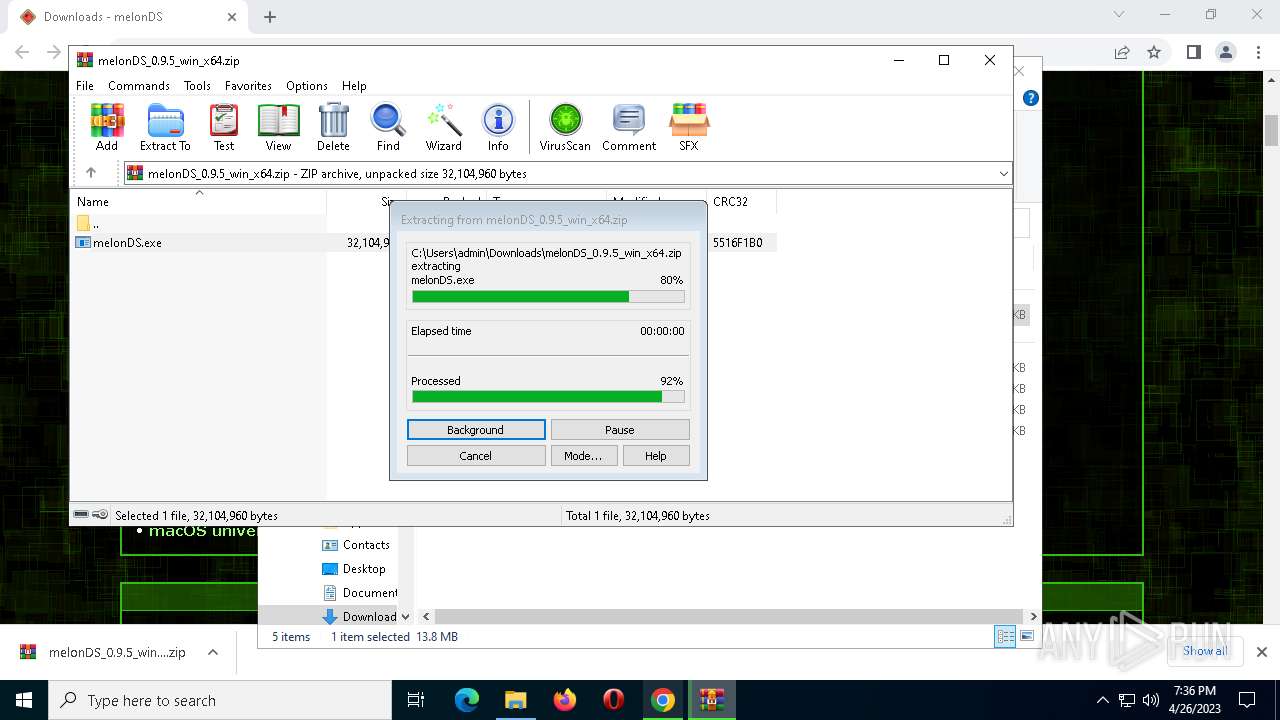
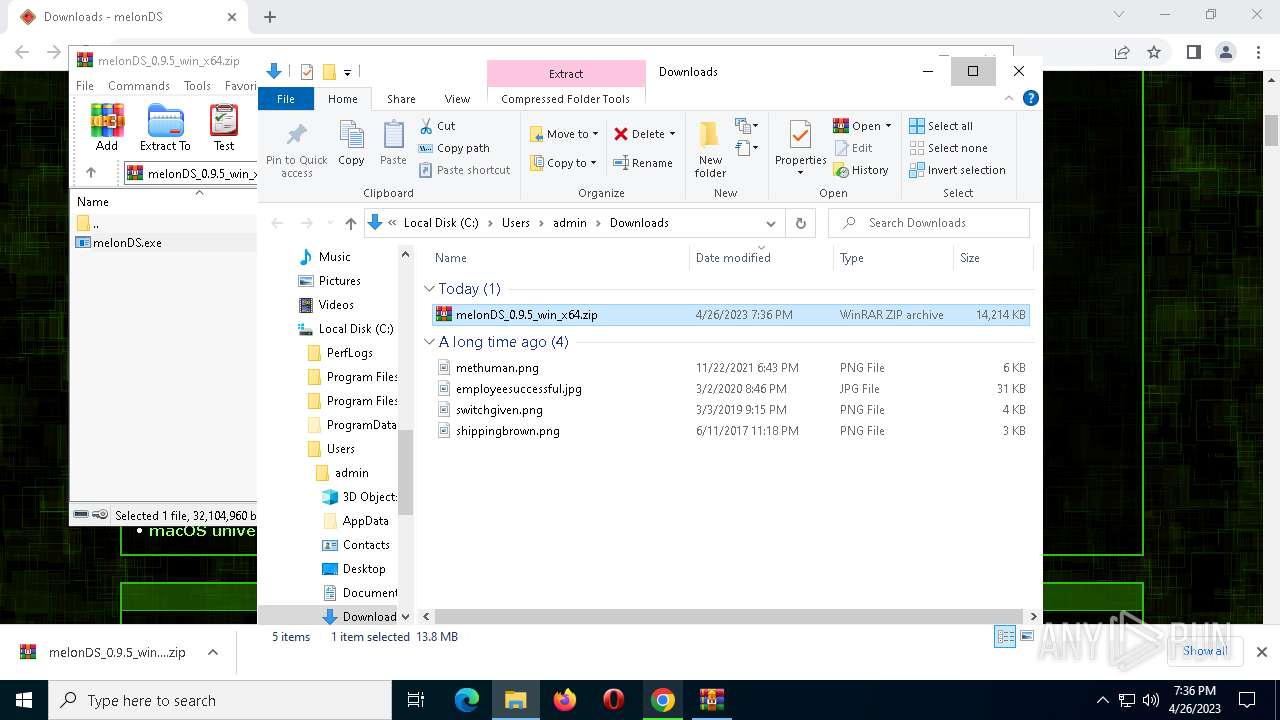
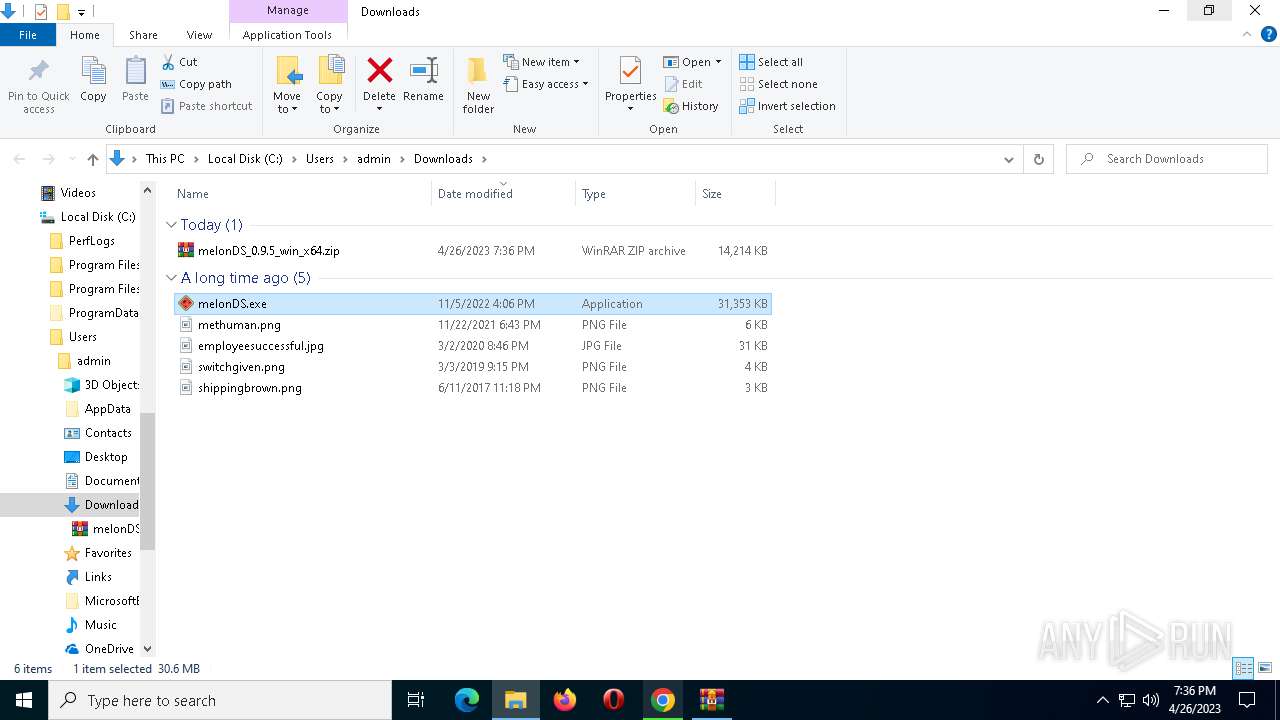
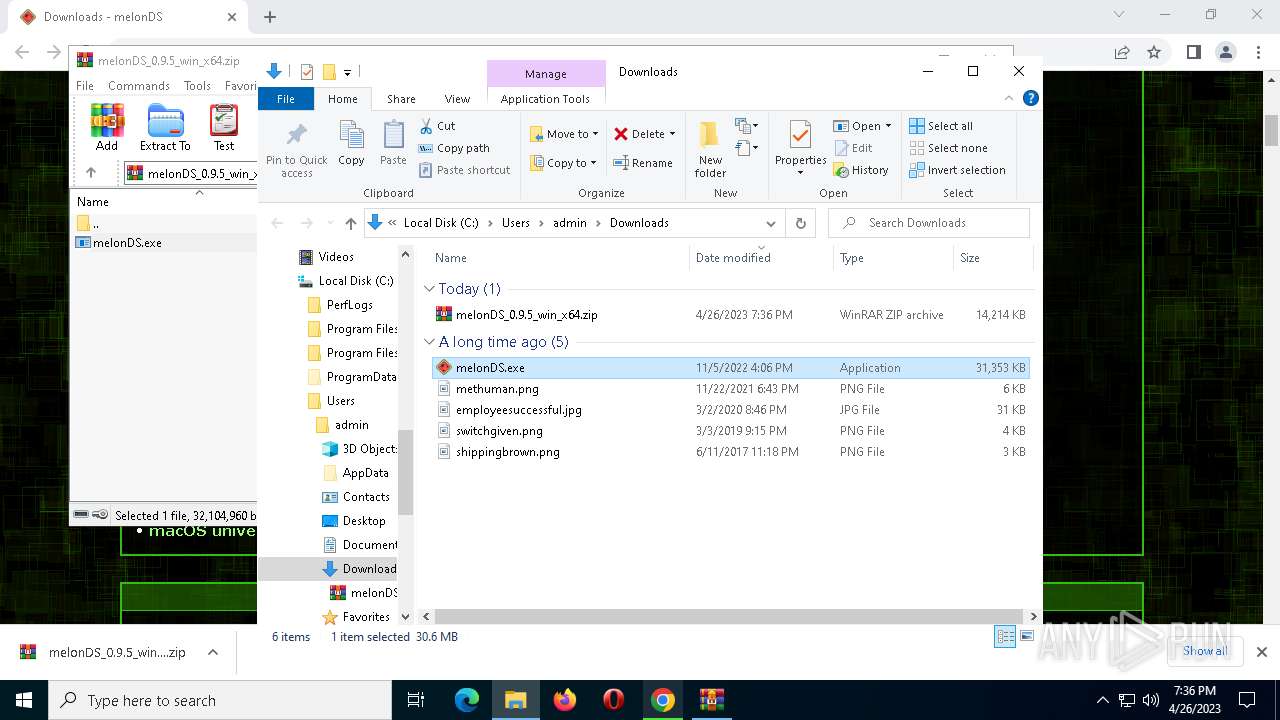
| URL: | https://melonds.kuribo64.net/downloads.php |
| Full analysis: | https://app.any.run/tasks/1a10ea9f-9cac-4489-9946-8820d37cf91f |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2023, 19:36:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 722119306B2288D7E660D7087A70FA60 |
| SHA1: | 260879CB2297A9D55378B722ED9051E054BACEAF |
| SHA256: | F03B17B34AB469F629A2C6B16138CADE735148D228CB836B580A32664BD4678B |
| SSDEEP: | 3:N8U1WAqdLoKBKXLV:2U1WA7K8h |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- elevation_service.exe (PID: 3420)
- elevation_service.exe (PID: 5852)
Executable content was dropped or overwritten
- elevation_service.exe (PID: 5852)
Reads settings of System Certificates
- ChromeRecovery.exe (PID: 6052)
Application launched itself
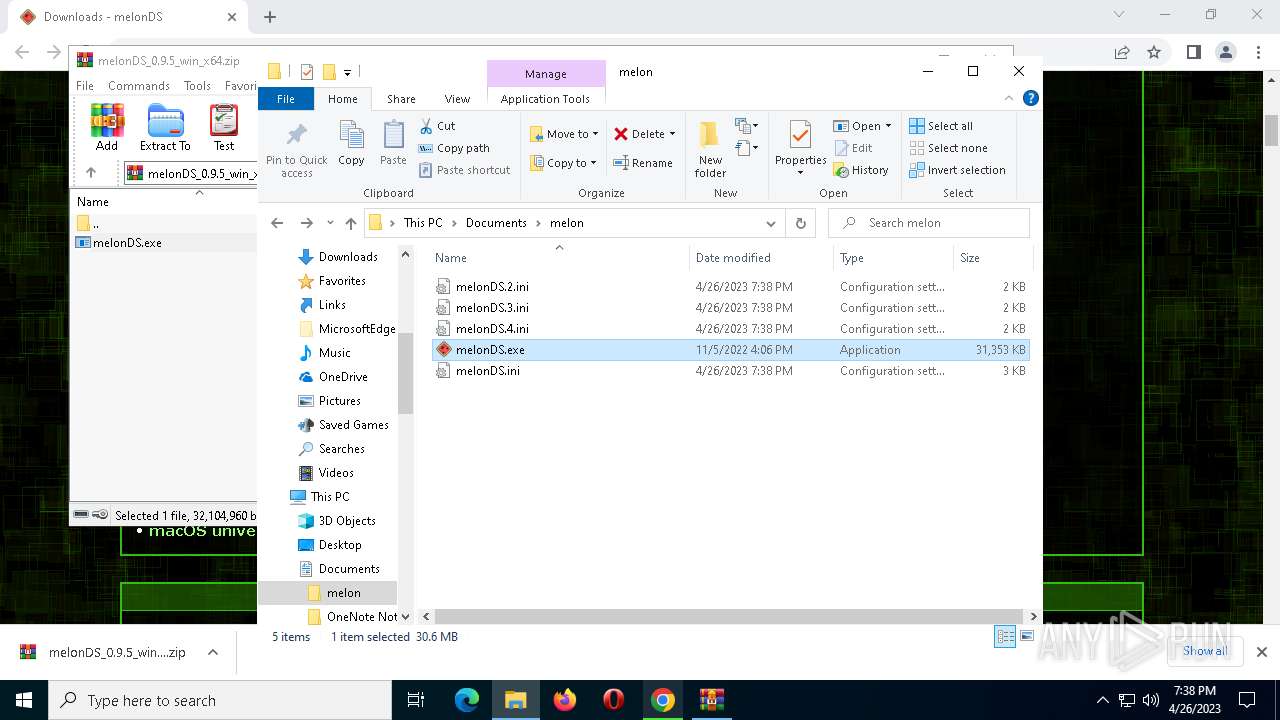
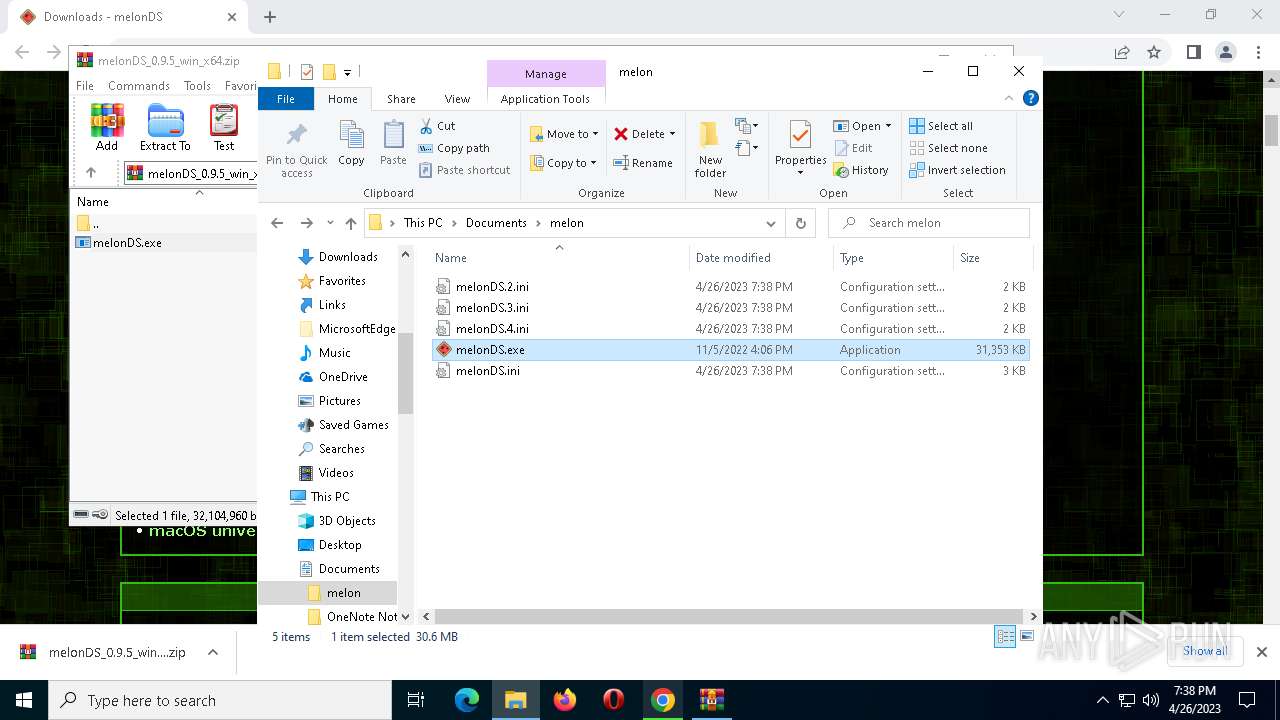
- melonDS.exe (PID: 2248)
- melonDS.exe (PID: 1340)
- melonDS.exe (PID: 2592)
INFO
Reads the computer name
- elevation_service.exe (PID: 3420)
- melonDS.exe (PID: 2248)
- elevation_service.exe (PID: 5852)
- ChromeRecovery.exe (PID: 6052)
- melonDS.exe (PID: 1340)
- melonDS.exe (PID: 2592)
- melonDS.exe (PID: 3344)
Application launched itself
- chrmstp.exe (PID: 6628)
- chrmstp.exe (PID: 1912)
- chrome.exe (PID: 5808)
The process uses the downloaded file
- chrome.exe (PID: 4432)
- chrome.exe (PID: 1108)
- chrome.exe (PID: 5576)
- WinRAR.exe (PID: 4200)
- chrome.exe (PID: 884)
- chrome.exe (PID: 4884)
- chrome.exe (PID: 2916)
Create files in a temporary directory
- chrome.exe (PID: 5808)
The process checks LSA protection
- melonDS.exe (PID: 2248)
- ChromeRecovery.exe (PID: 6052)
- melonDS.exe (PID: 1340)
- melonDS.exe (PID: 2592)
- melonDS.exe (PID: 3344)
- elevation_service.exe (PID: 3420)
- slui.exe (PID: 6432)
- elevation_service.exe (PID: 5852)
Checks supported languages
- melonDS.exe (PID: 1340)
- elevation_service.exe (PID: 5852)
- melonDS.exe (PID: 2592)
- ChromeRecovery.exe (PID: 6052)
- elevation_service.exe (PID: 3420)
- melonDS.exe (PID: 2248)
- melonDS.exe (PID: 3344)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4200)
- chrome.exe (PID: 4000)
Manual execution by a user
- WinRAR.exe (PID: 4200)
- melonDS.exe (PID: 2248)
Checks proxy server information
- slui.exe (PID: 6432)
Reads the software policy settings
- slui.exe (PID: 6432)
Creates files in the program directory
- elevation_service.exe (PID: 5852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
172
Monitored processes
42
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2464 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3948 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=5652 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4876 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1340 | C:\Users\admin\Documents\melon\melonDS.exe | C:\Users\admin\Documents\melon\melonDS.exe | — | melonDS.exe | |||||||||||
User: admin Company: Melon Factory of Kuribo64 Integrity Level: MEDIUM Description: melonDS emulator Exit code: 0 Version: 0.9.5 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2224 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3044 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1912 | "C:\Program Files\Google\Chrome\Application\112.0.5615.50\Installer\chrmstp.exe" --system-level --verbose-logging --installerdata="C:\Program Files\Google\Chrome\Application\master_preferences" --create-shortcuts=1 --install-level=0 | C:\Program Files\Google\Chrome\Application\112.0.5615.50\Installer\chrmstp.exe | — | chrmstp.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Installer Exit code: 73 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3076 --field-trial-handle=1912,i,413309715464633948,3511911459348500909,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 2248 | "C:\Users\admin\Documents\melon\melonDS.exe" | C:\Users\admin\Documents\melon\melonDS.exe | — | explorer.exe | |||||||||||
User: admin Company: Melon Factory of Kuribo64 Integrity Level: MEDIUM Description: melonDS emulator Exit code: 0 Version: 0.9.5 Modules
| |||||||||||||||
Total events
33 388
Read events
33 230
Write events
148
Delete events
10
Modification events
| (PID) Process: | (5808) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (5808) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 39 | |||
| (PID) Process: | (5808) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1912) chrmstp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Taskband |
| Operation: | write | Name: | FavoritesResolve |
Value: B20200004C0000000114020000000000C00000000000004683008000200000002A04B02FAAB7D801B3D1B42FAAB7D80155FC7D2FAAB7D8014209000000000000010000000000000000000000000000001E013A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D3012EDF76ACA9B7D801F568B22FAAB7D8011400560031000000000018555D5911005461736B42617200400009000400EFBE274B1B4018555D592E000000058A0200000005000000000000000000000000000000D6C802005400610073006B00420061007200000016008C0032004209000018555D5920004D4943524F537E312E4C4E4B0000560009000400EFBE18555D5918555D592E0000006FC50000000004000000000000000000000000000000ABD034004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B0000001C001A0000001D00EFBE02004D005300450064006700650000001C0000009D0000001C000000010000001C0000002D000000000000009C0000001100000003000000FA99B7261000000000433A5C55736572735C61646D696E5C417070446174615C526F616D696E675C4D6963726F736F66745C496E7465726E6574204578706C6F7265725C517569636B204C61756E63685C557365722050696E6E65645C5461736B4261725C4D6963726F736F667420456467652E6C6E6B000060000000030000A058000000000000006465736B746F702D6A676C6C6A6C640064D4FD8DD0913E488A778CA768B799805F4440C69C23ED11B4AB18F7786F96EE64D4FD8DD0913E488A778CA768B799805F4440C69C23ED11B4AB18F7786F96EE45000000090000A03900000031535053B1166D44AD8D7048A748402EA43D788C1D000000680000000048000000725E5C2FA985EB1190A89A9B76358421000000000000000000000000210300004C0000000114020000000000C00000000000004683008000200000007D43EB6CAF27D3017D43EB6CAF27D301DD21942857DFD1019701000000000000010000000000000000000000000000008E013A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D301FEE1E86CAF27D301FEE1E86CAF27D30114005600310000000000274B1B4011005461736B42617200400009000400EFBE274B1B40274B1B402E000000A88E0100000001000000000000000000000000000000833BF4005400610073006B0042006100720000001600FC00320097010000F048555D200046494C4545587E312E4C4E4B00007C0009000400EFBE274B1B40274B1B402E000000A98E01000000010000000000000000005200000000002383CF00460069006C00650020004500780070006C006F007200650072002E006C006E006B00000040007300680065006C006C00330032002E0064006C006C002C002D003200320030003600370000001C00220000001E00EFBE02005500730065007200500069006E006E006500640000001C00420000001D00EFBE02004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F0072006500720000001C0000009C0000001C000000010000001C0000002D000000000000009B0000001100000003000000FA99B7261000000000433A5C55736572735C61646D696E5C417070446174615C526F616D696E675C4D6963726F736F66745C496E7465726E6574204578706C6F7265725C517569636B204C61756E63685C557365722050696E6E65645C5461736B4261725C46696C65204578706C6F7265722E6C6E6B000060000000030000A058000000000000006465736B746F702D6A676C6C6A6C640064D4FD8DD0913E488A778CA768B79980ABF5E88CA293E711B4245254004AAD1164D4FD8DD0913E488A778CA768B79980ABF5E88CA293E711B4245254004AAD1145000000090000A03900000031535053B1166D44AD8D7048A748402EA43D788C1D000000680000000048000000B52F24F3000000000000501F00000000000000000000000000000000D10200004C0000000114020000000000C0000000000000468300800020000000EFB59A0A457AD701EFB59A0A457AD70139686D0A457AD701ED030000000000000100000000000000000000000000000044013A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D301929B4CECC1D0D301929B4CECC1D0D30114005600310000000000F052496A11005461736B42617200400009000400EFBE274B1B40F052496A2E00000058CC0300000003000000000000000000000000000000119300005400610073006B0042006100720000001600B2003200ED030000F052496A200046697265666F782E6C6E6B00480009000400EFBEF052496AF052496A2E000000ABAB0000000004000000000000000000000000000000C7E02D00460069007200650066006F0078002E006C006E006B0000001A00220000001E00EFBE02005500730065007200500069006E006E006500640000001A002E0000001D00EFBE0200330030003800300034003600420030004100460034004100330039004300420000001A000000960000001C000000010000001C0000002D00000000000000950000001100000003000000FA99B7261000000000433A5C55736572735C61646D696E5C417070446174615C526F616D696E675C4D6963726F736F66745C496E7465726E6574204578706C6F7265725C517569636B204C61756E63685C557365722050696E6E65645C5461736B4261725C46697265666F782E6C6E6B000060000000030000A058000000000000006465736B746F702D6A676C6C6A6C640064D4FD8DD0913E488A778CA768B799804A4DEABB37E6EB11B47718F7786F96EE64D4FD8DD0913E488A778CA768B799804A4DEABB37E6EB11B47718F7786F96EE45000000090000A03900000031535053B1166D44AD8D7048A748402EA43D788C1D000000680000000048000000725E5C2FA985EB1190A89A9B76358421000000000000000000000000370300004C0000000114020000000000C00000000000004683008000200000006D22EB10467AD7016D22EB10467AD7015C60C710467AD701760700000000000001000000000000000000000000000000A2013A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D301929B4CECC1D0D301929B4CECC1D0D30114005600310000000000F052346B11005461736B42617200400009000400EFBE274B1B40F052346B2E00000058CC030000000300000000000000000000000000000093FF23015400610073006B00420061007200000016001001320076070000F052336B20004F50455241317E312E4C4E4B0000580009000400EFBEF052346BF052346B2E000000B3B40000000003000000000000000000000000000000A49416004F007000650072006100310032002E0031003500200031003700340038002E006C006E006B0000001C00220000001E00EFBE02005500730065007200500069006E006E006500640000001C007A0000001D00EFBE02007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C004F0070006500720061005C006F0070006500720061002E0065007800650000001C0000009E0000001C000000010000001C0000002D000000000000009D0000001100000003000000FA99B7261000000000433A5C55736572735C61646D696E5C417070446174615C526F616D696E675C4D6963726F736F66745C496E7465726E6574204578706C6F7265725C517569636B204C61756E63685C557365722050696E6E65645C5461736B4261725C4F7065726131322E313520313734382E6C6E6B000060000000030000A058000000000000006465736B746F702D6A676C6C6A6C640064D4FD8DD0913E488A778CA768B79980C3FD470D39E6EB11B47818F7786F96EE64D4FD8DD0913E488A778CA768B79980C3FD470D39E6EB11B47818F7786F96EE45000000090000A03900000031535053B1166D44AD8D7048A748402EA43D788C1D000000680000000048000000725E5C2FA985EB1190A89A9B76358421000000000000000000000000 | |||
| (PID) Process: | (1912) chrmstp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Taskband |
| Operation: | write | Name: | Favorites |
Value: 001E0100003A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D3012EDF76ACA9B7D801F568B22FAAB7D8011400560031000000000018555D5911005461736B42617200400009000400EFBE274B1B4018555D592E000000058A0200000005000000000000000000000000000000D6C802005400610073006B00420061007200000016008C0032004209000018555D5920004D4943524F537E312E4C4E4B0000560009000400EFBE18555D5918555D592E0000006FC50000000004000000000000000000000000000000ABD034004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B0000001C001A0000001D00EFBE02004D005300450064006700650000001C00000000920100003A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D301FEE1E86CAF27D301FEE1E86CAF27D30114005600310000000000274B1B4011005461736B42617200400009000400EFBE274B1B40274B1B402E000000A88E0100000001000000000000000000000000000000833BF4005400610073006B00420061007200000016000001320097010000F048555D200046494C4545587E312E4C4E4B00007C0009000400EFBE274B1B40274B1B402E000000A98E01000000010000000000000000005200000000002383CF00460069006C00650020004500780070006C006F007200650072002E006C006E006B00000040007300680065006C006C00330032002E0064006C006C002C002D003200320030003600370000001C00420000001D00EFBE02004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F0072006500720000001C00260000001E00EFBE0200530079007300740065006D00500069006E006E006500640000001C00000000440100003A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D301929B4CECC1D0D301929B4CECC1D0D30114005600310000000000F052496A11005461736B42617200400009000400EFBE274B1B40F052496A2E00000058CC0300000003000000000000000000000000000000119300005400610073006B0042006100720000001600B2003200ED030000F052496A200046697265666F782E6C6E6B00480009000400EFBEF052496AF052496A2E000000ABAB0000000004000000000000000000000000000000C7E02D00460069007200650066006F0078002E006C006E006B0000001A00220000001E00EFBE02005500730065007200500069006E006E006500640000001A002E0000001D00EFBE0200330030003800300034003600420030004100460034004100330039004300420000001A00000000A20100003A001F80C827341F105C1042AA032EE45287D668260001002600EFBE12000000E9E9C368AF27D301929B4CECC1D0D301929B4CECC1D0D30114005600310000000000F052346B11005461736B42617200400009000400EFBE274B1B40F052346B2E00000058CC030000000300000000000000000000000000000093FF23015400610073006B00420061007200000016001001320076070000F052336B20004F50455241317E312E4C4E4B0000580009000400EFBEF052346BF052346B2E000000B3B40000000003000000000000000000000000000000A49416004F007000650072006100310032002E0031003500200031003700340038002E006C006E006B0000001C00220000001E00EFBE02005500730065007200500069006E006E006500640000001C007A0000001D00EFBE02007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C004F0070006500720061005C006F0070006500720061002E0065007800650000001C000000FF | |||
| (PID) Process: | (1912) chrmstp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Taskband |
| Operation: | write | Name: | FavoritesChanges |
Value: 12 | |||
| (PID) Process: | (1912) chrmstp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Taskband |
| Operation: | write | Name: | FavoritesVersion |
Value: 3 | |||
| (PID) Process: | (1912) chrmstp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 40 | |||
| (PID) Process: | (4432) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4432) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
8
Suspicious files
167
Text files
238
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\First Run | — | |
MD5:— | SHA256:— | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\33263d58-d2ec-400a-b24b-80ca65528605.tmp | text | |
MD5:0736F546C62DDE5581D445ECE3B7443E | SHA256:8A140428AC74BAA4799BED38DF5562EF775294C5488EC63D35BFF435B012EC0F | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:6938856FB4E39ADCAA9D9664D679E7E3 | SHA256:9FC3A390773A9E5326F7731EF4D54D80400FB7C36BAA62CA81AC2CA8141EDBD3 | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\CURRENT | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Local State | text | |
MD5:0736F546C62DDE5581D445ECE3B7443E | SHA256:8A140428AC74BAA4799BED38DF5562EF775294C5488EC63D35BFF435B012EC0F | |||
| 5808 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
67
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3044 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | der | 409 b | whitelisted |
4420 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rzgupy2nqocui26rvxpe5scoa_389/lmelglejhemejginpboagddgdfbepgmp_389_all_ZZ_ivmhoilgskkpiasz3mpfm2baze.crx3 | US | binary | 1.90 Kb | whitelisted |
5756 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | binary | 471 b | whitelisted |
4420 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjFkQUFWdmlaXy12MHFUTGhWQUViMUVlUQ/0.57.44.2492_hnimpnehoodheedghdeeijklkeaacbdc.crx | US | binary | 86.4 Kb | whitelisted |
4420 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjFkQUFWdmlaXy12MHFUTGhWQUViMUVlUQ/0.57.44.2492_hnimpnehoodheedghdeeijklkeaacbdc.crx | US | binary | 359 Kb | whitelisted |
4420 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjFkQUFWdmlaXy12MHFUTGhWQUViMUVlUQ/0.57.44.2492_hnimpnehoodheedghdeeijklkeaacbdc.crx | US | binary | 1.14 Mb | whitelisted |
4420 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rzgupy2nqocui26rvxpe5scoa_389/lmelglejhemejginpboagddgdfbepgmp_389_all_ZZ_ivmhoilgskkpiasz3mpfm2baze.crx3 | US | binary | 1.26 Kb | whitelisted |
4420 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 1.26 Kb | whitelisted |
4420 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rzgupy2nqocui26rvxpe5scoa_389/lmelglejhemejginpboagddgdfbepgmp_389_all_ZZ_ivmhoilgskkpiasz3mpfm2baze.crx3 | US | binary | 1.09 Kb | whitelisted |
5952 | MoUsoCoreWorker.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | der | 814 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5952 | MoUsoCoreWorker.exe | 2.18.233.62:80 | — | AKAMAI-AS | DE | whitelisted |
5756 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5288 | chrome.exe | 174.138.8.161:443 | melonds.kuribo64.net | DIGITALOCEAN-ASN | NL | unknown |
5288 | chrome.exe | 216.58.212.141:443 | accounts.google.com | GOOGLE | US | whitelisted |
5288 | chrome.exe | 216.58.212.132:443 | www.google.com | GOOGLE | US | whitelisted |
1872 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4736 | SearchApp.exe | 2.16.186.203:443 | — | Akamai International B.V. | DE | whitelisted |
4736 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5756 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3044 | SIHClient.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
melonds.kuribo64.net |
| unknown |
accounts.google.com |
| shared |
officeclient.microsoft.com |
| whitelisted |
www.google.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |