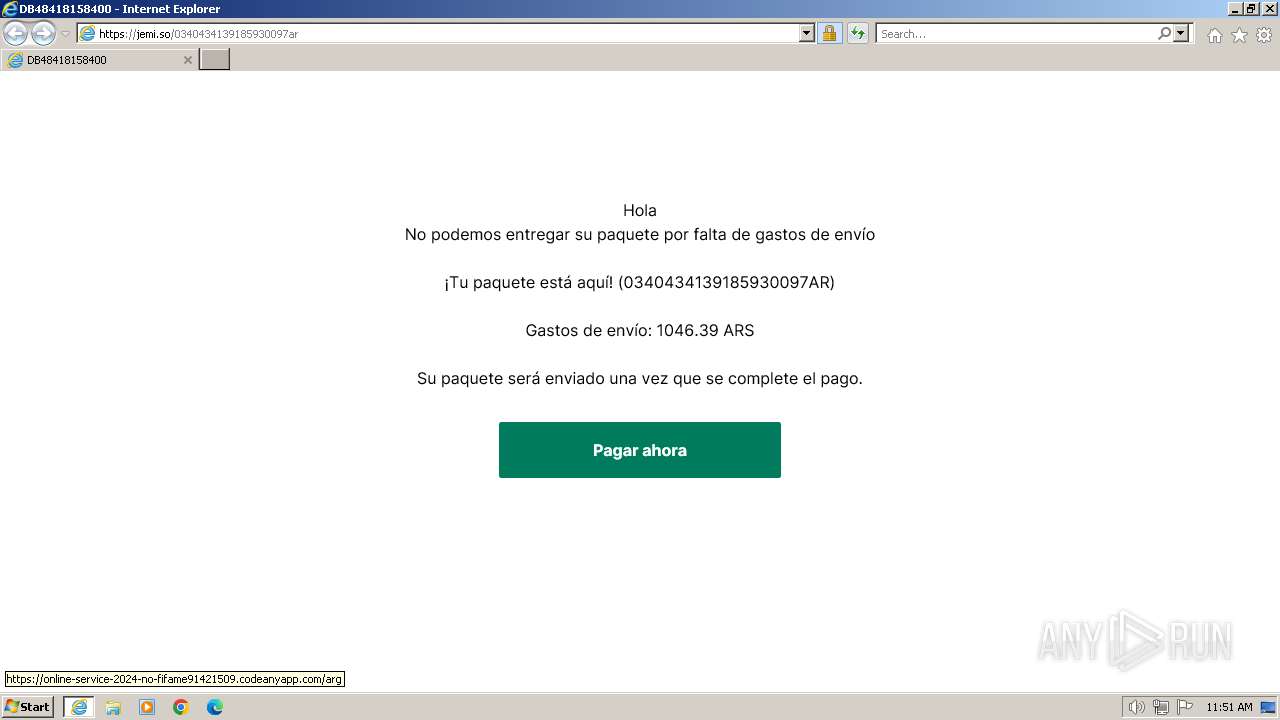
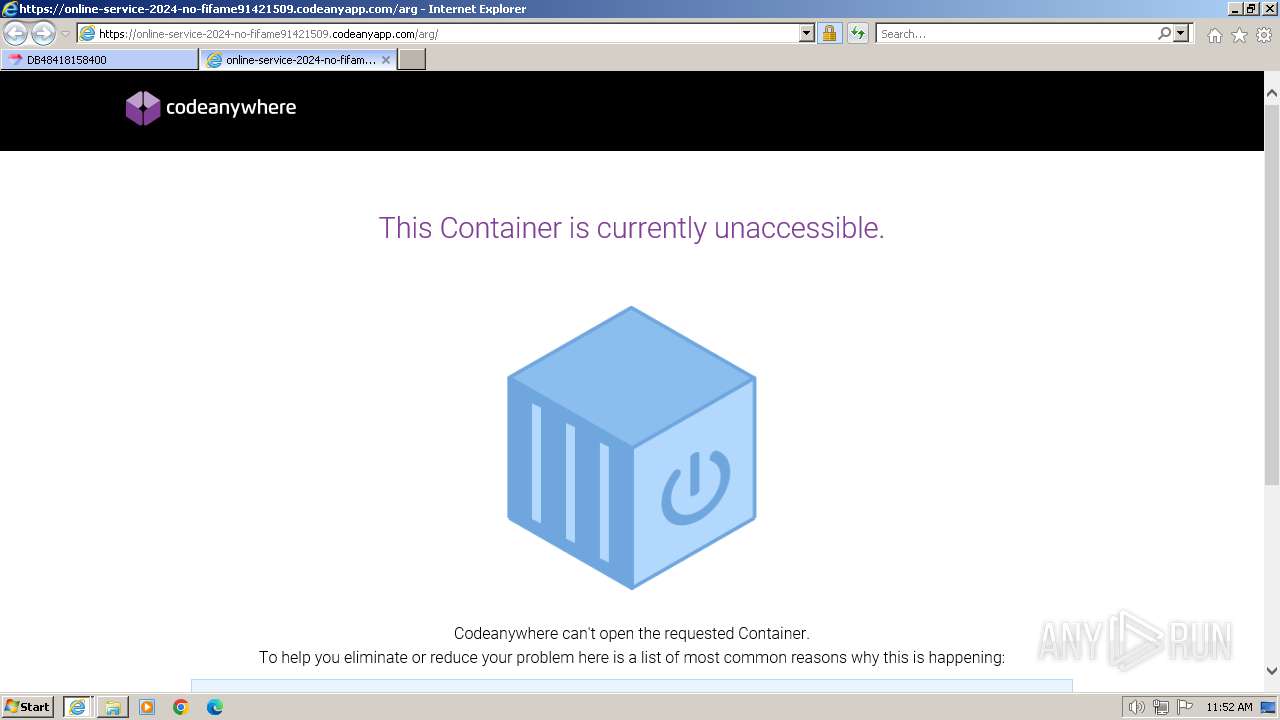
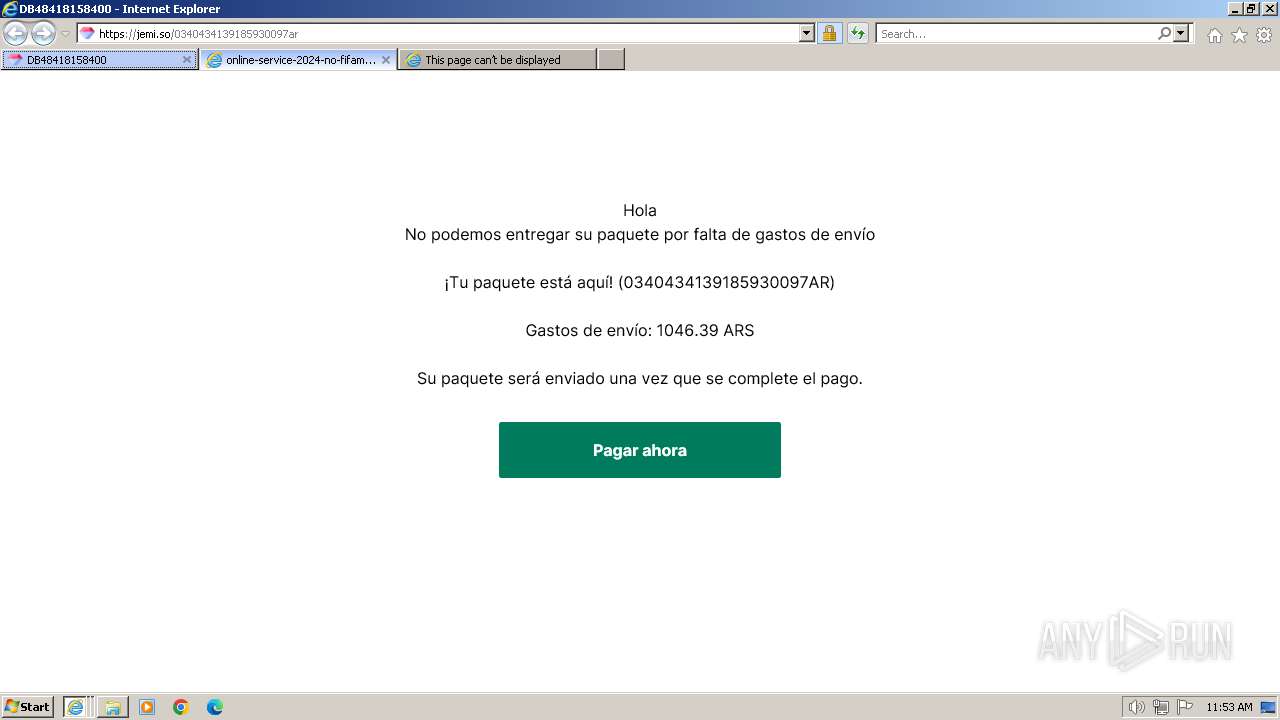
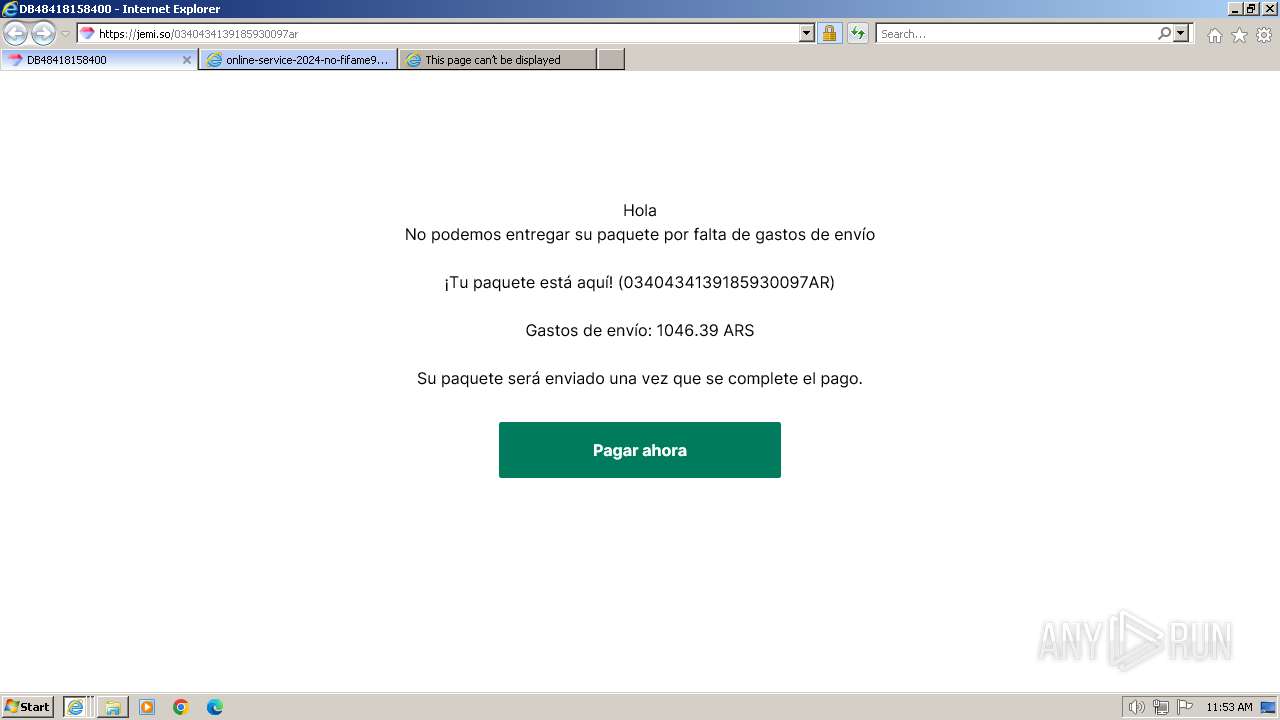
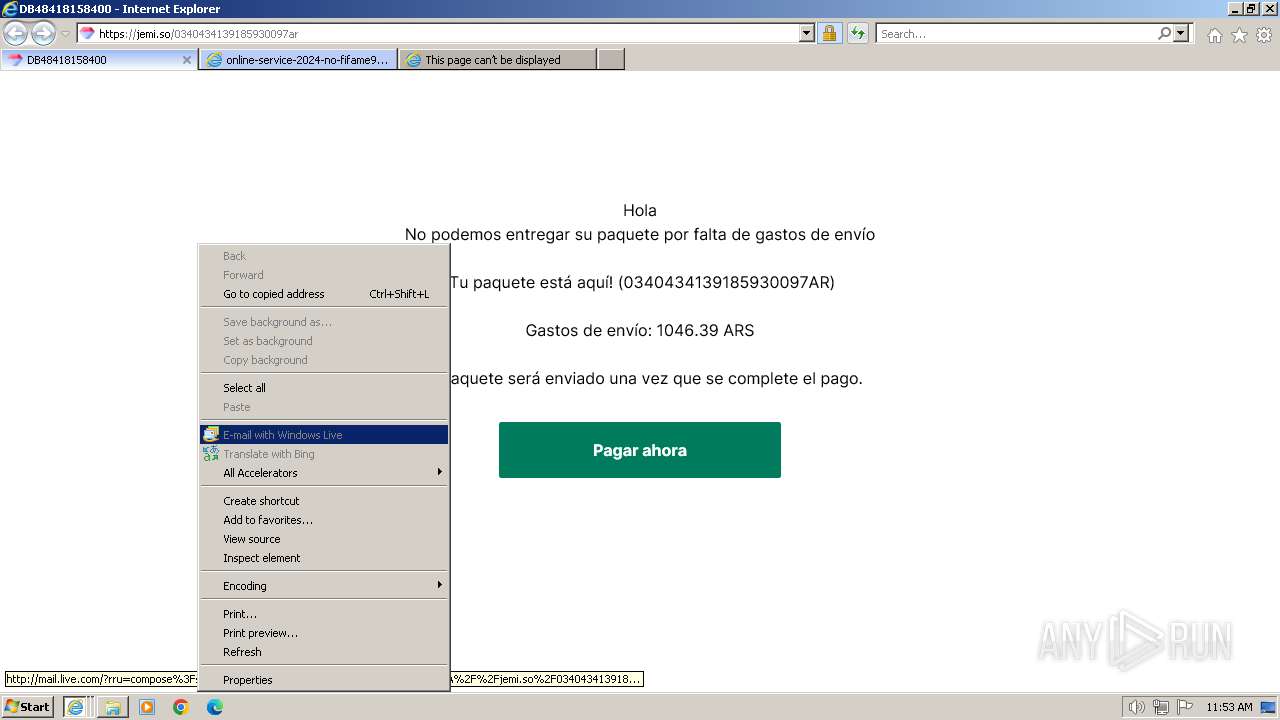
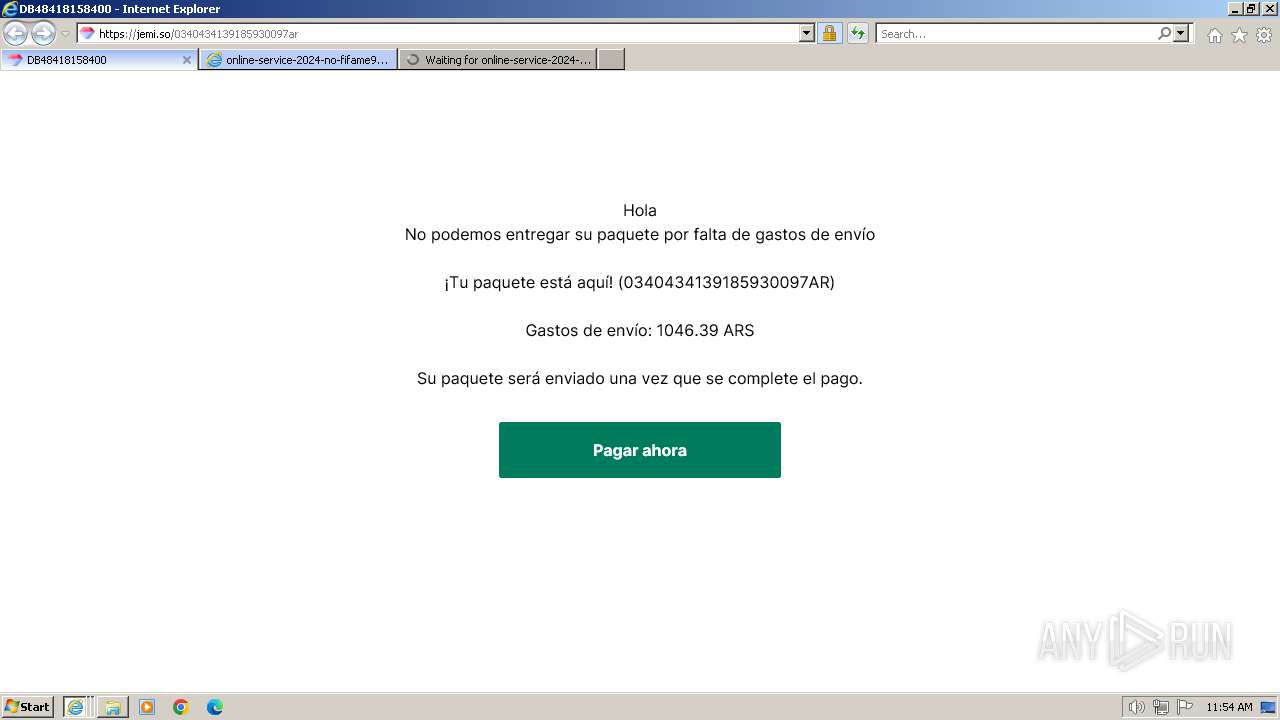
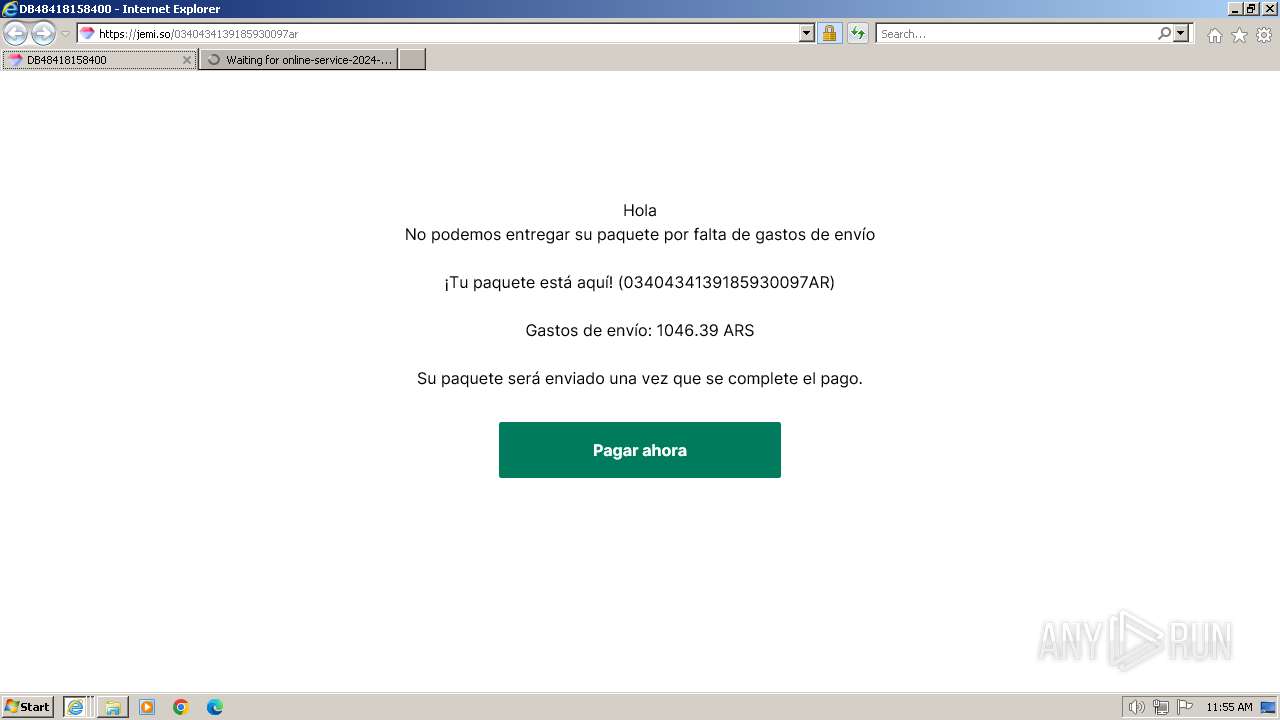
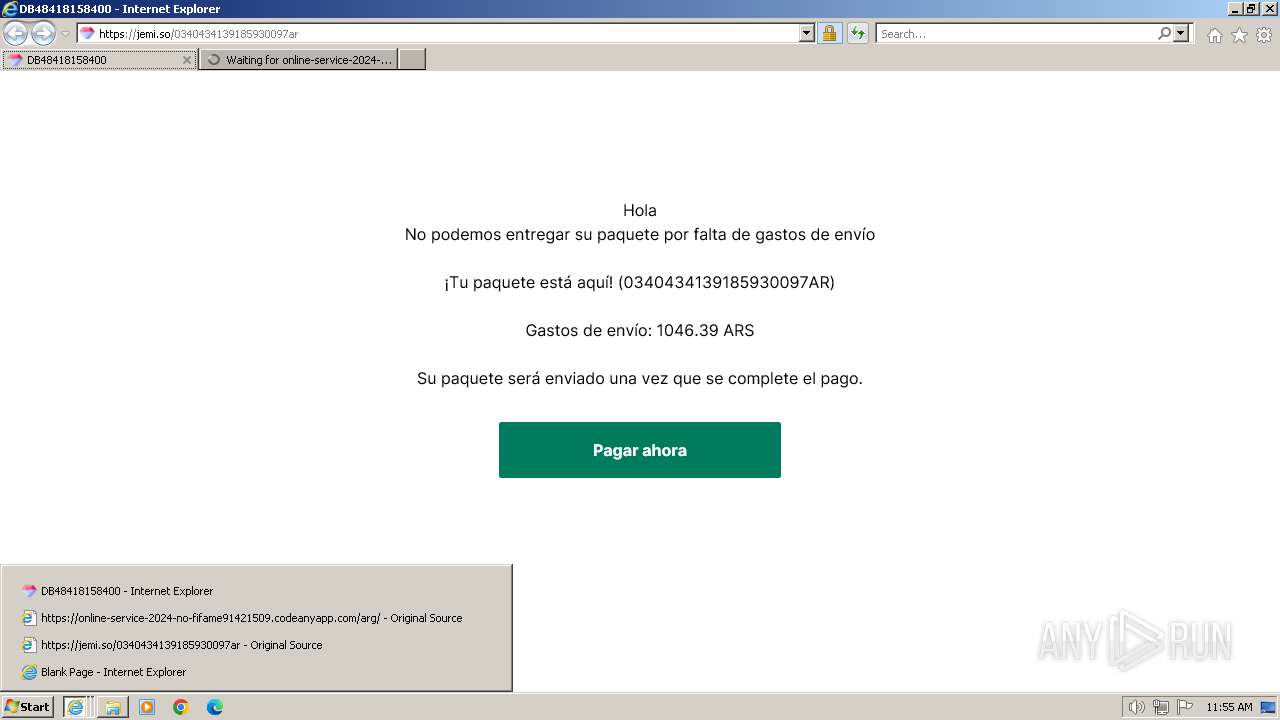
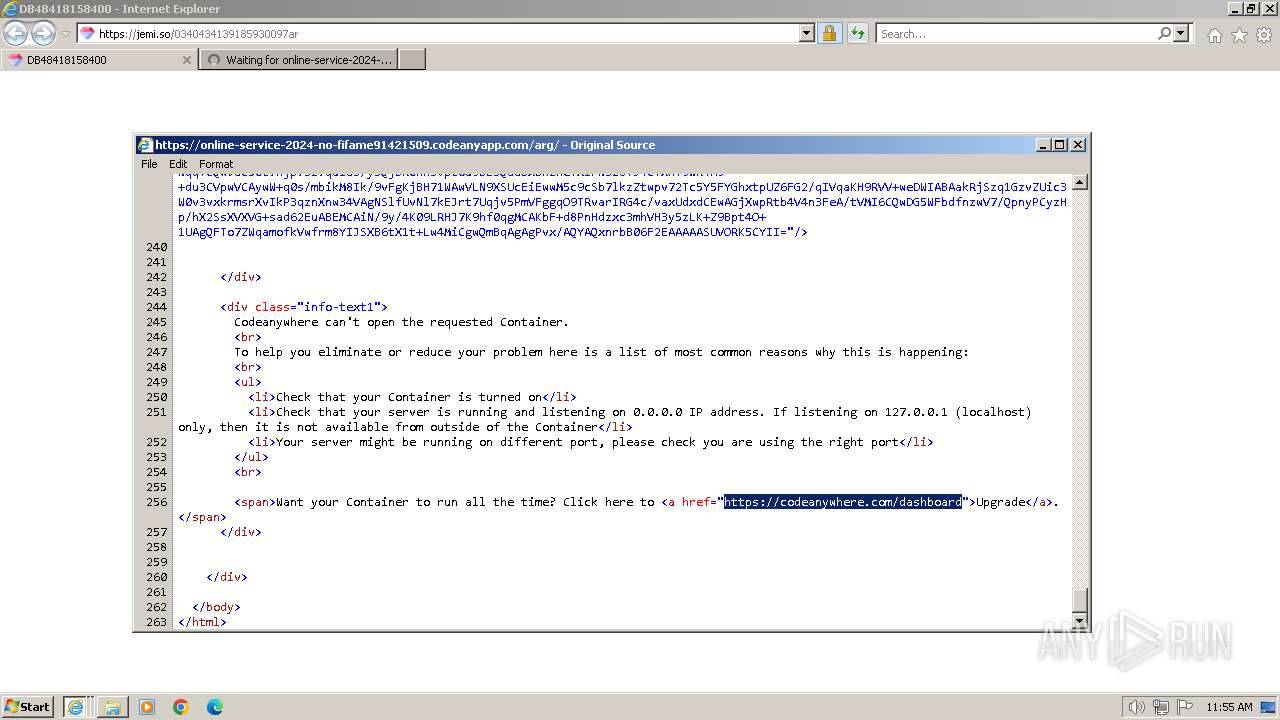
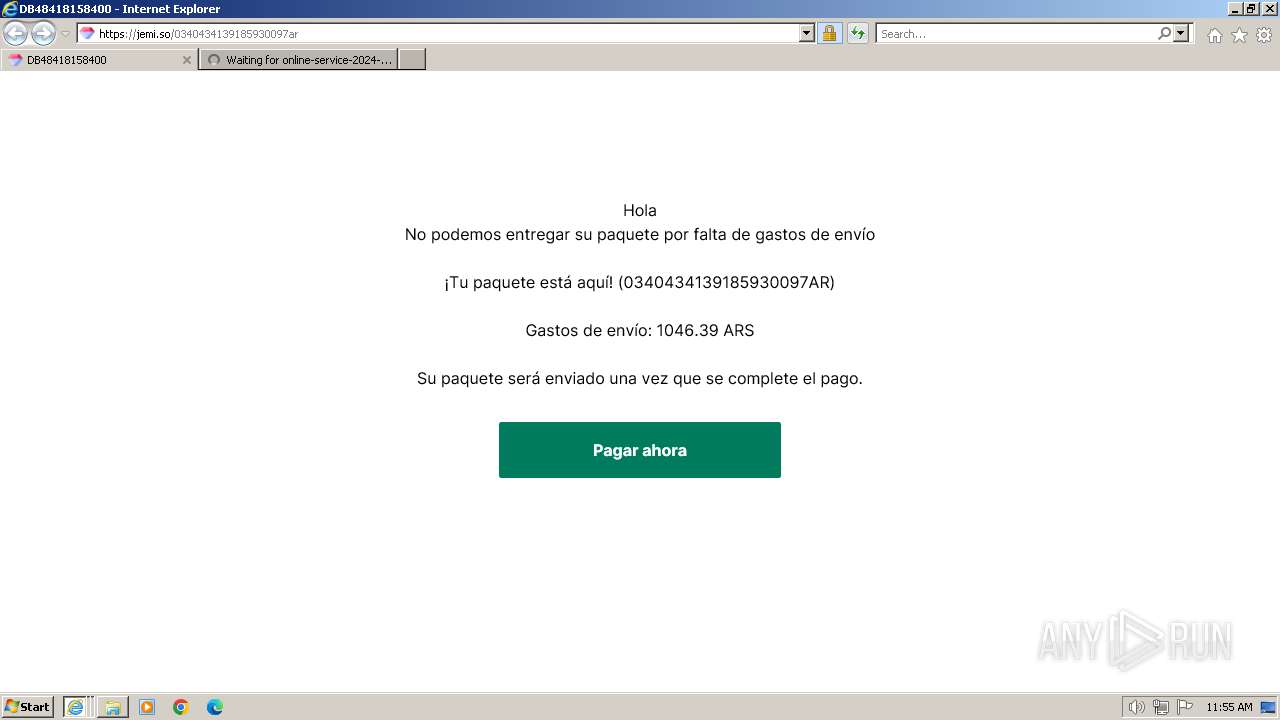
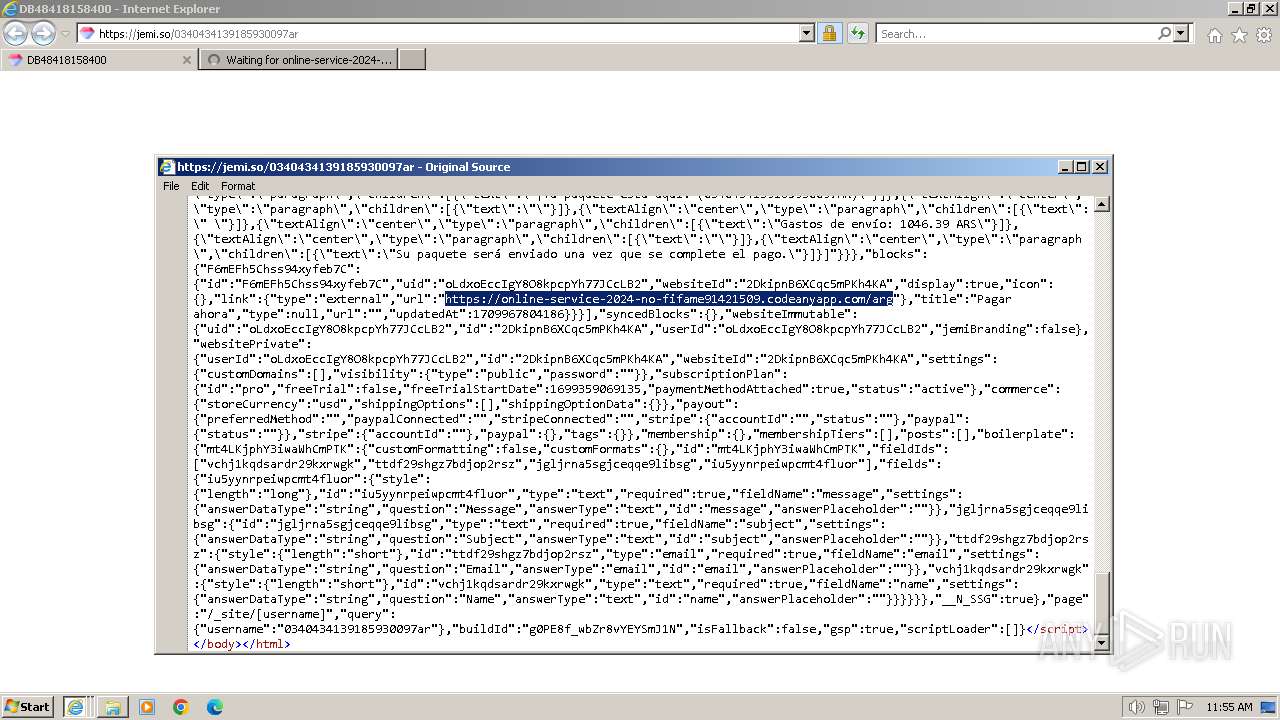
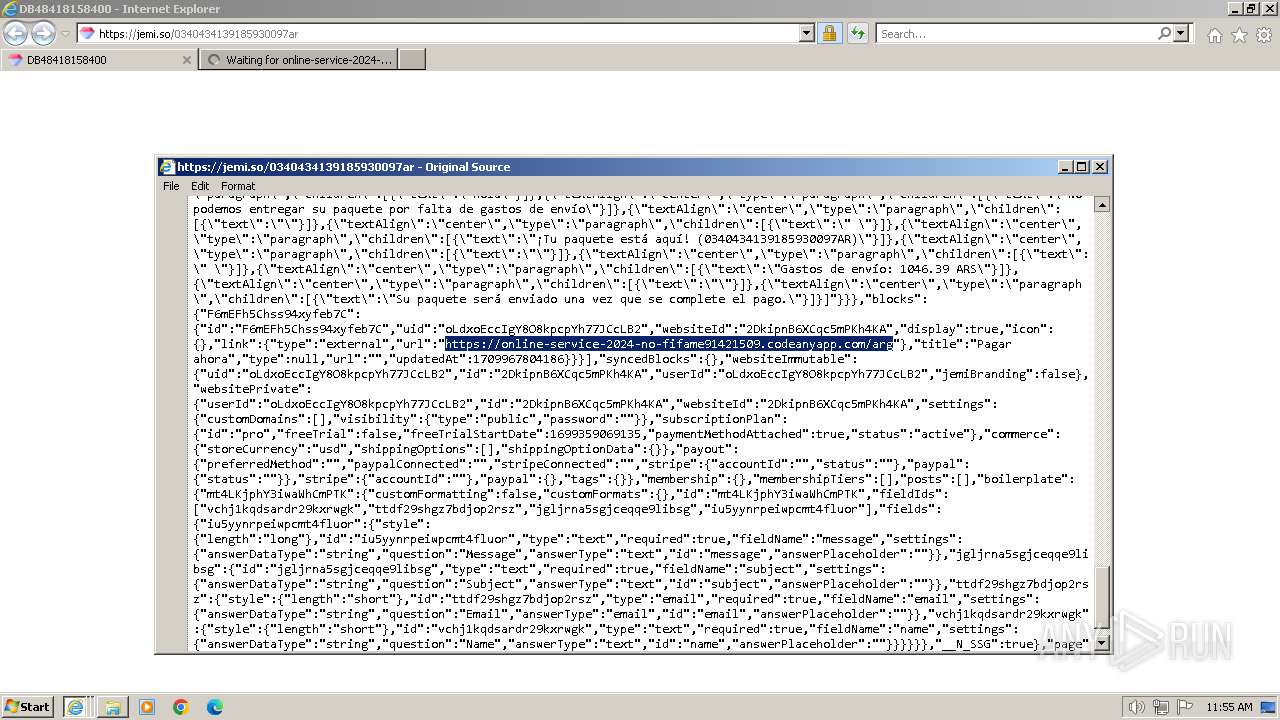
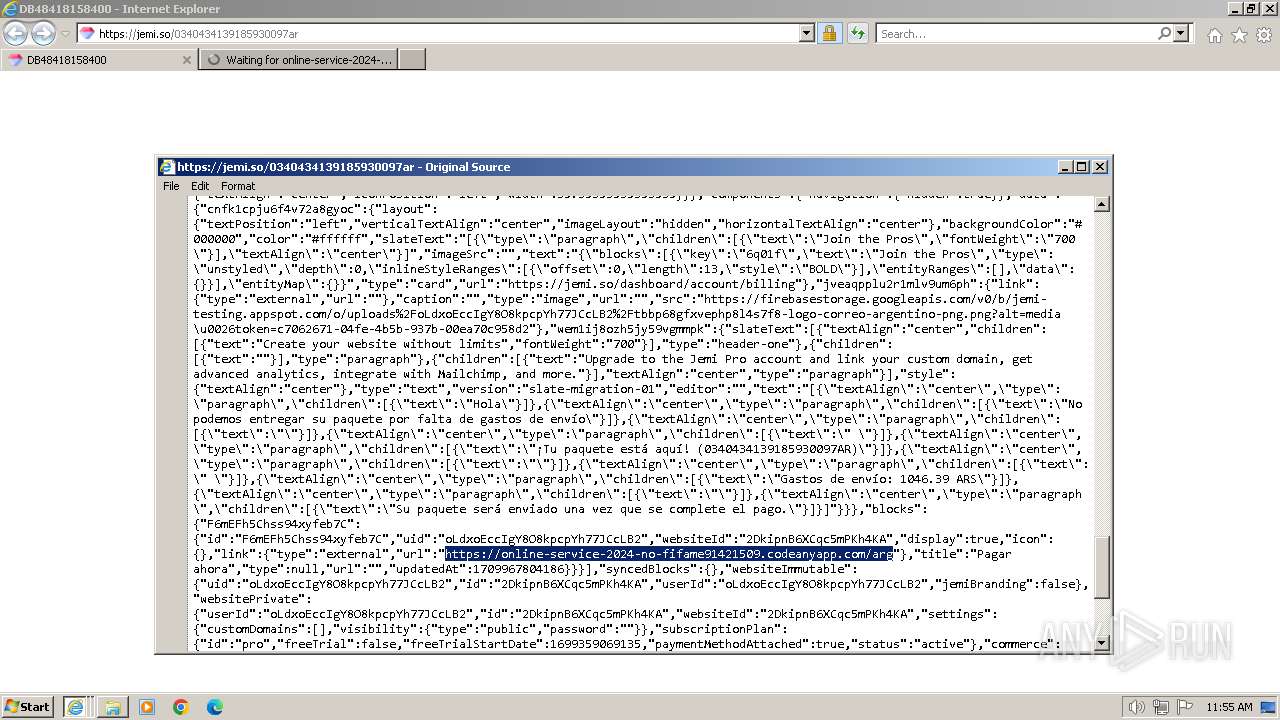
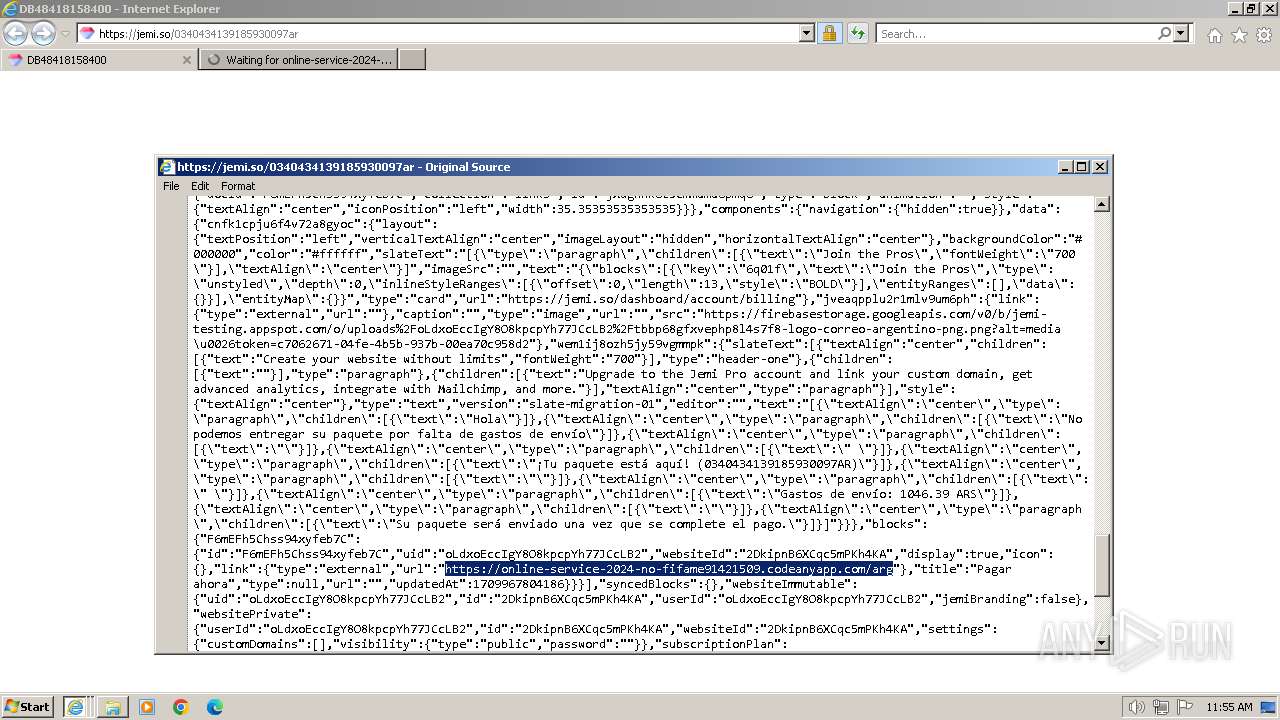
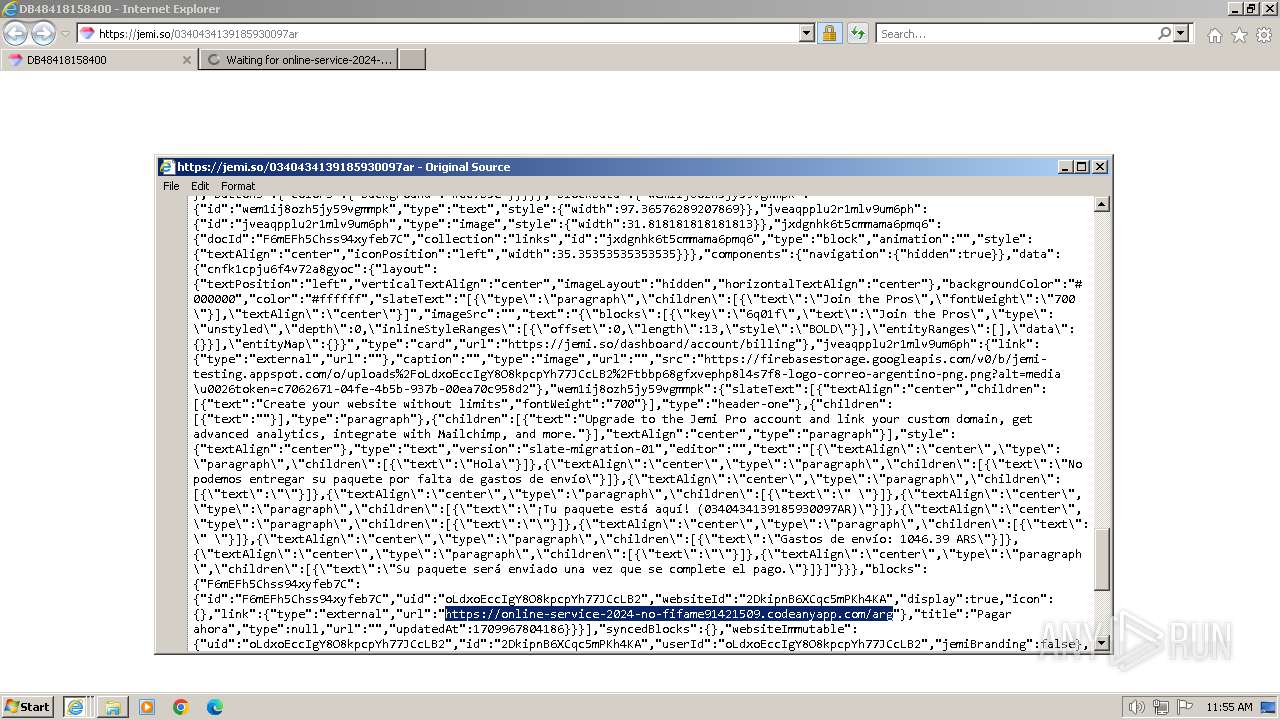
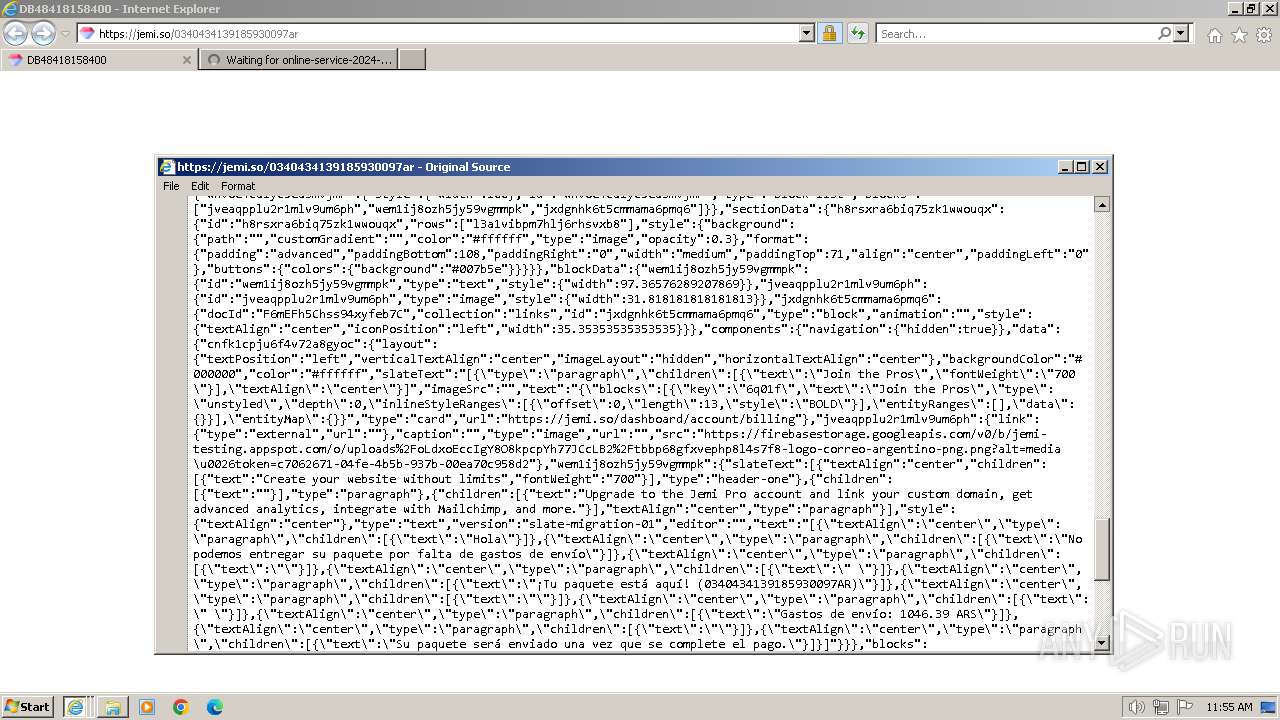
| URL: | https://jemi.so/0340434139185930097ar |
| Full analysis: | https://app.any.run/tasks/26a85592-18a4-4188-ac8f-99552587090e |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 11:51:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 10371281A4ED106B1EC9310795FE5D6C |
| SHA1: | 8ACCE039AF16BD493036AC5E59BCBD99711DB9C2 |
| SHA256: | F08EF729DDE86E8F0FB6DF10B286D301629EFFB9557E068AF9812B3385C3F8A8 |
| SSDEEP: | 3:N8PNKOwbEQcS1EX:2PVwNV1EX |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- explorer.exe (PID: 2904)
Application launched itself
- iexplore.exe (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2020 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3656 CREDAT:2430217 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2904 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3128 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3656 CREDAT:1447194 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3164 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3656 CREDAT:2626825 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3656 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://jemi.so/0340434139185930097ar" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3720 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3656 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
43 570
Read events
43 217
Write events
171
Delete events
182
Modification events
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093674 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093674 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
35
Text files
61
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3720 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\0340434139185930097ar[1].htm | html | |
MD5:F13D1C353322260C74F13A28AE11BFC2 | SHA256:1AD2E4F6E78965555B8CD903C2B5A3E50F5CFF913313215BCD5037E5448A36E7 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\51e946ef9a7721c1[1].css | text | |
MD5:68E674C6BE4F92C7B258176AC467A9AD | SHA256:F017E4FBAEA9E0BD0D96CE3F629C6231B9850AC7E1DF4FF25016C4EE5F45DE46 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:0DF576571F0D99550FFDC32ACEB96AC6 | SHA256:905A9A9706D008AD20AF0C19C41B6B256FE126790F59BC7B0682D8476ABAB679 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:D7AE309332DA4A350D819FE778FD0D7F | SHA256:6F79012A0DAEBF2A0917C9D9F9D37970DDFDEEE03FD0C5FB0C8FF2550C18ED1F | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\5675-59dde0e98cb22e67[1].js | text | |
MD5:727D8262ED75FCB242947DD3ED550811 | SHA256:51A2097EB5E56F0688A7D38ABC109842A275F60DF3390E55E27256FDBDB37E50 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\5720-b4ce86a272a7def2[1].js | text | |
MD5:AF5AB26F4E306D7B0738A9961C9FA7E3 | SHA256:1053DC448BE5A1CF2D684D58F63D301A898DE35E11F7207D0B8A8A6EC6967910 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\500f6f06-04aadfe60e3aace1[1].js | text | |
MD5:41DAD15DC9131298A2A0B6A18C2EB4A7 | SHA256:745E8B7B4090C7F6C50EB1167C9867BD2AD46FF8A7E1F080784098B15955D3A6 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\polyfills-c67a75d1b6f99dc8[1].js | text | |
MD5:837C0DF77FD5009C9E46D446188ECFD0 | SHA256:0225EB034D024A03BDC90EA6C79F56193662E7C3EEE909696298820E517CBB83 | |||
| 3720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\ec35c2edb97e1c77[1].css | text | |
MD5:B0A5D31FC6CEA6C5E5345EC405E6F8E9 | SHA256:E58E6404584BDB2578340BD4E83019D23CCA86A203213FFBA603DFAB96044E05 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
64
DNS requests
40
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3720 | iexplore.exe | GET | 304 | 2.18.121.71:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5b0325f31ae0f9b6 | unknown | — | — | unknown |
3720 | iexplore.exe | GET | 304 | 2.18.121.71:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
3720 | iexplore.exe | GET | 200 | 2.16.209.51:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3720 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3720 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3720 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3720 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCimReIRyQtphKmdTNhBzaE | unknown | binary | 472 b | unknown |
3720 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH6FWuT3fbHwEAPEHSB2q%2B0%3D | unknown | binary | 471 b | unknown |
3656 | iexplore.exe | GET | 304 | 2.18.121.71:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4dd617501e33218a | unknown | — | — | unknown |
3720 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEmjnEcAcBIRCdkf7NhadAI%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3720 | iexplore.exe | 76.76.21.22:443 | jemi.so | AMAZON-02 | US | unknown |
3720 | iexplore.exe | 2.18.121.71:80 | ctldl.windowsupdate.com | AKAMAI-AS | FR | unknown |
3720 | iexplore.exe | 2.16.209.51:80 | x1.c.lencr.org | AKAMAI-AS | FR | unknown |
3720 | iexplore.exe | 142.250.186.40:443 | www.googletagmanager.com | GOOGLE | US | unknown |
3720 | iexplore.exe | 104.16.85.20:443 | cdn.jsdelivr.net | CLOUDFLARENET | — | shared |
3720 | iexplore.exe | 216.58.206.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3720 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jemi.so |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DNS Query to Domain used for Phishing (jemi .so) |
3720 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |
3720 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |
3720 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |
3720 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |
3720 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3720 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |
3720 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3720 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |
3656 | iexplore.exe | Misc activity | ET INFO Observed Domain used for Phishing in TLS SNI (jemi .so) |