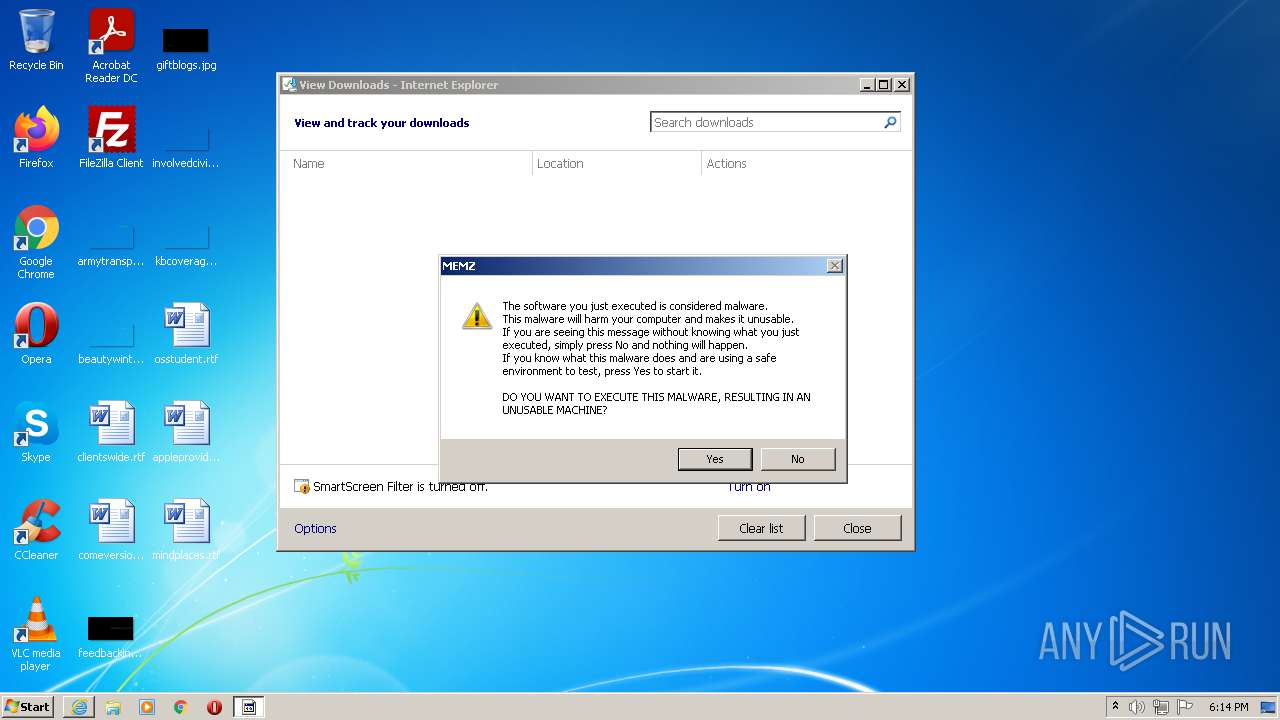
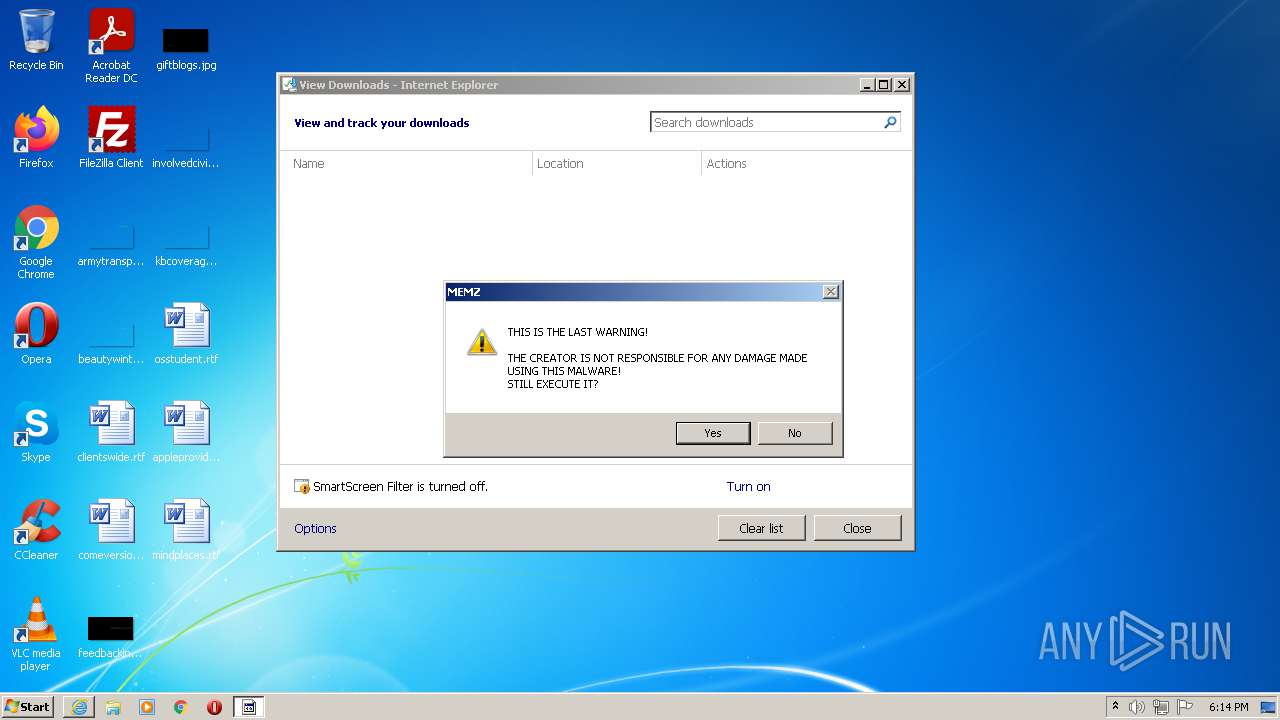
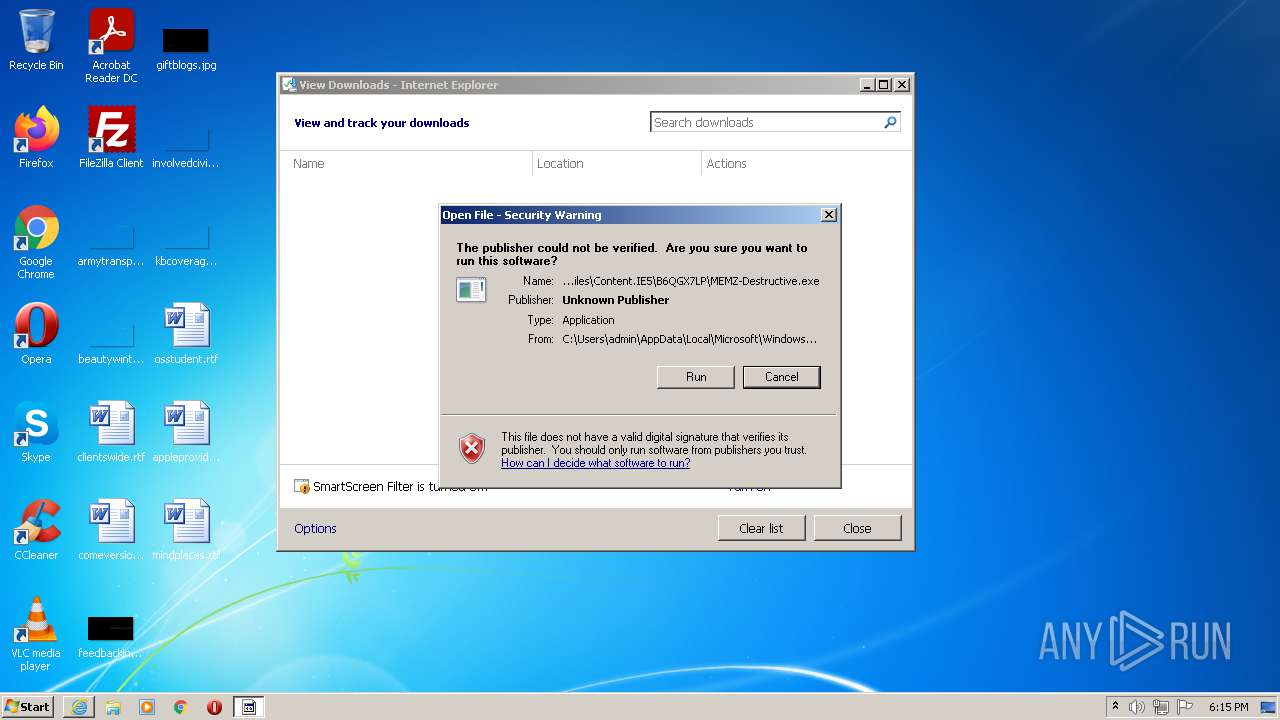
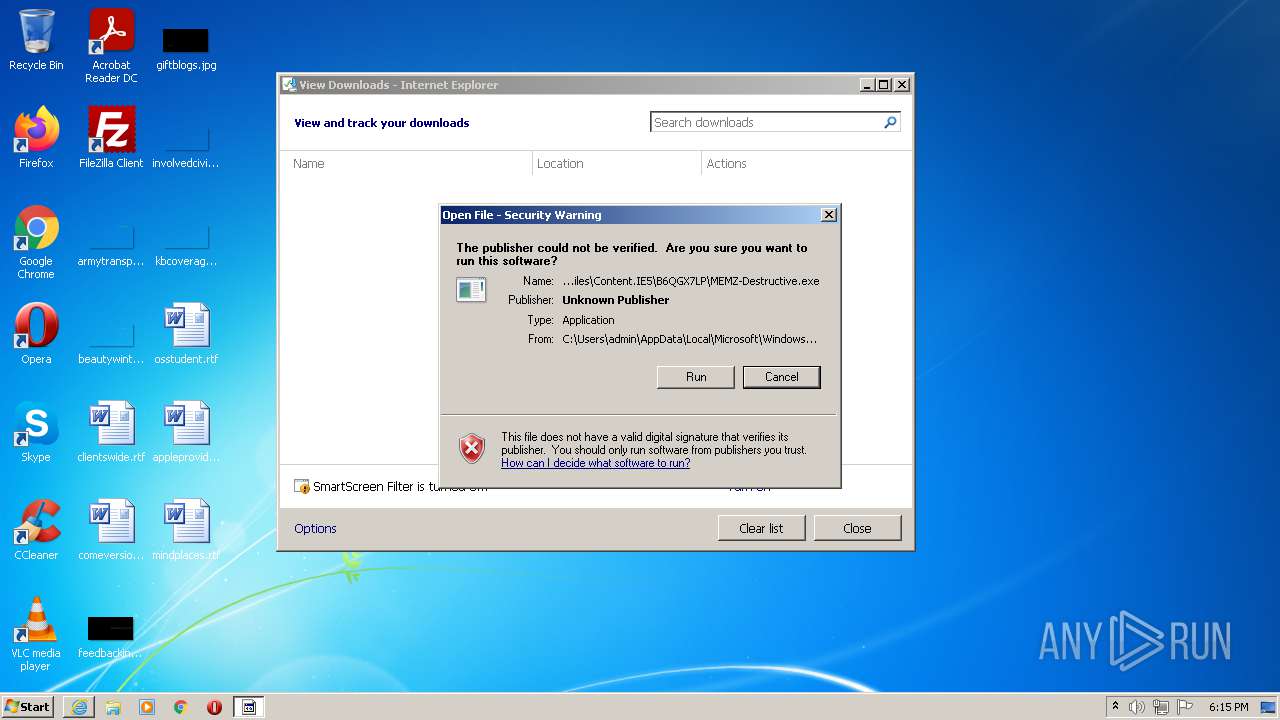
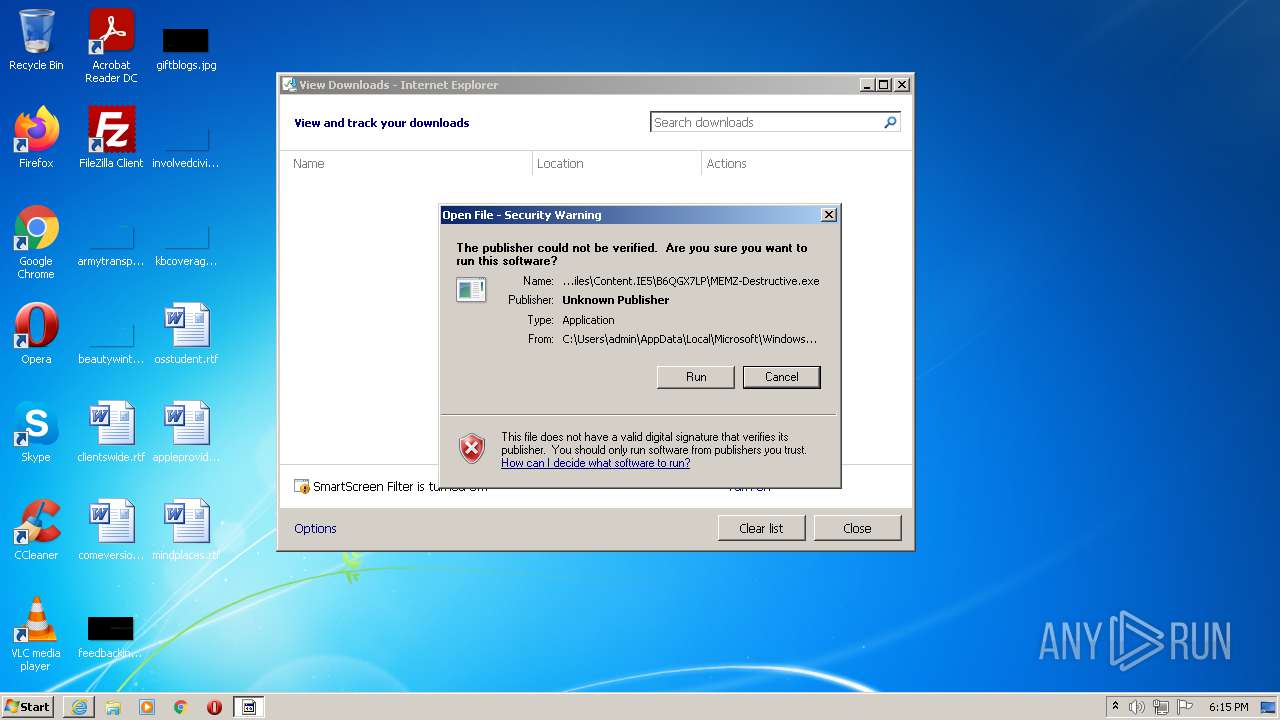
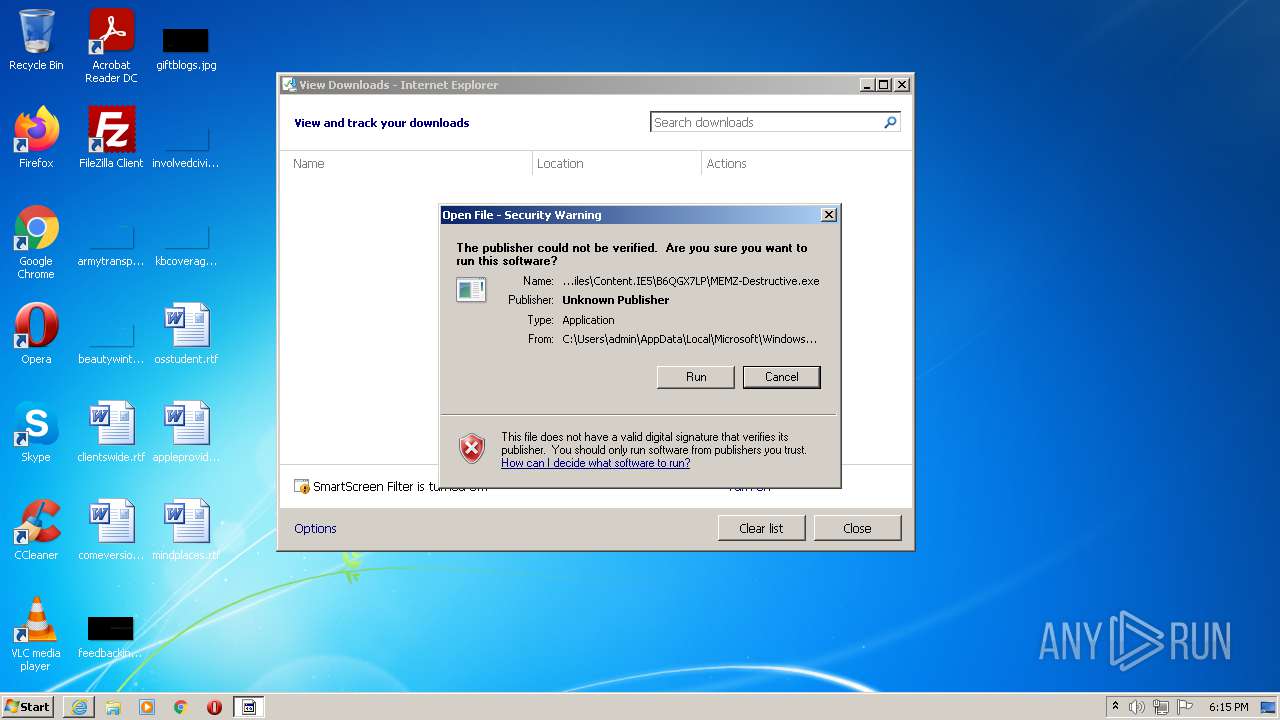
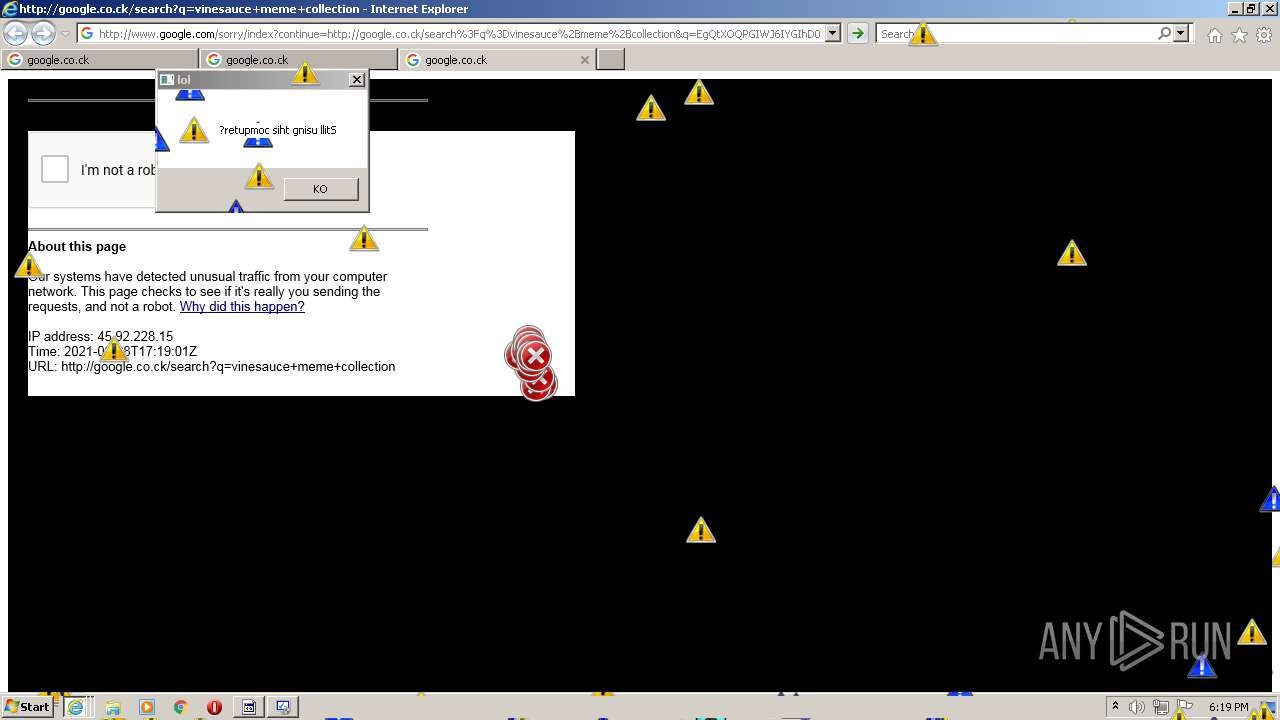
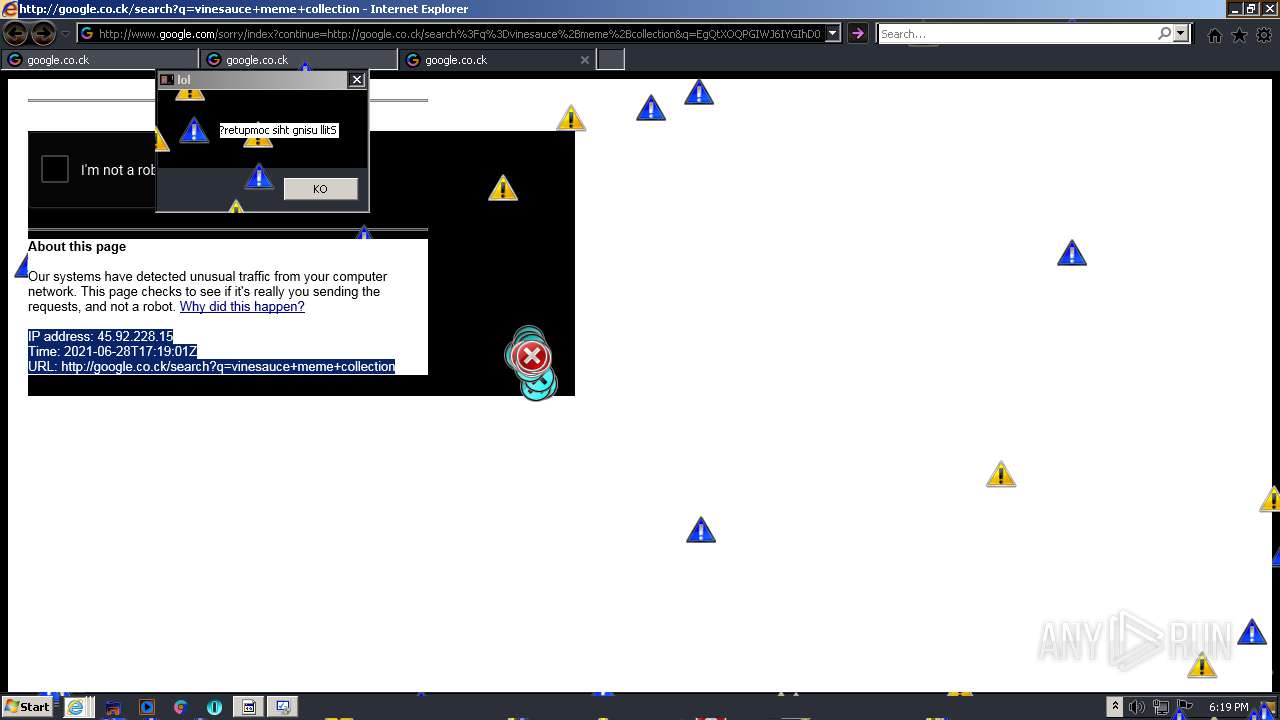
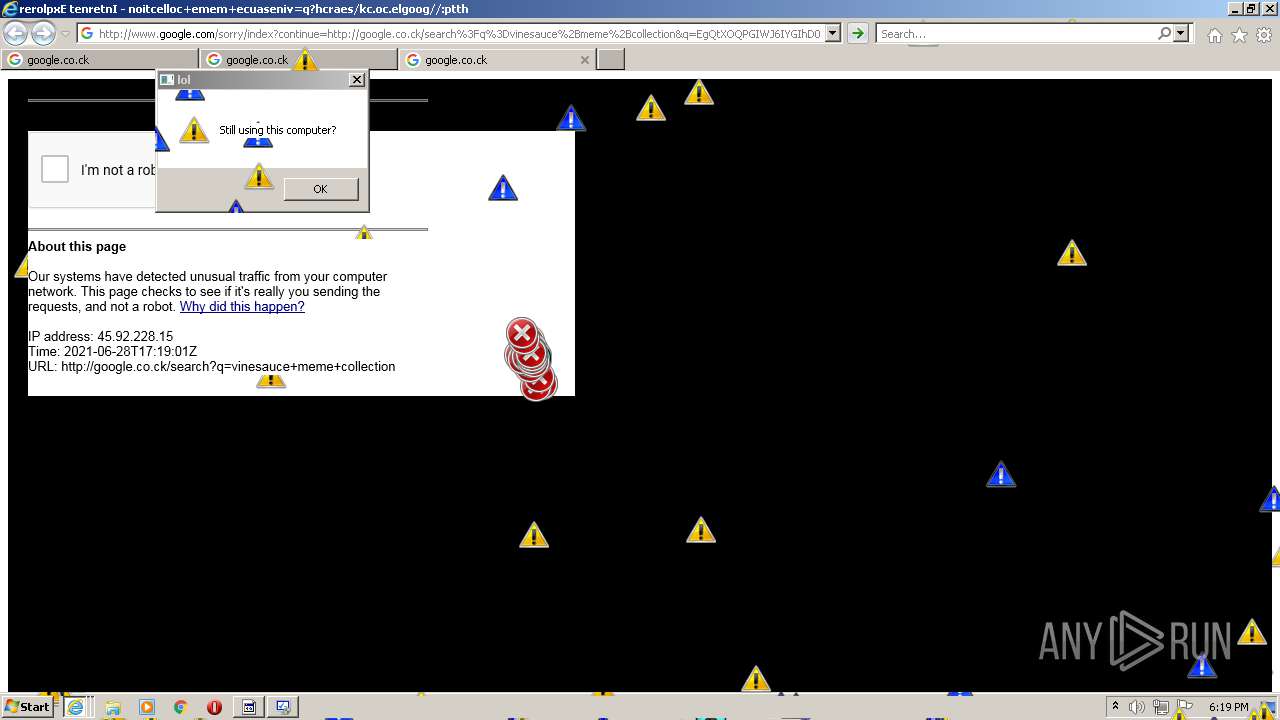
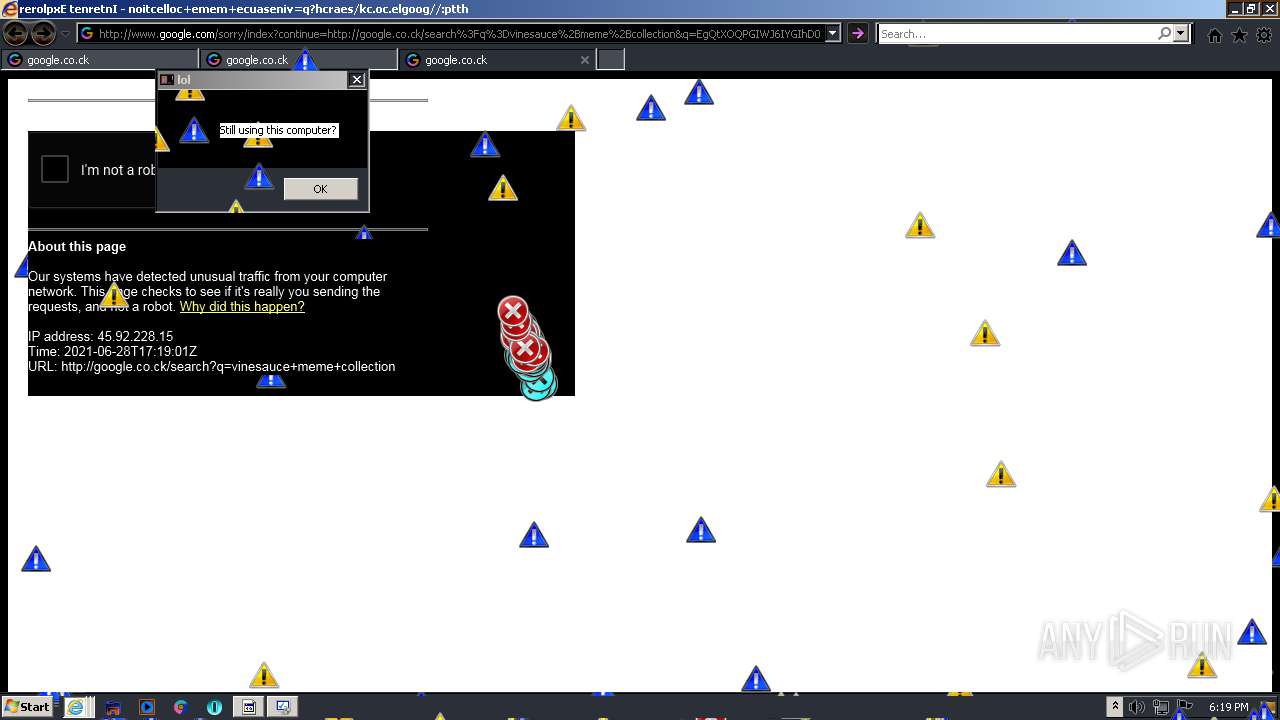
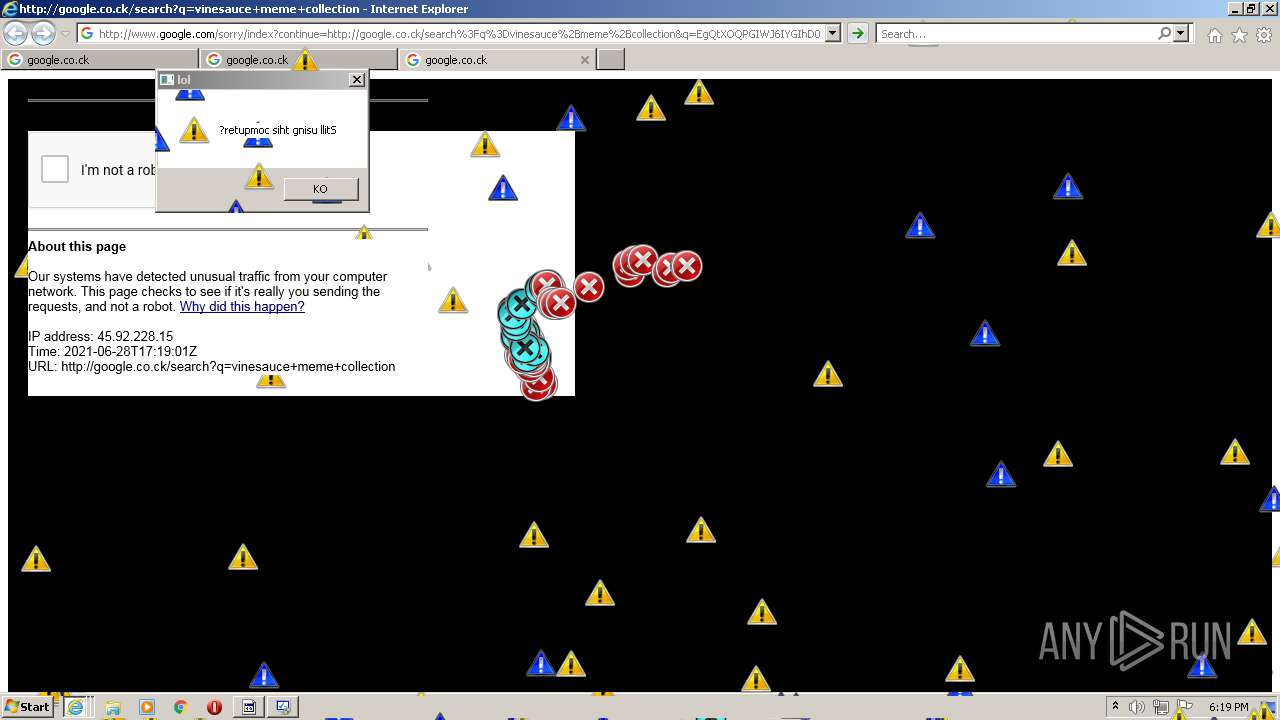
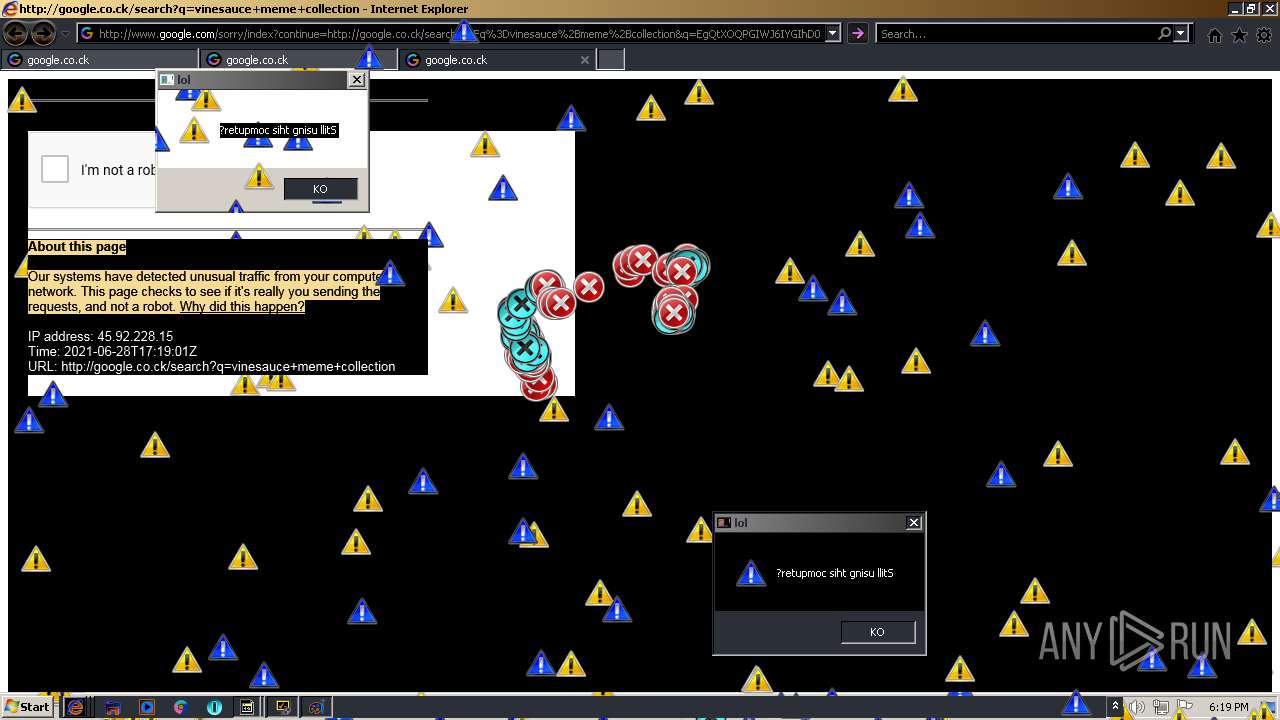
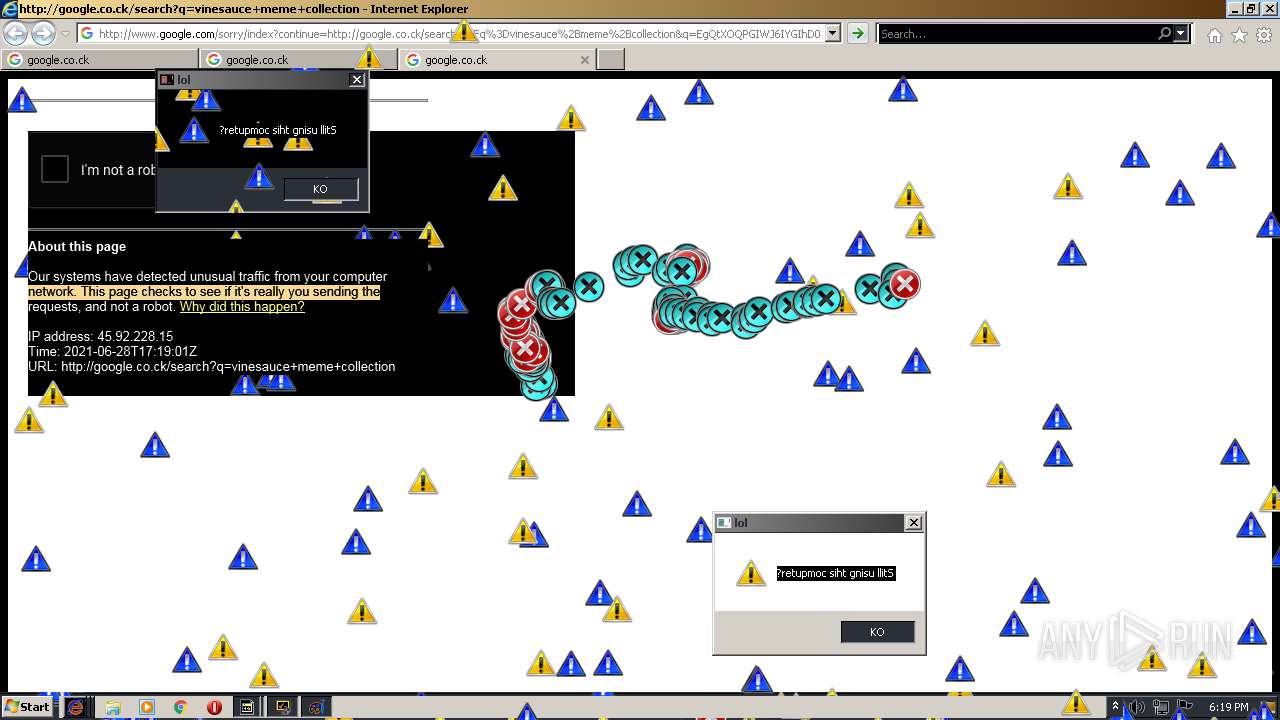
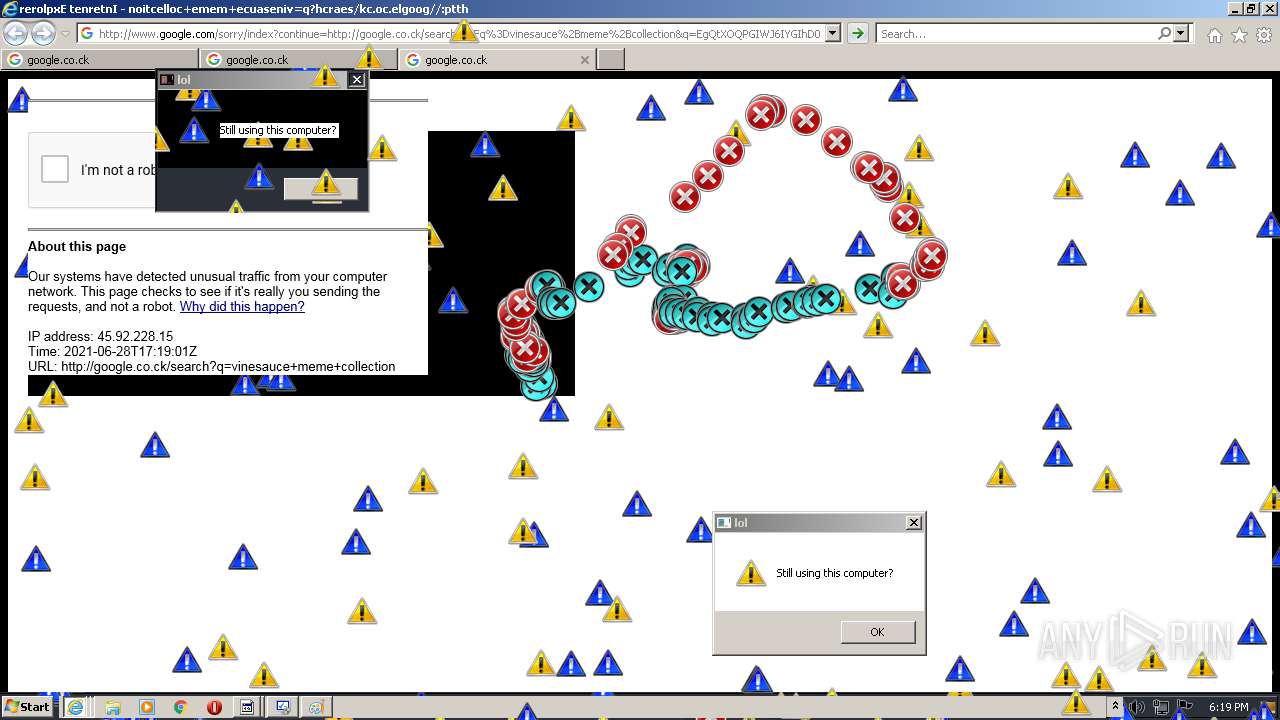
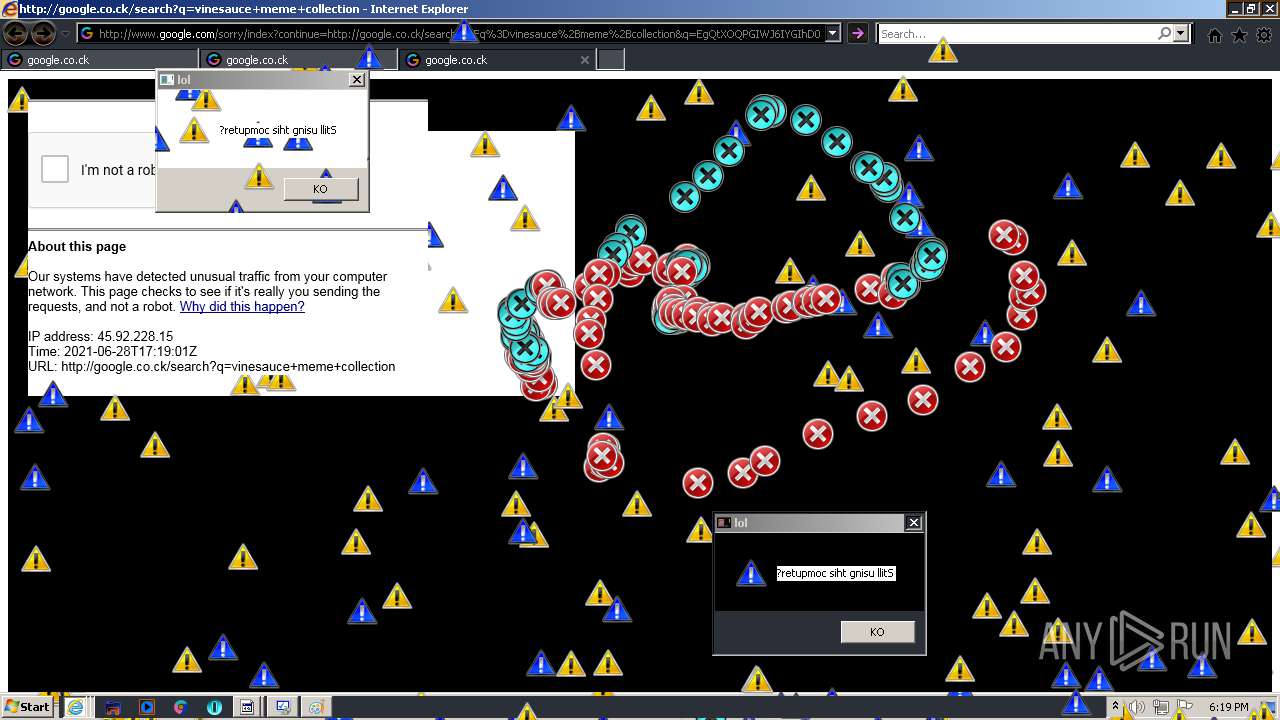
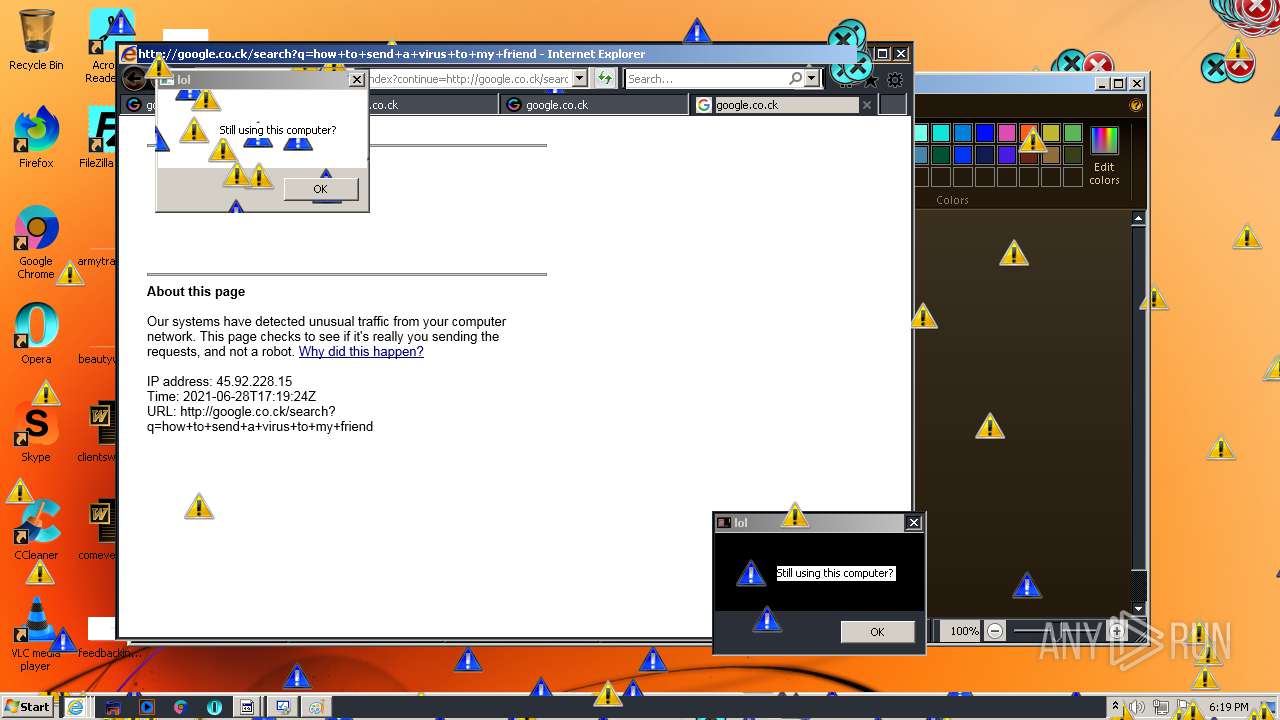
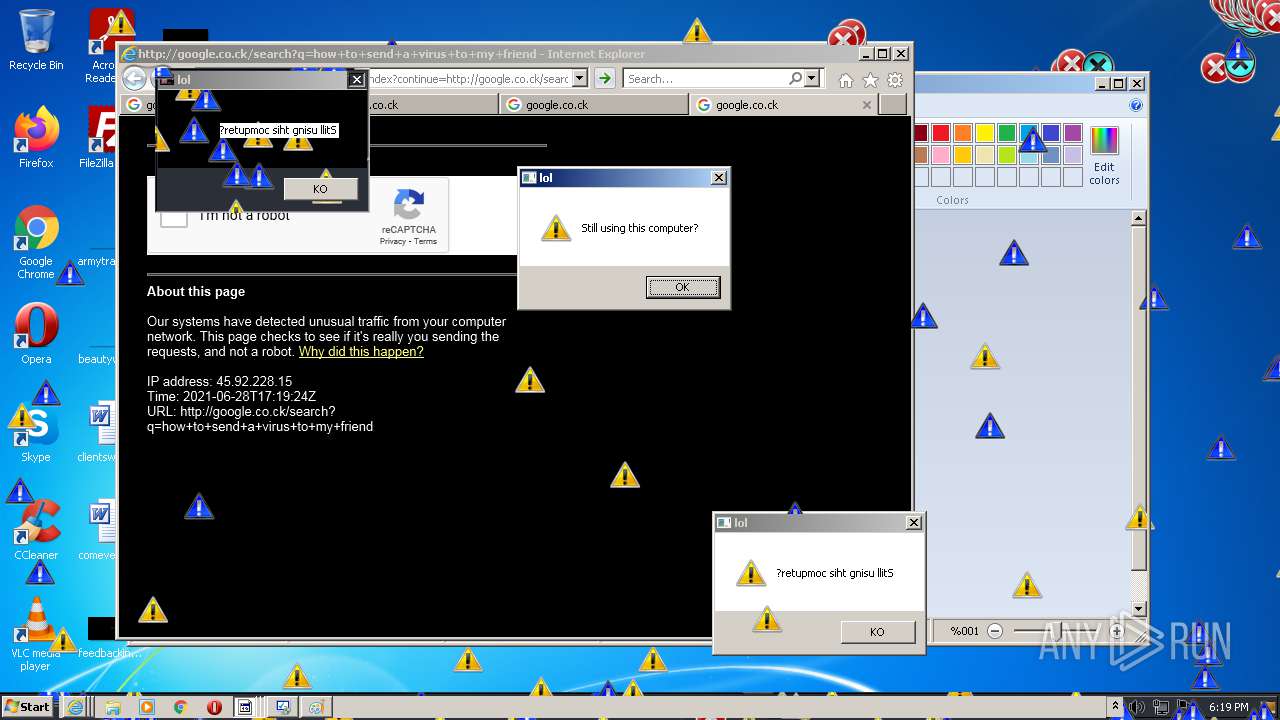
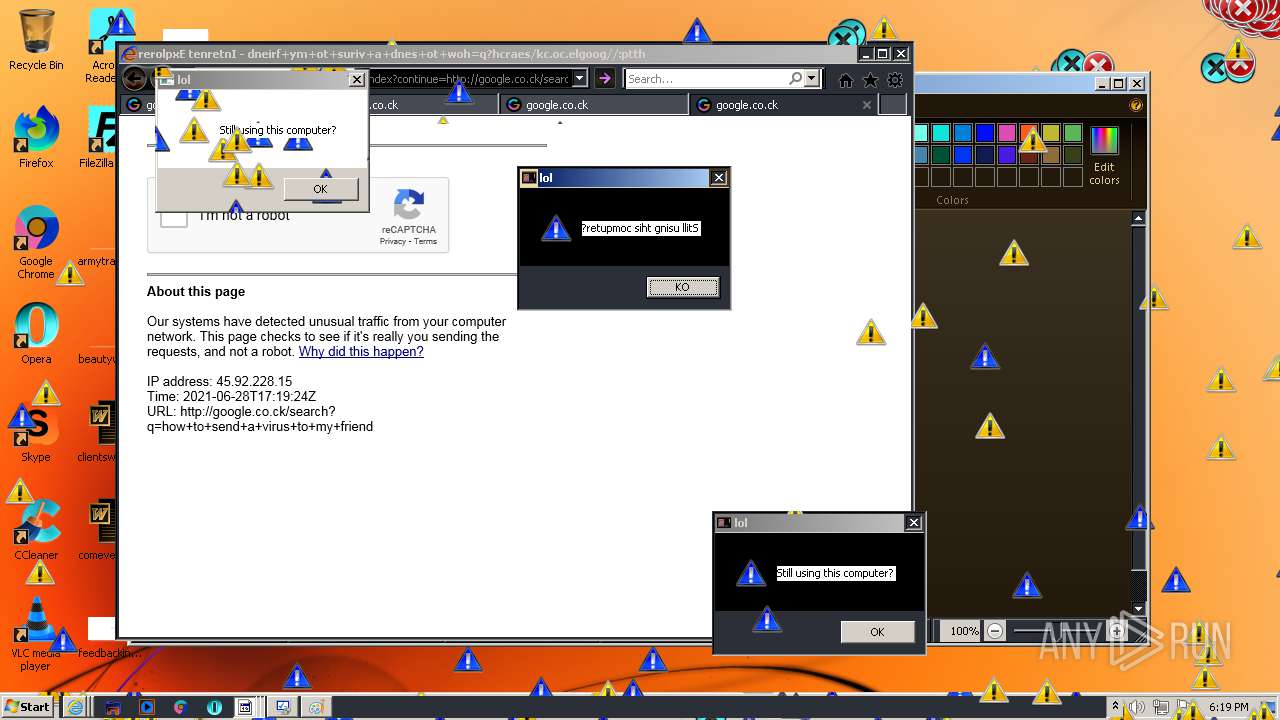
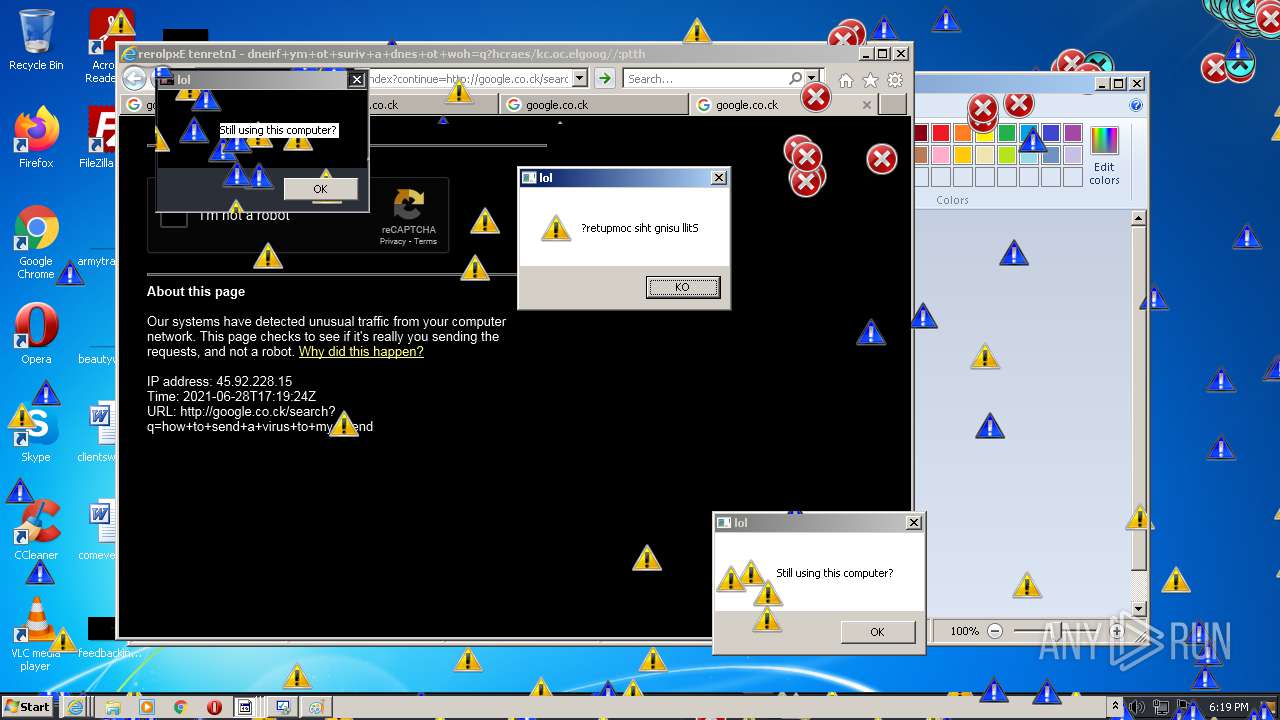
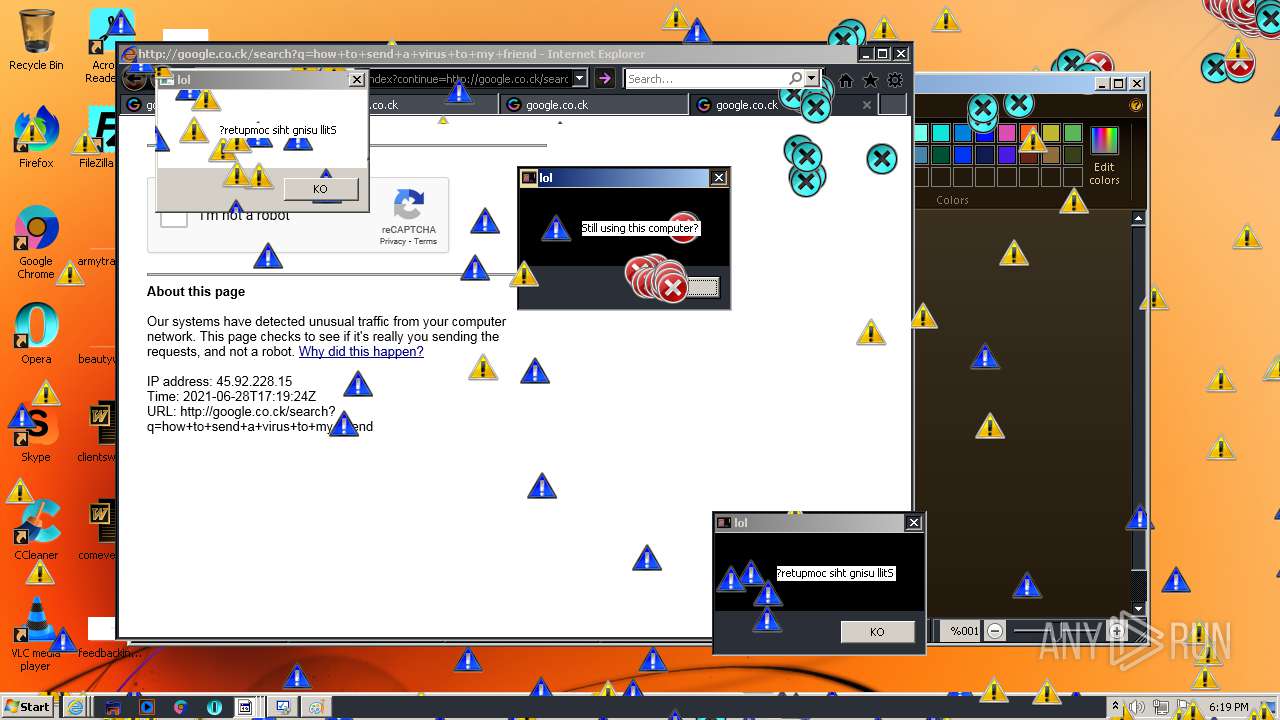
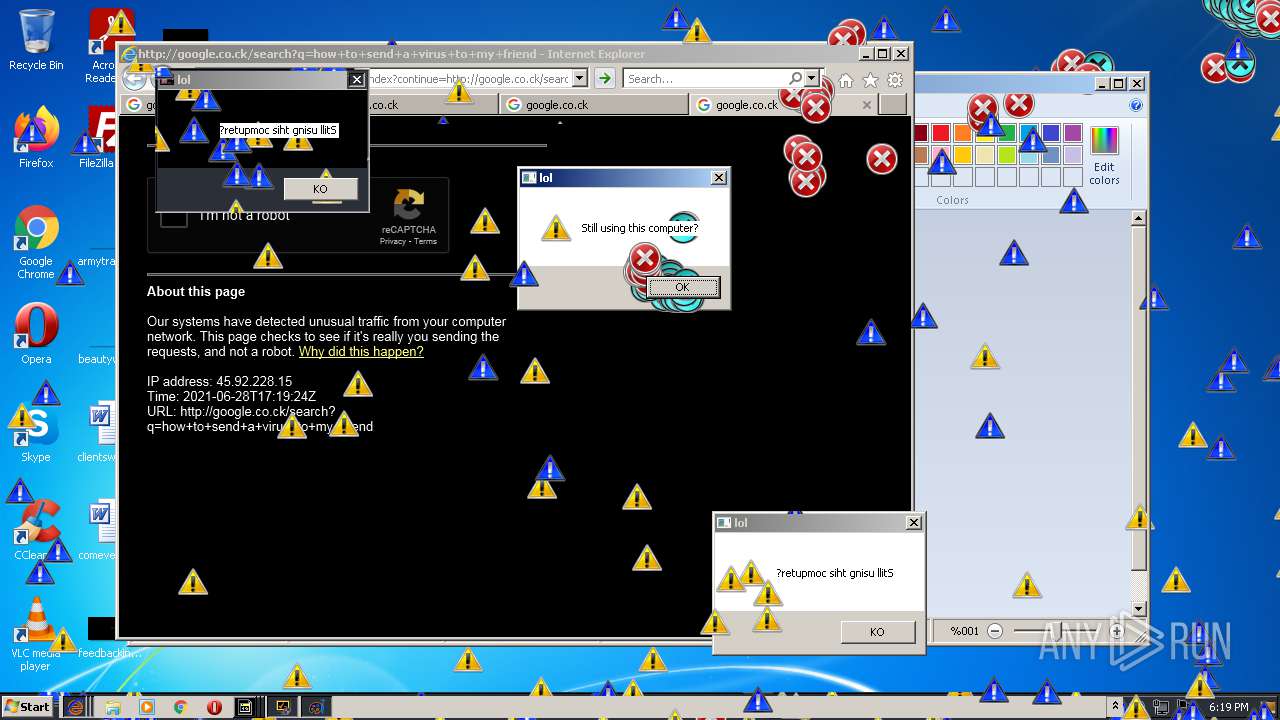
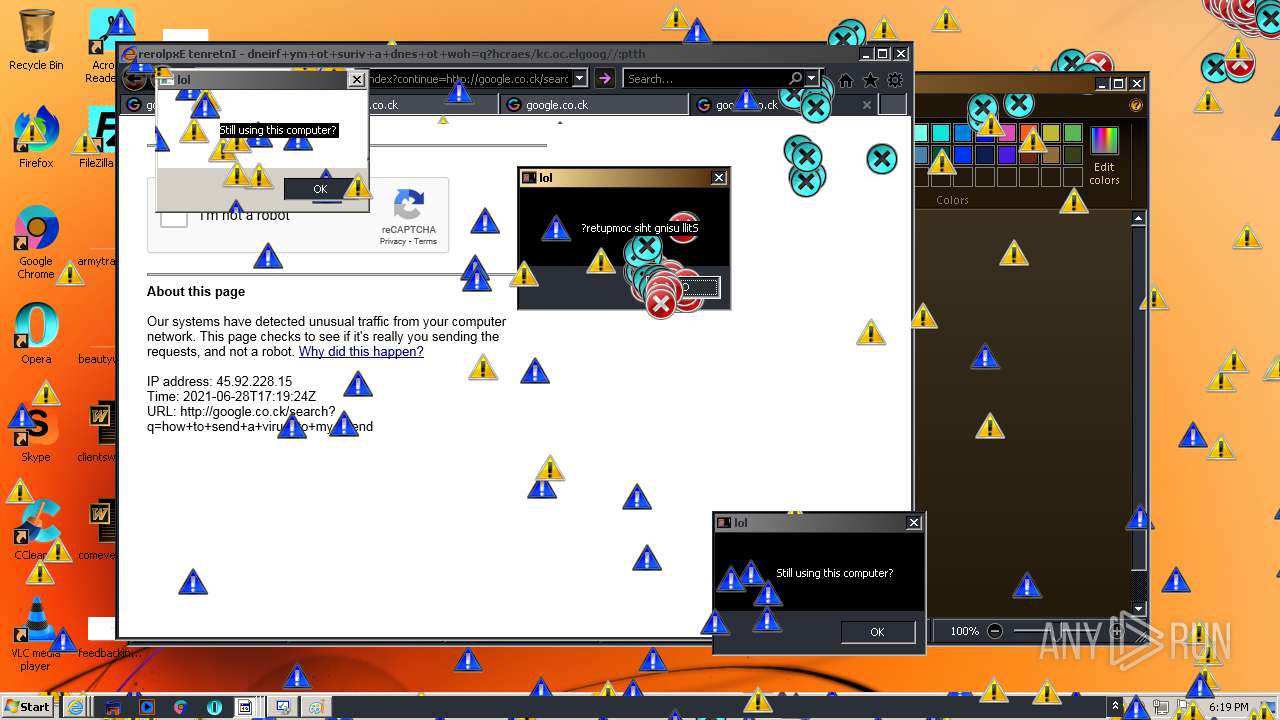
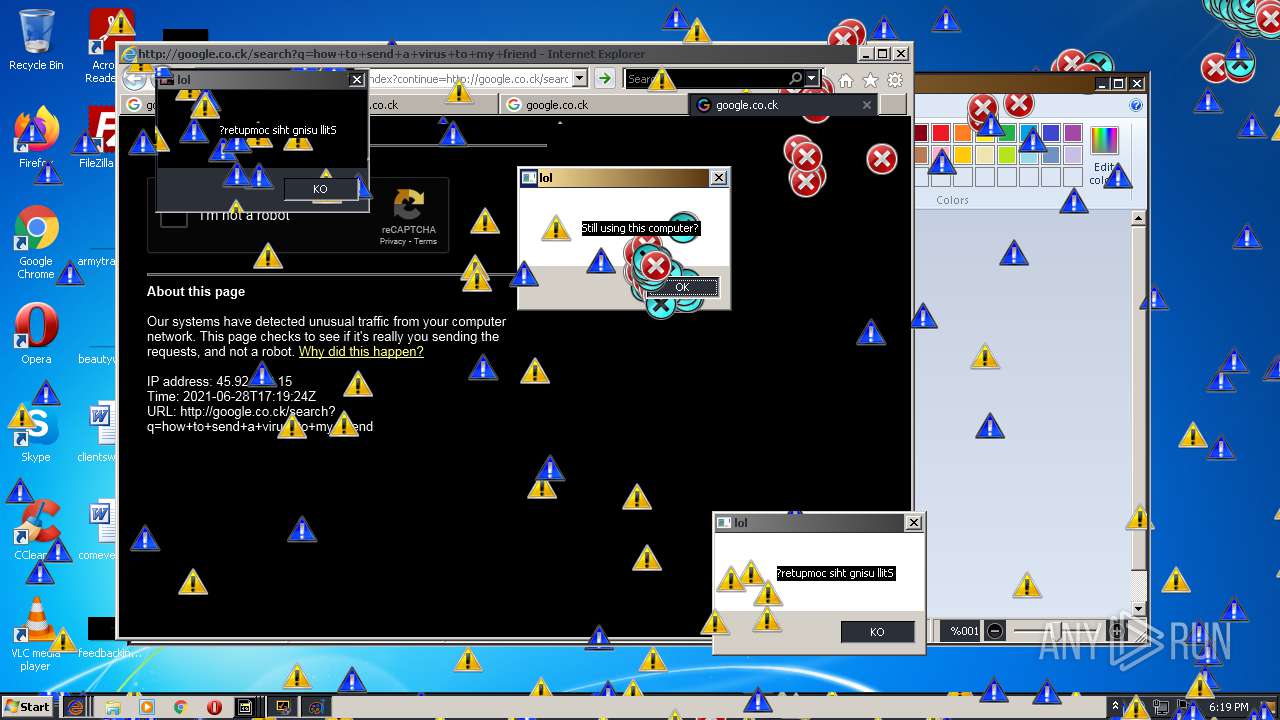
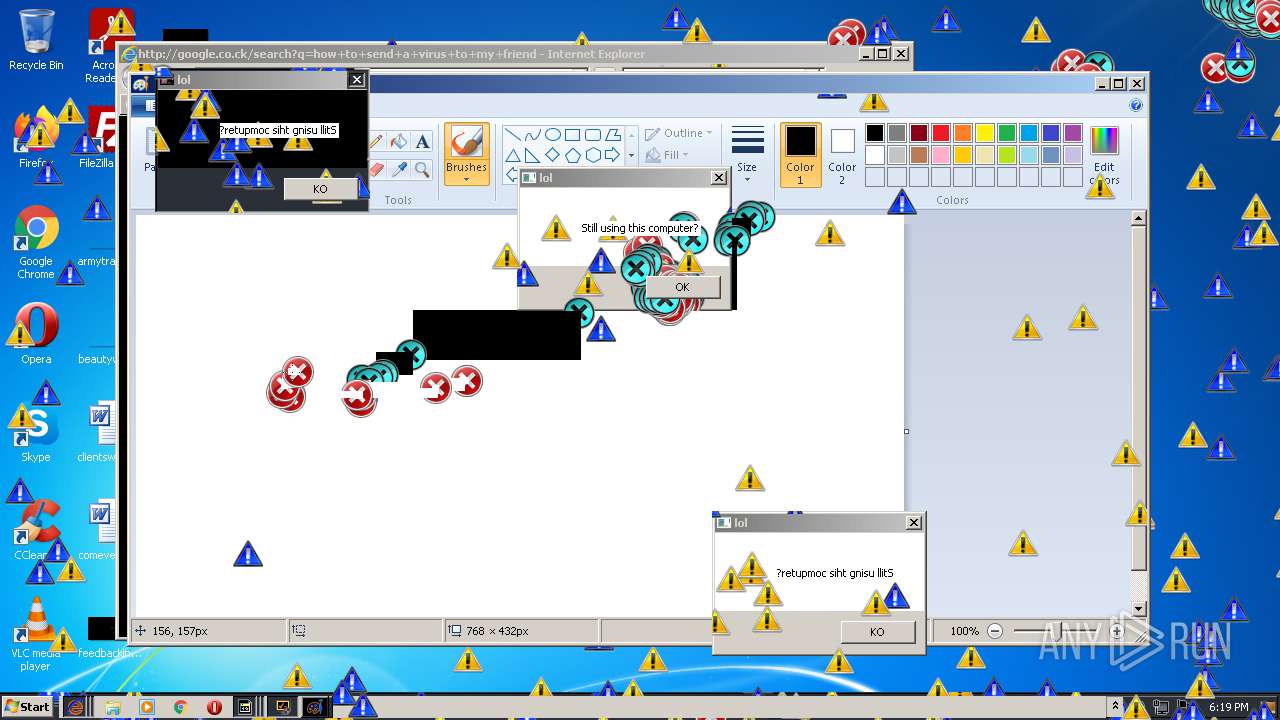
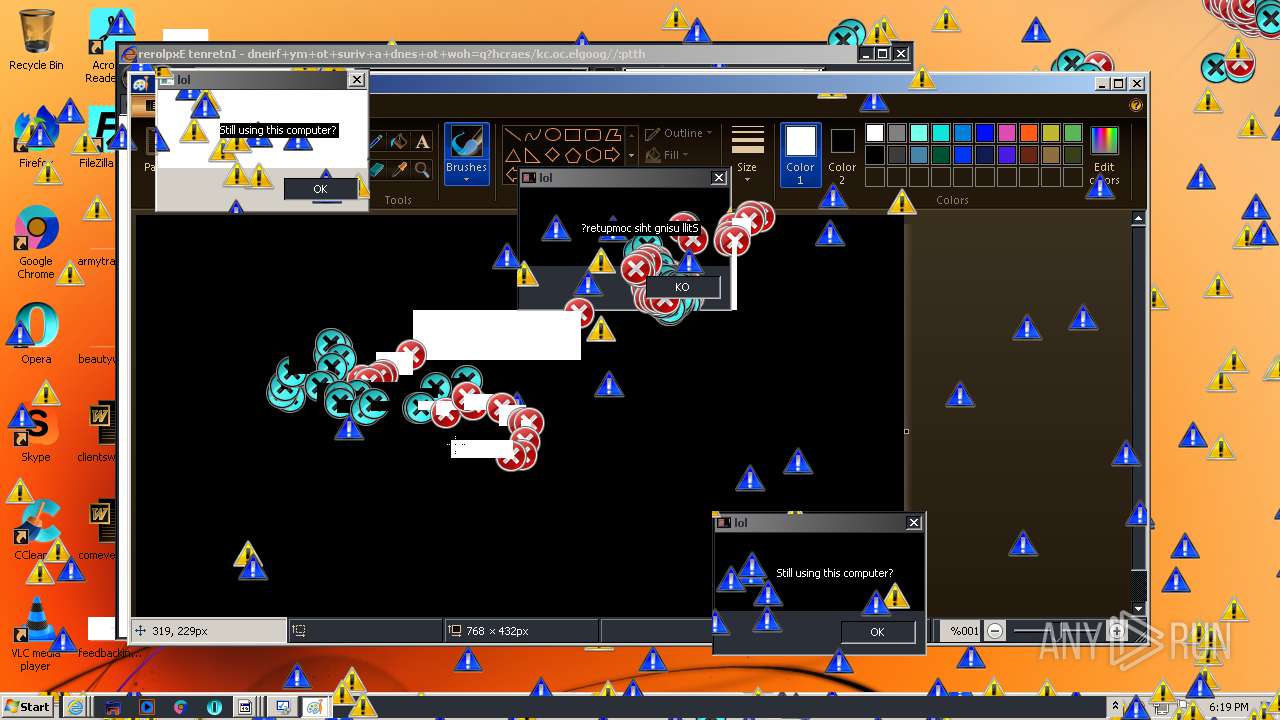
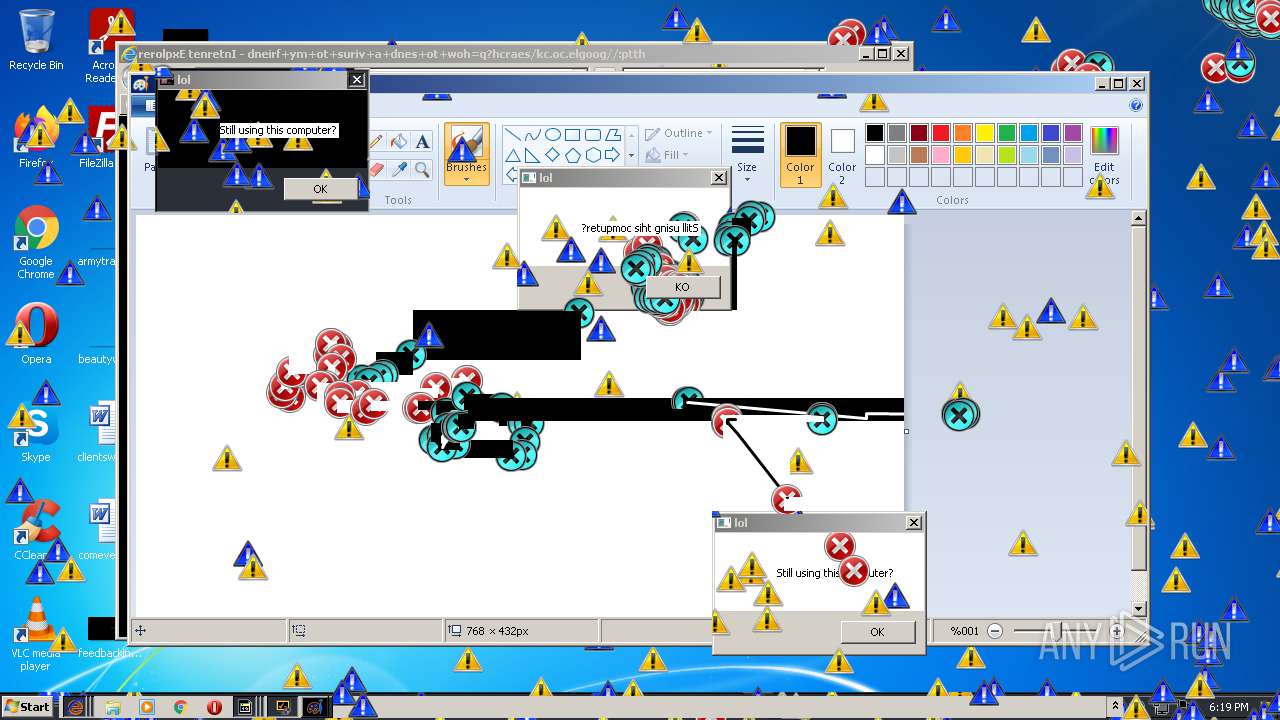
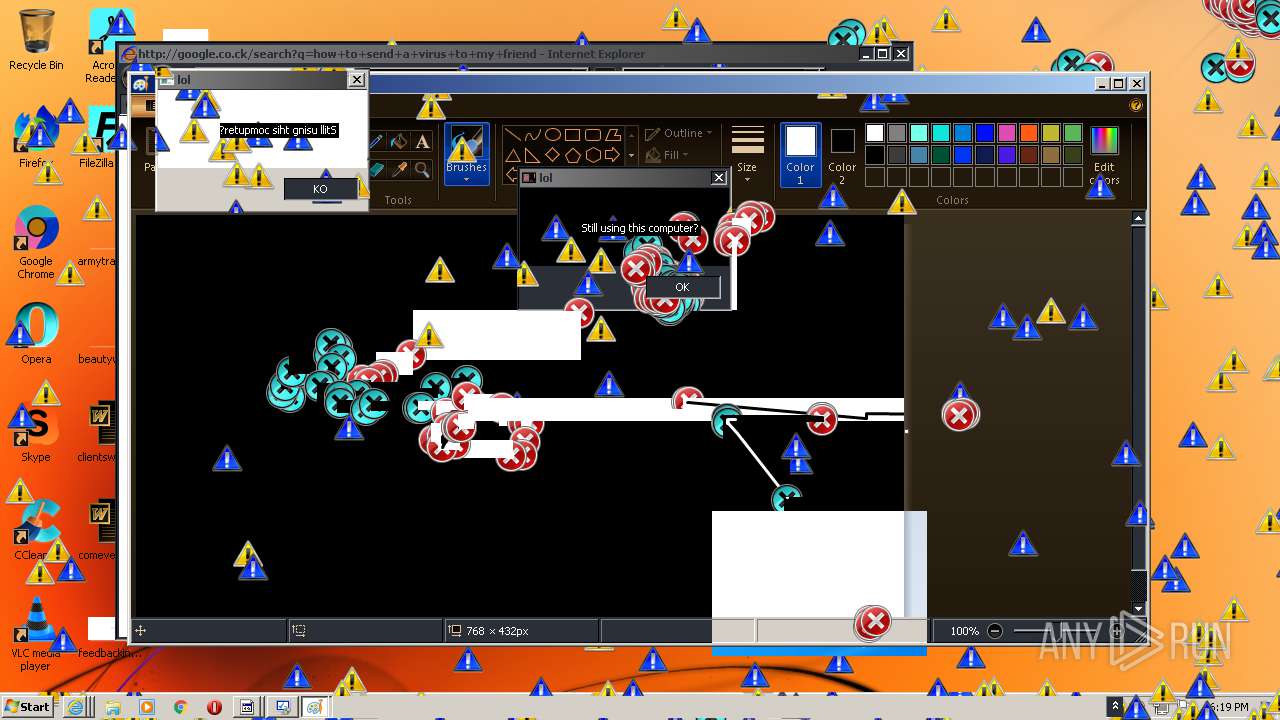
| URL: | https://github.com/OwO-Studio/MEMZ-4.0/raw/master/MEMZ-Destructive.exe |
| Full analysis: | https://app.any.run/tasks/f784d467-9367-486a-a6ba-588c9d7b96b9 |
| Verdict: | Malicious activity |
| Analysis date: | June 28, 2021, 17:14:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 70243CE3F19BA497CDD58E3E395ED453 |
| SHA1: | CEC0E62F2A41157E22C63B00CACA727D63CE942A |
| SHA256: | F15AA408AC0929B102CDF967AC18A7B31568C50E6D6E6F3CAF35A0CE2A086DA3 |
| SSDEEP: | 3:N8tEdUI2gMFhKE+QGAC:2uu1Fc0C |
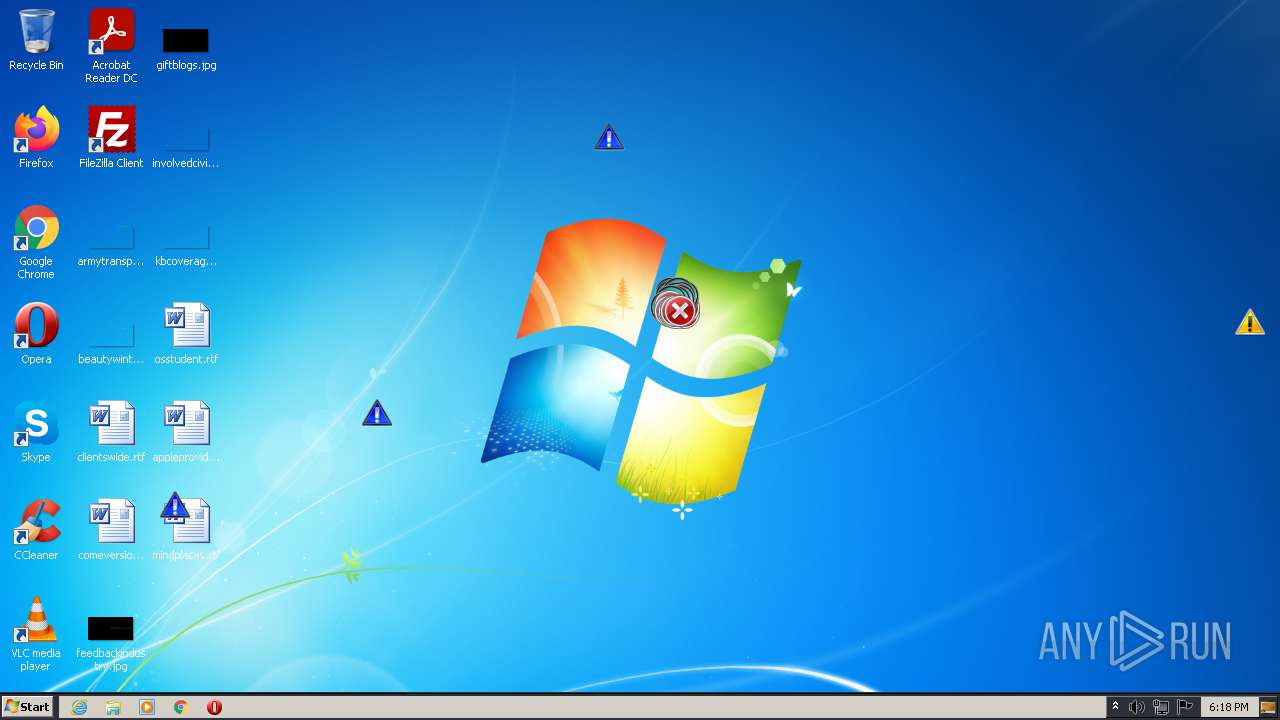
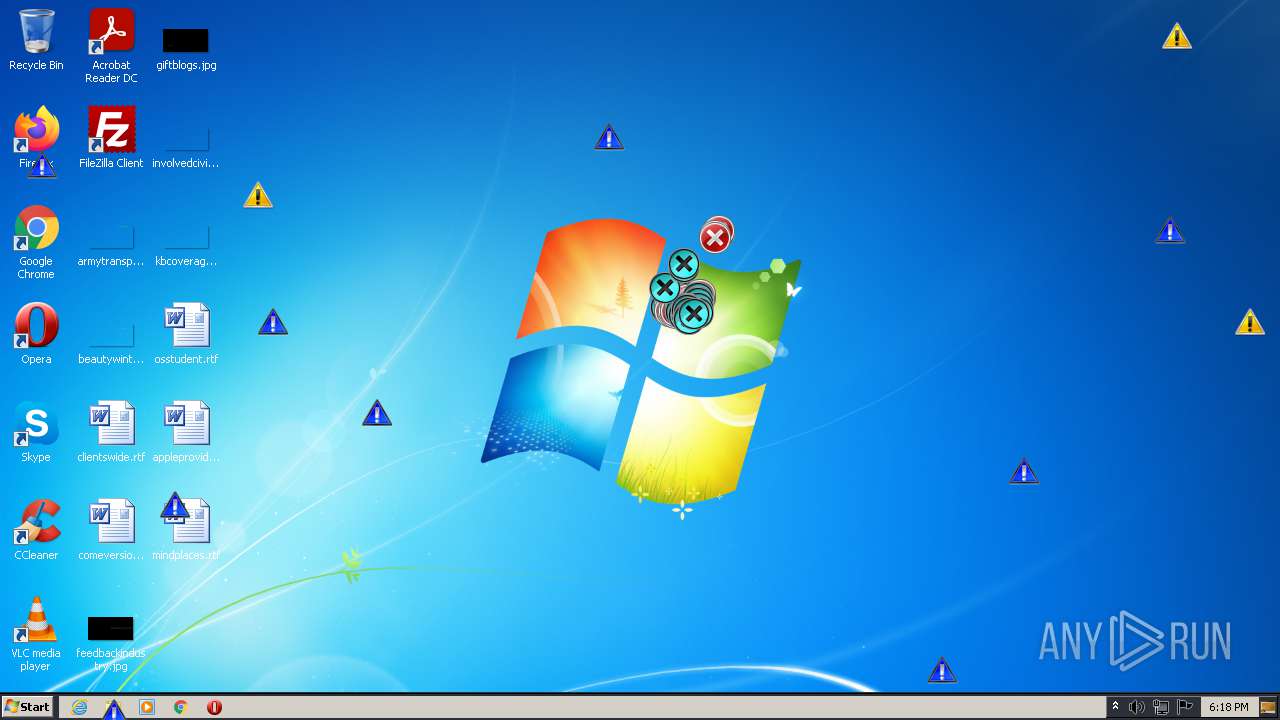
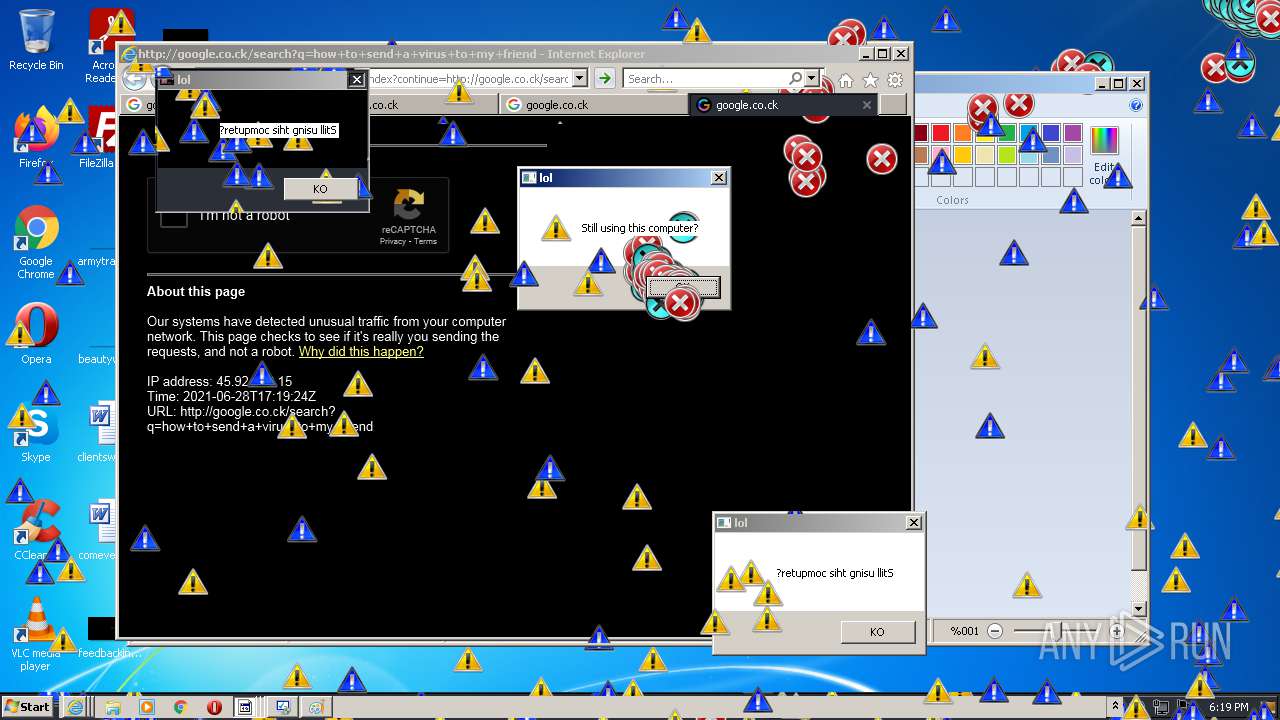
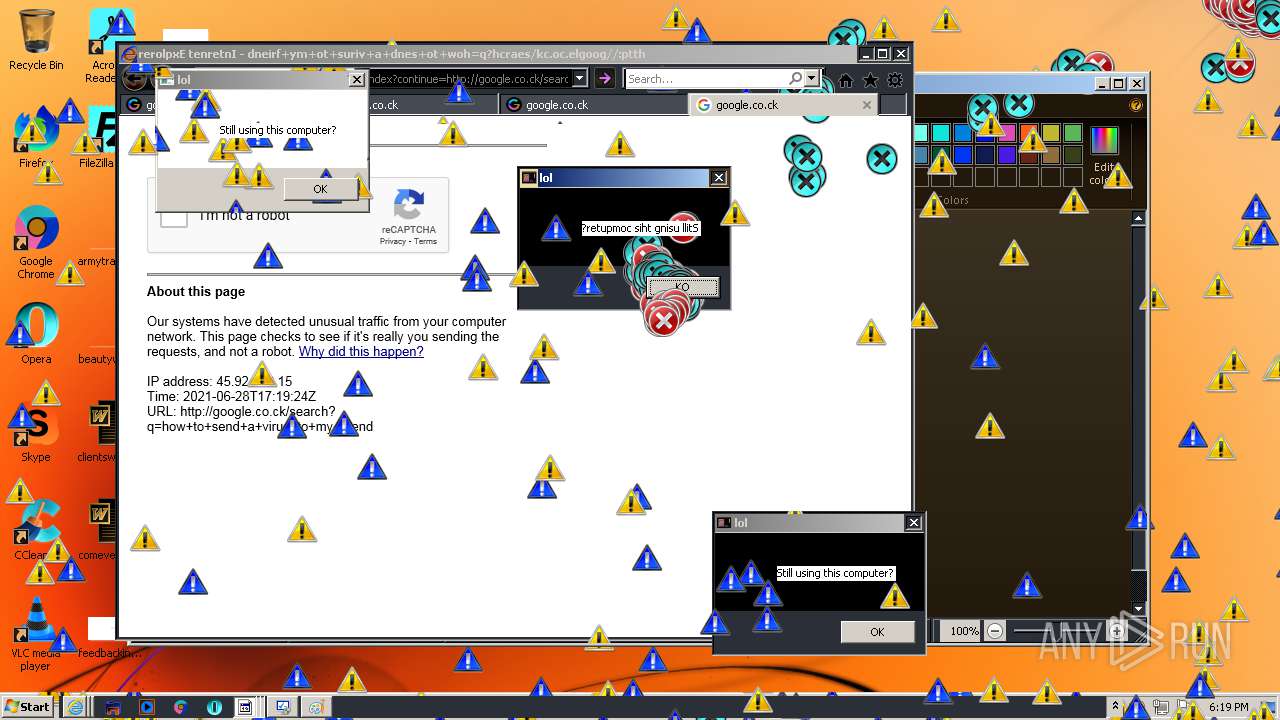
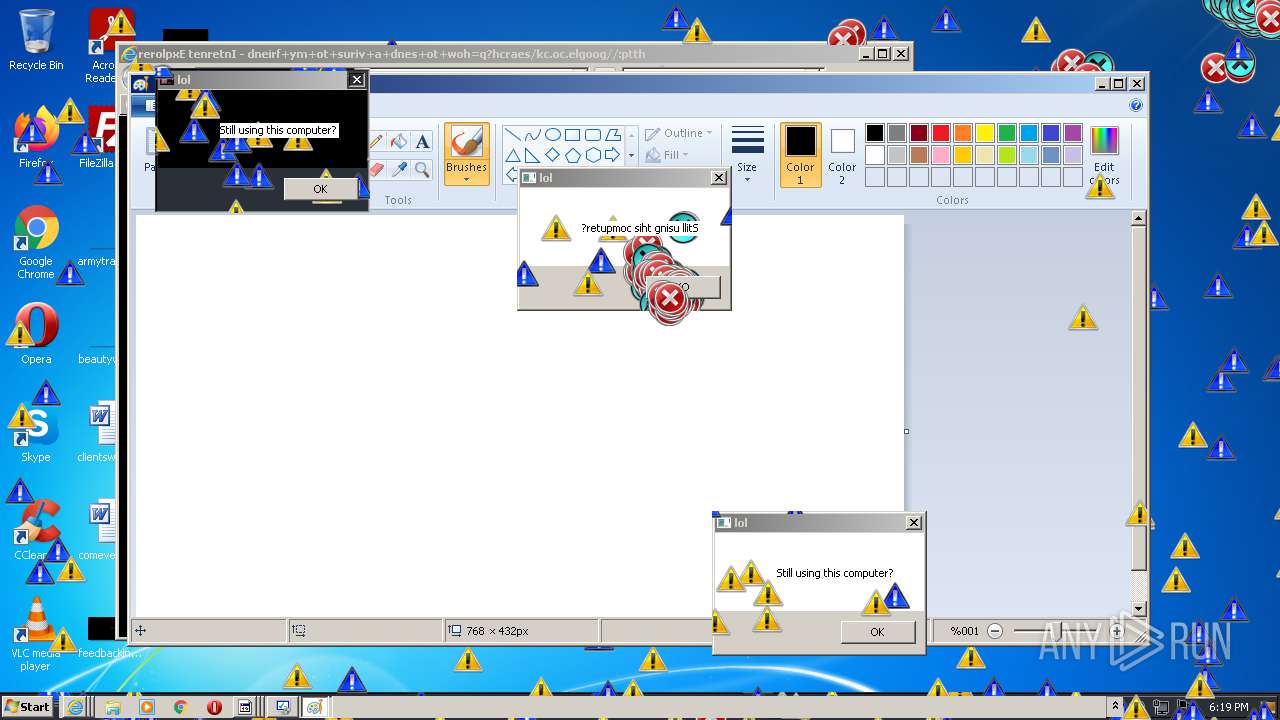
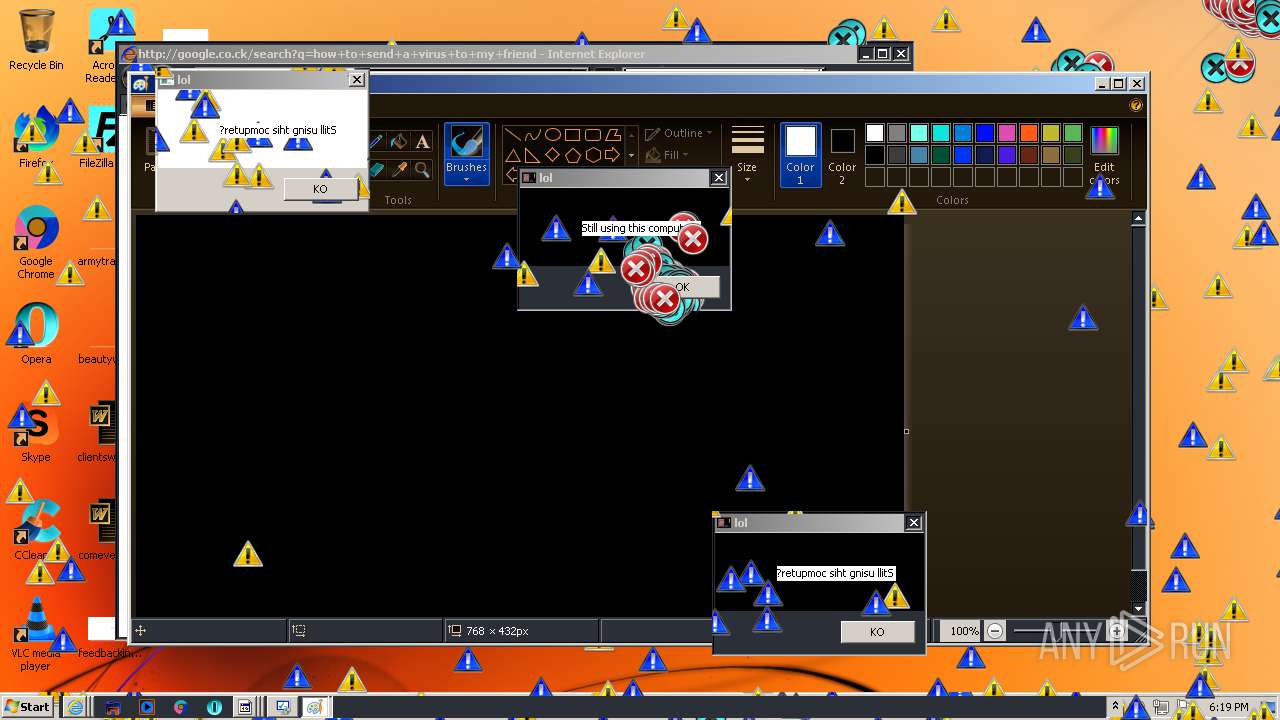
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ-Destructive.exe (PID: 760)
- MEMZ-Destructive.exe (PID: 720)
- MEMZ-Destructive.exe (PID: 2388)
- MEMZ-Destructive.exe (PID: 2932)
- MEMZ-Destructive.exe (PID: 3384)
- MEMZ-Destructive.exe (PID: 1796)
- MEMZ-Destructive.exe (PID: 588)
- MEMZ-Destructive.exe (PID: 2756)
Changes the autorun value in the registry
- reg.exe (PID: 1936)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 2736)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 1196)
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 780)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 3756)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 3552)
Checks supported languages
- MEMZ-Destructive.exe (PID: 760)
- MEMZ-Destructive.exe (PID: 2388)
- MEMZ-Destructive.exe (PID: 2932)
- MEMZ-Destructive.exe (PID: 3384)
- MEMZ-Destructive.exe (PID: 1796)
- MEMZ-Destructive.exe (PID: 588)
- MEMZ-Destructive.exe (PID: 2756)
- Skype.exe (PID: 268)
- Skype.exe (PID: 388)
- Skype.exe (PID: 3656)
- Skype.exe (PID: 2920)
- Skype.exe (PID: 2904)
- Skype.exe (PID: 1448)
Application launched itself
- MEMZ-Destructive.exe (PID: 760)
- Skype.exe (PID: 268)
- Skype.exe (PID: 3656)
- Skype.exe (PID: 2904)
Reads the computer name
- MEMZ-Destructive.exe (PID: 760)
- MEMZ-Destructive.exe (PID: 2756)
- Skype.exe (PID: 268)
- Skype.exe (PID: 388)
- Skype.exe (PID: 3656)
- Skype.exe (PID: 2920)
- Skype.exe (PID: 2904)
- Skype.exe (PID: 1448)
Starts Internet Explorer
- MEMZ-Destructive.exe (PID: 2756)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 268)
Creates files in the user directory
- Skype.exe (PID: 268)
- Skype.exe (PID: 3656)
- Skype.exe (PID: 2904)
Reads CPU info
- Skype.exe (PID: 268)
Changes default file association
- Skype.exe (PID: 268)
INFO
Application launched itself
- iexplore.exe (PID: 3552)
- chrome.exe (PID: 3092)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 2616)
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 1604)
- iexplore.exe (PID: 3152)
Changes internet zones settings
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 2616)
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 1604)
- iexplore.exe (PID: 3152)
Reads the computer name
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 3552)
- chrome.exe (PID: 3092)
- chrome.exe (PID: 3648)
- chrome.exe (PID: 3456)
- chrome.exe (PID: 2544)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 2736)
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2616)
- iexplore.exe (PID: 1196)
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 1604)
- mmc.exe (PID: 4024)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 3152)
- iexplore.exe (PID: 780)
- msconfig.exe (PID: 1876)
- iexplore.exe (PID: 2692)
- mspaint.exe (PID: 3372)
- iexplore.exe (PID: 3104)
- mspaint.exe (PID: 3348)
- iexplore.exe (PID: 3796)
Checks Windows Trust Settings
- iexplore.exe (PID: 2536)
- MEMZ-Destructive.exe (PID: 760)
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 2736)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 1196)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 780)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 3152)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3552)
Reads the date of Windows installation
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 2616)
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 1604)
Reads settings of System Certificates
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 3552)
- chrome.exe (PID: 3456)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 2736)
- Skype.exe (PID: 268)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 1196)
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 780)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 3152)
Checks supported languages
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 2536)
- notepad.exe (PID: 2020)
- chrome.exe (PID: 3092)
- chrome.exe (PID: 1416)
- chrome.exe (PID: 3456)
- chrome.exe (PID: 3176)
- chrome.exe (PID: 3648)
- chrome.exe (PID: 1440)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 908)
- chrome.exe (PID: 2544)
- chrome.exe (PID: 1016)
- iexplore.exe (PID: 1112)
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 3652)
- chrome.exe (PID: 2968)
- iexplore.exe (PID: 2736)
- reg.exe (PID: 1936)
- reg.exe (PID: 1852)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3976)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 2616)
- iexplore.exe (PID: 952)
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 1196)
- iexplore.exe (PID: 1604)
- mmc.exe (PID: 4024)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 3152)
- iexplore.exe (PID: 780)
- msconfig.exe (PID: 1876)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 2692)
- mspaint.exe (PID: 3372)
- iexplore.exe (PID: 3796)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3244)
- mspaint.exe (PID: 3348)
Manual execution by user
- chrome.exe (PID: 3092)
- Skype.exe (PID: 268)
Reads the hosts file
- chrome.exe (PID: 3092)
- chrome.exe (PID: 3456)
- Skype.exe (PID: 268)
Reads internet explorer settings
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 2736)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 1196)
- iexplore.exe (PID: 3316)
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 780)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3104)
- iexplore.exe (PID: 3796)
Creates files in the user directory
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 3152)
Changes settings of System certificates
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3152)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1420)
- iexplore.exe (PID: 3756)
- iexplore.exe (PID: 3152)
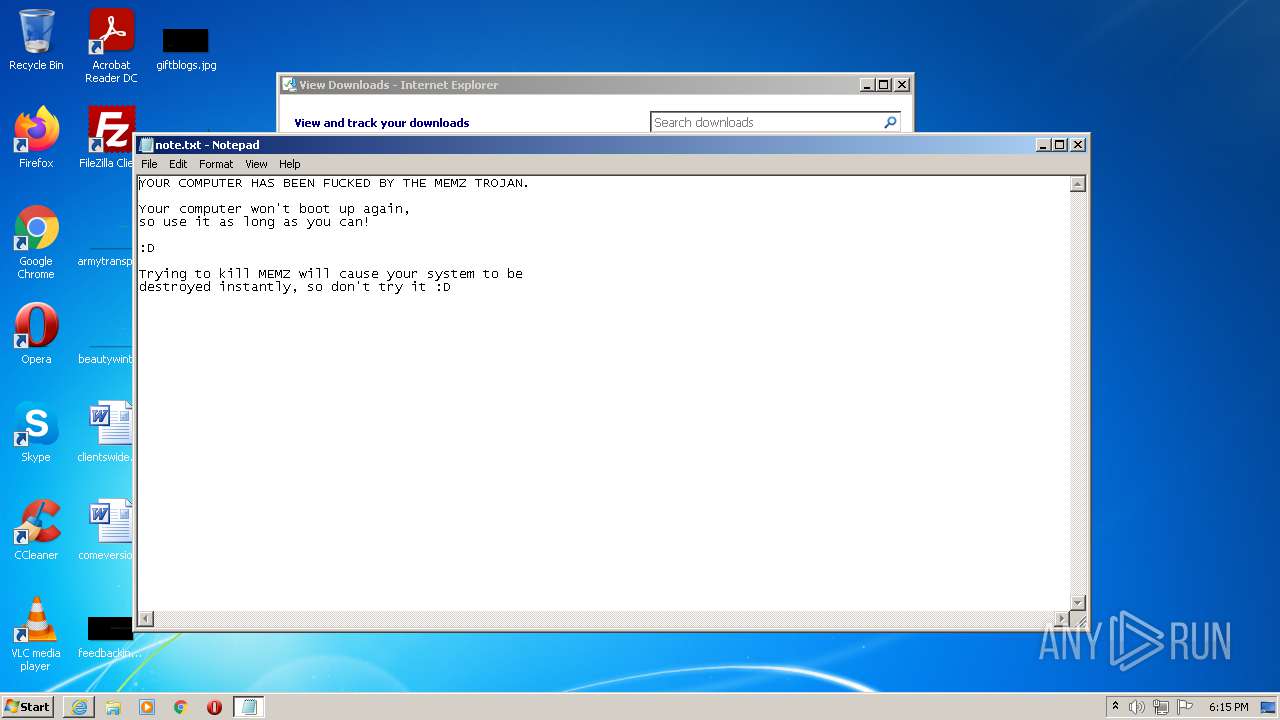
Dropped object may contain Bitcoin addresses
- Skype.exe (PID: 268)
Reads CPU info
- iexplore.exe (PID: 3756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
107
Monitored processes
55
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Explorer.EXE | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 388 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
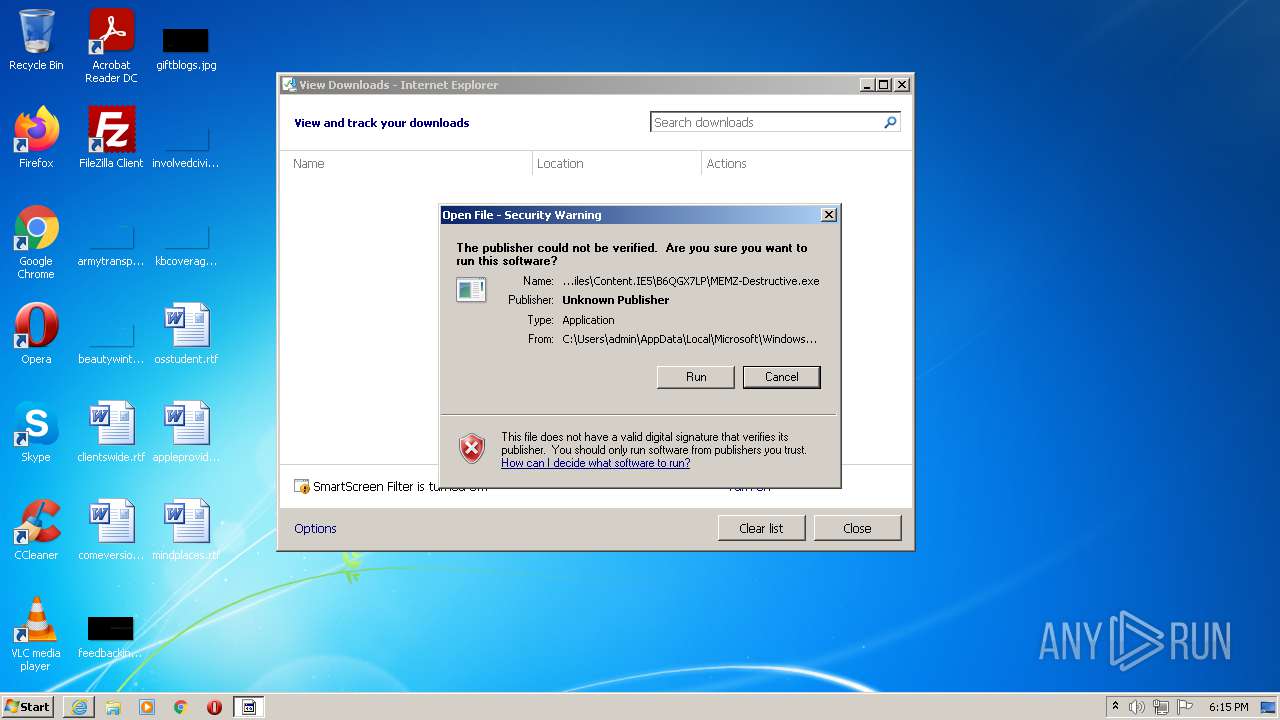
| 588 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 760 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3152 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,9874076031426163288,18391405740835887297,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1924 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
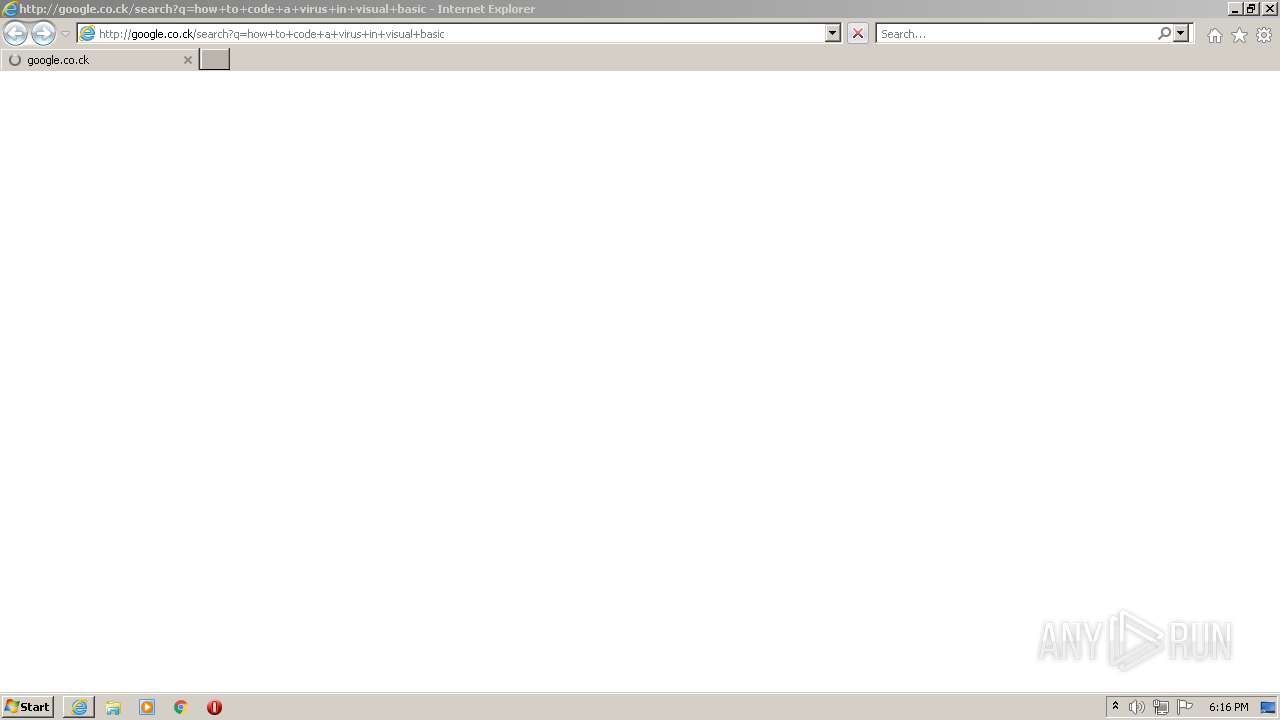
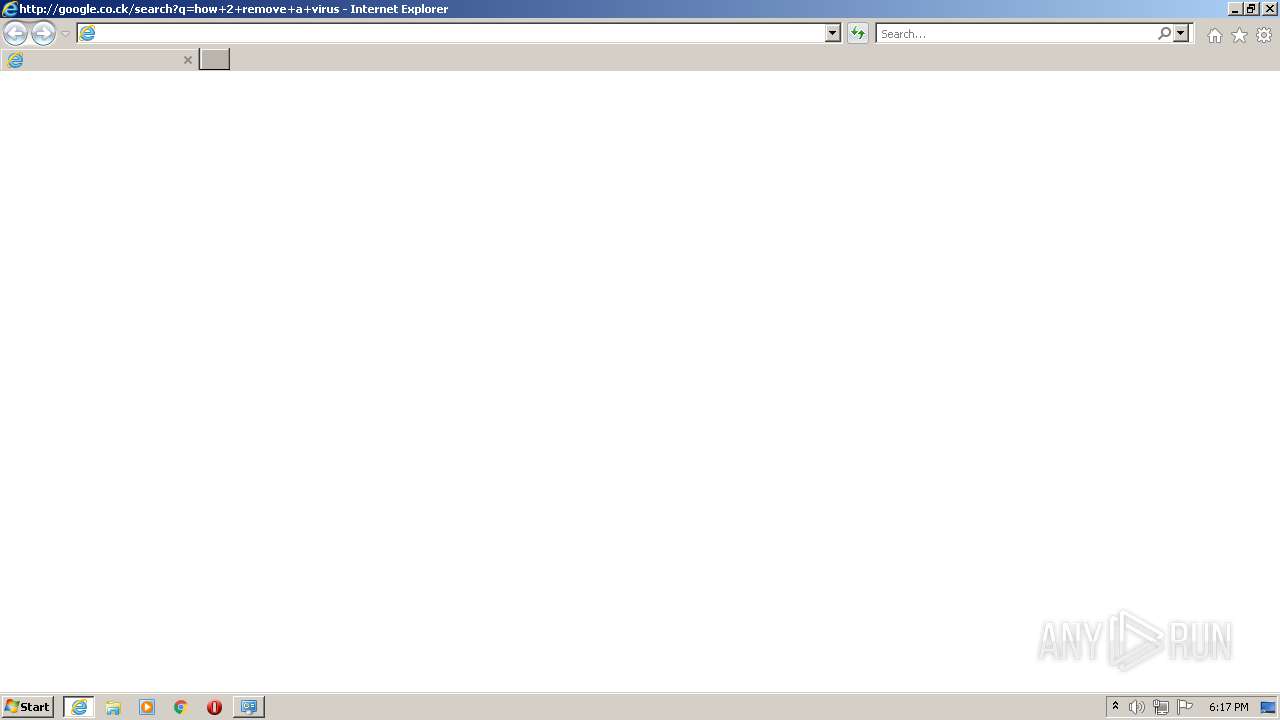
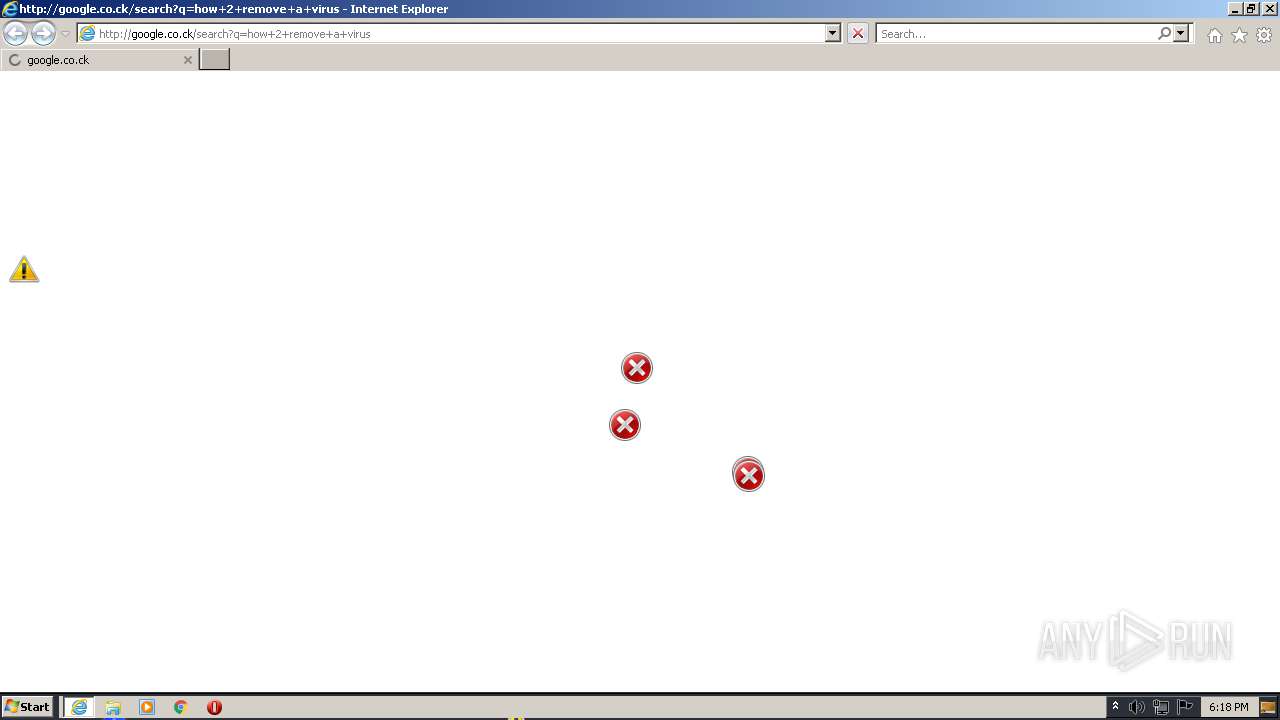
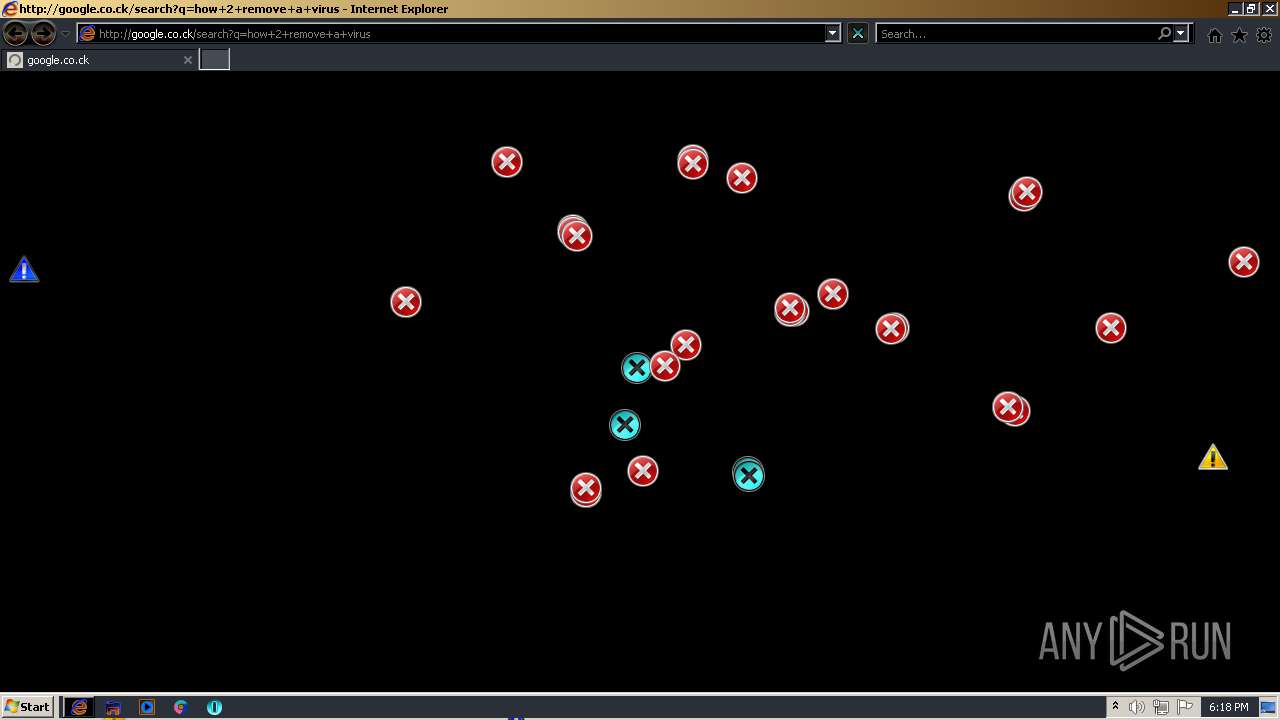
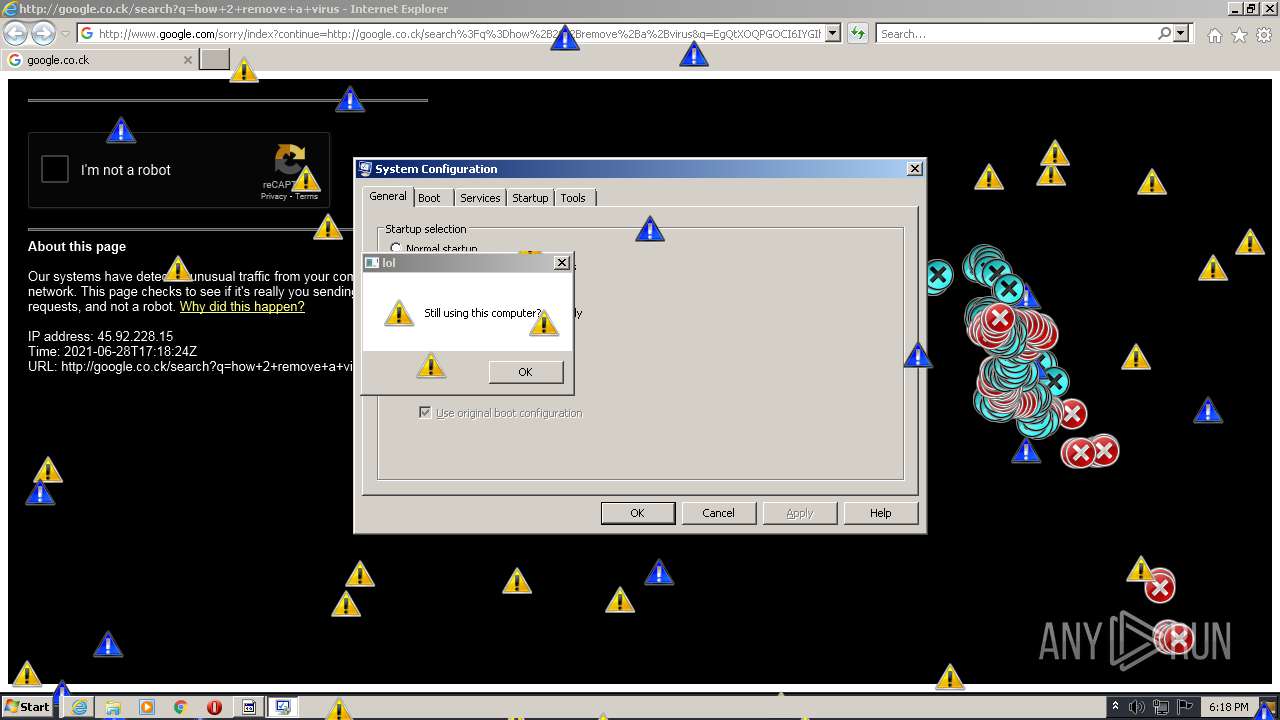
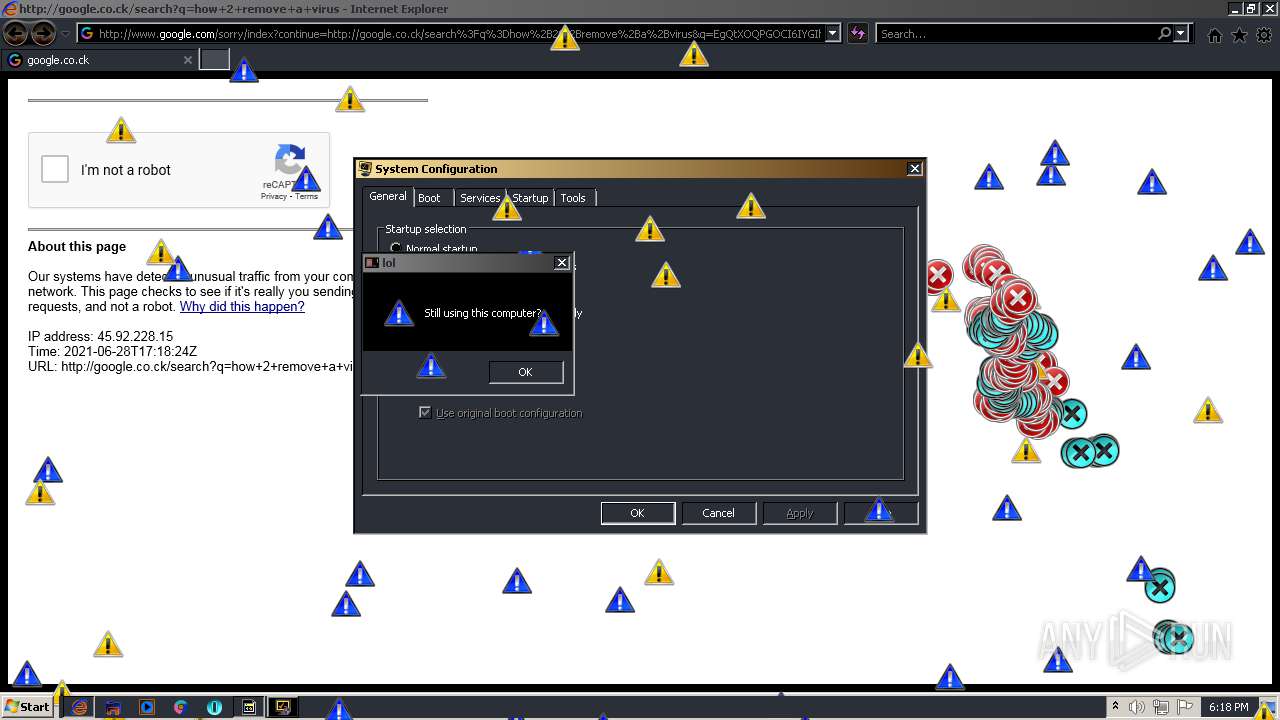
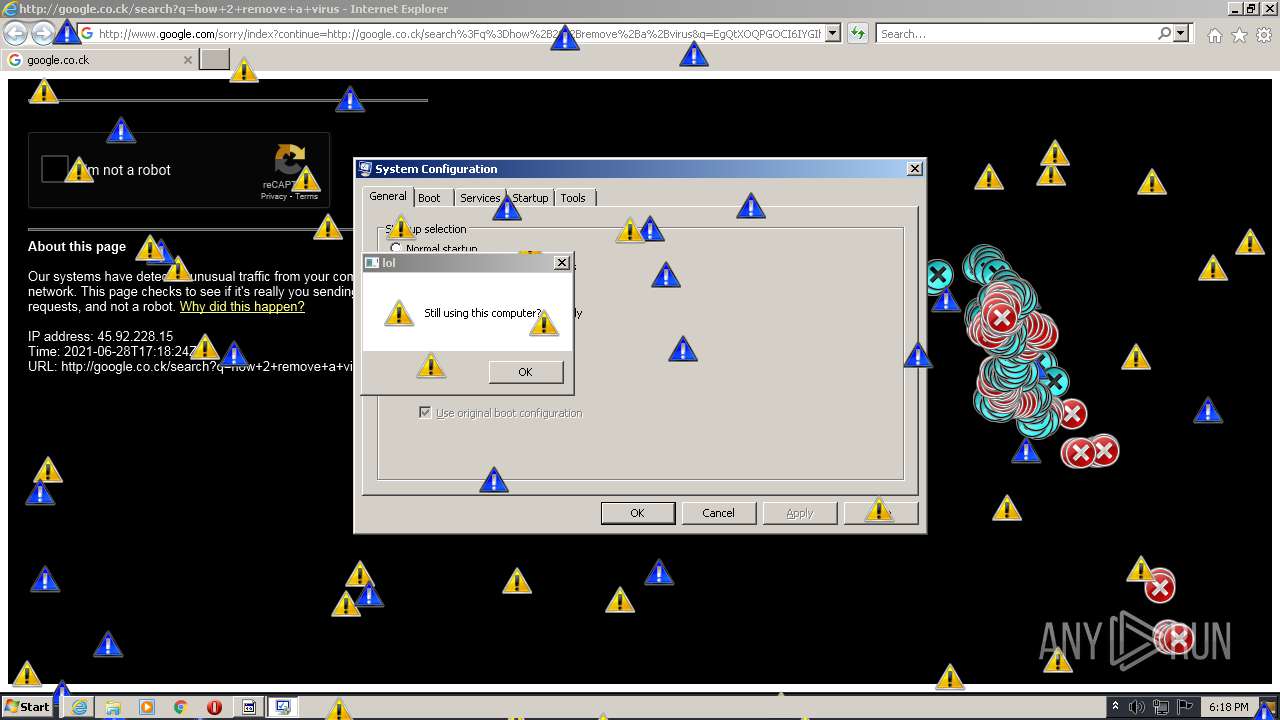
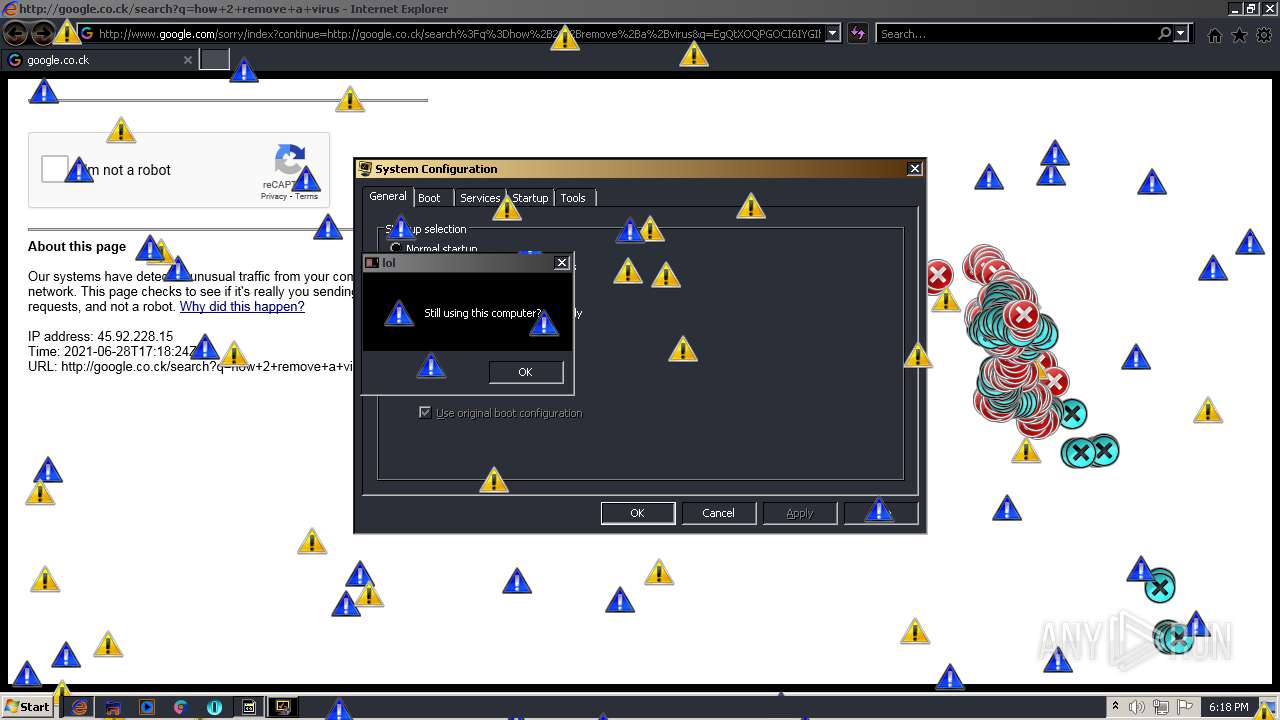
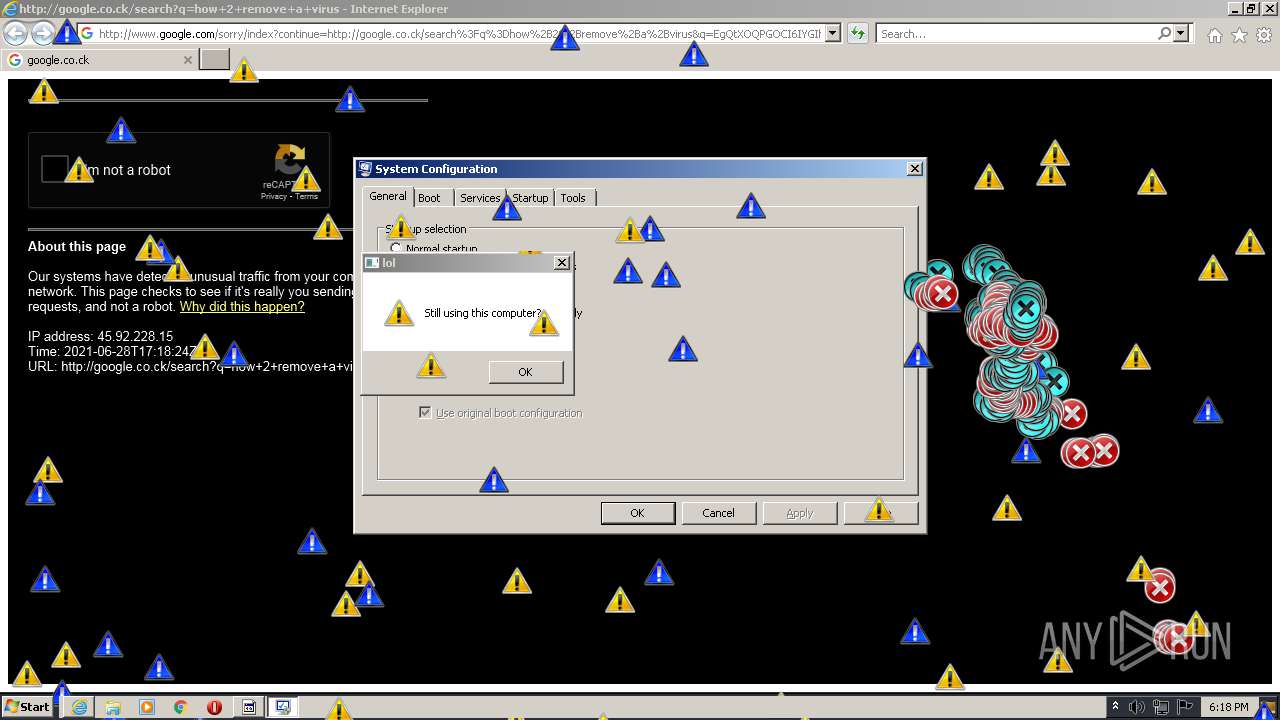
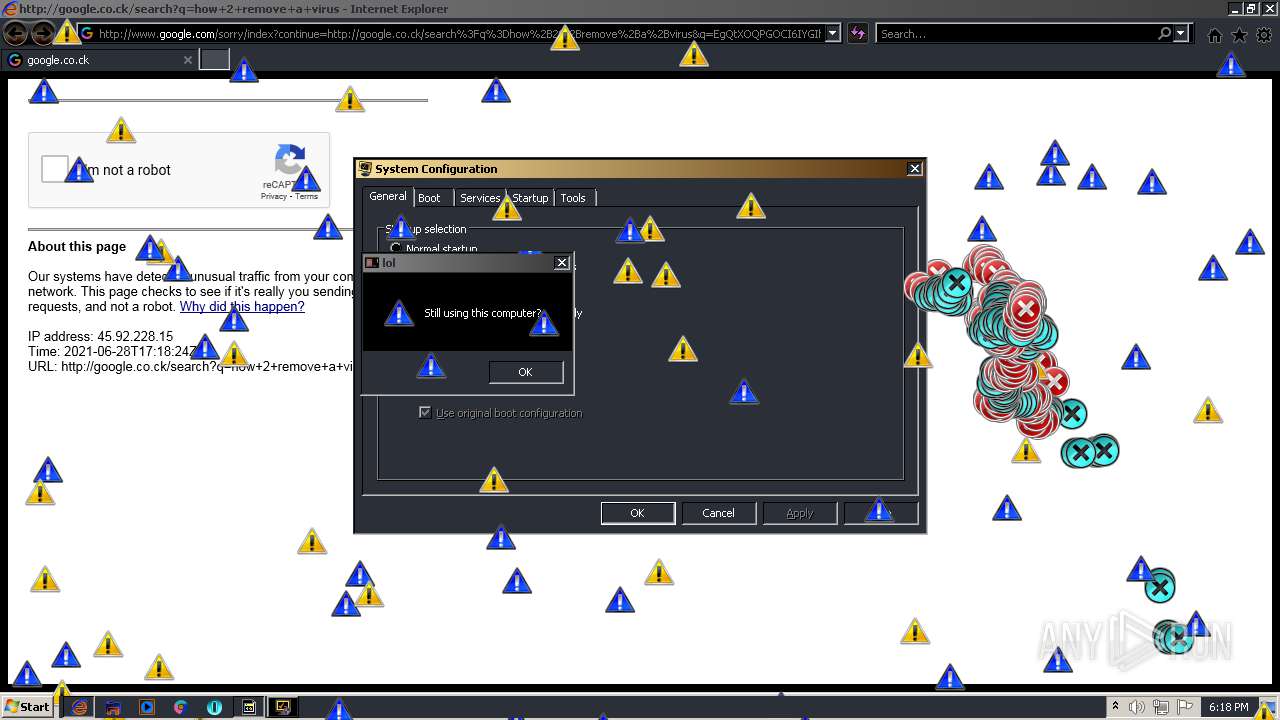
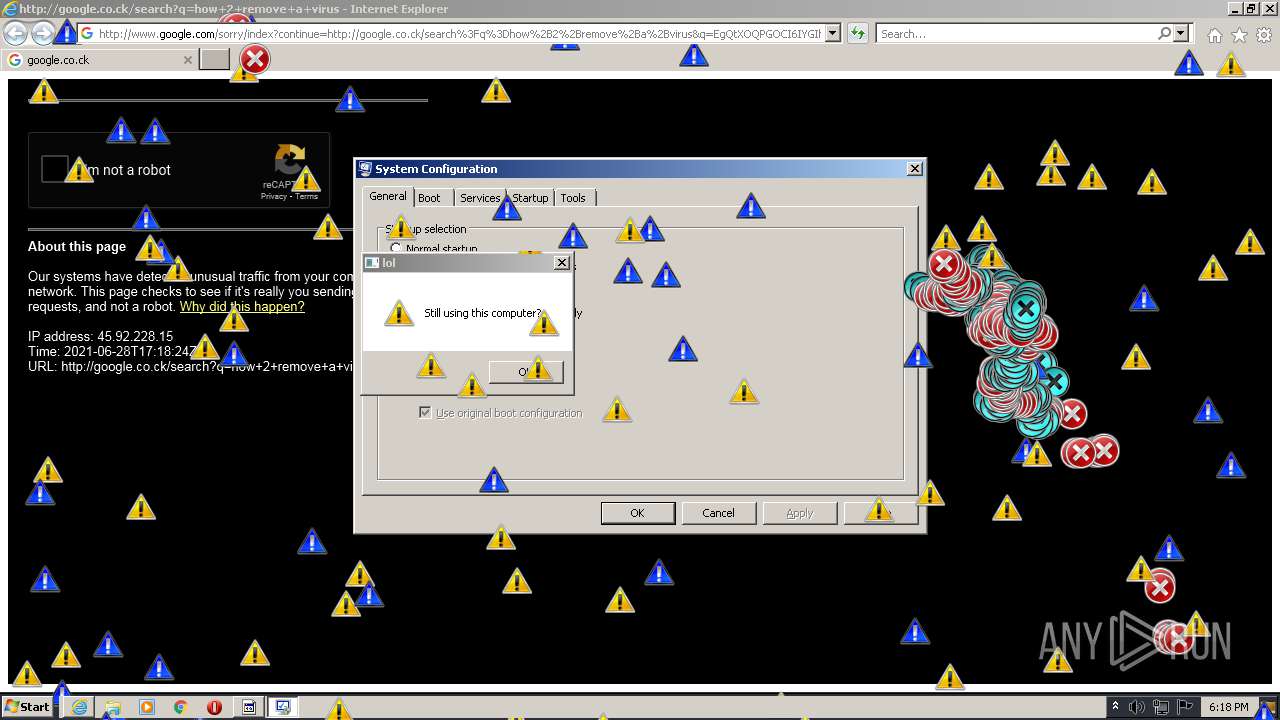
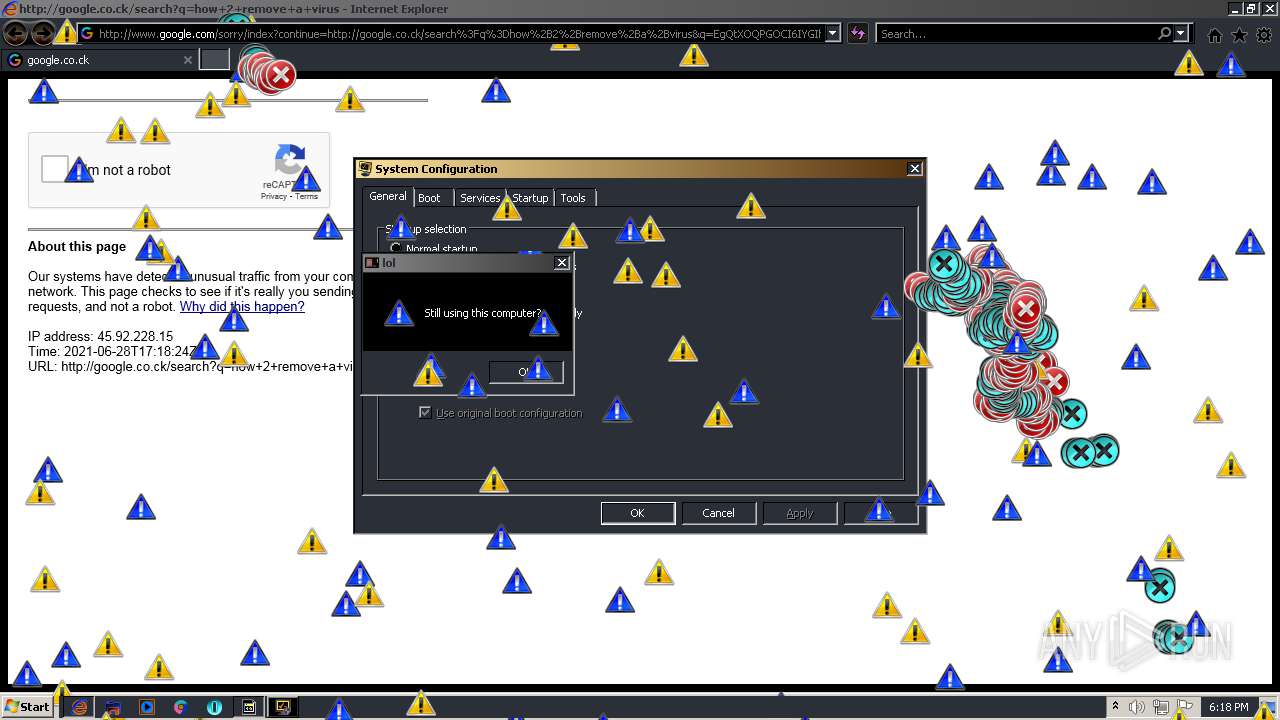
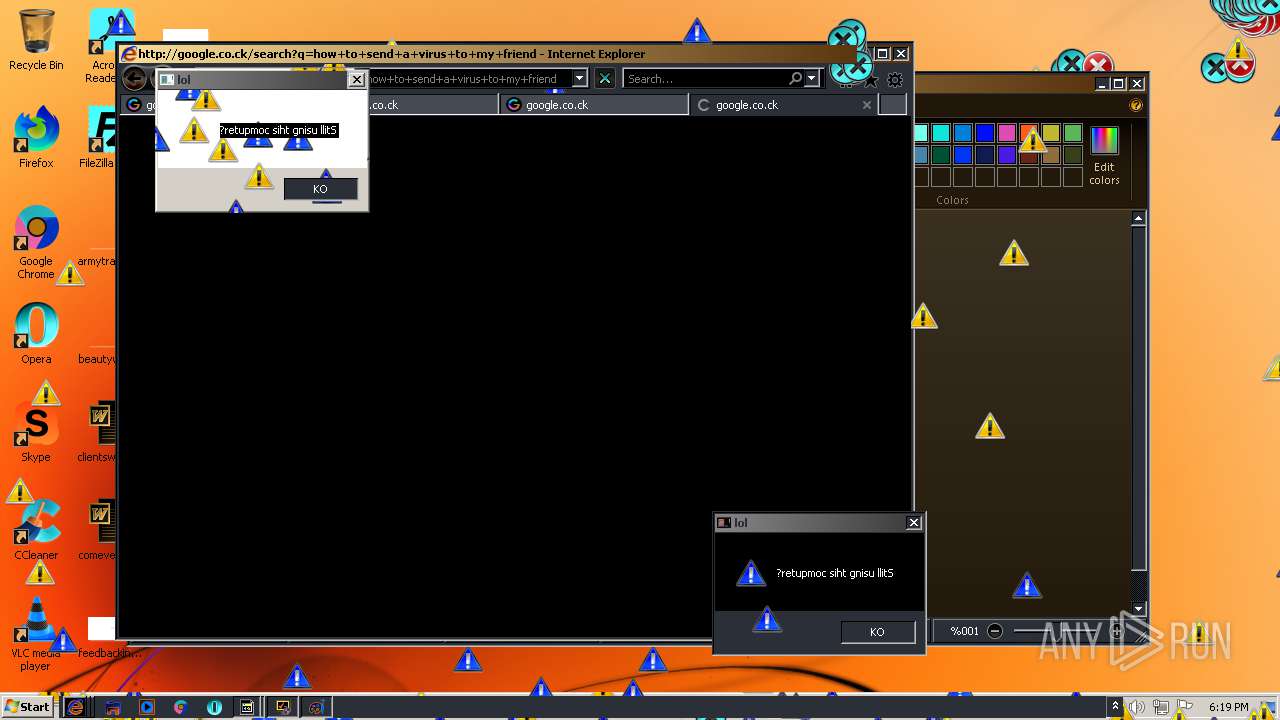
| 952 | "C:\Program Files\Internet Explorer\iexplore.exe" http://google.co.ck/search?q=how+2+remove+a+virus | C:\Program Files\Internet Explorer\iexplore.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,9874076031426163288,18391405740835887297,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2928 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Internet Explorer\iexplore.exe" http://google.co.ck/search?q=how+2+remove+a+virus | C:\Program Files\Internet Explorer\iexplore.exe | MEMZ-Destructive.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
108 691
Read events
107 370
Write events
1 301
Delete events
20
Modification events
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 362616976 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30895169 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 662776820 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30895169 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3552) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
90
Text files
196
Unknown types
73
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{53428B69-D834-11EB-A754-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2A7611428D62805A3E4E5BC4103D82E4_D0FA13DADFB59BDF00C474952E166CC1 | binary | |
MD5:— | SHA256:— | |||
| 2536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2A7611428D62805A3E4E5BC4103D82E4_D0FA13DADFB59BDF00C474952E166CC1 | der | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 3092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60DA03AC-C14.pma | — | |
MD5:— | SHA256:— | |||
| 2536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 2536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\MEMZ-Destructive.exe.7hes09n.partial | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6C59500C87CEF999.TMP | gmc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
183
DNS requests
78
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3756 | iexplore.exe | GET | — | 151.101.1.132:80 | http://motherboard.vice.com/read/watch-this-malware-turn-a-computer-into-a-digital-hellscape | US | — | — | whitelisted |
2536 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTGMlruL6P9M9B3if1rTM7wyj%2FQKQQUUGGmoNI1xBEqII0fD6xC8M0pz0sCEA6L83cNktGW8Lth%2BTxBZr4%3D | US | der | 279 b | whitelisted |
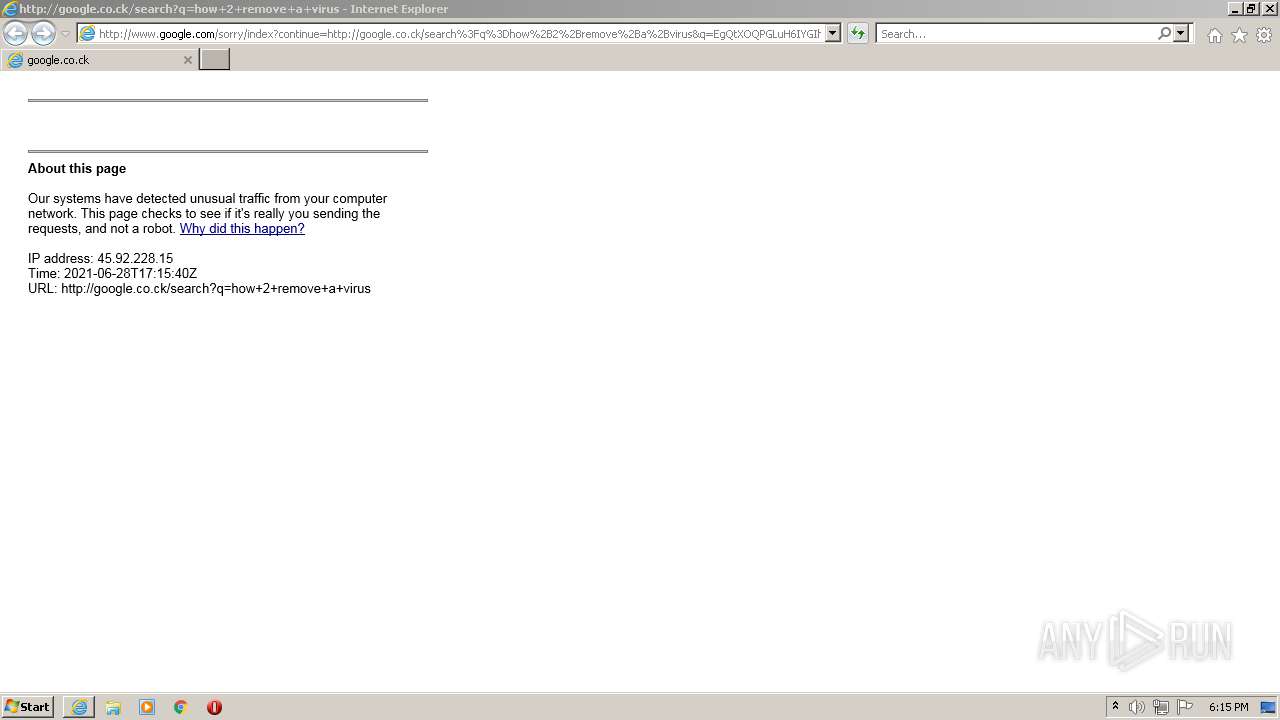
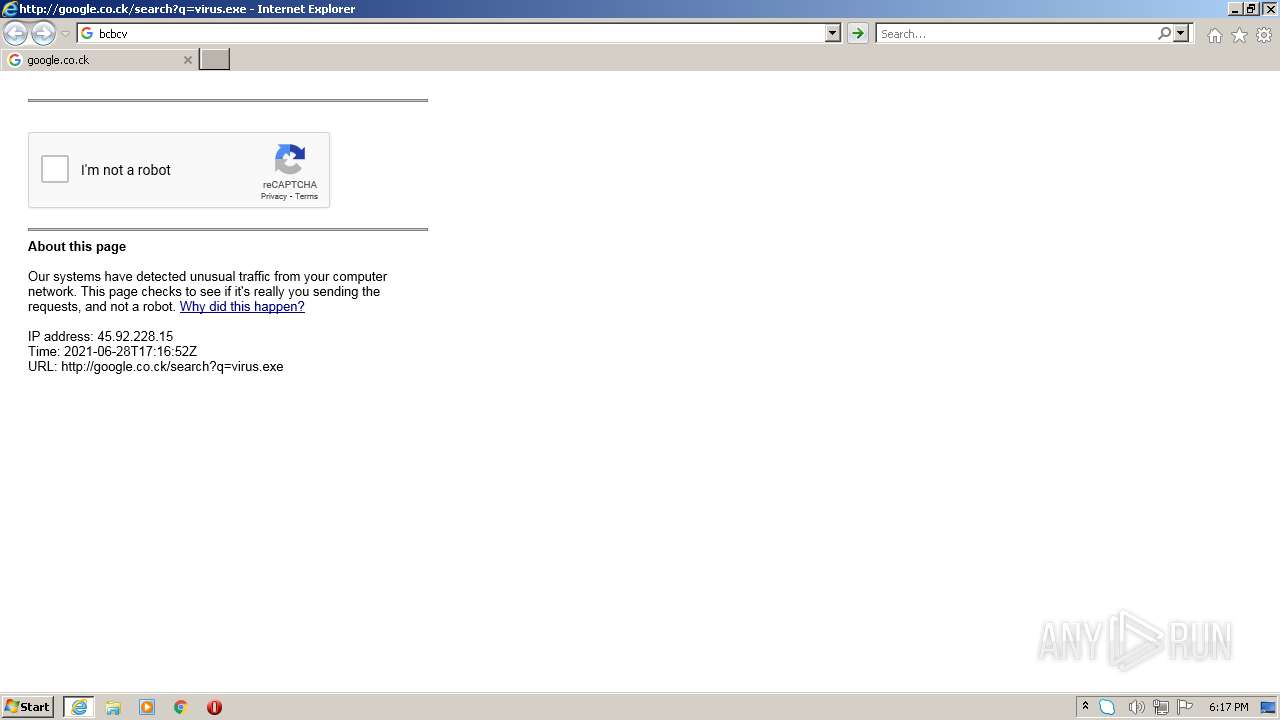
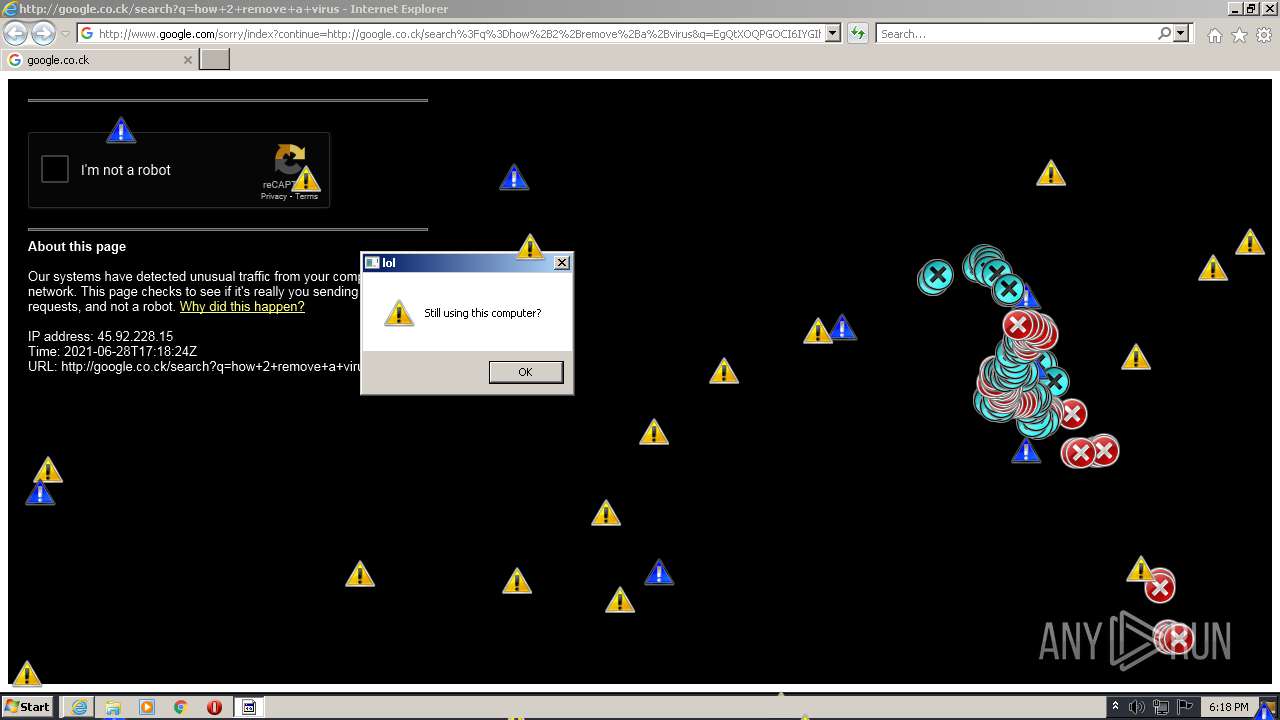
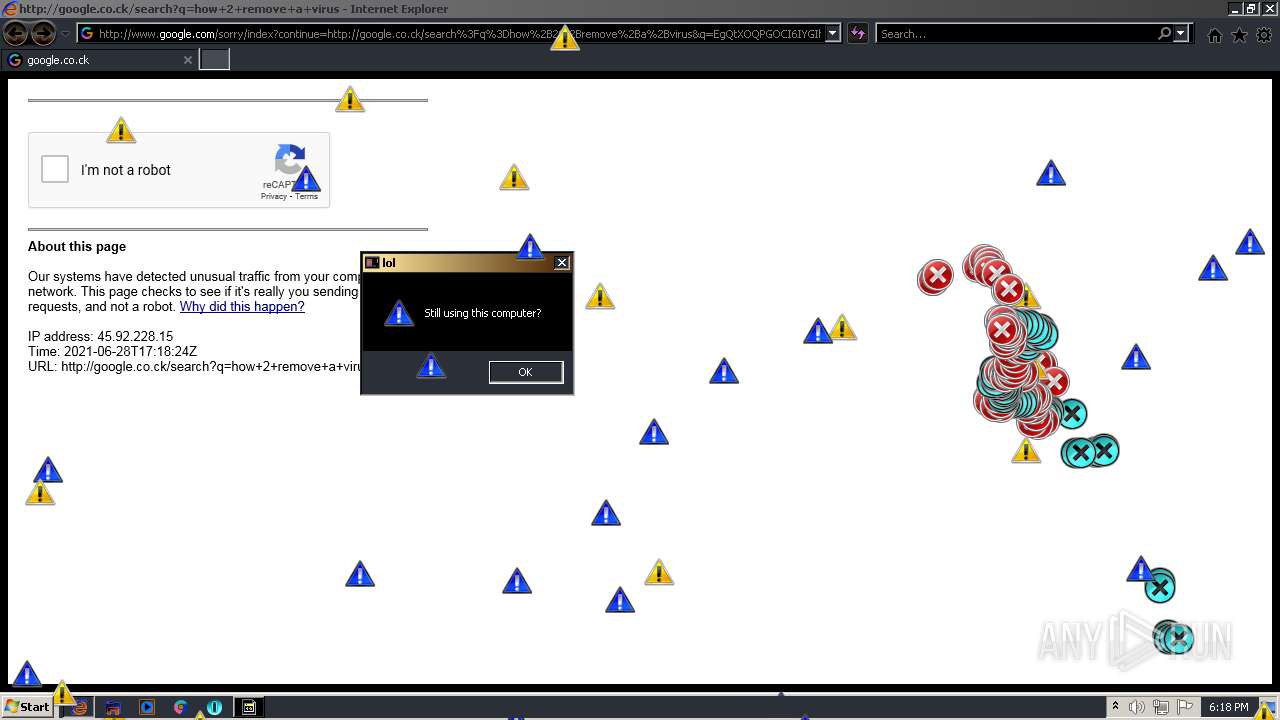
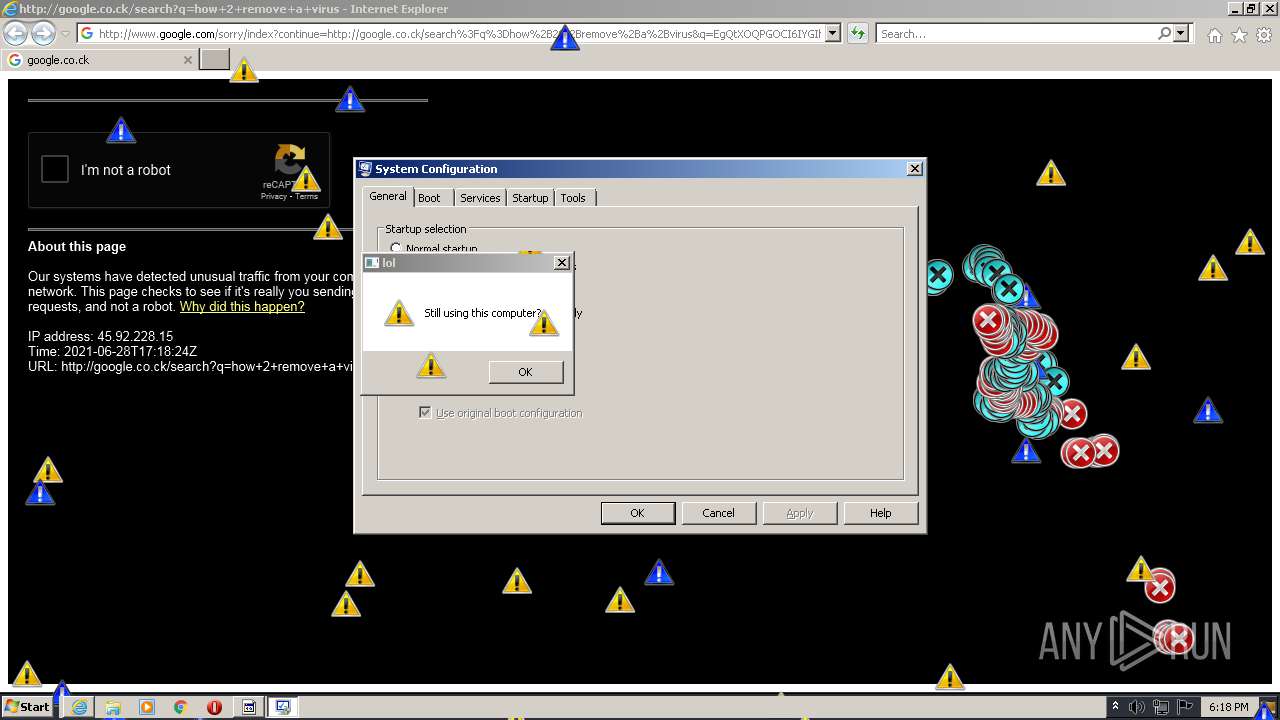
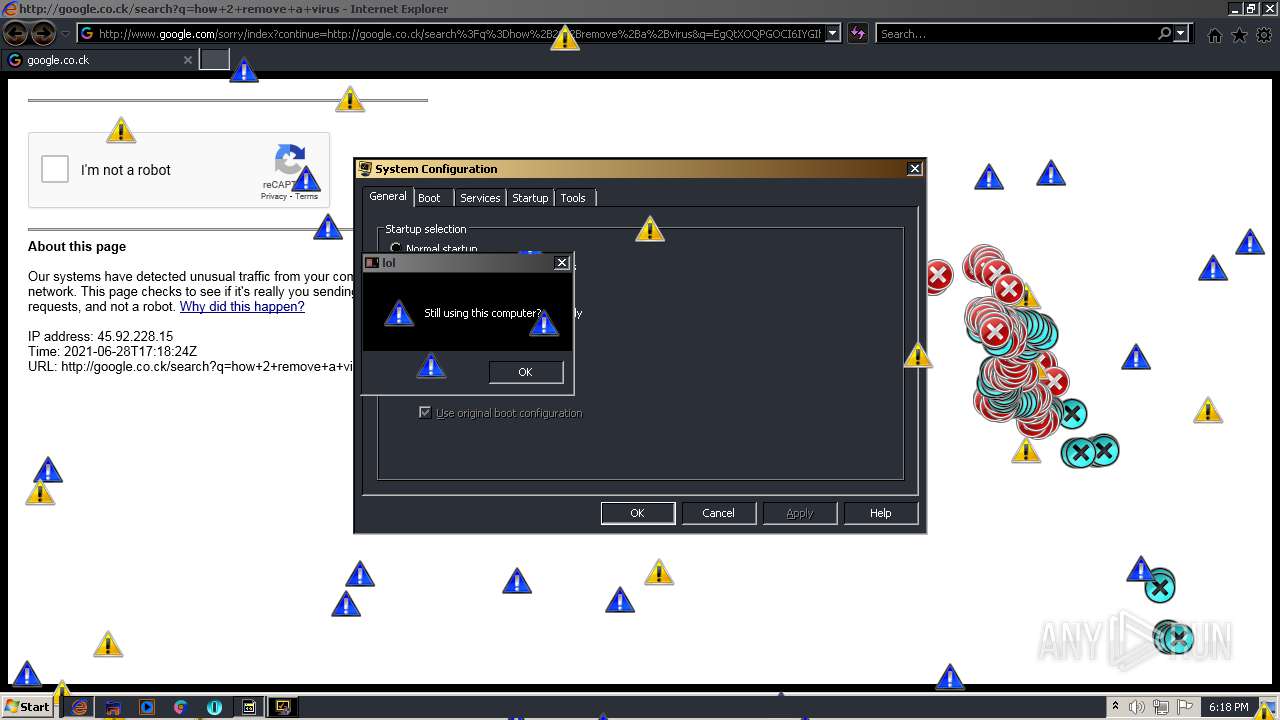
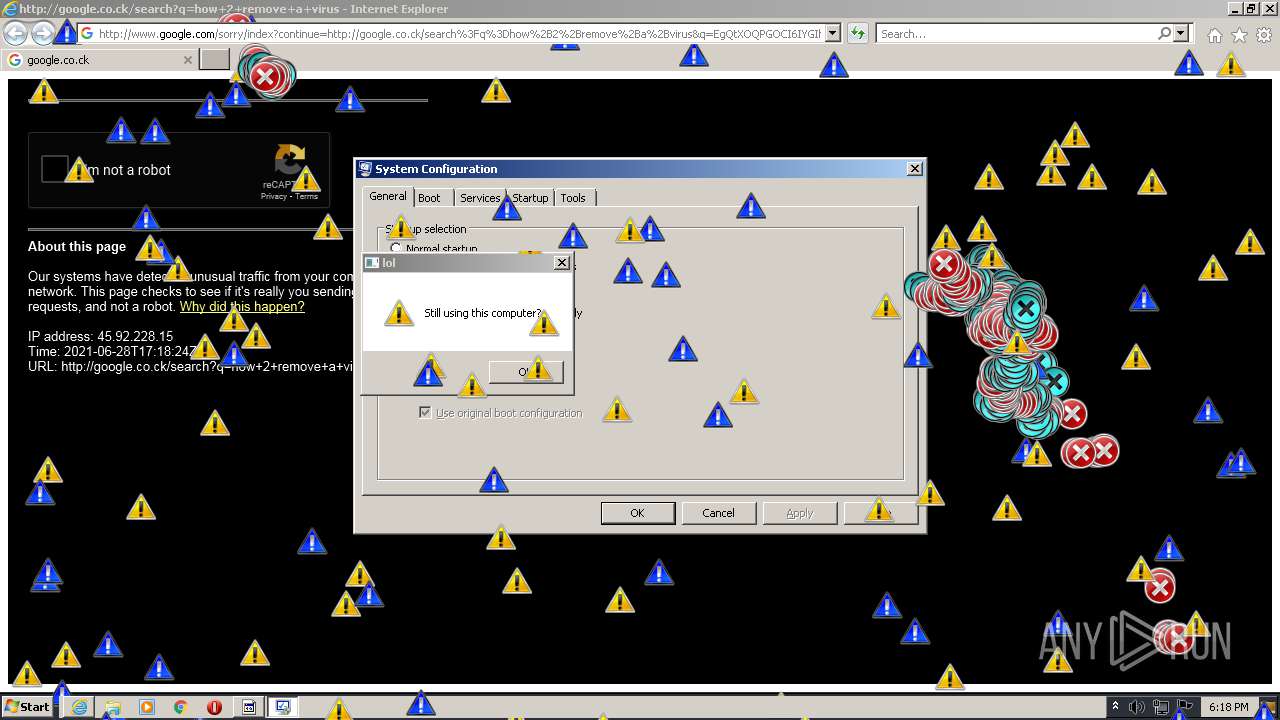
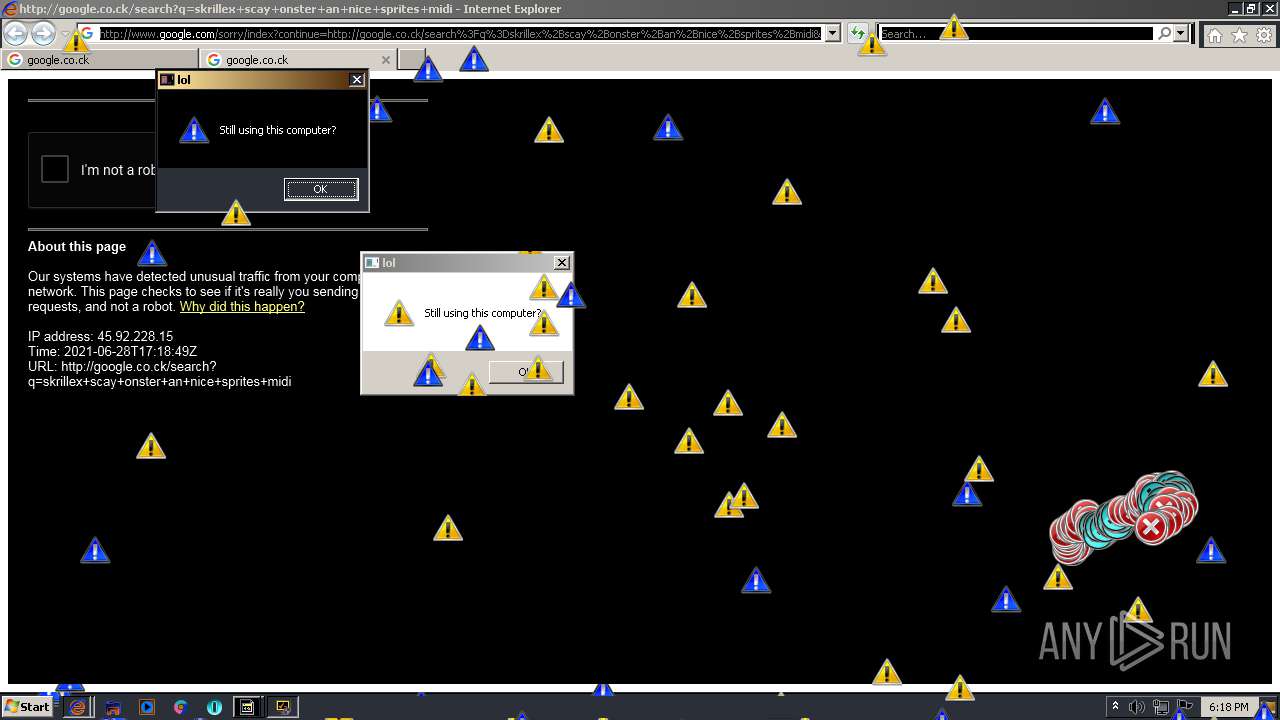
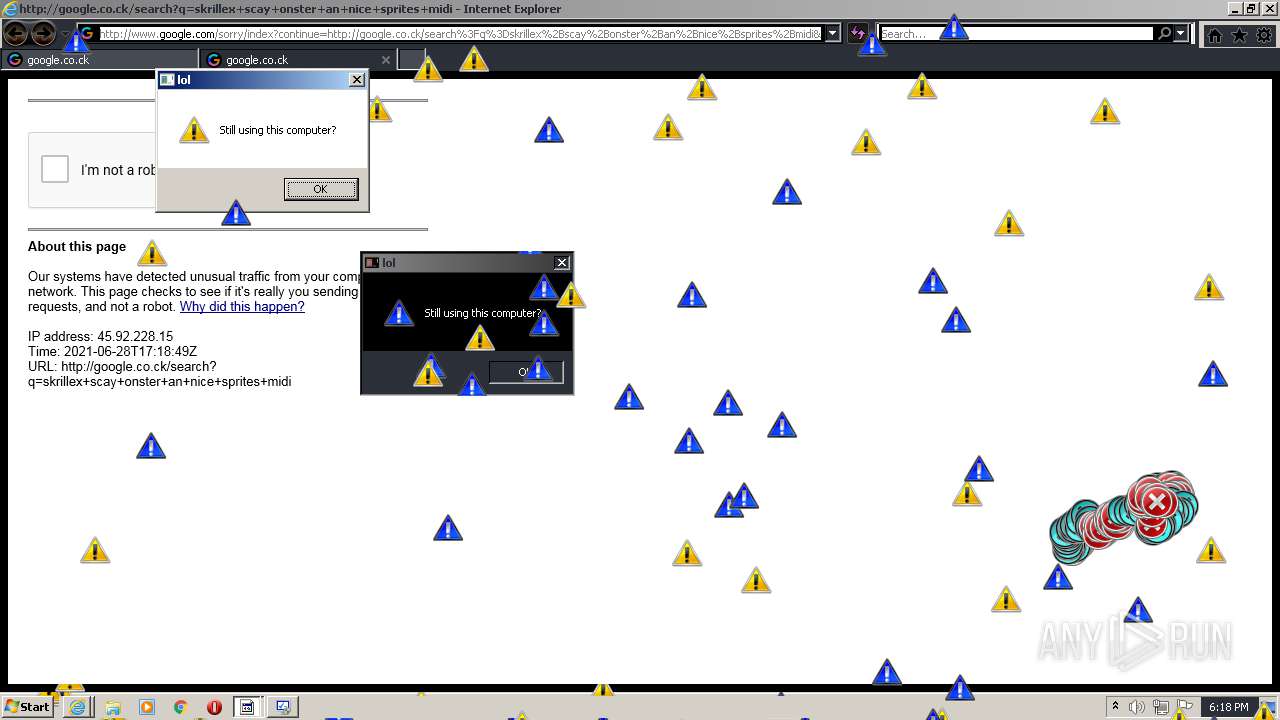
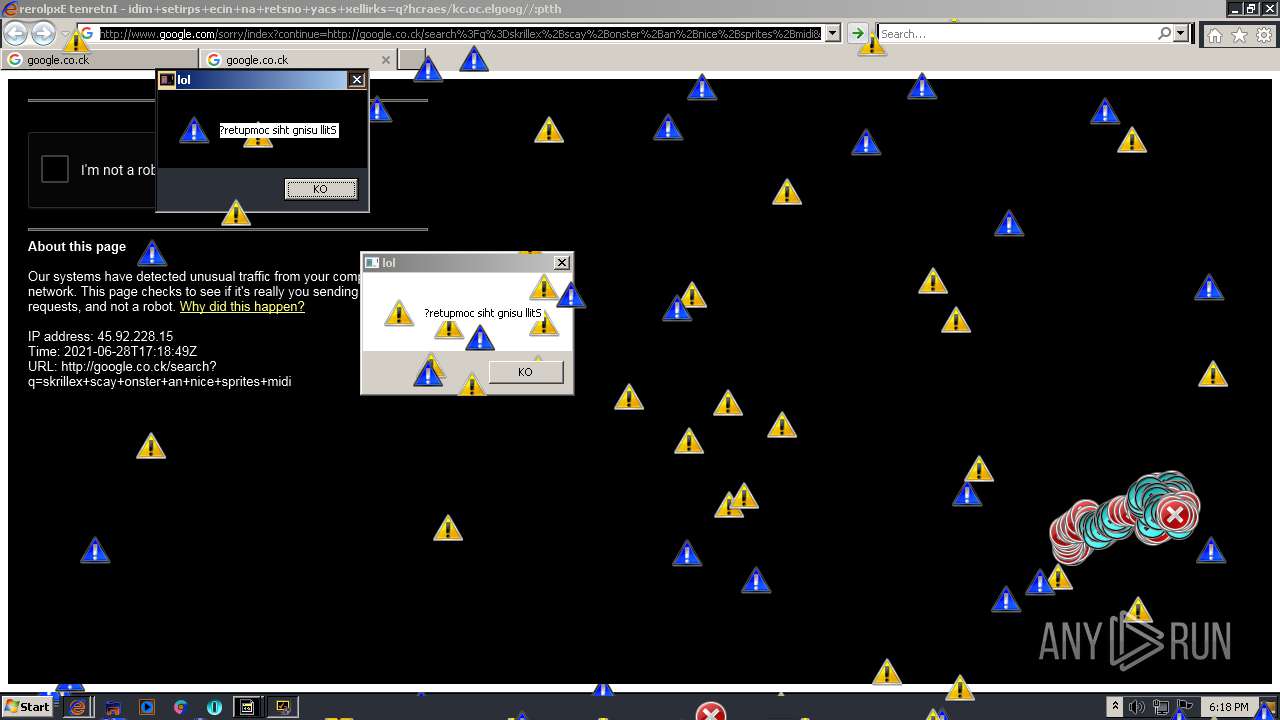
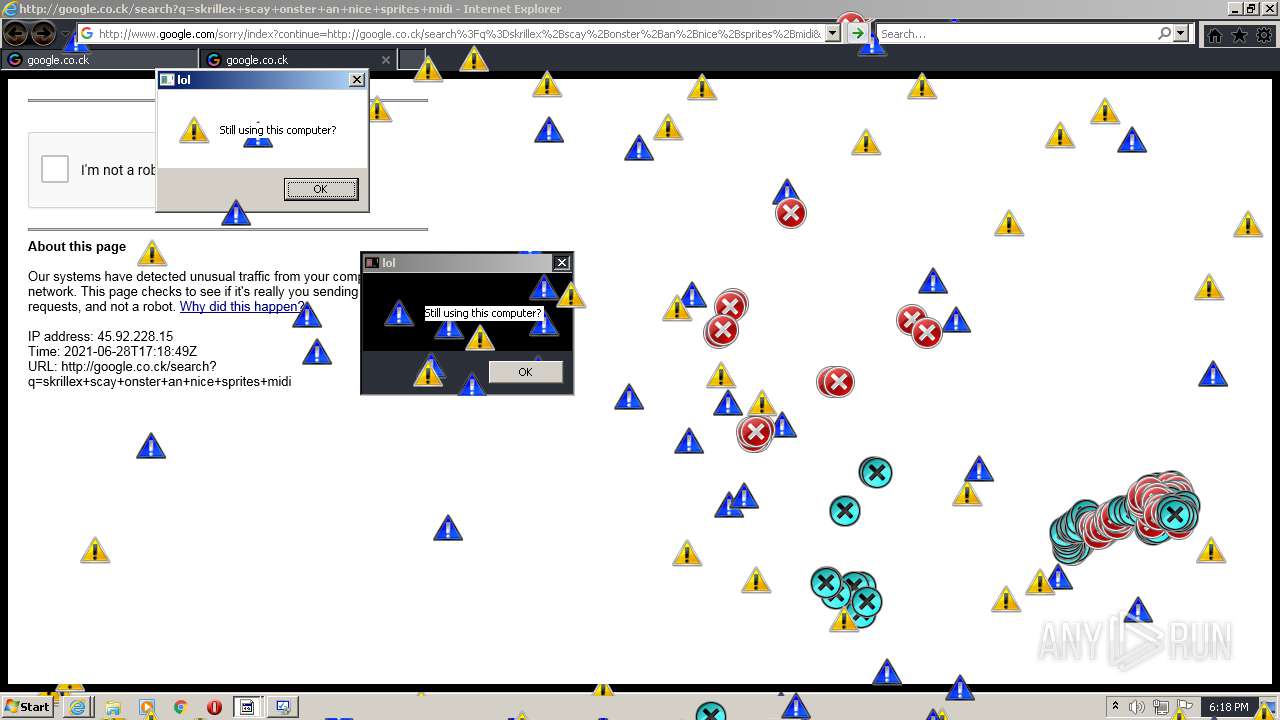
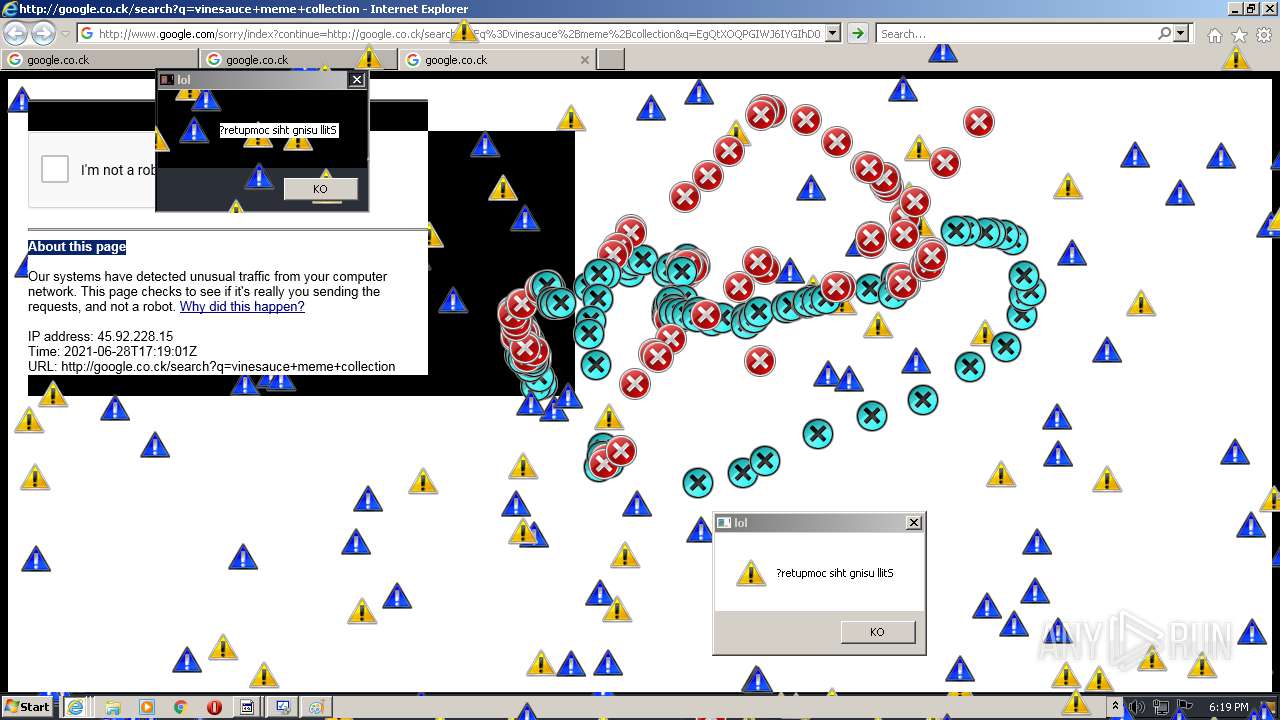
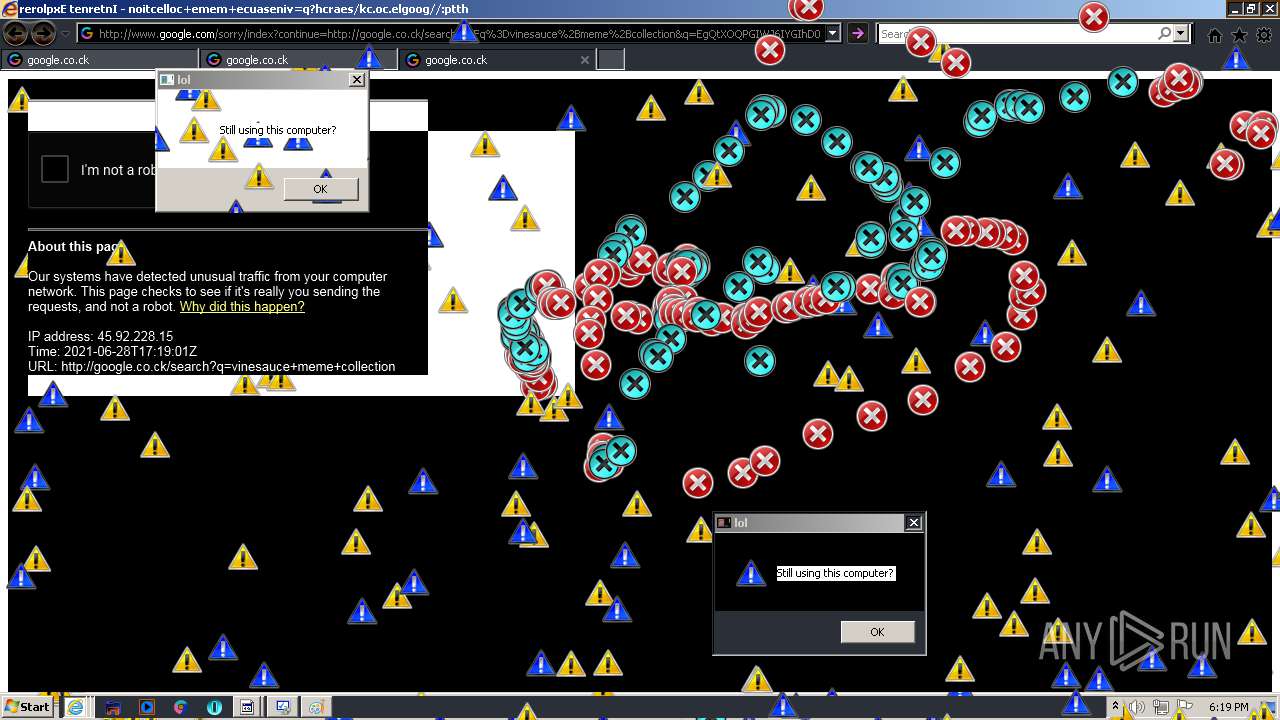
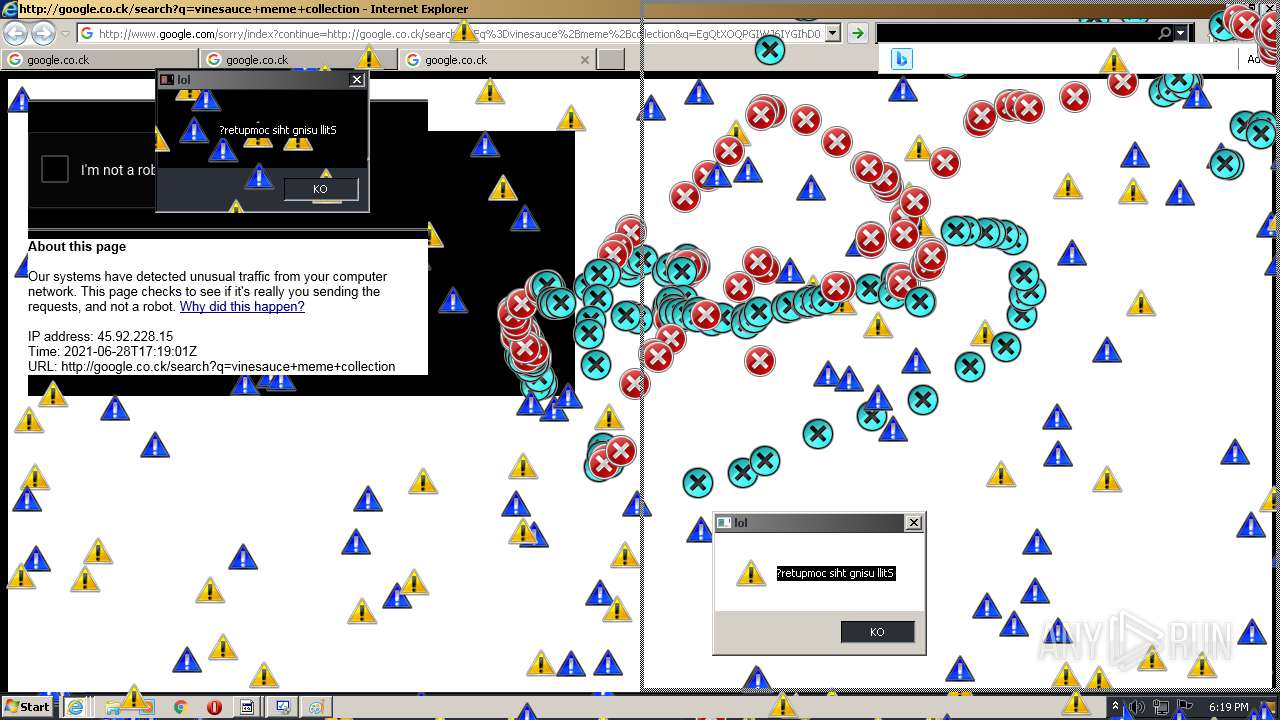
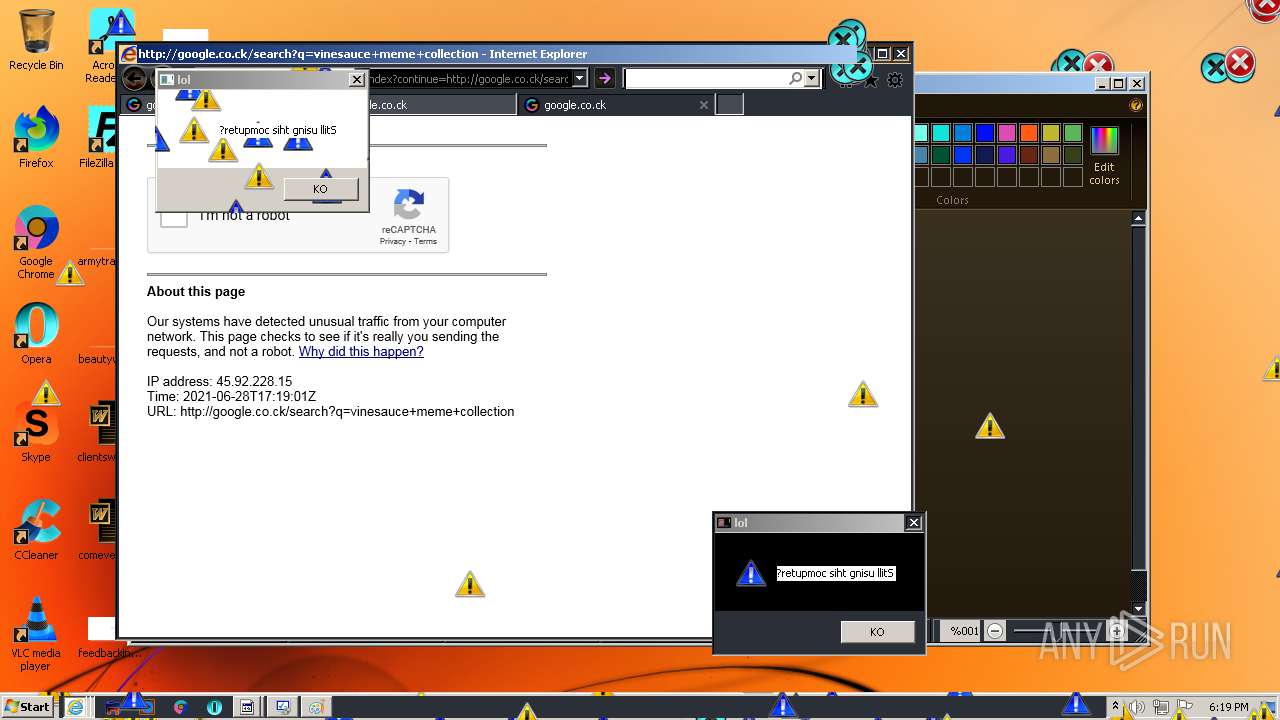
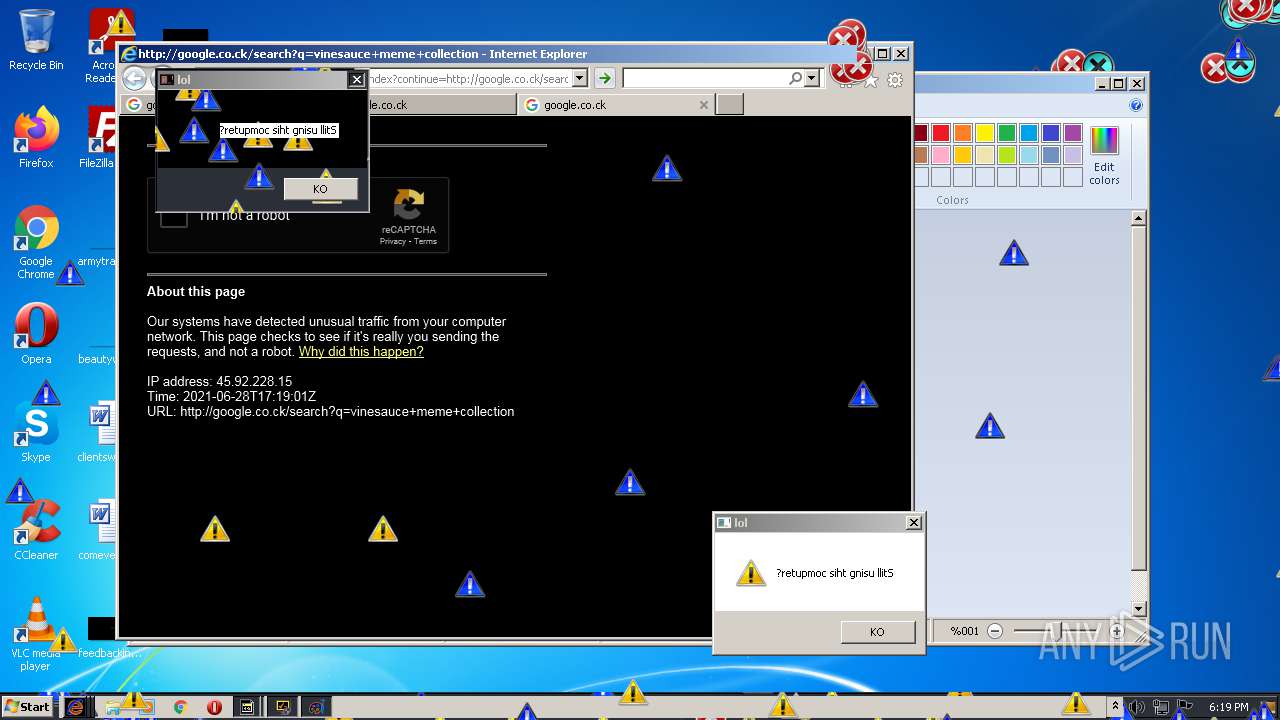
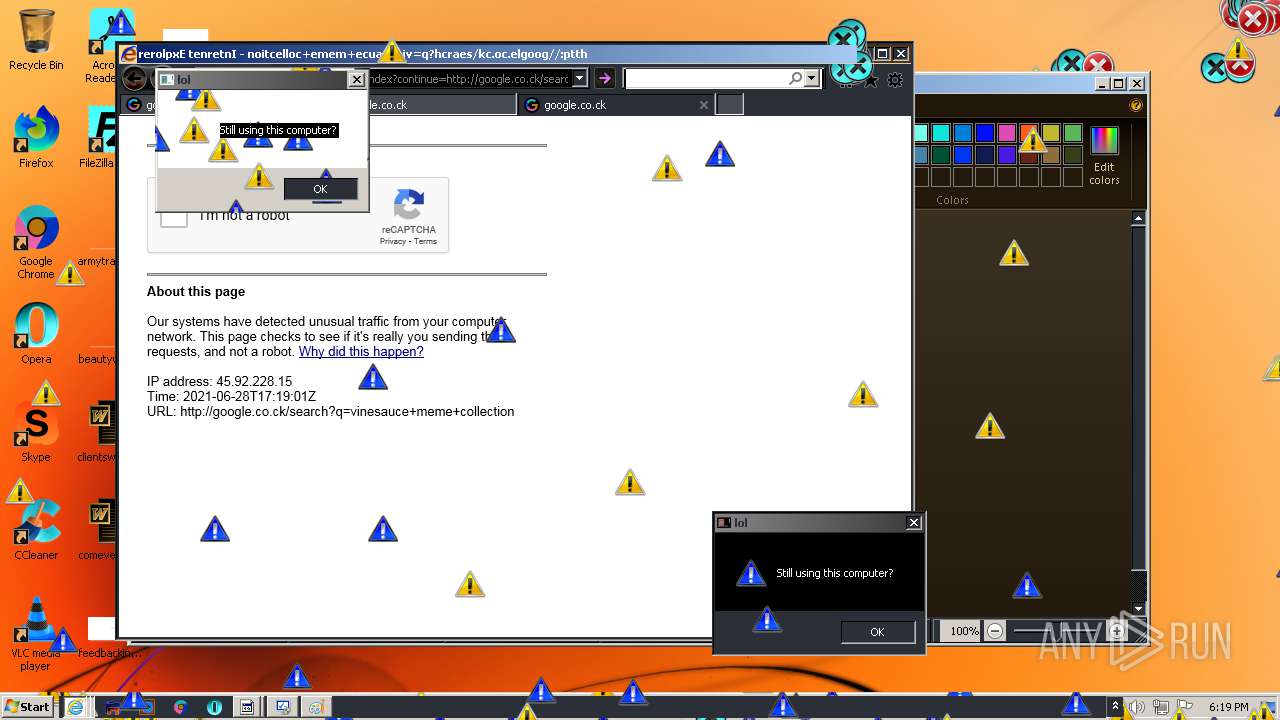
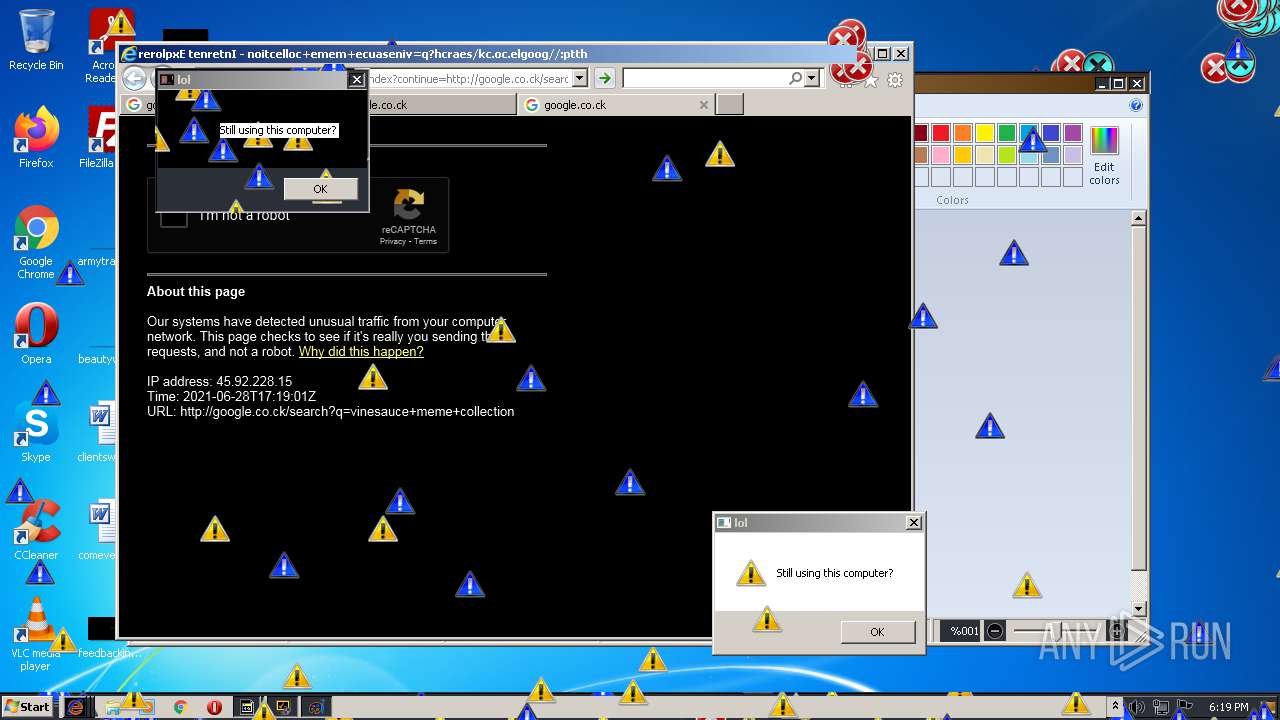
1420 | iexplore.exe | GET | 302 | 142.250.186.68:80 | http://google.co.ck/search?q=how+2+remove+a+virus | US | html | 352 b | whitelisted |
1420 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCa%2BkMO6O7i%2FwoAAAAA3KDI | US | der | 472 b | whitelisted |
2536 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAZnA1u7FP1jr8DWqFNO%2FhY%3D | US | der | 471 b | whitelisted |
3552 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1420 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
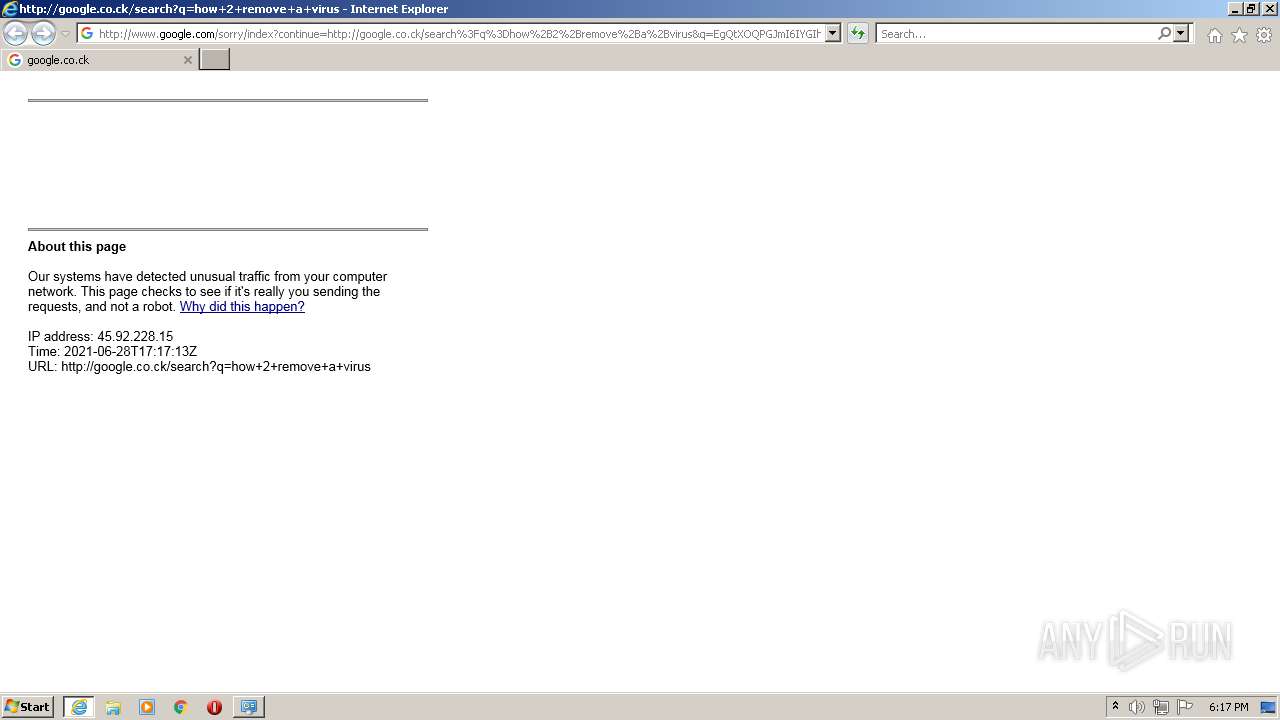
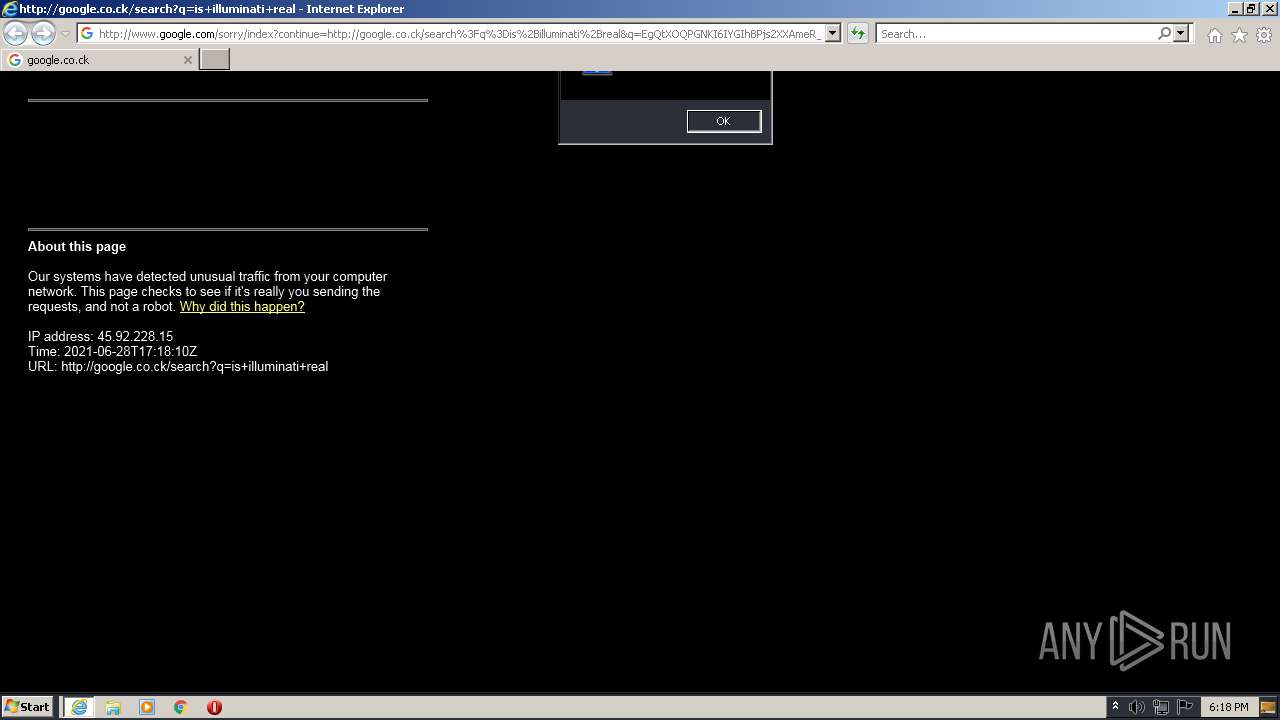
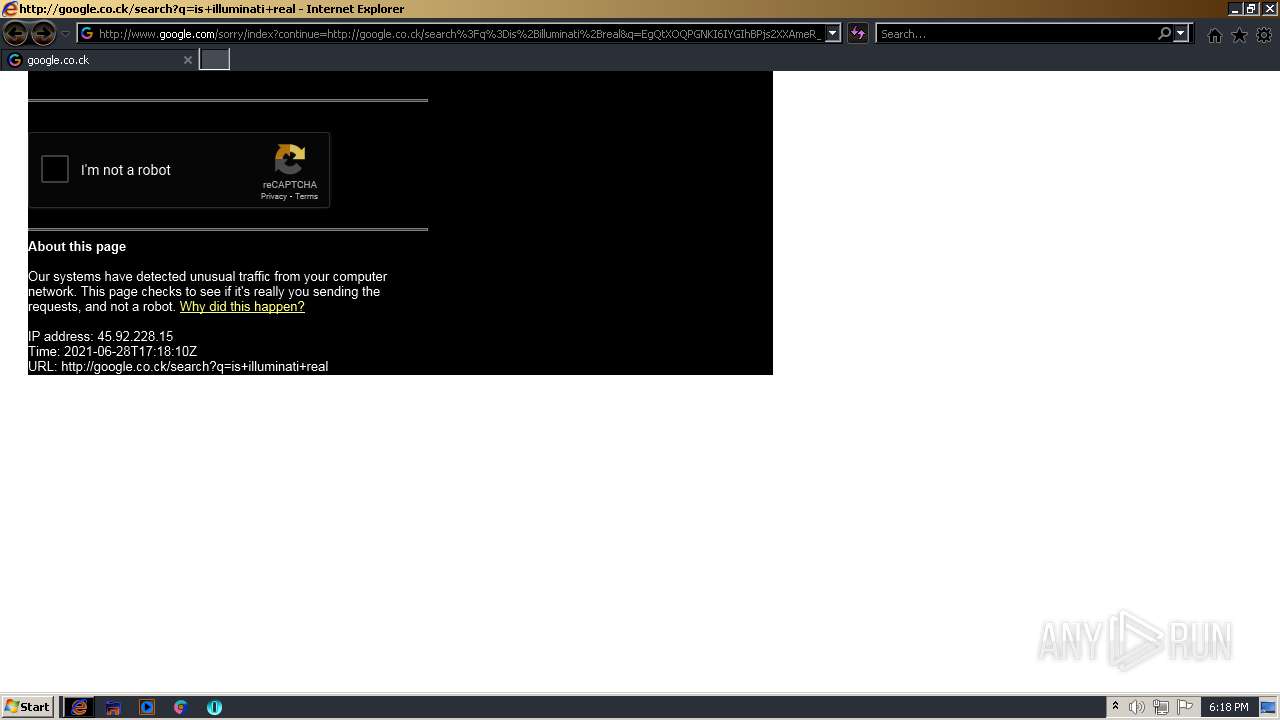
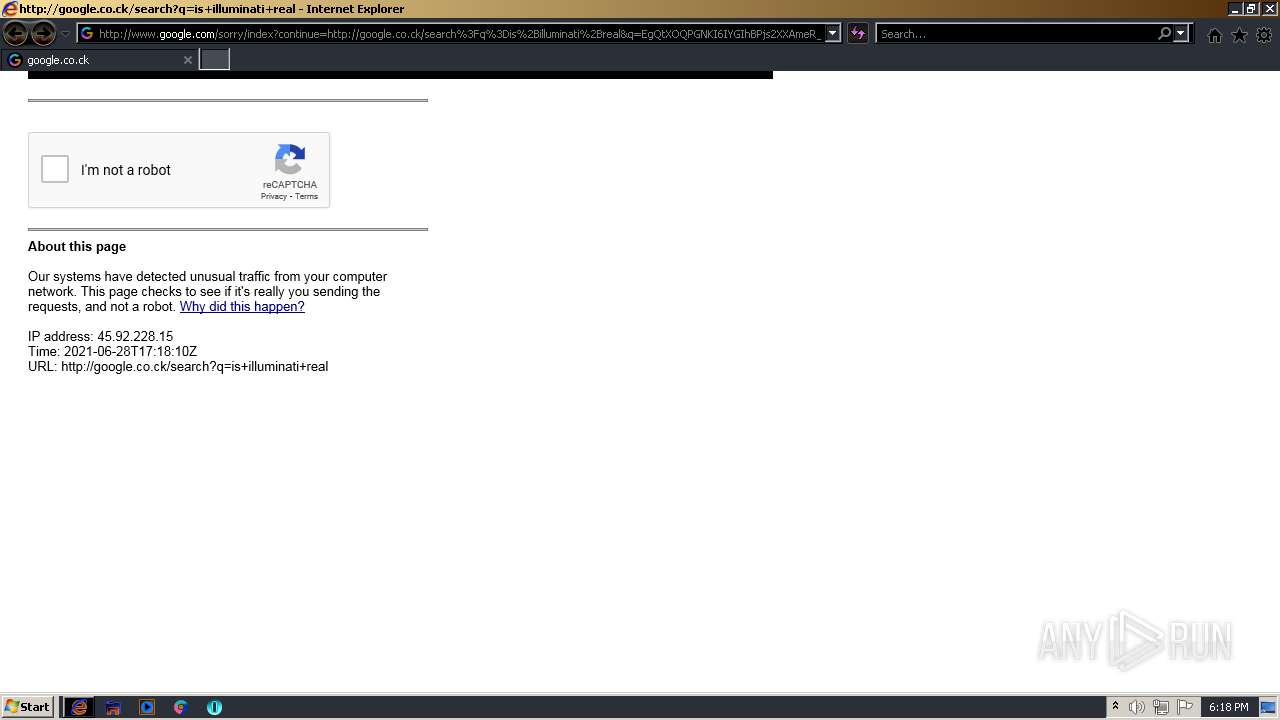
1420 | iexplore.exe | GET | 429 | 142.250.185.196:80 | http://www.google.com/sorry/index?continue=http://google.co.ck/search%3Fq%3Dhow%2B2%2Bremove%2Ba%2Bvirus&q=EgQtXOQPGLuH6IYGIhBx8Iz1wTgHpOXZCeOCpojhMgFy | US | html | 2.78 Kb | malicious |
1112 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2536 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2536 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2536 | iexplore.exe | 8.248.117.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
2536 | iexplore.exe | 140.82.121.3:443 | github.com | — | US | suspicious |
2536 | iexplore.exe | 185.199.110.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | malicious |
3552 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3552 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3456 | chrome.exe | 172.217.16.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
3456 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3456 | chrome.exe | 142.250.185.237:443 | accounts.google.com | Google Inc. | US | suspicious |
3456 | chrome.exe | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |