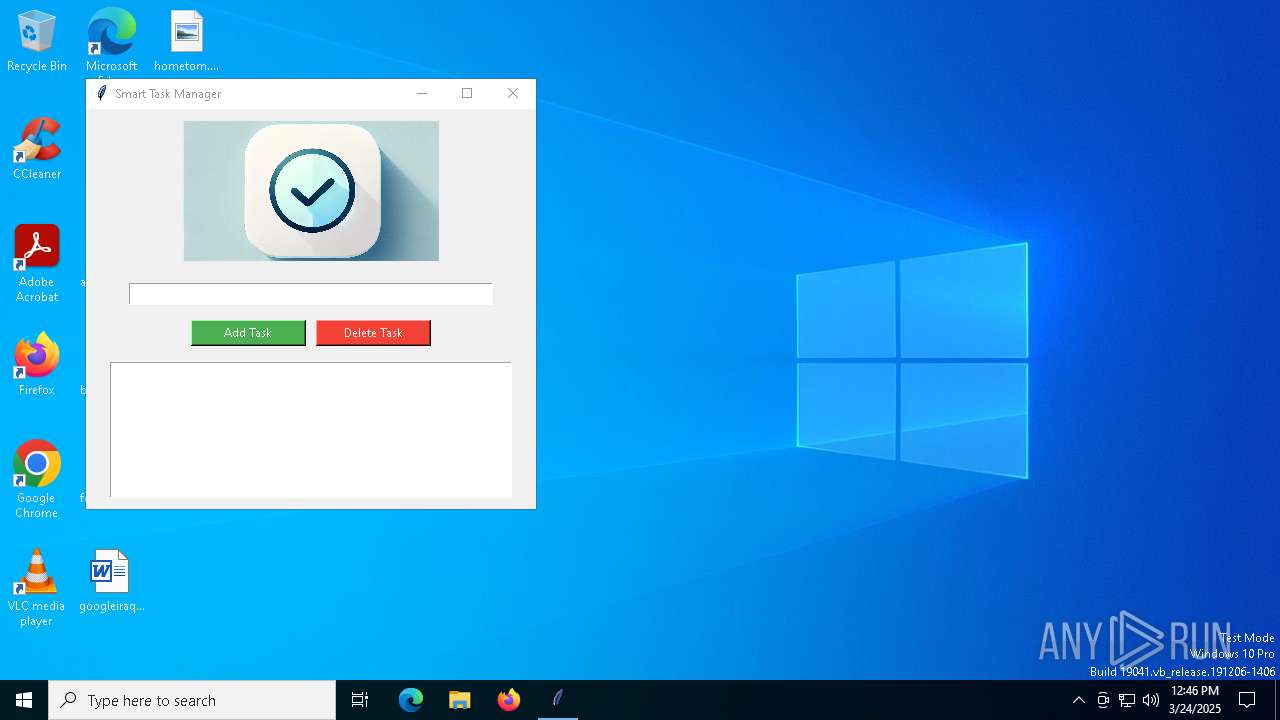
| File name: | todo_app.exe |
| Full analysis: | https://app.any.run/tasks/a8c1f28f-8f06-4269-b82e-cc4d09a3d716 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 12:45:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 9BEAD0499F5A86EF3FD155E19D0A8FA3 |
| SHA1: | BC14B5298A09EA97AA56A4EF165C97ACF96554A2 |
| SHA256: | F133028C1C2954D40F0A8FA45E0766397C7BCDF7758FE532288E0F017BCAF994 |
| SSDEEP: | 196608:G35oG8gKDl2TaMzpdTyYoklNUfkGrCKvgLl9t0:q55HKEZpdTylGNUfkGOK4Rn0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- todo_app.exe (PID: 7776)
- todo_app.exe (PID: 7752)
Process drops legitimate windows executable
- todo_app.exe (PID: 7776)
- todo_app.exe (PID: 7752)
The process drops C-runtime libraries
- todo_app.exe (PID: 7776)
- todo_app.exe (PID: 7752)
Executable content was dropped or overwritten
- todo_app.exe (PID: 7776)
- todo_app.exe (PID: 7752)
Application launched itself
- todo_app.exe (PID: 7776)
Loads Python modules
- todo_app.exe (PID: 1348)
INFO
Reads the computer name
- todo_app.exe (PID: 7776)
Checks supported languages
- todo_app.exe (PID: 7776)
Create files in a temporary directory
- todo_app.exe (PID: 7776)
- todo_app.exe (PID: 7752)
Manual execution by a user
- todo_app.exe (PID: 7752)
The sample compiled with english language support
- todo_app.exe (PID: 7776)
- todo_app.exe (PID: 7752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:22 16:31:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 173568 |
| InitializedDataSize: | 155648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce20 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
134
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Users\admin\Desktop\todo_app.exe" | C:\Users\admin\Desktop\todo_app.exe | — | todo_app.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7752 | "C:\Users\admin\Desktop\todo_app.exe" | C:\Users\admin\Desktop\todo_app.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7776 | "C:\Users\admin\Desktop\todo_app.exe" | C:\Users\admin\Desktop\todo_app.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
179
Read events
179
Write events
0
Delete events
0
Modification events
Executable files
43
Suspicious files
6
Text files
1 774
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_lzma.pyd | executable | |
MD5:3E73BC69EFB418E76D38BE5857A77027 | SHA256:6F48E7EBA363CB67F3465A6C91B5872454B44FC30B82710DFA4A4489270CE95C | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_hashlib.pyd | executable | |
MD5:CF4120BAD9A7F77993DD7A95568D83D7 | SHA256:14765E83996FE6D50AEDC11BB41D7C427A3E846A6A6293A4A46F7EA7E3F14148 | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_queue.pyd | executable | |
MD5:59C05030E47BDE800AD937CCB98802D8 | SHA256:E4956834DF819C1758D17C1C42A152306F7C0EA7B457CA24CE2F6466A6CB1CAA | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\PIL\_imaging.cp313-win_amd64.pyd | executable | |
MD5:A9BB6A0FF7A73BE913412C8A29B76B5F | SHA256:DA0917FB34AE6902818960B9E50F66FA779ED8A4B0D80C7D9D96321AD99122E0 | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_ctypes.pyd | executable | |
MD5:2185849BC0423F6641EE30804F475478 | SHA256:199CD8D7DB743C316771EF7BBF414BA9A9CDAE1F974E90DA6103563B2023538D | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_tcl_data\auto.tcl | text | |
MD5:97EFA9EBE840EA051F9706504C8BD783 | SHA256:08113823951619D659EB03A1F6ACD2F9500E1264795219125A5DF7B83CABCB99 | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_socket.pyd | executable | |
MD5:69C4A9A654CF6D1684B73A431949B333 | SHA256:8DAEFAFF53E6956F5AEA5279A7C71F17D8C63E2B0D54031C3B9E82FCB0FB84DB | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\_ssl.pyd | executable | |
MD5:CE19076F6B62292ED66FD06E5BA67BBA | SHA256:21CA71B2C1766FC68734CB3D1E7C2C0439B86BCFB95E00B367C5FD48C59E617C | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\PIL\_webp.cp313-win_amd64.pyd | executable | |
MD5:F12EB0F075399240E8C42A1584EE16AB | SHA256:EB77C7461AB4120FC0A6FADE67B78A0F96ECE2BD40A1FD314563B9A9F27F50F2 | |||
| 7776 | todo_app.exe | C:\Users\admin\AppData\Local\Temp\_MEI77762\PIL\_imagingmath.cp313-win_amd64.pyd | executable | |
MD5:4CDB59704F5E26DE6F8A1D5B363BAE27 | SHA256:823E8BE2F52CF54FBAA23BD3351EAE476F54749798C6BED0773B5647F408041E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8172 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7312 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8172 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7312 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7312 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |