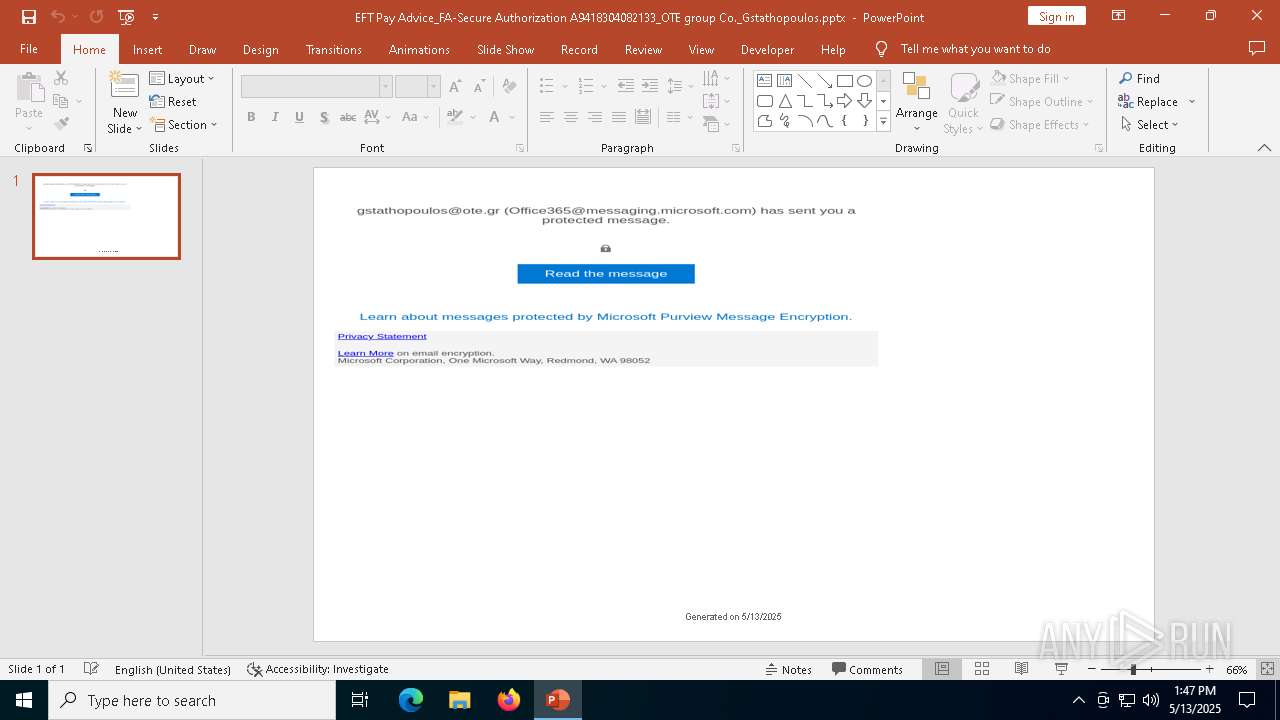
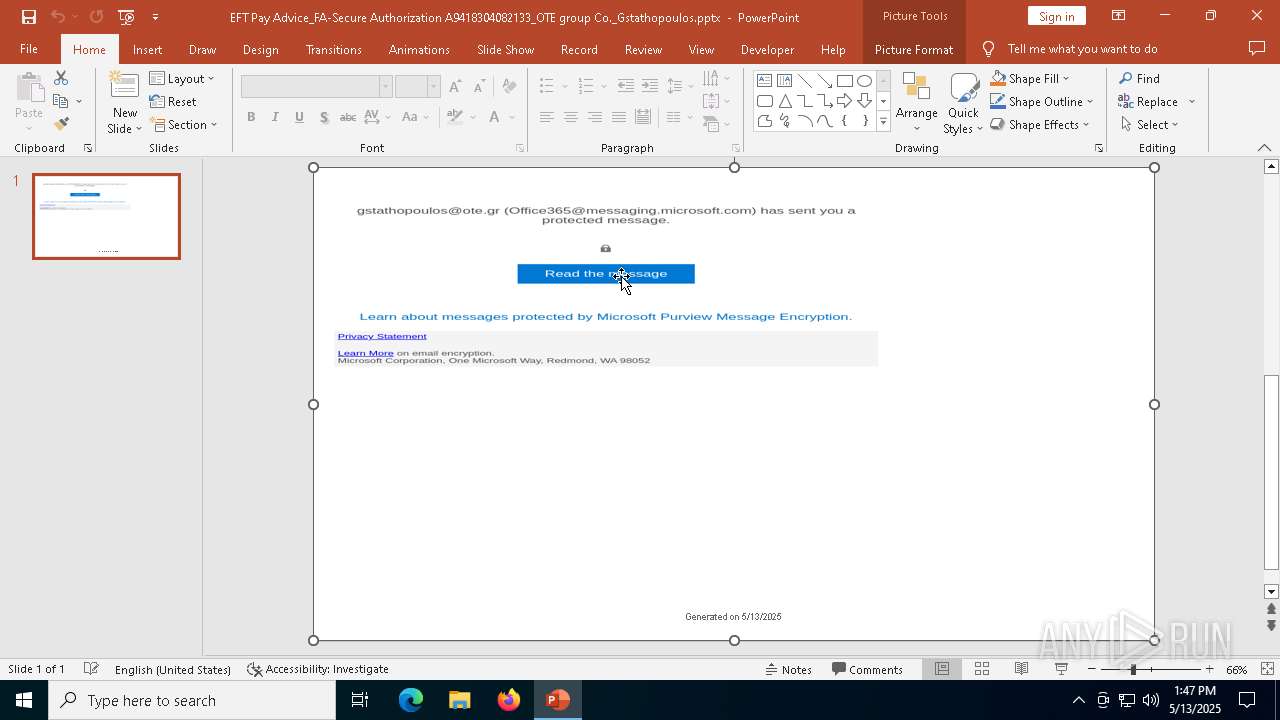
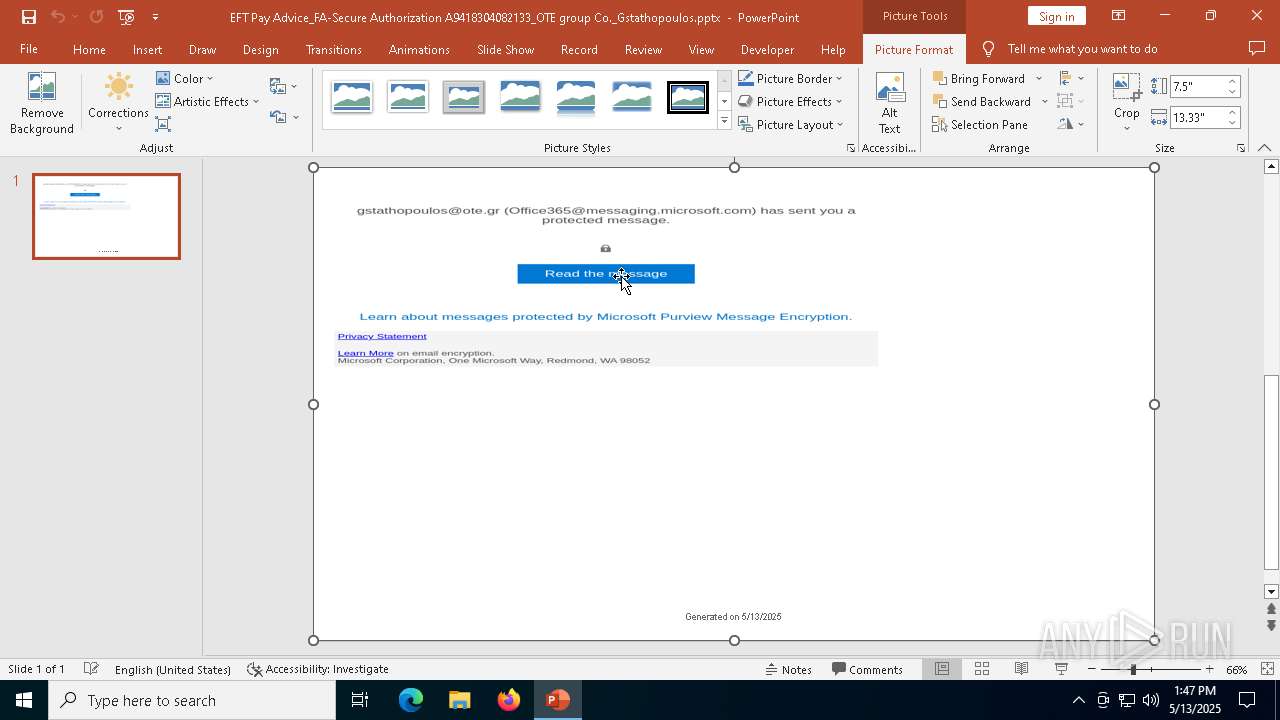
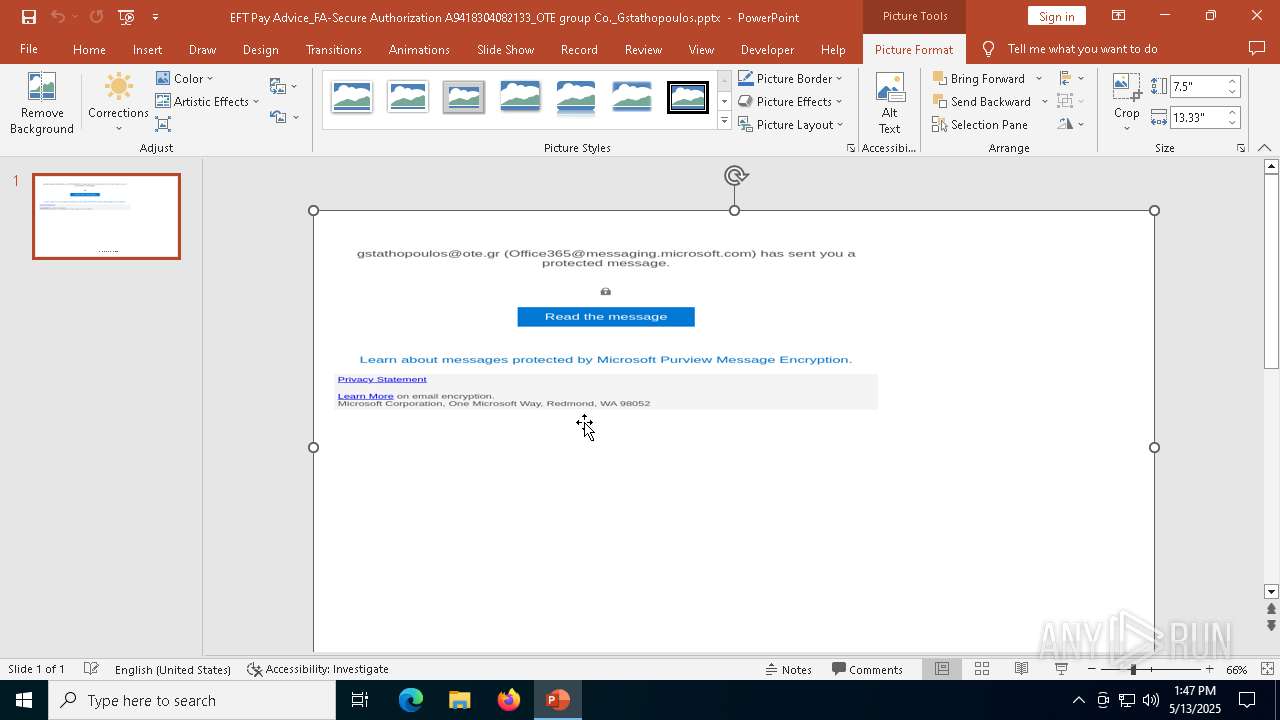
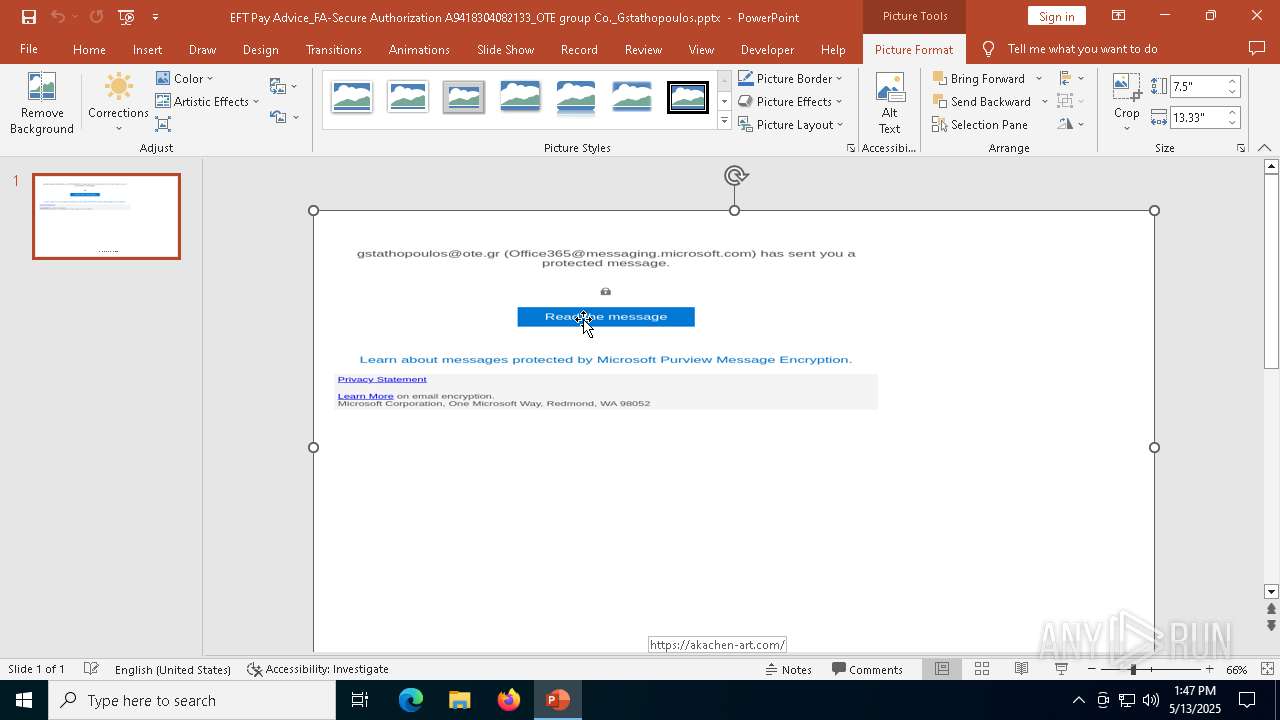
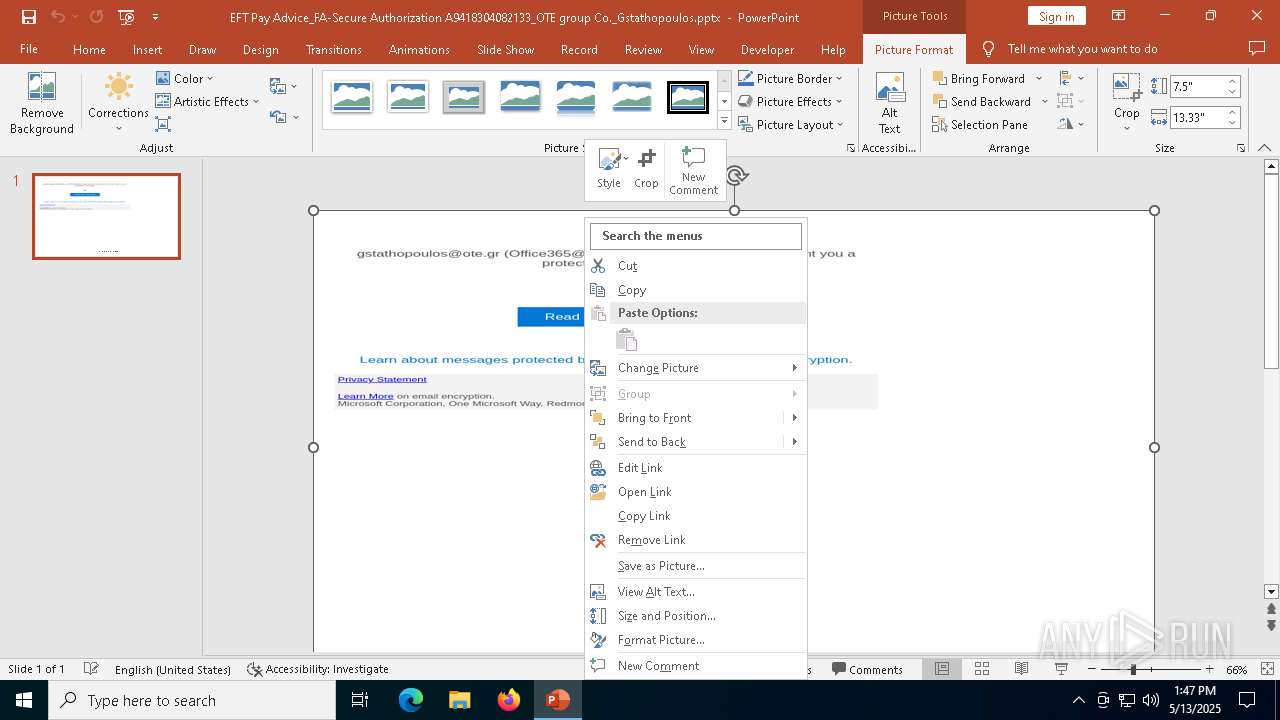
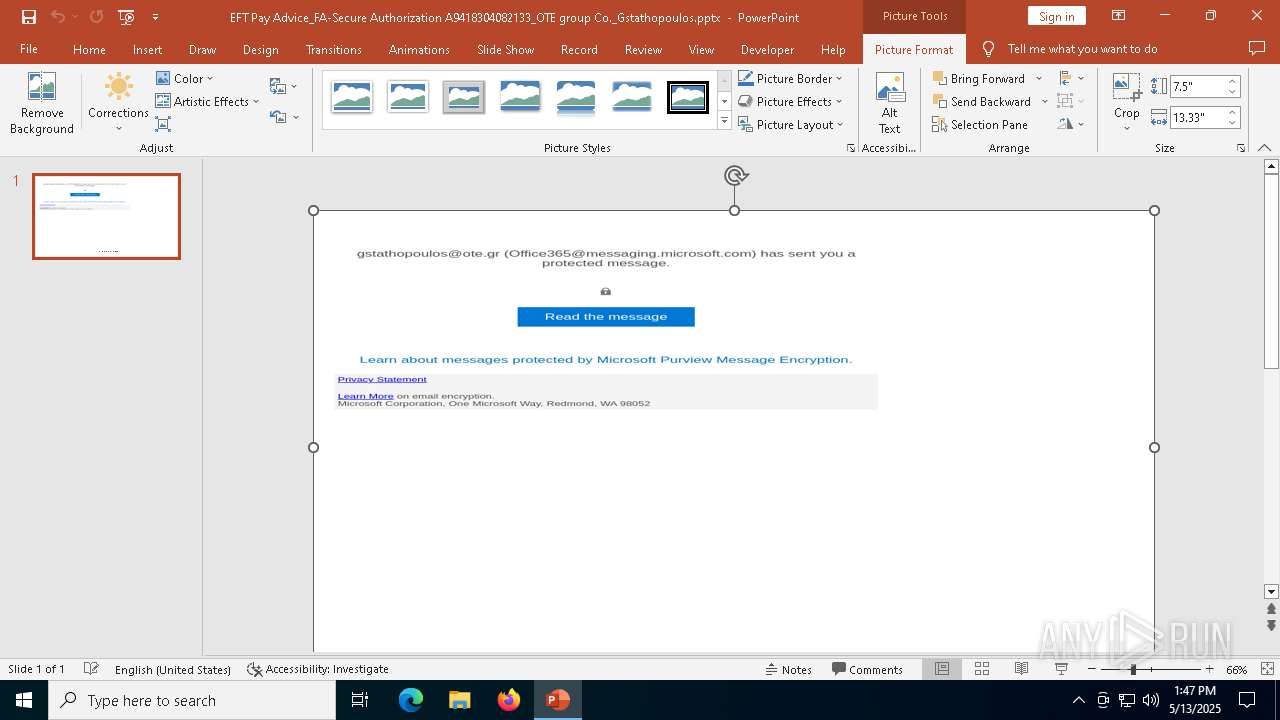
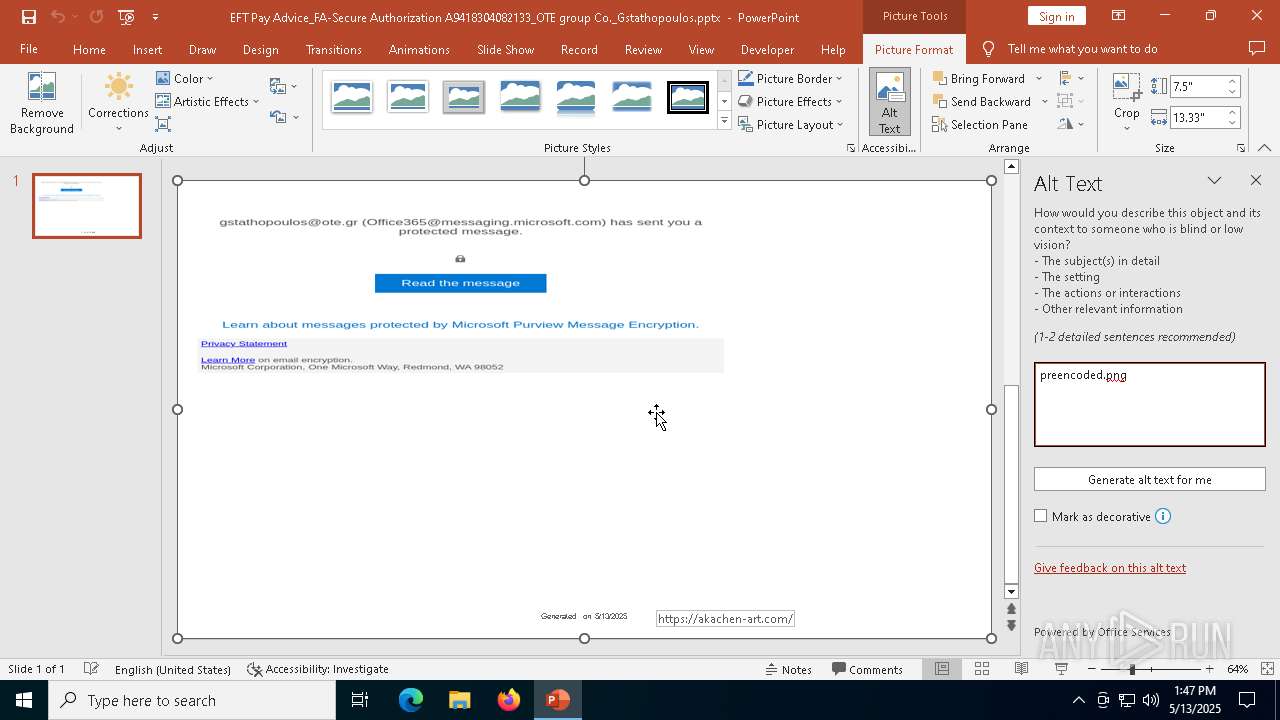
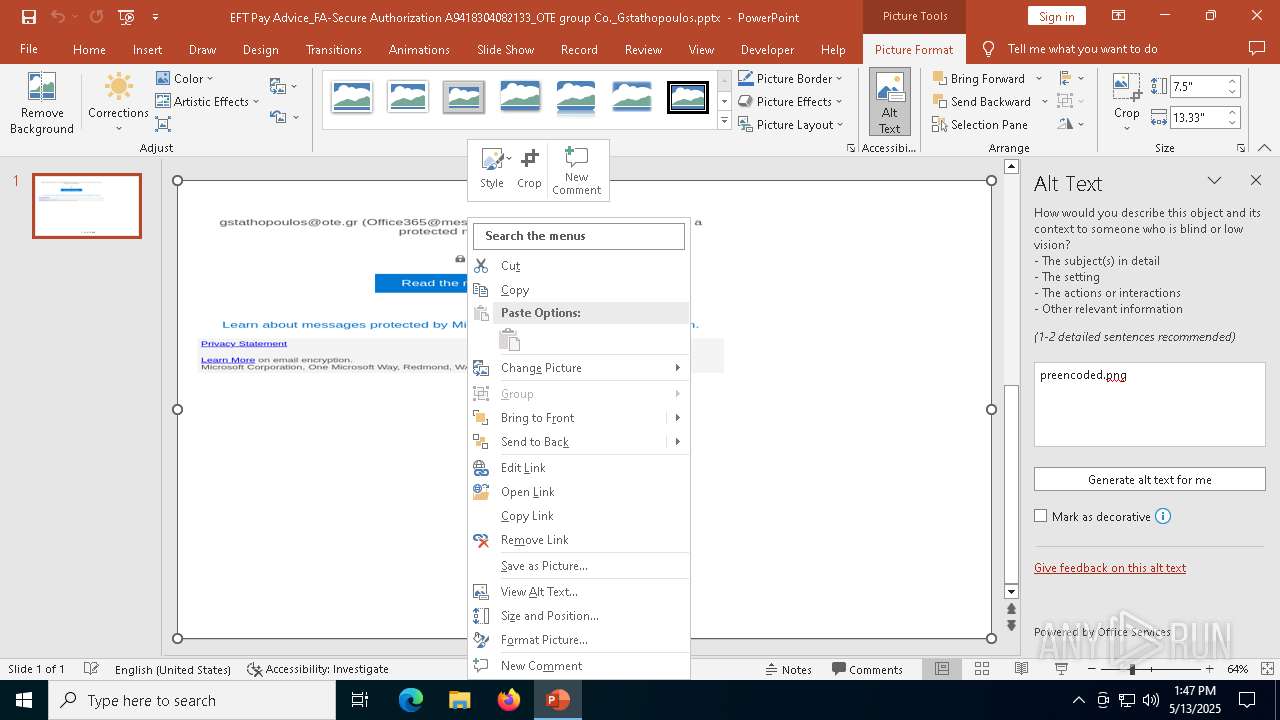
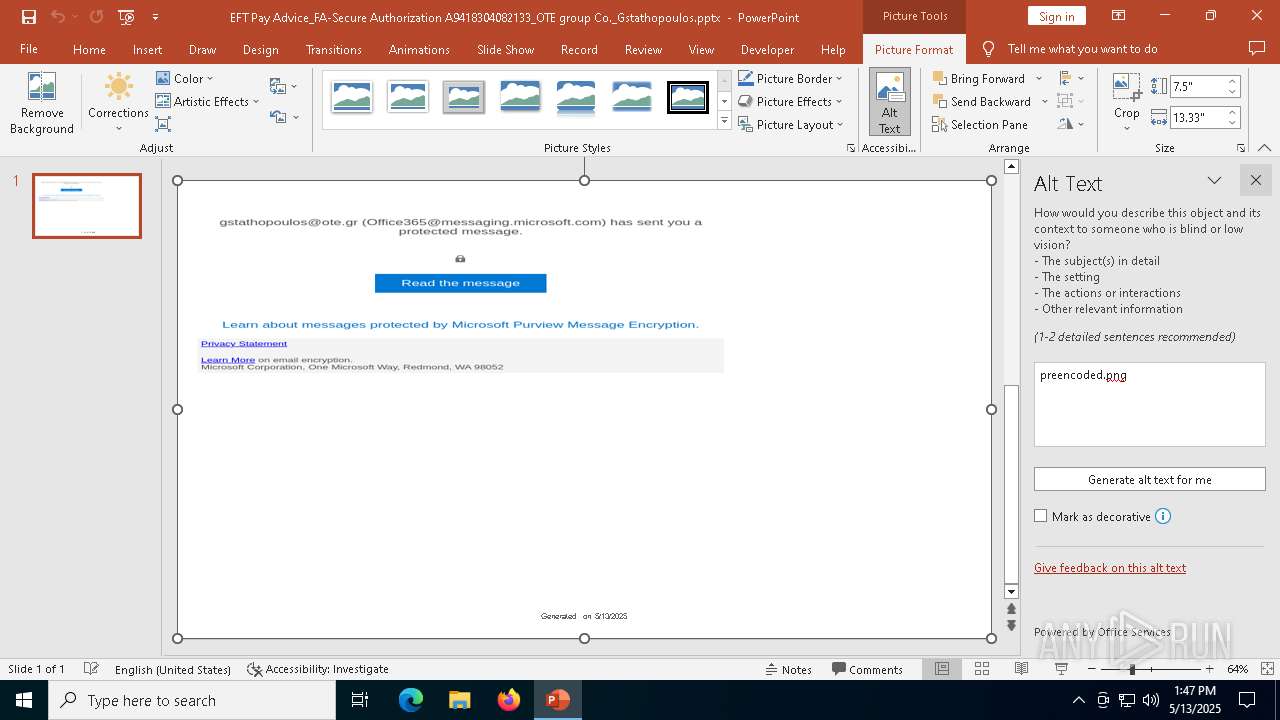
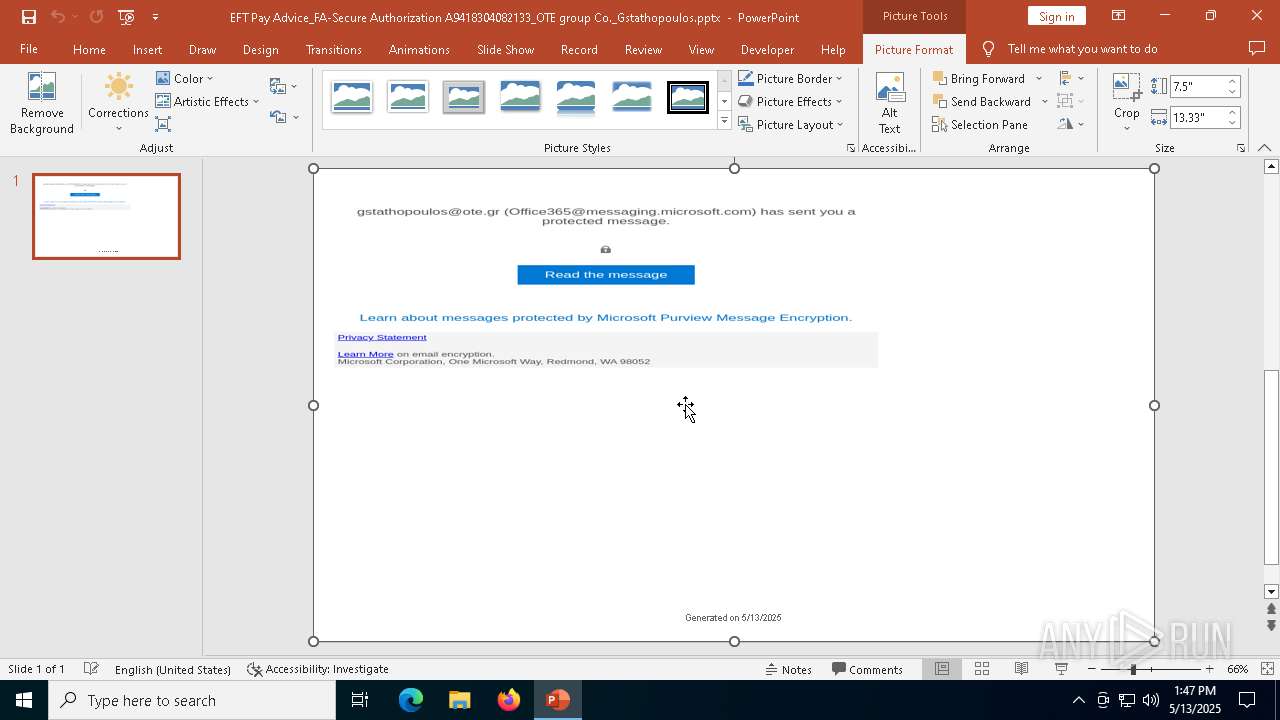
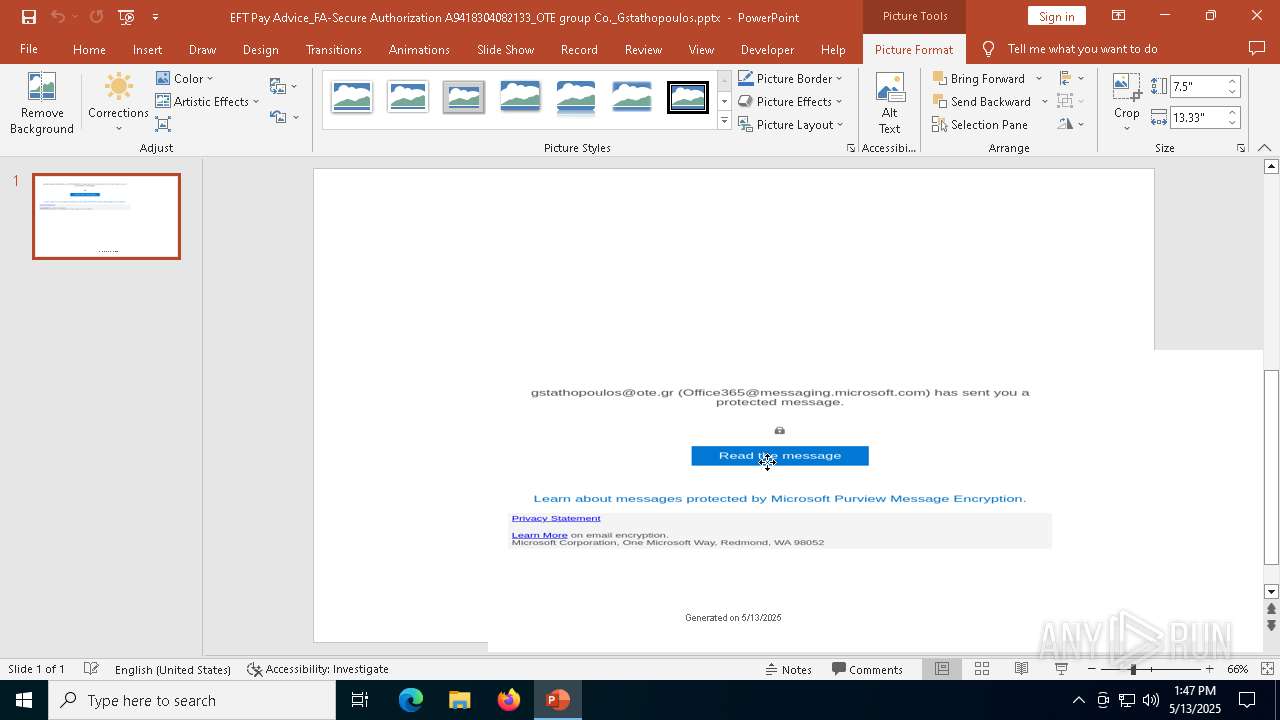
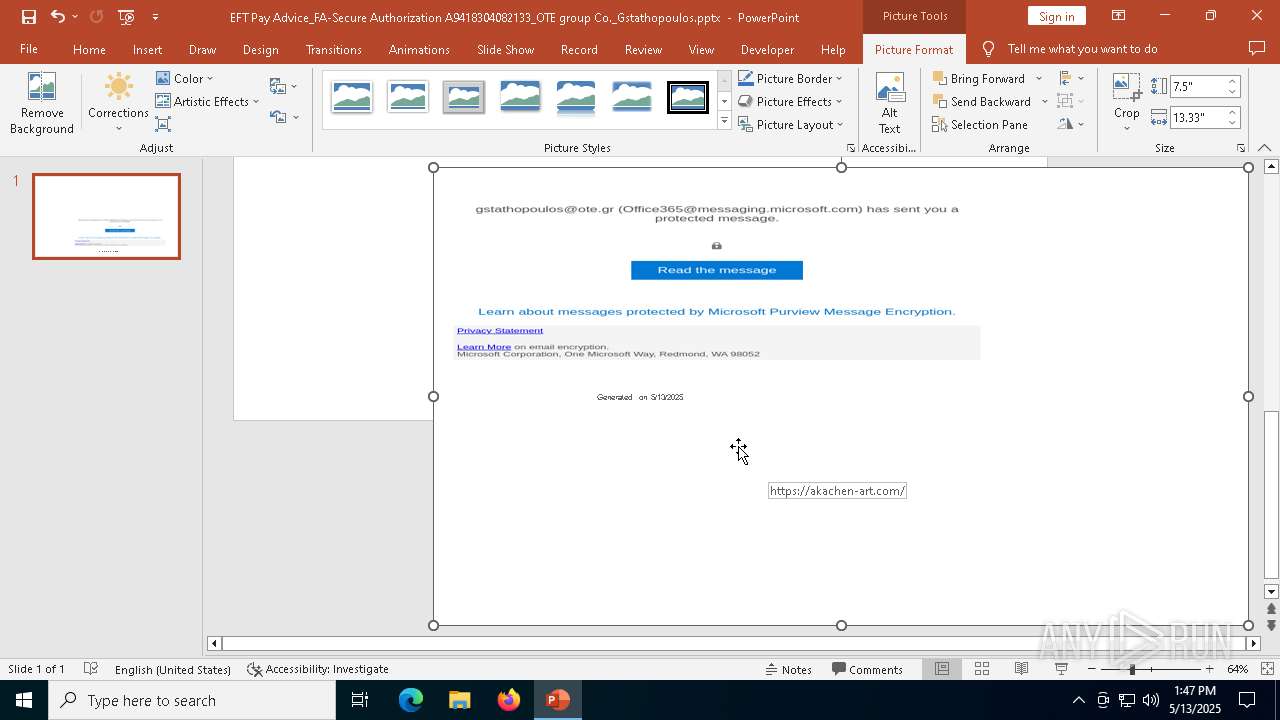
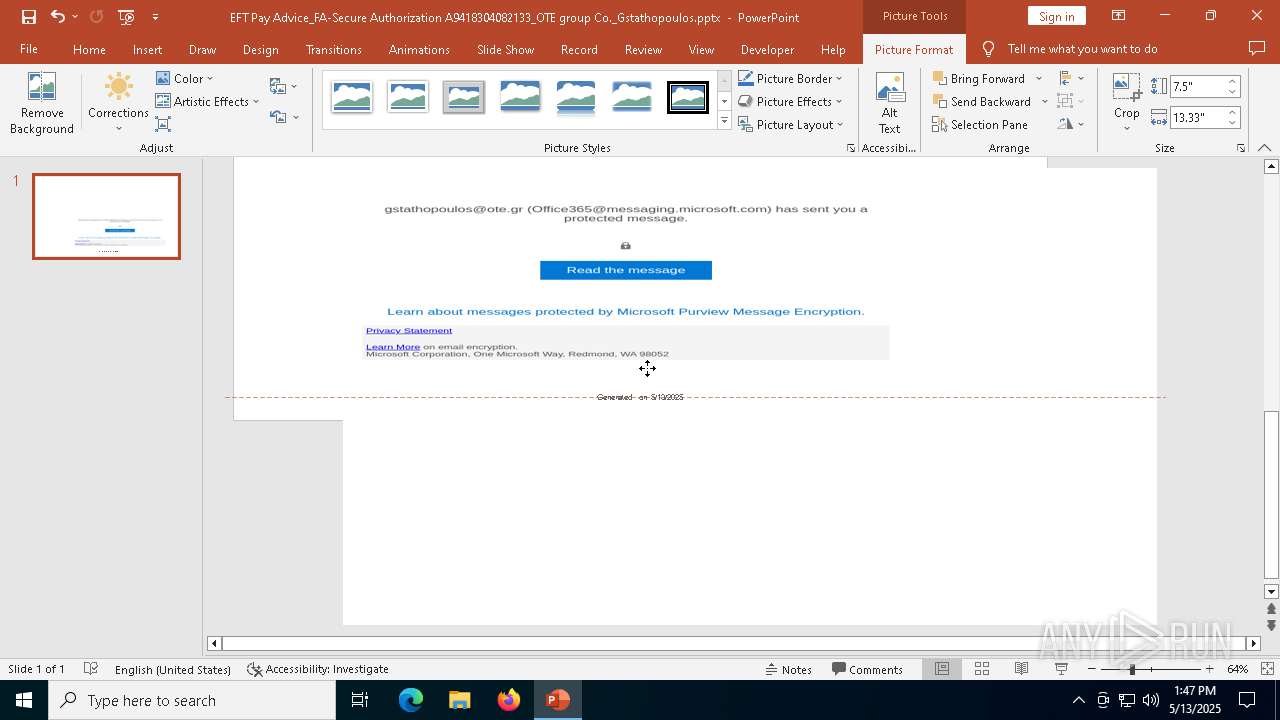
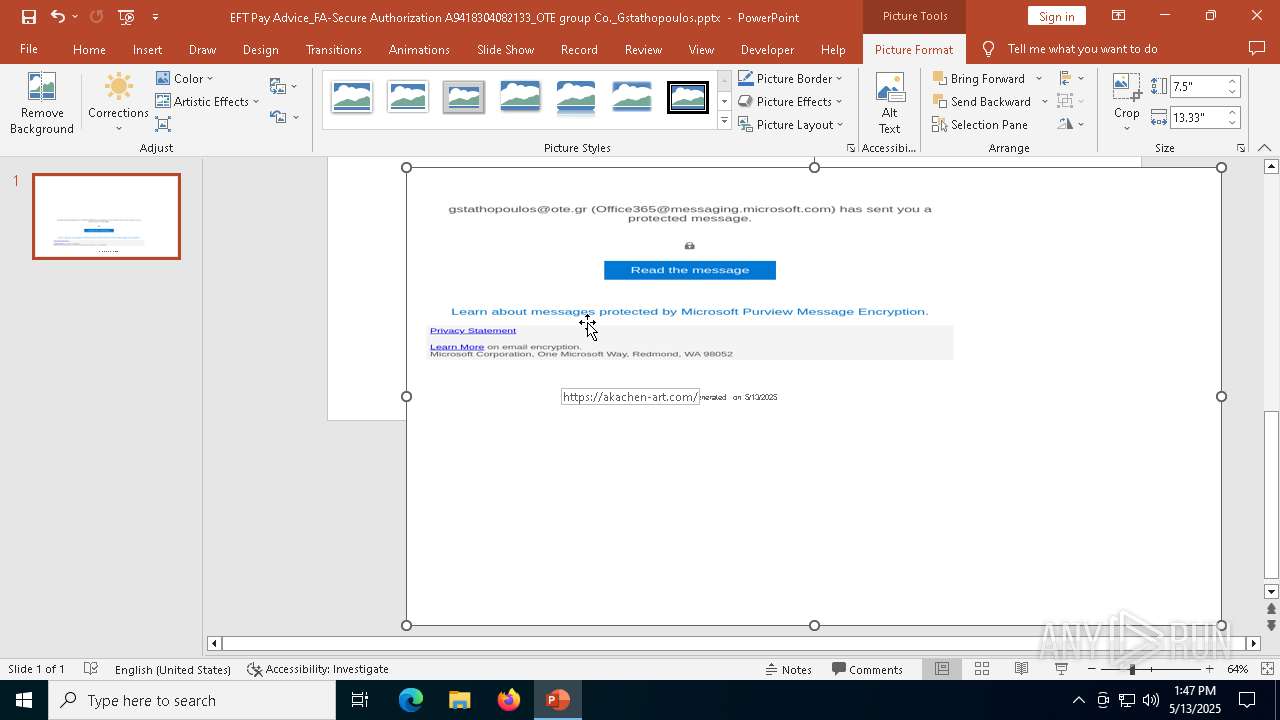
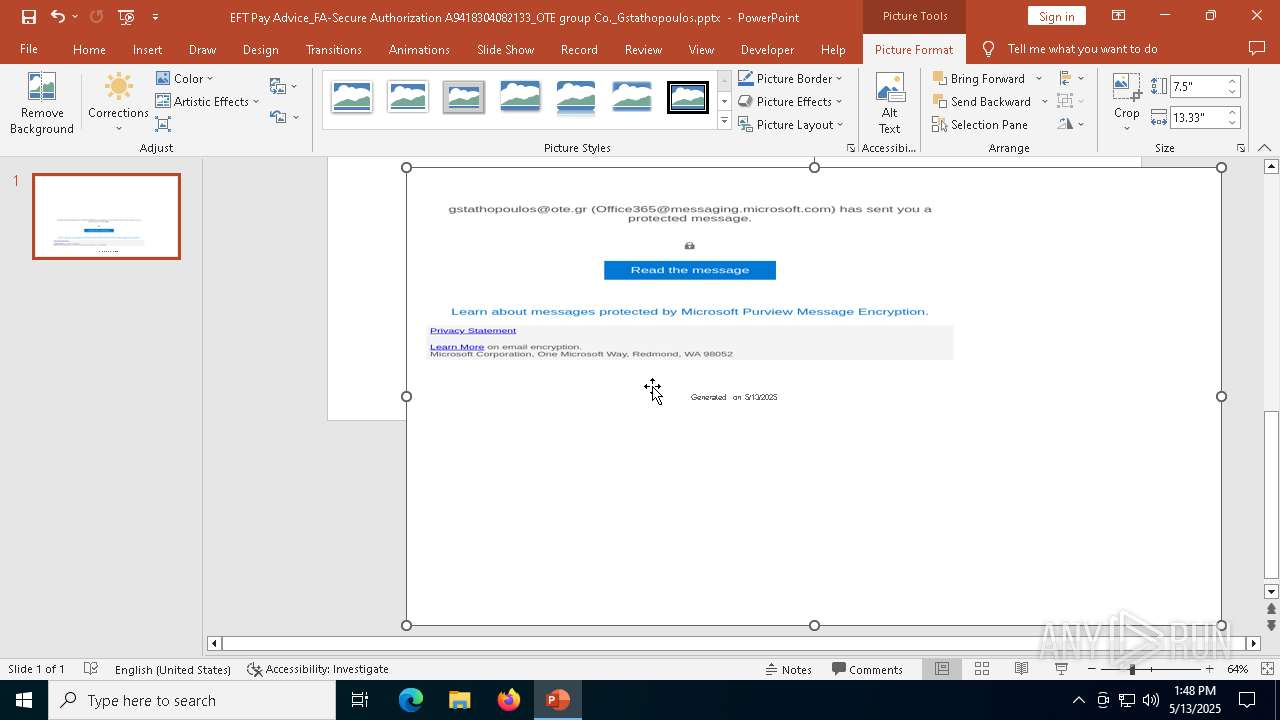
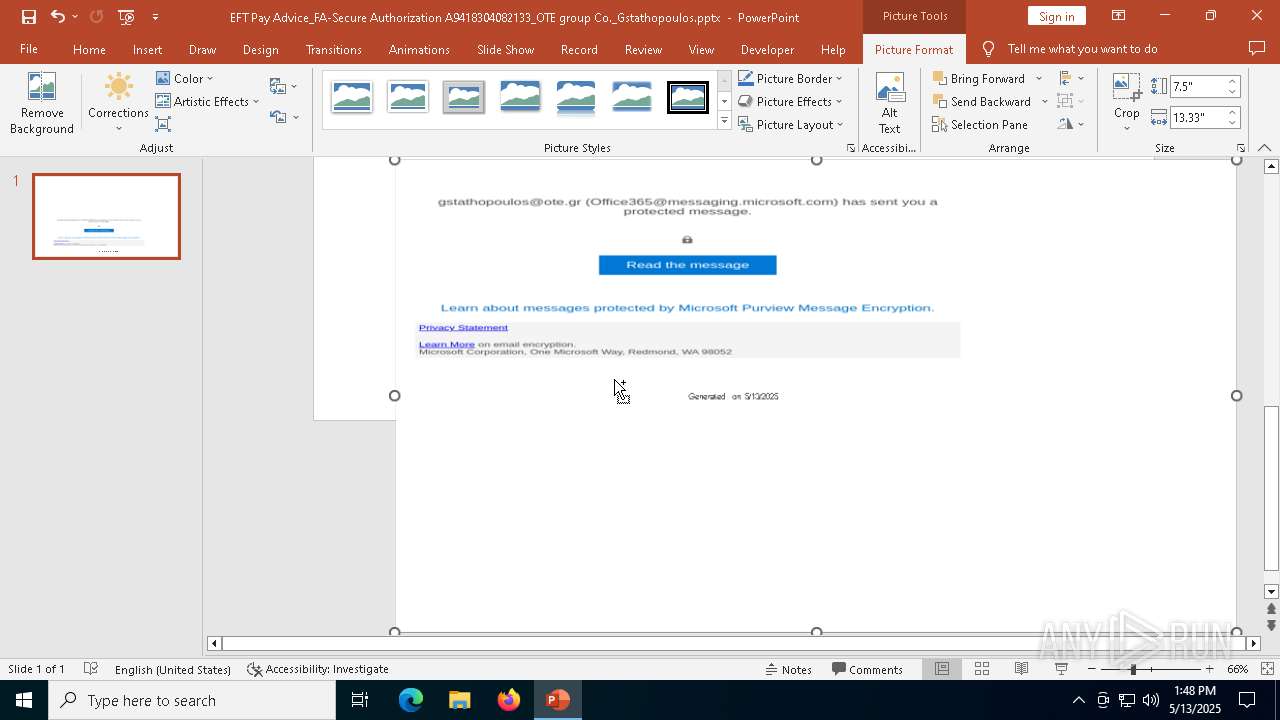
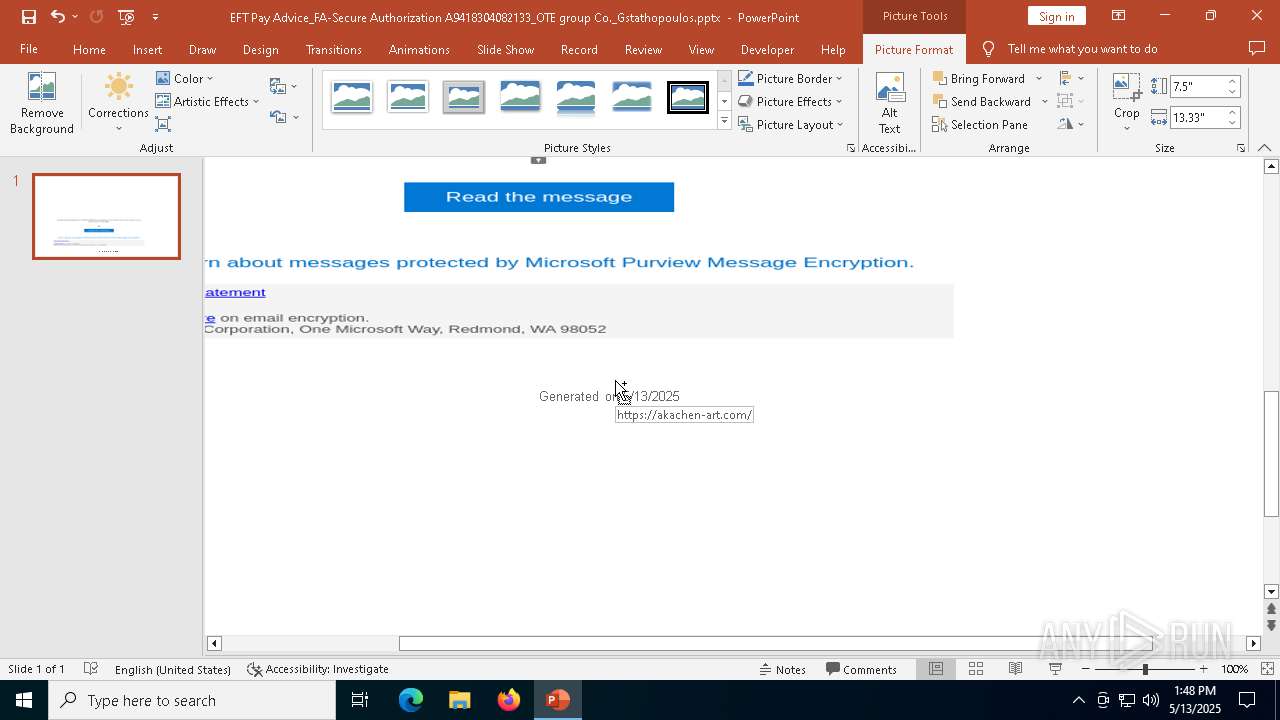
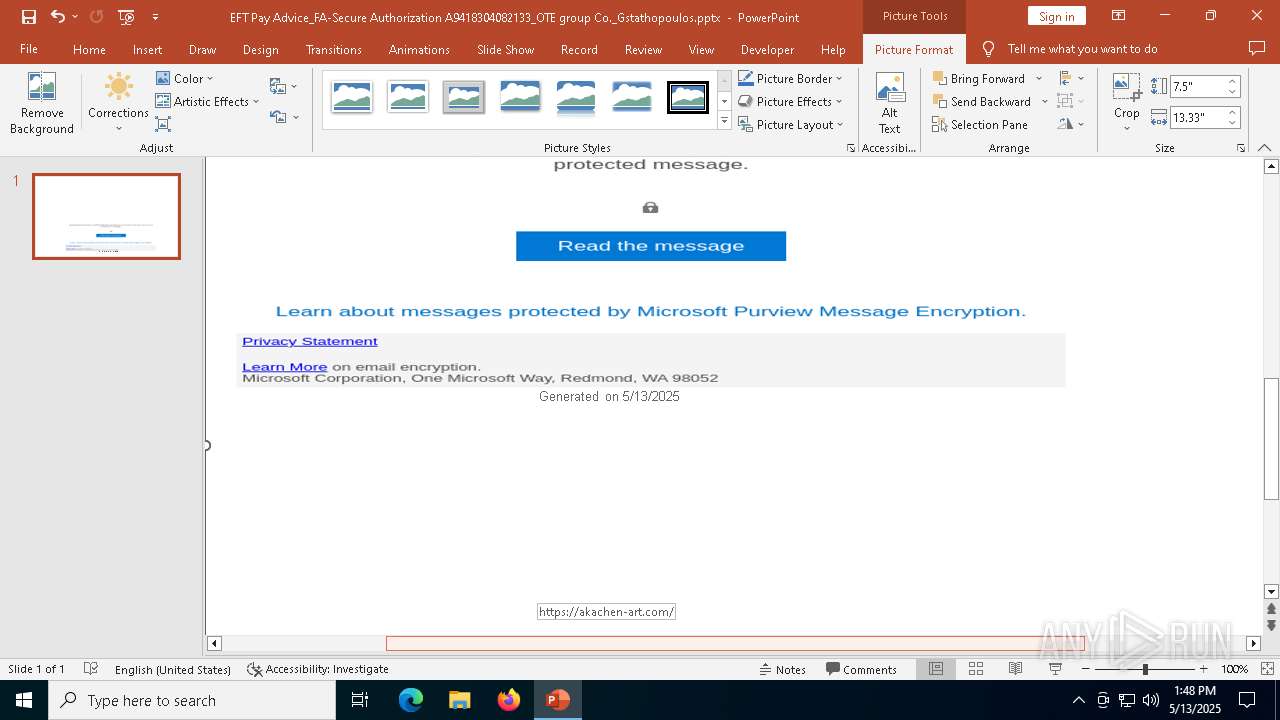
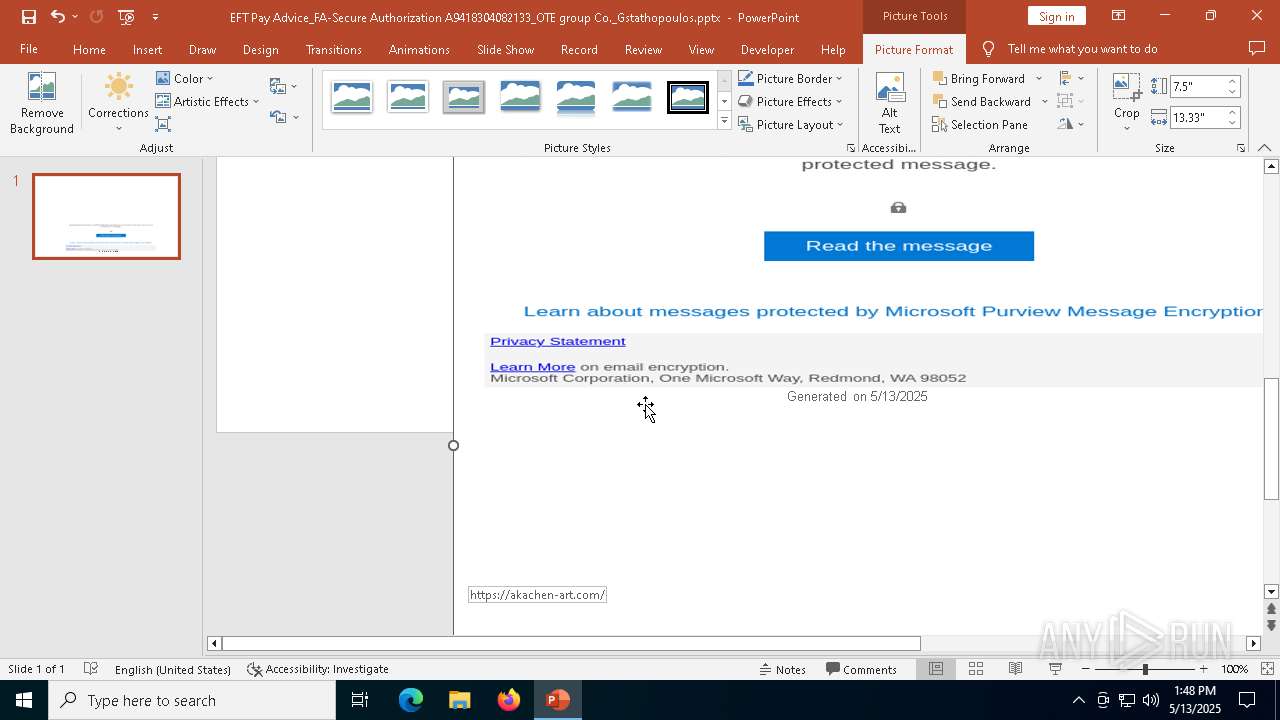
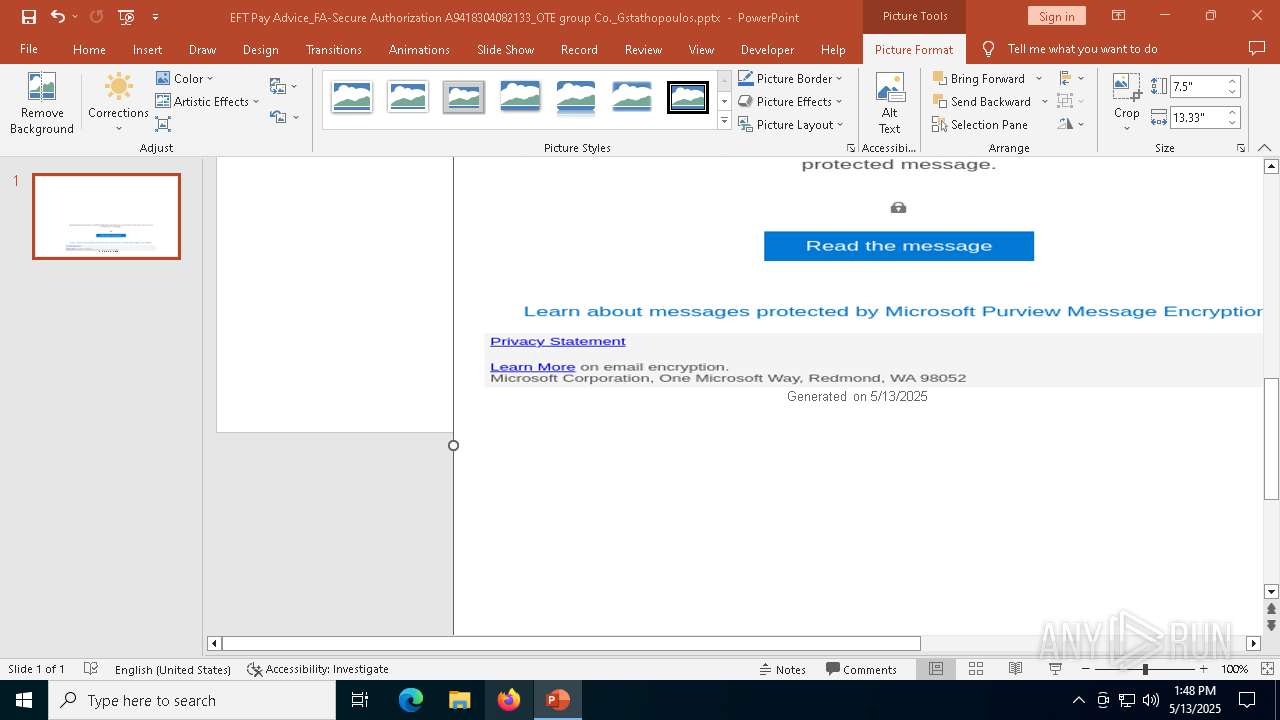
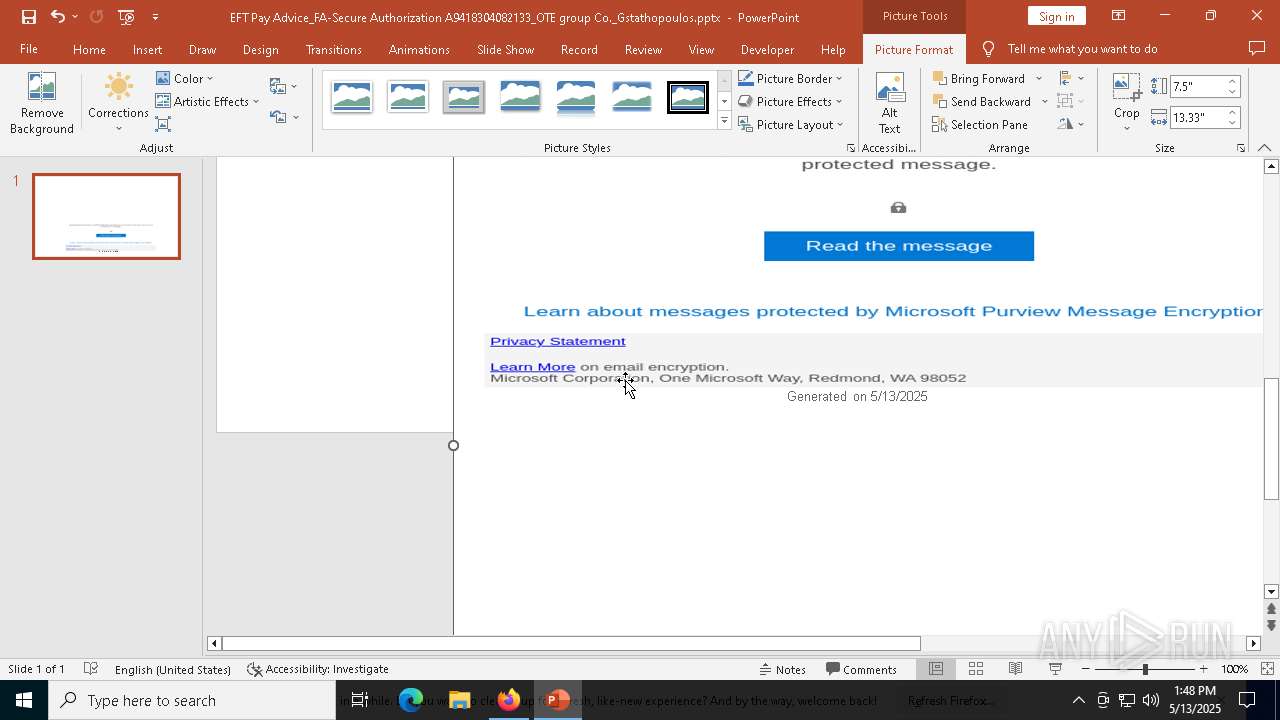
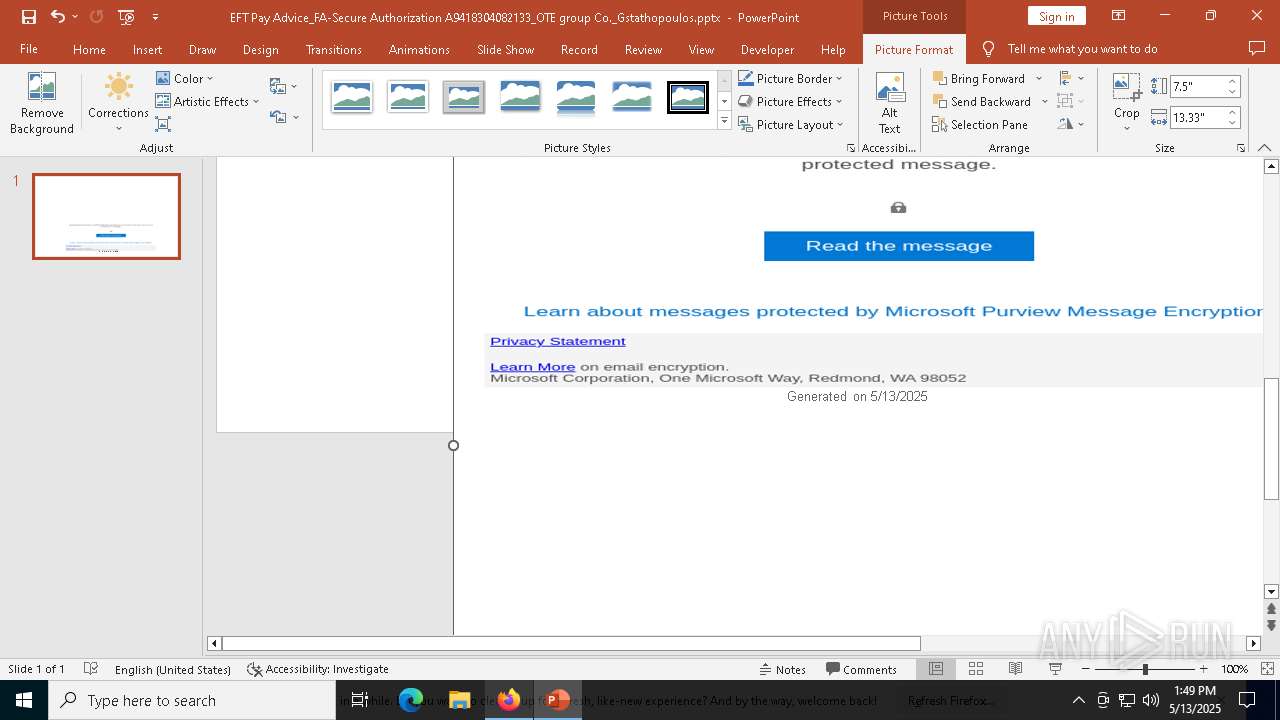
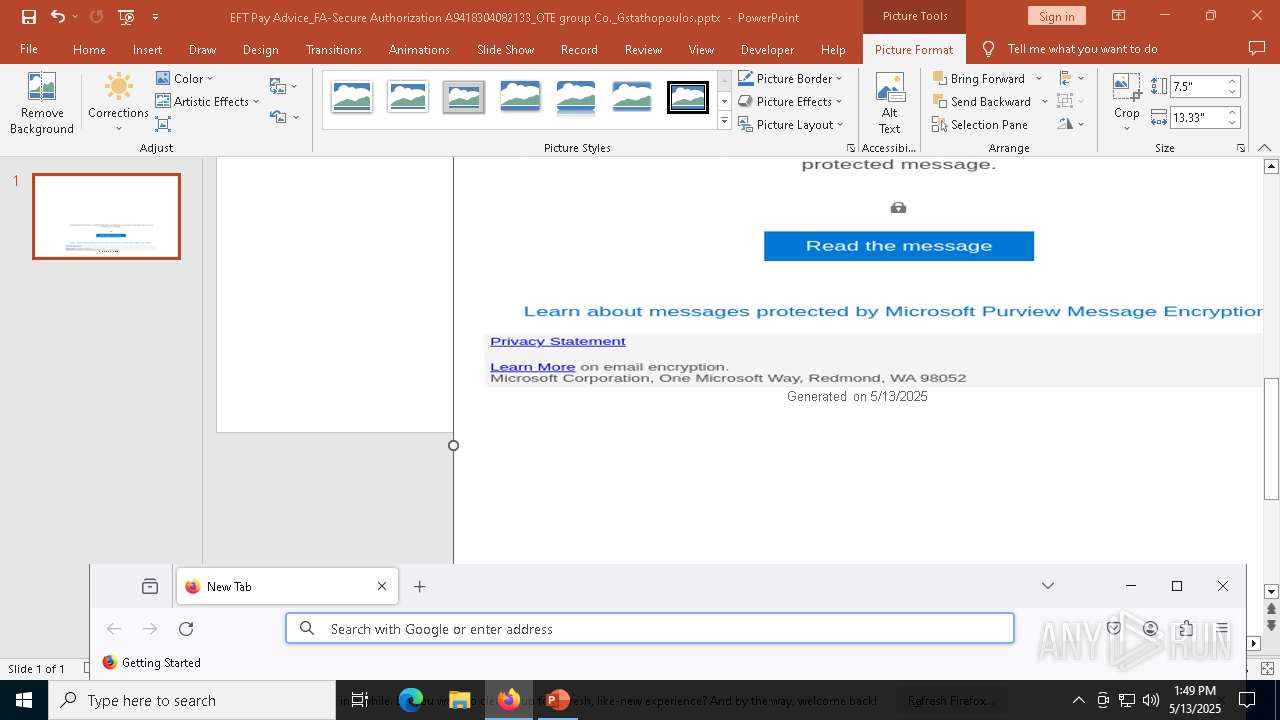
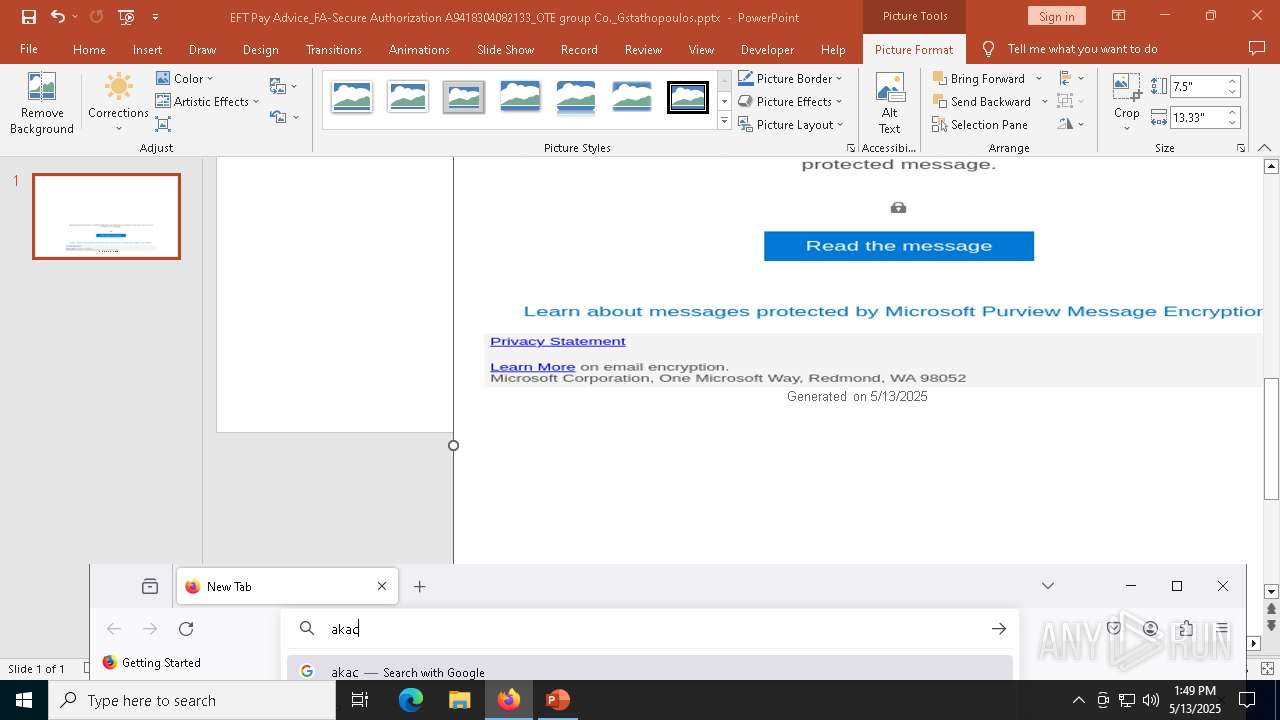
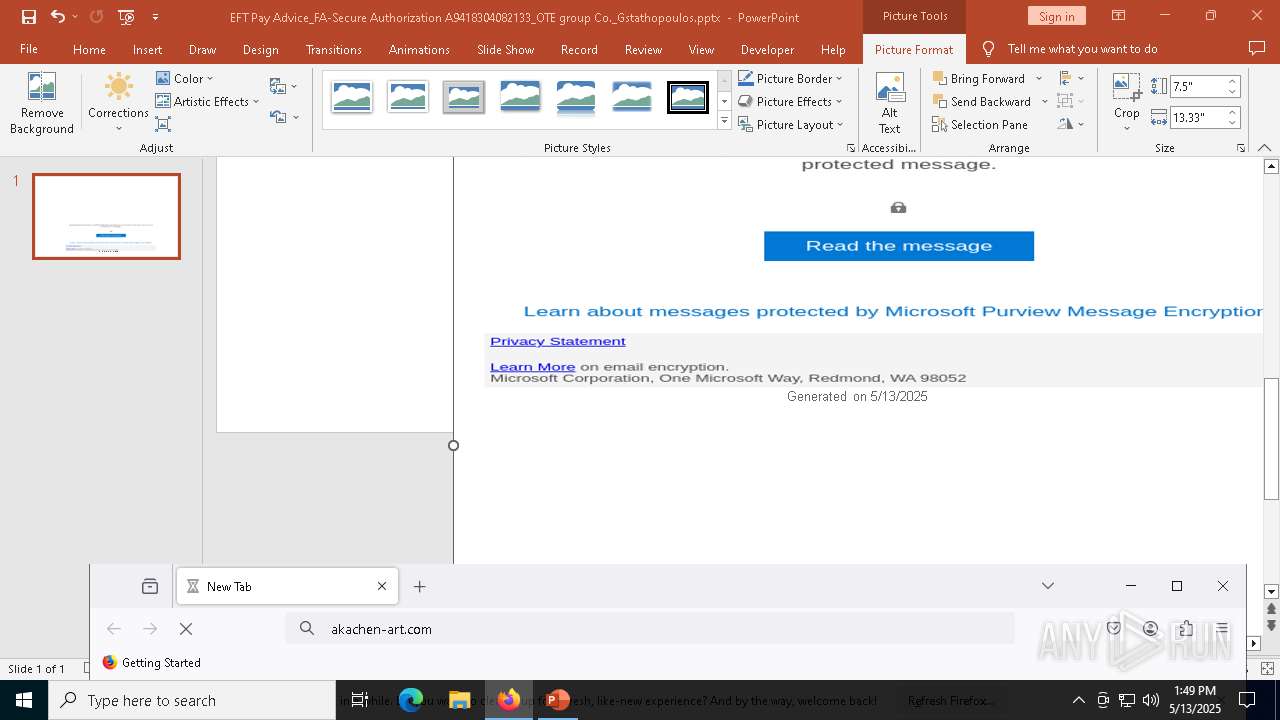
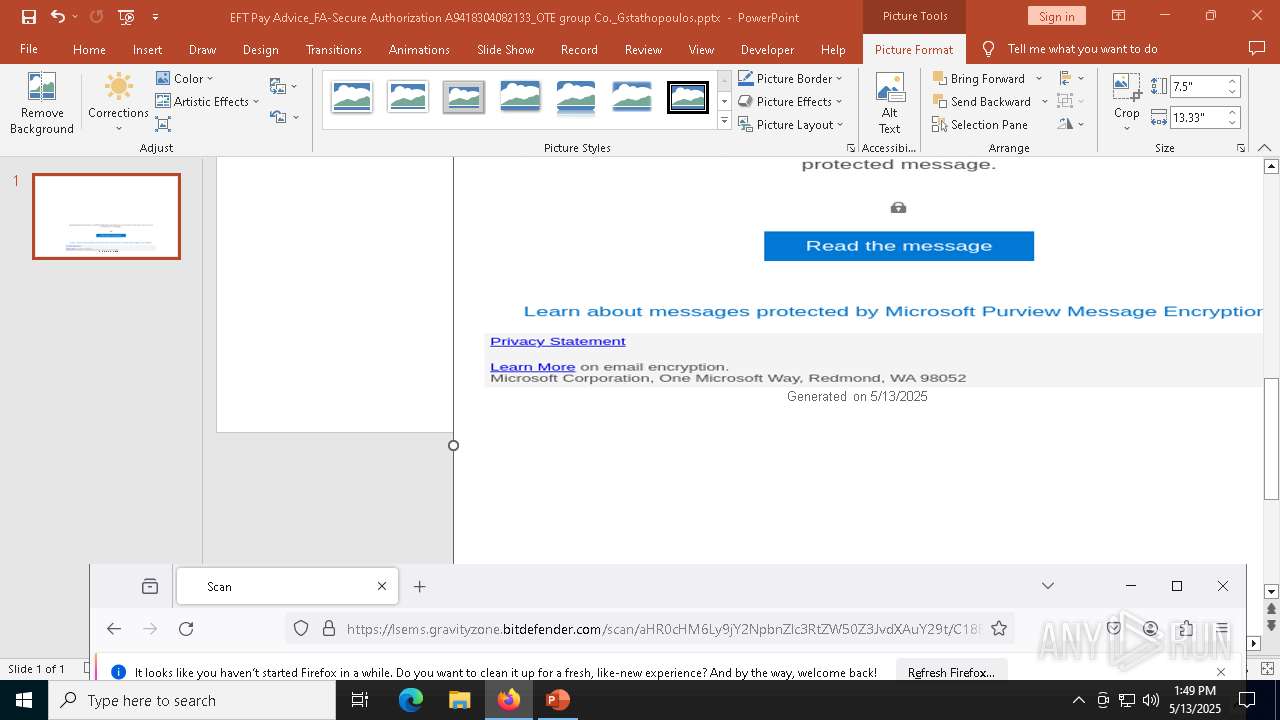
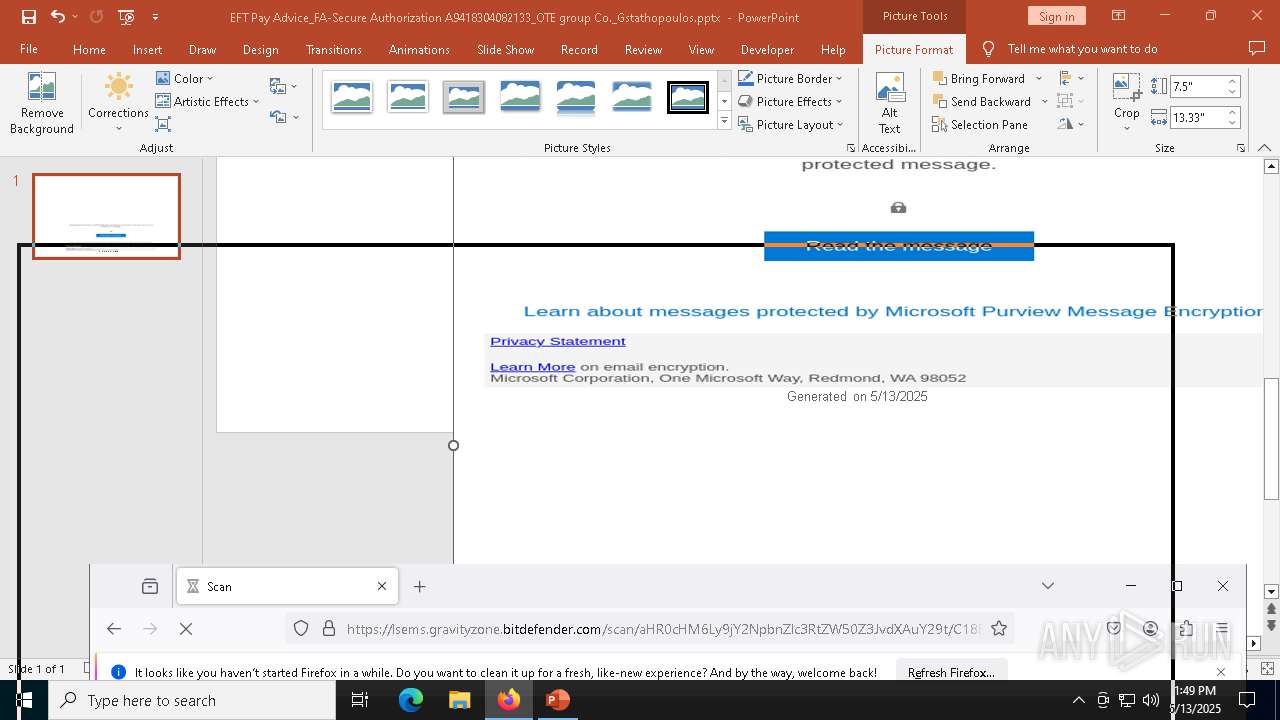
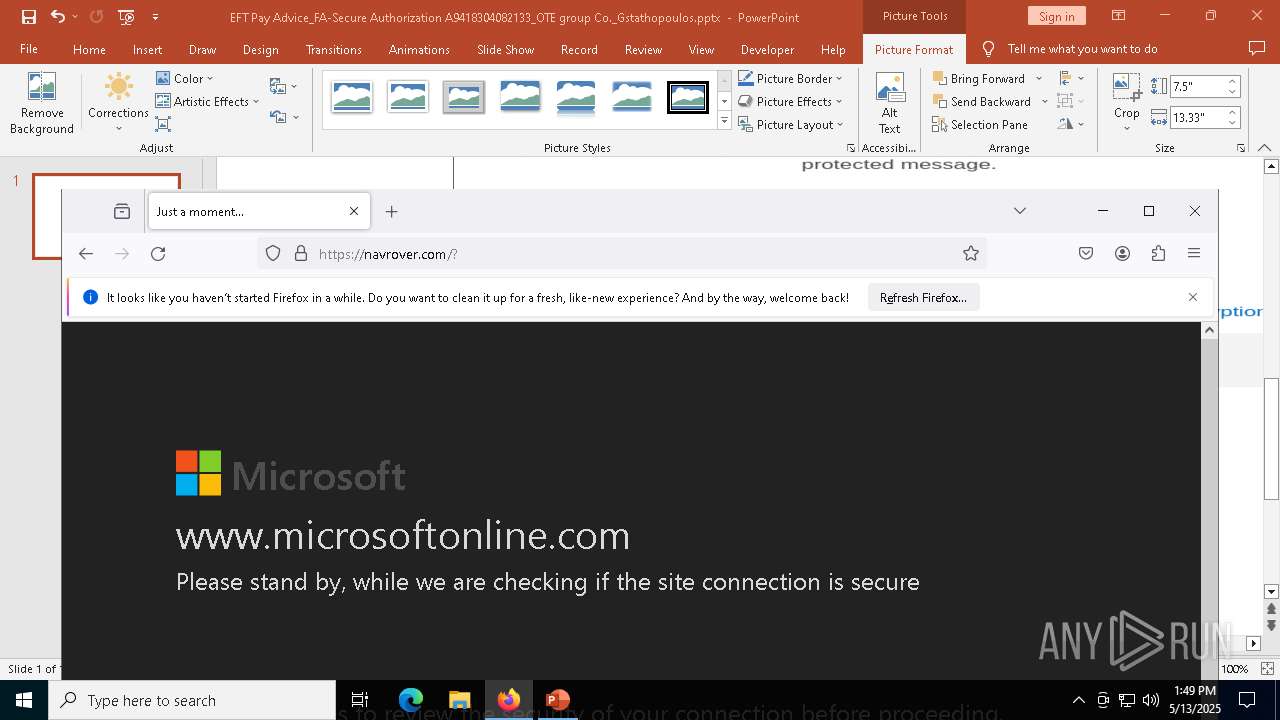
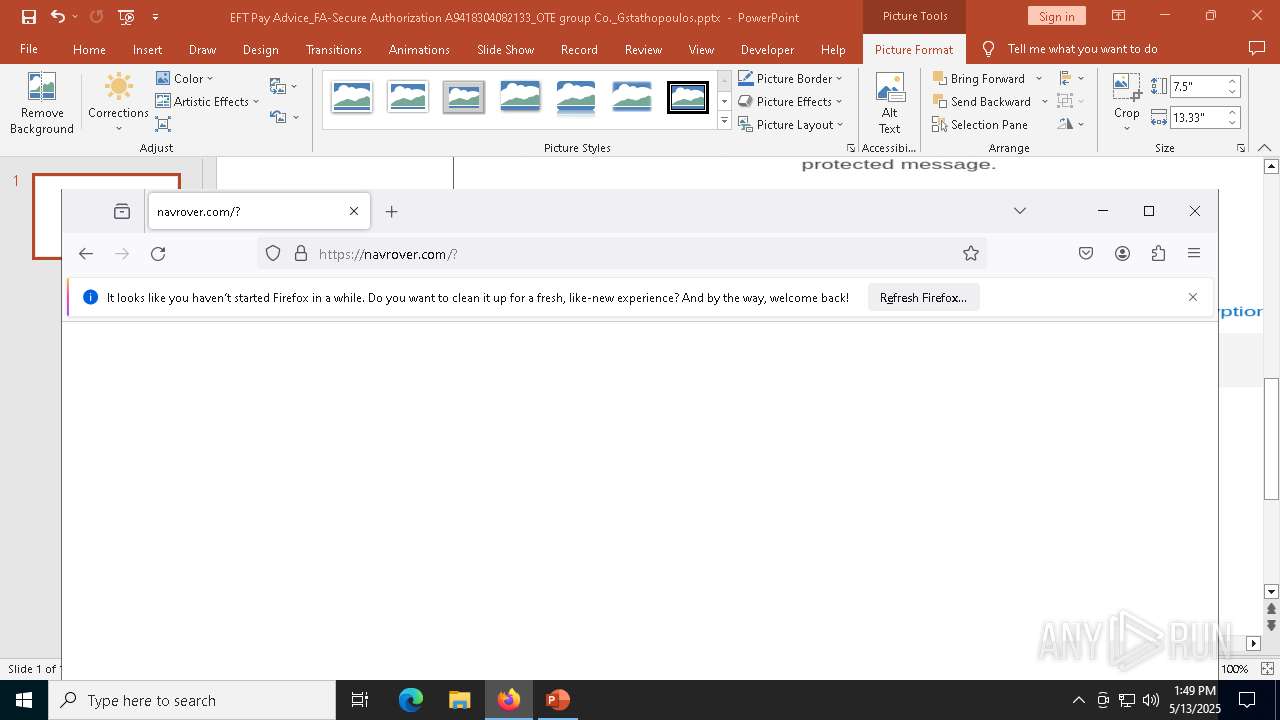
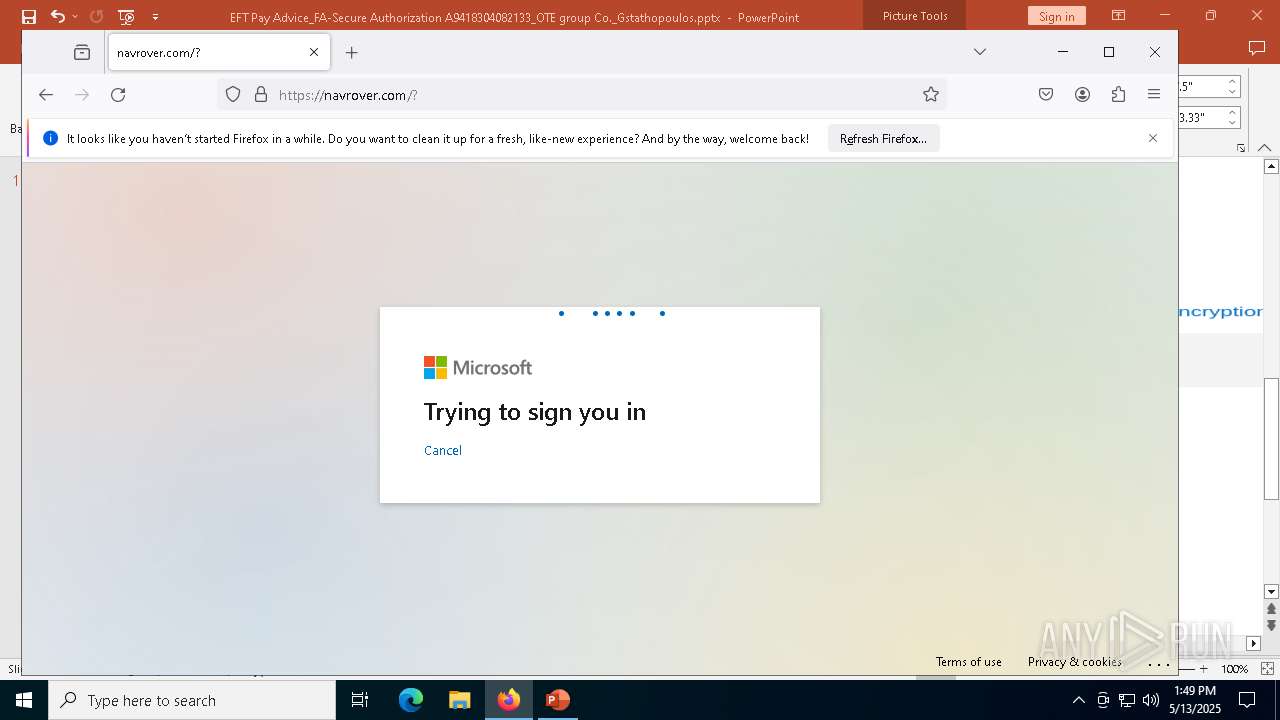
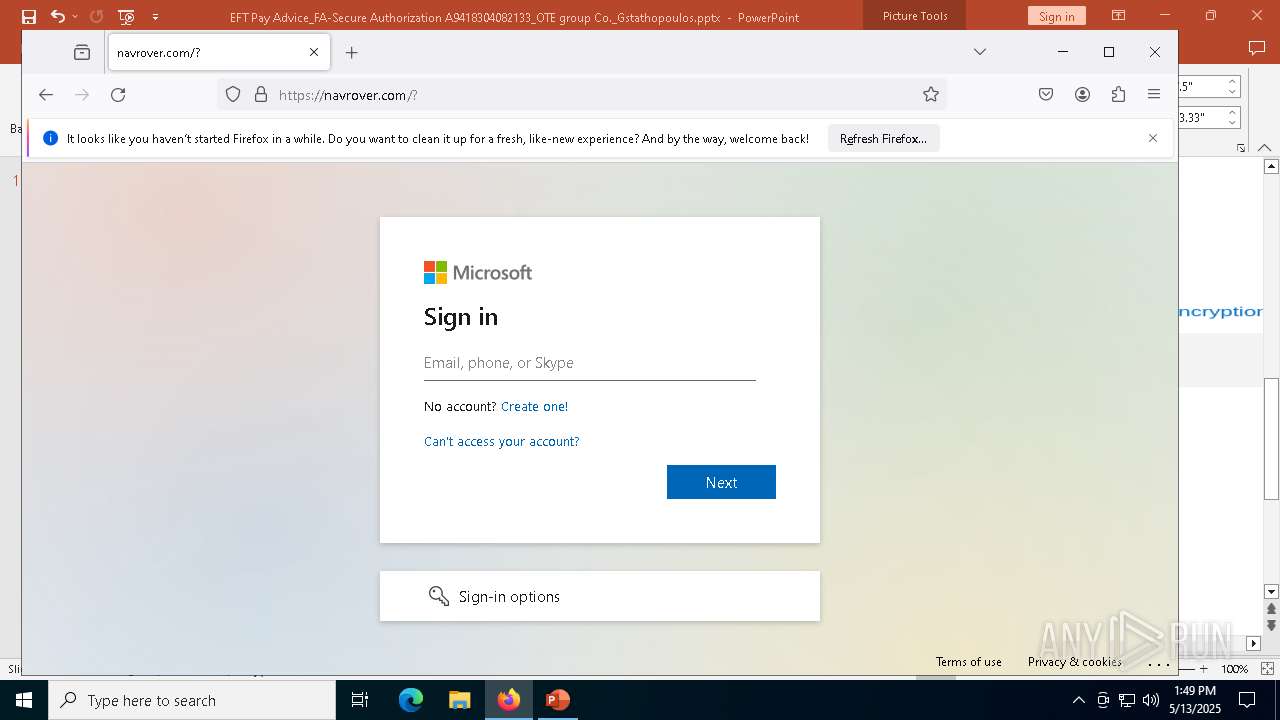
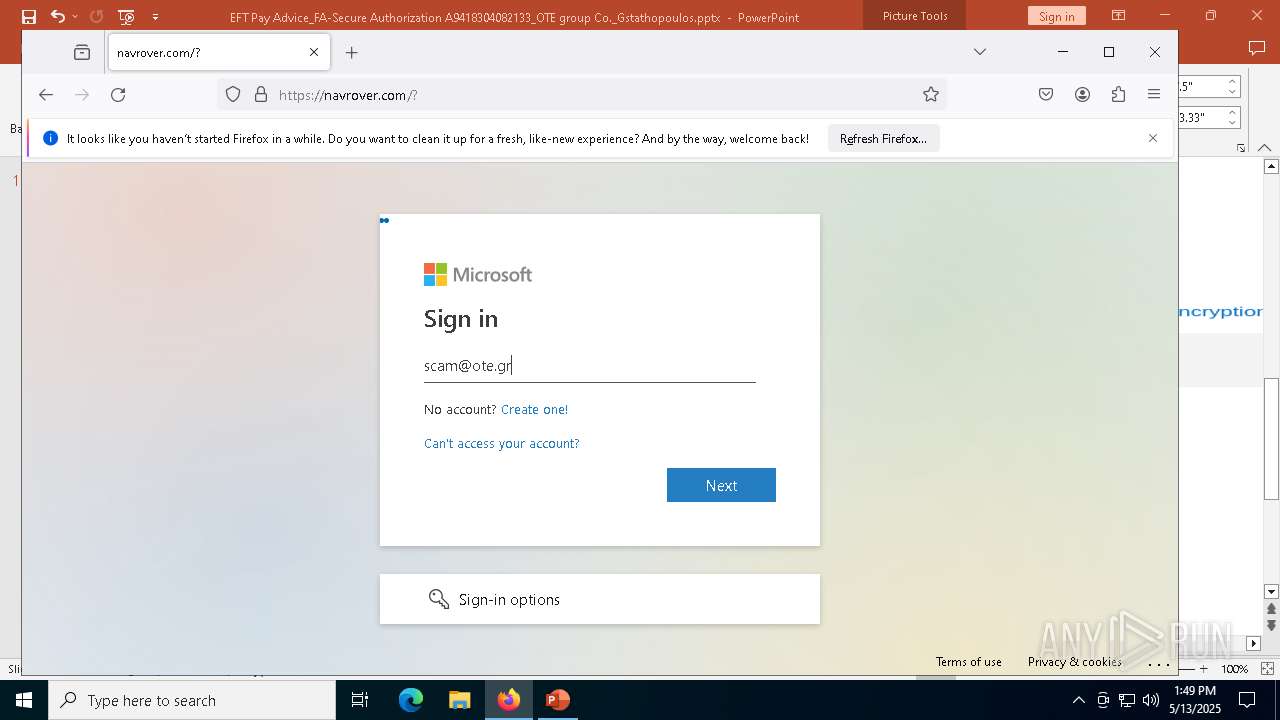
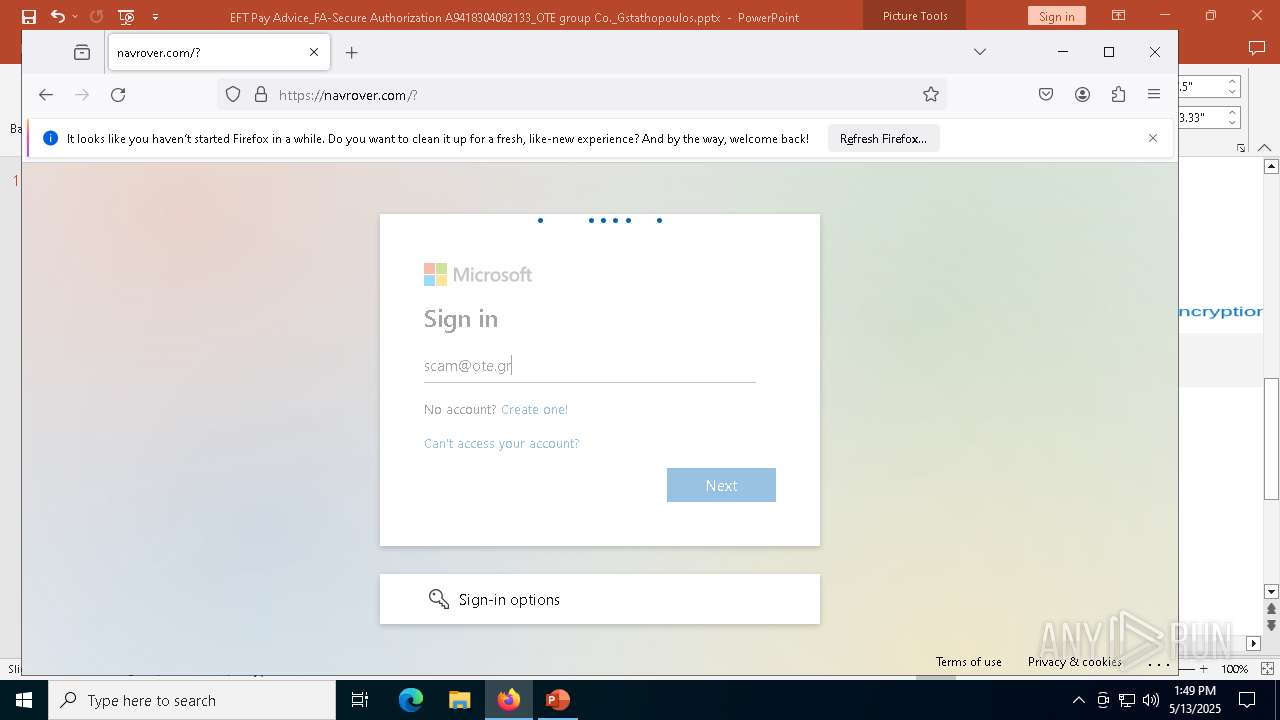
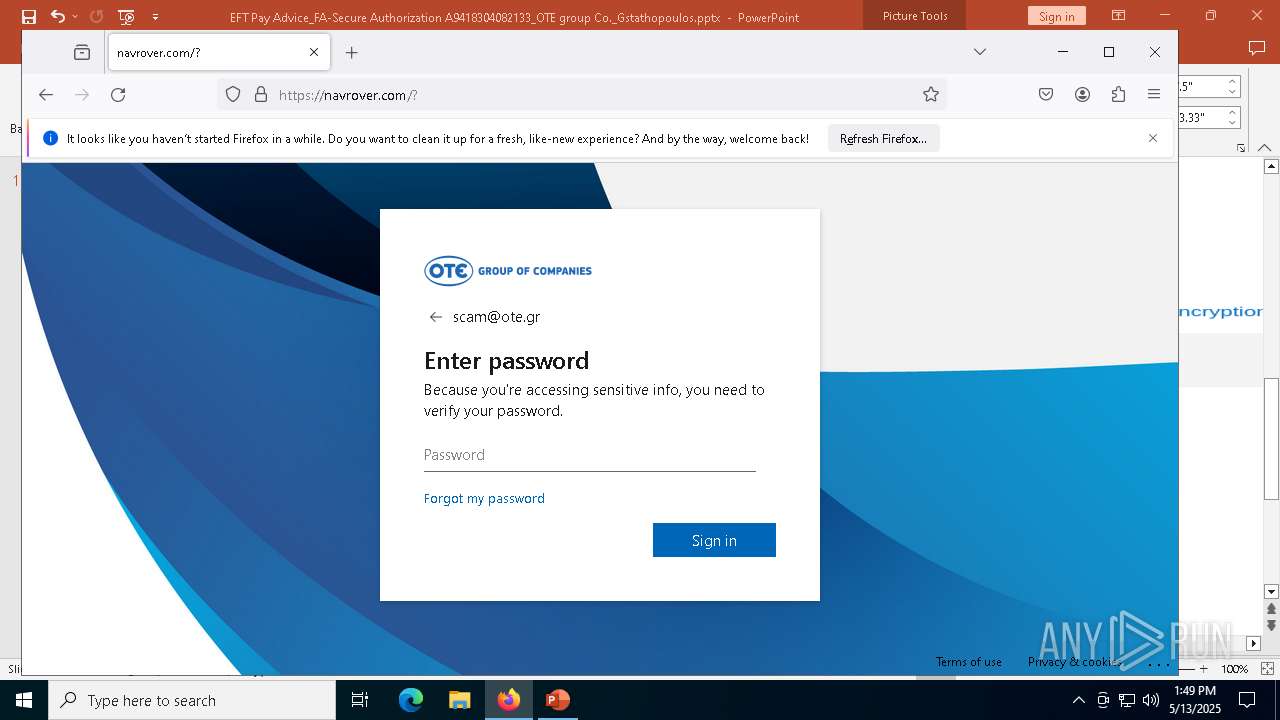
| File name: | EFT Pay Advice_FA-Secure Authorization A9418304082133_OTE group Co._Gstathopoulos.pptx |
| Full analysis: | https://app.any.run/tasks/cfcdaad3-7f2f-4272-8399-f4588690b657 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 13:46:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 526C9124B6CA55E8770F5D17A161A980 |
| SHA1: | 70D9A9C12CFA2DE0BBBD0EEE55851BFD6F73AA6F |
| SHA256: | F10D7E555345A2911CF5D39B48A45FCDF99A36F37D79D5069782F59081130D79 |
| SSDEEP: | 1536:bfUbqtBFAeMNuvGRRBRViGSwO/LGDsx6YPosmeideim6eil/eiTLCeiLcIaauXNN:JR2PKQRDTWq3JSr5rAGo |
MALICIOUS
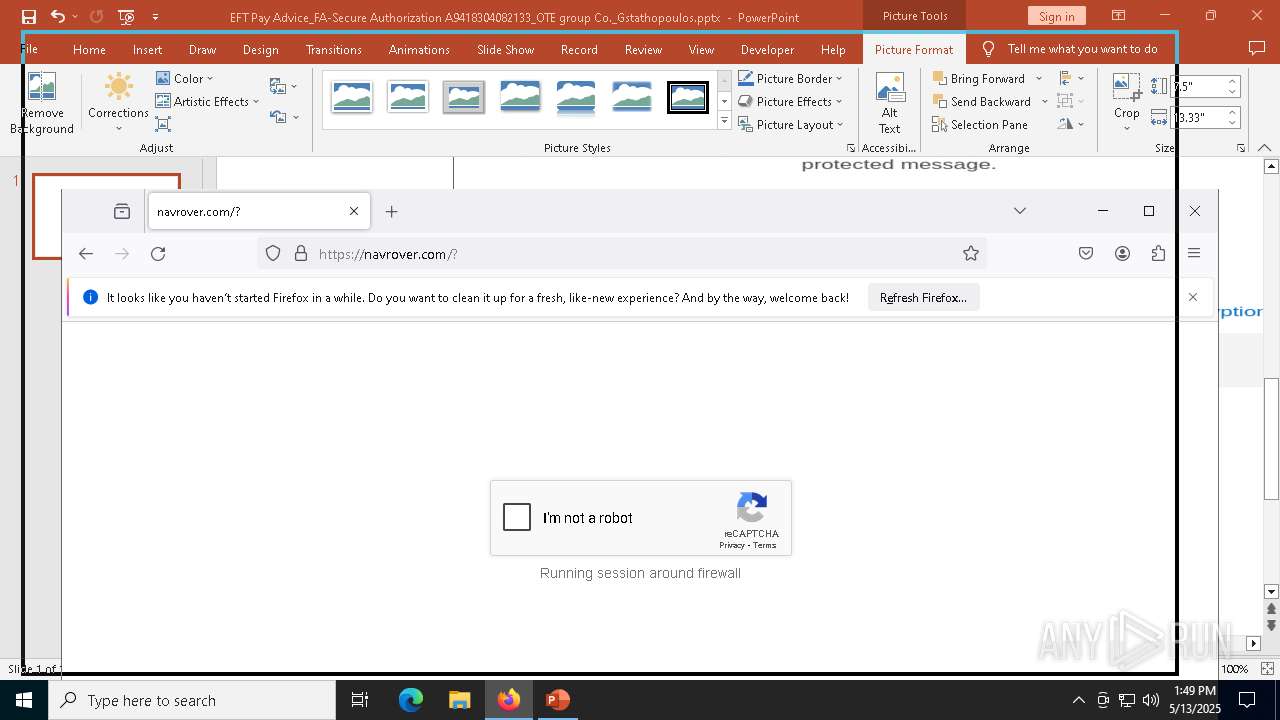
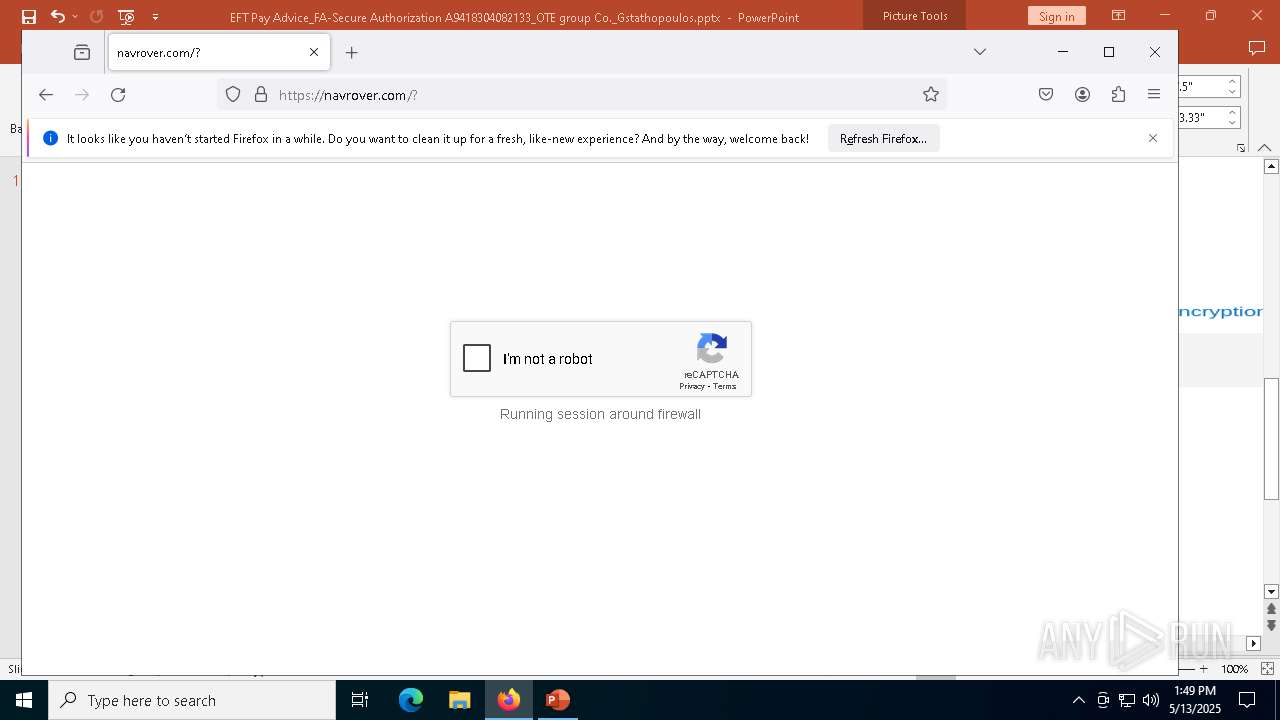
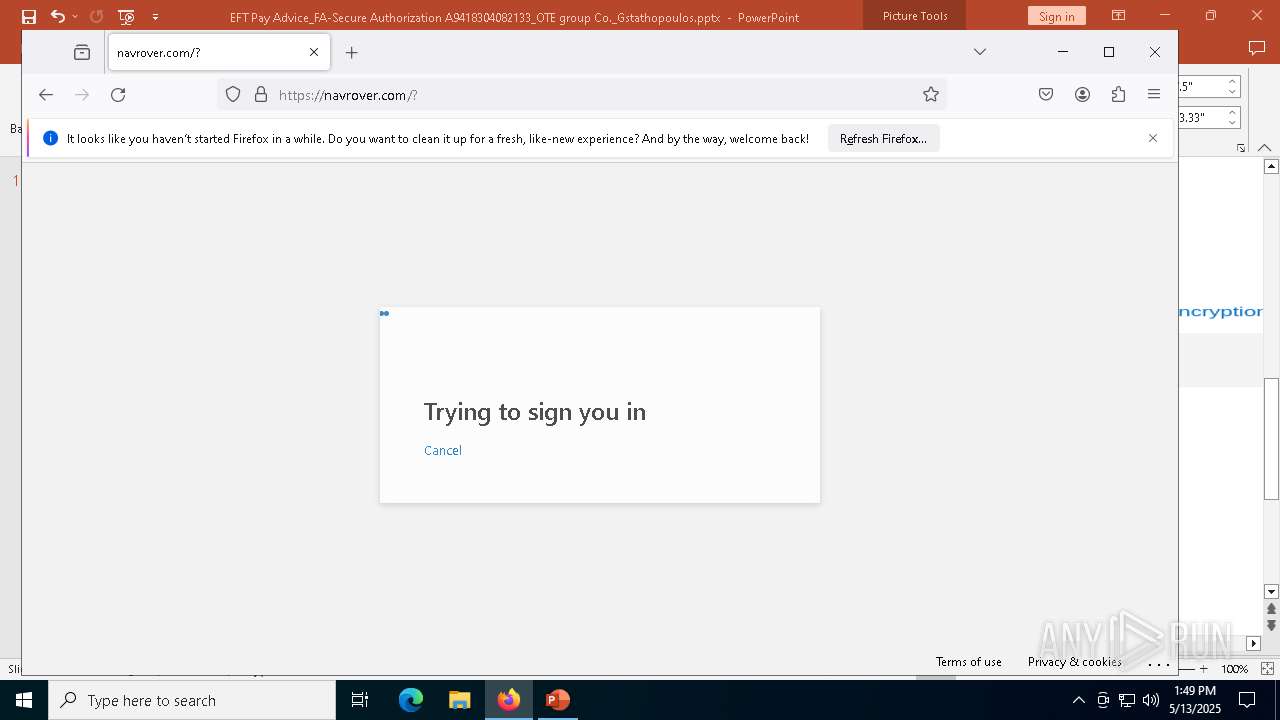
PHISHING has been detected (SURICATA)
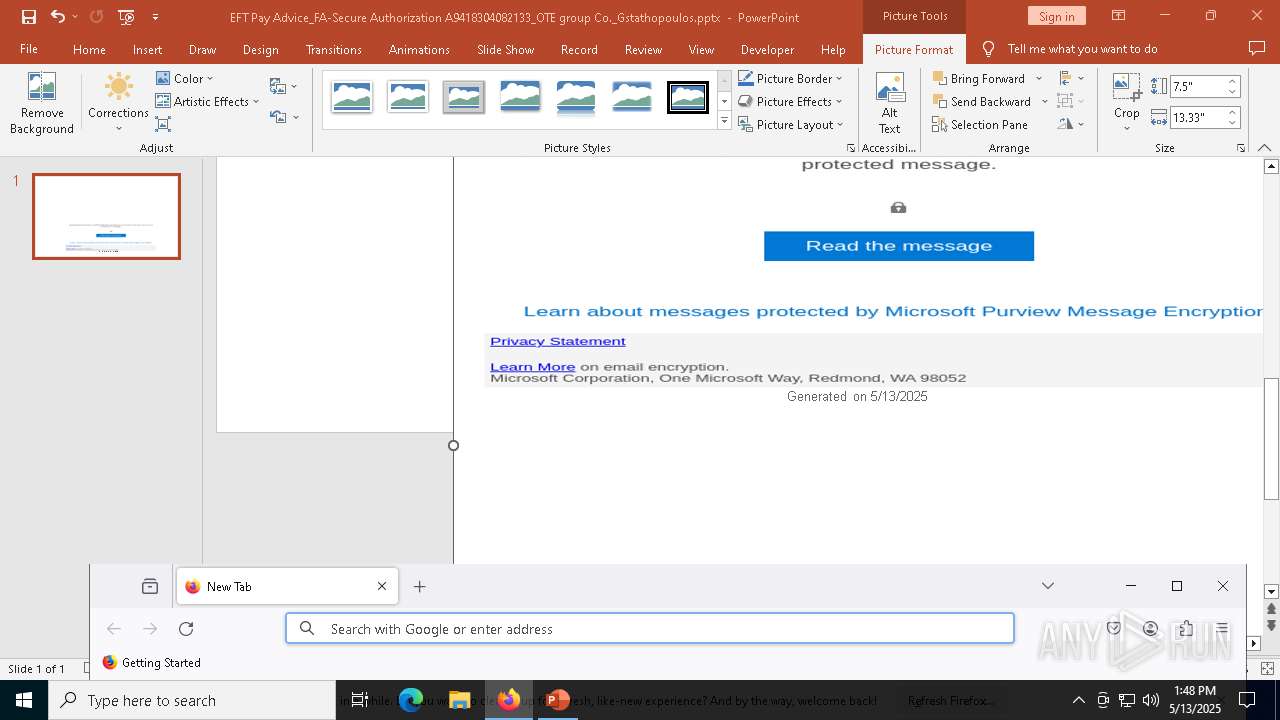
- svchost.exe (PID: 2196)
- firefox.exe (PID: 728)
SUSPICIOUS
Checks for external IP
- svchost.exe (PID: 2196)
INFO
Application launched itself
- firefox.exe (PID: 728)
- firefox.exe (PID: 664)
Manual execution by a user
- firefox.exe (PID: 664)
Reads the software policy settings
- slui.exe (PID: 6808)
- slui.exe (PID: 8148)
Checks proxy server information
- slui.exe (PID: 8148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pptx | | | PowerPoint Microsoft Office Open XML Format document (87) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (10.5) |
| .zip | | | ZIP compressed archive (2.4) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:13 10:56:58 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | _rels/ |
XML
| TotalEditTime: | - |
|---|---|
| Words: | - |
| Application: | Microsoft Office PowerPoint |
| PresentationFormat: | On-screen Show (16:9) |
| Paragraphs: | - |
| Slides: | 1 |
| Notes: | 1 |
| HiddenSlides: | - |
| MMClips: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| Company: | ote.gr |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| LastModifiedBy: | System |
| RevisionNumber: | 1 |
| CreateDate: | 2025:05:13 10:56:59Z |
| ModifyDate: | 2025:05:13 10:56:59Z |
XMP
| Title: | Security Document |
|---|---|
| Subject: | Security Document |
| Creator: | System |
Total processes
157
Monitored processes
20
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 664 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 | ||||
| 728 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 | ||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 4016 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5964 -childID 6 -isForBrowser -prefsHandle 4704 -prefMapHandle 5168 -prefsLen 31642 -prefMapSize 244583 -jsInitHandle 1452 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {549d5174-b76a-458d-a7da-a18dc3dc4c8b} 728 "\\.\pipe\gecko-crash-server-pipe.728" 1e656dd7690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 | ||||
| 4040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5056 -childID 8 -isForBrowser -prefsHandle 1548 -prefMapHandle 5704 -prefsLen 31642 -prefMapSize 244583 -jsInitHandle 1452 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e794bbb9-3807-42e8-b9d0-4786429a4d0a} 728 "\\.\pipe\gecko-crash-server-pipe.728" 1e656528f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 | ||||
| 4220 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4732 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4800 -prefMapHandle 4168 -prefsLen 38445 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {740b3afd-3c6e-4803-8243-b943dc5e61a0} 728 "\\.\pipe\gecko-crash-server-pipe.728" 1e65488c310 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 | ||||
| 4528 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4936 -childID 3 -isForBrowser -prefsHandle 2632 -prefMapHandle 2628 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1452 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {5b2962aa-fdfe-4ef3-b890-74b9352d5676} 728 "\\.\pipe\gecko-crash-server-pipe.728" 1e656528d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 | ||||
| 4932 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4324 -childID 2 -isForBrowser -prefsHandle 4316 -prefMapHandle 4312 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1452 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {036a6a33-3371-42a9-be1d-17c8d0e381d8} 728 "\\.\pipe\gecko-crash-server-pipe.728" 1e6530e3850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 | ||||
| 5404 | "C:\Program Files\Microsoft Office\Root\Office16\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\EFT Pay Advice_FA-Secure Authorization A9418304082133_OTE group Co._Gstathopoulos.pptx" /ou "" | C:\Program Files\Microsoft Office\root\Office16\POWERPNT.EXE | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Version: 16.0.16026.20146 | ||||
| 5864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5988 -childID 7 -isForBrowser -prefsHandle 5028 -prefMapHandle 5136 -prefsLen 31642 -prefMapSize 244583 -jsInitHandle 1452 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {049d8ddf-46f0-485a-be8c-43606f27f1b4} 728 "\\.\pipe\gecko-crash-server-pipe.728" 1e656dd7d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
16
Suspicious files
274
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:3D01CBB9EA37C5E467B0A7ED0F82CB93 | SHA256:8053633885E3D63FAED06A30F27CD5F1BDCAFB31C025C7B19B5EA6B7D62AA167 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:A2A95288873661D4ECAD44D04496767B | SHA256:F1ED145EB341F0E207479422AE3BE4975AE839E57D91A06B521043FABA2B28BD | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d00655d2aa12ff6d.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_41.ttf | pi2 | |
MD5:A807151D5747F6460143DC1FD2C3195F | SHA256:C0C3B354480E34CCC0C25D371B30D0272DB86C786AF6438C217998B0A30E5EB0 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:54CB6FA0C881FDC924A9951B05AF8179 | SHA256:E5FAF6A480E41A32C69246E6C40B7E9A4929D488B563C61CA4218D914952EB40 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\cab17EA.tmp | compressed | |
MD5:ABBF10CEE9480E41D81277E9538F98CB | SHA256:557E0714D5536070131E7E7CDD18F0EF23FE6FB12381040812D022EC0FEE7957 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\95HQLFFXMSOROOAIDX0V.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:54CB6FA0C881FDC924A9951B05AF8179 | SHA256:E5FAF6A480E41A32C69246E6C40B7E9A4929D488B563C61CA4218D914952EB40 | |||
| 5404 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\PowerPoint\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:45A14FB8DA9B697E1839F2004D0F897E | SHA256:23AD0C1EF45202F8CA786B3C7C2936608006C9E21EF93D134CD2CBA84CA99813 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
182
DNS requests
200
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5404 | POWERPNT.EXE | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2316 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5404 | POWERPNT.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5404 | POWERPNT.EXE | 52.123.130.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5404 | POWERPNT.EXE | 23.48.23.30:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
5404 | POWERPNT.EXE | 52.109.28.47:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5404 | POWERPNT.EXE | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
messaging.engagement.office.com |
| whitelisted |
login.live.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
728 | firefox.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 14 |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (kayatbqdqg .es) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (kayatbqdqg .es) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (kayatbqdqg .es) |