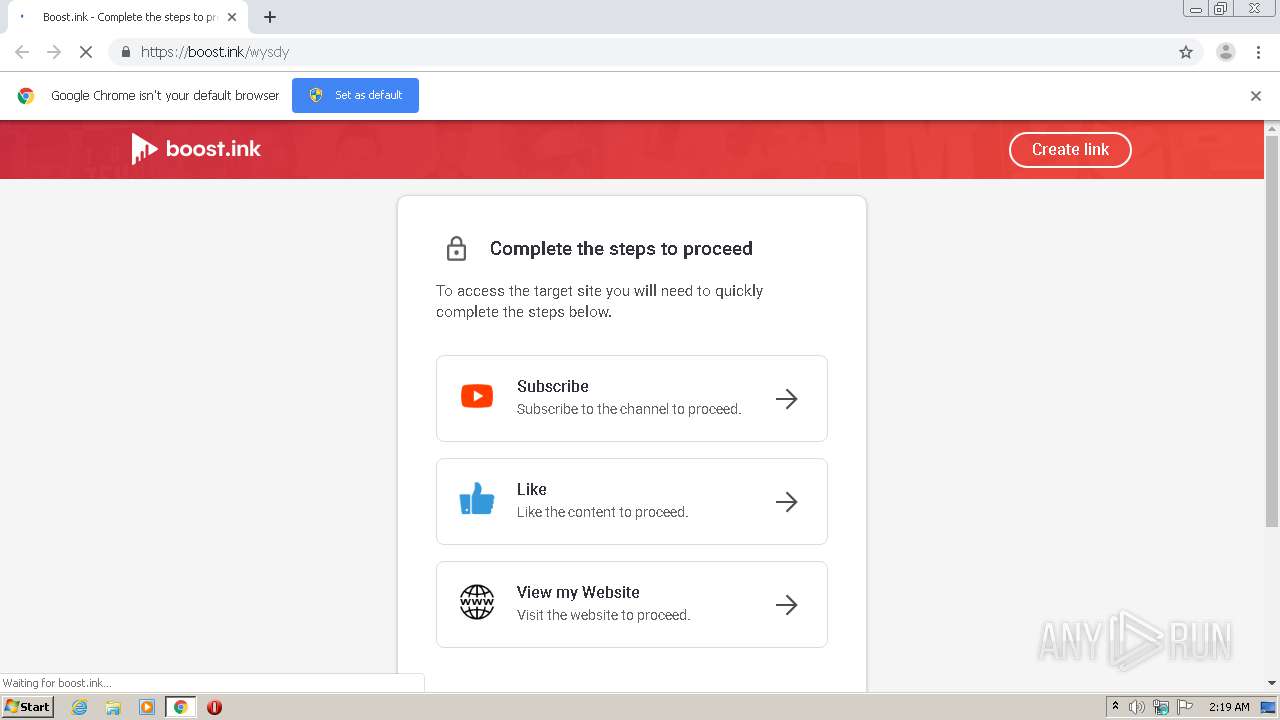
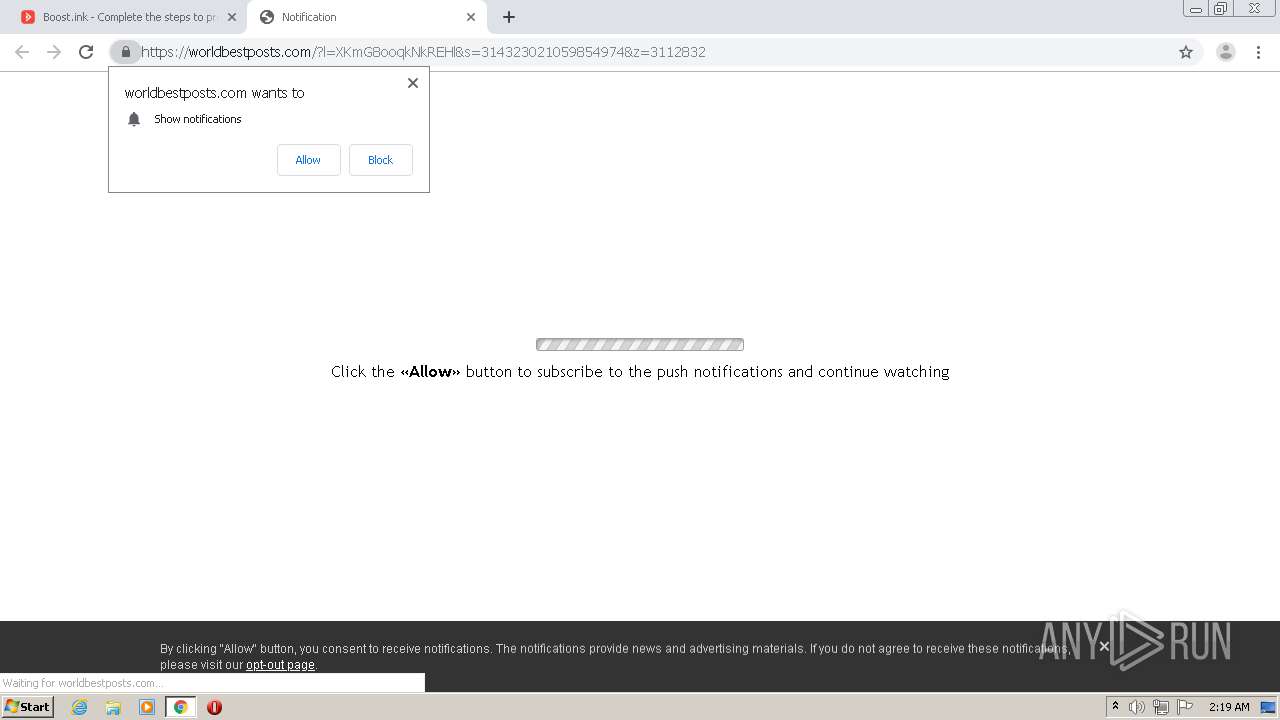
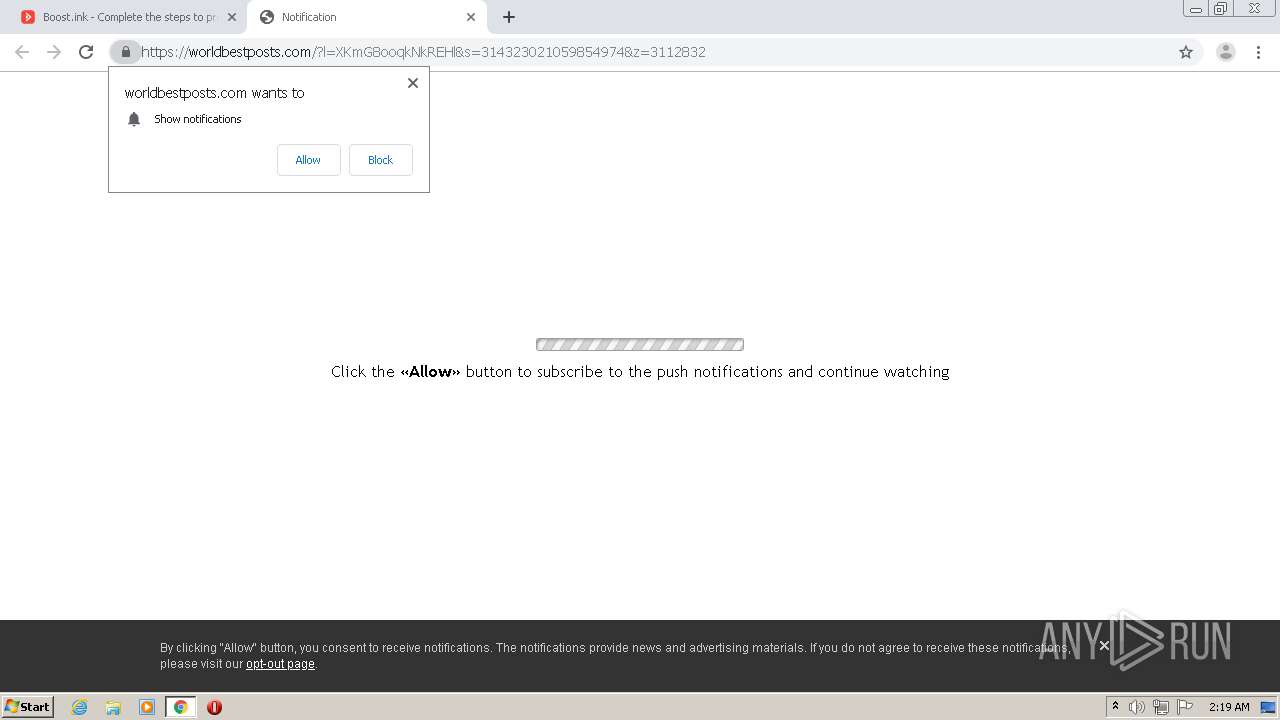
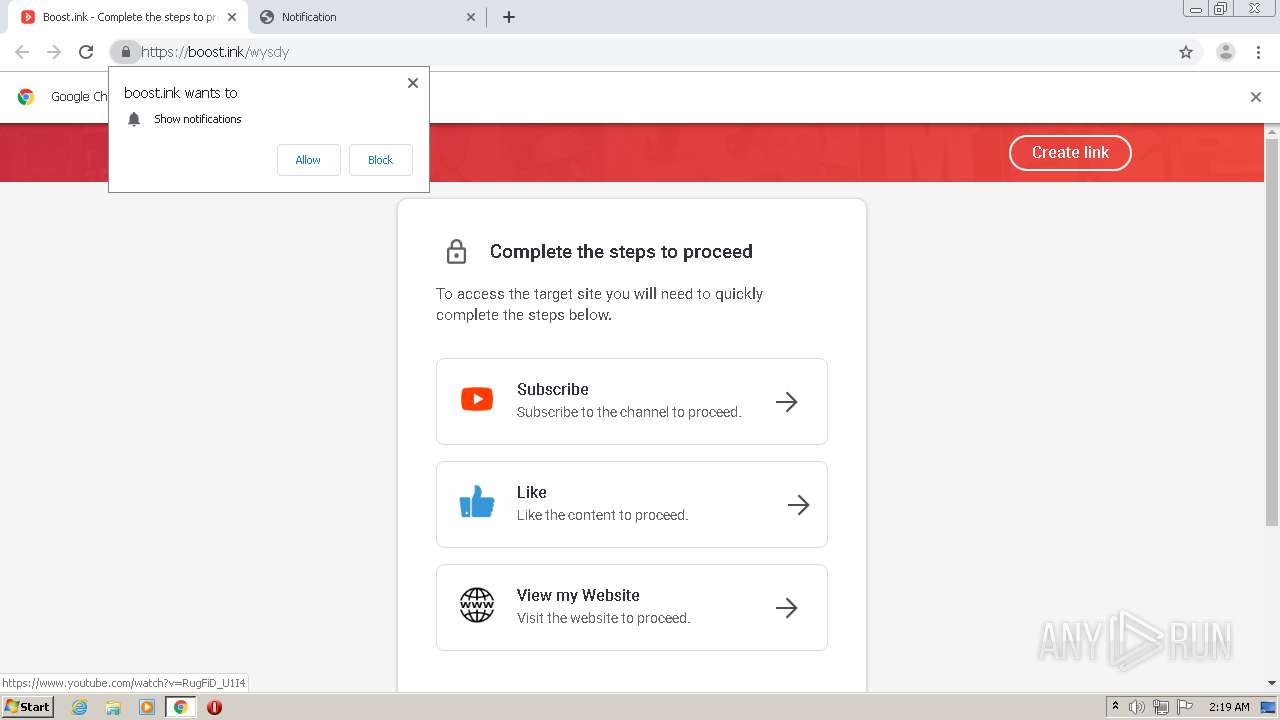
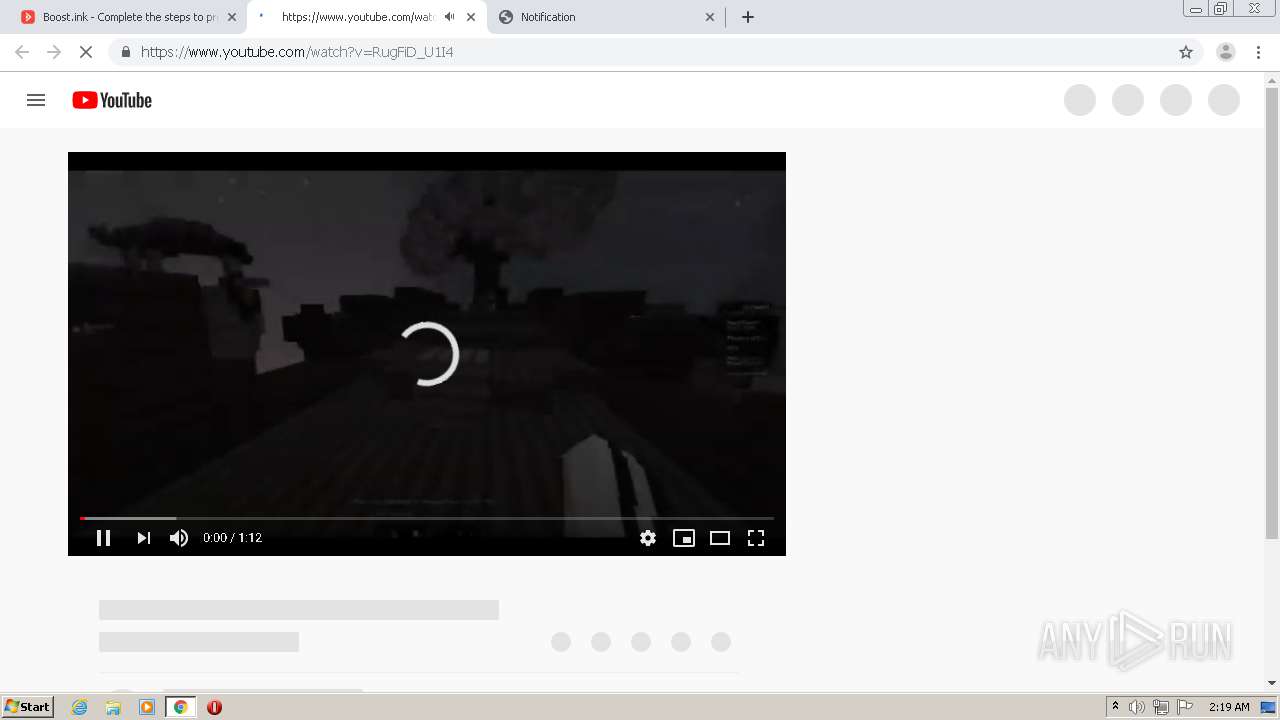
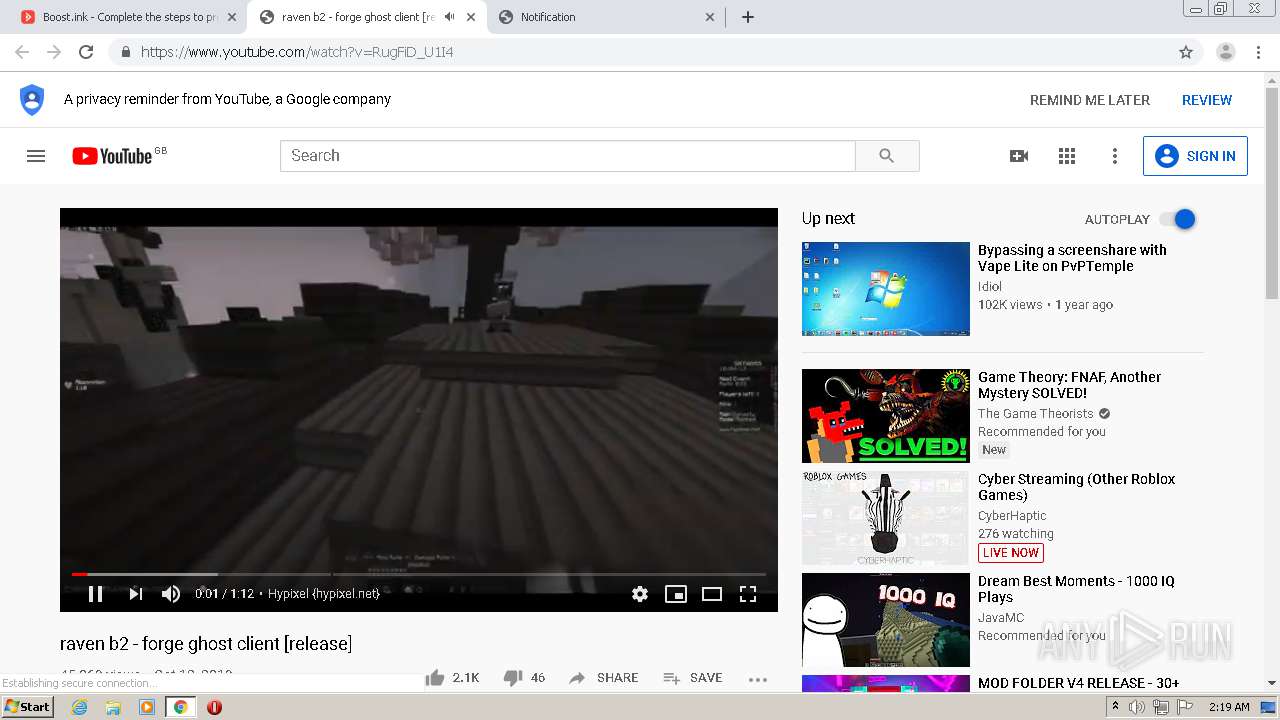
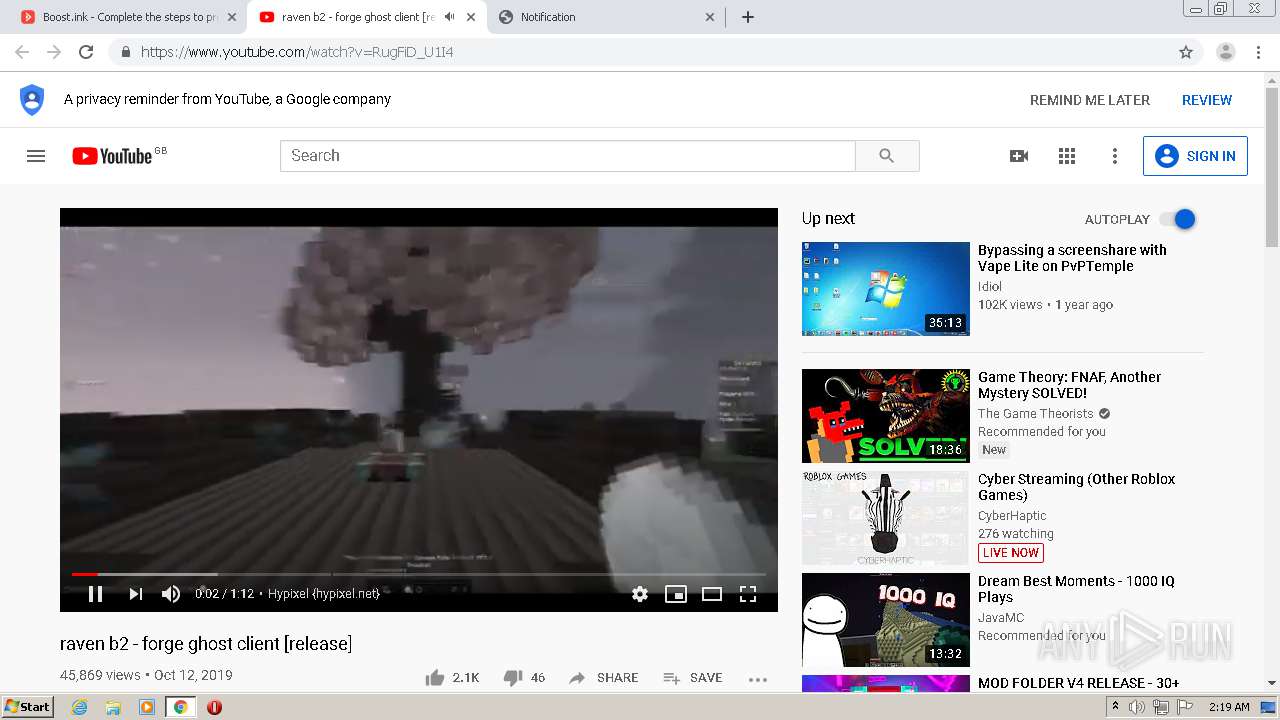
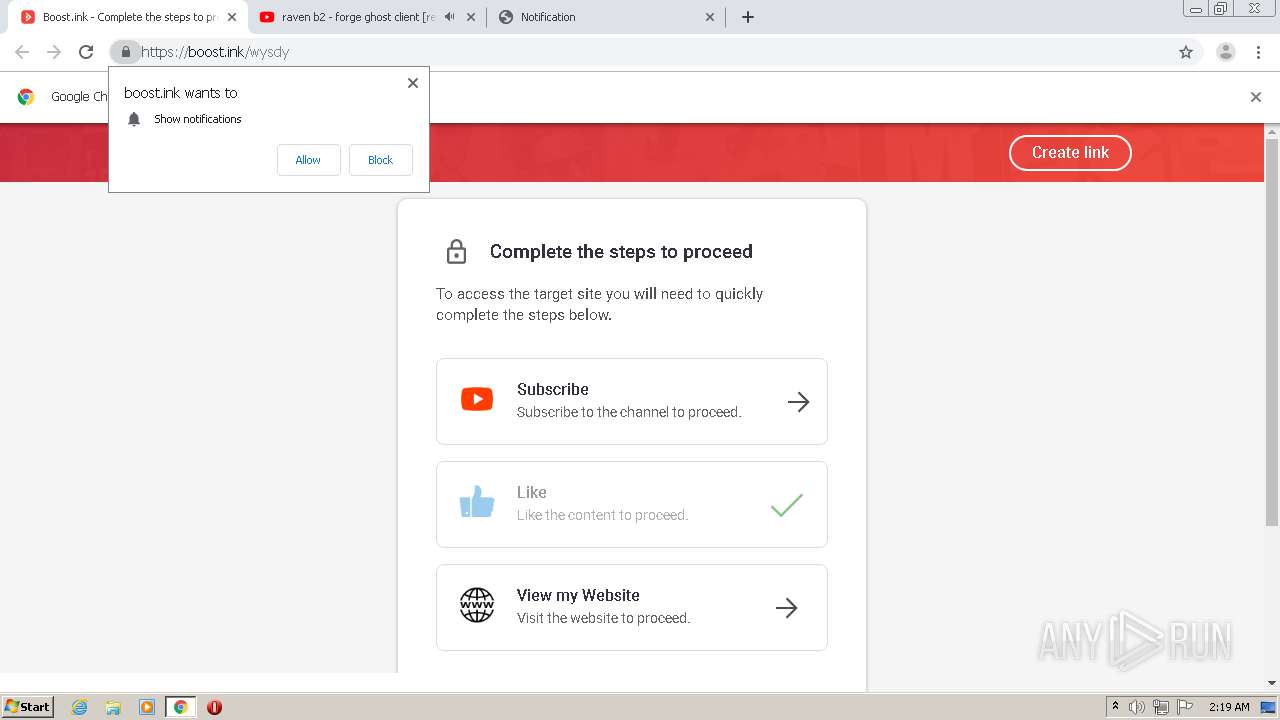
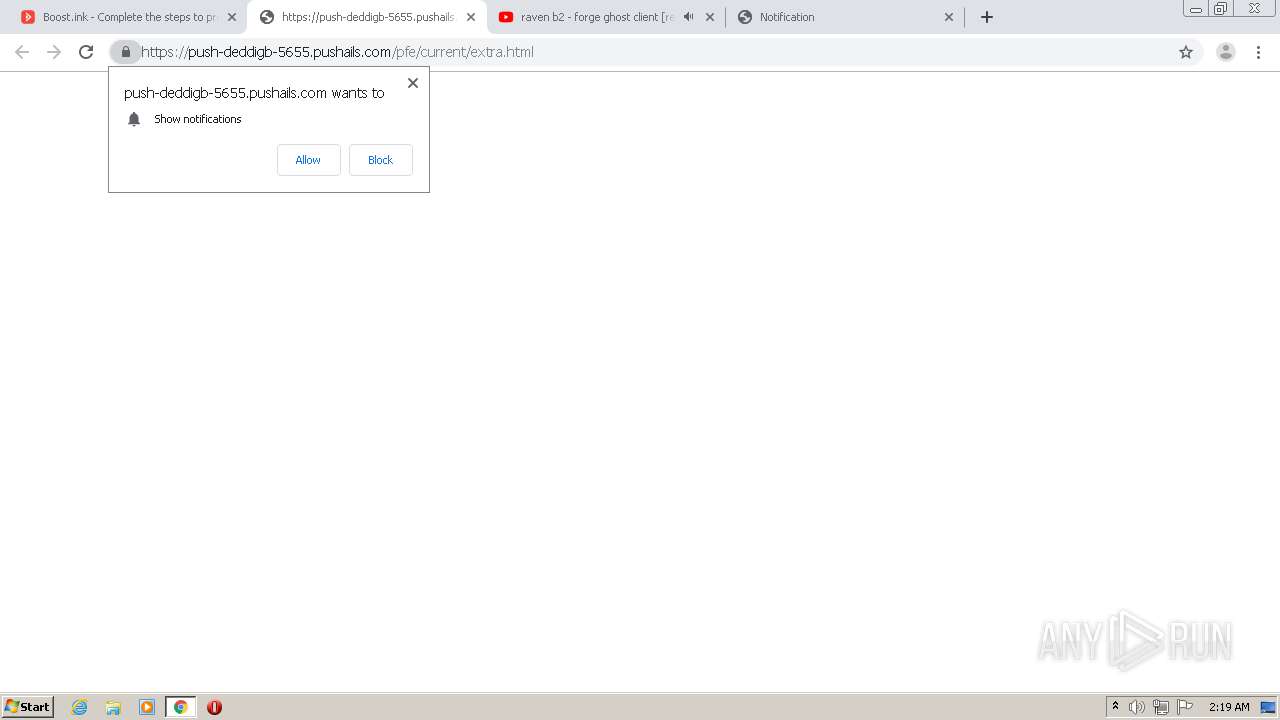
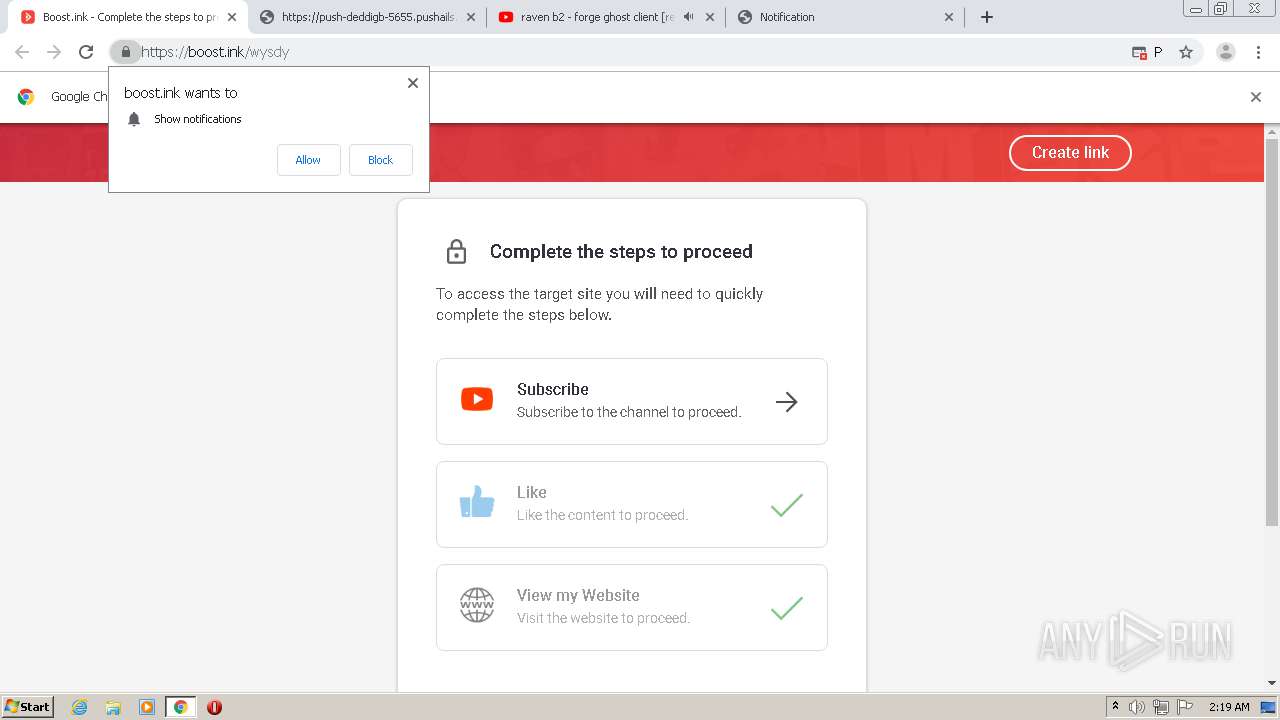
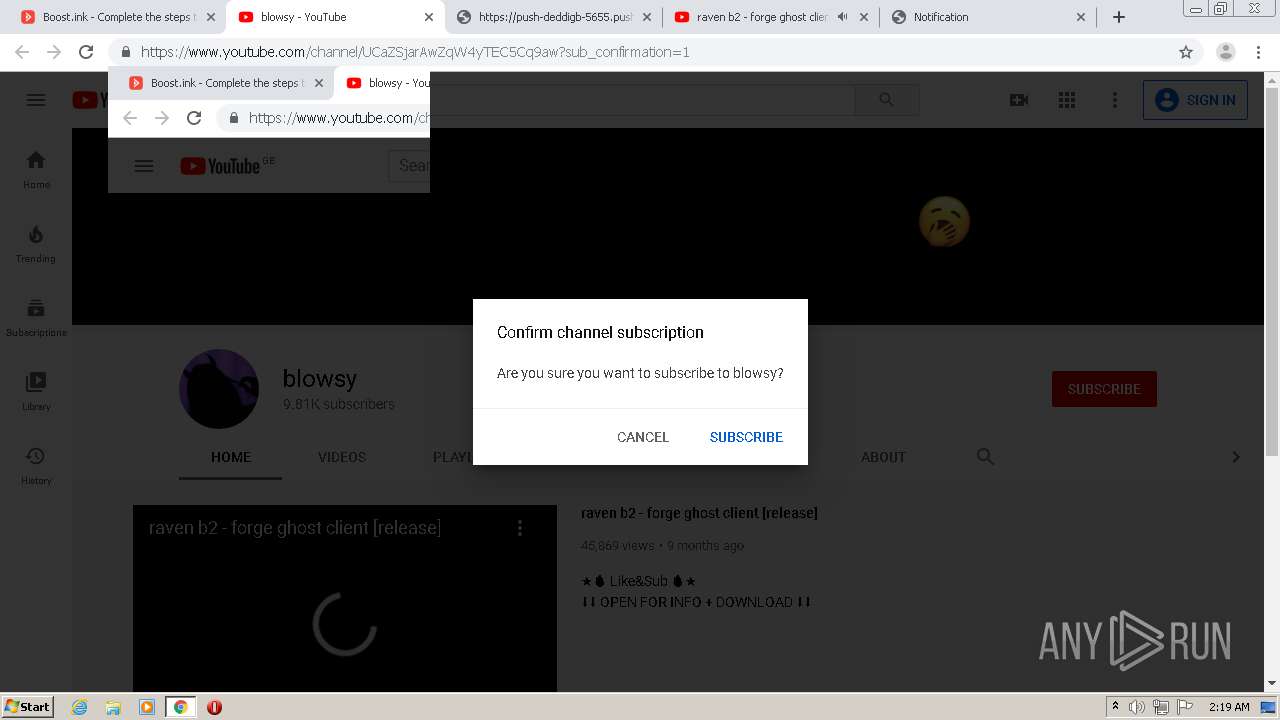
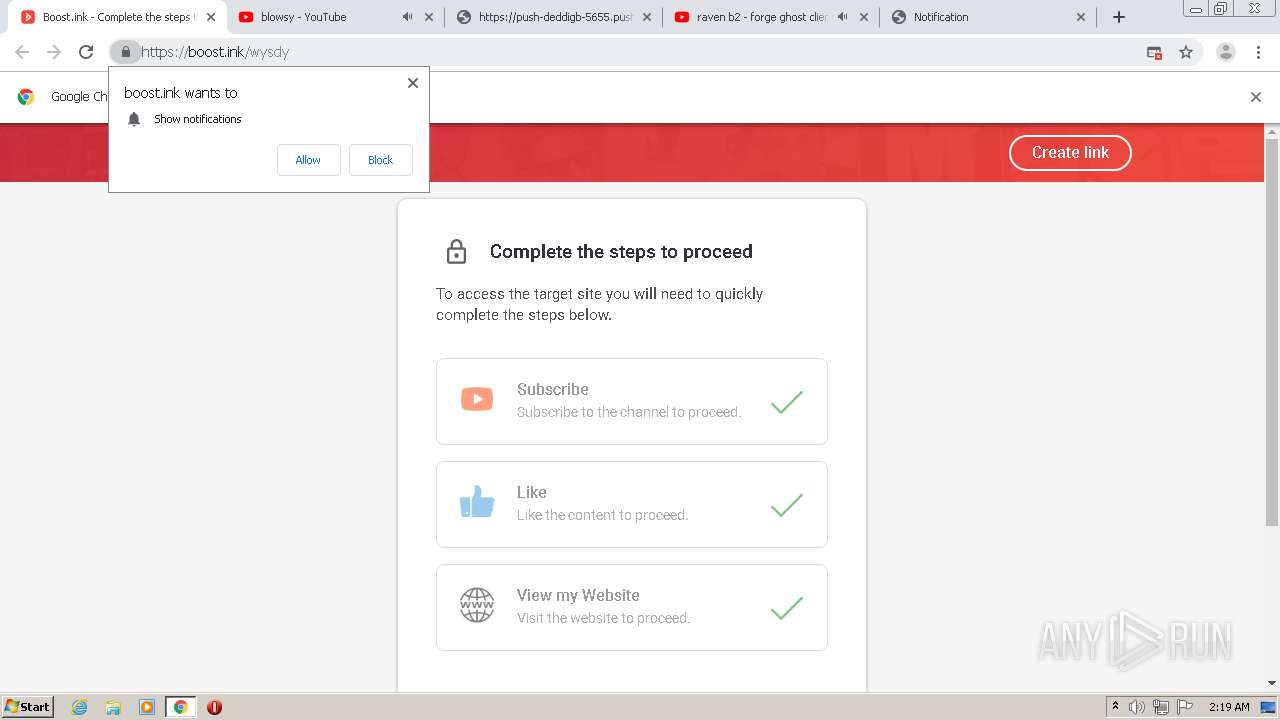
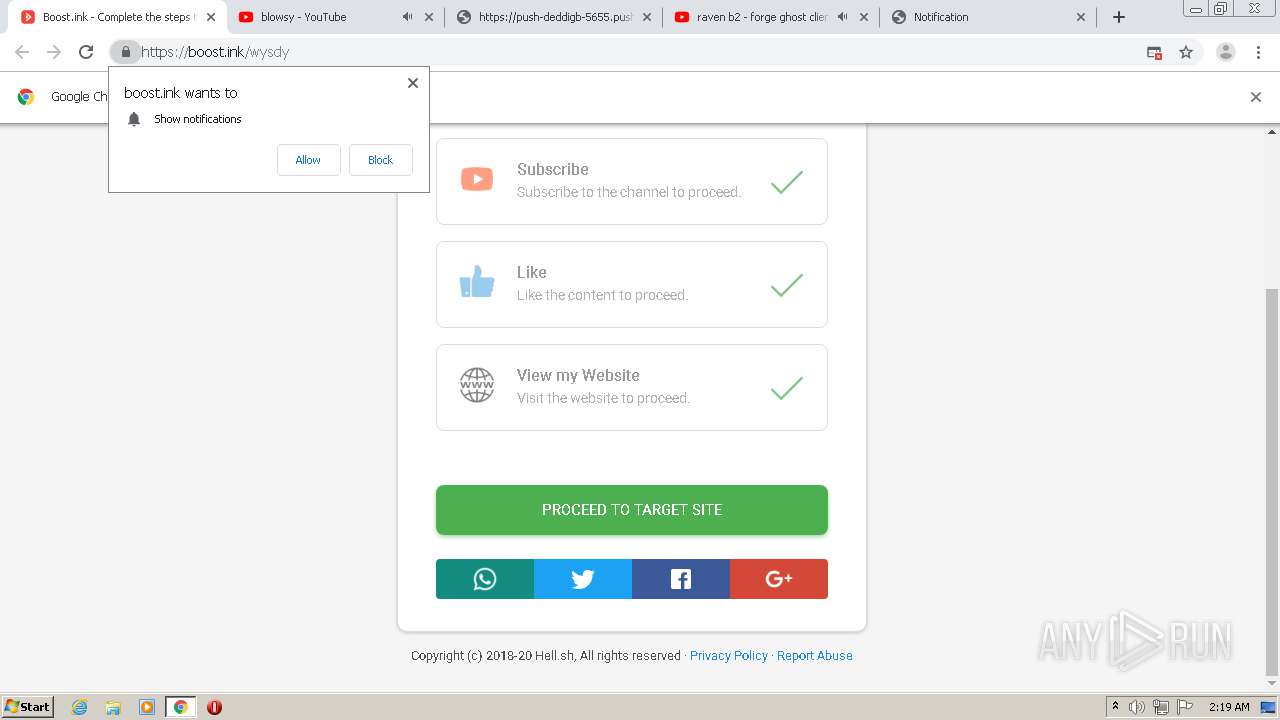
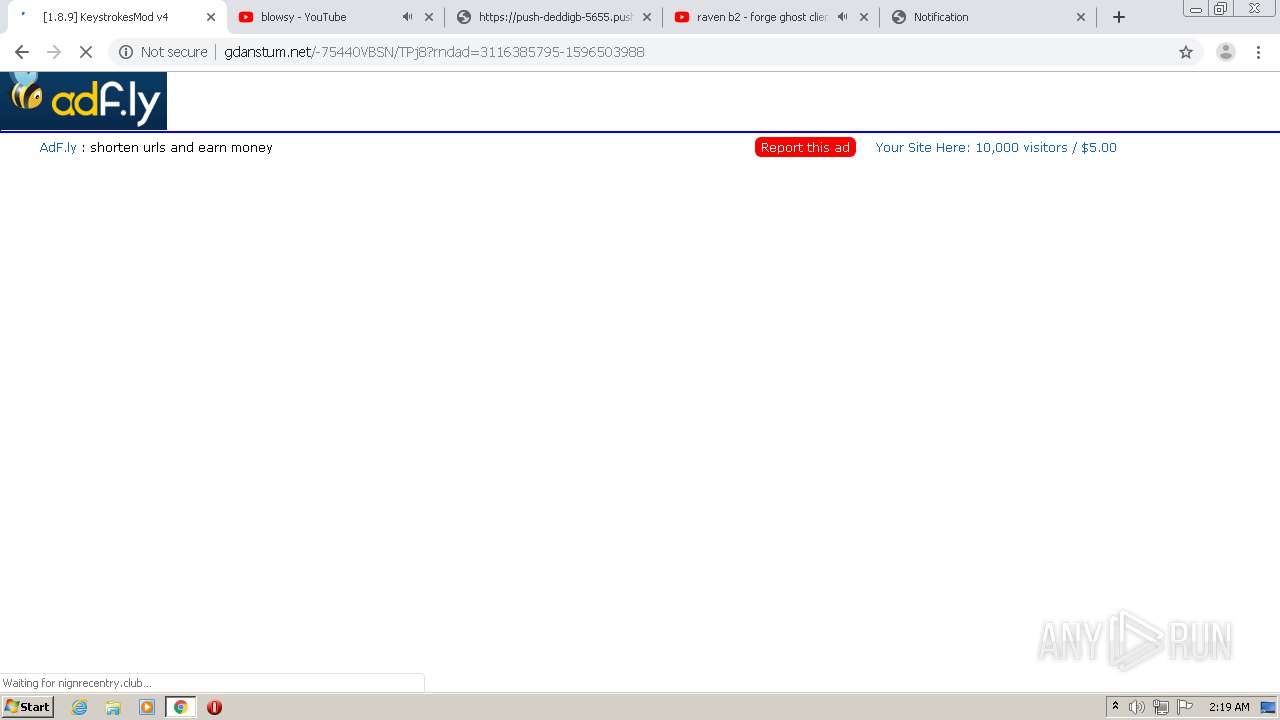
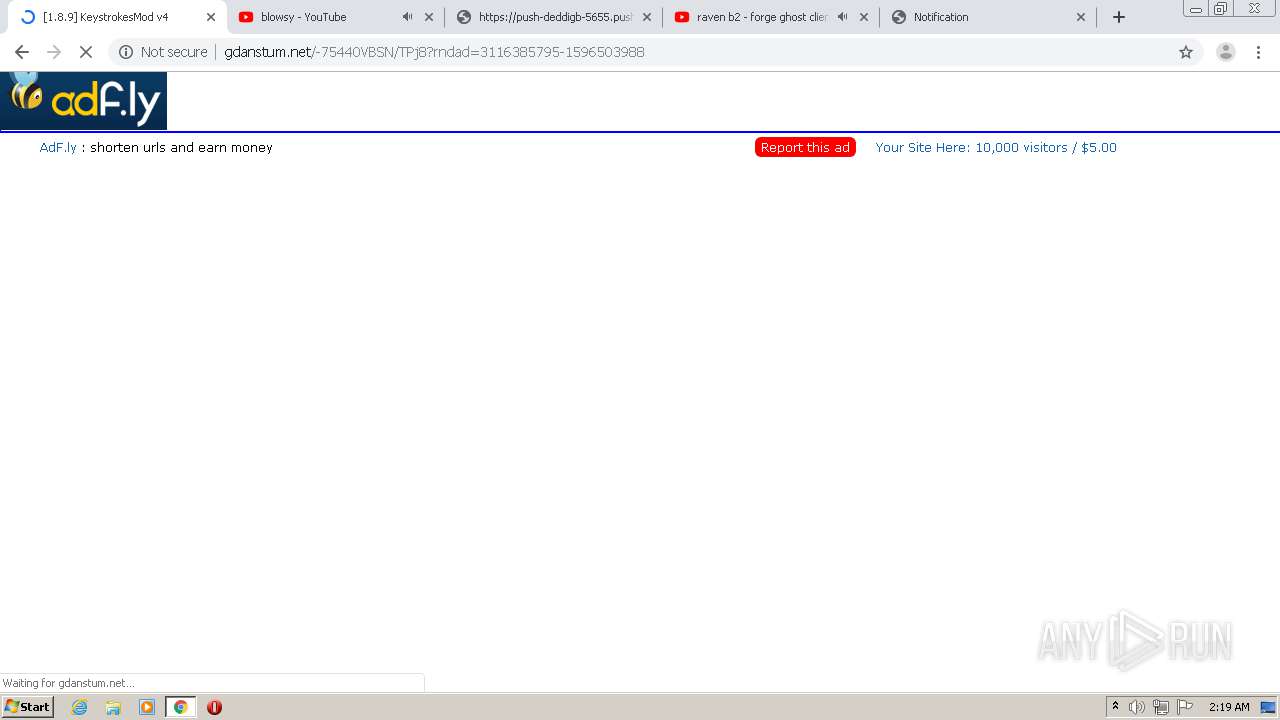
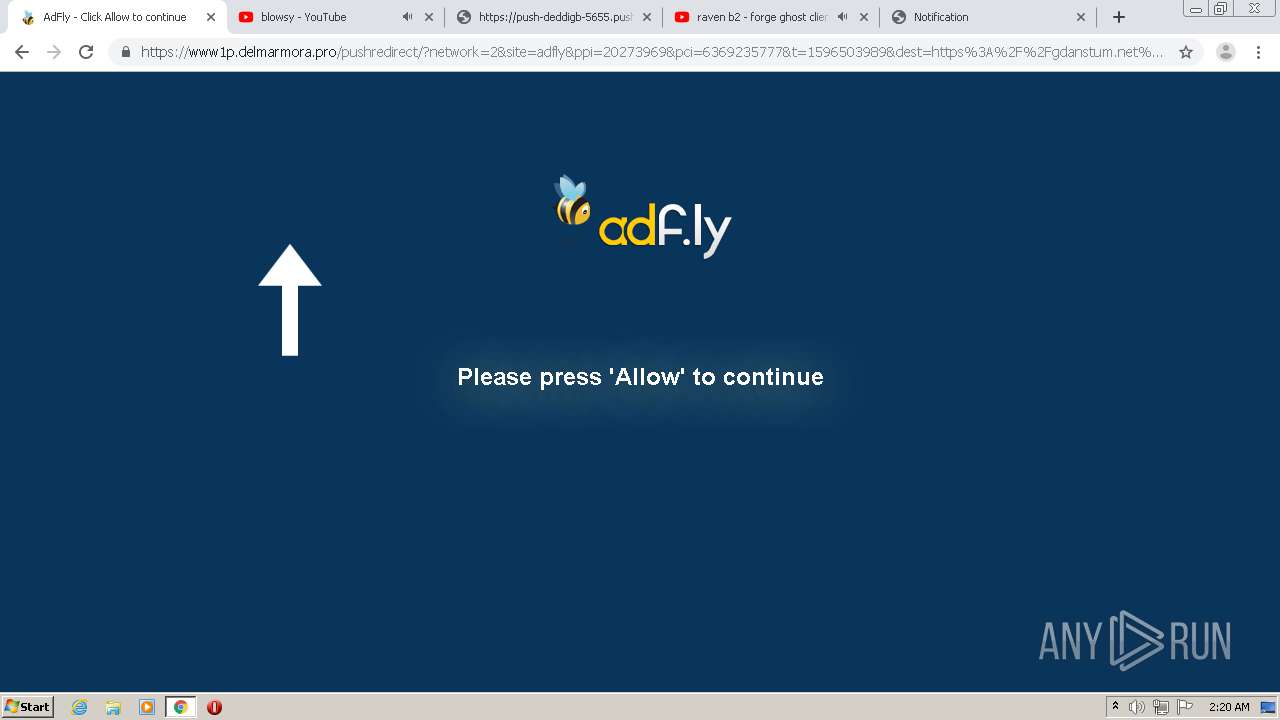
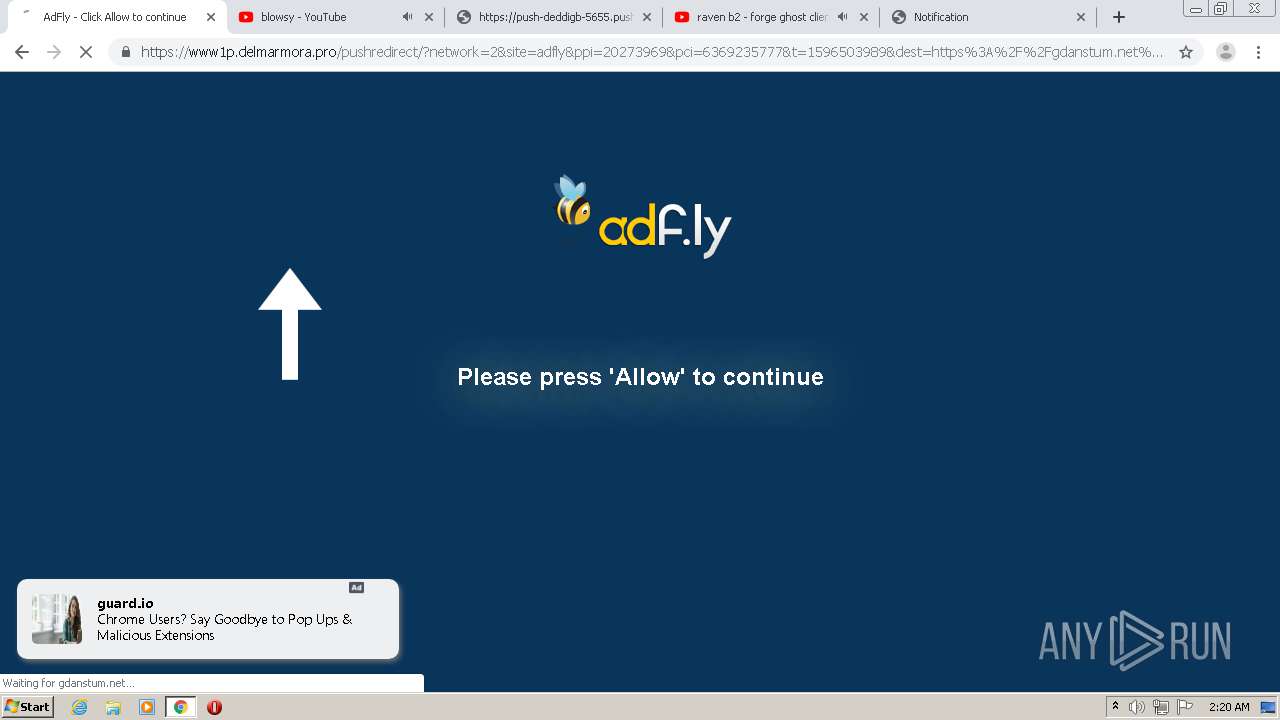
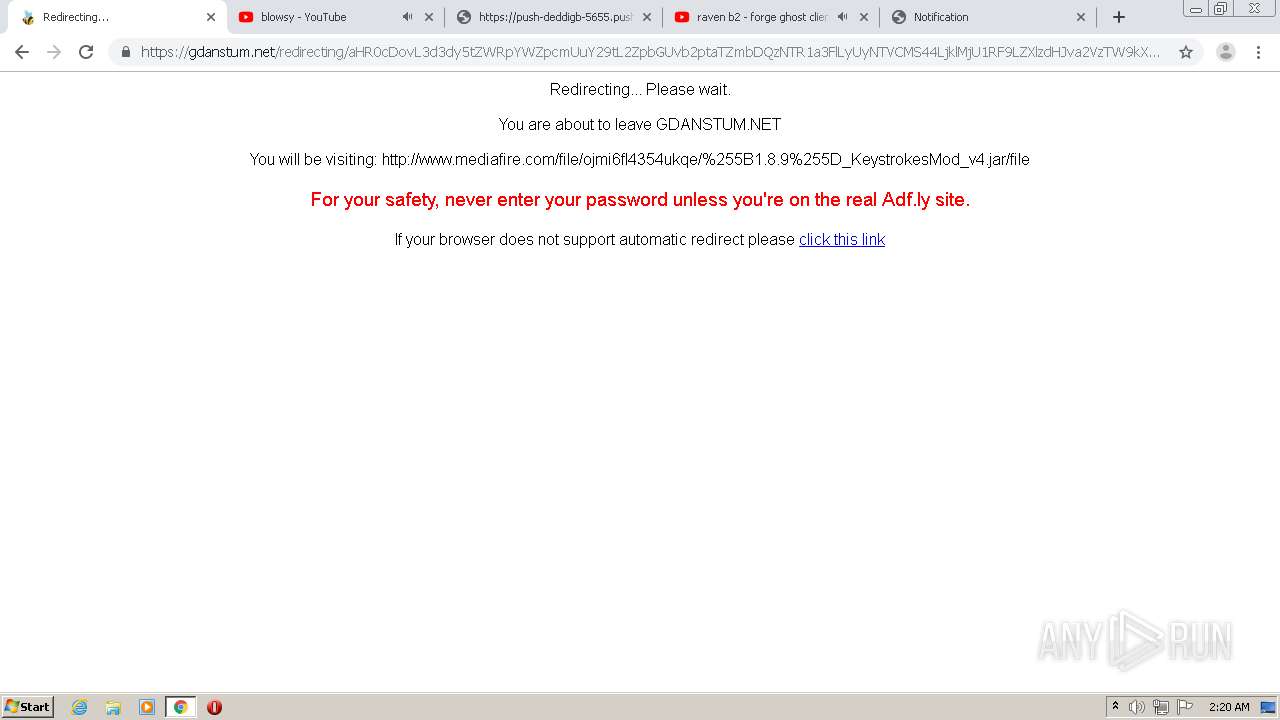
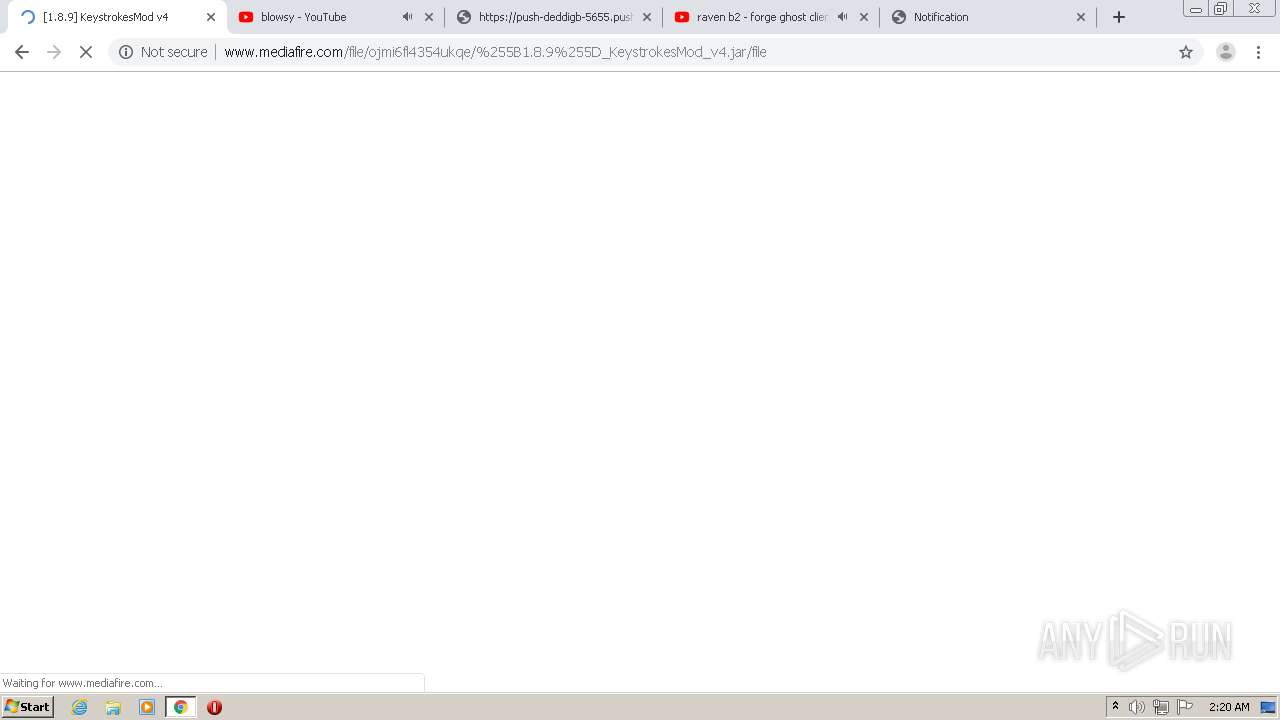
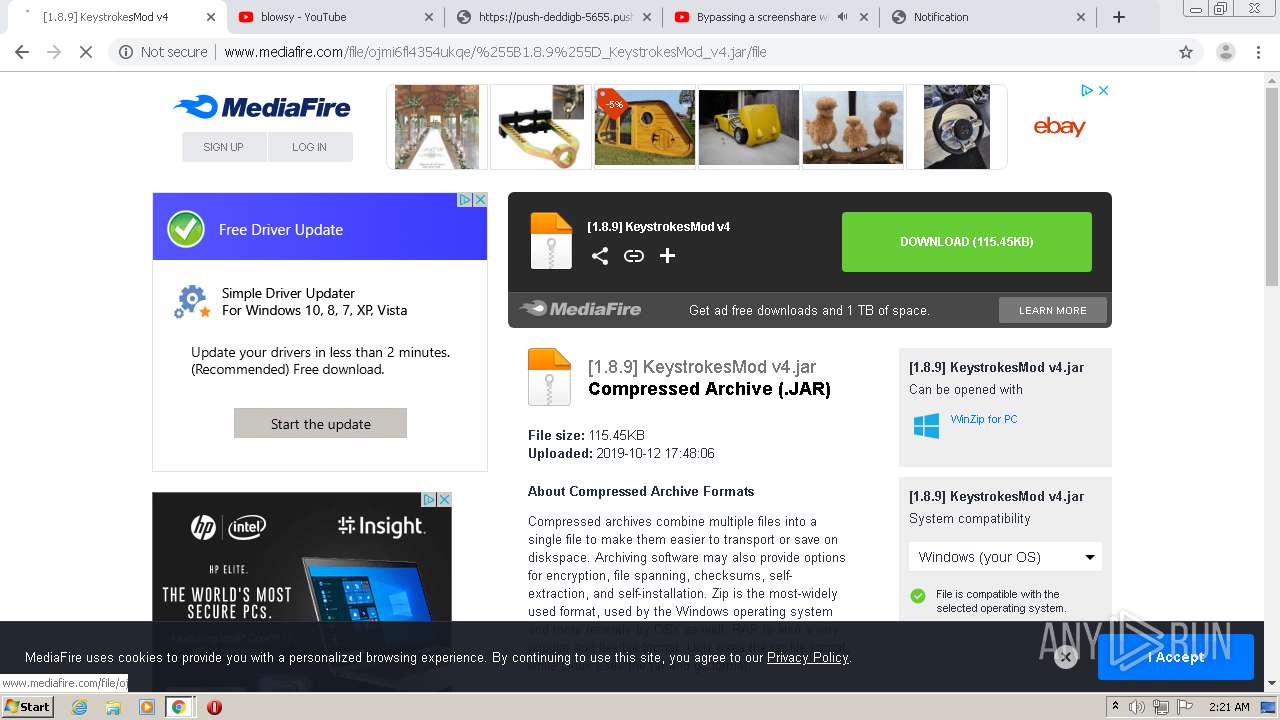
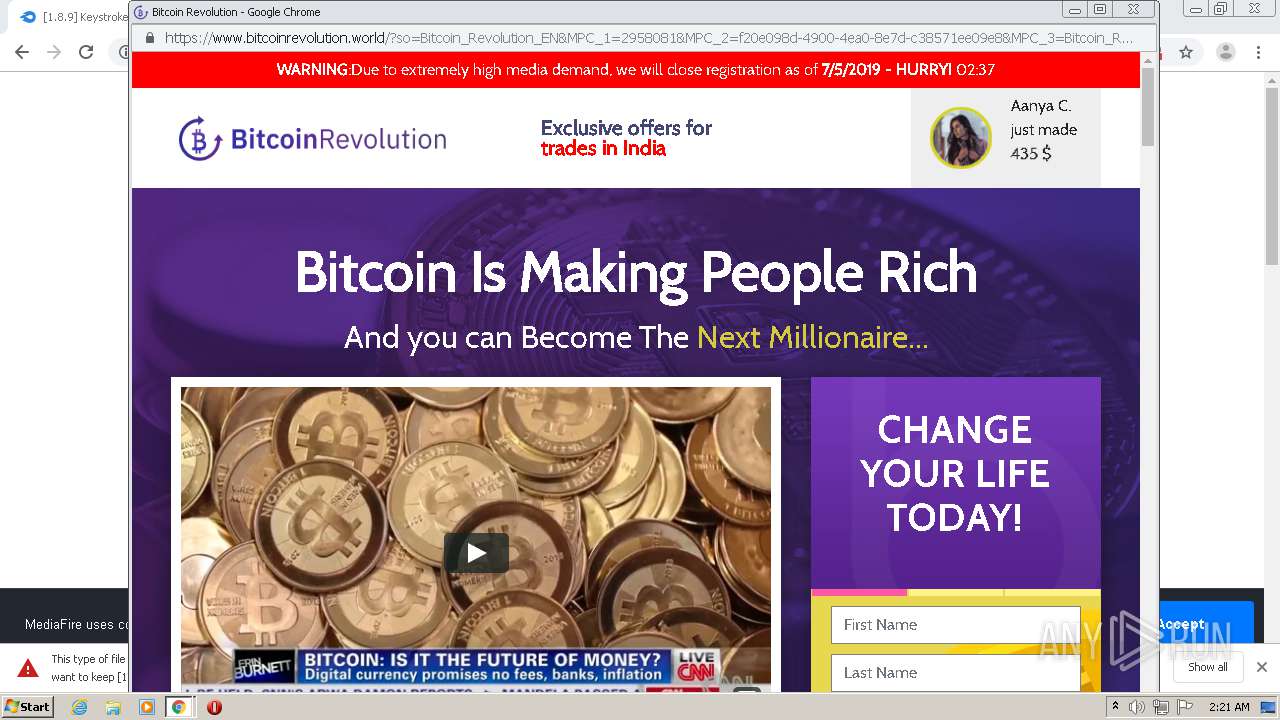
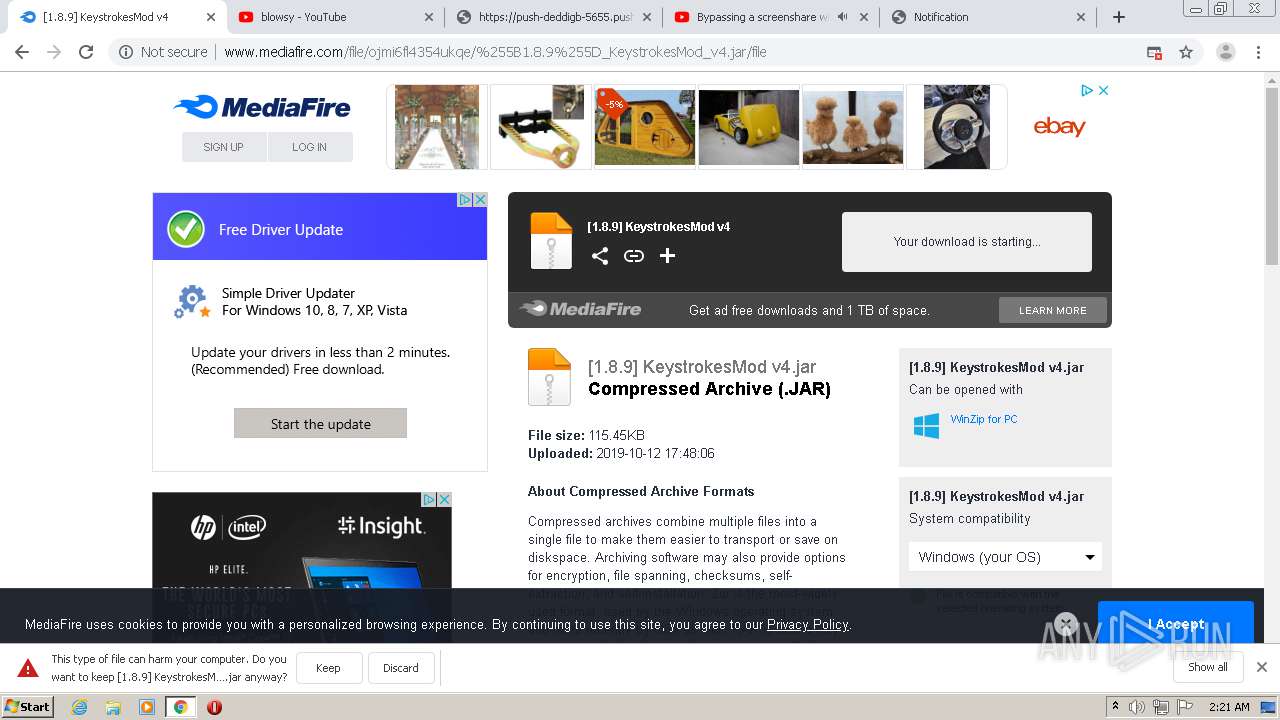
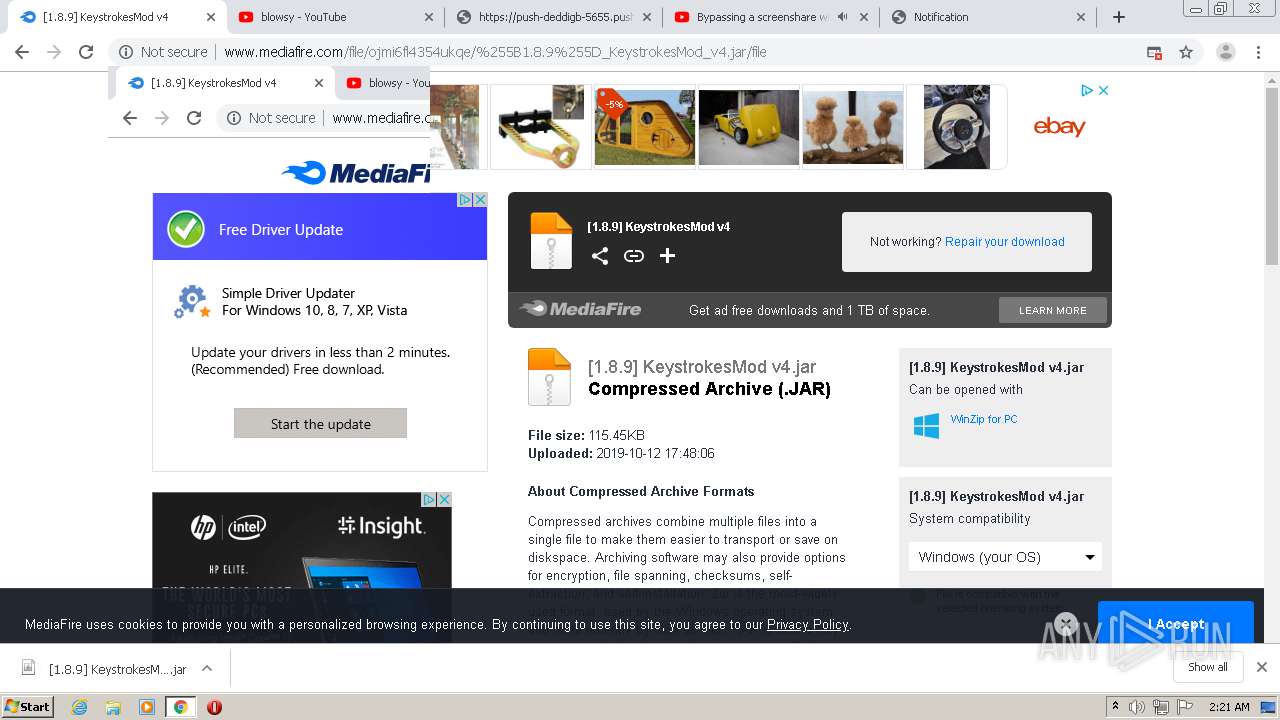
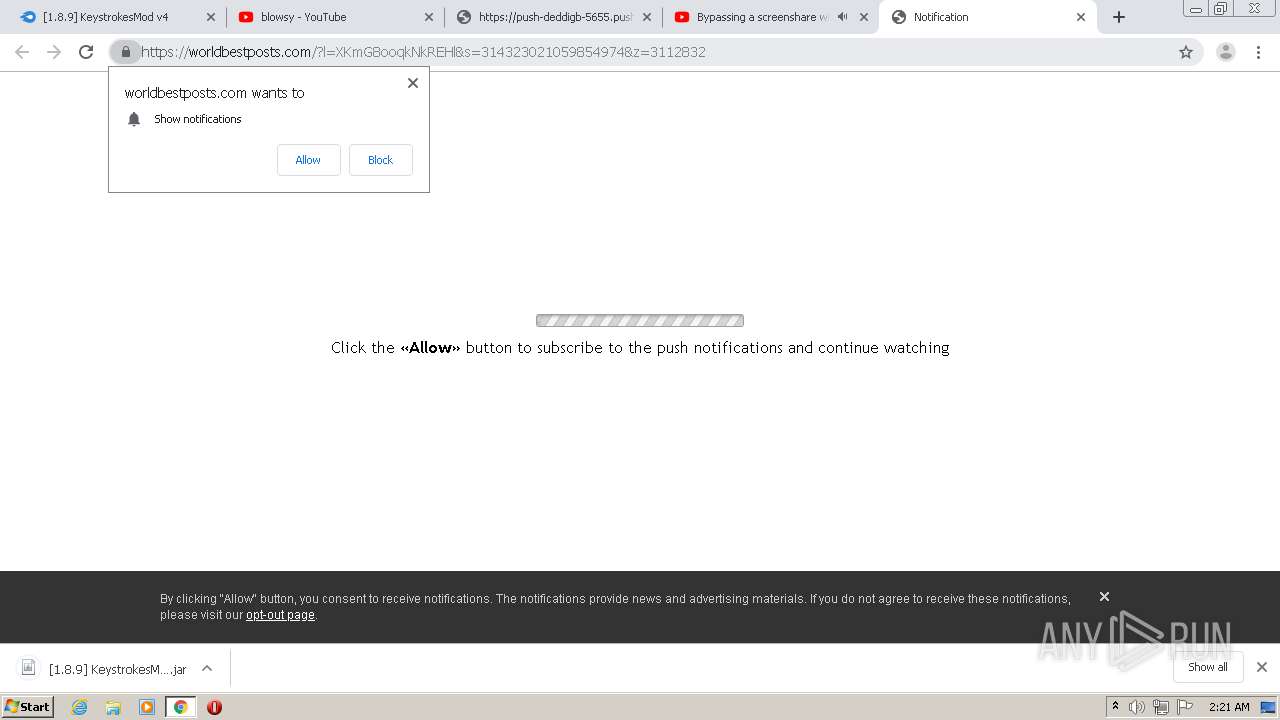
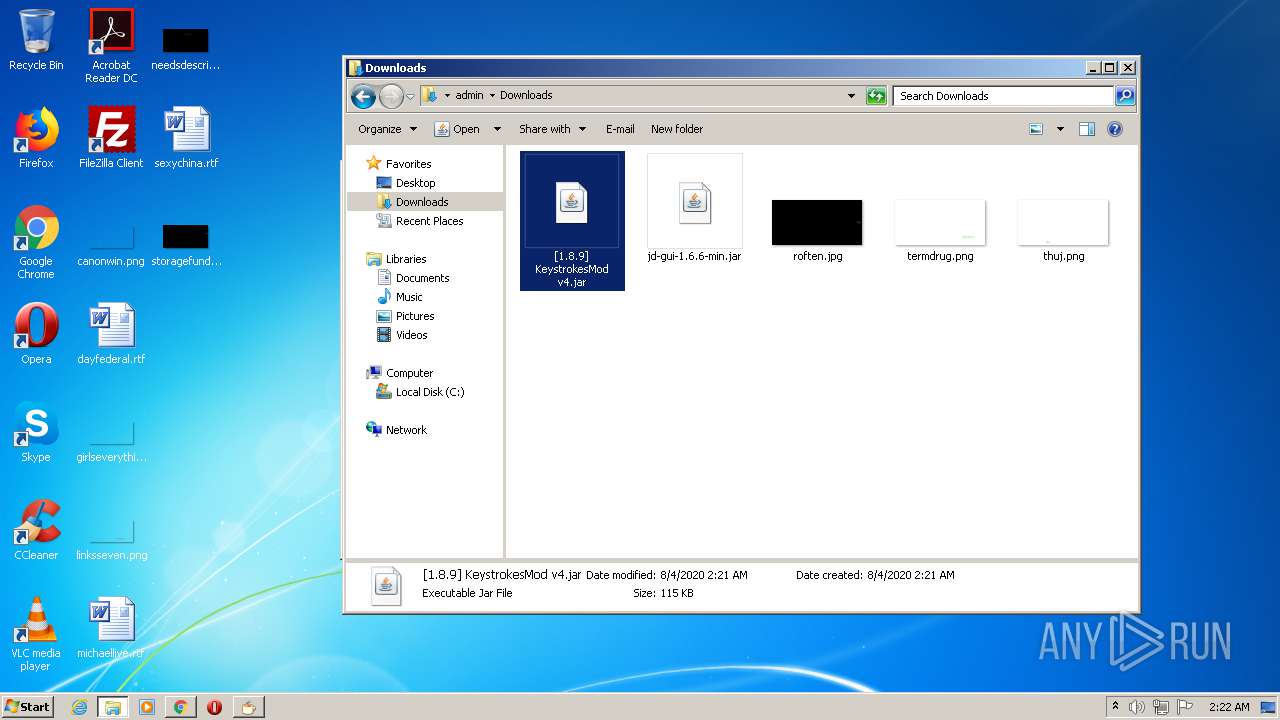
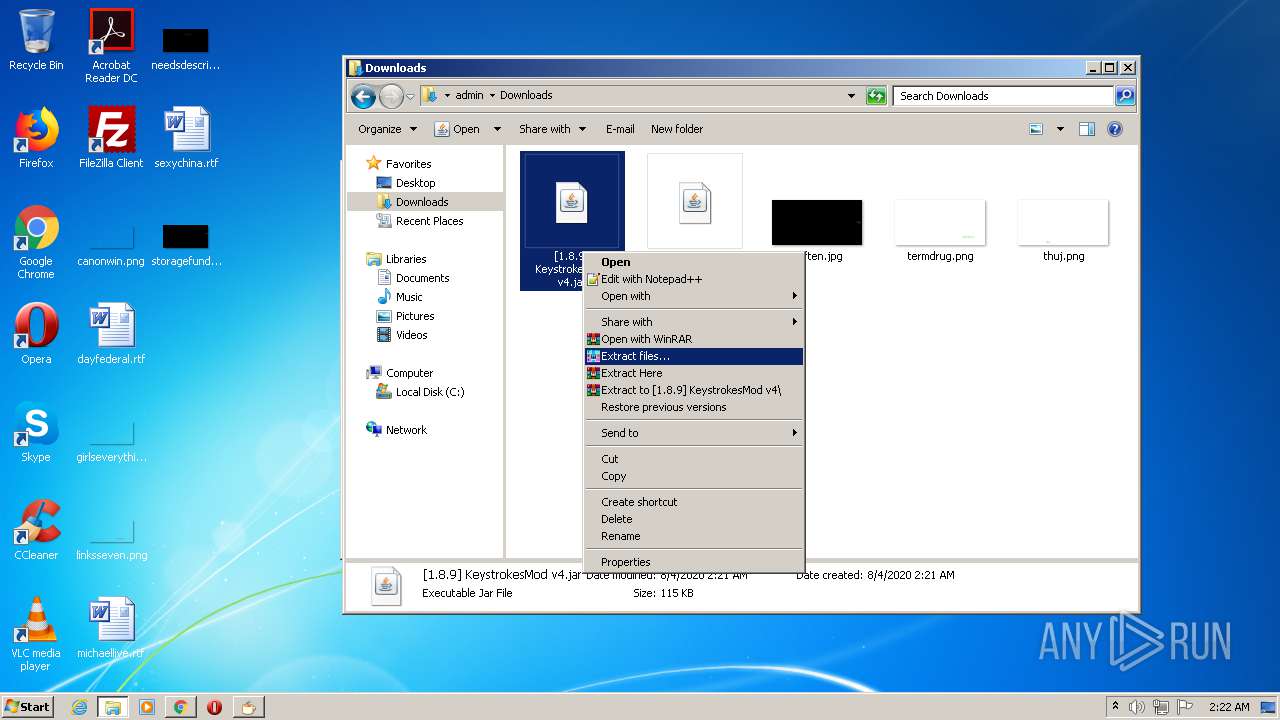
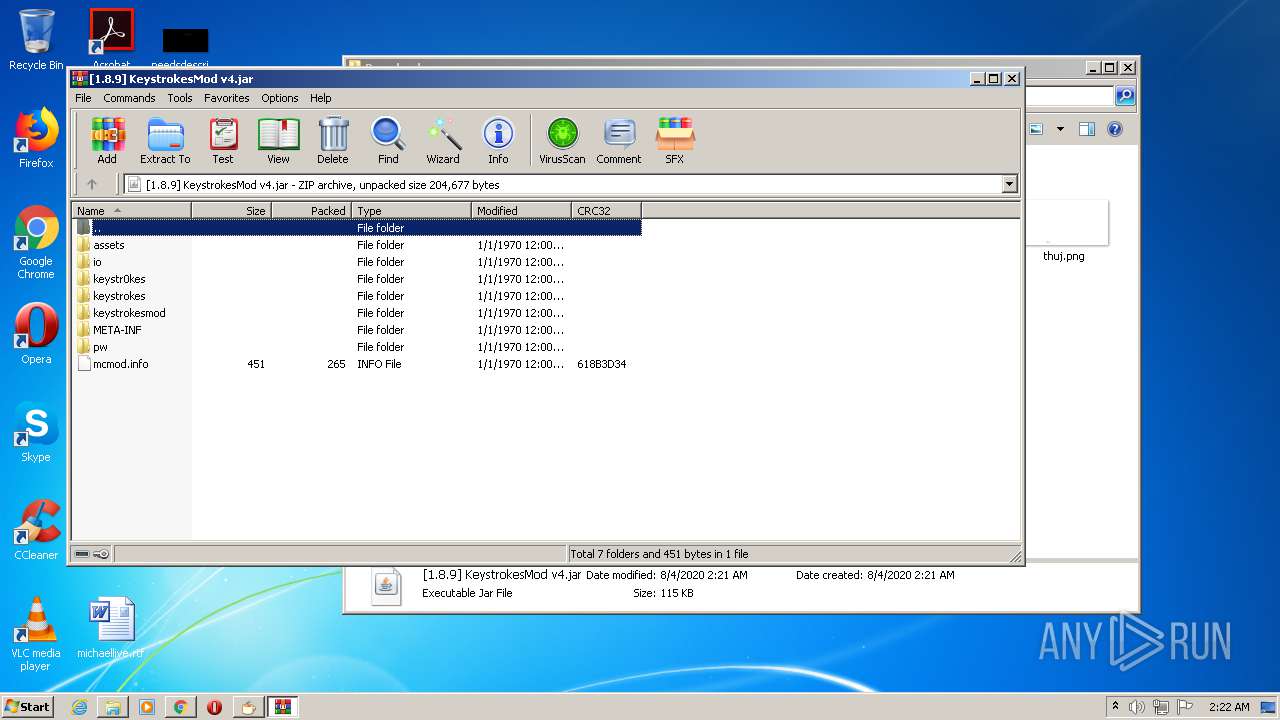
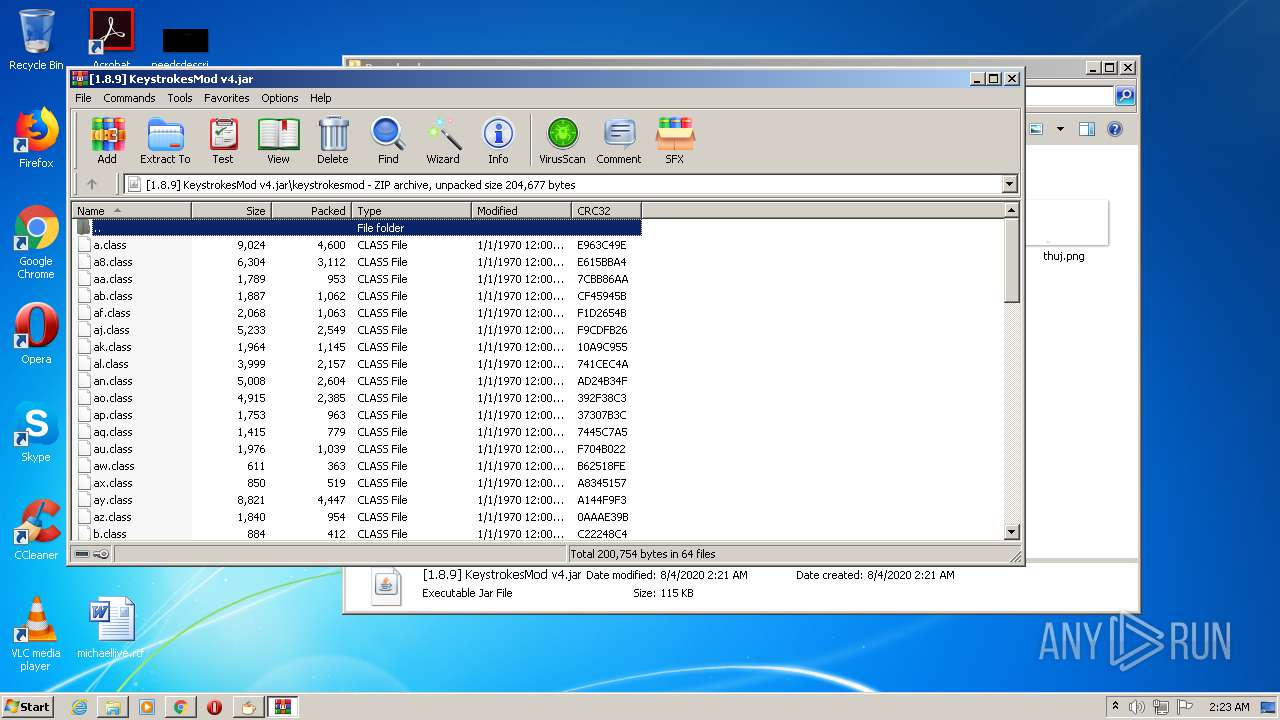
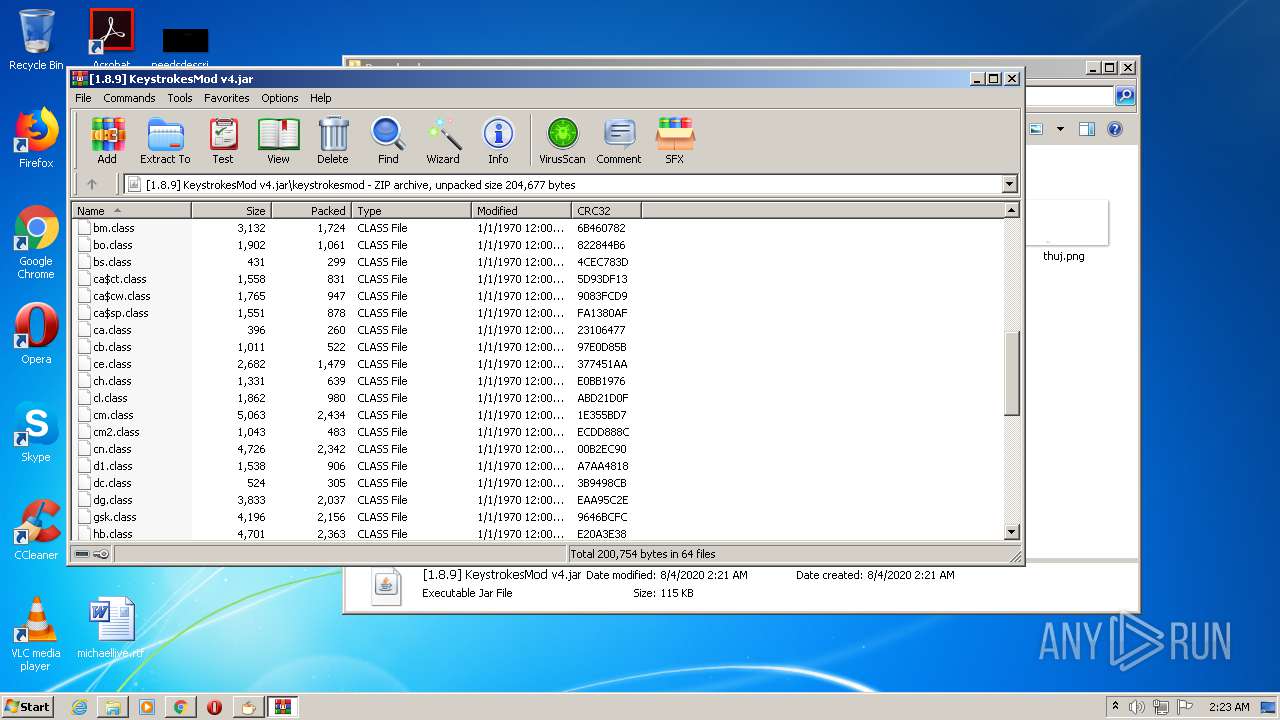
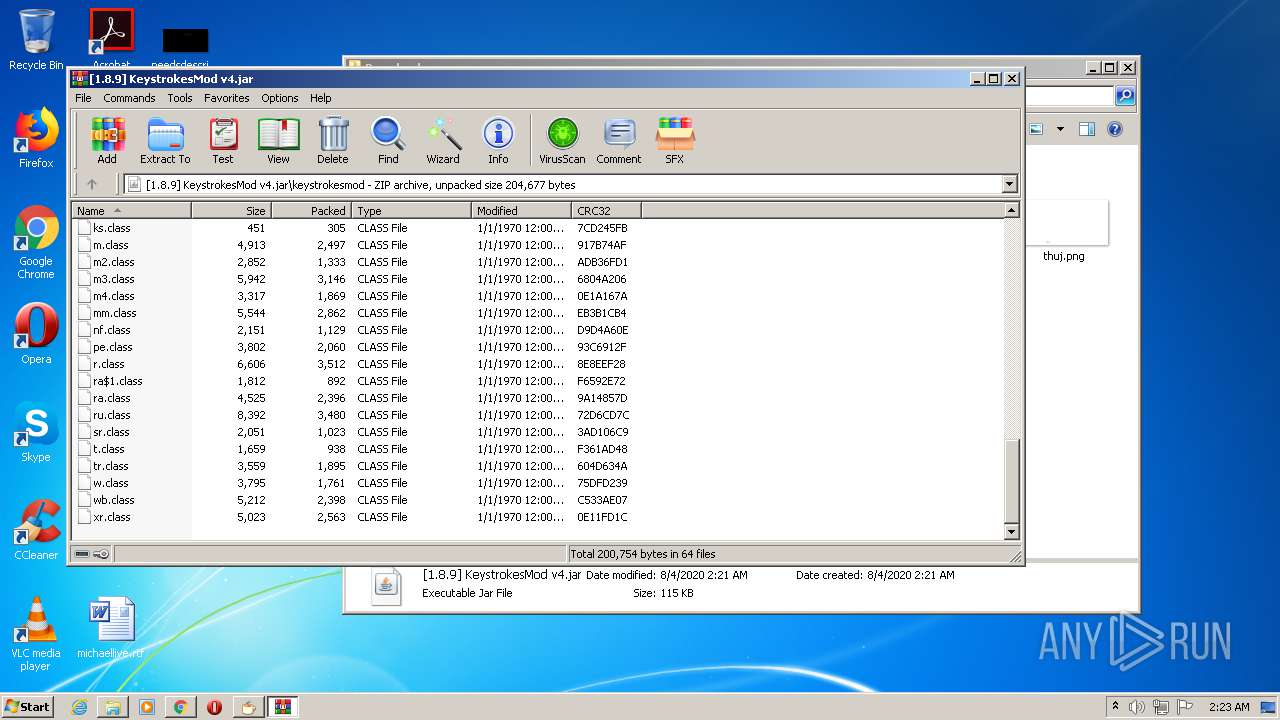
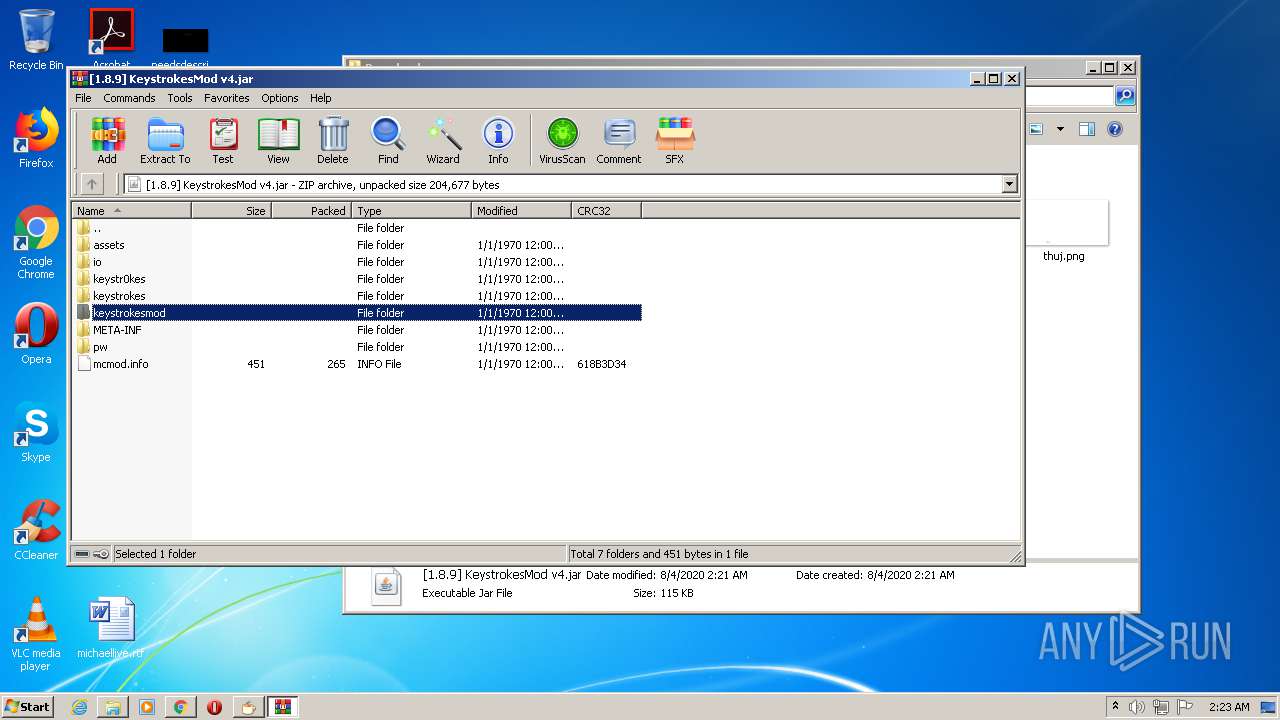
| URL: | https://bit.ly/ravenb2client |
| Full analysis: | https://app.any.run/tasks/0b68dbe5-aeb4-4fc0-bea5-fb22a40e2366 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2020, 01:19:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6369AA6F83B507D1BF8C38BB9CFDE512 |
| SHA1: | 982900B8ED75F9D29EF6FEEC26BC960C42F5D45C |
| SHA256: | F0B220A14C38C9659C92CADC129AECFDCD85621715D876D38F39B0836FE1FD64 |
| SSDEEP: | 3:N8krXMLRn:2pLR |
MALICIOUS
No malicious indicators.SUSPICIOUS
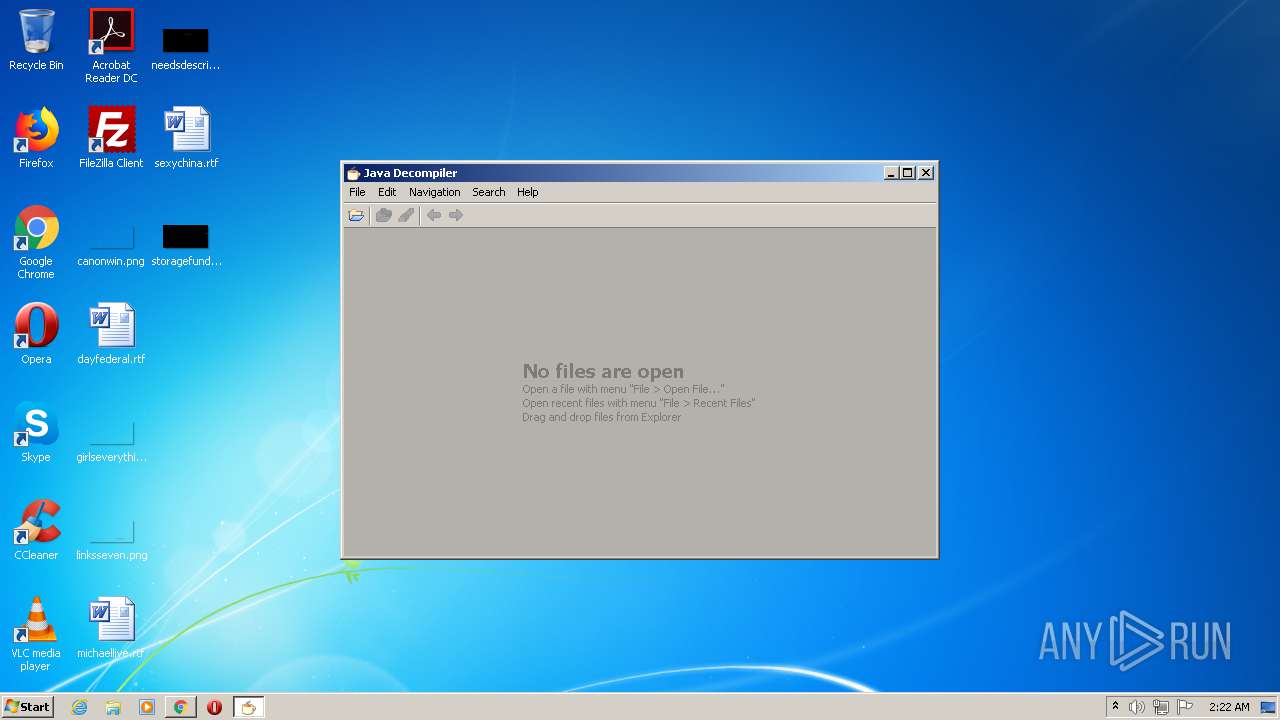
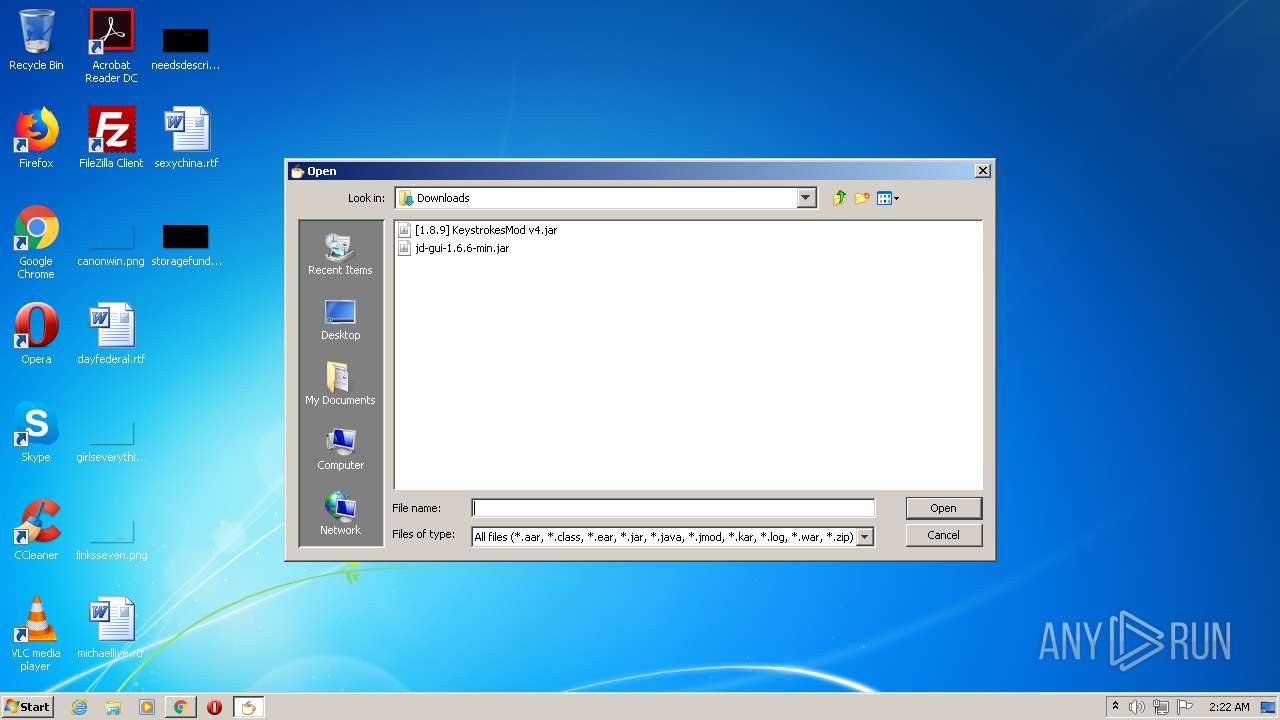
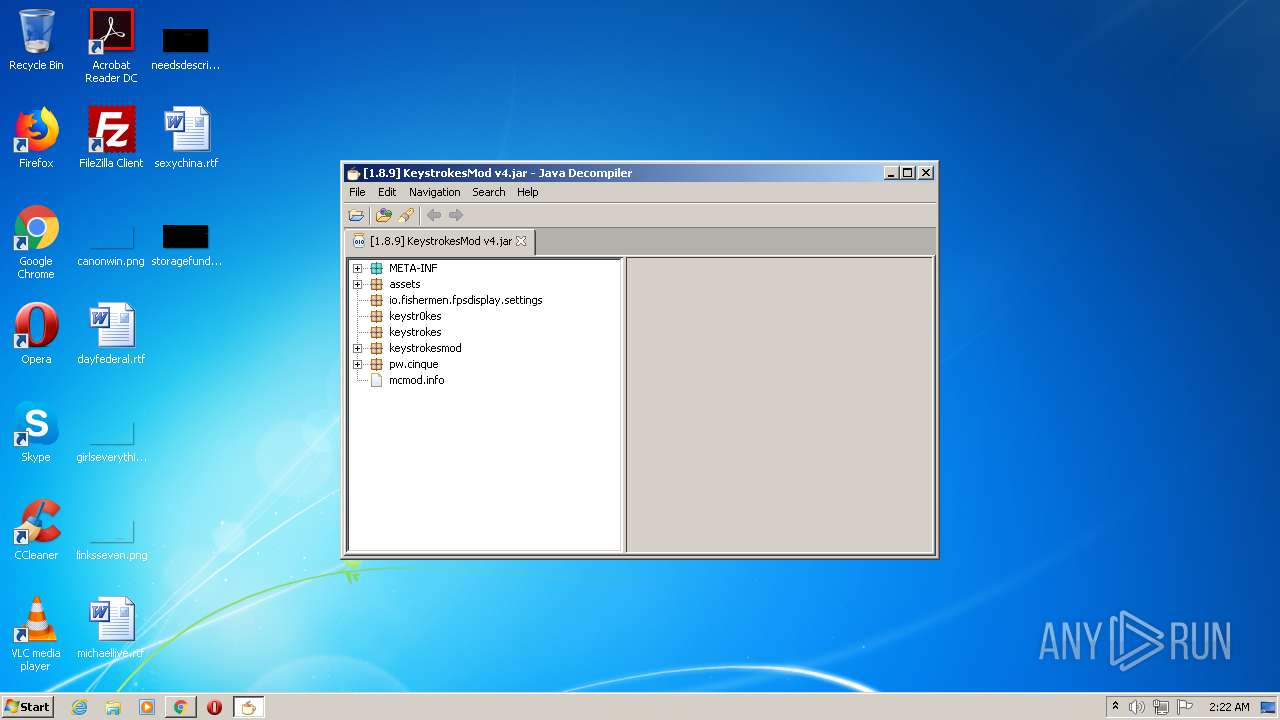
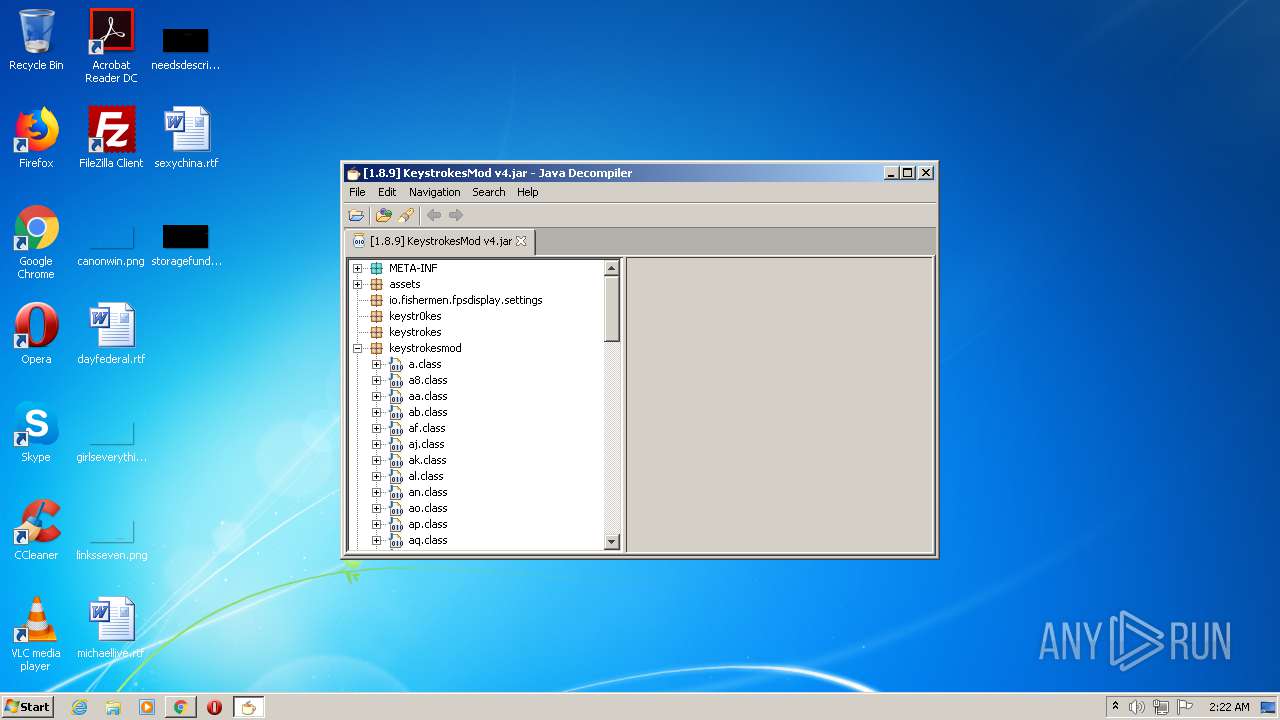
Executes JAVA applets
- chrome.exe (PID: 2592)
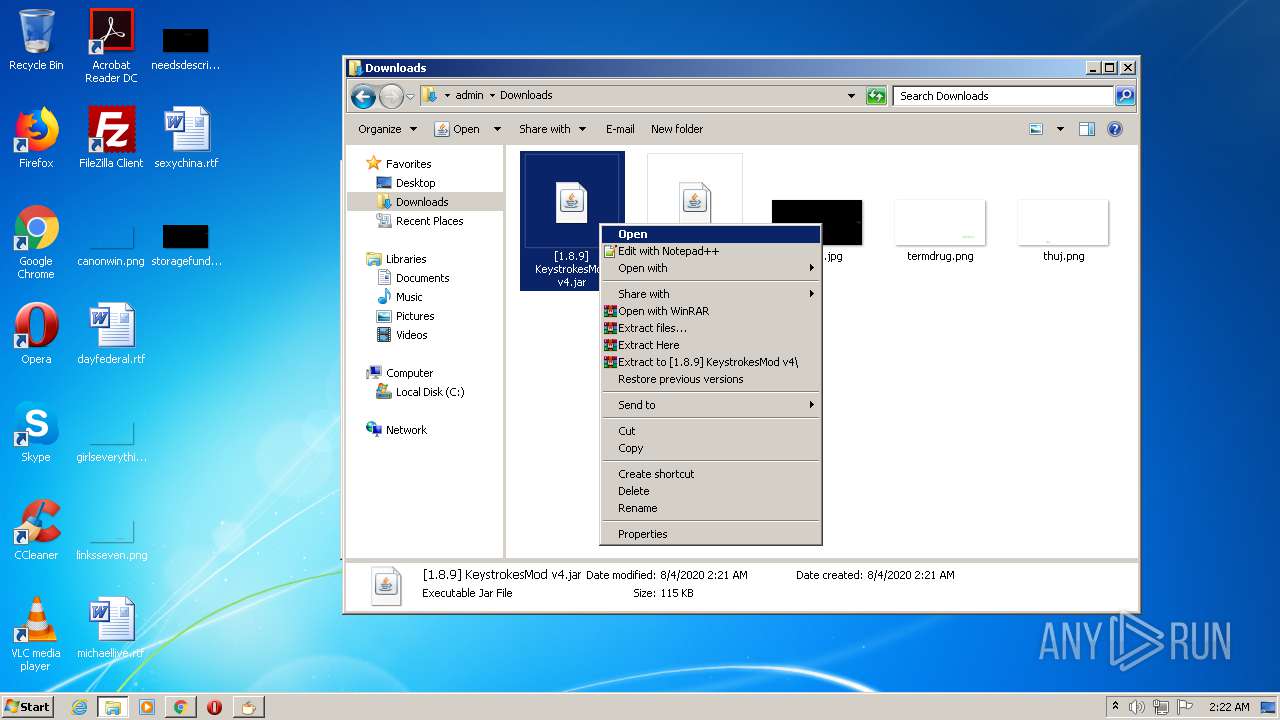
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 312)
INFO
Reads the hosts file
- chrome.exe (PID: 2592)
- chrome.exe (PID: 2200)
Reads settings of System Certificates
- chrome.exe (PID: 2200)
Reads Internet Cache Settings
- chrome.exe (PID: 2592)
Changes settings of System certificates
- chrome.exe (PID: 2200)
Manual execution by user
- explorer.exe (PID: 2720)
- javaw.exe (PID: 3528)
- WinRAR.exe (PID: 312)
Modifies the open verb of a shell class
- rundll32.exe (PID: 4036)
Application launched itself
- chrome.exe (PID: 2592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
116
Monitored processes
77
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
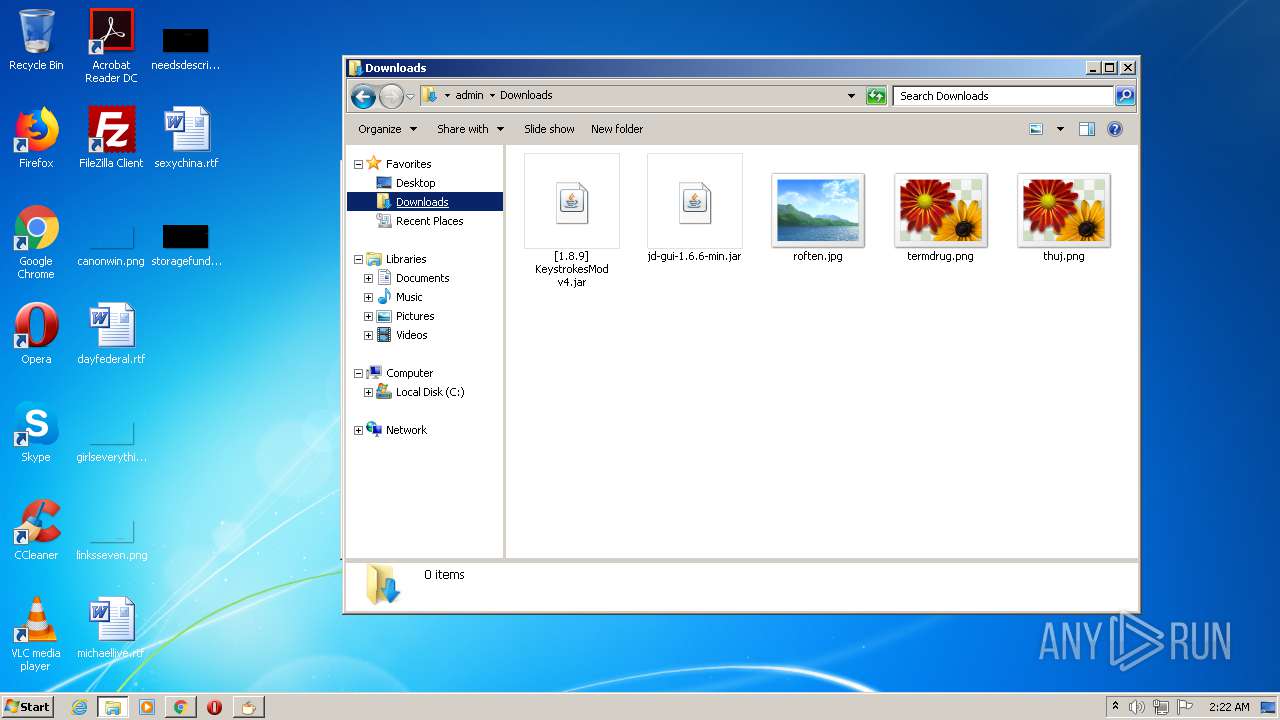
| 312 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\[1.8.9] KeystrokesMod v4.jar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1117000953340605821 --renderer-client-id=49 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5540 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3890428547089953888 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4708 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14637905036138772465 --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1960 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13382134249730275020 --mojo-platform-channel-handle=508 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16676021941115133978 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2460 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9608935791095740194 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3796 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12590631843475651684 --renderer-client-id=46 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4320 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=4293647854514395124 --mojo-platform-channel-handle=4784 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,1112626684407969127,1138403693606498917,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=355299737700570303 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4756 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 632
Read events
2 375
Write events
252
Delete events
5
Modification events
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2496) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2592-13240977560014875 |
Value: 259 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
| (PID) Process: | (2592) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
326
Text files
211
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\49d7b08b-bf9e-4eed-a86f-72e4f9294c4f.tmp | — | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old~RFd6c09.TMP | text | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFd6aef.TMP | text | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFd6aef.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
280
DNS requests
199
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
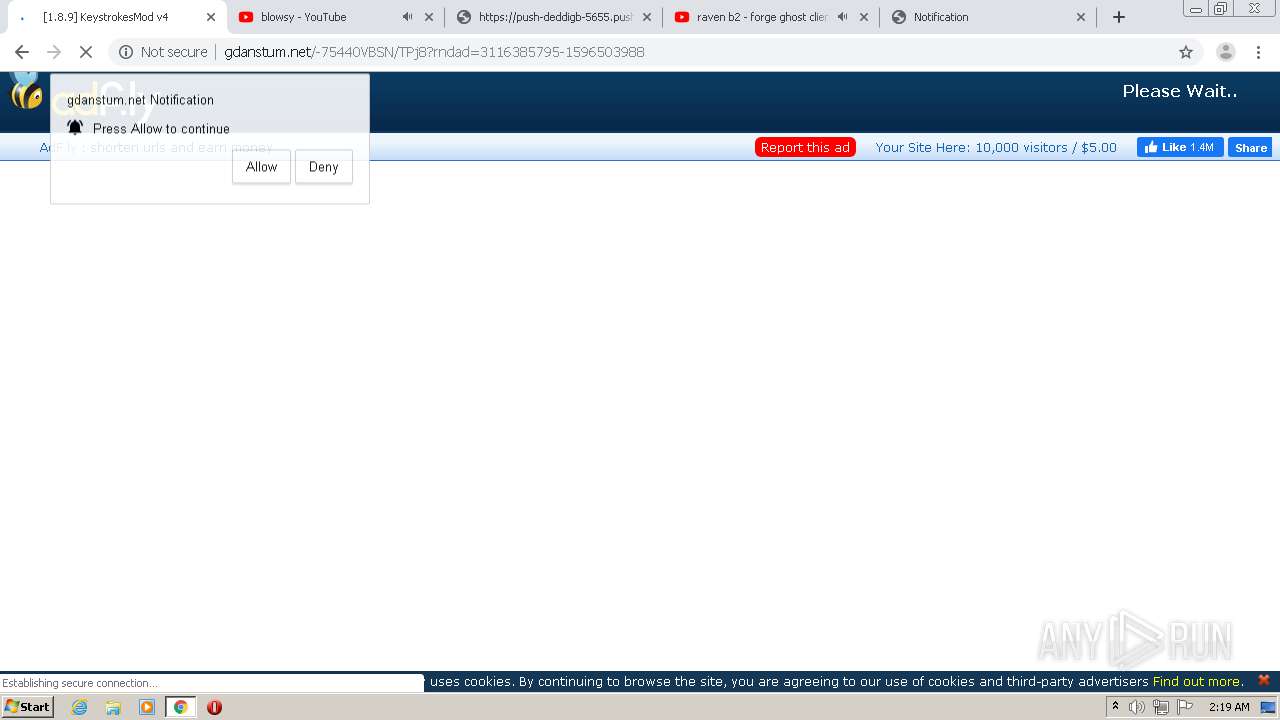
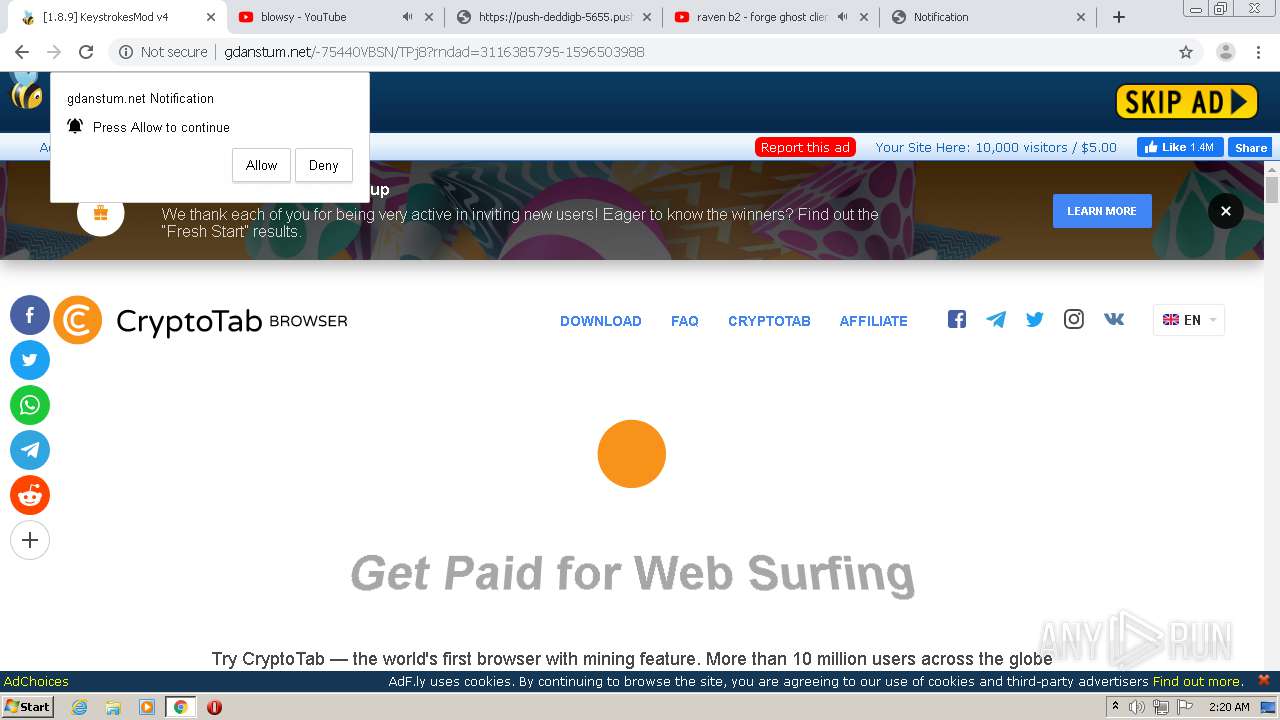
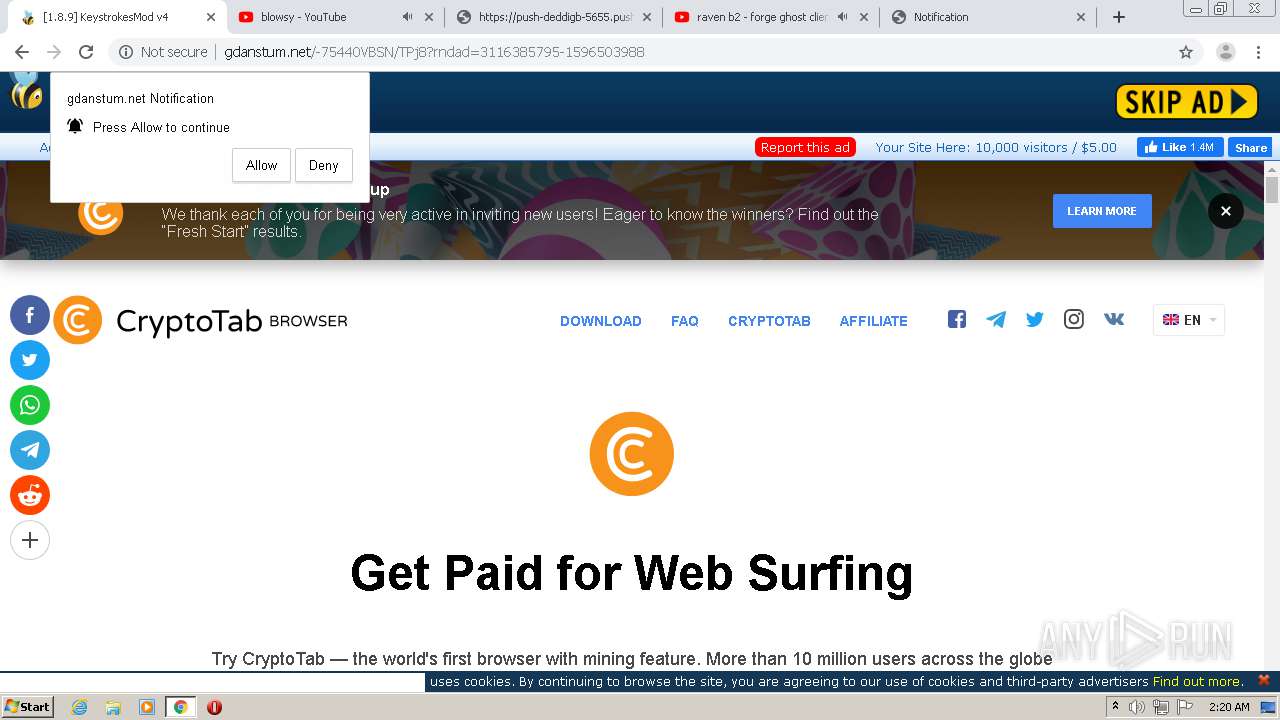
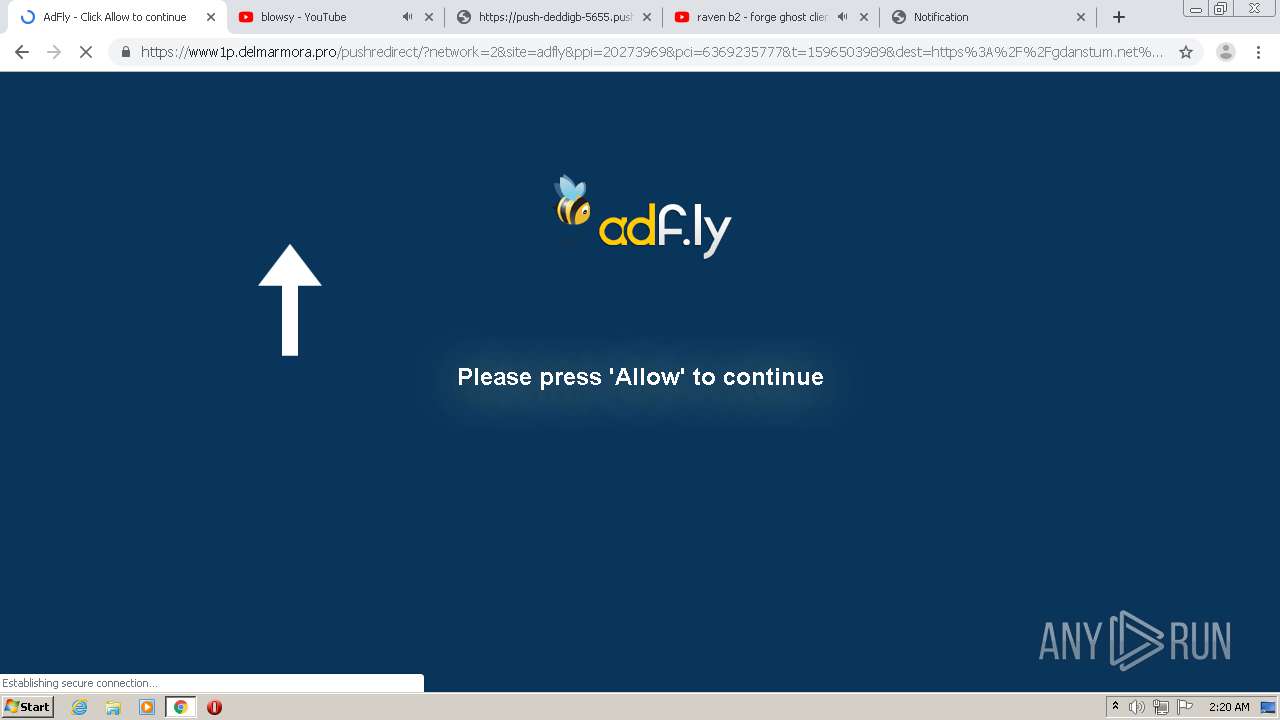
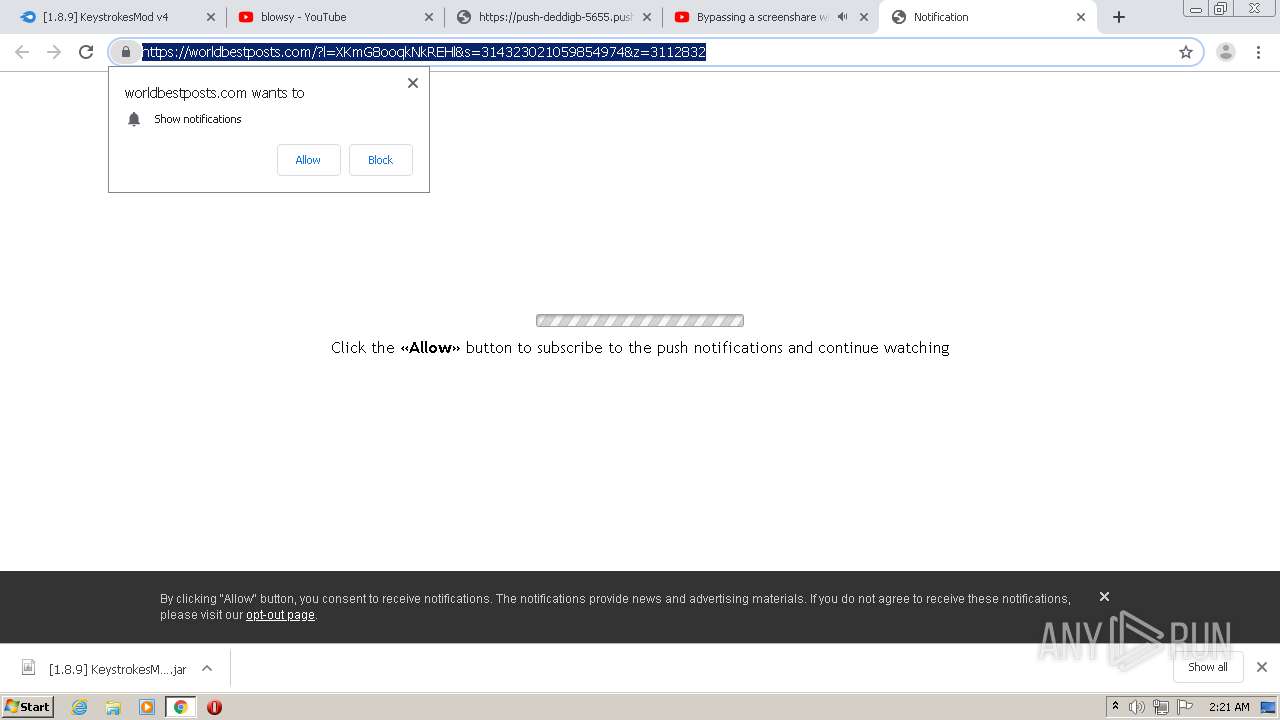
2200 | chrome.exe | GET | 301 | 104.27.165.216:80 | http://eunsetee.com/TPj8 | US | — | — | whitelisted |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://cdn.gdanstum.net/static/js/b64.js | US | text | 1.07 Kb | suspicious |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://cdn.gdanstum.net/static/js/view111.js | US | text | 28.1 Kb | suspicious |
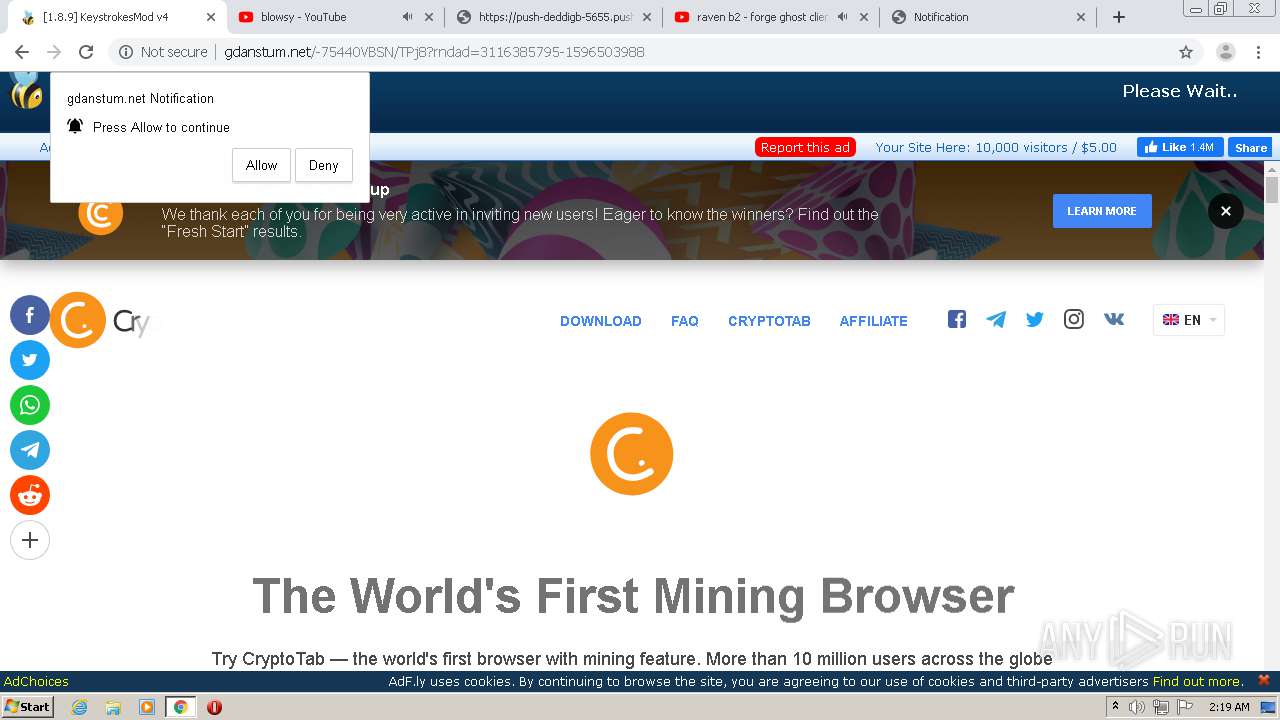
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://gdanstum.net/-75440VBSN/TPj8?rndad=3116385795-1596503988 | US | html | 5.83 Kb | suspicious |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://cdn.gdanstum.net/static/js/amvn.js | US | text | 89.5 Kb | suspicious |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://gdanstum.net/fp.rev11.php?ver=20273969&nocache=7076 | US | text | 12.8 Kb | suspicious |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://cdn.gdanstum.net/static/image/skip_ad/en_tran.png | US | image | 4.96 Kb | suspicious |
2200 | chrome.exe | GET | 200 | 13.224.194.47:80 | http://dentedporc.club/popunder.gif | US | compressed | 58 b | whitelisted |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://cdn.gdanstum.net/static/image/spinner.gif | US | image | 34.6 Kb | suspicious |
2200 | chrome.exe | GET | 200 | 172.64.171.11:80 | http://cdn.gdanstum.net/static/js/main.js | US | text | 667 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2200 | chrome.exe | 67.199.248.11:443 | bit.ly | Bitly Inc | US | shared |
2200 | chrome.exe | 172.217.22.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2200 | chrome.exe | 172.217.23.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 139.45.196.130:443 | pushsar.com | — | US | suspicious |
2200 | chrome.exe | 104.27.162.4:443 | boost.ink | Cloudflare Inc | US | shared |
2200 | chrome.exe | 172.217.18.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2200 | chrome.exe | 139.45.196.11:443 | shorteh.com | — | US | unknown |
2200 | chrome.exe | 172.217.18.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bit.ly |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ocsp.digicert.com |
| whitelisted |
boost.ink |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
shorteh.com |
| malicious |
pushsar.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | chrome.exe | Attempted User Privilege Gain | AV POLICY Observed Suspicious JScript serving Adware Inbound |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2200 | chrome.exe | Misc Attack | ET DROP Dshield Block Listed Source group 1 |
2200 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
2200 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
2200 | chrome.exe | Attempted User Privilege Gain | AV POLICY Observed Suspicious JScript serving Adware Inbound |