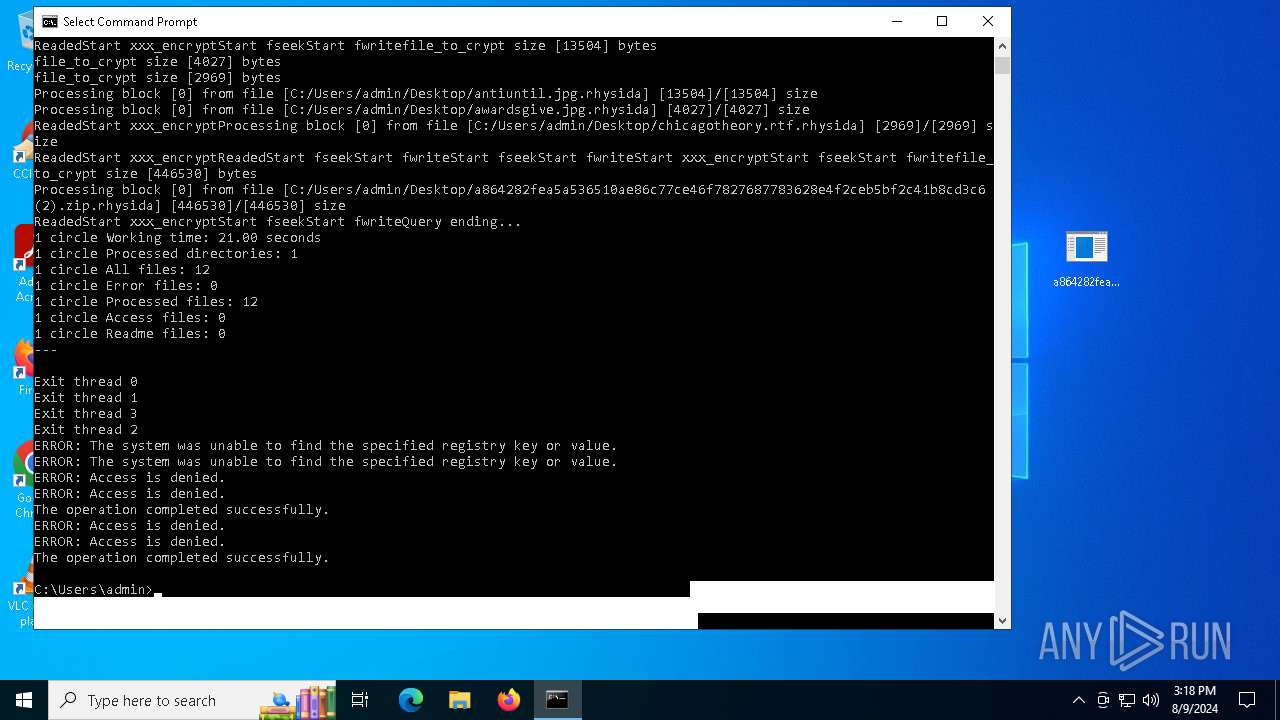
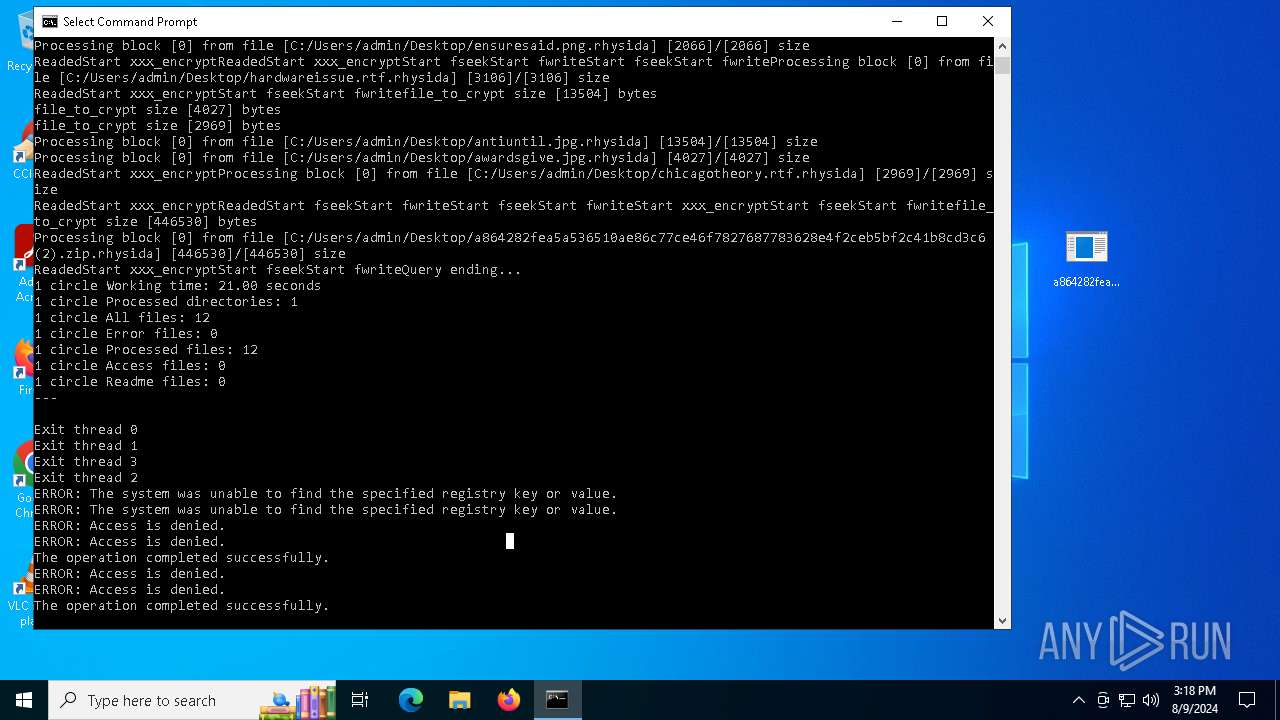
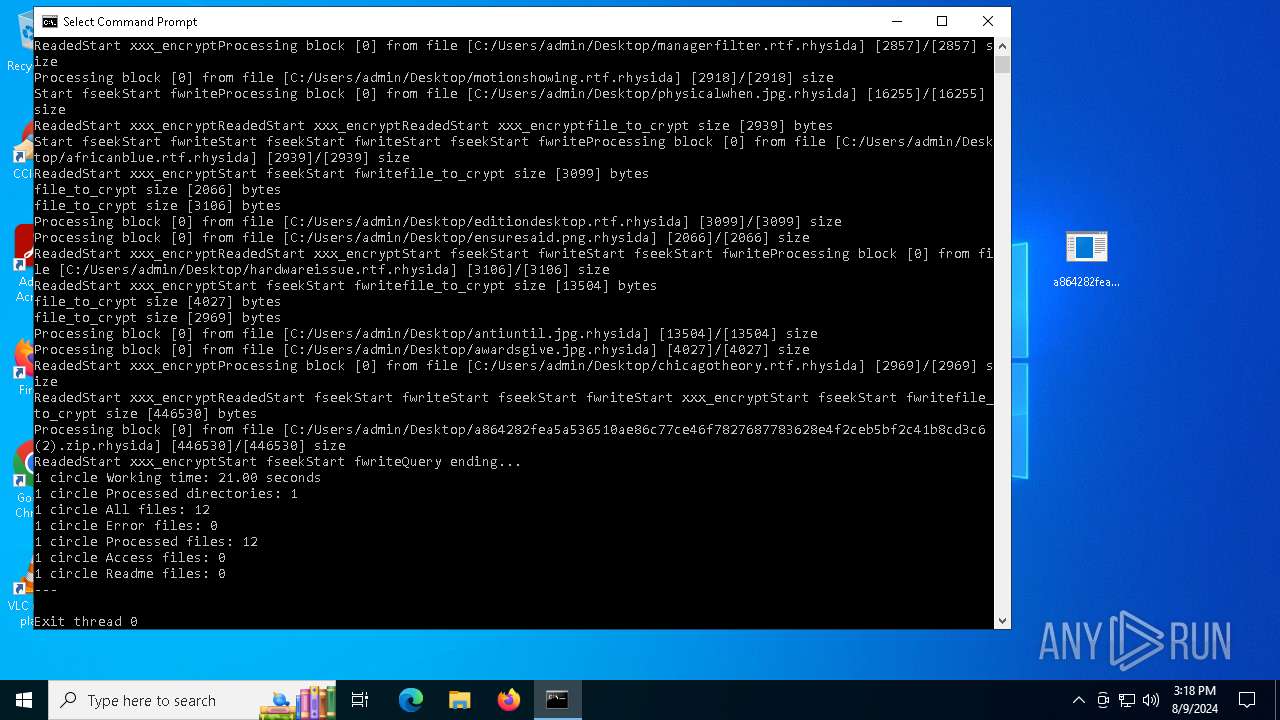
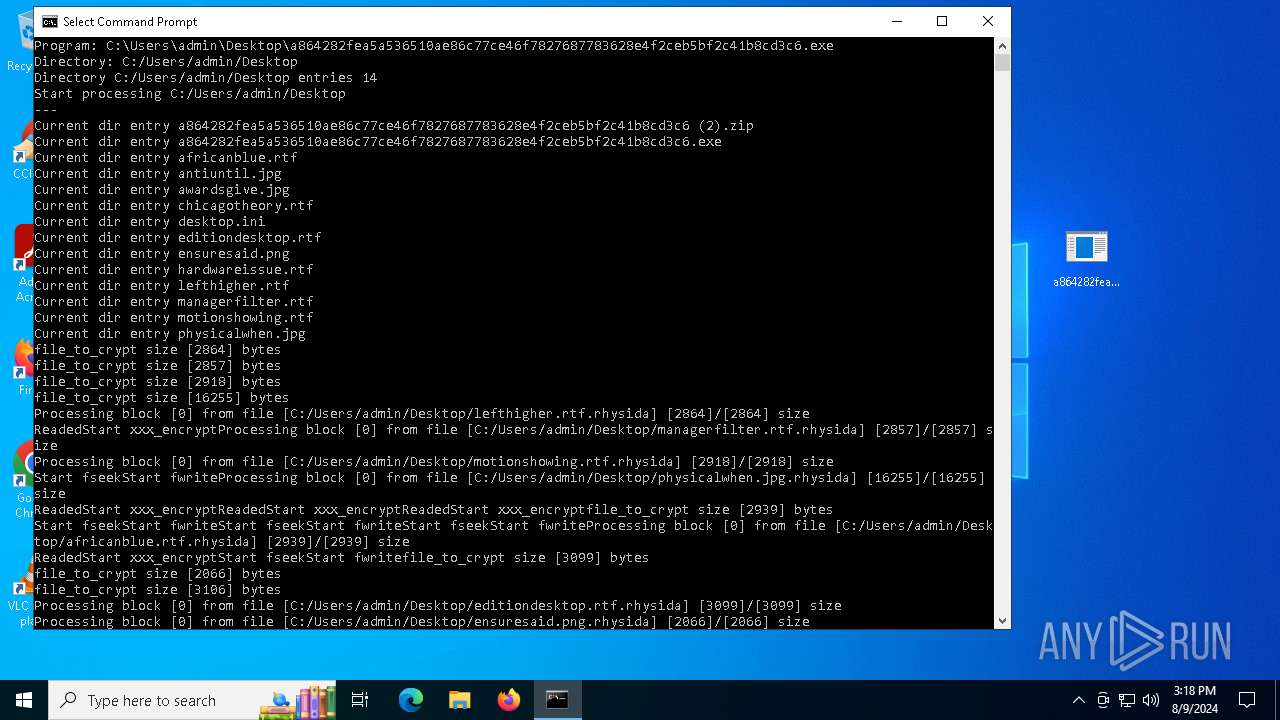
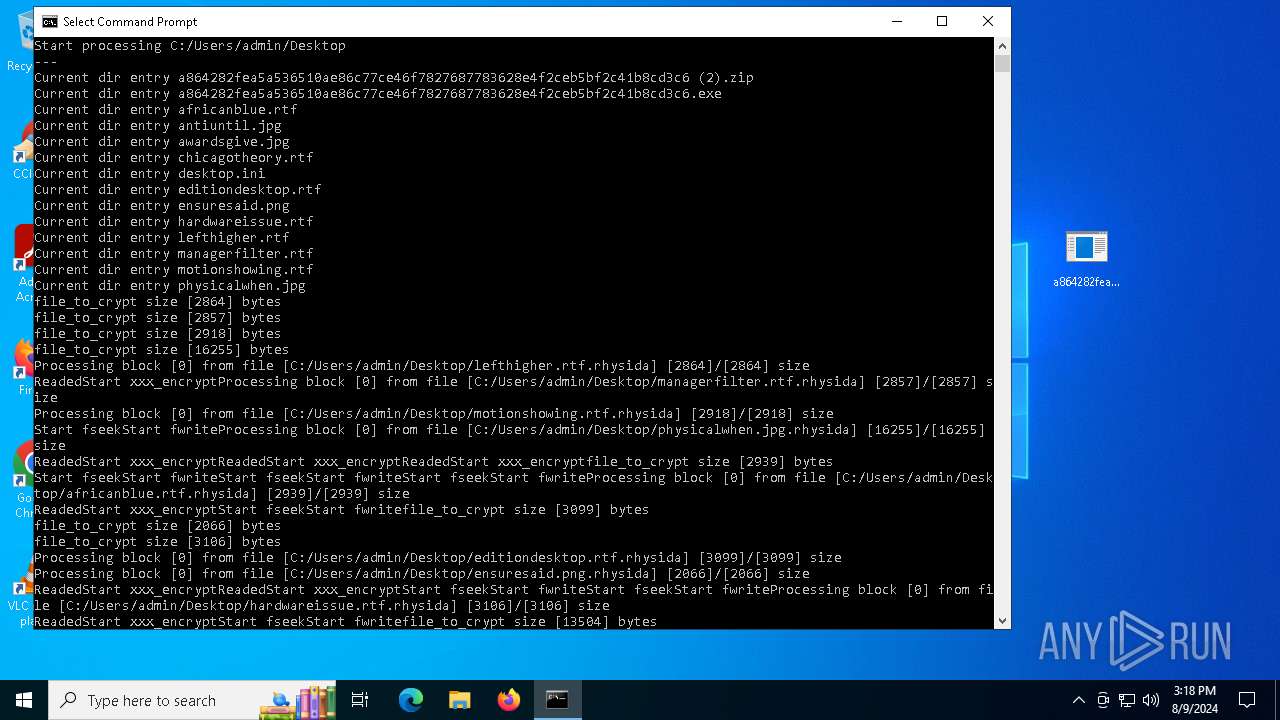
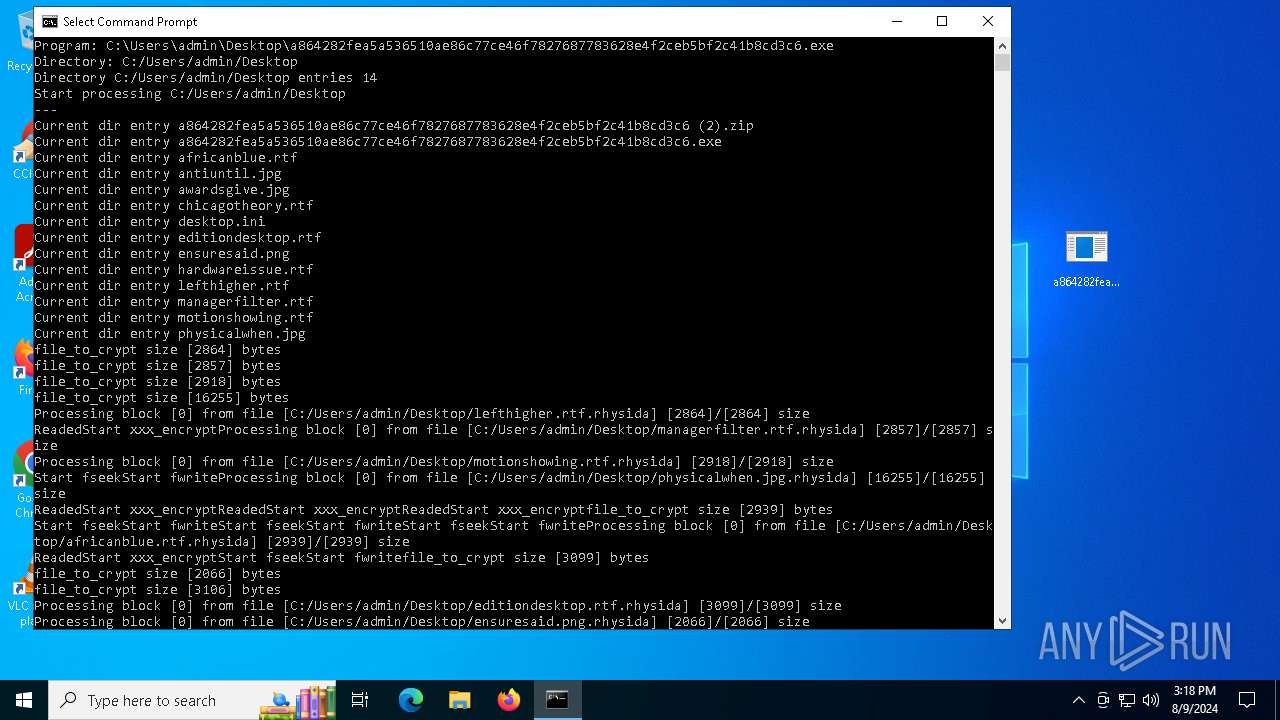
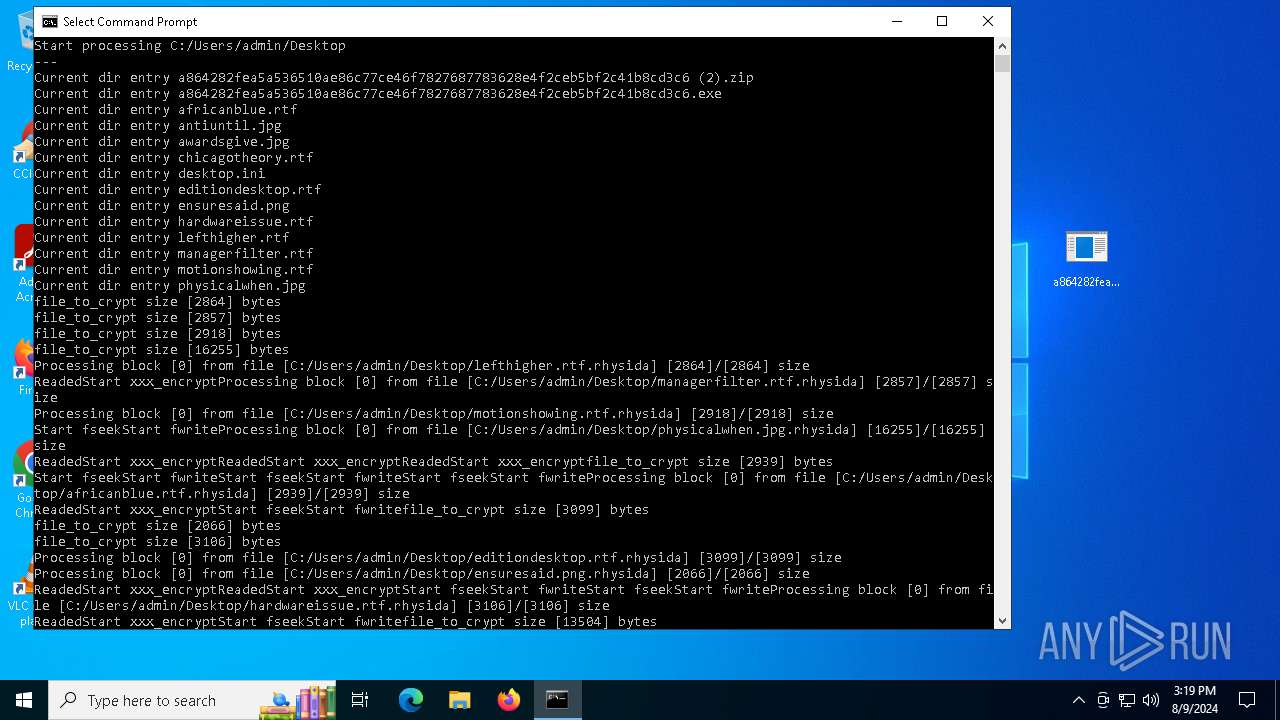
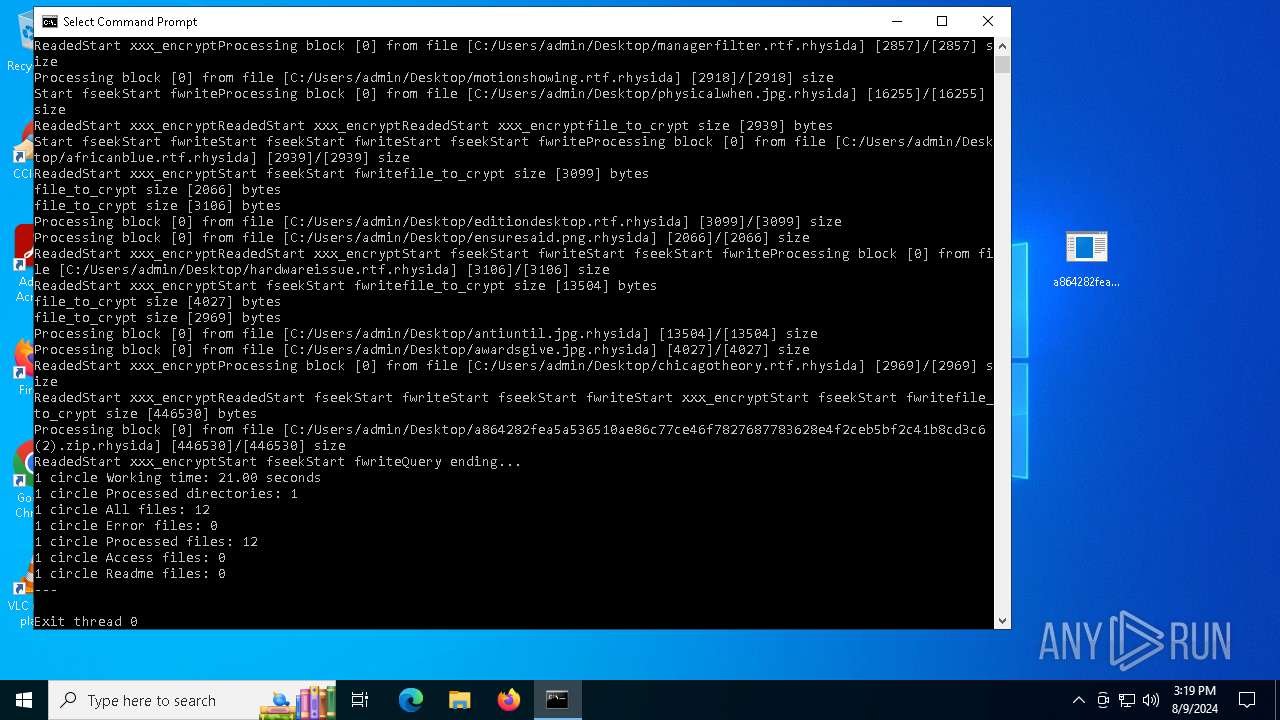
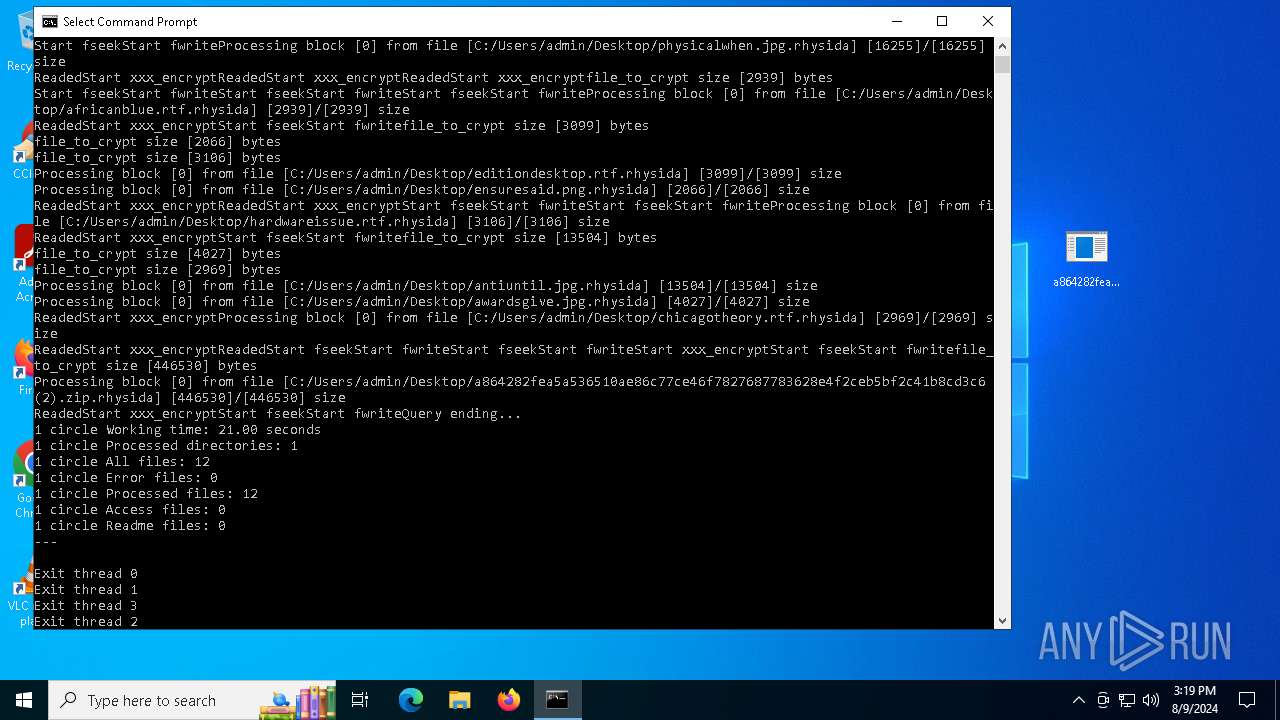
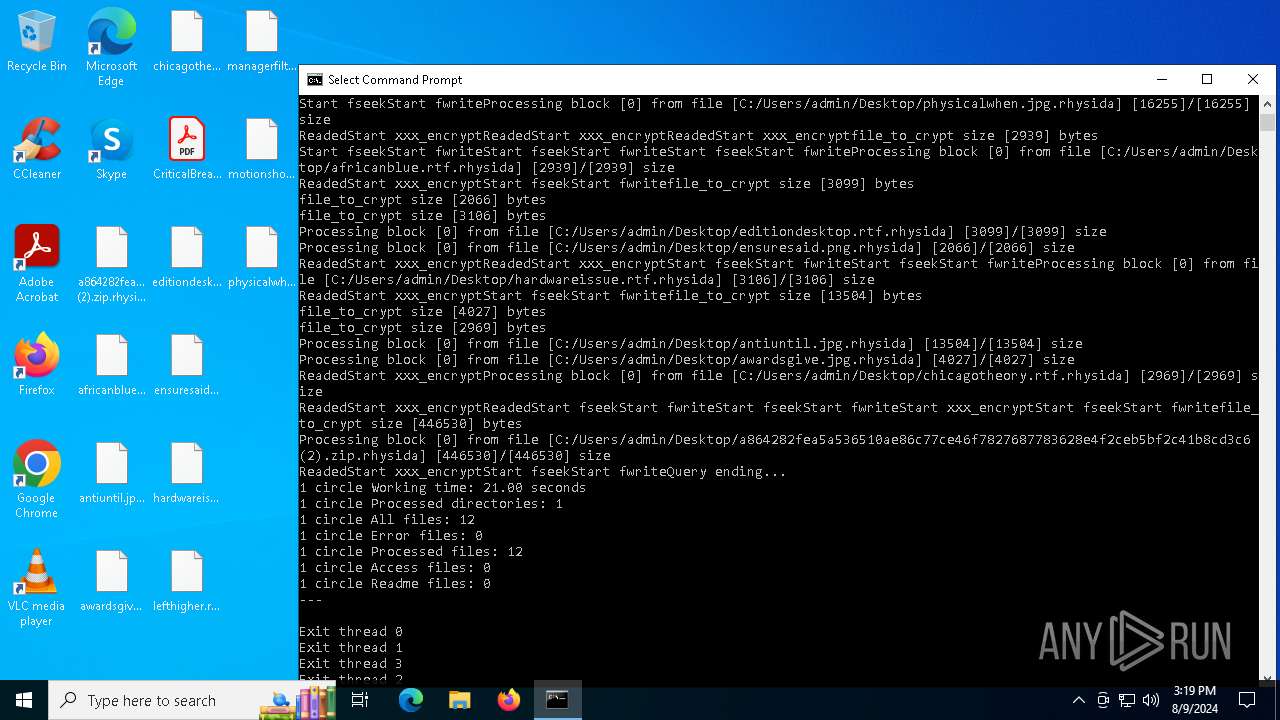
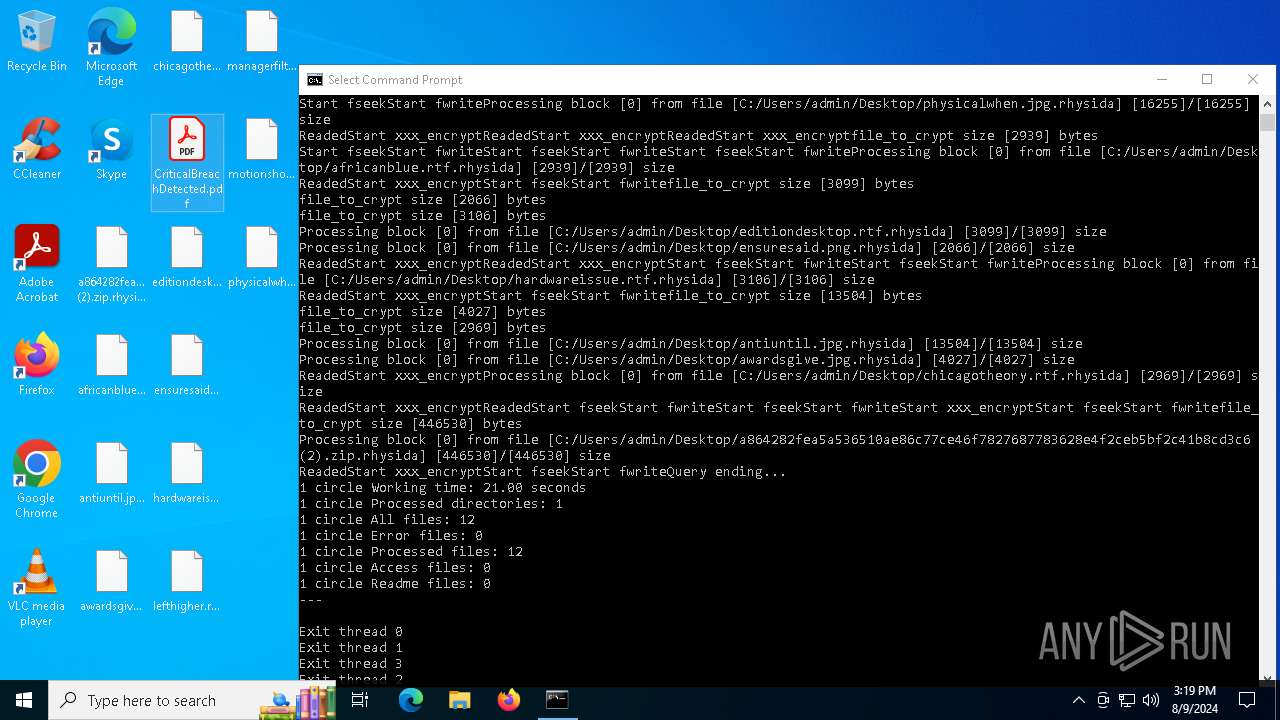
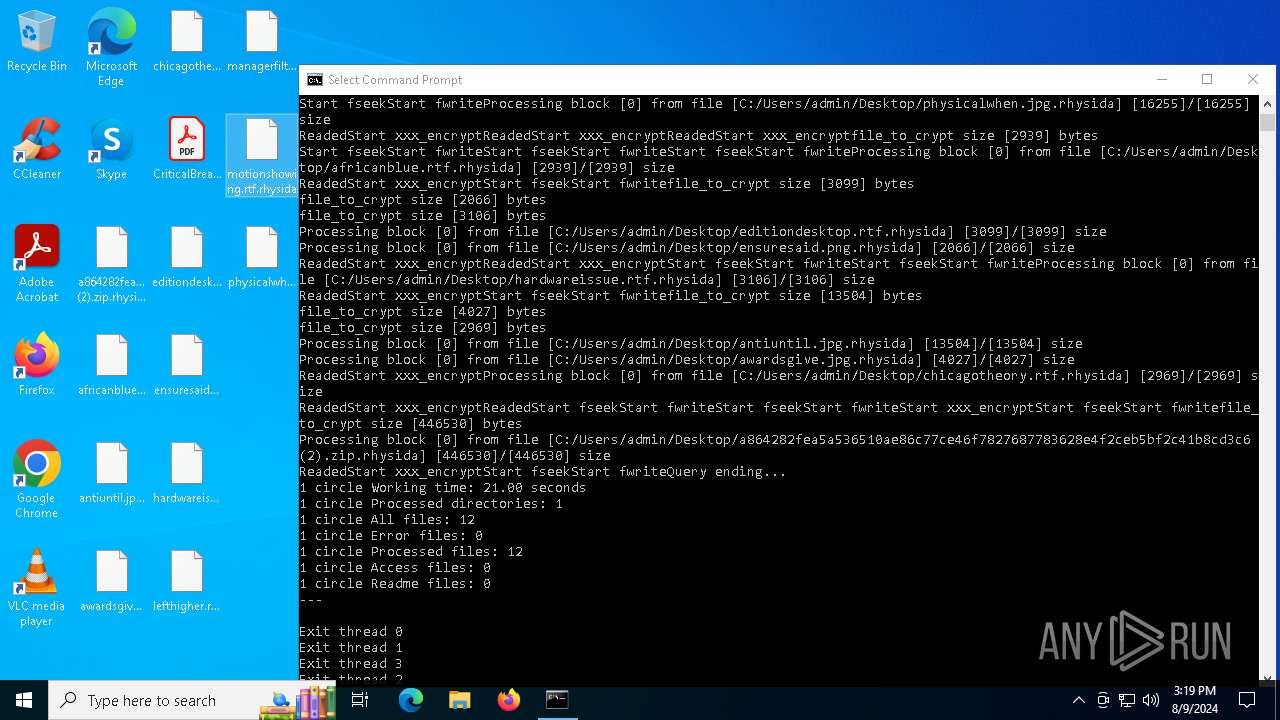
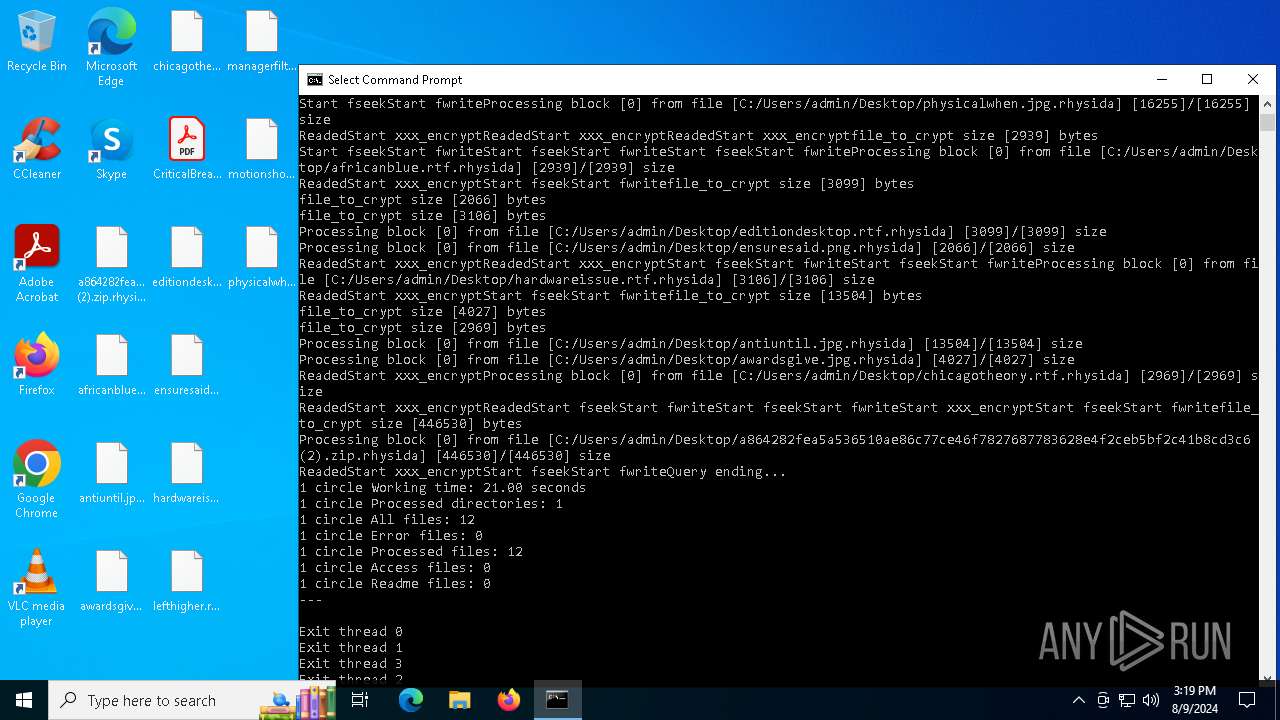
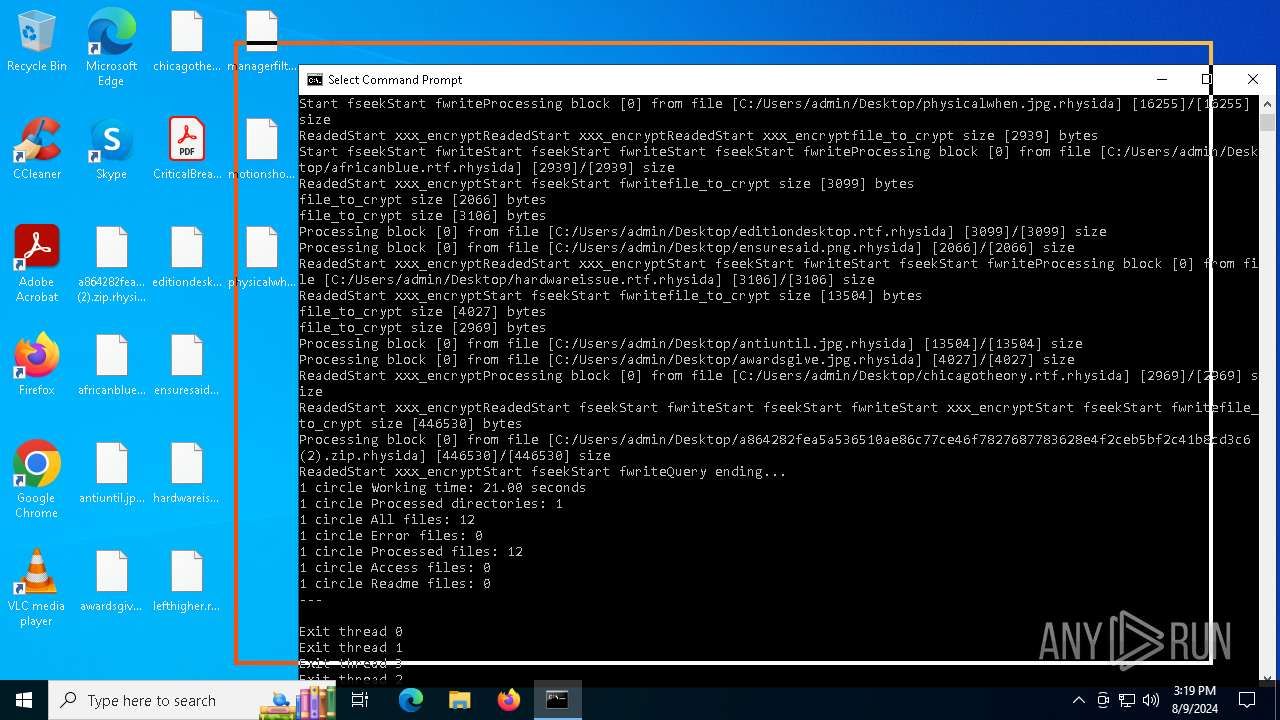
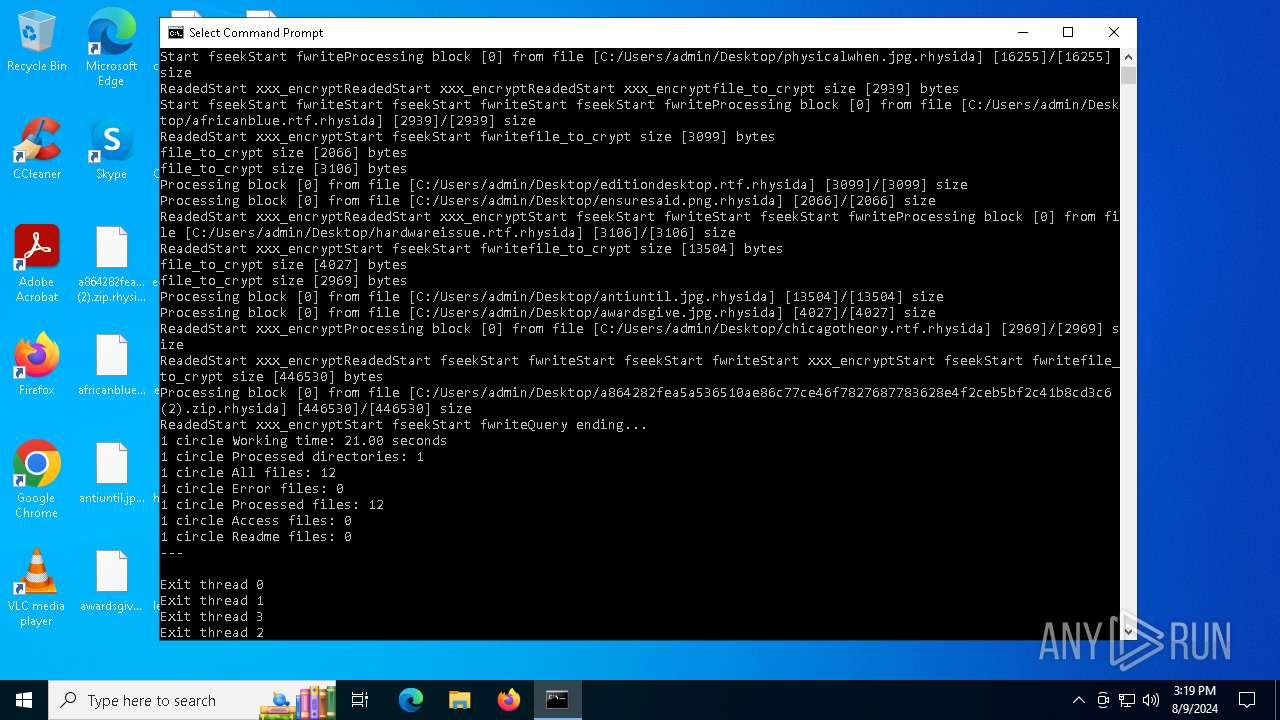
| File name: | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6 (2).zip |
| Full analysis: | https://app.any.run/tasks/9dfd77a8-c9e9-4b3e-8f0b-a0311ba7bc4d |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2024, 15:16:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
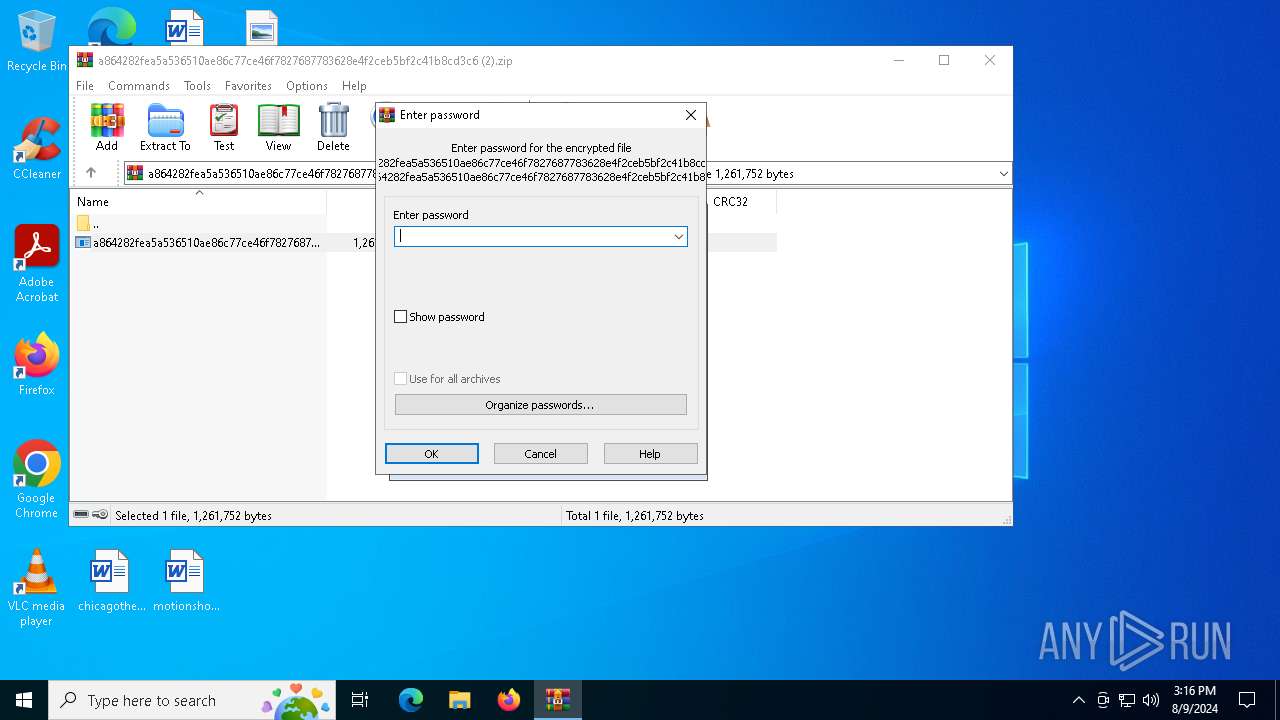
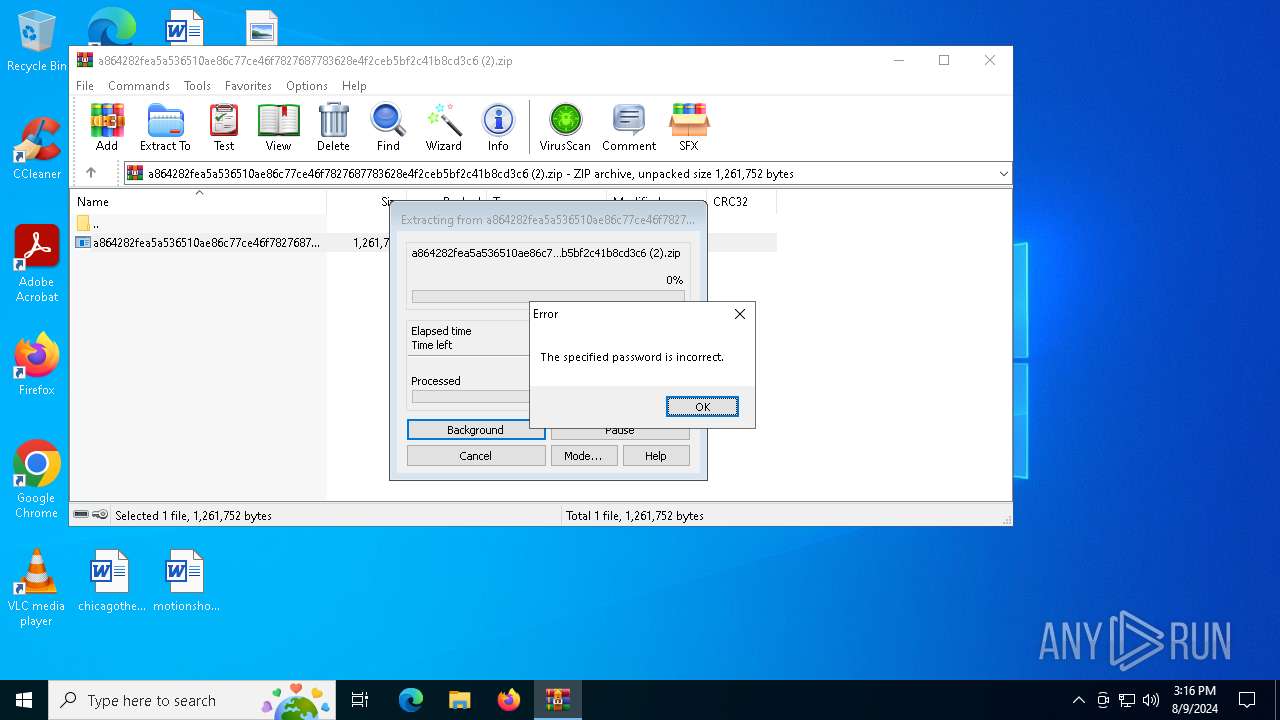
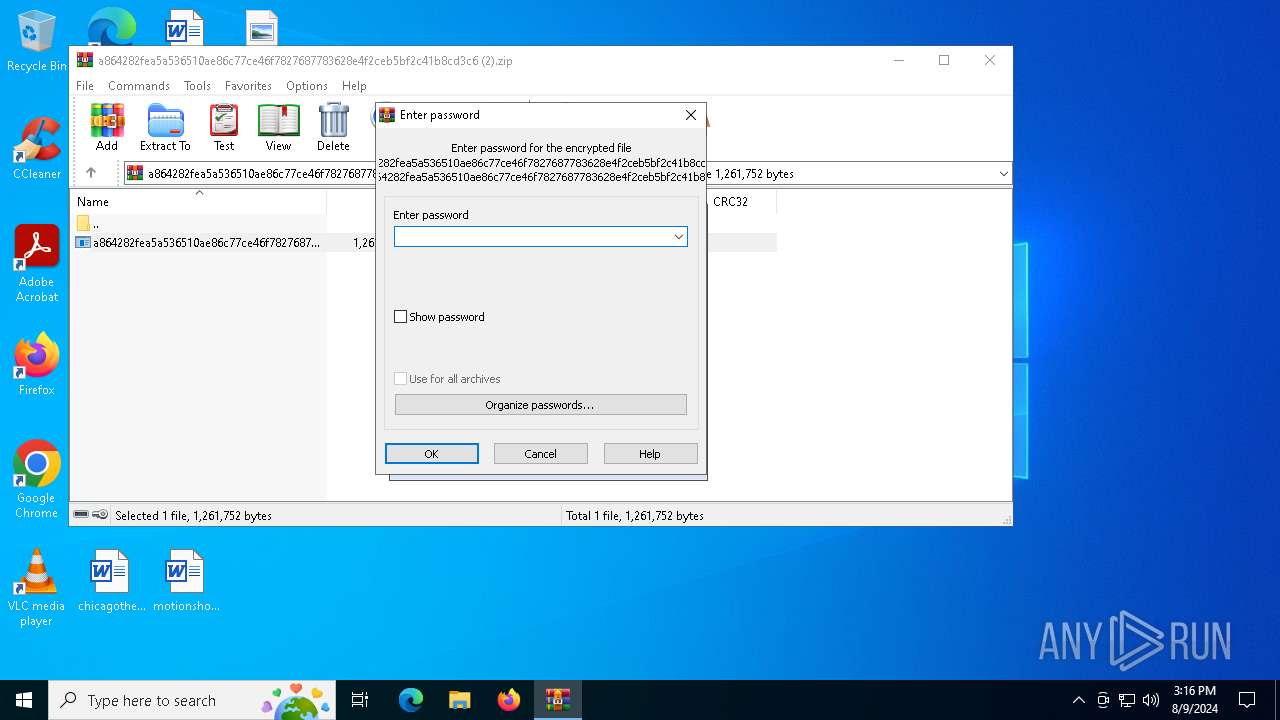
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 2C9E9F65F00363CD648D5C866483A6BB |
| SHA1: | CF5018D36363A5BDBEA4D8BAA768547F16B24483 |
| SHA256: | F1768C9F736C42332C9E195134E0DCCE7C762FD50B7BFC71CB55BF0C3E770A60 |
| SSDEEP: | 6144:OttWV7qEogQRPS8qq9vZbGYnc9+uLyOFfllOzAHnu5rojhPgfUTS5+xufl:OfGMPRTqYutL/hH4ojhxTK4ufl |
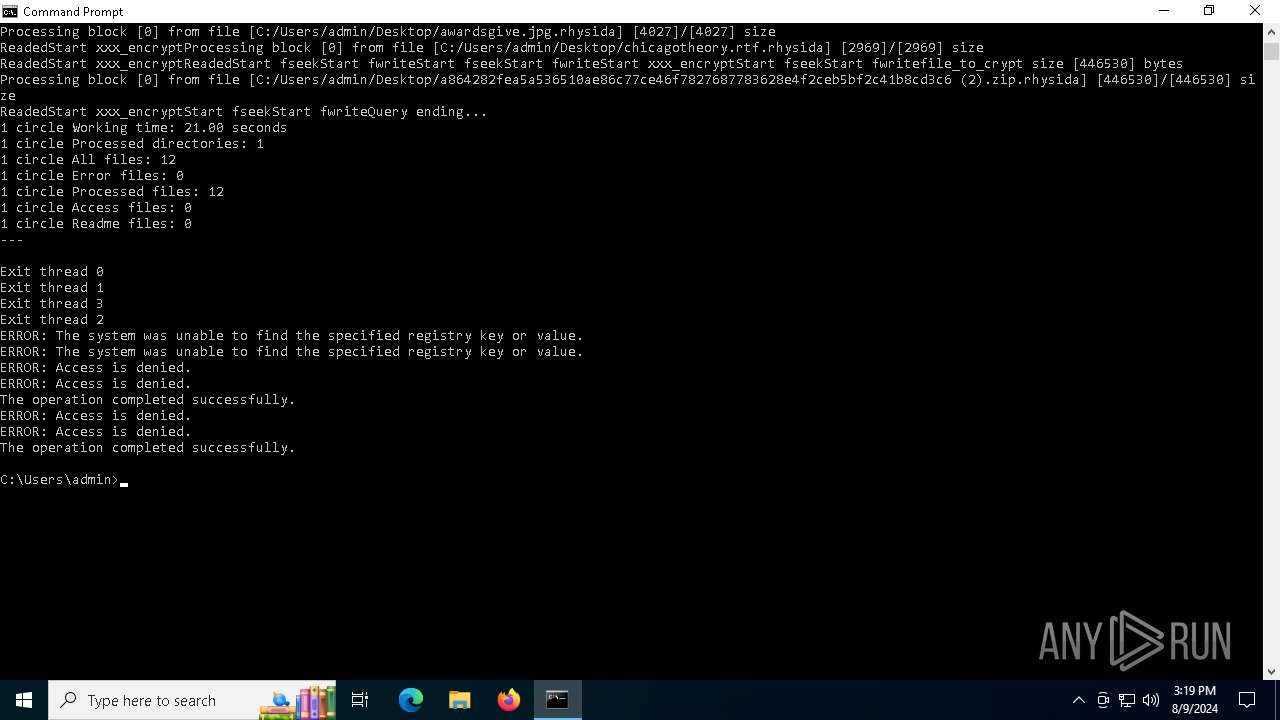
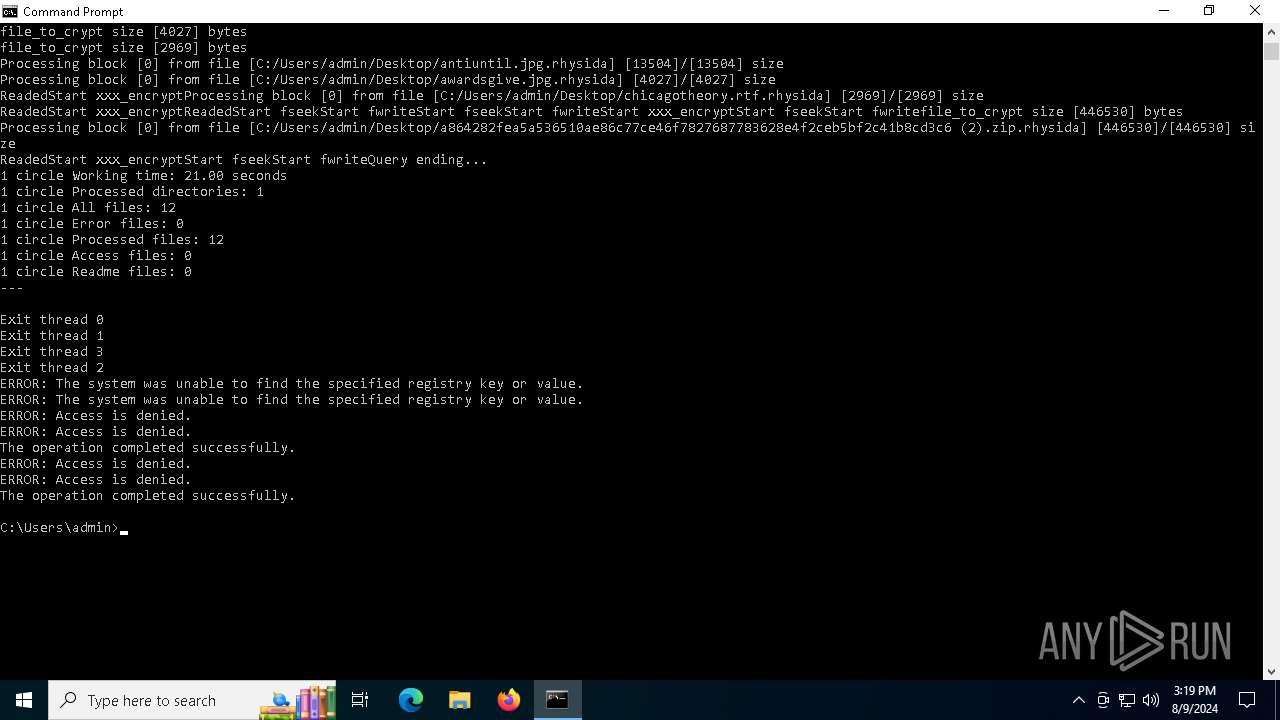
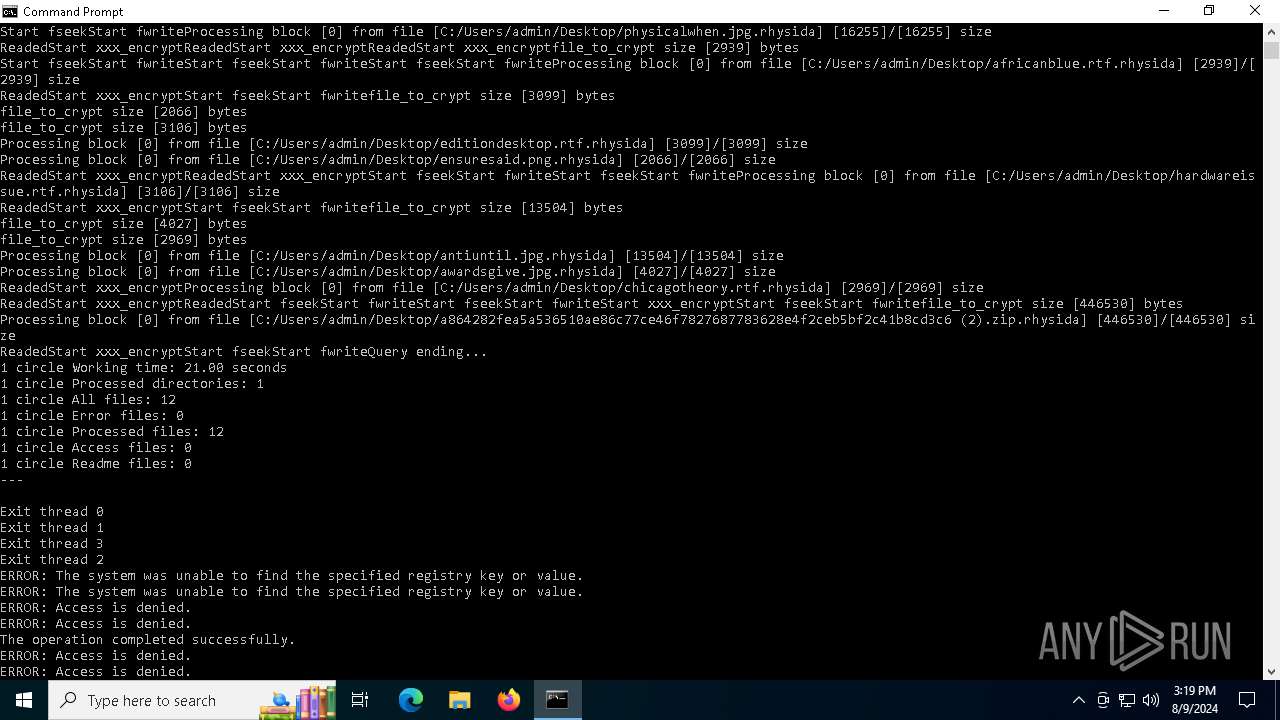
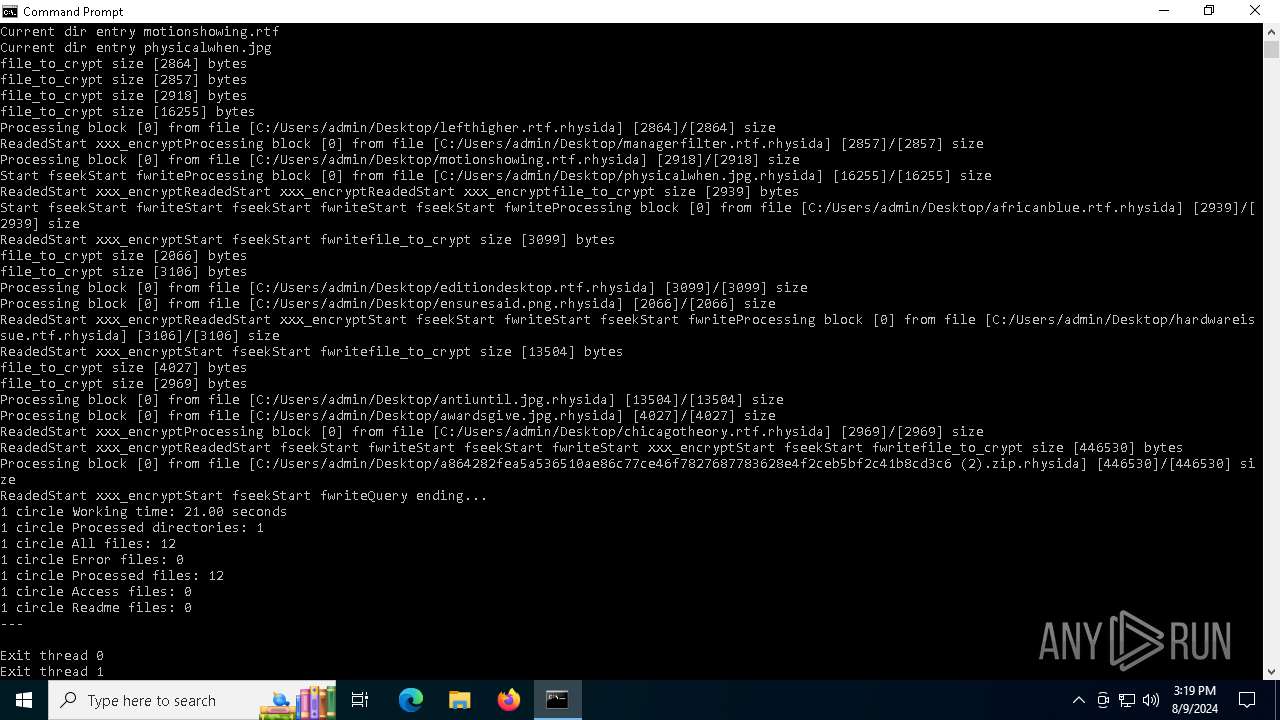
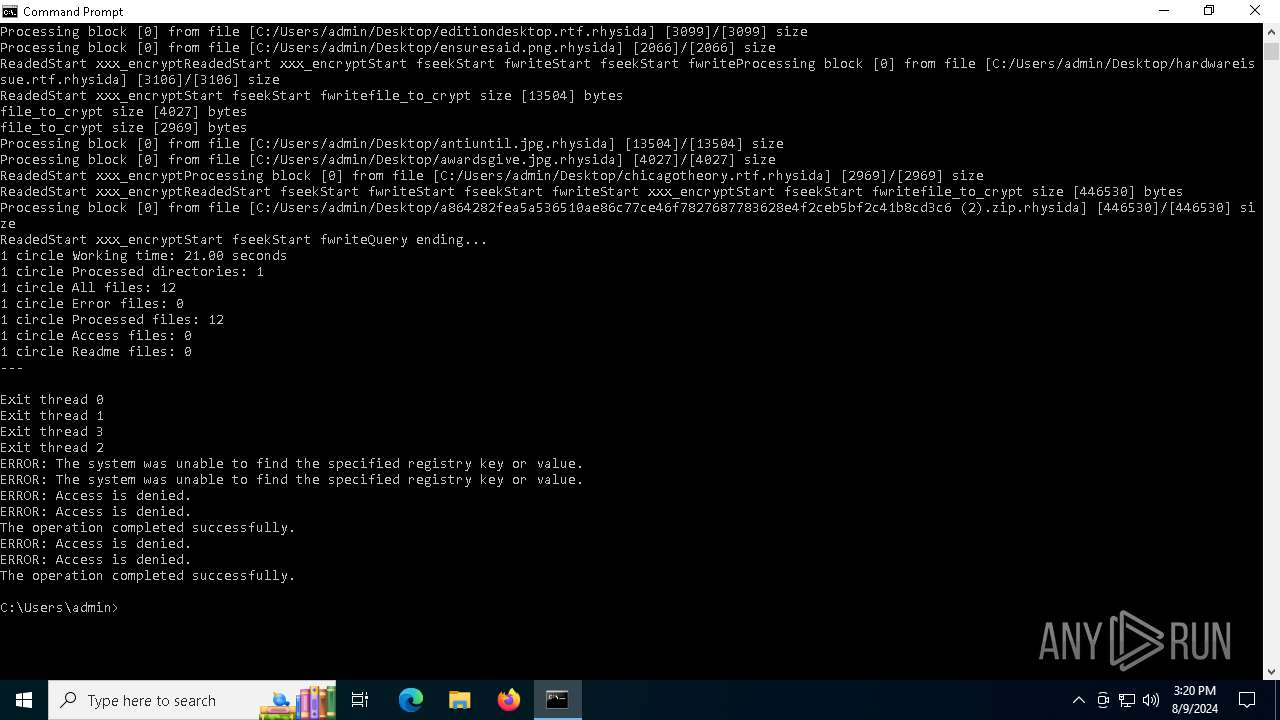
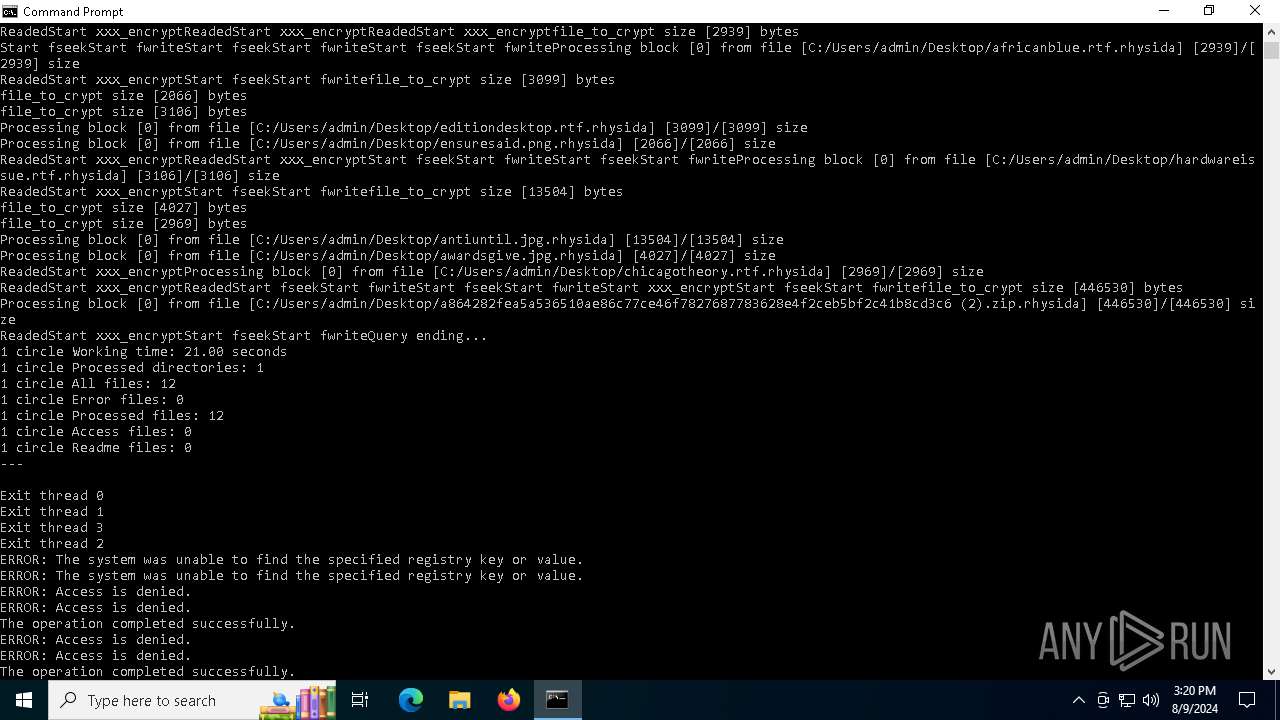
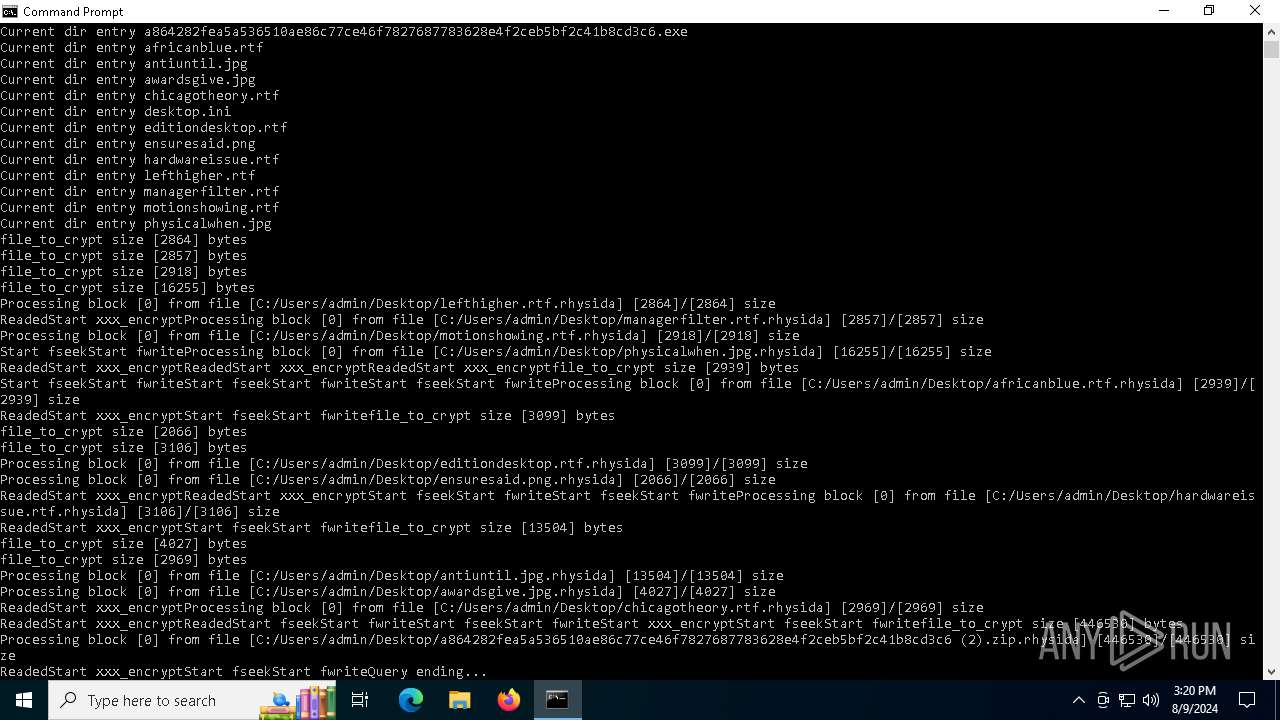
MALICIOUS
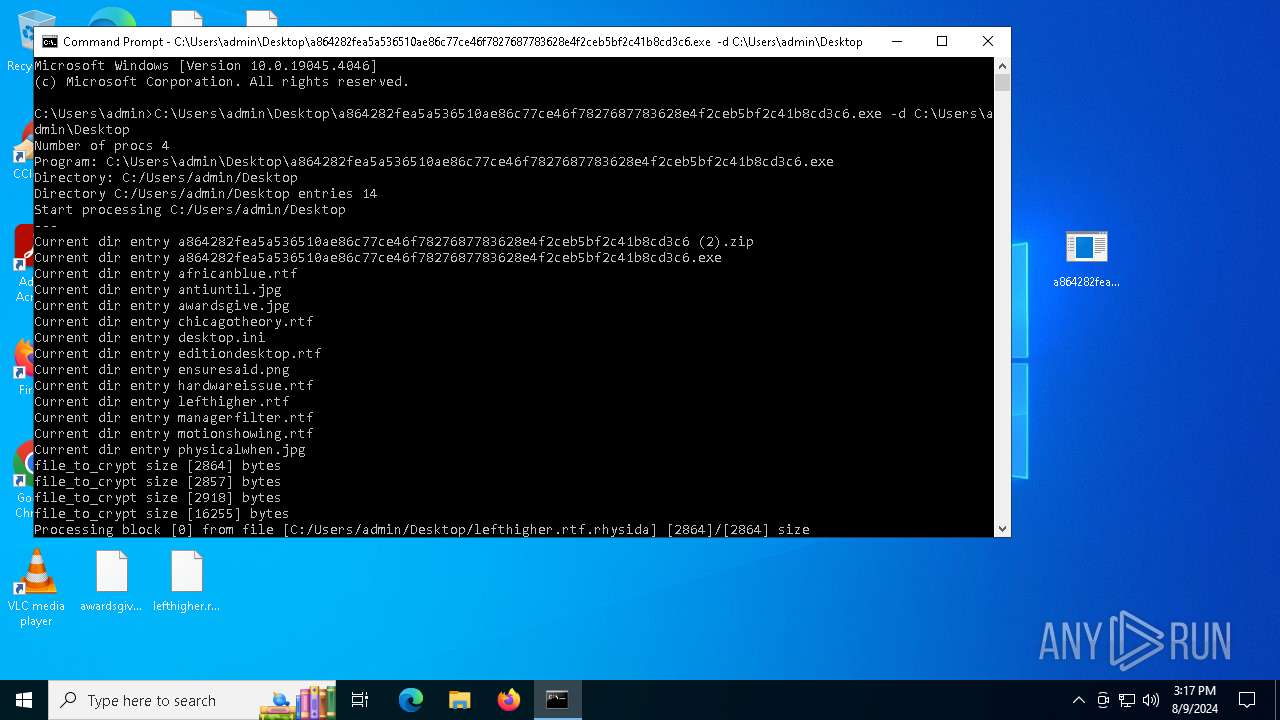
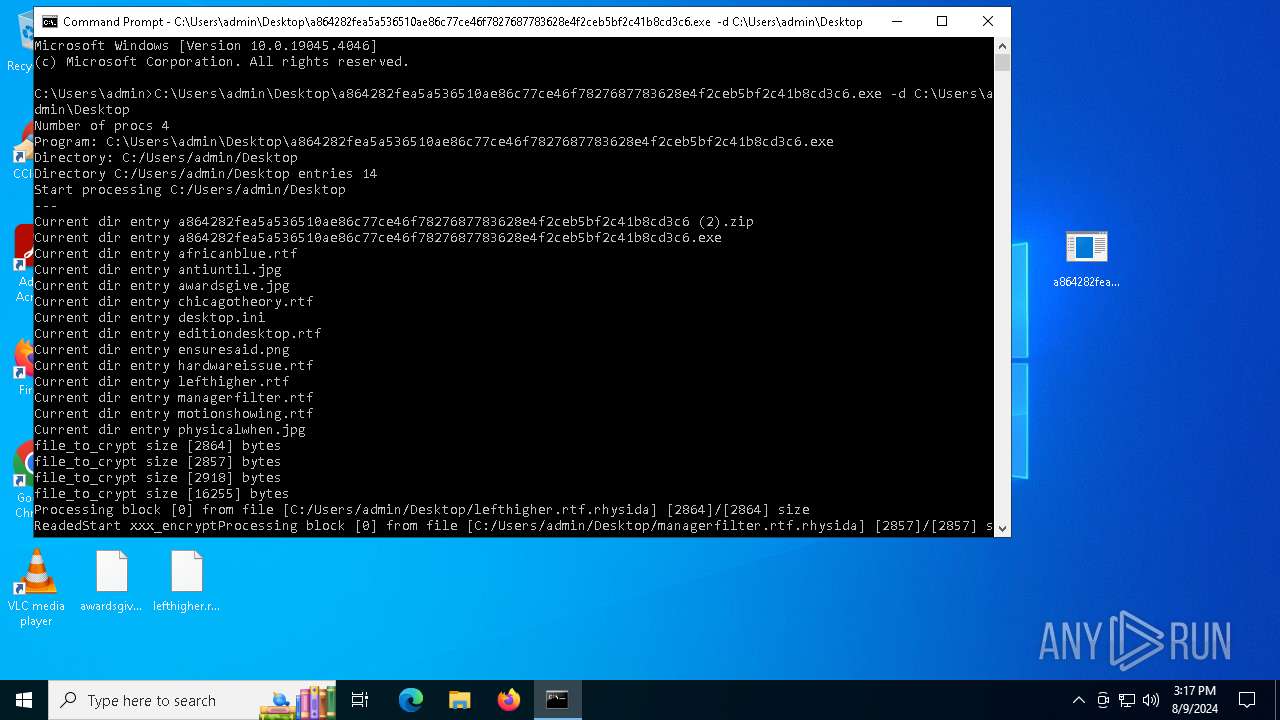
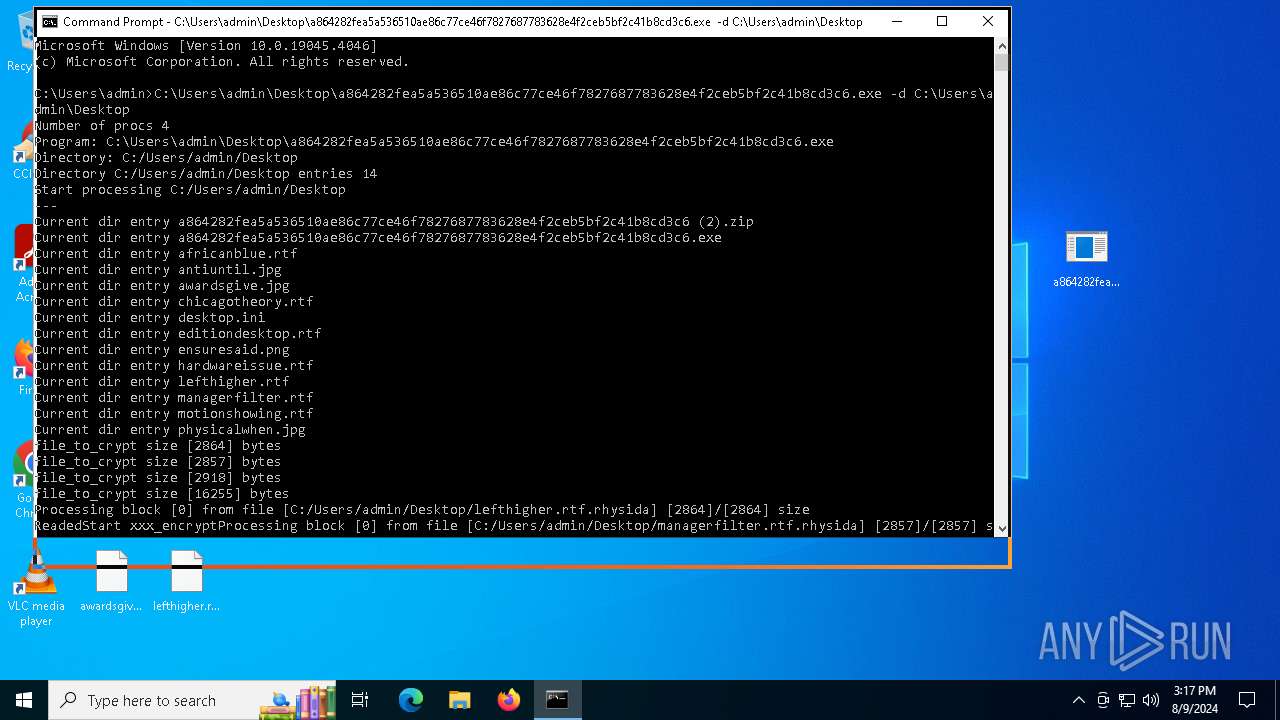
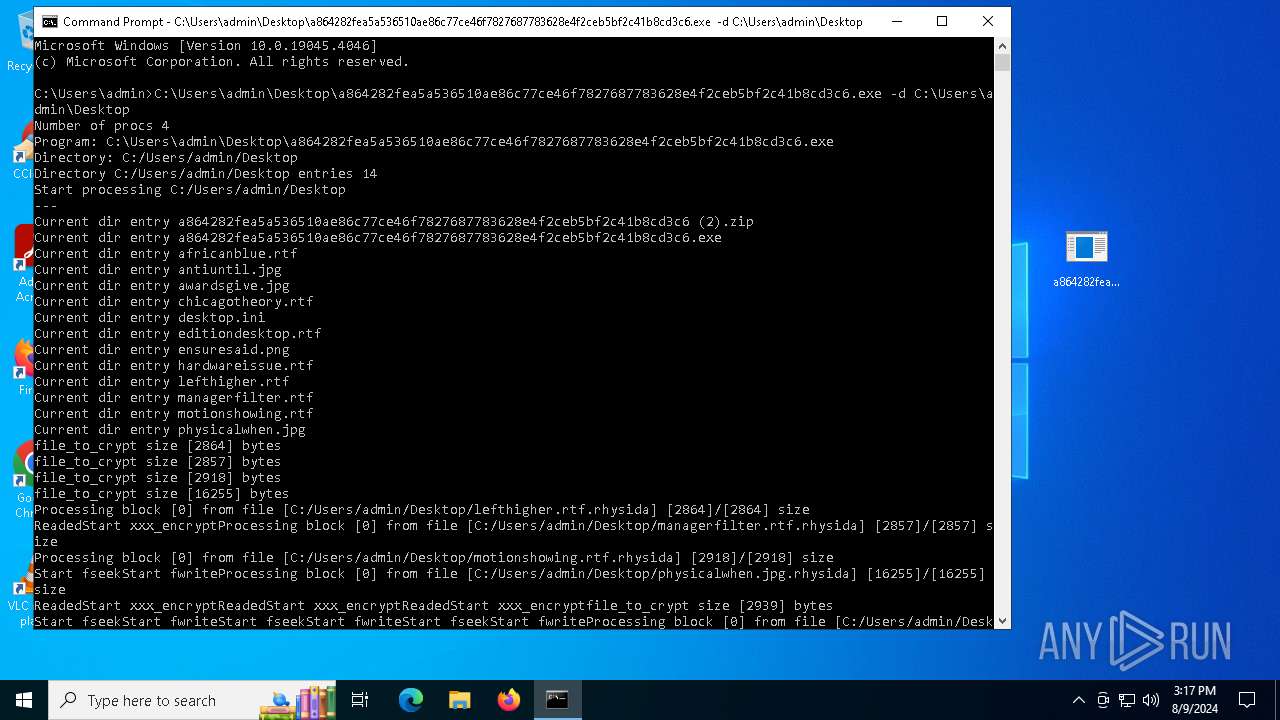
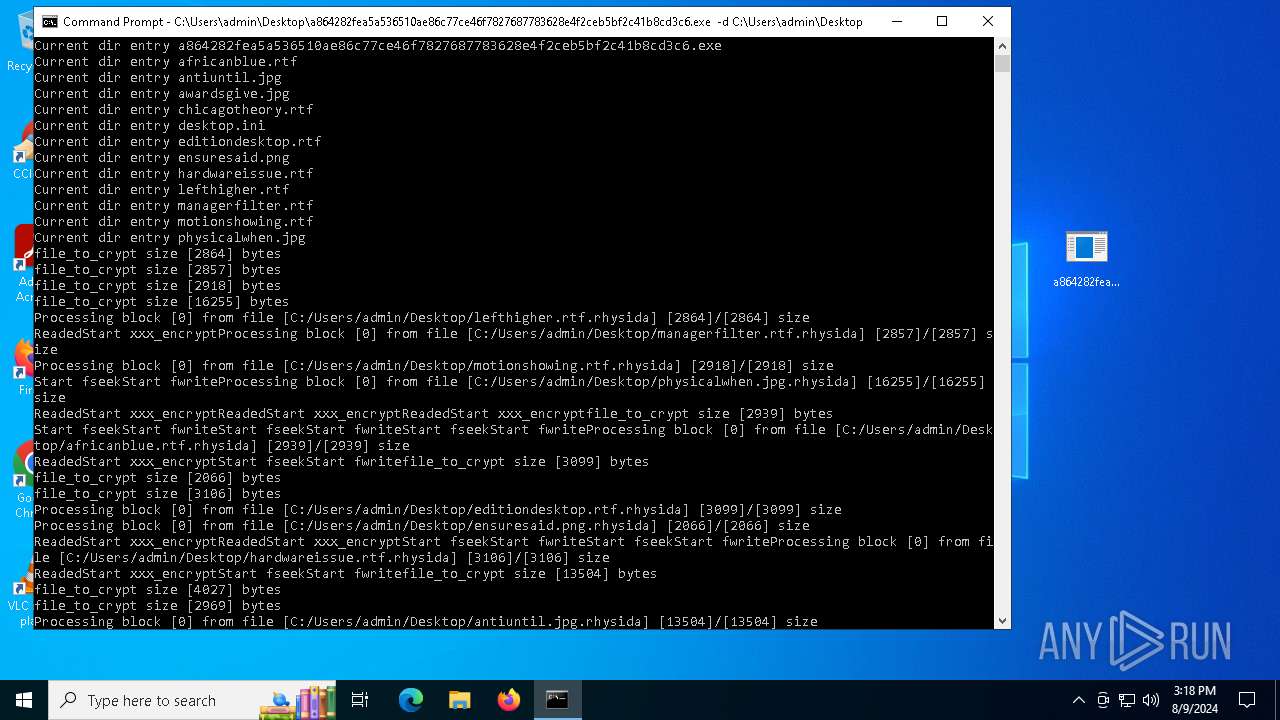
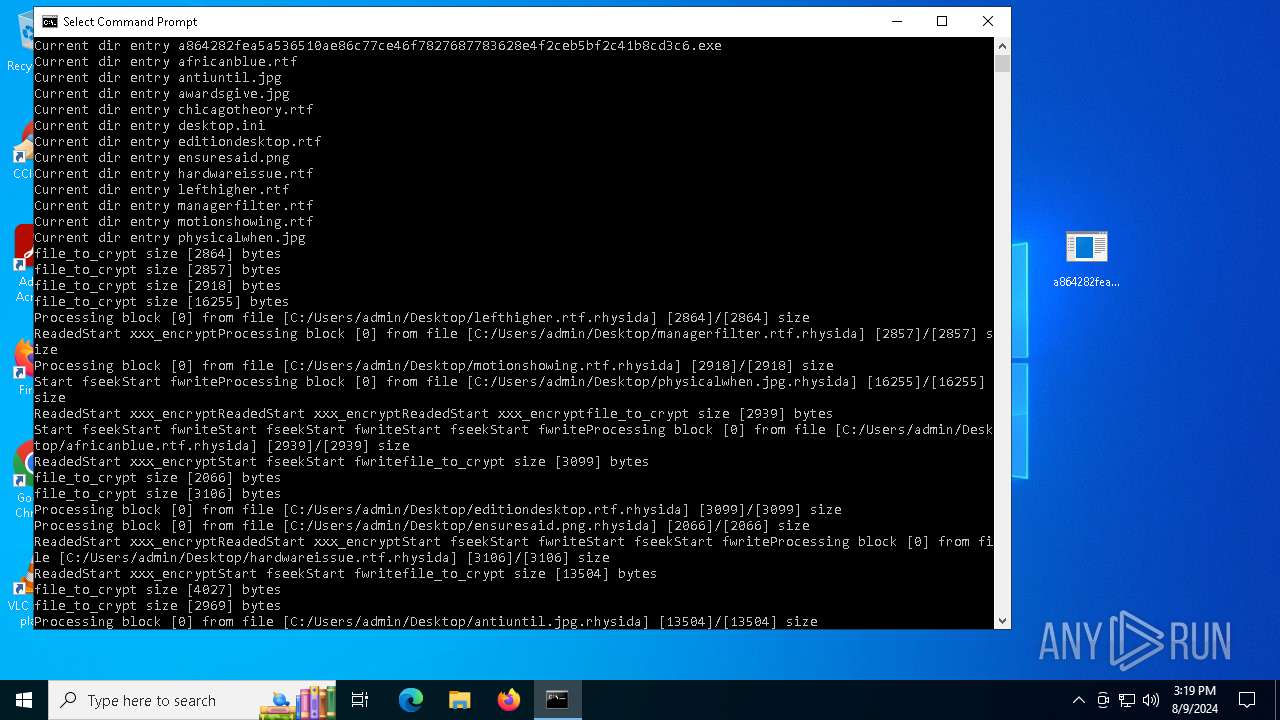
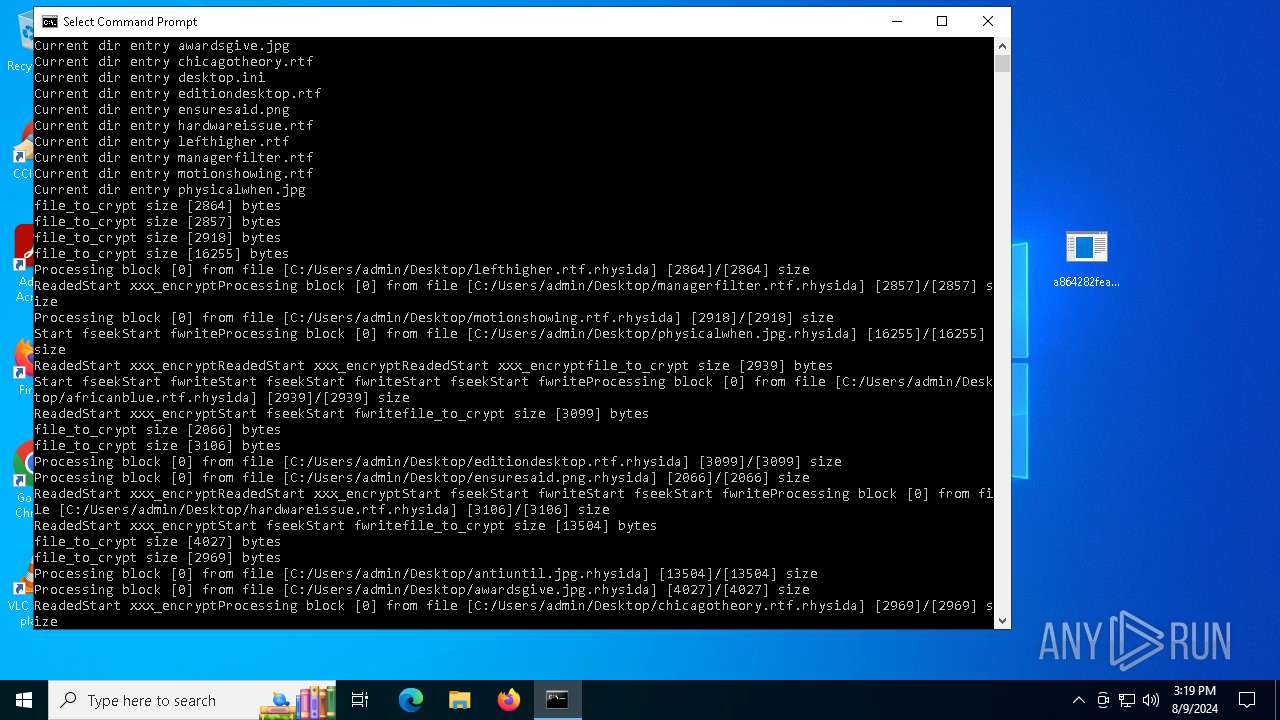
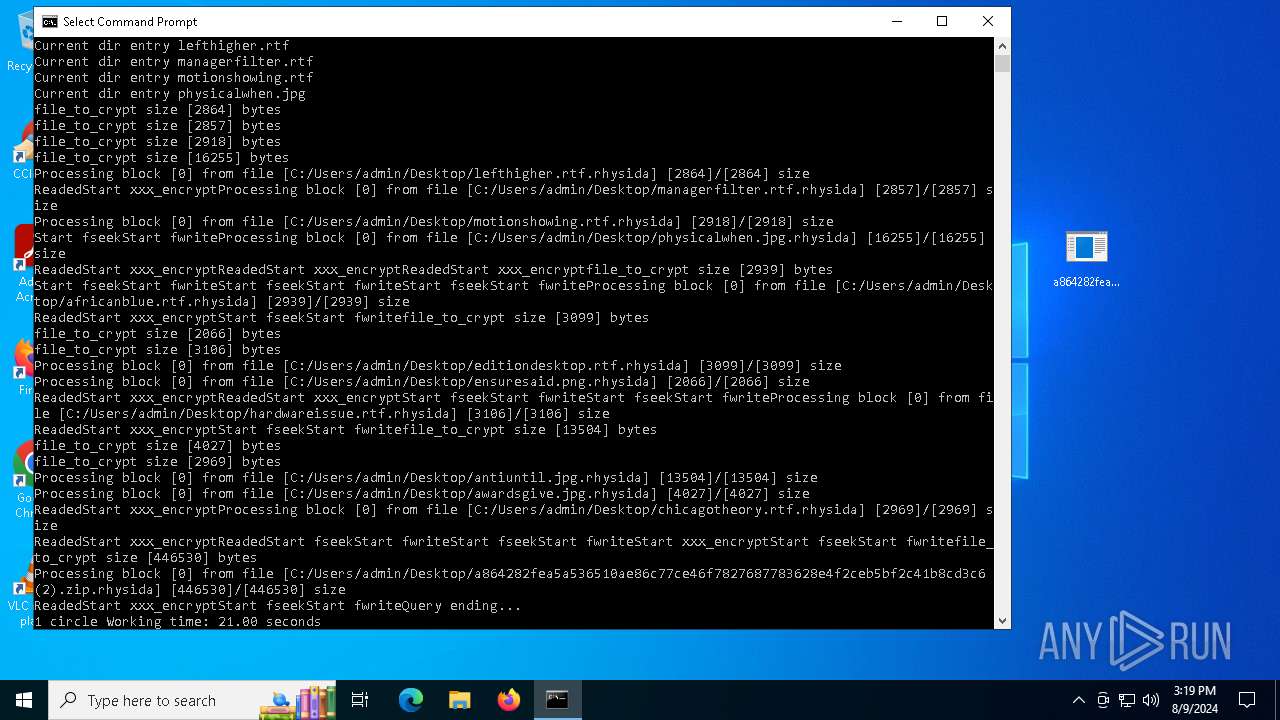
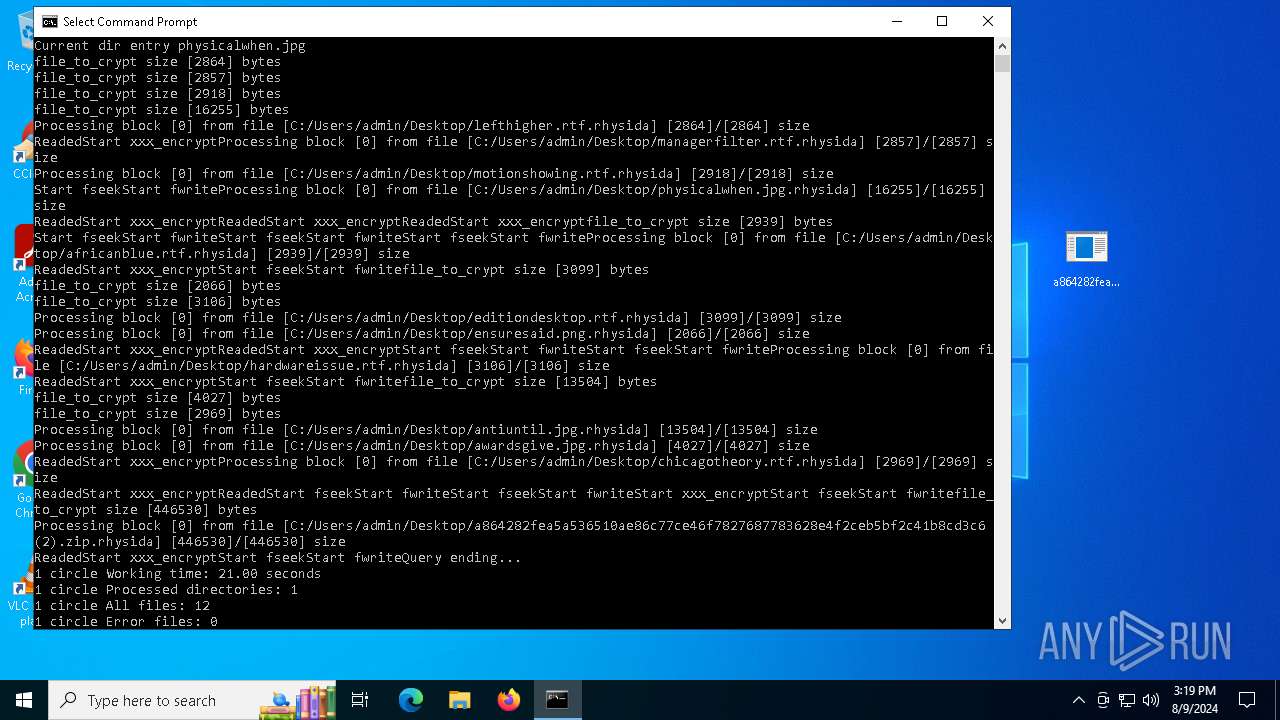
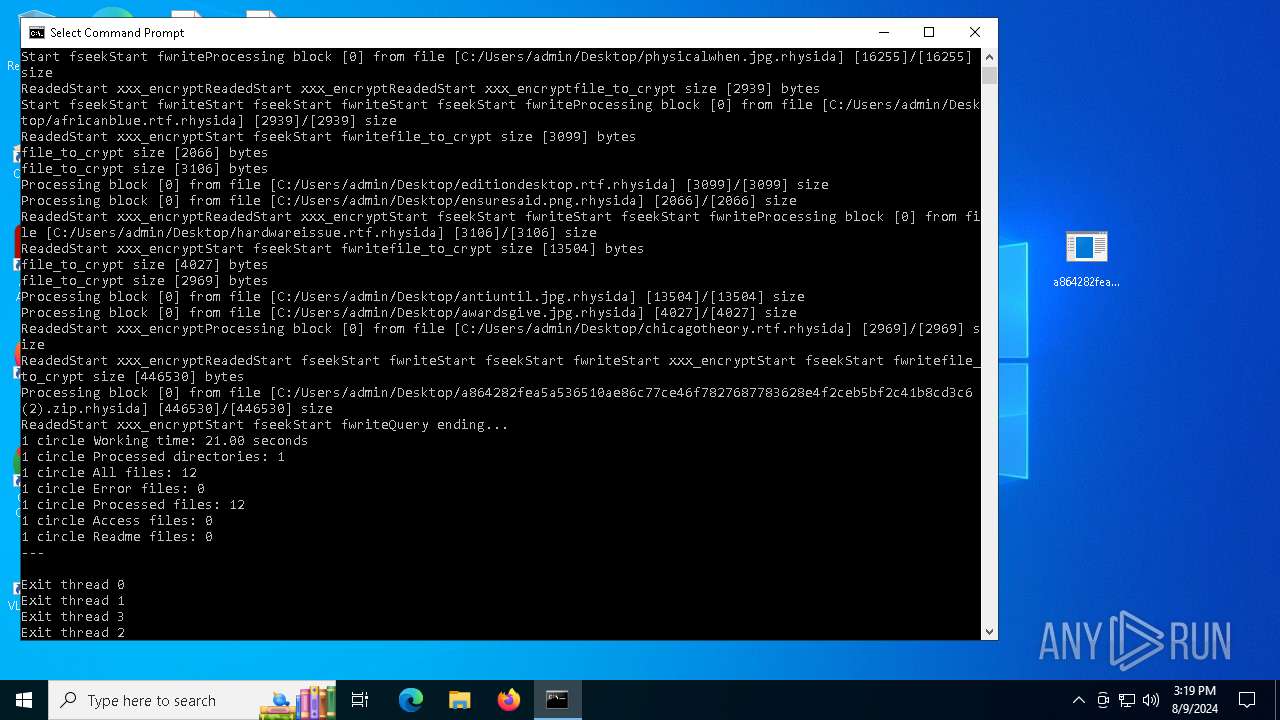
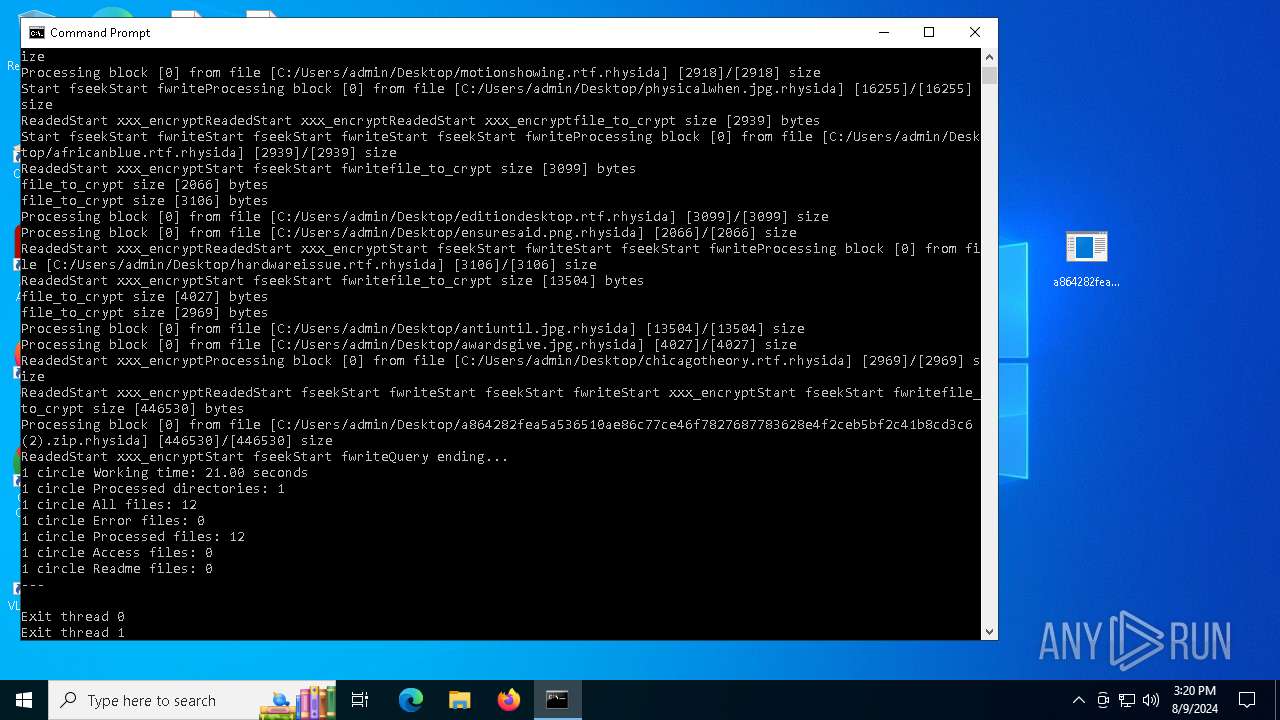
Rhysida note has been found
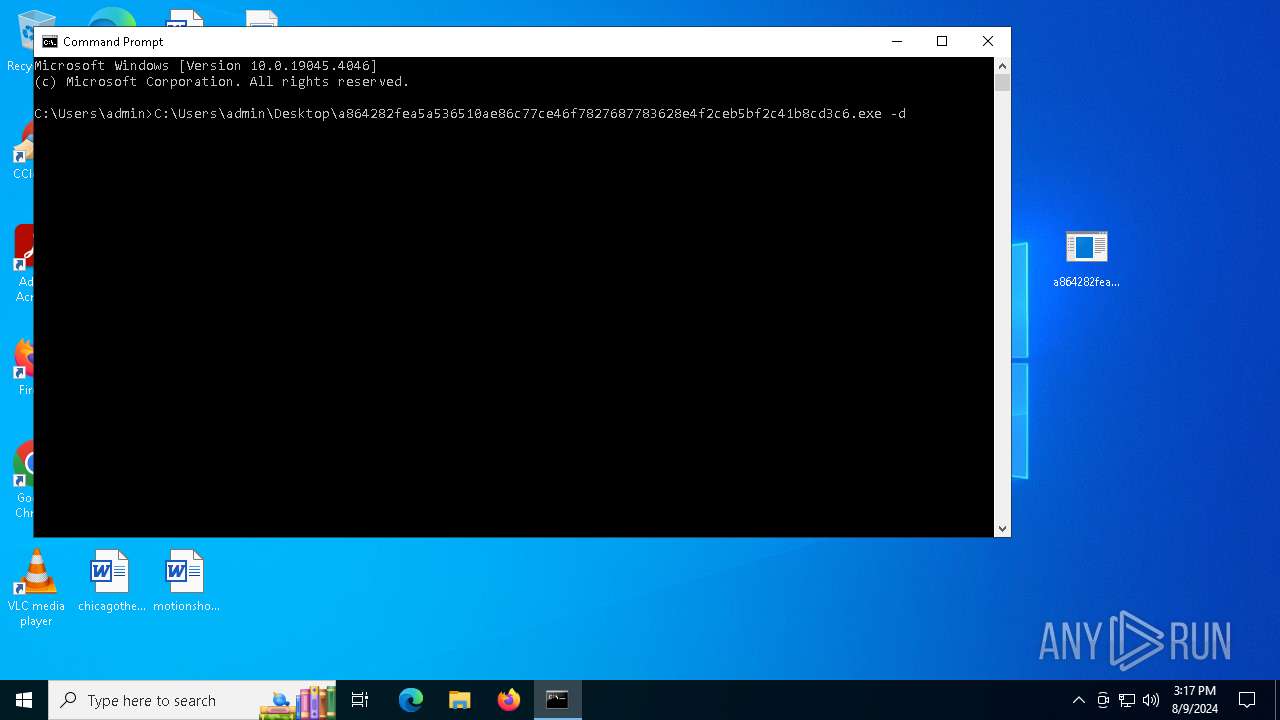
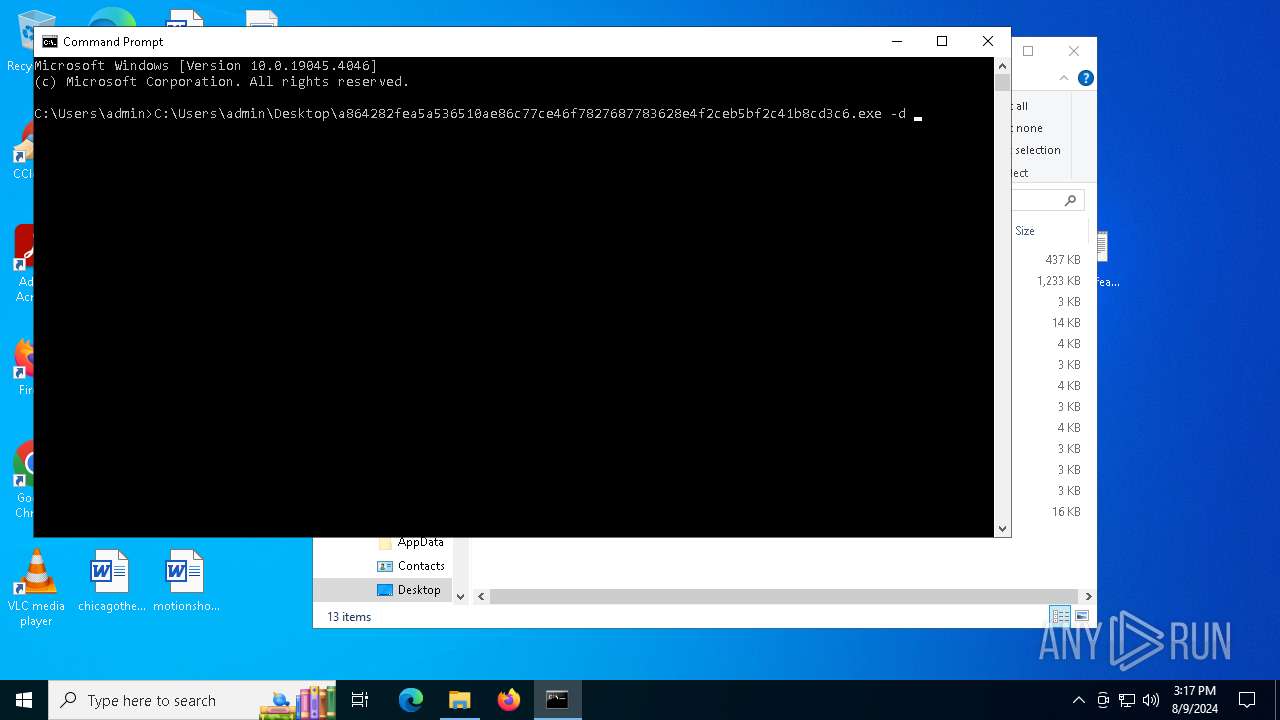
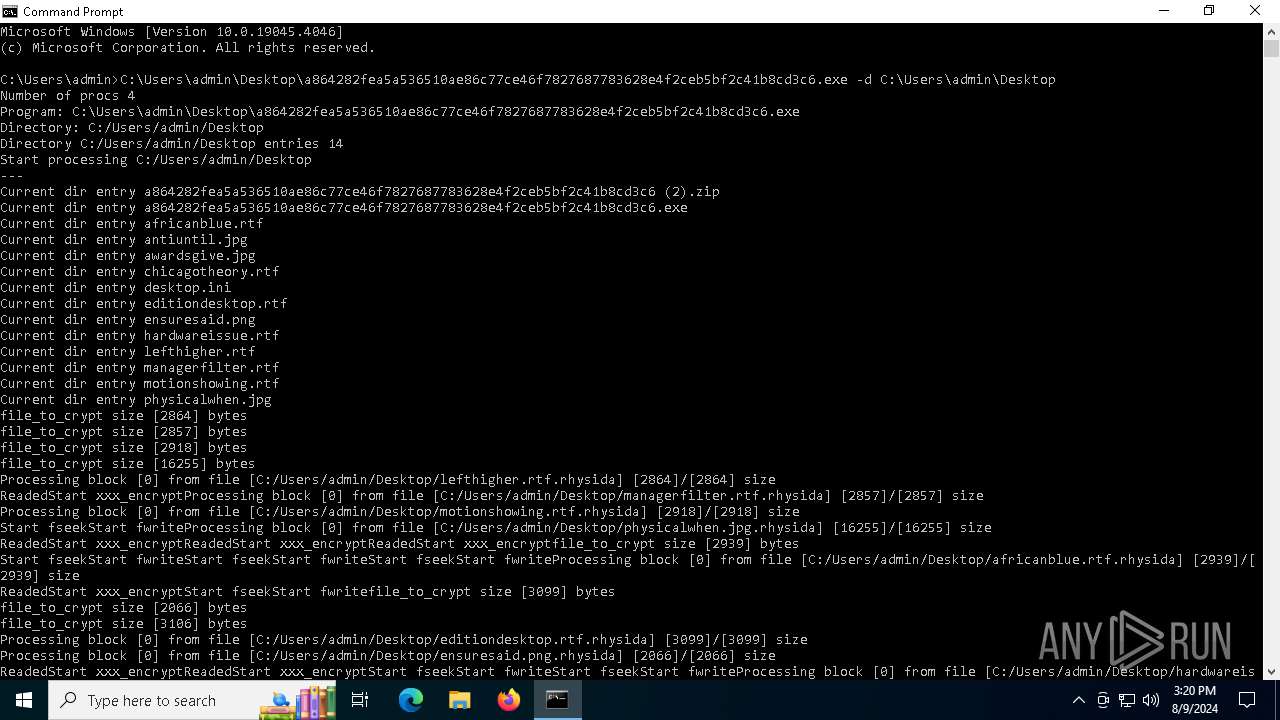
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6712)
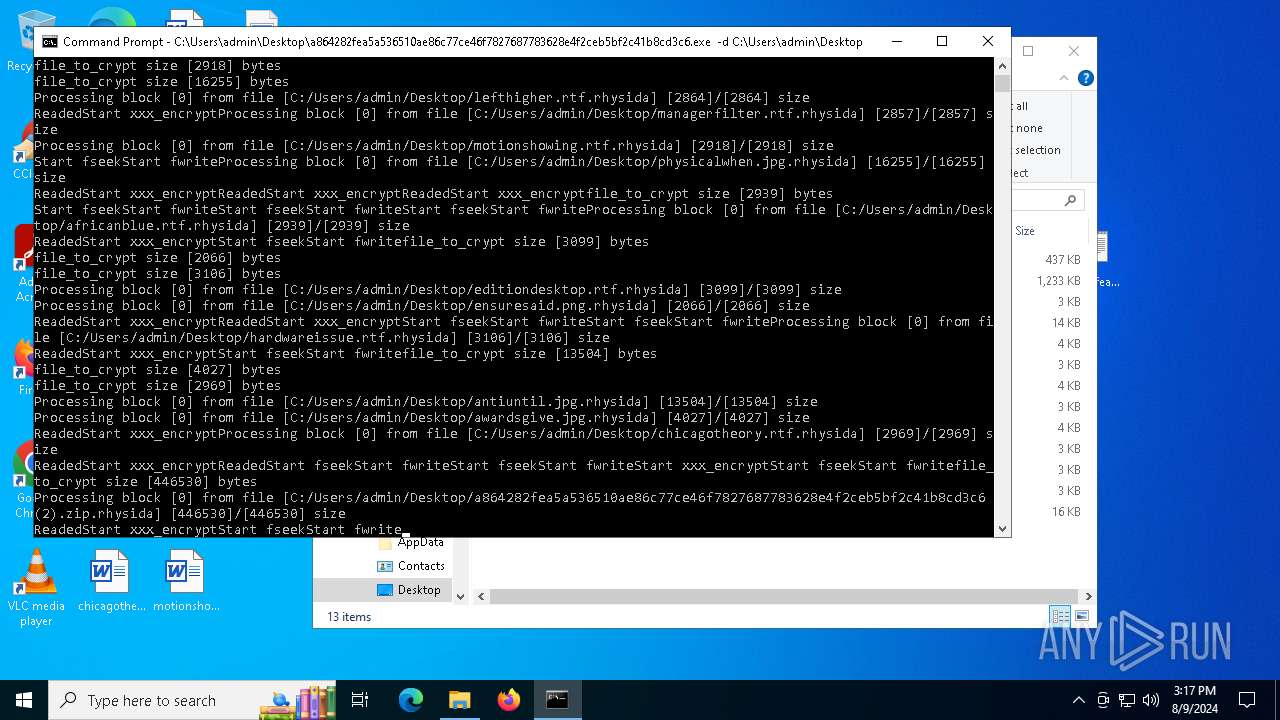
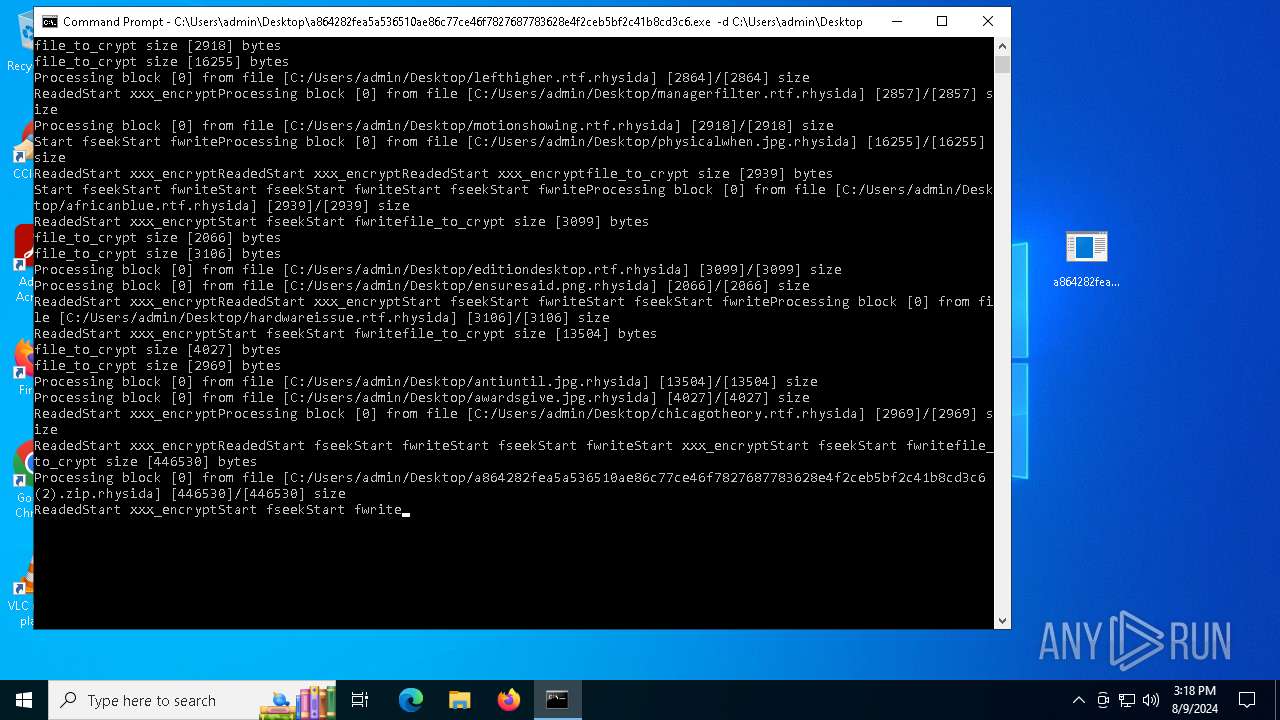
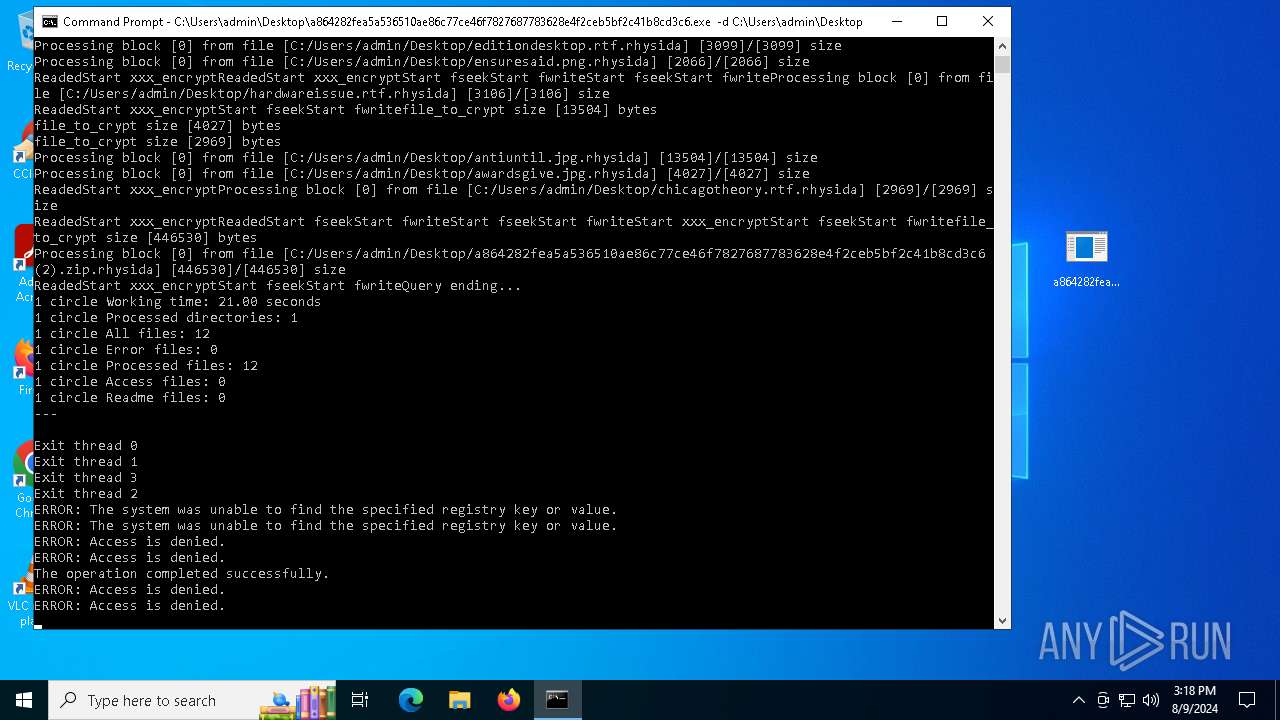
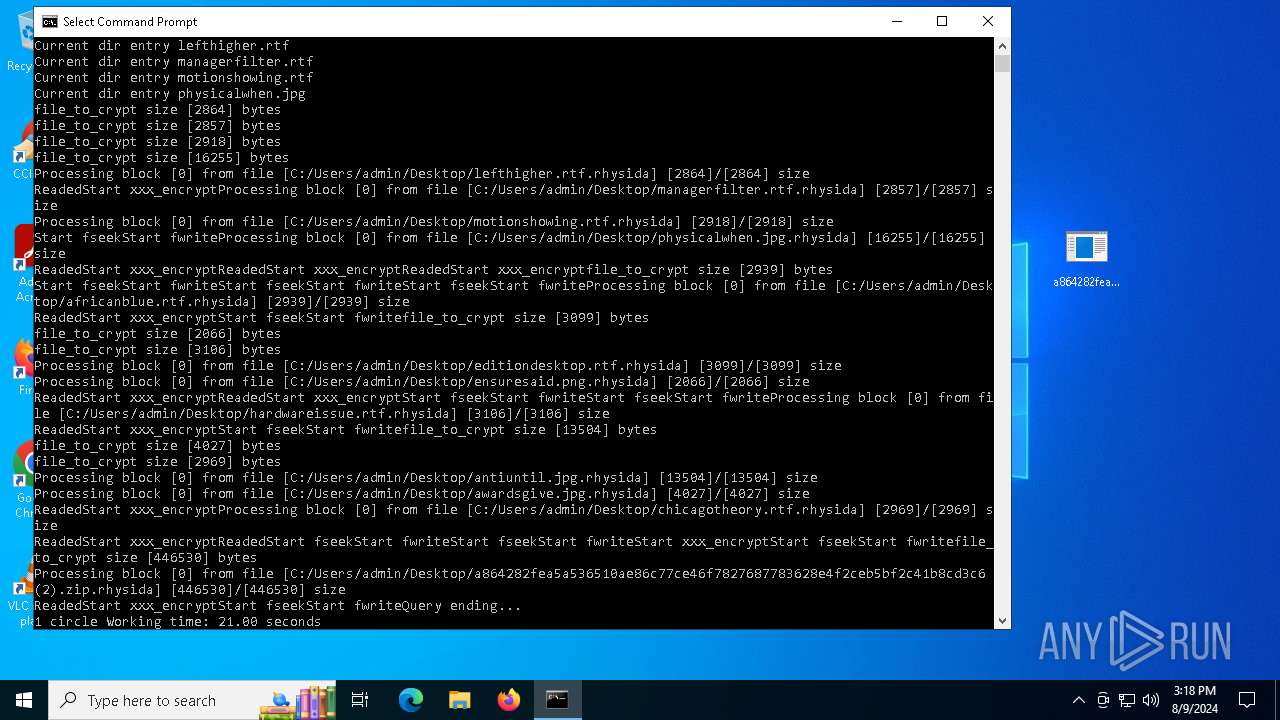
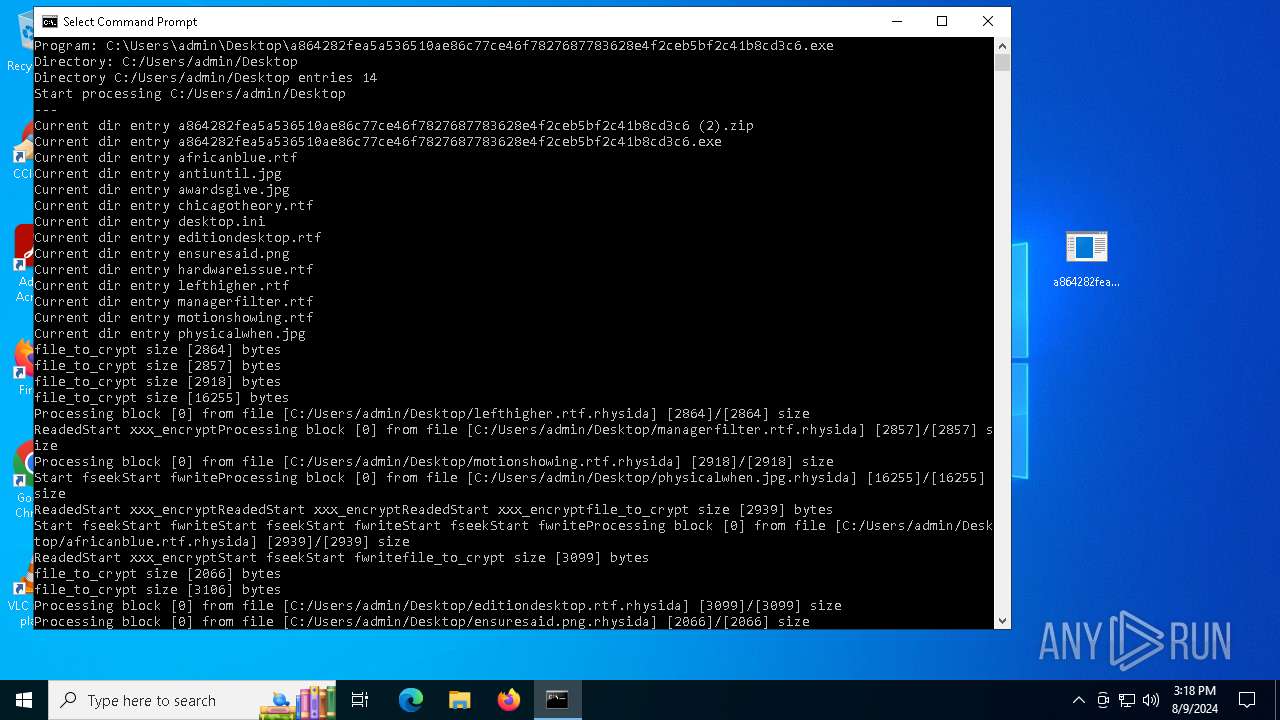
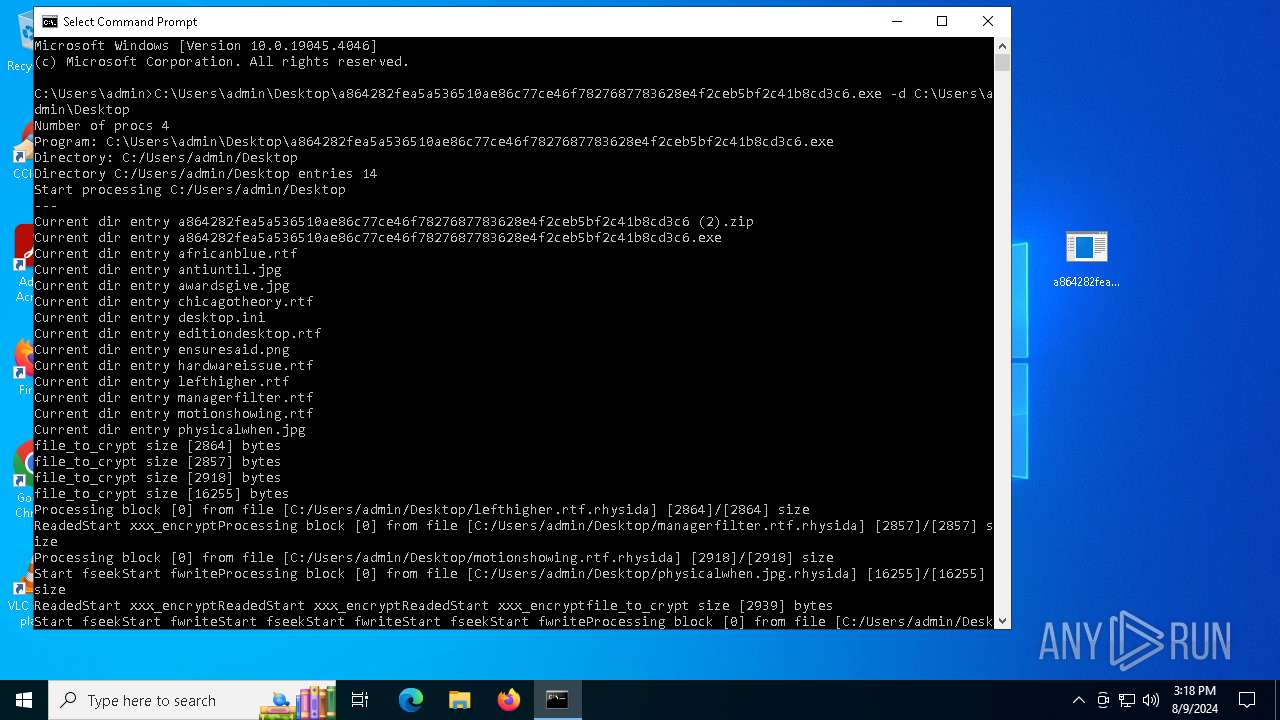
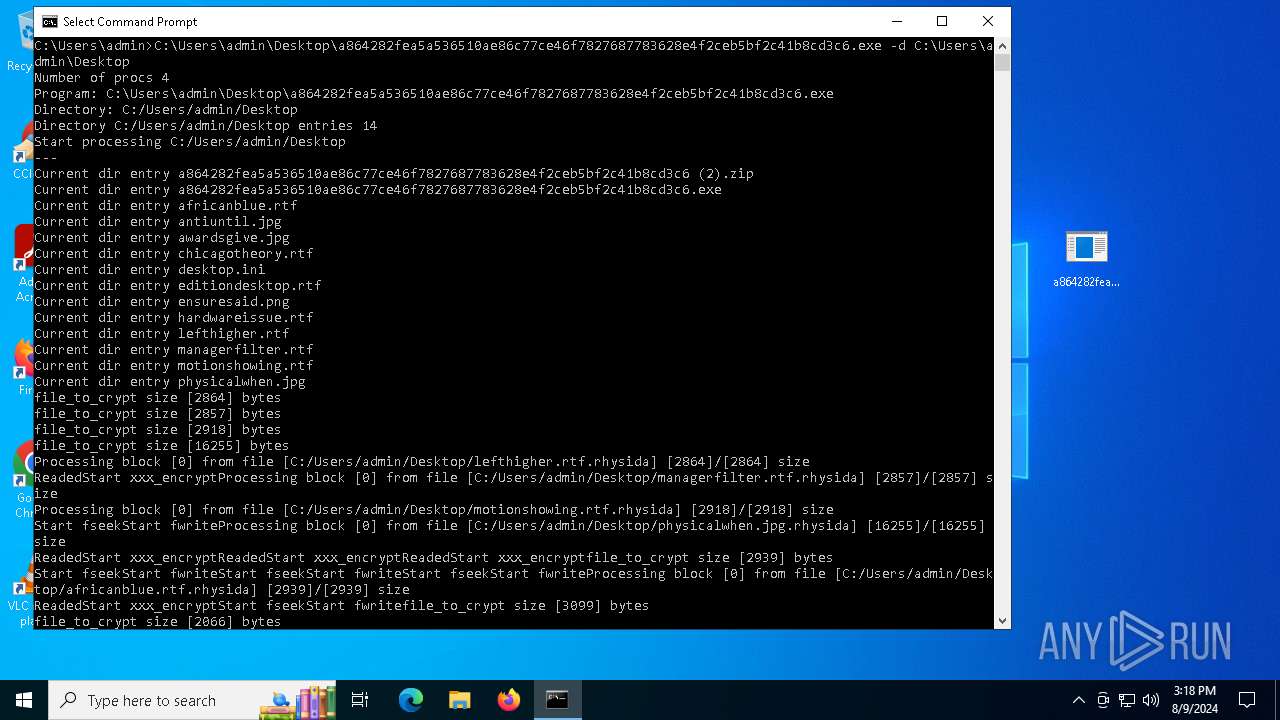
Renames files like ransomware
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6712)
Run PowerShell with an invisible window
- powershell.exe (PID: 6808)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6576)
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6712)
Application launched itself
- cmd.exe (PID: 6984)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 1420)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 6716)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 4772)
- cmd.exe (PID: 3672)
- cmd.exe (PID: 4236)
Starts CMD.EXE for commands execution
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6712)
- cmd.exe (PID: 6984)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 1420)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 6716)
- cmd.exe (PID: 4772)
- cmd.exe (PID: 3672)
- cmd.exe (PID: 5920)
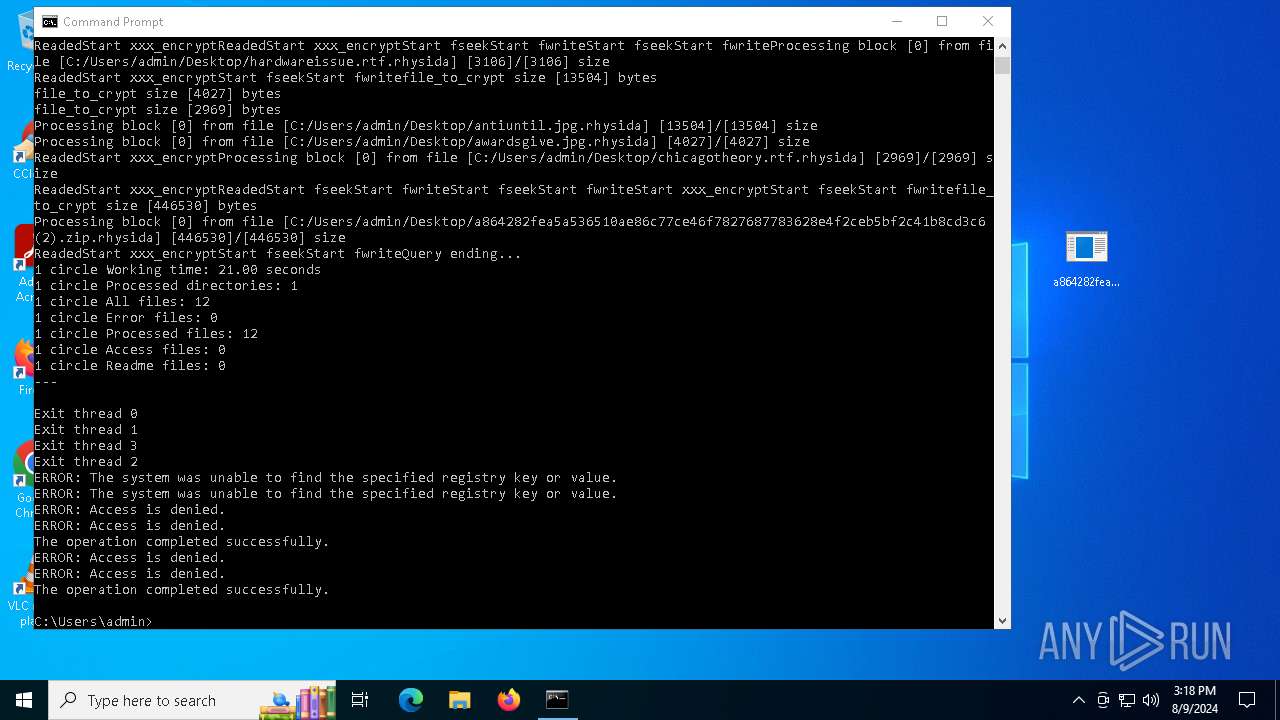
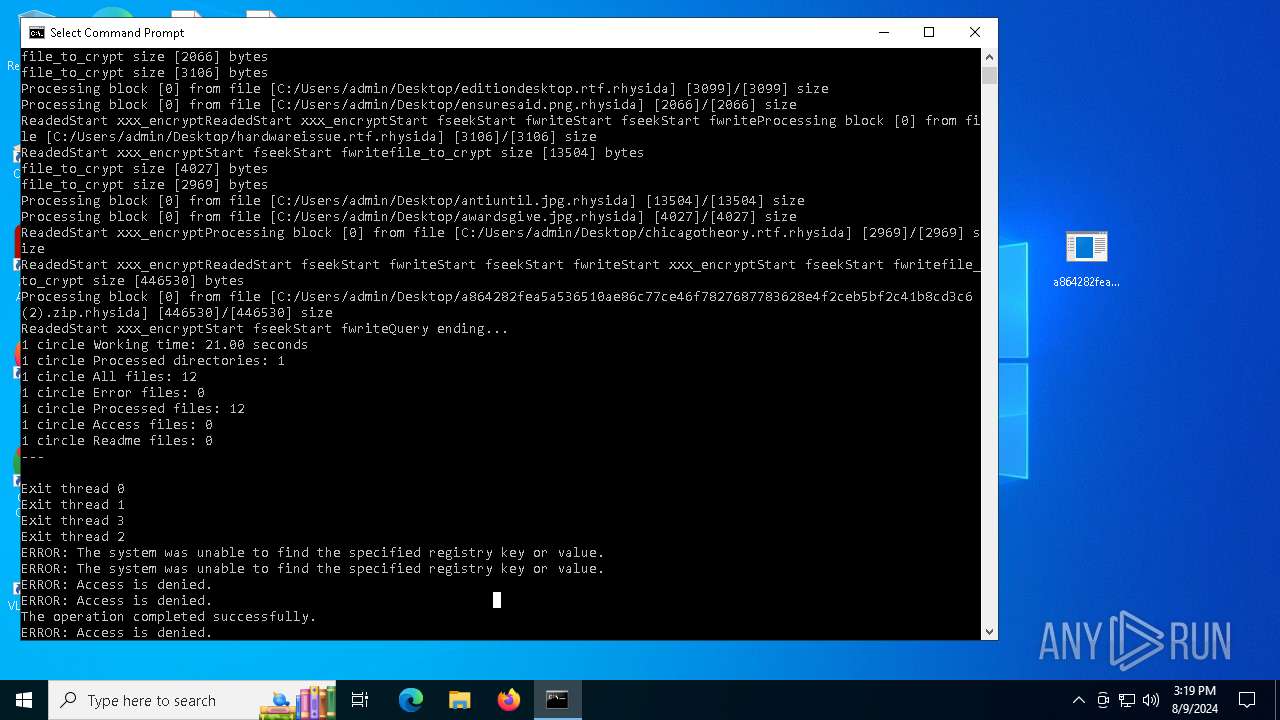
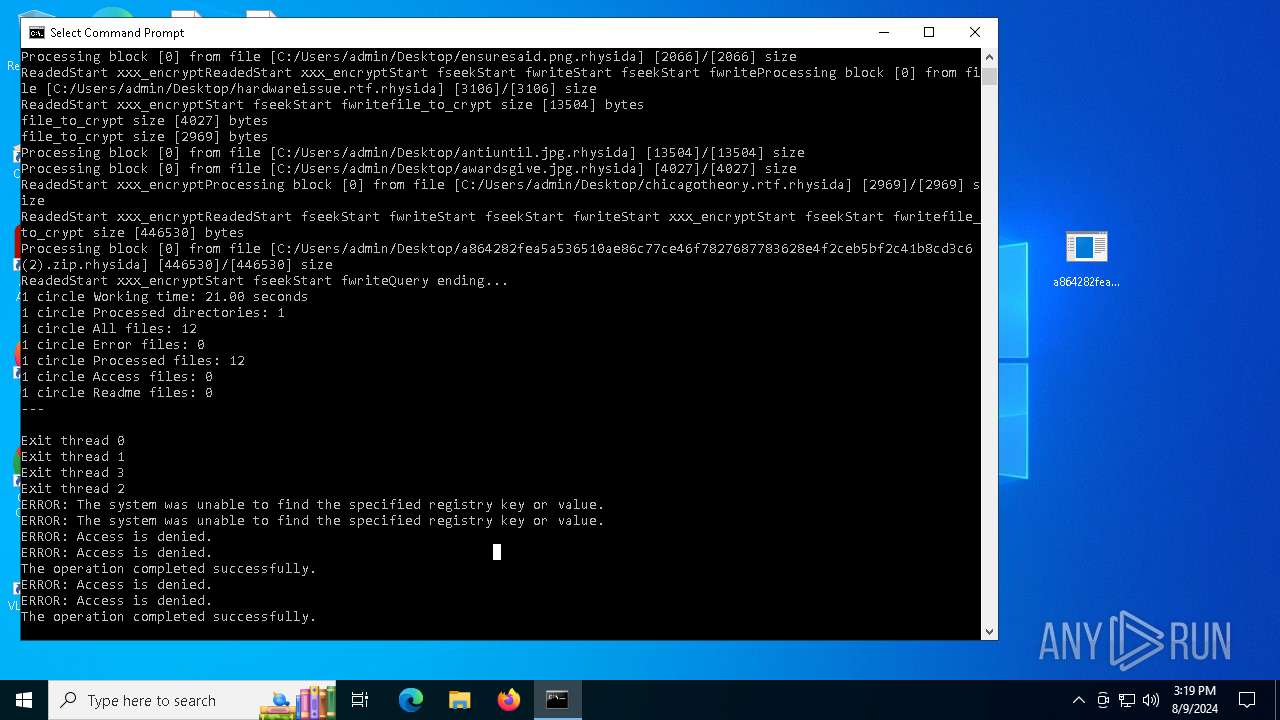
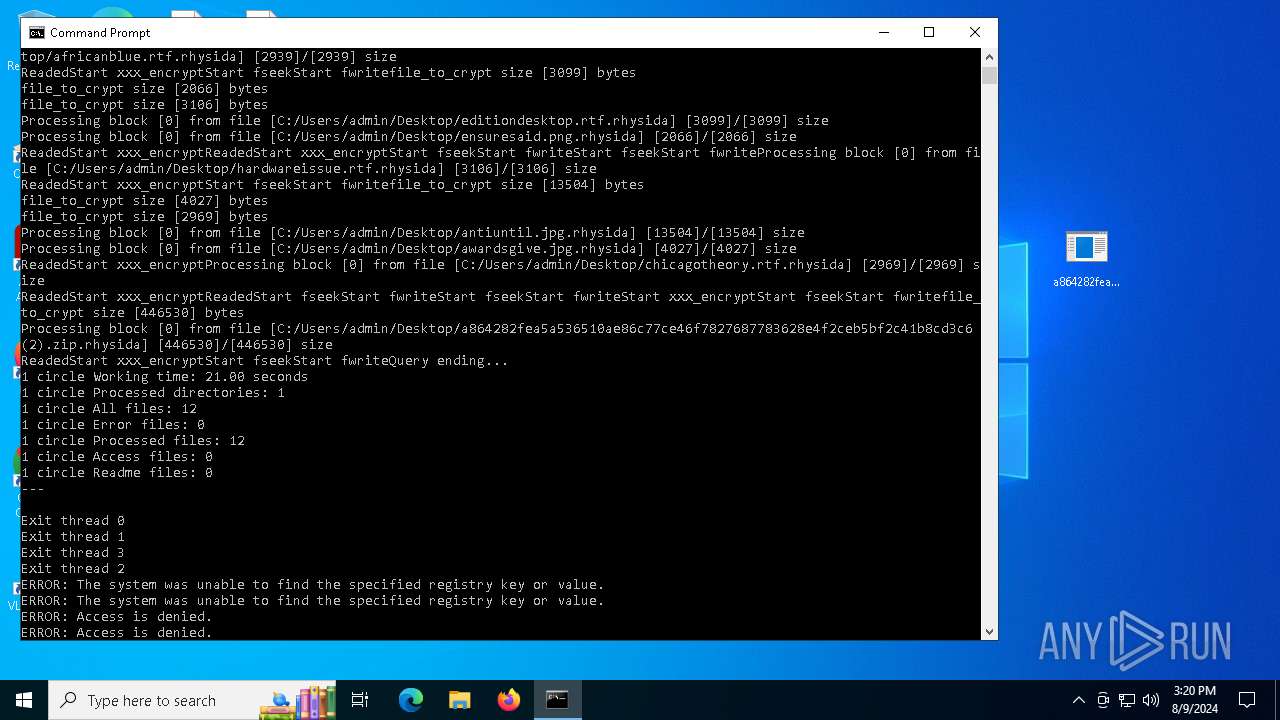
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2720)
- cmd.exe (PID: 5084)
- cmd.exe (PID: 2044)
- cmd.exe (PID: 6240)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 1292)
Likely accesses (executes) a file from the Public directory
- reg.exe (PID: 6168)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 5084)
- cmd.exe (PID: 1292)
- reg.exe (PID: 3996)
- cmd.exe (PID: 6716)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2720)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 6276)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 6808)
Changes the desktop background image
- reg.exe (PID: 6168)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6576)
Application launched itself
- msedge.exe (PID: 5068)
- msedge.exe (PID: 3992)
Checks supported languages
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6712)
- identity_helper.exe (PID: 6296)
- TextInputHost.exe (PID: 236)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3992)
- msedge.exe (PID: 5068)
Dropped object may contain TOR URL's
- a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe (PID: 6712)
- WinRAR.exe (PID: 6576)
Reads the computer name
- TextInputHost.exe (PID: 236)
- identity_helper.exe (PID: 6296)
Reads Environment values
- identity_helper.exe (PID: 6296)
Manual execution by a user
- msedge.exe (PID: 5068)
- cmd.exe (PID: 6148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2023:07:08 22:37:08 |
| ZipCRC: | 0x7a7b5808 |
| ZipCompressedSize: | 446274 |
| ZipUncompressedSize: | 1261752 |
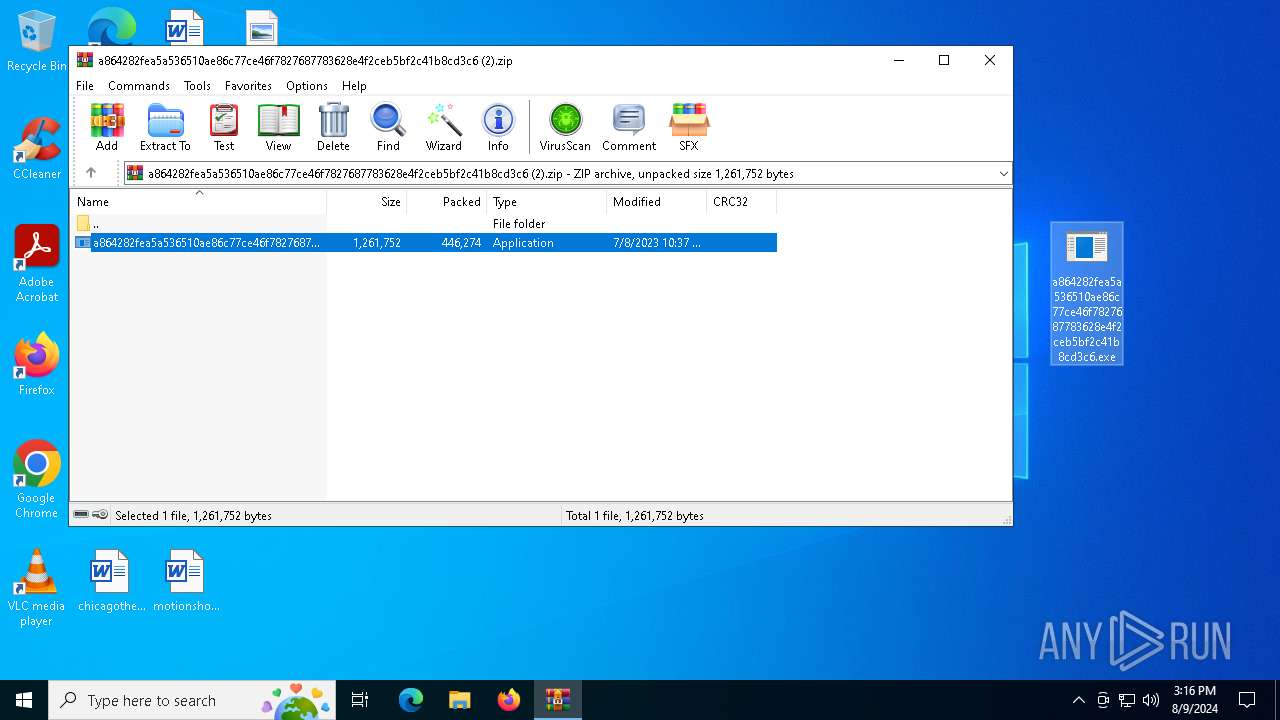
| ZipFileName: | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe |
Total processes
203
Monitored processes
80
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 252 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4072 --field-trial-handle=2276,i,7329721195941558940,17581287795074549036,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1116 | reg delete "HKCU\Conttol Panel\Desktop" /v Wallpaper /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5660 --field-trial-handle=2280,i,1556337099292016492,14650569213419930050,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1292 | cmd.exe /c reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v Wallpaper /t REG_SZ /d "C:\Users\Public\bg.jpg" /f | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1420 | C:\WINDOWS\system32\cmd.exe /c cmd.exe /c reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop" /v NoChangingWallPaper /t REG_SZ /d 1 /f | C:\Windows\System32\cmd.exe | — | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2384 --field-trial-handle=2280,i,1556337099292016492,14650569213419930050,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2044 | cmd.exe /c reg delete "HKCU\Conttol Panel\Desktop" /v WallpaperStyle /f | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 470
Read events
25 348
Write events
118
Delete events
4
Modification events
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6 (2).zip | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
21
Suspicious files
519
Text files
167
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFee710.TMP | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFee710.TMP | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFee71f.TMP | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFee74e.TMP | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFee74e.TMP | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
116
DNS requests
172
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1452 | msedge.exe | GET | 304 | 88.221.221.186:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1452 | msedge.exe | GET | 304 | 104.108.145.136:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1452 | msedge.exe | GET | 304 | 104.108.145.136:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
6384 | svchost.exe | HEAD | 200 | 2.16.183.229:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465454&P2=404&P3=2&P4=lZ0nim4fEATQwRFHMl%2bu6lNfEyP0IgF%2b31gCyDJIJt274QdE%2b1dlLx6VRO%2fLqH3ccS7FvIRLpL9Be4AidkwOZA%3d%3d | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 206 | 2.16.183.229:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465454&P2=404&P3=2&P4=lZ0nim4fEATQwRFHMl%2bu6lNfEyP0IgF%2b31gCyDJIJt274QdE%2b1dlLx6VRO%2fLqH3ccS7FvIRLpL9Be4AidkwOZA%3d%3d | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 206 | 2.16.183.229:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465454&P2=404&P3=2&P4=lZ0nim4fEATQwRFHMl%2bu6lNfEyP0IgF%2b31gCyDJIJt274QdE%2b1dlLx6VRO%2fLqH3ccS7FvIRLpL9Be4AidkwOZA%3d%3d | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 206 | 2.16.183.229:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e456c896-44a6-416b-bdf2-a332bb03a659?P1=1723465454&P2=404&P3=2&P4=lZ0nim4fEATQwRFHMl%2bu6lNfEyP0IgF%2b31gCyDJIJt274QdE%2b1dlLx6VRO%2fLqH3ccS7FvIRLpL9Be4AidkwOZA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4064 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4064 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 88.221.221.155:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 88.221.221.154:443 | th.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
r.bing.com |
| whitelisted |
t-ring-fallback-s2.msedge.net |
| unknown |
teams-ring.msedge.net |
| unknown |
ax-ring.msedge.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1452 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1452 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1452 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1452 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
1452 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
1452 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |