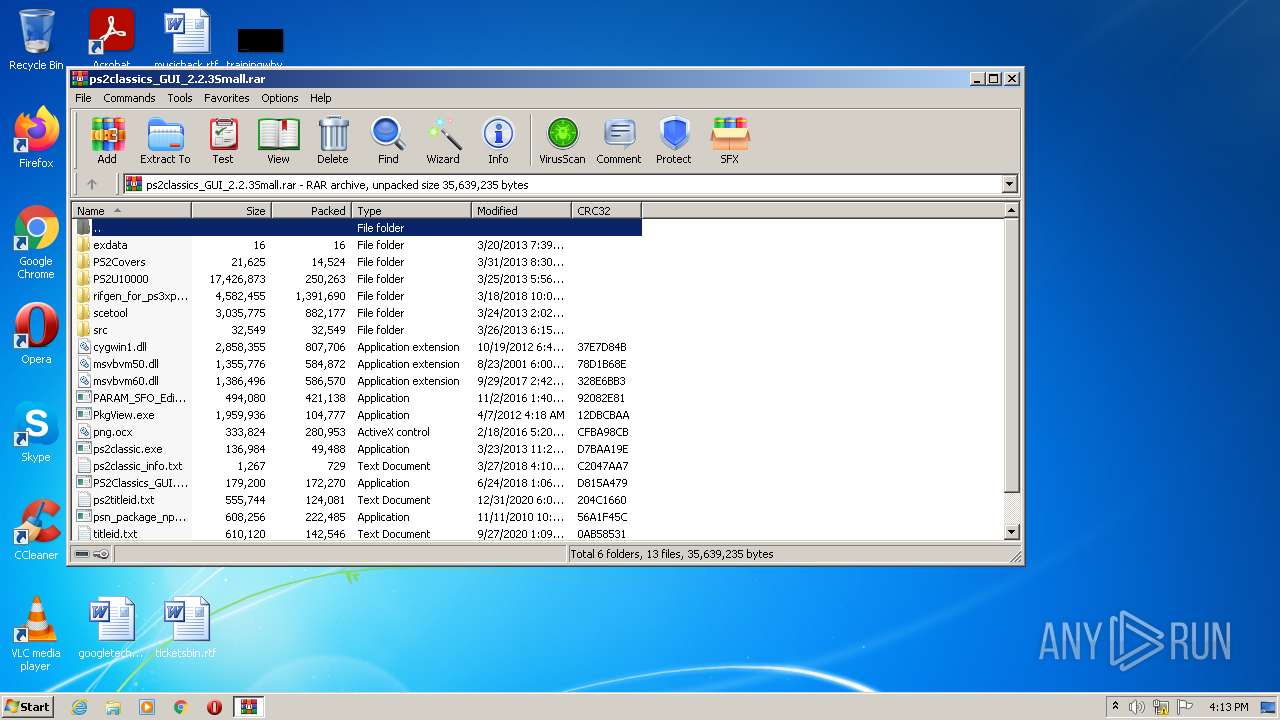
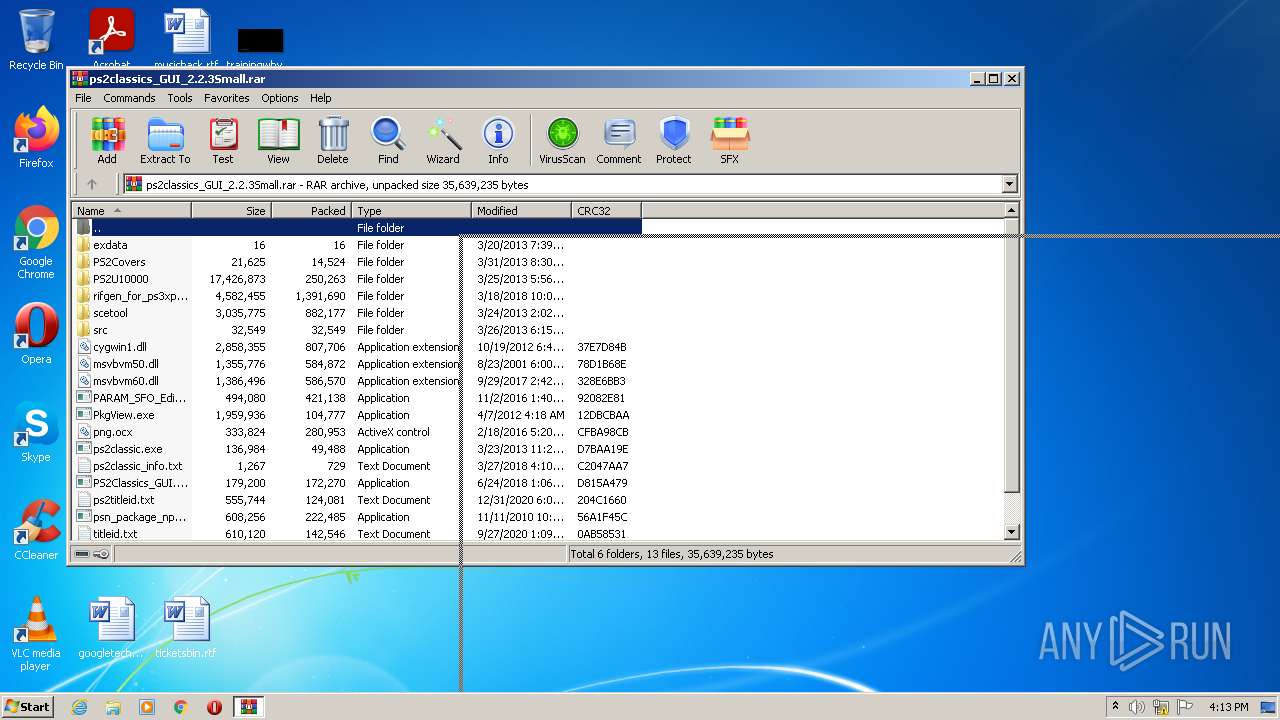
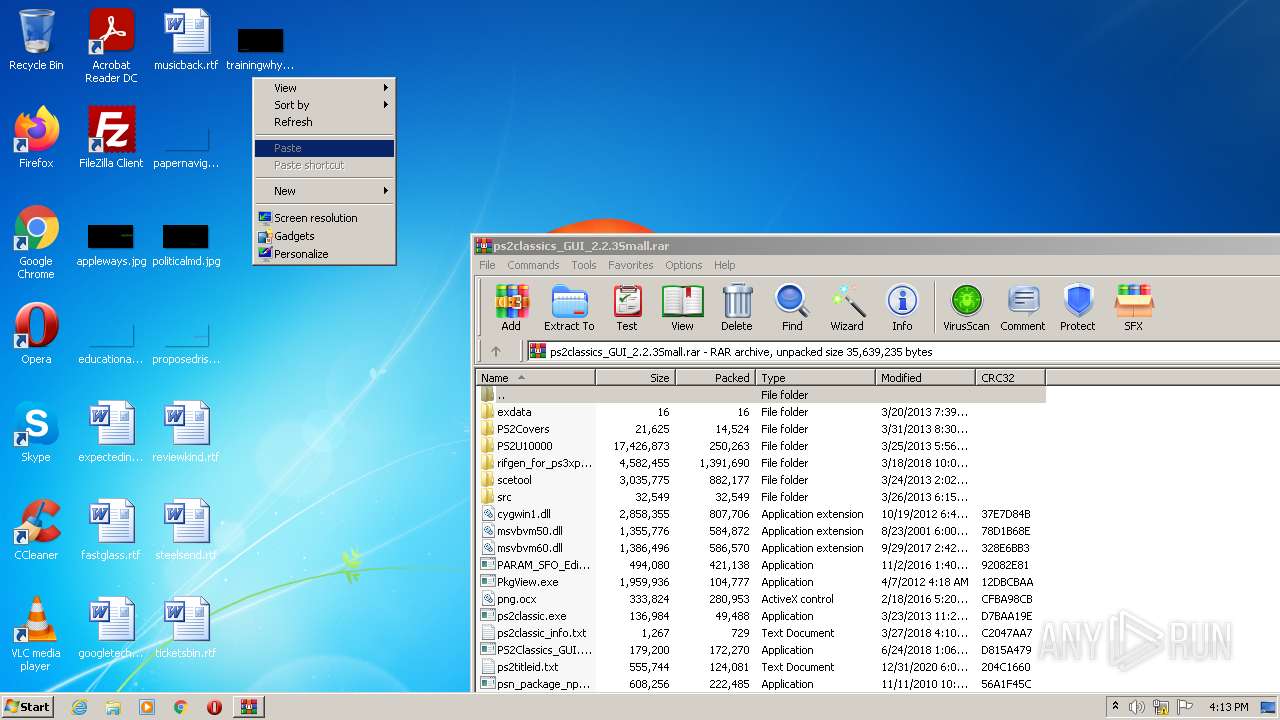
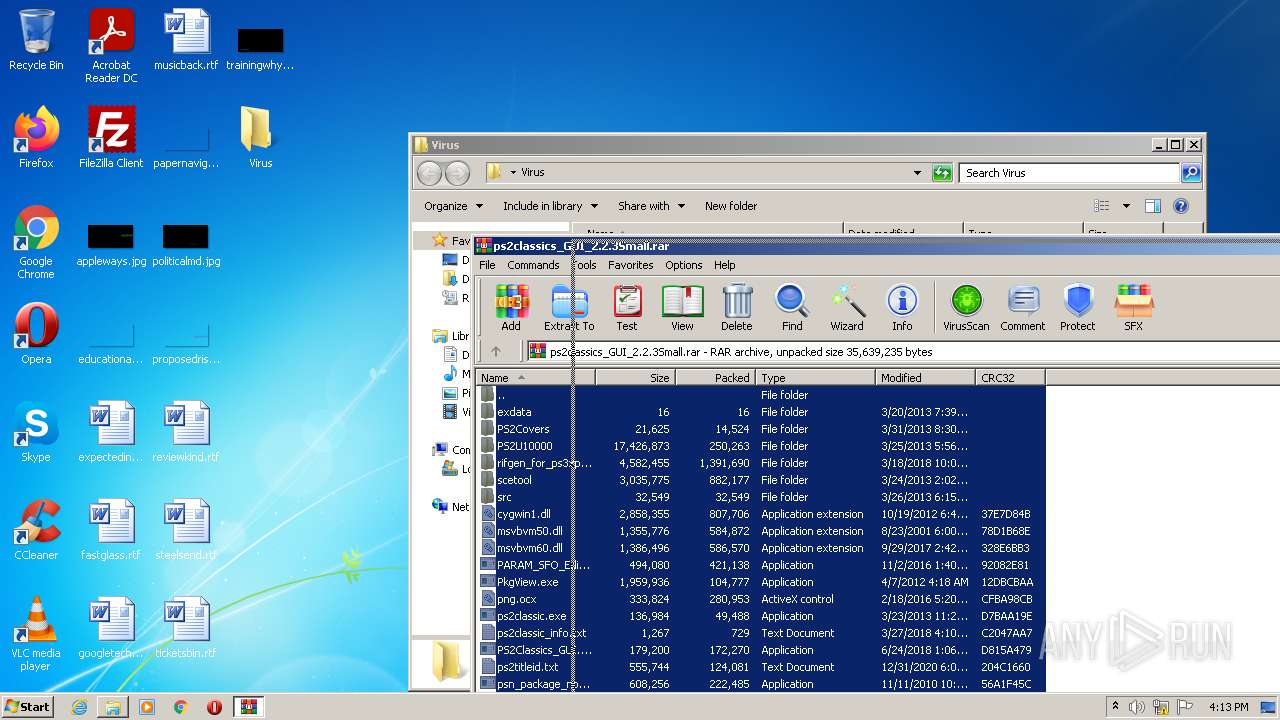
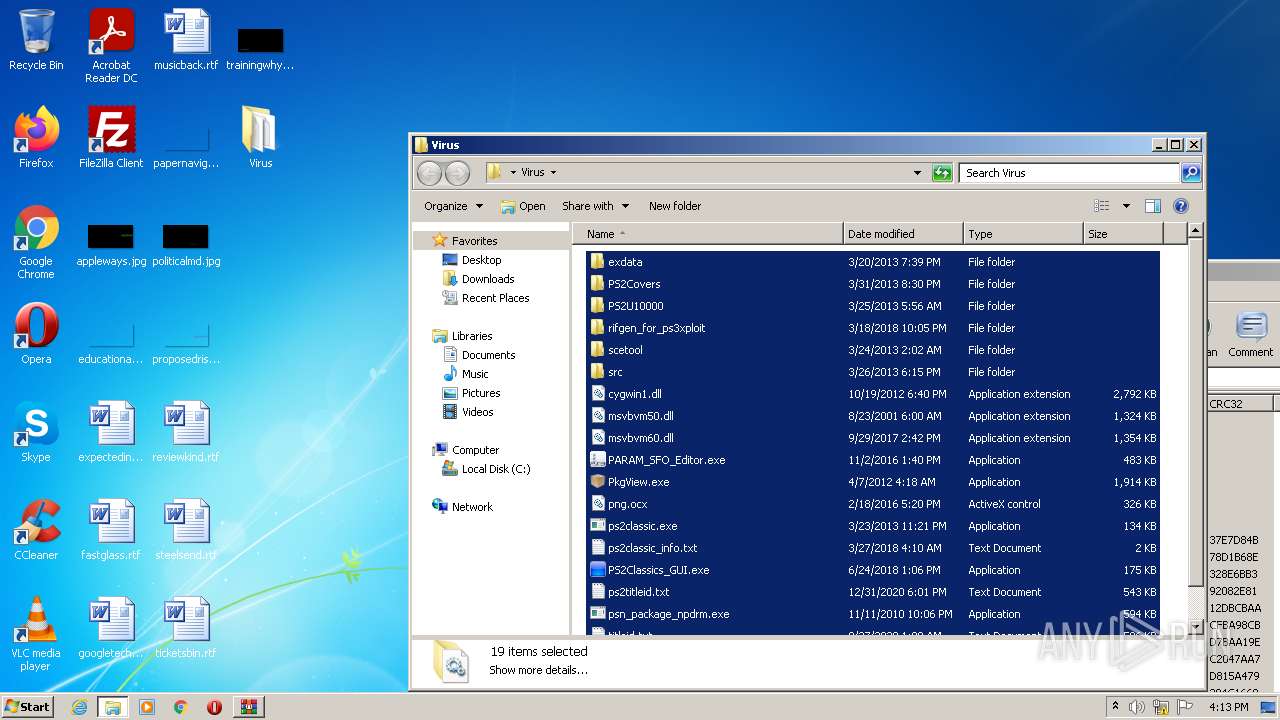
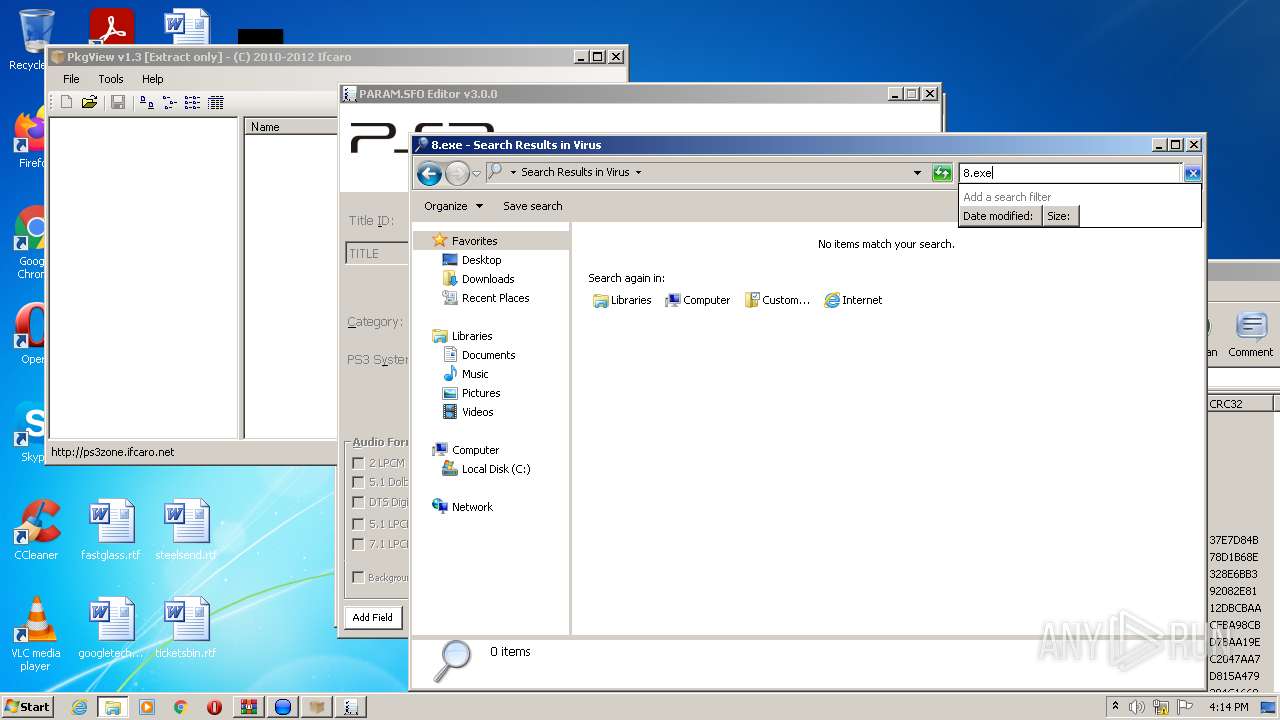
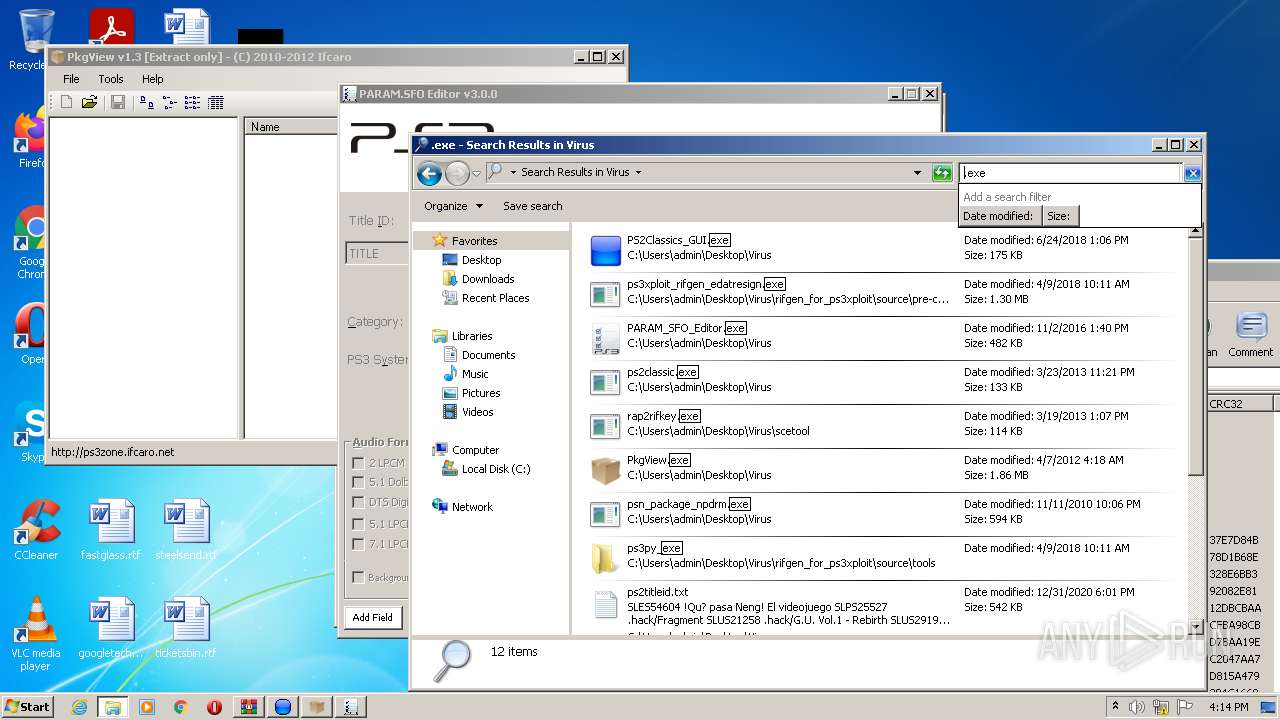
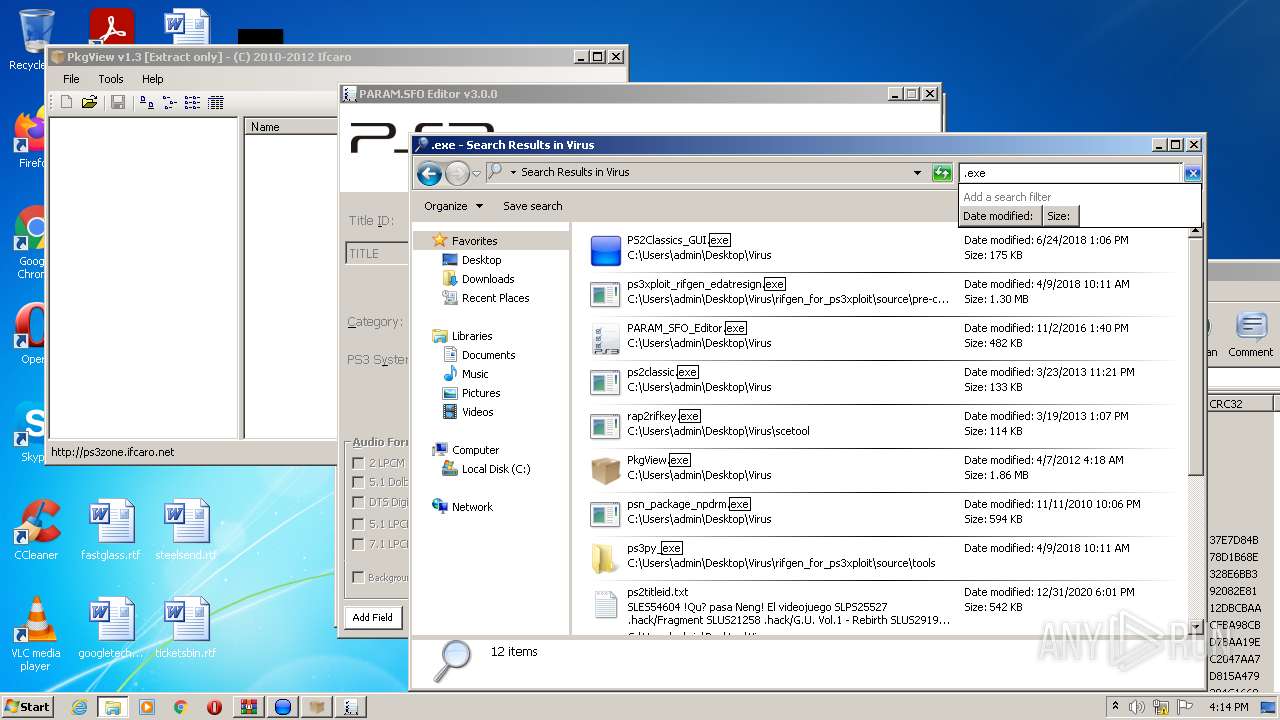
| File name: | ps2classics_GUI_2.2.3Small.rar |
| Full analysis: | https://app.any.run/tasks/a93bad0a-ed59-439c-bd8d-488143149925 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2022, 15:13:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 9C14F5D1BA60F717BDA8F14F0EBC47C5 |
| SHA1: | 685CCC54492603E99F8101B938CA7156A66169DB |
| SHA256: | F0CC726C0D0B18AB21F0C8DBB9263C7C9F9BA0A8B32FB38056E7B1F7A8F6BBE4 |
| SSDEEP: | 98304:ZMJtAU4PhcXtIGm0f2Xl55pmm9njAUfQrnu64fl+J5GdBpyJRn+5IqwEOMK3n:Cz4POmGfuXl55xnjAUfyu6ew+dQR+5Ip |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2284)
- PS2Classics_GUI.exe (PID: 3588)
- ps2classic.exe (PID: 2404)
- PARAM_SFO_Editor.exe (PID: 1204)
- Explorer.EXE (PID: 1464)
- ps2classic.exe (PID: 3984)
- PARAM_SFO_Editor.exe (PID: 184)
- ps3xploit_rifgen_edatresign.exe (PID: 3112)
- PS2Classics_GUI.exe (PID: 2620)
- rap2rifkey.exe (PID: 920)
Detects Cygwin installation
- WinRAR.exe (PID: 2992)
Drops executable file immediately after starts
- Explorer.EXE (PID: 1464)
- WinRAR.exe (PID: 2992)
Application was dropped or rewritten from another process
- PS2Classics_GUI.exe (PID: 3588)
- ps2classic.exe (PID: 2404)
- PkgView.exe (PID: 2788)
- PARAM_SFO_Editor.exe (PID: 1204)
- psn_package_npdrm.exe (PID: 4000)
- psn_package_npdrm.exe (PID: 2656)
- PkgView.exe (PID: 1928)
- PARAM_SFO_Editor.exe (PID: 184)
- ps3xploit_rifgen_edatresign.exe (PID: 3112)
- PS2Classics_GUI.exe (PID: 2620)
- rap2rifkey.exe (PID: 920)
- ps2classic.exe (PID: 3984)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2992)
- PS2Classics_GUI.exe (PID: 3588)
- ps2classic.exe (PID: 2404)
- PkgView.exe (PID: 2788)
- PARAM_SFO_Editor.exe (PID: 1204)
- psn_package_npdrm.exe (PID: 2656)
- psn_package_npdrm.exe (PID: 4000)
- PkgView.exe (PID: 1928)
- ps2classic.exe (PID: 3984)
- PARAM_SFO_Editor.exe (PID: 184)
- ps3xploit_rifgen_edatresign.exe (PID: 3112)
- PS2Classics_GUI.exe (PID: 2620)
- rap2rifkey.exe (PID: 920)
Reads the computer name
- WinRAR.exe (PID: 2992)
- PS2Classics_GUI.exe (PID: 3588)
- PARAM_SFO_Editor.exe (PID: 1204)
- PARAM_SFO_Editor.exe (PID: 184)
- ps3xploit_rifgen_edatresign.exe (PID: 3112)
- PS2Classics_GUI.exe (PID: 2620)
- PkgView.exe (PID: 1928)
- PkgView.exe (PID: 2788)
Drops a file with a compile date too recent
- Explorer.EXE (PID: 1464)
- WinRAR.exe (PID: 2992)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 2284)
- WinRAR.exe (PID: 2992)
- Explorer.EXE (PID: 1464)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2992)
INFO
Manual execution by user
- PS2Classics_GUI.exe (PID: 3588)
- ps2classic.exe (PID: 2404)
- PkgView.exe (PID: 2788)
- PARAM_SFO_Editor.exe (PID: 1204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
56
Monitored processes
15
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
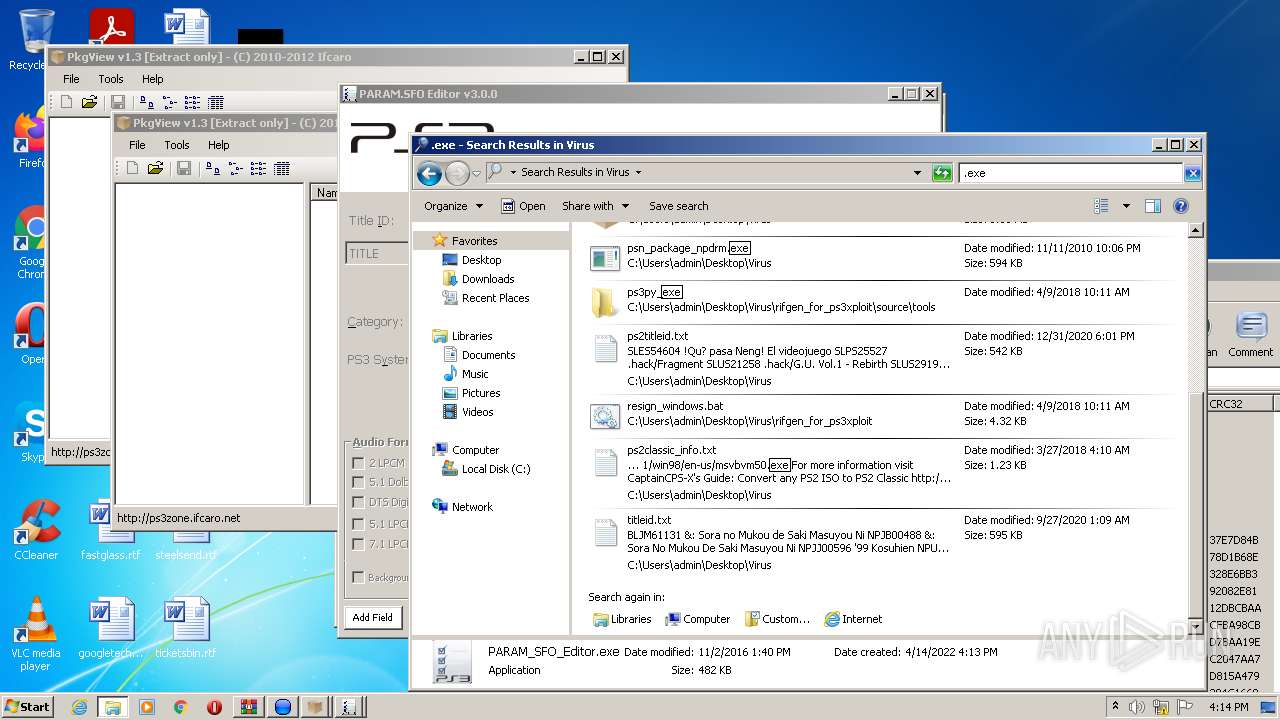
| 184 | "C:\Users\admin\Desktop\Virus\PARAM_SFO_Editor.exe" | C:\Users\admin\Desktop\Virus\PARAM_SFO_Editor.exe | — | Explorer.EXE | |||||||||||
User: admin Company: aldostools.org Integrity Level: MEDIUM Description: PARAM.SFO Editor Exit code: 0 Version: 3.00 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\Virus\scetool\rap2rifkey.exe" | C:\Users\admin\Desktop\Virus\scetool\rap2rifkey.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1204 | "C:\Users\admin\Desktop\Virus\PARAM_SFO_Editor.exe" | C:\Users\admin\Desktop\Virus\PARAM_SFO_Editor.exe | — | Explorer.EXE | |||||||||||
User: admin Company: aldostools.org Integrity Level: MEDIUM Description: PARAM.SFO Editor Exit code: 0 Version: 3.00 Modules
| |||||||||||||||
| 1464 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\Desktop\Virus\PkgView.exe" | C:\Users\admin\Desktop\Virus\PkgView.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: PkgView Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2284 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2404 | "C:\Users\admin\Desktop\Virus\ps2classic.exe" | C:\Users\admin\Desktop\Virus\ps2classic.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\Desktop\Virus\PS2Classics_GUI.exe" | C:\Users\admin\Desktop\Virus\PS2Classics_GUI.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Aldo Vargas - http://www.aldostools.org Integrity Level: MEDIUM Description: PS3Classics GUI Exit code: 0 Version: 2.02.0003 Modules
| |||||||||||||||
| 2656 | "C:\Users\admin\Desktop\Virus\psn_package_npdrm.exe" | C:\Users\admin\Desktop\Virus\psn_package_npdrm.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967294 Modules
| |||||||||||||||
| 2788 | "C:\Users\admin\Desktop\Virus\PkgView.exe" | C:\Users\admin\Desktop\Virus\PkgView.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: PkgView Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
Total events
12 684
Read events
12 012
Write events
670
Delete events
2
Modification events
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ps2classics_GUI_2.2.3Small.rar | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
25
Suspicious files
10
Text files
33
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\src\pkg2zip_aes.h | text | |
MD5:9DAEAEE3056AFEAB5A9952FD81008F31 | SHA256:70160253DA9E907D90A36373BD6166C1D7EEA99E71665A503FAB45D57F495B7D | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\src\aes_omac.h | text | |
MD5:5660F4E1F814FC0A7BD2770A8BADC7C0 | SHA256:FA14BBB9CF9FB3E8209649685574BA0B5658739600FF66BB7DD08A42AD2C7BE6 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\src\Makefile | text | |
MD5:E078D7C8191ADDCECD44A47293FF1D7D | SHA256:F028390992D5F62FE038E099C3F7CEA1EA758AC38C1752FF9E0EB9116EBB3DE4 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\src\aes_omac.cpp | text | |
MD5:02A6A3DBB945B14CCD5B84CFCC5EAA53 | SHA256:20CF4D132309274C793F4F8E8E39F90298FD0A0F255A0518FAAC7CC4E200D4A5 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\src\pkg2zip_aes_x86.h | text | |
MD5:D77C17EEBCE3421606D0399A02D81CBD | SHA256:D7D6E939886CC1539E1529A31D6AC79F5EB7E4CC9A1FE0B2A4C1F159CB53343D | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\LICENSE | text | |
MD5:D32239BCB673463AB874E80D47FAE504 | SHA256:8CEB4B9EE5ADEDDE47B31E975C1D90C73AD27B6B165A1DCD80C7C545EB65B903 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\src\aes.c | text | |
MD5:3EF189AFA1637AD848986D8B8AC7A70F | SHA256:476328A2FDDE5462C06E108550022B923A5A36981E7CFA42834D6594F873AF4D | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\source\pre-compiled\windows\ps3xploit_rifgen_edatresign.exe | executable | |
MD5:4936C630FF882560A64481BEA7B0E8AA | SHA256:90C2901241ED3E61A4657A3922FED212600406E5CEA16F18B3DBEB8E28844F97 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\resign_windows.bat | text | |
MD5:7BB672EDC0D80F69F089EA5414BB33AB | SHA256:B26CA1FA2E27A24C15D31AEE818DB003DE64D2C6259C1931C65C6C48A6698094 | |||
| 2992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2992.38208\rifgen_for_ps3xploit\README.md | html | |
MD5:FCBEEE920905A6FBEE315E5288AF35B8 | SHA256:D9A1C5CAC7B18E60D98D24B5D89A36478D97A5599BB4E7AA38E8F6326F7FC6F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report