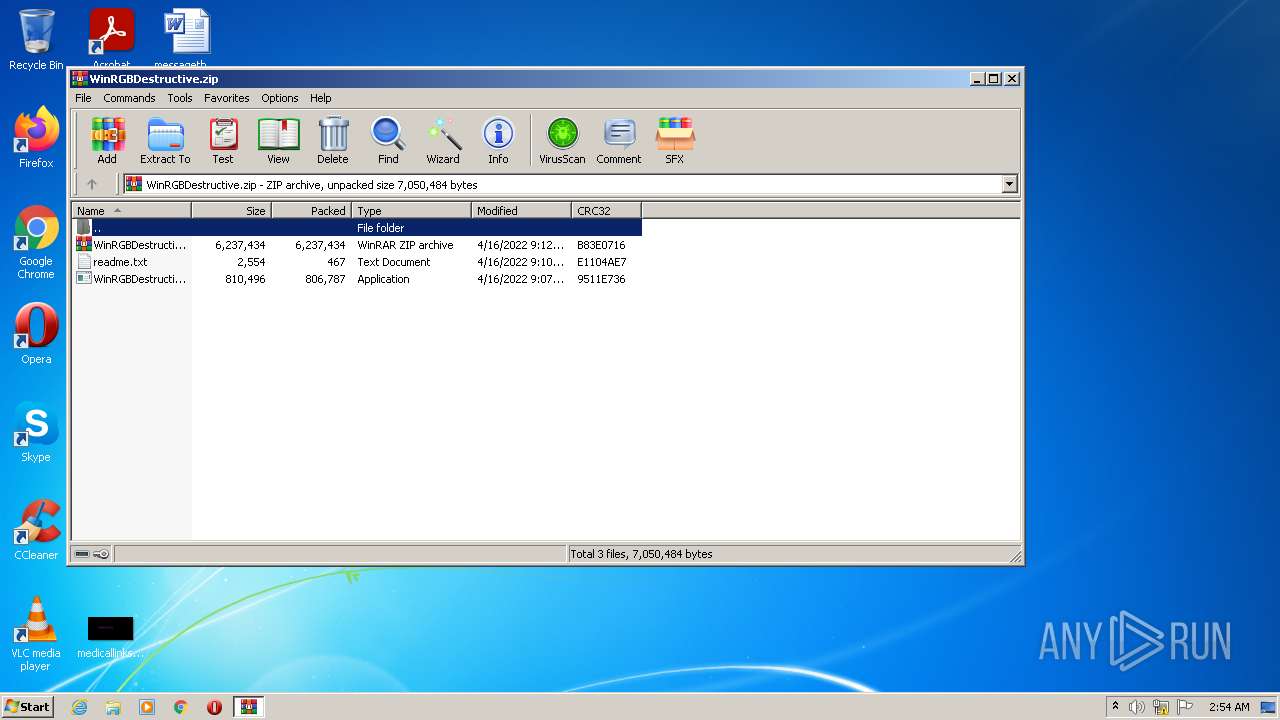
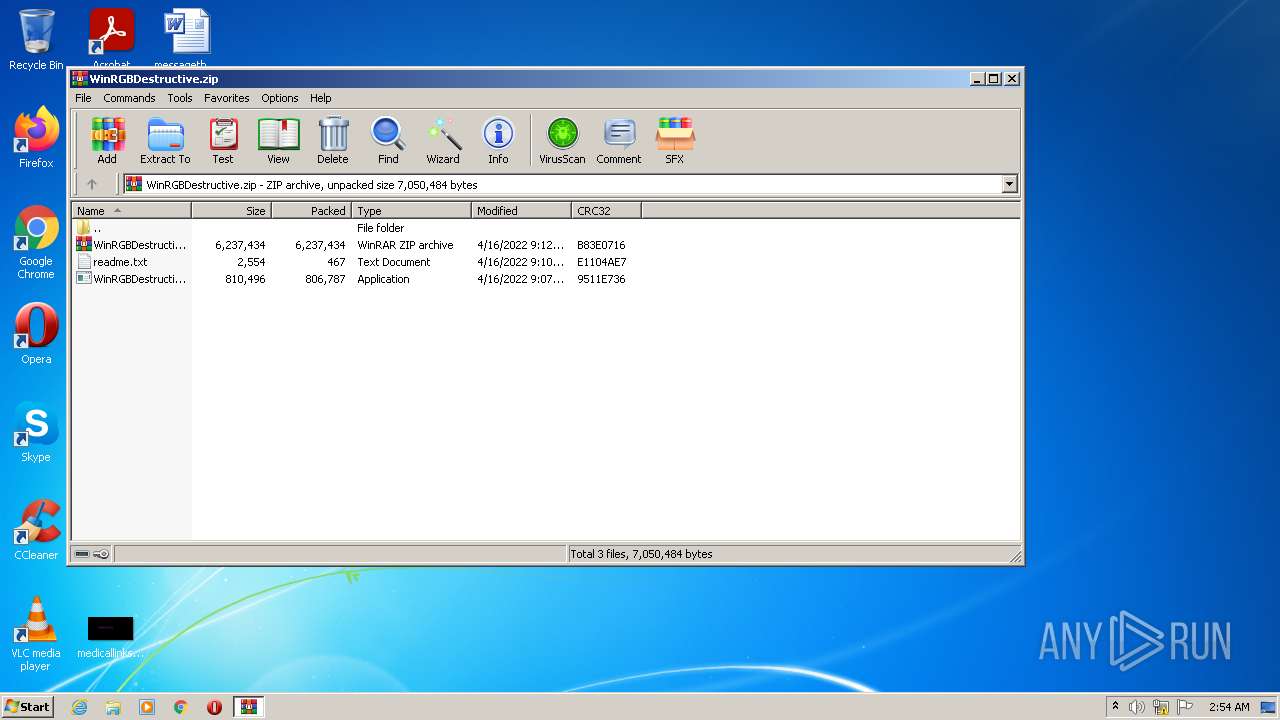
| File name: | WinRGBDestructive.zip |
| Full analysis: | https://app.any.run/tasks/2b85ed79-d9a4-4cf8-9ab0-b5d19ac9c344 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2022, 01:53:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2CCF48C0F0E4379E7FE1290008E9E27B |
| SHA1: | 4841AE2EF01EB9CF6046034EE605EB0082EFCD48 |
| SHA256: | F14DC938825E26808CEB544D8DBDEEA14A3E88EE299D9B07F60B851E4F4B188B |
| SSDEEP: | 98304:AUKmwLFDU3FsvhB70f+deONz7niiyvMwsNAyOyOnGw+/asdVLor85nw2pVistzQ0:CxLFDUGhq4799OnG3isTDnwOQo8CV |
MALICIOUS
Application was dropped or rewritten from another process
- WinRGBDestructive.exe (PID: 2976)
- WinRGBDestructive.exe (PID: 268)
- bytebeat1.exe (PID: 1904)
- rgb.exe (PID: 3412)
- sinewaves.exe (PID: 2468)
- mbr.exe (PID: 1908)
- Lines.exe (PID: 3632)
Drops executable file immediately after starts
- WinRAR.exe (PID: 3296)
- WinRGBDestructive.exe (PID: 268)
SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3296)
- WinRGBDestructive.exe (PID: 268)
Reads the computer name
- WinRAR.exe (PID: 3296)
- WinRGBDestructive.exe (PID: 268)
- bytebeat1.exe (PID: 1904)
- wscript.exe (PID: 3712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3296)
- WinRGBDestructive.exe (PID: 268)
Checks supported languages
- WinRAR.exe (PID: 3296)
- WinRGBDestructive.exe (PID: 268)
- bytebeat1.exe (PID: 1904)
- rgb.exe (PID: 3412)
- wscript.exe (PID: 3712)
- mbr.exe (PID: 1908)
- sinewaves.exe (PID: 2468)
- Lines.exe (PID: 3632)
Executes scripts
- WinRGBDestructive.exe (PID: 268)
INFO
Manual execution by user
- WinRGBDestructive.exe (PID: 268)
- WinRGBDestructive.exe (PID: 2976)
Checks Windows Trust Settings
- wscript.exe (PID: 3712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | WinRGBDestructive.exe |
|---|---|
| ZipUncompressedSize: | 810496 |
| ZipCompressedSize: | 806787 |
| ZipCRC: | 0x9511e736 |
| ZipModifyDate: | 2022:04:16 10:07:15 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
46
Monitored processes
9
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\Desktop\WinRGBDestructive.exe" | C:\Users\admin\Desktop\WinRGBDestructive.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1904 | "C:\Users\admin\AppData\Local\Temp\2682.tmp\bytebeat1.exe" | C:\Users\admin\AppData\Local\Temp\2682.tmp\bytebeat1.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1908 | "C:\Users\admin\AppData\Local\Temp\2682.tmp\mbr.exe" | C:\Users\admin\AppData\Local\Temp\2682.tmp\mbr.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Temp\2682.tmp\sinewaves.exe" | C:\Users\admin\AppData\Local\Temp\2682.tmp\sinewaves.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\Desktop\WinRGBDestructive.exe" | C:\Users\admin\Desktop\WinRGBDestructive.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3296 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\WinRGBDestructive.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3412 | "C:\Users\admin\AppData\Local\Temp\2682.tmp\rgb.exe" | C:\Users\admin\AppData\Local\Temp\2682.tmp\rgb.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3632 | "C:\Users\admin\AppData\Local\Temp\2682.tmp\Lines.exe" | C:\Users\admin\AppData\Local\Temp\2682.tmp\Lines.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3712 | "C:\Windows\system32\wscript.exe" C:\Users\admin\AppData\Local\Temp\2682.tmp\2683.tmp\2684.vbs //Nologo | C:\Windows\system32\wscript.exe | — | WinRGBDestructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
2 080
Read events
2 051
Write events
29
Delete events
0
Modification events
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WinRGBDestructive.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
12
Suspicious files
1
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\bytebeat1.exe | executable | |
MD5:6B673ECE600BCC8A665EBF251D7D926E | SHA256:41AC58D922F32134E75E87898D2C179D478C81EDAAE0D9BC28E7CE7D6F422F8B | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\bytebeat1.wav | wav | |
MD5:09D2094F56D2D38AA64EAC1D90C5A554 | SHA256:4599F6F06C7F491A50E3C4012A83CCE9F3EE13AE209189CB8964F0B6BA14614C | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\bytebeat1.txt | text | |
MD5:848CDE3FC92870D6315795FA5E0CFEFA | SHA256:185E5B831B37F992D07570B7A2EFFDE08734513884867967B67B2086ECE659E6 | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\bsod.cpp | text | |
MD5:CA73D197DEF1B095BC712CBEC6168FE2 | SHA256:72BB7E3AE6DA142F61E824951DC4ADD9B1851C010CCABF6C68671AF0C970ECCB | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\bytebeat1.cpp | text | |
MD5:68C309CE1FAEFBF83A6F4B9988B84D2F | SHA256:D1FED31D11B387B29AE25E9CBC43AAA633A60BECA039A4AFCFBA4FB11117C11A | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\cubes.cpp | text | |
MD5:A7B13FE165BE9EE2D89CF818D25C6B78 | SHA256:C385660B680E0EE1C0C3AD0D76246E6088963DBCBD316E1ABCC0661C741E3E5C | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\cubes.exe | executable | |
MD5:ED695DAC2B14CCAD335E75F5DDD44139 | SHA256:2D3E7CDBF244704934AFA447552C049A891A9CCBD6D4AB42CA2504AD0A99E803 | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\Lines.cpp | text | |
MD5:5C8FF3E01DA6C6184A6DD9E9E3362DB9 | SHA256:3751238F33A241EDB16D166D1F9A21D71B3BA51A872D32DB05490A229AC67F29 | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\invmelter.cpp | text | |
MD5:E7FD701F5A6A52859DBE7E4DA3C2E2FA | SHA256:105AA5FE1C61EADC3BBCF82433BBBC4DD1AB9250FA697E5612AA85634BF14A22 | |||
| 268 | WinRGBDestructive.exe | C:\Users\admin\AppData\Local\Temp\2682.tmp\invmelter.exe | executable | |
MD5:0928425141C06EBB894E50A54C2AA1F0 | SHA256:229F07414798ADB8F850697CB0AD12A1911443C8B31C0484C1B96A16EFEE9A02 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report