| File name: | vJoySetup.exe |
| Full analysis: | https://app.any.run/tasks/0a132b9f-df25-48b7-973d-b0f6f8fc0533 |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2023, 20:58:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2AB668A12EBDEA3BD8FA1D5A2CA7CB45 |
| SHA1: | 535822F96003B9B68F155A1FBDC226DE93D1D1AF |
| SHA256: | F103CED4E7FF7CCB49C8415A542C56768ED4DA4FEA252B8F4FFDAC343074654A |
| SSDEEP: | 98304:lbUMv+3ec9TMYWBg0UJIJV+bbRgT4jZNvbaXG3NF6Sn3KWlnuZbgQ2PinzJCxyen:1b5nJJuIyzfmGj |
MALICIOUS
Drops the executable file immediately after the start
- vJoySetup.exe (PID: 3448)
- vJoySetup.exe (PID: 3480)
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
- vJoySetup.tmp (PID: 3512)
Creates a writable file the system directory
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
SUSPICIOUS
Reads the Windows owner or organization settings
- vJoySetup.tmp (PID: 3512)
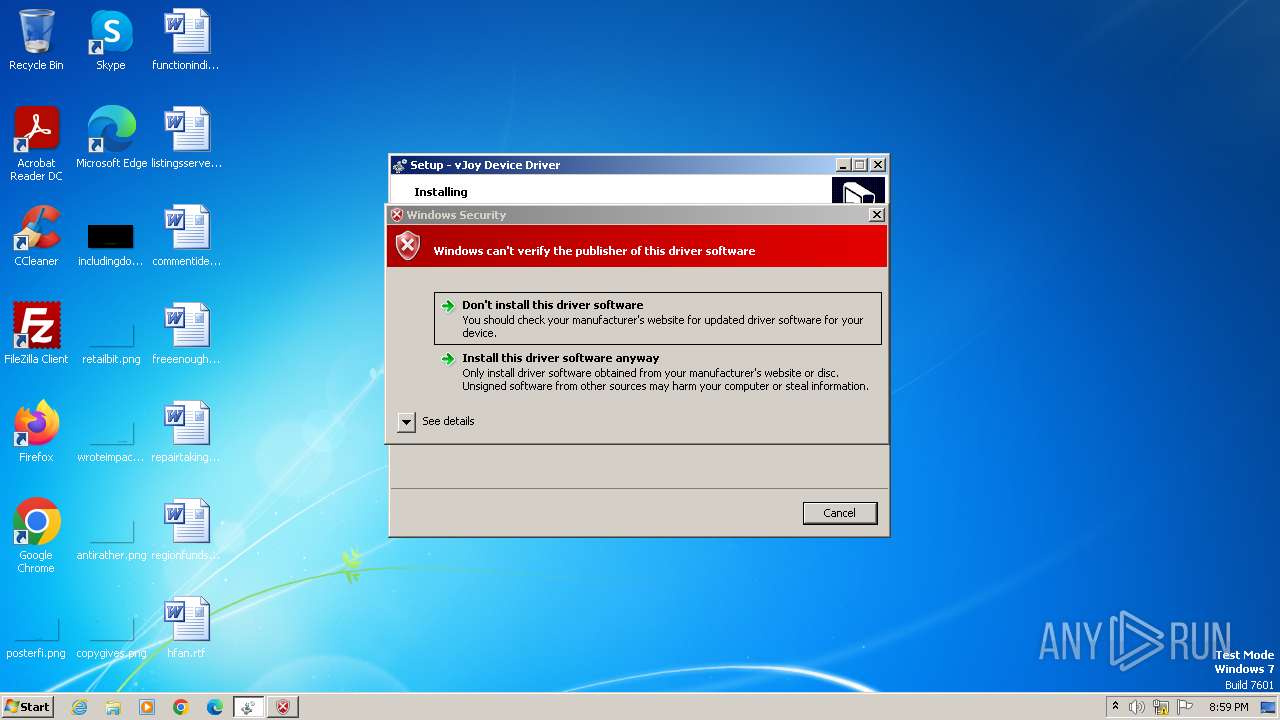
Drops a system driver (possible attempt to evade defenses)
- vJoySetup.tmp (PID: 3512)
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
Process drops legitimate windows executable
- vJoySetup.tmp (PID: 3512)
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
The process drops C-runtime libraries
- vJoySetup.tmp (PID: 3512)
Reads security settings of Internet Explorer
- vJoyInstall.exe (PID: 3632)
Checks Windows Trust Settings
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
Reads settings of System Certificates
- vJoyInstall.exe (PID: 3632)
Creates files in the driver directory
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
Executes as Windows Service
- VSSVC.exe (PID: 3908)
INFO
Checks supported languages
- vJoySetup.exe (PID: 3448)
- vJoySetup.exe (PID: 3480)
- vJoySetup.tmp (PID: 3156)
- vJoySetup.tmp (PID: 3512)
- wmpnscfg.exe (PID: 3400)
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
- drvinst.exe (PID: 916)
- drvinst.exe (PID: 2056)
- vJoyList.exe (PID: 1420)
- vJoyConf.exe (PID: 2756)
- drvinst.exe (PID: 668)
Reads the computer name
- vJoySetup.tmp (PID: 3156)
- vJoySetup.tmp (PID: 3512)
- wmpnscfg.exe (PID: 3400)
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
- drvinst.exe (PID: 916)
- drvinst.exe (PID: 2056)
- vJoyList.exe (PID: 1420)
- vJoyConf.exe (PID: 2756)
- drvinst.exe (PID: 668)
Create files in a temporary directory
- vJoySetup.exe (PID: 3480)
- vJoySetup.exe (PID: 3448)
- vJoySetup.tmp (PID: 3512)
- vJoyInstall.exe (PID: 3632)
- rundll32.exe (PID: 1856)
Creates files in the program directory
- vJoySetup.tmp (PID: 3512)
- vJoyInstall.exe (PID: 3632)
Manual execution by a user
- wmpnscfg.exe (PID: 3400)
- vJoyList.exe (PID: 1420)
- vJoyConf.exe (PID: 3868)
- vJoyConf.exe (PID: 2756)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3400)
- vJoyInstall.exe (PID: 3632)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3700)
- drvinst.exe (PID: 668)
Creates files or folders in the user directory
- rundll32.exe (PID: 1856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:04:27 10:22:11+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 682496 |
| InitializedDataSize: | 300032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7ed0 |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.9.1 |
| ProductVersionNumber: | 2.1.9.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Shaul Eizikovich |
| FileDescription: | vJoy Device Driver Setup |
| FileVersion: | 2.1.9.1 |
| LegalCopyright: | Copyright (c) 2005-2016 by Shaul Eizikovich |
| OriginalFileName: | |
| ProductName: | vJoy Device Driver |
| ProductVersion: | 2.1.9.1 |
Total processes
60
Monitored processes
18
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | DrvInst.exe "2" "201" "HID\HIDCLASS\1&2D595CA7&0&0000" "C:\Windows\INF\input.inf" "input.inf:Standard.NTx86:HID_Raw_Inst:6.1.7601.24386::hid_device_system_game" "6070ed7cf" "00000620" "000005D4" "00000630" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | DrvInst.exe "1" "200" "HID\HIDCLASS\1&2d595ca7&0&0000" "" "" "6eeb73e57" "00000000" "000005E4" "000005D8" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 3758096899 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | "C:\Program Files\vJoy\x86\vJoyList.exe" | C:\Program Files\vJoy\x86\vJoyList.exe | — | explorer.exe | |||||||||||
User: admin Company: Shaul Eizikovich Integrity Level: MEDIUM Description: vJoyList - List vJoy devices Exit code: 0 Version: 0.0.0 Modules
| |||||||||||||||
| 1856 | rundll32.exe C:\Windows\system32\newdev.dll,pDiDeviceInstallNotification \\.\pipe\PNP_Device_Install_Pipe_1.{f33acce7-e58a-4eda-95c7-14cd65e0b81e} "(null)" | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2000 | C:\Windows\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {995C996E-D918-4a8c-A302-45719A6F4EA7} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | DrvInst.exe "1" "200" "{D6E55CA0-1A2E-4234-AAF3-3852170B492F}\vJoyRawPdo\1&2d595ca7&0&vJoyInstance00" "" "" "60a97addf" "00000000" "000005D4" "00000618" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 3758096899 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Program Files\vJoy\x86\vJoyConf.exe" | C:\Program Files\vJoy\x86\vJoyConf.exe | explorer.exe | ||||||||||||
User: admin Company: Shaul Eizikovich Integrity Level: HIGH Description: vJoyConf - Configure vJoy devices Exit code: 0 Version: 0.0.0 Modules
| |||||||||||||||
| 3156 | "C:\Users\admin\AppData\Local\Temp\is-GGFSA.tmp\vJoySetup.tmp" /SL5="$50194,10728610,983552,C:\Users\admin\AppData\Local\Temp\vJoySetup.exe" | C:\Users\admin\AppData\Local\Temp\is-GGFSA.tmp\vJoySetup.tmp | — | vJoySetup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3400 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3448 | "C:\Users\admin\AppData\Local\Temp\vJoySetup.exe" | C:\Users\admin\AppData\Local\Temp\vJoySetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Shaul Eizikovich Integrity Level: MEDIUM Description: vJoy Device Driver Setup Exit code: 0 Version: 2.1.9.1 Modules
| |||||||||||||||
Total events
11 066
Read events
10 988
Write events
69
Delete events
9
Modification events
| (PID) Process: | (3400) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{E6AA288E-56B3-4B08-A90B-FE9F12873CA2}\{FFE9D7E0-E0E7-4A19-84C2-B700DF3E92F2} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3400) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{E6AA288E-56B3-4B08-A90B-FE9F12873CA2} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3400) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{800D47F3-F9B4-481B-9988-41D5C5544BB2} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3632) vJoyInstall.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3860) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3860) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3860) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3860) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
| (PID) Process: | (3860) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008C62D6BA16B0D901C80700002C0A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3860) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 400000000000000064514ABC16B0D901C80700002C0A0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
62
Suspicious files
34
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3480 | vJoySetup.exe | C:\Users\admin\AppData\Local\Temp\is-J44CT.tmp\vJoySetup.tmp | executable | |
MD5:F8034AC234BF9638B31432E22FC2F53F | SHA256:C7548189B1EEFDC5BD0CAEB5E43B9496E5A7CFB9578FBECA0F31DD099D6AA47A | |||
| 3448 | vJoySetup.exe | C:\Users\admin\AppData\Local\Temp\is-GGFSA.tmp\vJoySetup.tmp | executable | |
MD5:F8034AC234BF9638B31432E22FC2F53F | SHA256:C7548189B1EEFDC5BD0CAEB5E43B9496E5A7CFB9578FBECA0F31DD099D6AA47A | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\is-FFU48.tmp | binary | |
MD5:9FD18355252D5A2D8A51C47EF04F5C4A | SHA256:CB240C8F6E7CC196B4E945C0CBE955E18E5BDE987A3096F4BE6914485AF50172 | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\vjoy.cat | binary | |
MD5:9FD18355252D5A2D8A51C47EF04F5C4A | SHA256:CB240C8F6E7CC196B4E945C0CBE955E18E5BDE987A3096F4BE6914485AF50172 | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\is-H849C.tmp | executable | |
MD5:8D3DB0D325B03D532AECD2F043255C53 | SHA256:E6D604466BA9A852BD48C269084A0643F1C81A29233ADEAE505BE1D081DCA6DB | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\vjoy.inf | binary | |
MD5:952F8DDE7EC6B3003BE80CC309B35AEF | SHA256:FE9736BC31B60A4DF4950F9065556B0A887096C3F743EC27D98418368876FF6E | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\is-8U9NT.tmp | executable | |
MD5:1452C1D1FE9859A991D76B8E77E33C7D | SHA256:04EA65C444C0A9CDEBBA64474549888DA5114D081FC6E899B7A4920B121E28A8 | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\is-2PM90.tmp | binary | |
MD5:952F8DDE7EC6B3003BE80CC309B35AEF | SHA256:FE9736BC31B60A4DF4950F9065556B0A887096C3F743EC27D98418368876FF6E | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\WdfCoinstaller01009.dll | executable | |
MD5:16A8D851CE07D6FDABF28707E50CC698 | SHA256:FC45FC877B470236C2FB4A335D16594CD2ADA6FA1CBCDFE9184885326D6EB5FA | |||
| 3512 | vJoySetup.tmp | C:\Program Files\vJoy\vJoy.sys | executable | |
MD5:1452C1D1FE9859A991D76B8E77E33C7D | SHA256:04EA65C444C0A9CDEBBA64474549888DA5114D081FC6E899B7A4920B121E28A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 88.221.124.138:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |