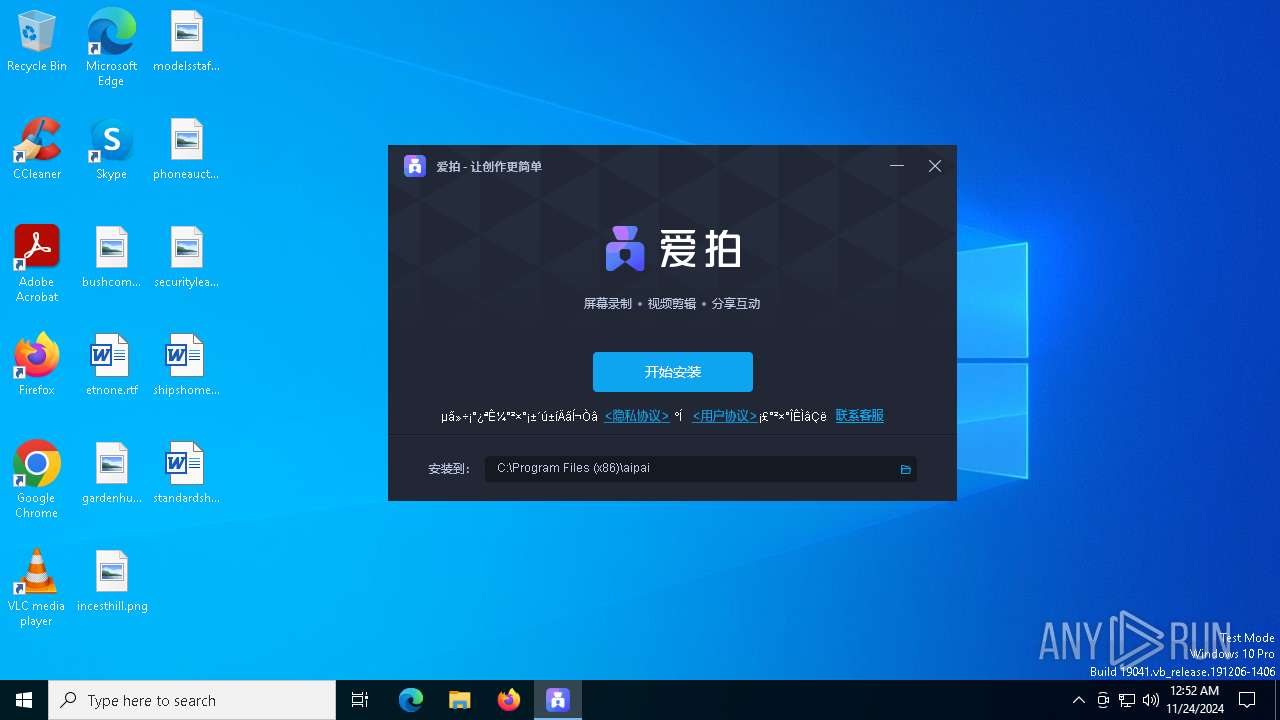
| File name: | aipai.exe |
| Full analysis: | https://app.any.run/tasks/1532926c-41f4-450c-b219-aad9fe9ca820 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 00:52:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 49EC36E7DEAFC1A74934BF9767C3A848 |
| SHA1: | 6B61D8F7A29AA716032680C55CC6DEA3D0D0B2B7 |
| SHA256: | F05602D2AD03C0428A718F74A1F7655A666B3F05826ACF89A7D7DD52E211522D |
| SSDEEP: | 24576:fbH0znk2/0GUFDPfSNvxUxKv3e3wWAGrHTZ1J0yMT1xce0vJul1SuSx6r5l4Ge:fr0znk28GUFDPfSNvxUxK/WwWA8TZ1Jr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- aipai.exe (PID: 1876)
The process creates files with name similar to system file names
- aipai.exe (PID: 1876)
Executable content was dropped or overwritten
- aipai.exe (PID: 1876)
Reads security settings of Internet Explorer
- aipai.exe (PID: 1876)
Drops 7-zip archiver for unpacking
- aipai.exe (PID: 1876)
INFO
Checks supported languages
- aipai.exe (PID: 1876)
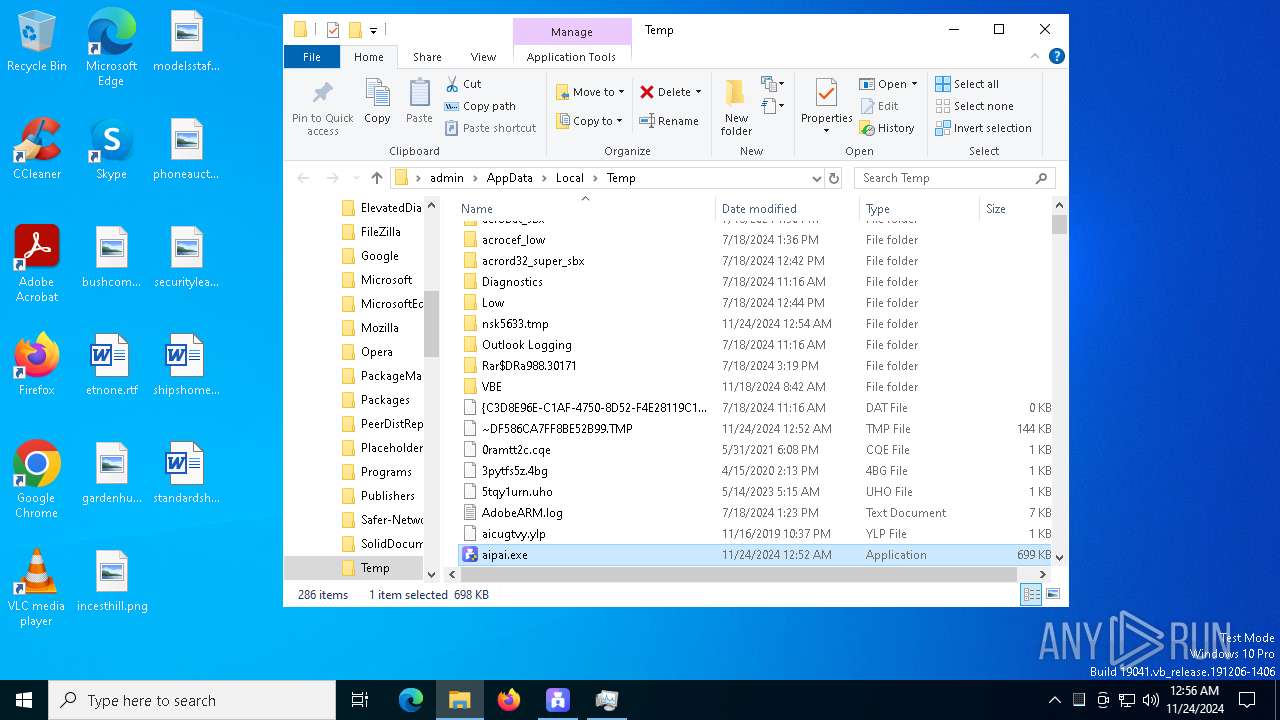
Create files in a temporary directory
- aipai.exe (PID: 1876)
Reads the computer name
- aipai.exe (PID: 1876)
Checks proxy server information
- aipai.exe (PID: 1876)
Creates files or folders in the user directory
- aipai.exe (PID: 1876)
Creates files in the program directory
- aipai.exe (PID: 1876)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3692)
Manual execution by a user
- Taskmgr.exe (PID: 5032)
- Taskmgr.exe (PID: 3692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 03:57:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 162816 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x320c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.9.0.0 |
| ProductVersionNumber: | 4.9.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | 爱拍安装程序 |
| CompanyName: | 广州音视舞动网络科技有限公司 |
| FileDescription: | 爱拍安装程序 |
| FileVersion: | 4.9.0.0 |
| LegalCopyright: | Copyright (c) 2008-2024 广州音视舞动网络科技有限公司 保留所有权利 |
| ProductName: | 爱拍 |
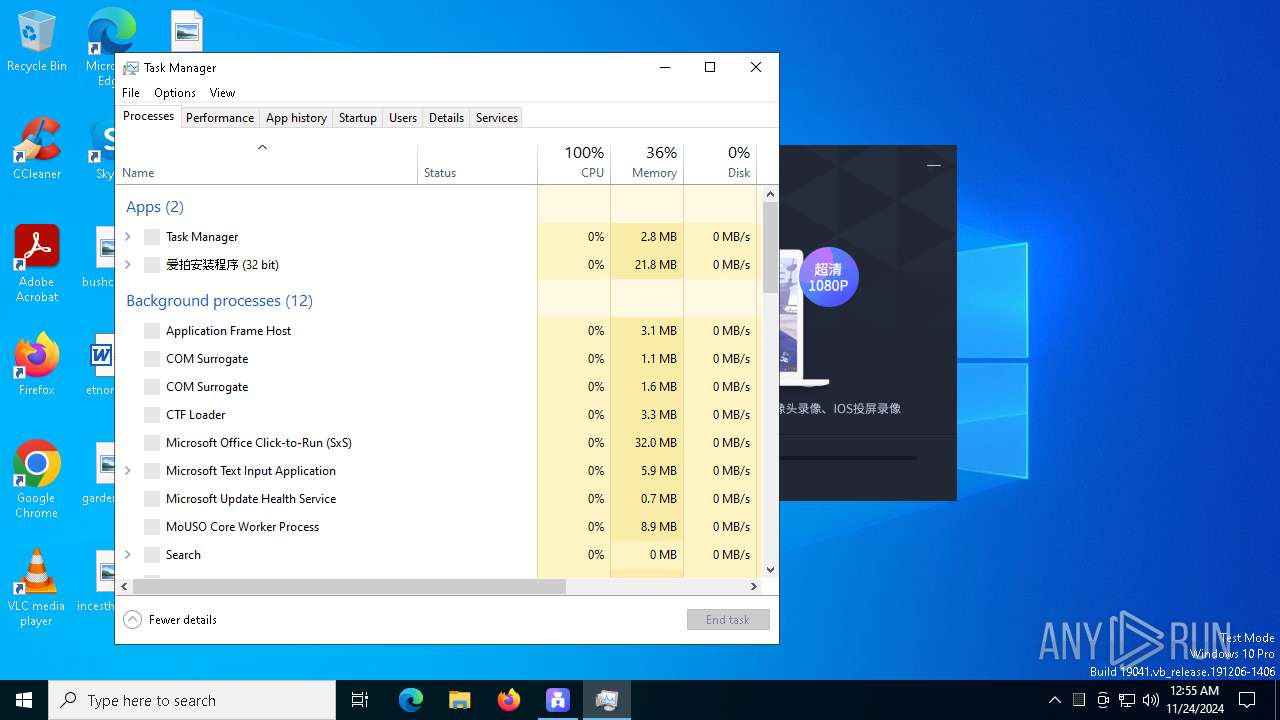
Total processes
130
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1876 | "C:\Users\admin\AppData\Local\Temp\aipai.exe" | C:\Users\admin\AppData\Local\Temp\aipai.exe | explorer.exe | ||||||||||||
User: admin Company: 广州音视舞动网络科技有限公司 Integrity Level: HIGH Description: 爱拍安装程序 Version: 4.9.0.0 Modules
| |||||||||||||||
| 3436 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\AppData\Local\Temp\aipai.exe" | C:\Users\admin\AppData\Local\Temp\aipai.exe | — | explorer.exe | |||||||||||
User: admin Company: 广州音视舞动网络科技有限公司 Integrity Level: MEDIUM Description: 爱拍安装程序 Exit code: 3221226540 Version: 4.9.0.0 Modules
| |||||||||||||||
| 3692 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 552
Read events
2 547
Write events
4
Delete events
1
Modification events
| (PID) Process: | (1876) aipai.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1876) aipai.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1876) aipai.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3692) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (3692) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA6C15F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA6C15F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB6C15F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB6C15F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB6C15F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AA6C15F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB6C15F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB6C15F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB6C15F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB6C15F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB6C15F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC6C15F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA6C15F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC6C15F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC6C15F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC6C15F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC6C15F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC6C15F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC6C15F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB6C15F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD6C15F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB6C15F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA6C15F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB6C15F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB6C15F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB6C15F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB6C15F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA6C15F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE6C15F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
Executable files
9
Suspicious files
68
Text files
3 231
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\bg_complete.bmp | image | |
MD5:DA8C250C43264A4737ECF8F4D911C272 | SHA256:8030D04B1EE53D92EF63EFDCD82007B469340FFBDDAECB3DBEAACB4A4BD9AB65 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\btn_complete.bmp | image | |
MD5:0B9EBCB2B92EF3A2DCFD7D42F39978D2 | SHA256:23F640813344821B7D29672B282A29DD645E76F19FD9CCD9C21754EE8119B5CF | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\UserInfo.dll | executable | |
MD5:DADA3E1836AF78D5B24499DA252D01E4 | SHA256:0073337816509851476C2CC154F471A3E3A1A2806B97C363870ACC09A30A5ED7 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\bg.bmp | image | |
MD5:EF03327C0C01CEEDB7A4324BB995257F | SHA256:EC79C542CCFF6013DBA23C211272031D3E60830CBE98C7457F60CD4144A82A15 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\btn_close.bmp | image | |
MD5:C37019BE4A261359EFA0CABFDA13492D | SHA256:E68572CC808470587FEDCFF5DA5671BEE78DFB954D90A5FC8C10374565597664 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\btn_next.bmp | image | |
MD5:A5AC314FBAD0FC15F12B8E051B16CAE2 | SHA256:981AF44A05576B2F969AC37AA34F43BCEE93CC97F51F477E68622878DC5BE375 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\btn_min.bmp | image | |
MD5:BD95CC1B1D6C260E4B7F1228B0D4E1D4 | SHA256:E21AA3F0AA8053C0E573928F06980454444868E097CEEF3919DCF498E575C6C9 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\btn_directoryselect.bmp | image | |
MD5:85B342E031EFFB6D4FAD4A51276027B1 | SHA256:866E469CD8070C1B646756934D45369FD410DA951503B98728A9CB154B8B1266 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\System.dll | executable | |
MD5:B0C77267F13B2F87C084FD86EF51CCFC | SHA256:A0CAC4CF4852895619BC7743EBEB89F9E4927CCDB9E66B1BCD92A4136D0F9C77 | |||
| 1876 | aipai.exe | C:\Users\admin\AppData\Local\Temp\nsk5633.tmp\btn_website.bmp | image | |
MD5:FD4E754E4D76AFA703EFC5F801E6A8D4 | SHA256:2953F1090AA5BE3458B54B2079EA51925D4453891AB6FAD6C26201CAA127C2A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
35
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2324 | svchost.exe | GET | 200 | 2.19.126.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 2.19.126.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.126.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2324 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1876 | aipai.exe | GET | 200 | 180.184.213.110:80 | http://mlog.aipai.com/a.gif?eyJhcGxhbl9wbGF0IjogInBjIiwgImFwbGFuX2FrIjogImQ4NWViY2I3YWJiZDRhNGU5N2E5OTExYWRiODIyOTZjMjJiZSIsICJhcGxhbl9jaCI6ICJvZmZpY2lhbF90IiwgImFwbGFuX3VpZCI6IDEsICJhcGxhbl9zZGt2IjogIjEiLCAiYXBsYW5fYXBwdmVyIjogIjQuOS4wIiwgImFwbGFuX2V0IjogInllcyIsICJhcGxhbl9laWQiOiAicGNpX3N0YXJ0IiwgImFwbGFuX2ZhIjogIjAiLCAiYXBsYW5fc2lkIjogIjEiLCAiYXBsYW5fdHMiOiAwfQ== | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2008 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1876 | aipai.exe | GET | — | 42.56.77.135:80 | http://download.aipai.com/dashi_files/aipai64x.7z | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.11.168.232:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2324 | svchost.exe | 2.19.126.146:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.126.146:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.19.126.146:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2324 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
mlog.aipai.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.aipai.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1876 | aipai.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
1876 | aipai.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |