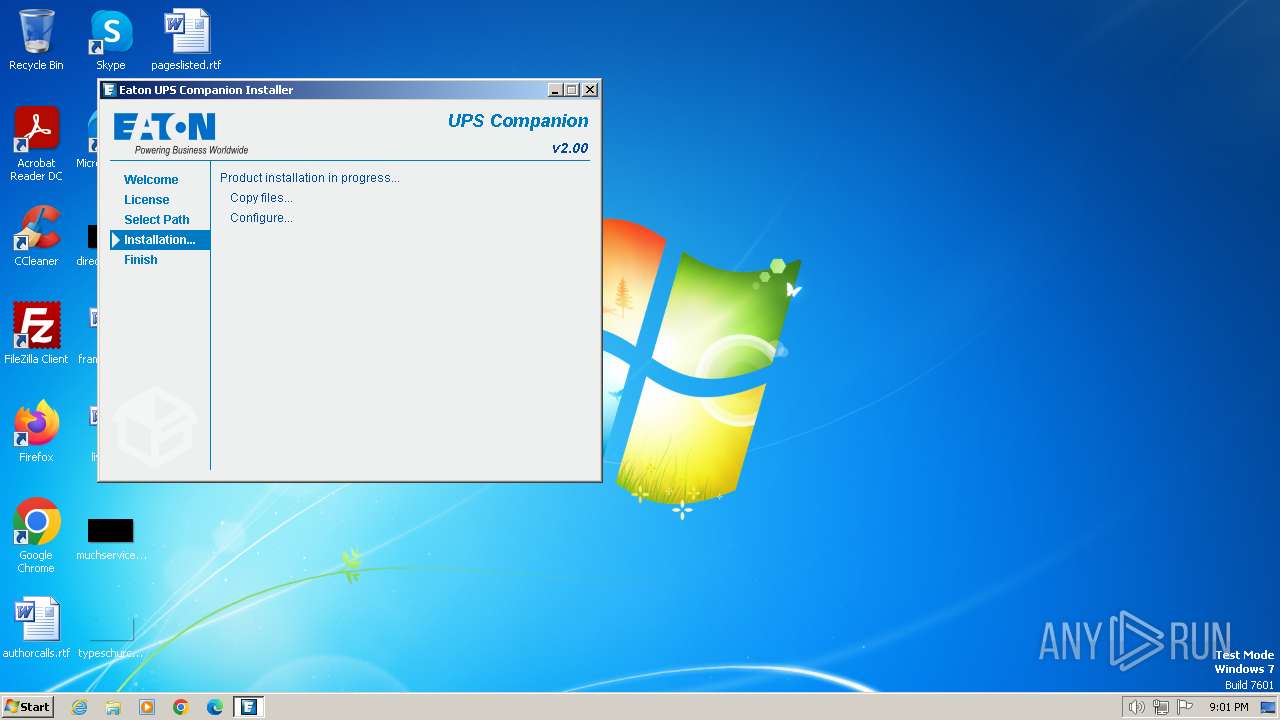
| File name: | euc_win_2_00_025.exe |
| Full analysis: | https://app.any.run/tasks/3dd6de03-c7bd-4898-96ed-8f2ebe3b6069 |
| Verdict: | Malicious activity |
| Analysis date: | January 03, 2024, 21:01:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C148FED94CE37246B536BBCC64F11741 |
| SHA1: | 59335560CECF377387F0D59D4916B50CFE996DA0 |
| SHA256: | F122D237705B1240C3E8E824ABBB110106C228D8DACB091280398C9DDB7B84C7 |
| SSDEEP: | 98304:5aeVqZfXZg+tApvzXkcPBQO3H84ibAESdnlYe/FOCVE97yK8w1n52WtMzdfU+k4G:tYmvA |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 1316)
SUSPICIOUS
Reads the Internet Settings
- euc_win_2_00_025.exe (PID: 116)
- euc_win_2_00_025.exe (PID: 548)
- mc2.exe (PID: 2560)
Drops a system driver (possible attempt to evade defenses)
- euc_win_2_00_025.exe (PID: 548)
- drvinst.exe (PID: 1316)
- setusb32.exe (PID: 572)
Uses REG/REGEDIT.EXE to modify registry
- euc_win_2_00_025.exe (PID: 548)
Creates files in the driver directory
- drvinst.exe (PID: 1316)
Checks Windows Trust Settings
- drvinst.exe (PID: 1316)
Reads Internet Explorer settings
- mc2.exe (PID: 2560)
Reads Microsoft Outlook installation path
- mc2.exe (PID: 2560)
INFO
Checks supported languages
- euc_win_2_00_025.exe (PID: 116)
- euc_win_2_00_025.exe (PID: 548)
- setusb32.exe (PID: 572)
- drvinst.exe (PID: 1316)
- mc2.exe (PID: 2468)
- mc2.exe (PID: 148)
- mc2.exe (PID: 2560)
Application launched itself
- euc_win_2_00_025.exe (PID: 116)
Reads the computer name
- euc_win_2_00_025.exe (PID: 116)
- euc_win_2_00_025.exe (PID: 548)
- setusb32.exe (PID: 572)
- drvinst.exe (PID: 1316)
- mc2.exe (PID: 2468)
- mc2.exe (PID: 148)
- mc2.exe (PID: 2560)
Drops the executable file immediately after the start
- euc_win_2_00_025.exe (PID: 116)
- euc_win_2_00_025.exe (PID: 548)
- setusb32.exe (PID: 572)
- drvinst.exe (PID: 1316)
Create files in a temporary directory
- euc_win_2_00_025.exe (PID: 116)
- euc_win_2_00_025.exe (PID: 548)
- setusb32.exe (PID: 572)
Creates files in the program directory
- euc_win_2_00_025.exe (PID: 548)
- mc2.exe (PID: 2468)
- mc2.exe (PID: 148)
Checks proxy server information
- euc_win_2_00_025.exe (PID: 548)
- mc2.exe (PID: 2560)
Reads the machine GUID from the registry
- setusb32.exe (PID: 572)
- drvinst.exe (PID: 1316)
- mc2.exe (PID: 2560)
Executes as Windows Service
- VSSVC.exe (PID: 1576)
- mc2.exe (PID: 148)
Starts itself from another location
- euc_win_2_00_025.exe (PID: 548)
Creates files or folders in the user directory
- mc2.exe (PID: 2560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:02:05 11:19:34+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 695808 |
| InitializedDataSize: | 329216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x81020 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
47
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\euc_win_2_00_025.exe" | C:\Users\admin\AppData\Local\Temp\euc_win_2_00_025.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 148 | "C:\Program Files\Eaton\UPSCompanion\mc2.exe" | C:\Program Files\Eaton\UPSCompanion\mc2.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Temp\euc_win_2_00_025.exe" -runas | C:\Users\admin\AppData\Local\Temp\euc_win_2_00_025.exe | euc_win_2_00_025.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 572 | bin\setusb32.exe -install bin\etn_libusb0.inf | C:\Program Files\Eaton\UPSCompanion\bin\setusb32.exe | — | euc_win_2_00_025.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1316 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{1e429df0-c19a-0029-83ce-d47ff09d421e}\etn_libusb0.inf" "0" "6a2a5eda3" "00000574" "WinSta0\Default" "00000338" "208" "C:\Program Files\Eaton\UPSCompanion\bin" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | regedit.exe /s bin\etn_ca.reg | C:\Windows\regedit.exe | — | euc_win_2_00_025.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Eaton\UPSCompanion\mc2.exe" -systray | C:\Program Files\Eaton\UPSCompanion\mc2.exe | — | euc_win_2_00_025.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2560 | "C:\Program Files\Eaton\UPSCompanion\mc2.exe" -open | C:\Program Files\Eaton\UPSCompanion\mc2.exe | — | euc_win_2_00_025.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
6 656
Read events
6 583
Write events
73
Delete events
0
Modification events
| (PID) Process: | (116) euc_win_2_00_025.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) euc_win_2_00_025.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) euc_win_2_00_025.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) euc_win_2_00_025.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (572) setusb32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1316) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1316) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1316) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1316) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 73 | |||
| (PID) Process: | (1316) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008543C5D72FB0D90164030000840D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
24
Suspicious files
30
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\install.log | text | |
MD5:E042BC3E57C0CD1BE47D40785B7AE2DE | SHA256:313B4AC46EA4D51F323FDE222B7B803CC89EED2A8FCA242C549FCFEE16EEE6FE | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\musb.dll | executable | |
MD5:AF6A4656DECAC129337E0AD0EABD10D0 | SHA256:7771EB19766F74652D3ED6E9FD852BE87800355B2401D5B6DC6DC7AF9D1832ED | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\etn_libusb0_x64.cat | binary | |
MD5:DC40F1C356DBDDFEE1E182114E3DB0B5 | SHA256:2F0F636FB4EEE2399ACEBBFB516D160899C439A116D5C781FF78966458B33022 | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\libusb0.sys | executable | |
MD5:6918B62F73A2AA6AC5B01870C2EE4DD3 | SHA256:39FD4912405F63D2DB1971FA8BF746F407635EDB1C5E3D2AE4D9CE97D46F5E1A | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\mwidget.dll | executable | |
MD5:C3D08DEAF14A04CB938451D26646F11C | SHA256:1DCDCB18586A5F3672F1181B77E5A85DEC6A9B41F28D071366D5A7C44CEBDFEE | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\etn_libusb0.cat | binary | |
MD5:876899EFC56E86912FEE64634E4BDE91 | SHA256:7667B2571DC50264E05FC8C5425D0709111E68704062D748AC26D0444D804B83 | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\msocket.dll | executable | |
MD5:AD329BE27AB7F1D871712F8E506FEA8B | SHA256:D05C89E9FAA2984F7790DF6D72AAD942FDFAE78990FC35E4CDA4A3C4318595AB | |||
| 548 | euc_win_2_00_025.exe | C:\Users\admin\AppData\Local\Temp\emc2Install\bin\mserial.dll | executable | |
MD5:E409F37D00C148F5562891A555B5C5A2 | SHA256:3A9BD87FA1CB1459EF66C09E1EDA95CFF76A51CA204511A0EB2B8AD08D8E997C | |||
| 548 | euc_win_2_00_025.exe | C:\Program Files\Eaton\UPSCompanion\bin\mserial.dll | executable | |
MD5:E409F37D00C148F5562891A555B5C5A2 | SHA256:3A9BD87FA1CB1459EF66C09E1EDA95CFF76A51CA204511A0EB2B8AD08D8E997C | |||
| 548 | euc_win_2_00_025.exe | C:\Program Files\Eaton\UPSCompanion\bin\libusb0.dll | executable | |
MD5:535779909A40B42F4F3E48598F5778A5 | SHA256:00CACA07869B19D10B370552AC7CC2F6F2EE246FC15DB11650F6CD3F4EF9B666 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pqsoftware.eaton.com |
| unknown |