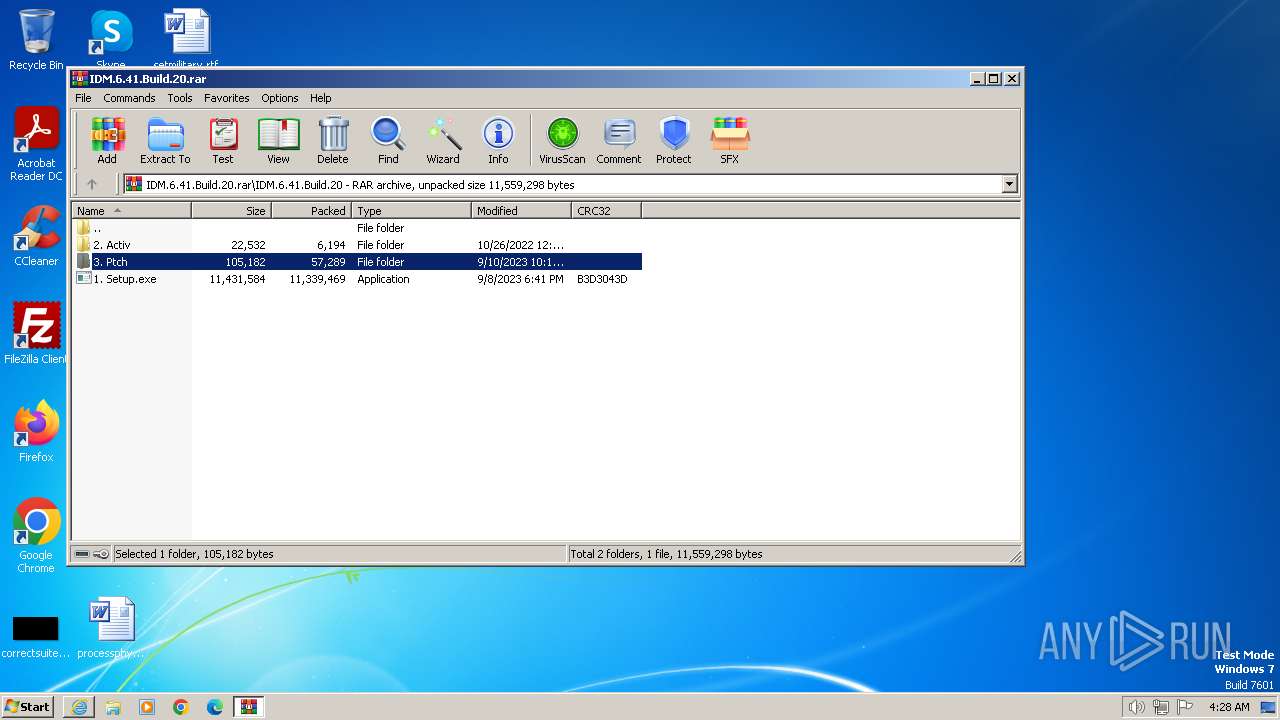
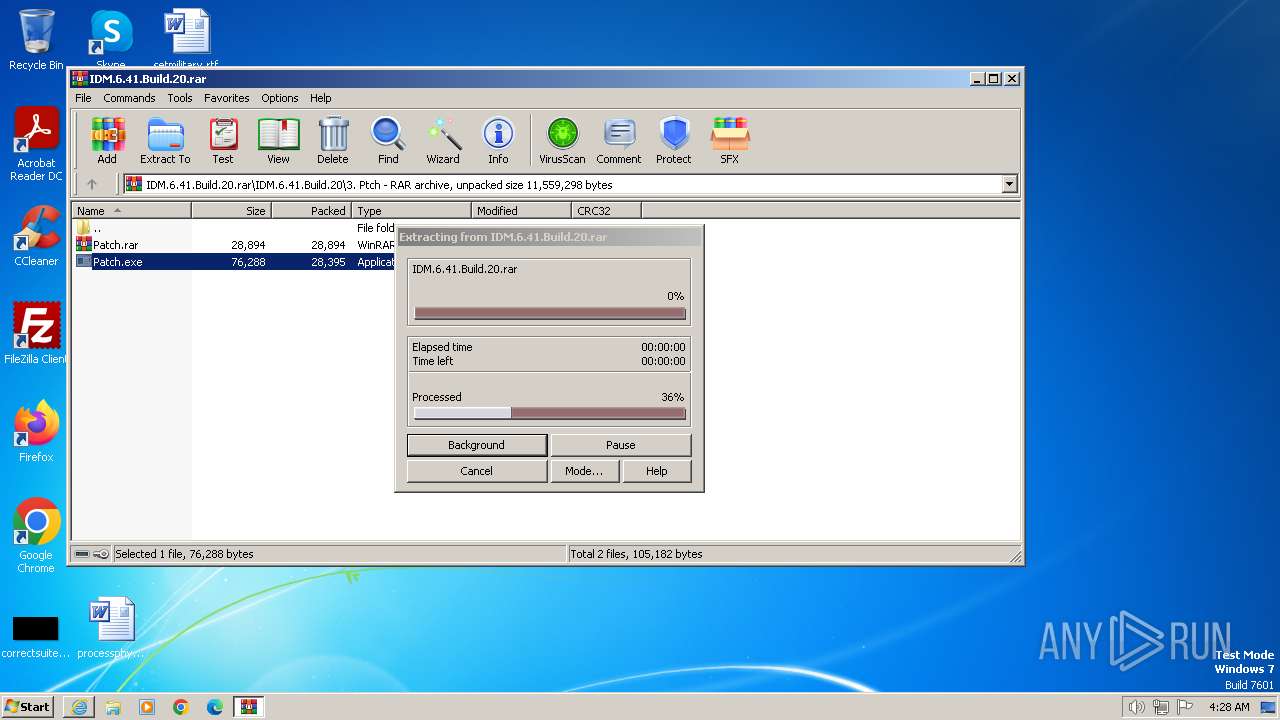
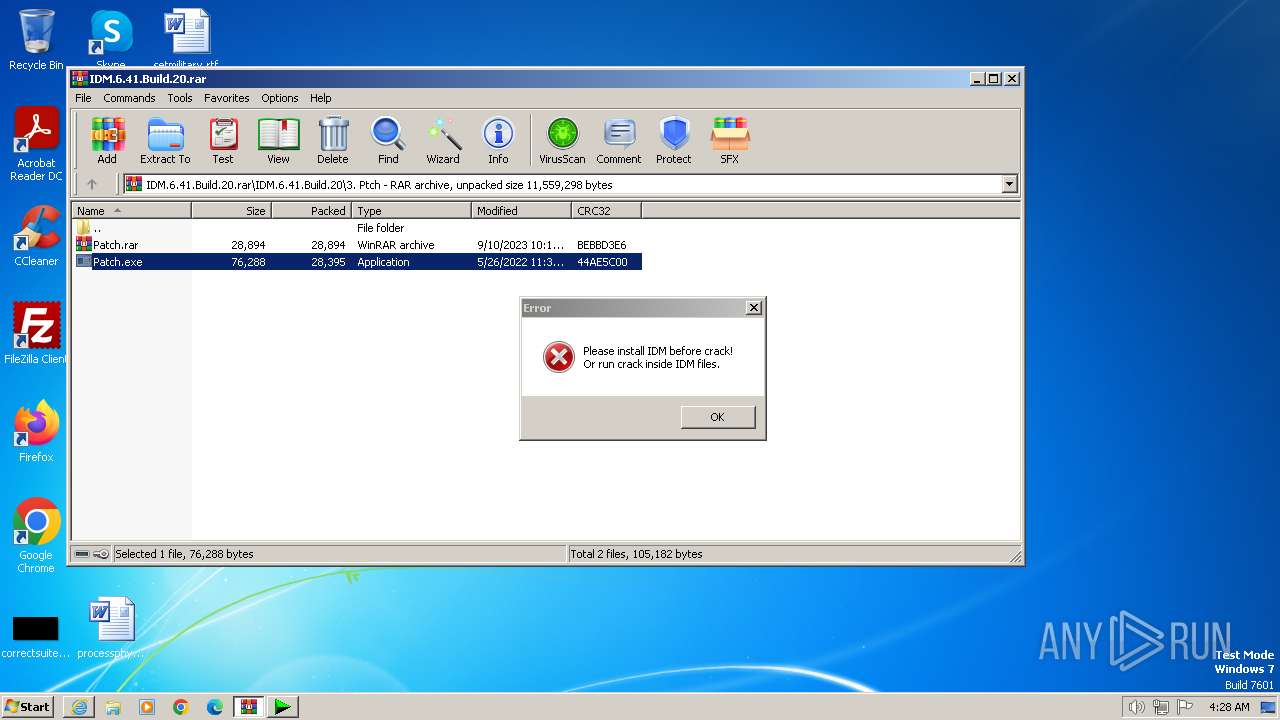
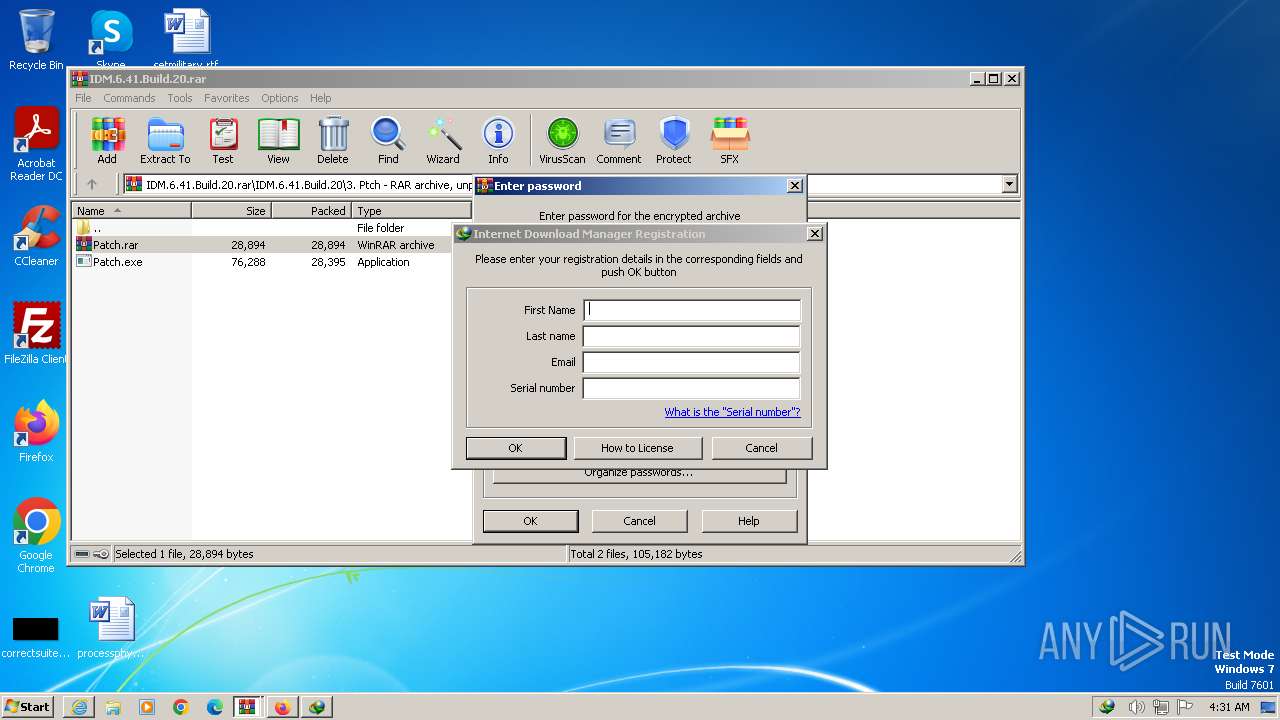
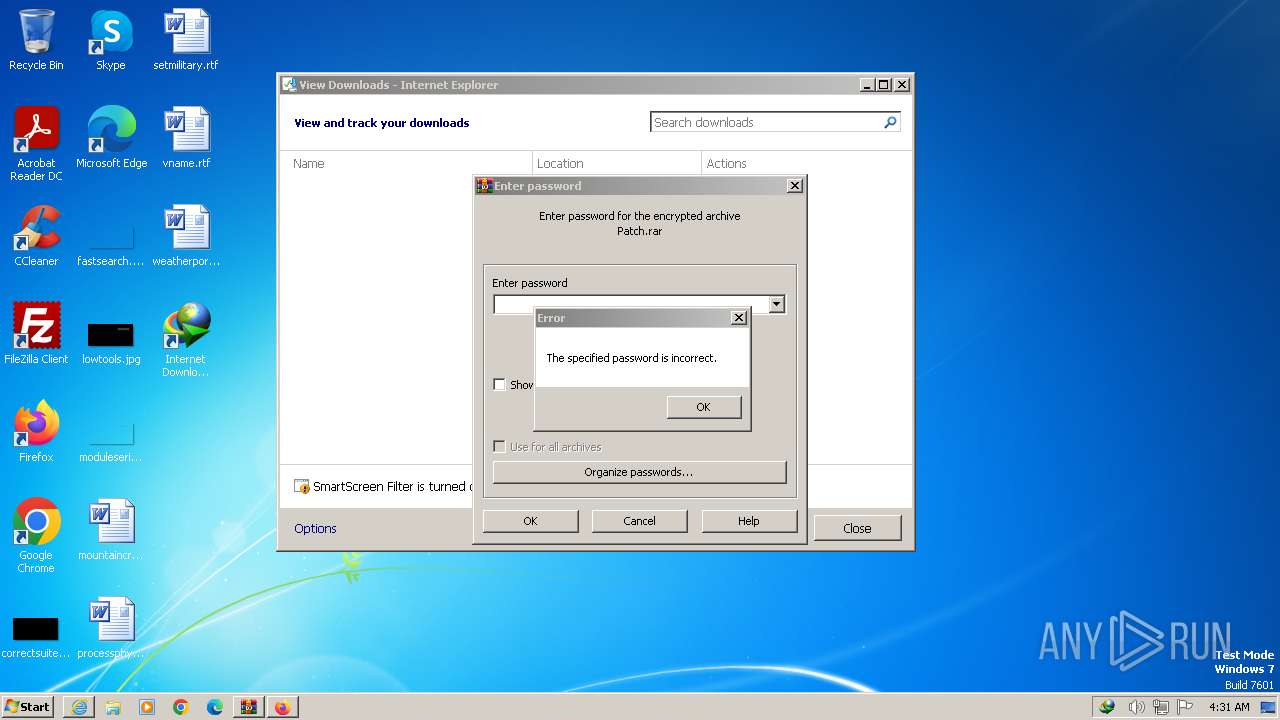
| URL: | https://pixeldrain.com/api/file/AStj56s2?download |
| Full analysis: | https://app.any.run/tasks/558a1fbd-2d9b-4fc4-bdb0-6281f06eab14 |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 04:26:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2C1C1D221FED739A3CC37B2BCFCC1702 |
| SHA1: | E990000BB6CD38472B51237FC4538F2B98EE9A8C |
| SHA256: | F0F38E9400DB7CF58AE9D29497961F99F9C8137FBD95723EA3A37E2B9C1226ED |
| SSDEEP: | 3:N8Icl/GK09saBFJKo:2IG/d01BFz |
MALICIOUS
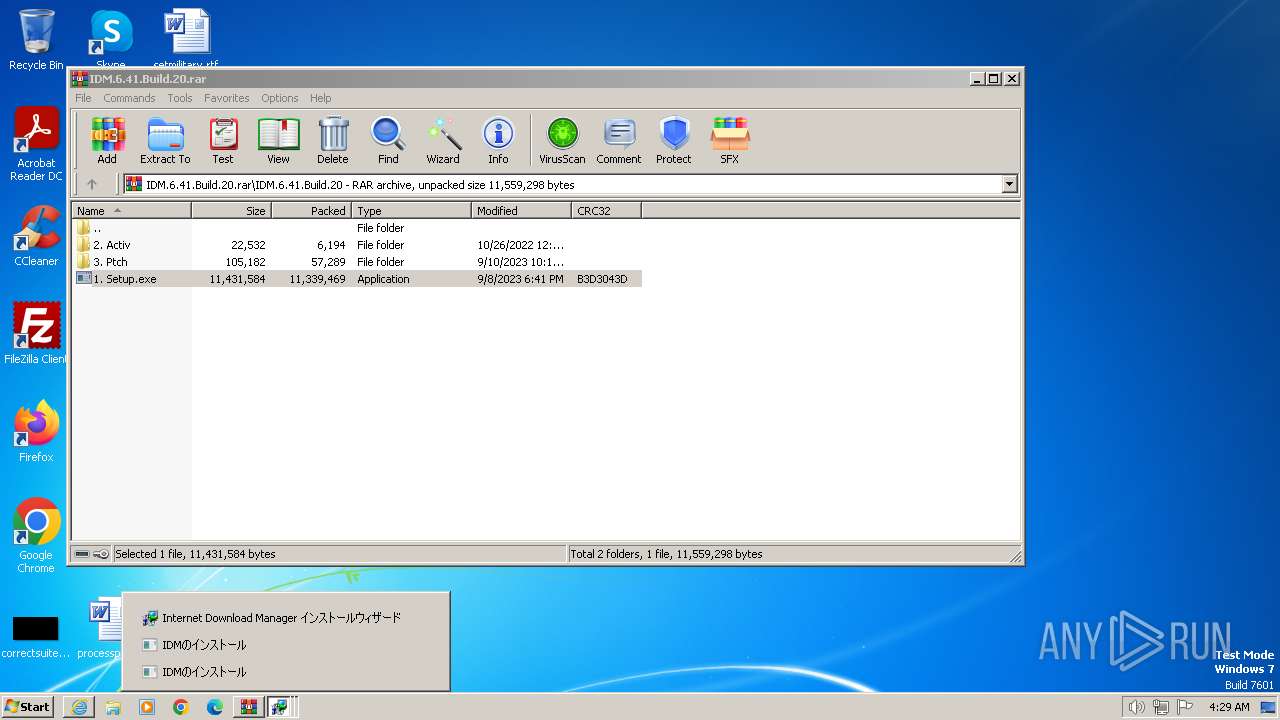
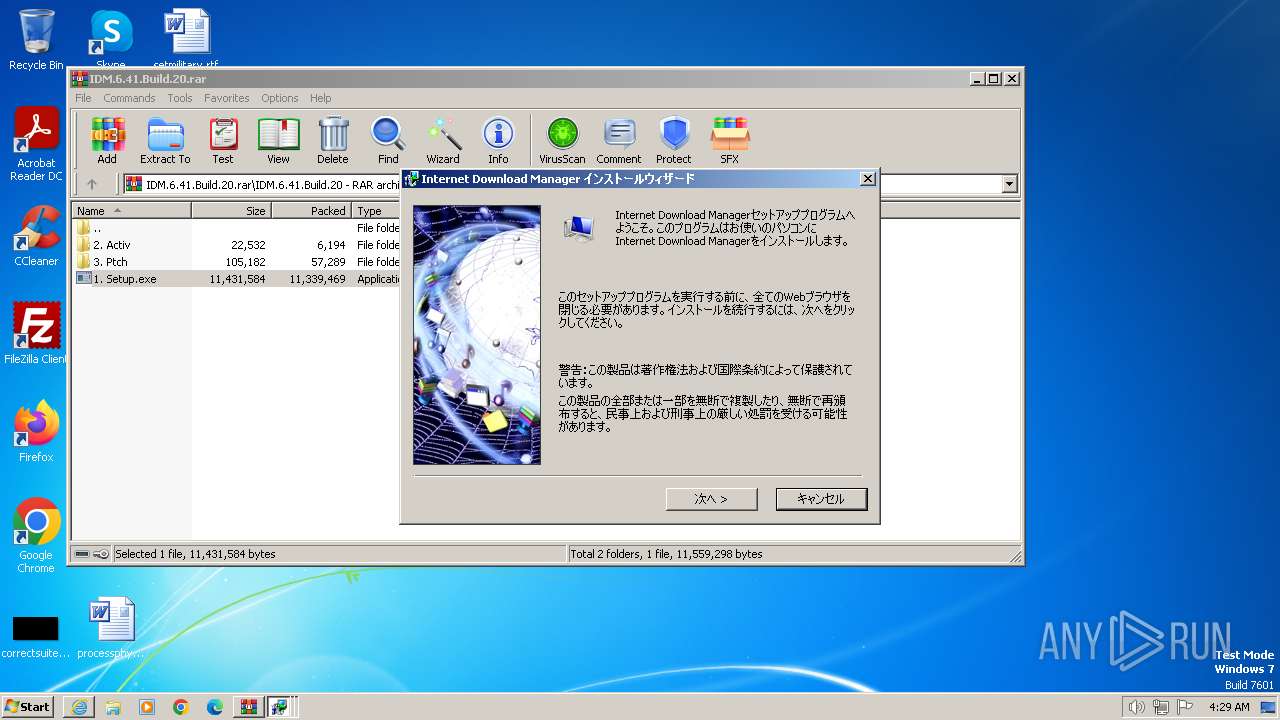
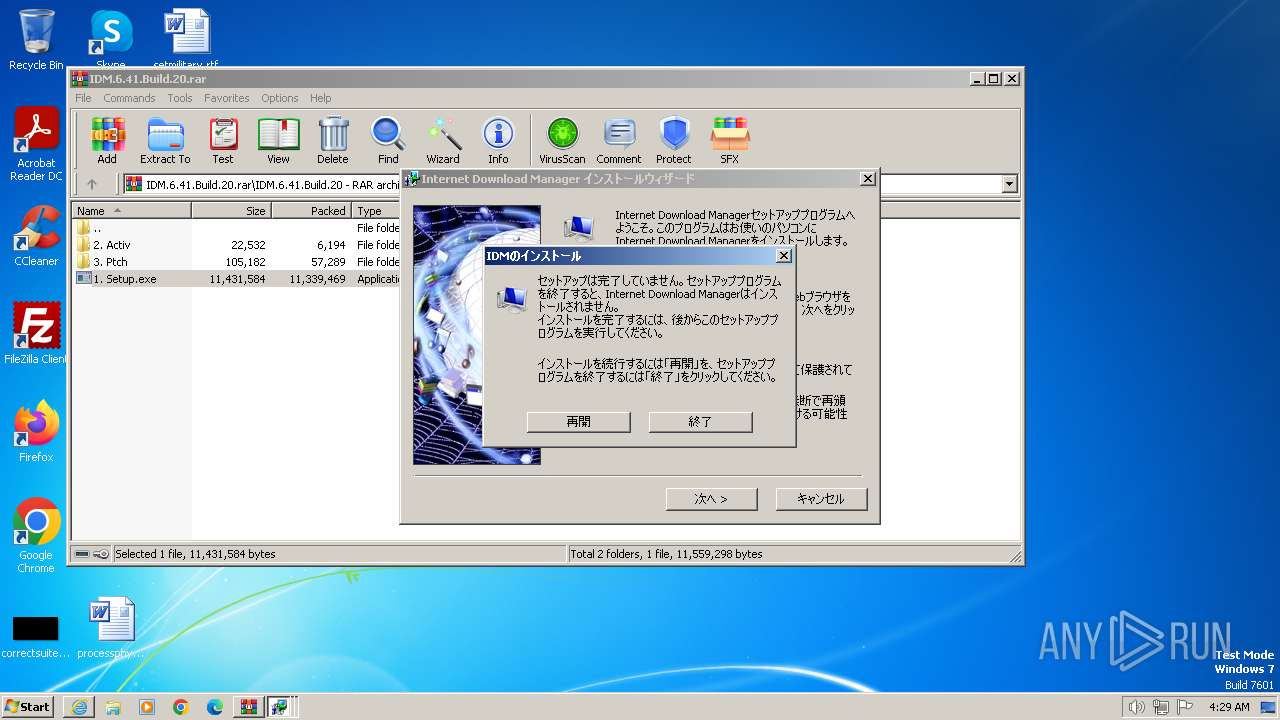
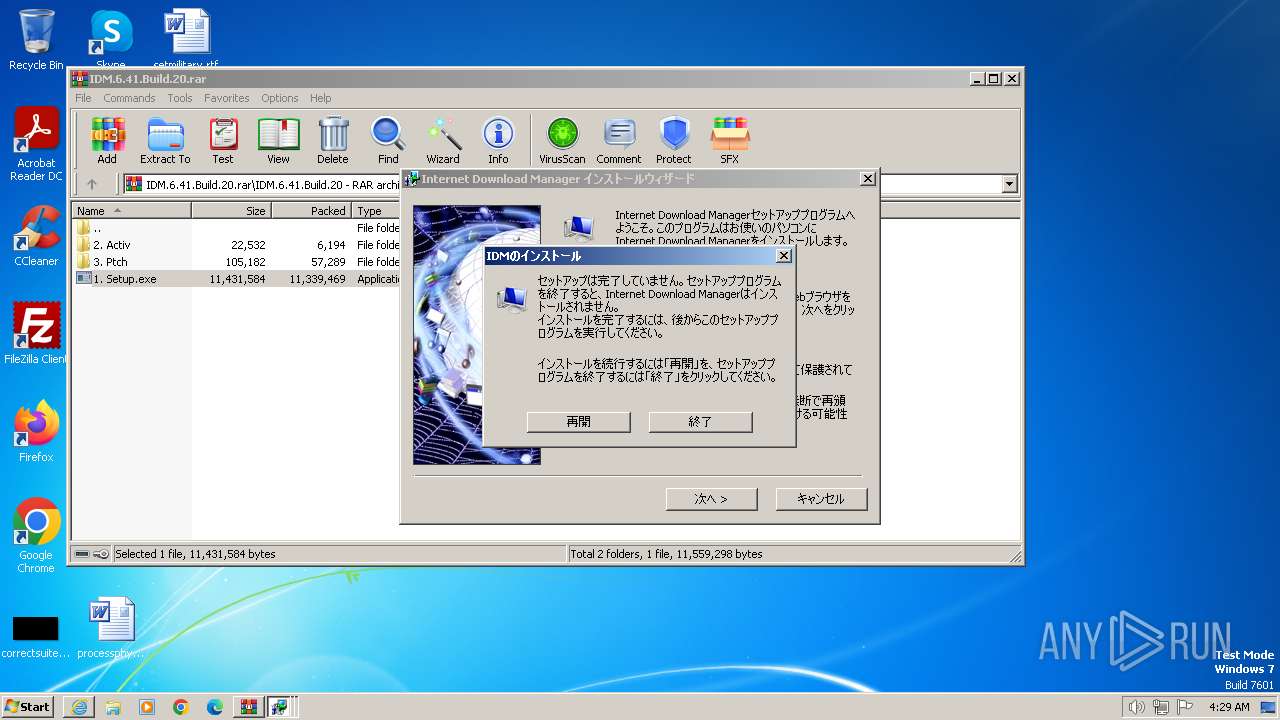
Drops the executable file immediately after the start
- IDMan.exe (PID: 1092)
Creates a writable file in the system directory
- rundll32.exe (PID: 3508)
Changes the autorun value in the registry
- rundll32.exe (PID: 3508)
- IDMan.exe (PID: 1092)
Starts NET.EXE for service management
- Uninstall.exe (PID: 3912)
- net.exe (PID: 2388)
SUSPICIOUS
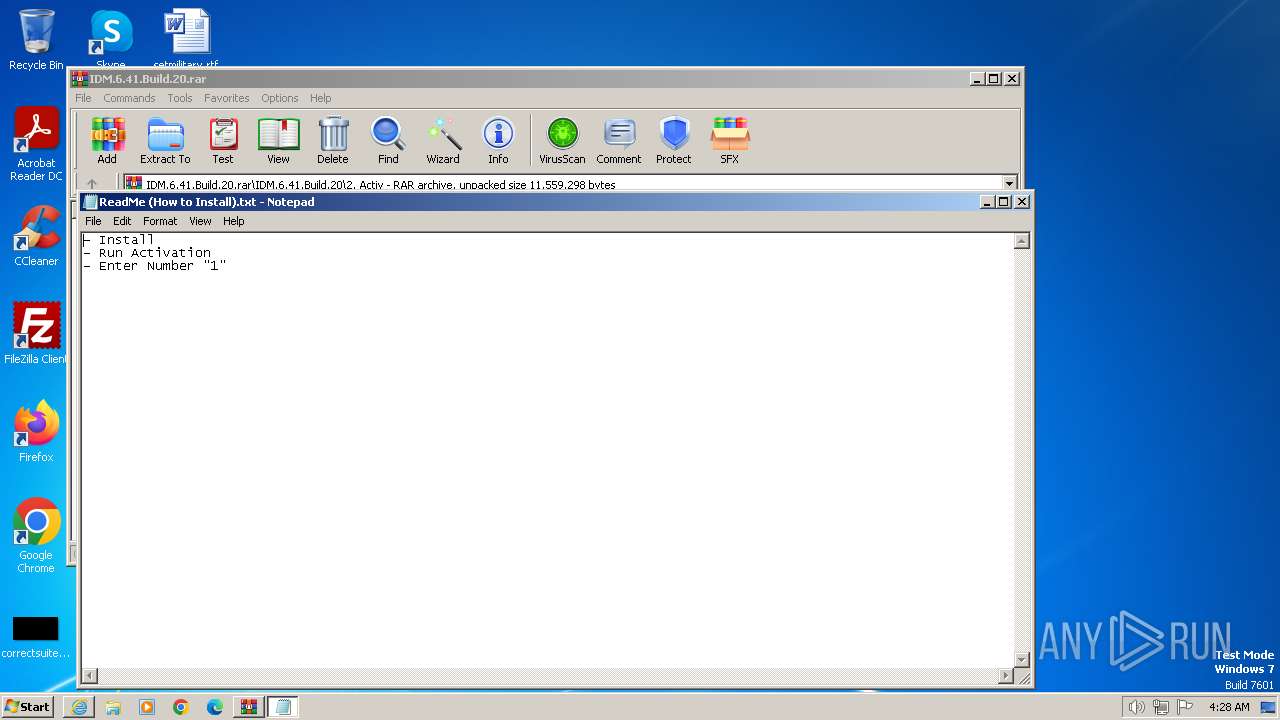
Executing commands from ".cmd" file
- WinRAR.exe (PID: 2724)
- powershell.exe (PID: 492)
Application launched itself
- cmd.exe (PID: 2260)
- cmd.exe (PID: 1596)
- WinRAR.exe (PID: 2724)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2724)
- cmd.exe (PID: 2260)
- powershell.exe (PID: 492)
- cmd.exe (PID: 1596)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2724)
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
- Uninstall.exe (PID: 3912)
- IDMan.exe (PID: 2228)
Hides command output
- cmd.exe (PID: 880)
- cmd.exe (PID: 2020)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 3504)
- cmd.exe (PID: 2640)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 880)
- cmd.exe (PID: 2020)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2260)
Reads the Internet Settings
- powershell.exe (PID: 492)
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
- Uninstall.exe (PID: 3912)
- runonce.exe (PID: 848)
- IDMan.exe (PID: 2228)
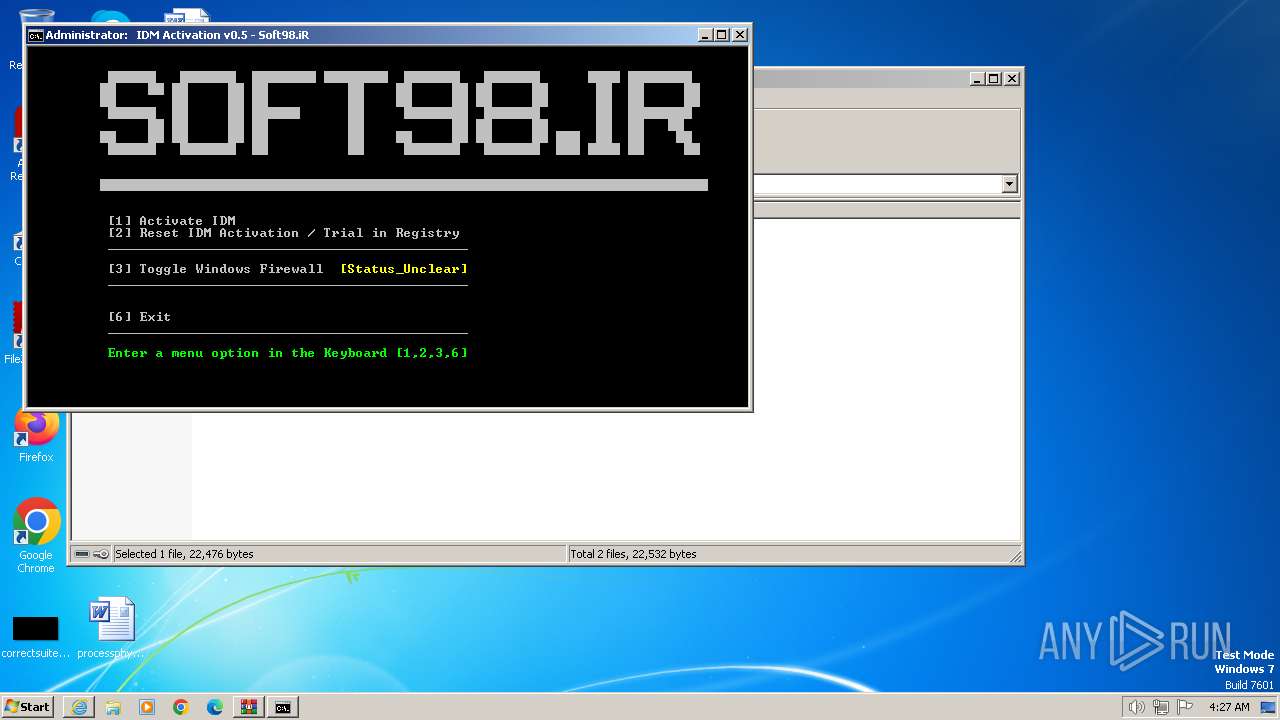
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2724)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1596)
Starts application with an unusual extension
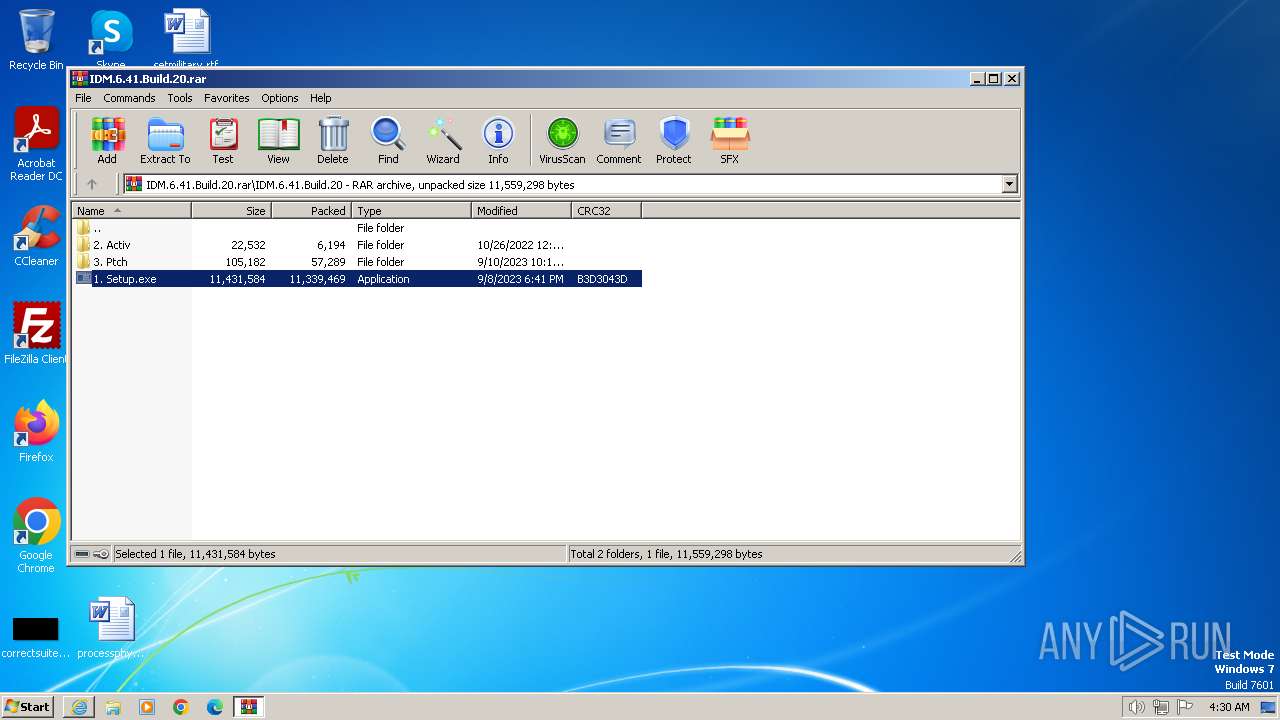
- 1. Setup.exe (PID: 2088)
- 1. Setup.exe (PID: 3364)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 3268)
Creates a software uninstall entry
- IDM1.tmp (PID: 3268)
Checks Windows Trust Settings
- IDMan.exe (PID: 1092)
- IDMan.exe (PID: 2228)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
- Uninstall.exe (PID: 3912)
Reads settings of System Certificates
- IDMan.exe (PID: 1092)
- IDMan.exe (PID: 2228)
Executable content was dropped or overwritten
- IDMan.exe (PID: 1092)
- rundll32.exe (PID: 3508)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 3912)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 3508)
Creates or modifies Windows services
- Uninstall.exe (PID: 3912)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2724)
- iexplore.exe (PID: 1696)
Application launched itself
- iexplore.exe (PID: 1696)
- firefox.exe (PID: 240)
- firefox.exe (PID: 2156)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1696)
Checks operating system version
- cmd.exe (PID: 2260)
- cmd.exe (PID: 1596)
Checks supported languages
- mode.com (PID: 2052)
- Patch.exe (PID: 668)
- 1. Setup.exe (PID: 2088)
- IDM1.tmp (PID: 3596)
- 1. Setup.exe (PID: 3364)
- IDM1.tmp (PID: 3268)
- idmBroker.exe (PID: 3276)
- IDMan.exe (PID: 1092)
- Uninstall.exe (PID: 3912)
- MediumILStart.exe (PID: 3032)
- IDMan.exe (PID: 2228)
- IEMonitor.exe (PID: 1836)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2724)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2724)
- rundll32.exe (PID: 3508)
Create files in a temporary directory
- 1. Setup.exe (PID: 2088)
- IDM1.tmp (PID: 3596)
- 1. Setup.exe (PID: 3364)
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
- IDMan.exe (PID: 2228)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 3596)
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
- MediumILStart.exe (PID: 3032)
- IDMan.exe (PID: 2228)
Creates files in the program directory
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
Creates files or folders in the user directory
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
Reads the computer name
- IDM1.tmp (PID: 3268)
- IDMan.exe (PID: 1092)
- Uninstall.exe (PID: 3912)
- IDMan.exe (PID: 2228)
- IEMonitor.exe (PID: 1836)
- MediumILStart.exe (PID: 3032)
Reads the software policy settings
- IDMan.exe (PID: 1092)
- IDMan.exe (PID: 2228)
Checks proxy server information
- IDMan.exe (PID: 1092)
Manual execution by a user
- firefox.exe (PID: 240)
Creates files in the driver directory
- rundll32.exe (PID: 3508)
Reads the time zone
- runonce.exe (PID: 848)
Reads security settings of Internet Explorer
- runonce.exe (PID: 848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
118
Monitored processes
64
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://www.internetdownloadmanager.com/support/installffextfrommozillasite.html --attempting-deelevation | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 316 | C:\Windows\system32\cmd.exe /c "prompt $H&for %B in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 492 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "start cmd.exe -arg '/c \""""C:\Users\admin\AppData\Local\Temp\Rar$DIa2724.5621\Activation.cmd""" -el \"' -verb runas" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 572 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2156.7.1678536682\57992673" -childID 6 -isForBrowser -prefsHandle 4204 -prefMapHandle 4208 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 924 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {0bae5ed2-f5f0-4e95-a763-5f328a2184d2} 2156 "\\.\pipe\gecko-crash-server-pipe.2156" 4012 18e93560 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
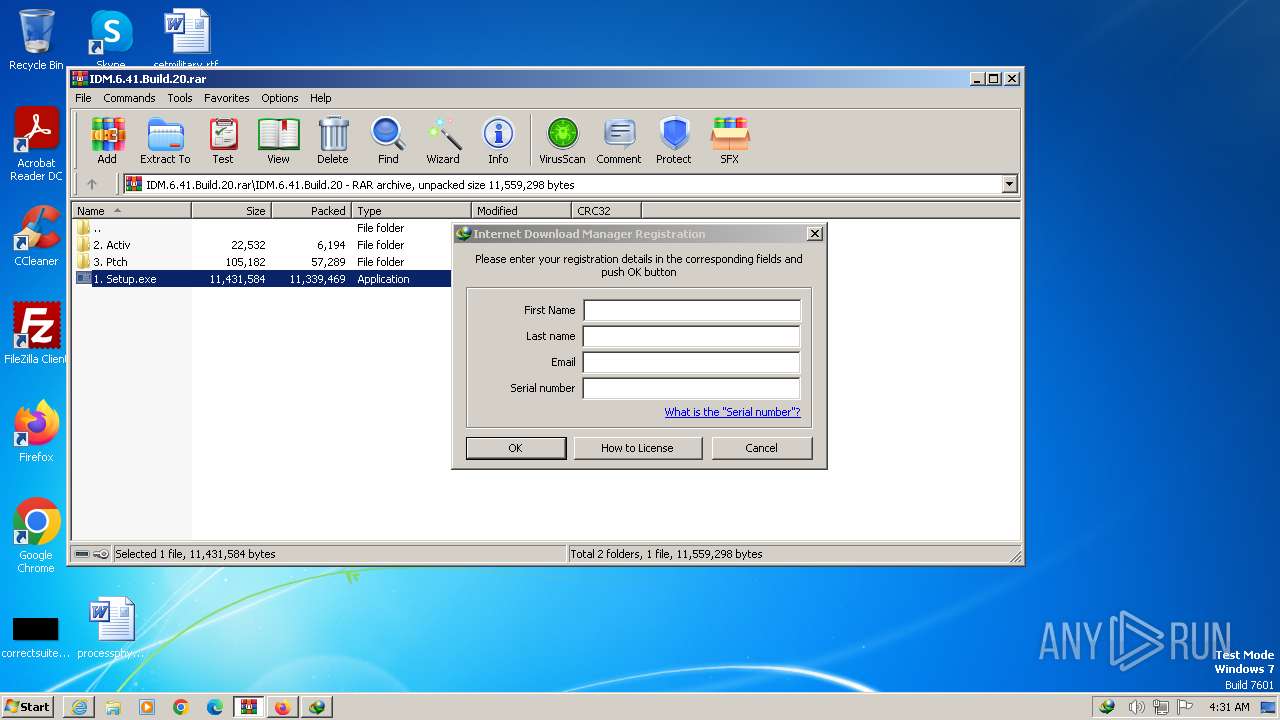
| 668 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2724.11926\IDM.6.41.Build.20\3. Ptch\Patch.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2724.11926\IDM.6.41.Build.20\3. Ptch\Patch.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 764 | reg query HKU\S-1-5-19 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | findstr /a:0E /f:`.txt "." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | C:\Windows\system32\cmd.exe /c reg query "HKCU\Software\DownloadManager" /v ExePath 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 924 | find /i "x86" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
62 131
Read events
61 276
Write events
727
Delete events
128
Modification events
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31095020 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31095020 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
18
Suspicious files
107
Text files
60
Unknown types
64
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\IDM.6.41.Build.20.rar.v3k9p51.partial | — | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{CC364454-E4DF-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:15AB0BA3CBA5C4D881B4FABD169FFA6C | SHA256:92EC56EB22A255406AC43415A551FC891E742ABC5B952BF048F00E52BDF00047 | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\IDM.6.41.Build.20.rar | — | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\IDM.6.41.Build.20[1].rar | compressed | |
MD5:758E34F2F1F5D95D0A80F7168FDD35ED | SHA256:B2412AB0B08E73F766E1177768E076678CB24A5874C13908B9F3C5C5360CB260 | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:525F4B85FD27497D2E1A276877A8A752 | SHA256:85450D167111AD556F7111DC2CC3759F805CFB7E92A958385760C25ACBC94813 | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7F6C.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:57611D4A5C32EC82FBAF56662BD4B6C3 | SHA256:B6B56DD36B4629981D9EFA1EC1D05AA7B202000AA80F2187E4FE03163B0C30C1 | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7F6D.tmp | cat | |
MD5:DD73CEAD4B93366CF3465C8CD32E2796 | SHA256:A6752B7851B591550E4625B832A393AABCC428DE18D83E8593CD540F7D7CAE22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
102
DNS requests
155
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2692 | iexplore.exe | GET | 304 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 304 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?12f52c1127979e35 | unknown | — | — | unknown |
2692 | iexplore.exe | GET | 200 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a08f35fbea17b647 | unknown | compressed | 67.5 Kb | unknown |
1696 | iexplore.exe | GET | 304 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?719f0b64dcb4a601 | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl4.digicert.com/DigiCertGlobalRootCA.crl | unknown | binary | 779 b | unknown |
1696 | iexplore.exe | GET | 304 | 23.53.40.49:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70d85e3b0e586cab | unknown | — | — | unknown |
2156 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2156 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
2156 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2692 | iexplore.exe | 50.7.24.66:443 | — | COGENT-174 | NL | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1696 | iexplore.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2692 | iexplore.exe | 50.7.236.50:443 | — | COGENT-174 | NL | unknown |
2692 | iexplore.exe | 23.53.40.35:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2692 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
1696 | iexplore.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1696 | iexplore.exe | 23.53.40.35:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pixeldrain.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
dns.msftncsi.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
2692 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
2692 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
2692 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (pixeldrain .com) |