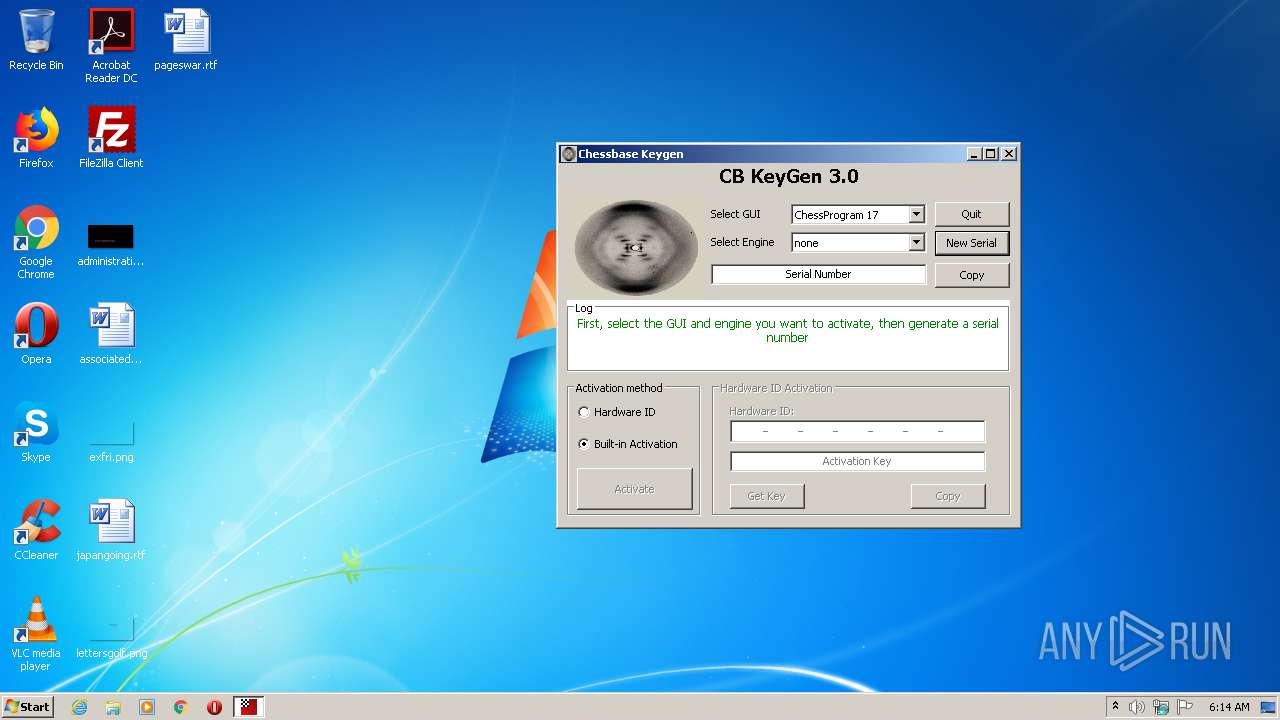
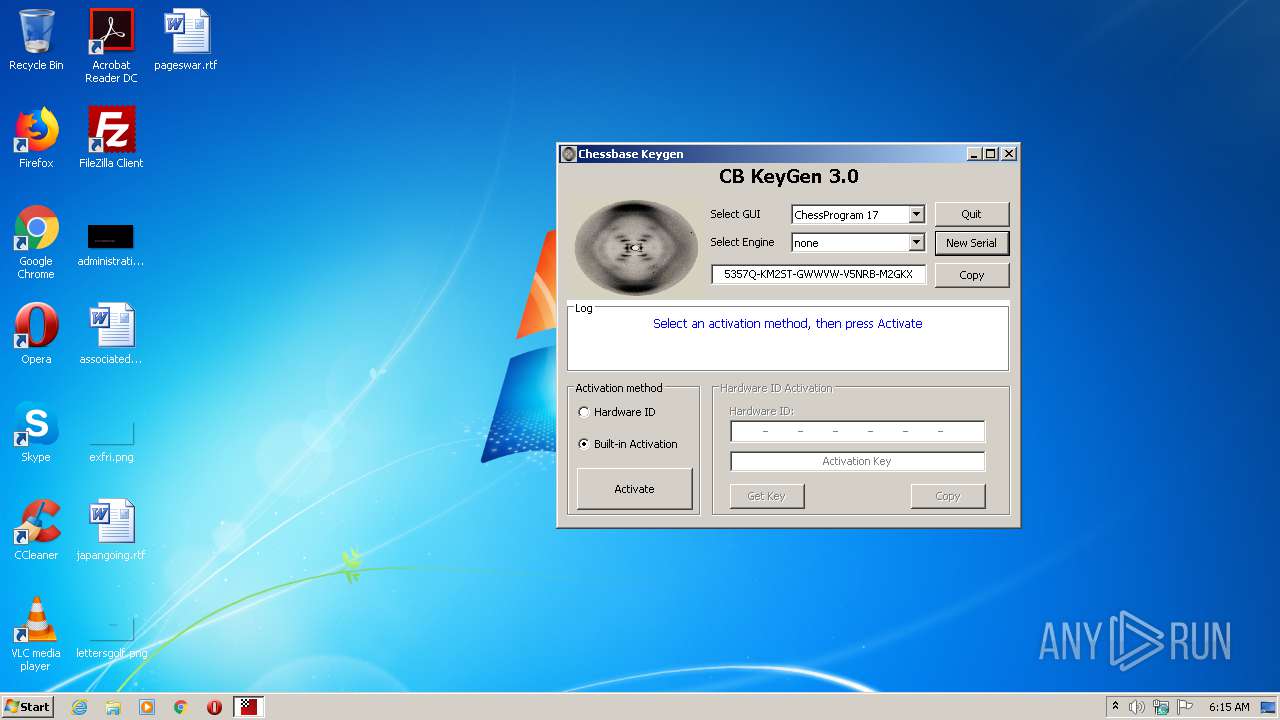
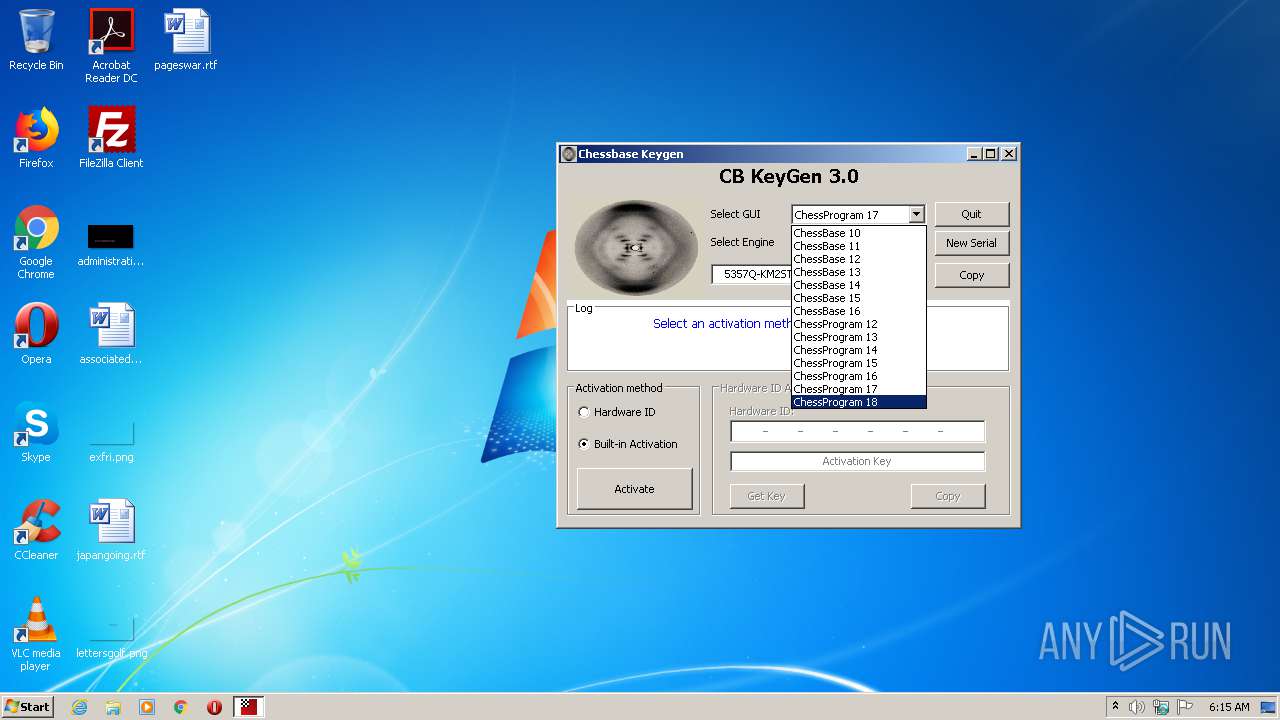
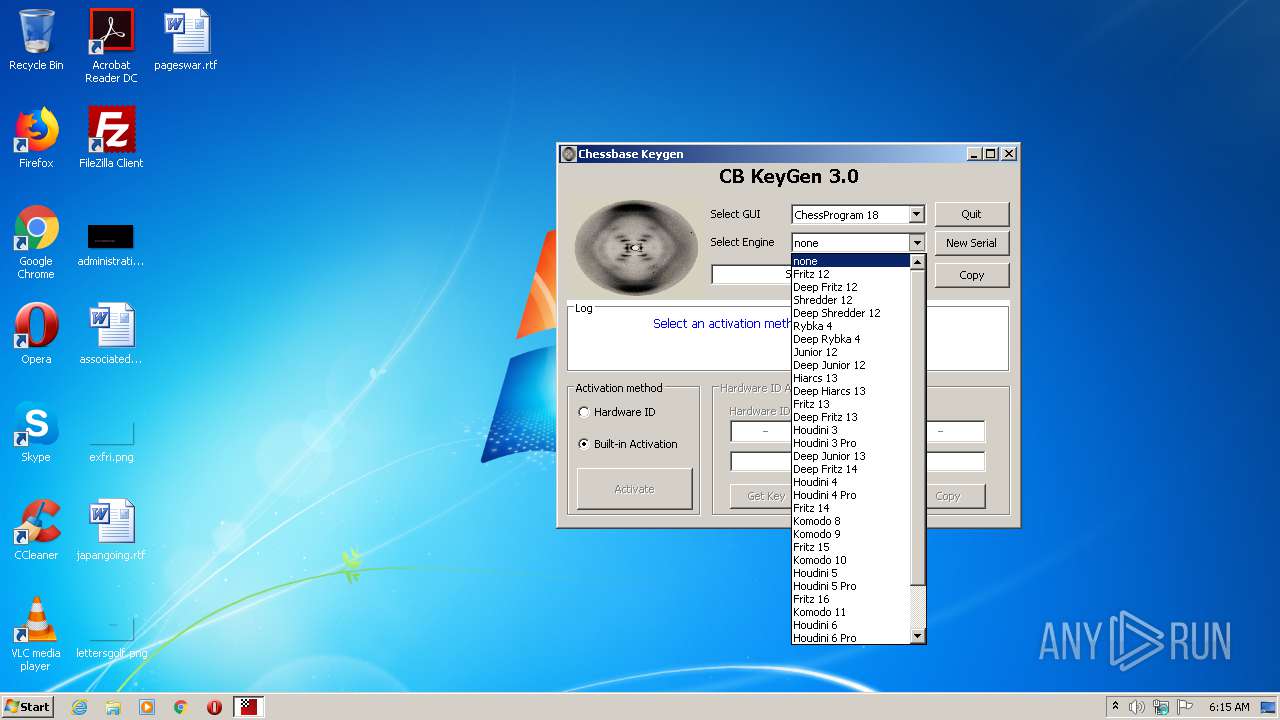
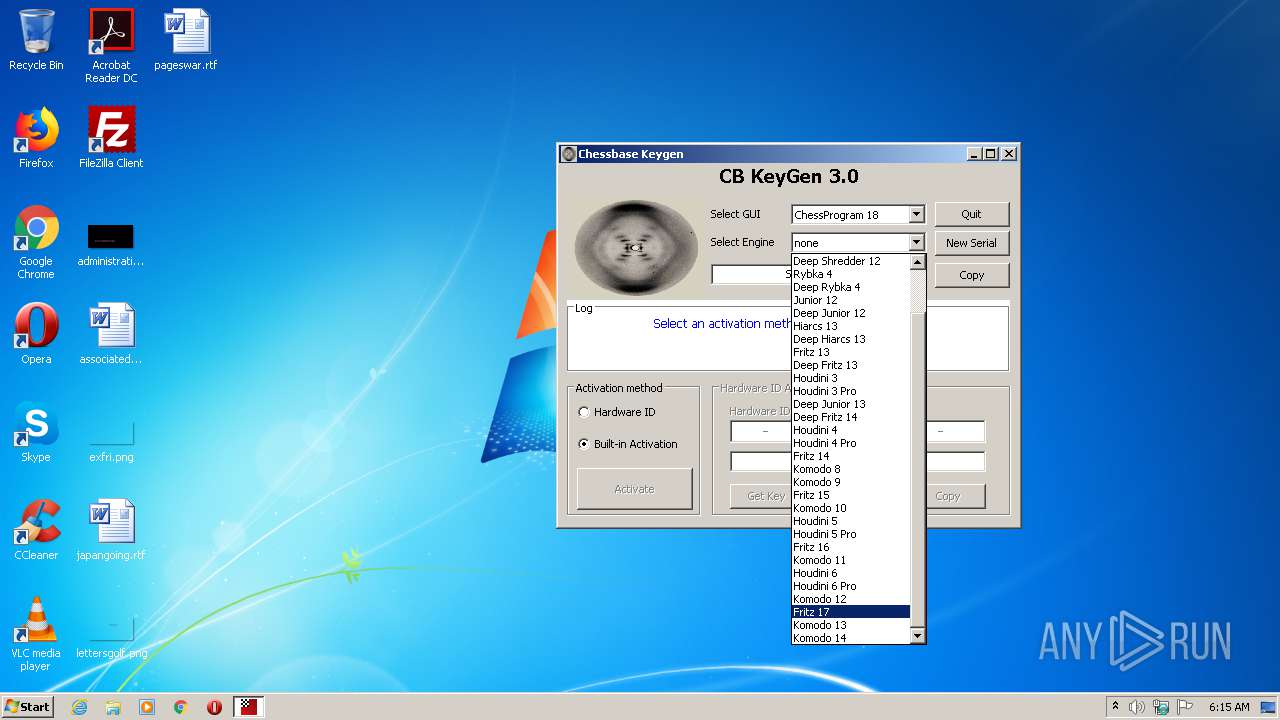
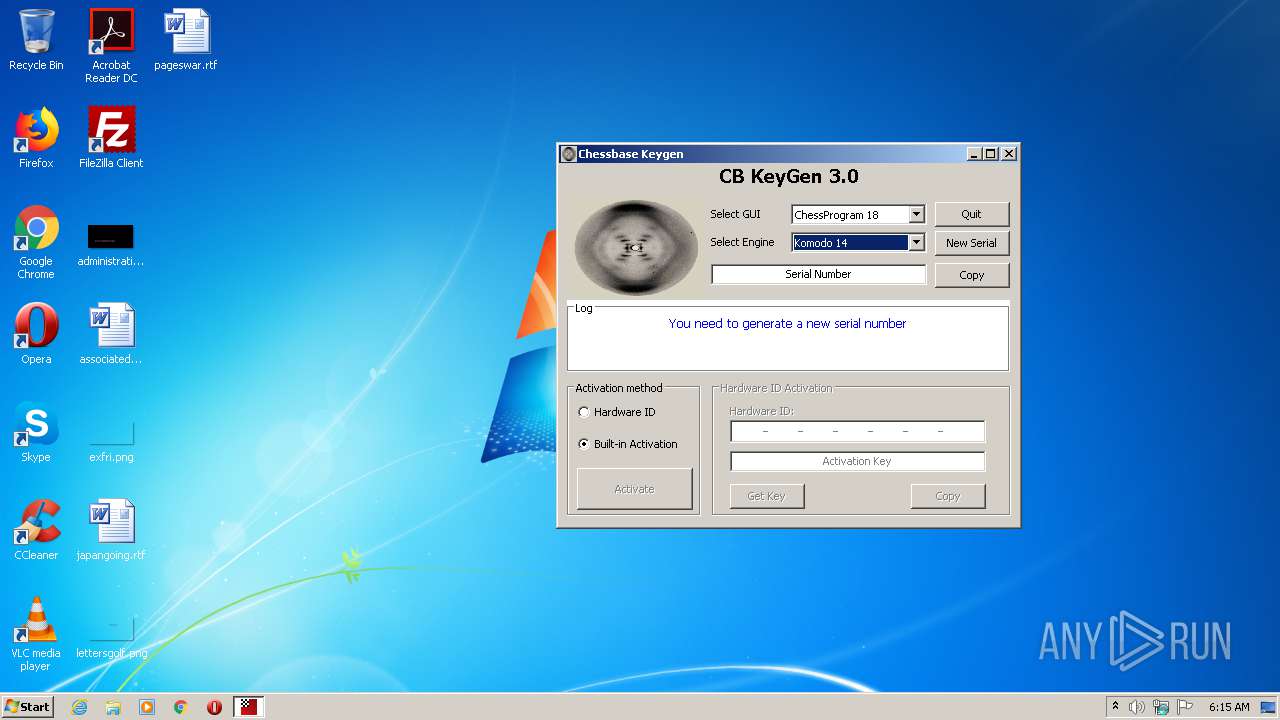
| File name: | CB-Keygen.exe |
| Full analysis: | https://app.any.run/tasks/a9ac125c-18a9-4235-a020-447b8ec5e9cd |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 05:14:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C1C8F7684189B73E401DCE446095CD2A |
| SHA1: | 42A8AE5E6D7DF85D0A34DEF989797D35A6B71ACD |
| SHA256: | F141B21BB0C96131958BC3B453EAEEA36293BD7D7D7C02504AAB6C5020BFB5E1 |
| SSDEEP: | 98304:mfd+ocR2lKPRan4Q5kSalQx/vyCguzX8znUieT:6d0K0RdliRyzuzXwPA |
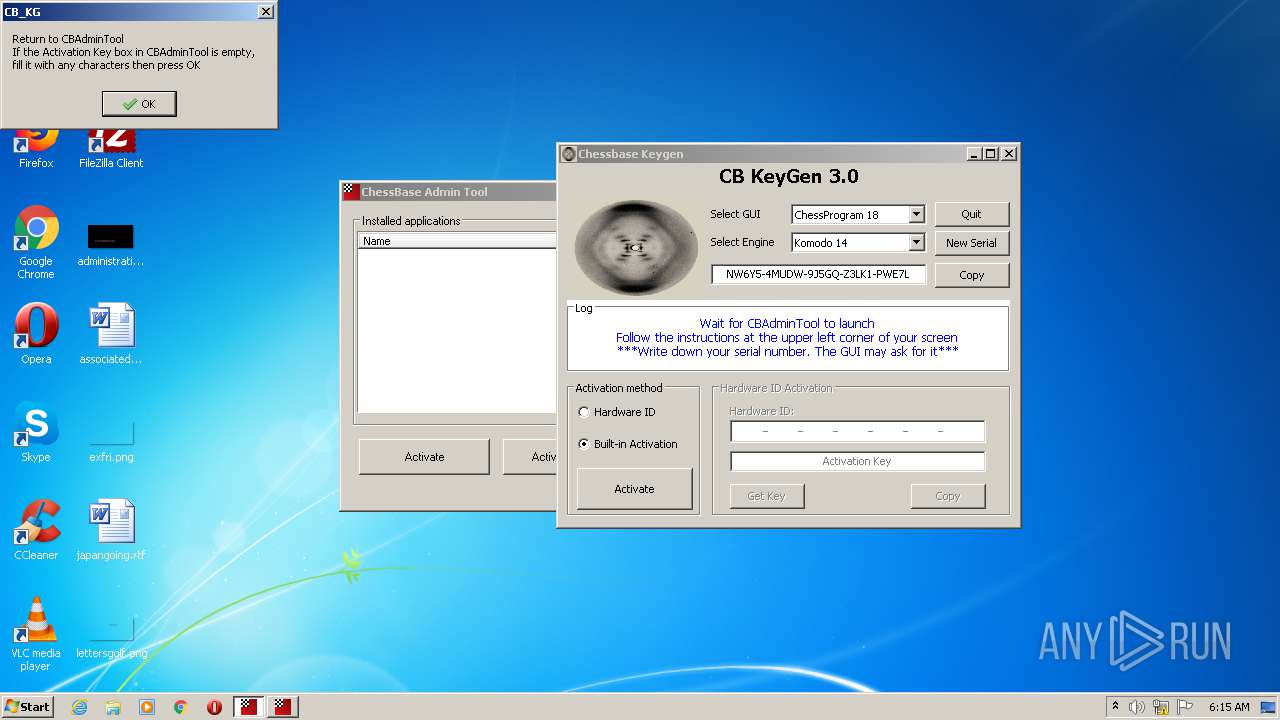
MALICIOUS
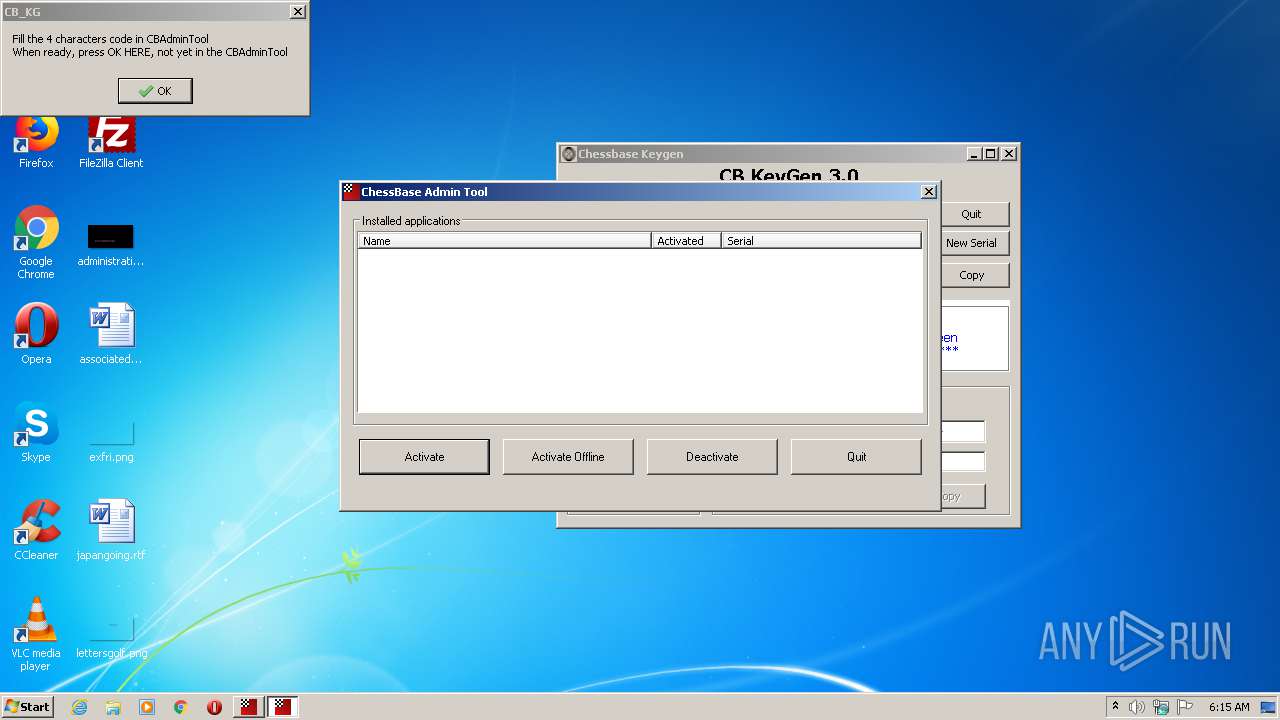
Application was dropped or rewritten from another process
- ChessBaseAdminTool.exe (PID: 2684)
- ChessBaseAdminTool.exe (PID: 3236)
- CB_KG.exe (PID: 2720)
Loads dropped or rewritten executable
- ChessBaseAdminTool.exe (PID: 2684)
SUSPICIOUS
Executable content was dropped or overwritten
- CB_KG.exe (PID: 2720)
- CB-Keygen.exe (PID: 2836)
INFO
Dropped object may contain Bitcoin addresses
- CB_KG.exe (PID: 2720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:26 11:02:47+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 198144 |
| InitializedDataSize: | 254464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e1f9 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Mar-2020 10:02:47 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 26-Mar-2020 10:02:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00030581 | 0x00030600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70021 |
.rdata | 0x00032000 | 0x0000A332 | 0x0000A400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.23888 |
.data | 0x0003D000 | 0x000238B0 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.83994 |
.gfids | 0x00061000 | 0x000000E8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.12166 |
.rsrc | 0x00062000 | 0x0000DFD0 | 0x0000E000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.63693 |
.reloc | 0x00070000 | 0x0000210C | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.61039 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.10026 | 2216 | UNKNOWN | English - United States | RT_ICON |
3 | 5.25868 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 5.02609 | 1128 | UNKNOWN | English - United States | RT_ICON |
5 | 5.18109 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.04307 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 3.1586 | 482 | UNKNOWN | English - United States | RT_STRING |
8 | 3.11685 | 460 | UNKNOWN | English - United States | RT_STRING |
9 | 3.11236 | 440 | UNKNOWN | English - United States | RT_STRING |
10 | 2.99727 | 326 | UNKNOWN | English - United States | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2684 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe" /ActivationOffline "1678901504" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | CB_KG.exe | ||||||||||||
User: admin Company: ChessBase GmbH Integrity Level: HIGH Description: ChessBase Admin Tool Exit code: 0 Version: 2, 0, 0, 3 Modules
| |||||||||||||||
| 2720 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe | CB-Keygen.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\AppData\Local\Temp\CB-Keygen.exe" | C:\Users\admin\AppData\Local\Temp\CB-Keygen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3236 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe" /ActivationOffline "1678901504" | C:\Users\admin\AppData\Local\Temp\RarSFX0\ChessBaseAdminTool.exe | — | CB_KG.exe | |||||||||||
User: admin Company: ChessBase GmbH Integrity Level: MEDIUM Description: ChessBase Admin Tool Exit code: 3221226540 Version: 2, 0, 0, 3 Modules
| |||||||||||||||
Total events
763
Read events
755
Write events
8
Delete events
0
Modification events
| (PID) Process: | (2836) CB-Keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2836) CB-Keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2720) CB_KG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2720) CB_KG.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
6
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\English\Frame.strings | text | |
MD5:C3BFF8A72031EBE05575857C8CEF554F | SHA256:47CD98D0998FC7B3793E4DDA00DCD2D7EC4AE66C4FCEC342860A114CADB1837D | |||
| 2684 | ChessBaseAdminTool.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\0f5007522459c86e95ffcc62f32308f1_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:— | SHA256:— | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Frame.inc | text | |
MD5:5D5BCE47AF974B17A8CA80179C12417F | SHA256:45C96FD79DBC1DE5098E16B6857CFD42140FE4C5BC85AF562413DEF44D1F7029 | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Deutsch\Frame.strings | text | |
MD5:9938B167BF4DD13D7917BFC25B541EC8 | SHA256:386752A44E8E6569D5FCA11A95A303748AE7393900F5947749052BBCFBA29E62 | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140.dll | executable | |
MD5:8E65E033799EB9FD46BC5C184E7D1B85 | SHA256:BE38A38E22128AF9A529AF33D1F02DD24B2A344D29175939E229CF3A280673E4 | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\msvcp140.dll | executable | |
MD5:CFBDF284C12056347E6773CB3949FBBA | SHA256:BBECDFDA2551B01AA16005C88305982C360A9FB9BA3D9BE2FB15F2E9C6EB809F | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\SView3.dll | executable | |
MD5:F295816040F4132E1D9F3FB11E64CE3C | SHA256:4C1056F76986838C01F835040FCDE9F0034BBC9A3E8A48D3B46F863C0DF44531 | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\English\Countries.strings | text | |
MD5:90B850C19BDFDA9A852A786878B31CB0 | SHA256:C52A78C82F7EEDD0CE5BE7BC678837496632C9DFD53A965E29F90D4367C8D211 | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\mfc140.dll | executable | |
MD5:9A145819FEB9B159176FB95368BCD0BE | SHA256:3262782C80CEF7EF2CC23FFBE5D12F312736198D2F81F70DE1AA5F346D652DEB | |||
| 2836 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Countries.inc | text | |
MD5:200710201C95F4E8A612299B132289DA | SHA256:A1FF5302B95A293433F77DB64B40F04A2BD6706521CF0A8702991D88378B015C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report