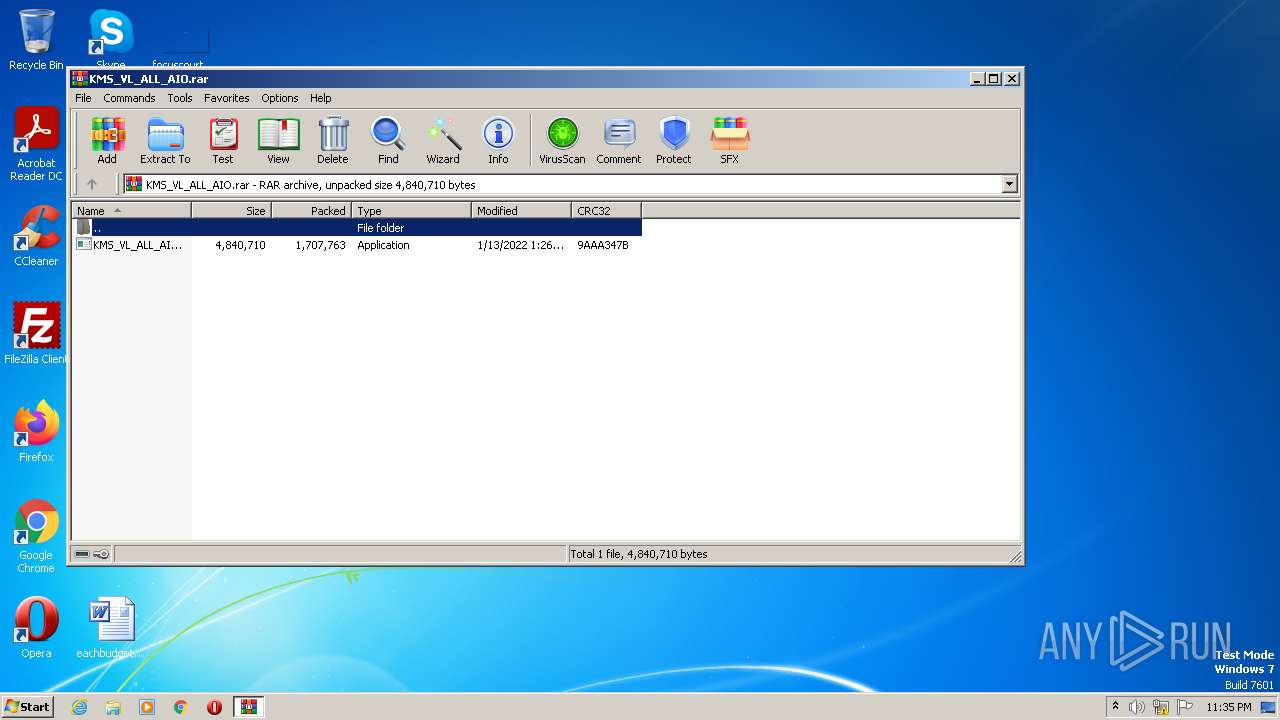
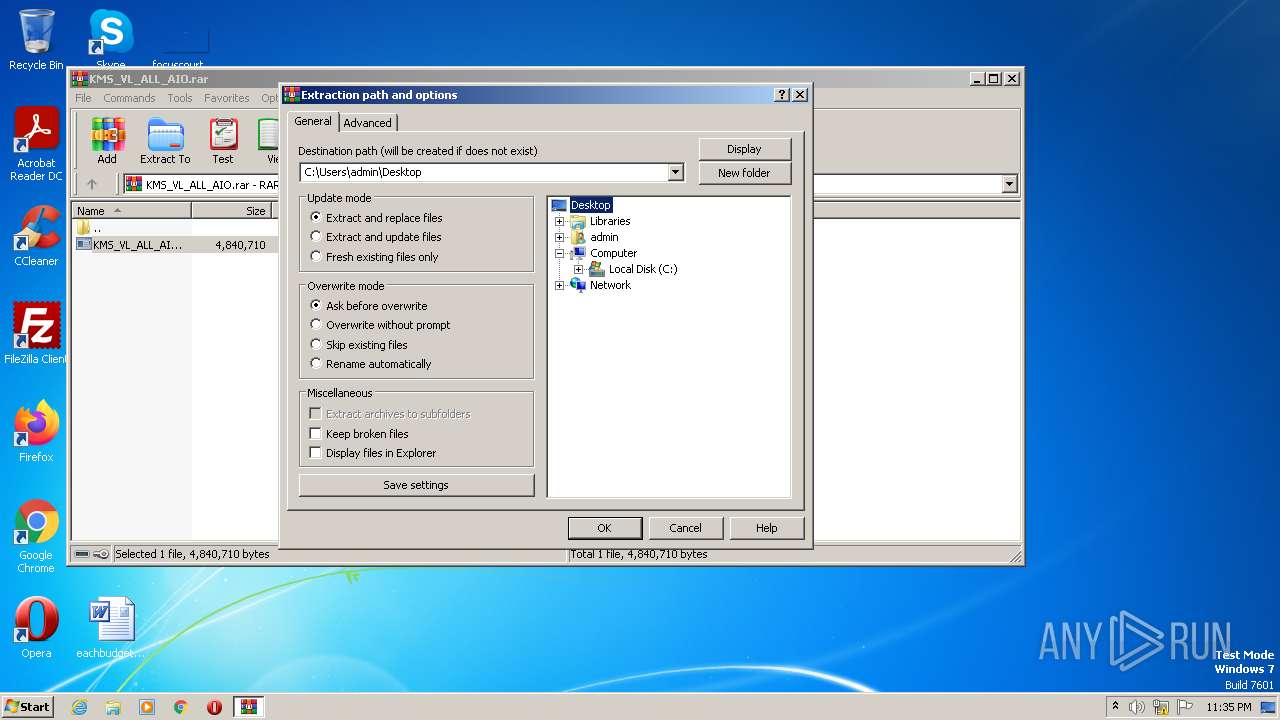
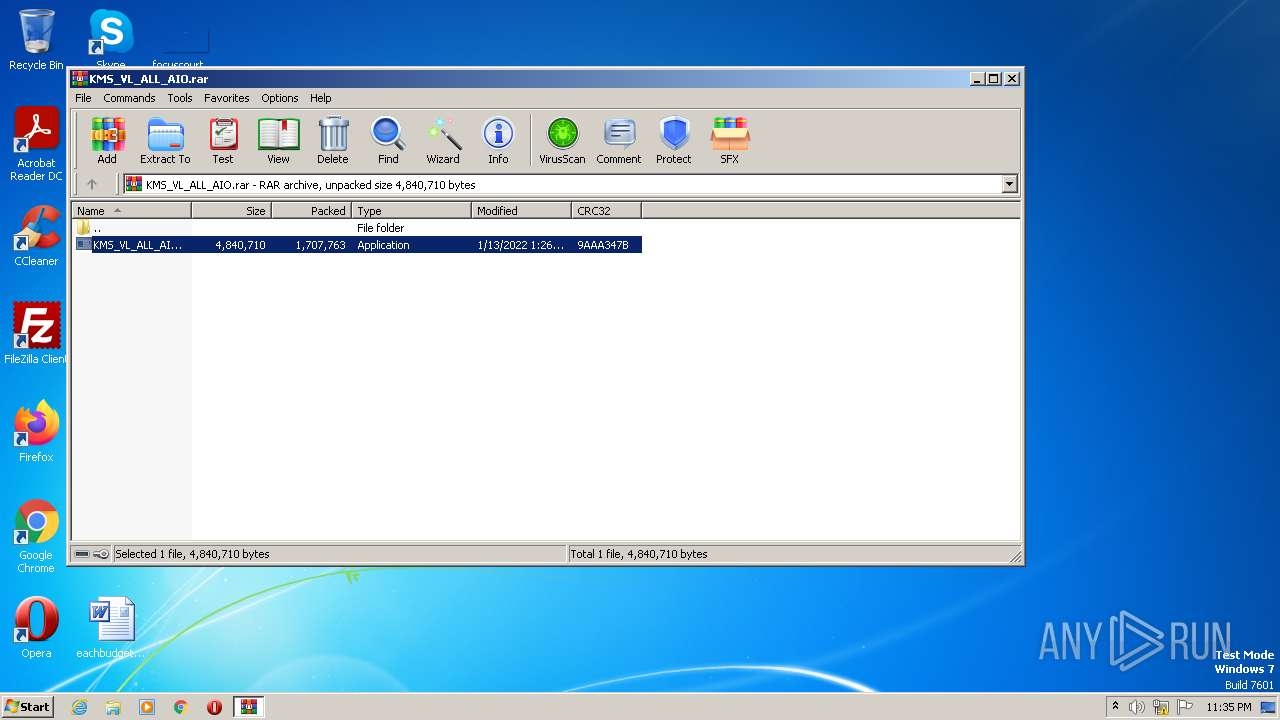
| File name: | KMS_VL_ALL_AIO.rar |
| Full analysis: | https://app.any.run/tasks/f682f7af-521a-471d-a8fb-3b53cbef1744 |
| Verdict: | Malicious activity |
| Analysis date: | April 02, 2023, 22:35:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 156E0EDD2F6E7903F04CA7794BFD09CA |
| SHA1: | CE2B3ED4EA22AF42505E3E2B007043A8C7475515 |
| SHA256: | F0397E428AB48FA901C5E9A287413B1E1C71D4691365168ADB94F054421E6A1D |
| SSDEEP: | 49152:qTVswVptk9scC1QGJeAKQn7jqN8uFeTCkPpeHHJsX:yVsskKc8kAbn08lTd42X |
MALICIOUS
Loads dropped or rewritten executable
- msiexec.exe (PID: 3496)
Application was dropped or rewritten from another process
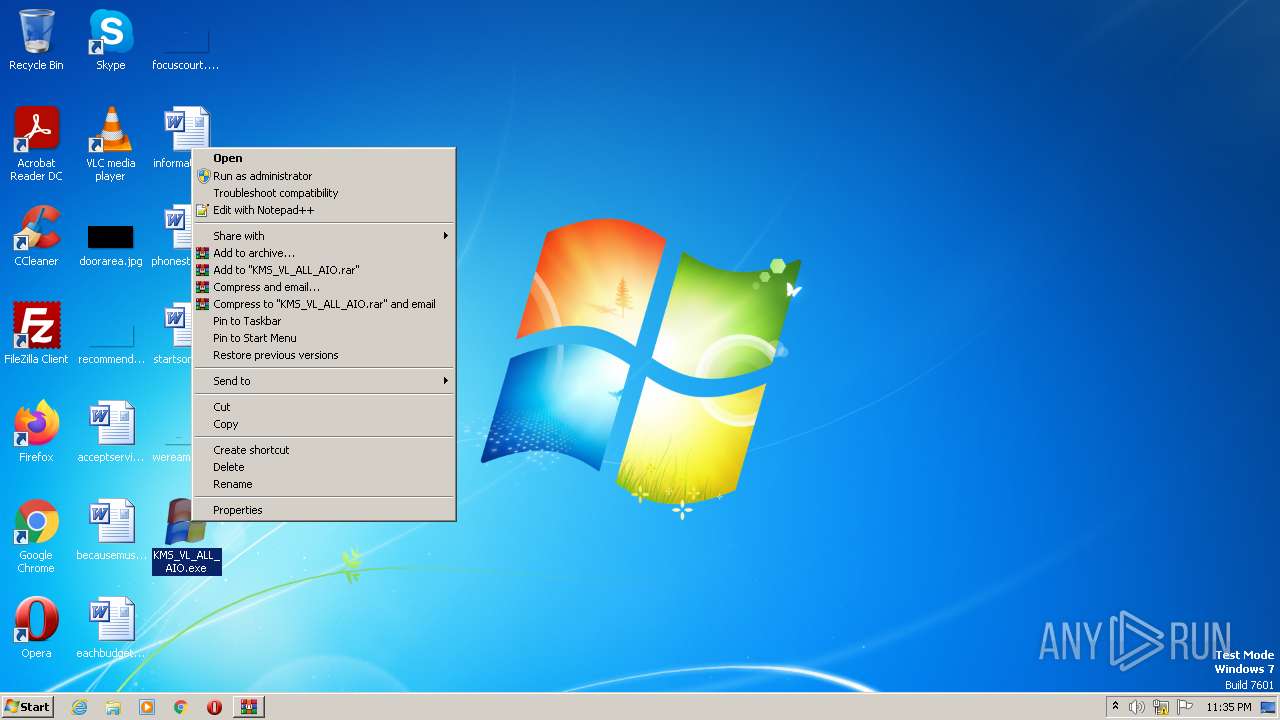
- KMS_VL_ALL_AIO.exe (PID: 3176)
- Active.exe (PID: 2348)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2880)
BASE64 encoded PowerShell command has been detected
- Active.exe (PID: 2348)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3492)
- KMS_VL_ALL_AIO.exe (PID: 3176)
Starts POWERSHELL.EXE for commands execution
- Active.exe (PID: 2348)
Application launched itself
- msiexec.exe (PID: 3492)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1900)
Manual execution by a user
- KMS_VL_ALL_AIO.exe (PID: 3176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
9
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1900 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\KMS_VL_ALL_AIO.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2348 | "C:\Users\admin\AppData\Roaming\WindowsActiveServices\Active.exe" | C:\Users\admin\AppData\Roaming\WindowsActiveServices\Active.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Background Task Host Exit code: 0 Version: 10.0.17763.1 | |||||||||||||||
| 2352 | "C:\Windows\system32\msiexec.exe" /i "C:\Users\admin\AppData\Roaming\KMS_VL_ALL_AIO\KMS_VL_ALL_AIO 1.0.0\install\KMS_VL_ALL_AIO.msi" AI_SETUPEXEPATH=C:\Users\admin\Desktop\KMS_VL_ALL_AIO.exe SETUPEXEDIR=C:\Users\admin\Desktop\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1680472490 " | C:\Windows\System32\msiexec.exe | — | KMS_VL_ALL_AIO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -enc UwB0AGEAcgB0AC0AUwBsAGUAZQBwACAALQBzACAAMQAwAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Active.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) | |||||||||||||||
| 2880 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3176 | "C:\Users\admin\Desktop\KMS_VL_ALL_AIO.exe" | C:\Users\admin\Desktop\KMS_VL_ALL_AIO.exe | explorer.exe | ||||||||||||
User: admin Company: KMS_VL_ALL_AIO Integrity Level: HIGH Description: KMS_VL_ALL_AIO Installer Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 3380 | C:\Windows\system32\MsiExec.exe -Embedding 5EA0D7B1DFDC63477D00245E42C731E9 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 3492 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3496 | C:\Windows\system32\MsiExec.exe -Embedding 9FC93251810FA78186FC1C200E29F1DB C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 433
Read events
6 395
Write events
38
Delete events
0
Modification events
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000011460B5E93FAD801F40E00002C040000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000011460B5E93FAD801F40E00002C040000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
34
Suspicious files
16
Text files
30
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Roaming\KMS_VL_ALL_AIO\KMS_VL_ALL_AIO 1.0.0\install\KMS_VL_ALL_AIO.msi | executable | |
MD5:CEC1E6A8D11A085632C32511EDF5C2F2 | SHA256:8536D4138DD6003691D90F63B95D34E93145D0AA291EA0DE296D2472BFDF6884 | |||
| 1900 | WinRAR.exe | C:\Users\admin\Desktop\KMS_VL_ALL_AIO.exe | executable | |
MD5:9065CB66E4232E63AAD8568259506DB6 | SHA256:2CE96DD0E86EDBAD2D62AF8CCD66247FCBAA928FFD47EFFF08DB131254CE7E74 | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3176\viewer.exe | executable | |
MD5:88A4962643AF83785B80EA15FE74E860 | SHA256:C8E5D349D9F6F3B5F20E5D5A0C5315C882D2AFCEDB21ABE66CFF00C1A57FD91E | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\MSIA8CE.tmp | executable | |
MD5:0981D5C068A9C33F4E8110F81FFBB92E | SHA256:B3F5E10FB1B7352A6DBBCBB10ED605A8FDA24F3F9C31F954835BD5A41EB6EA68 | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3176\repairic | image | |
MD5:D234CA0358B21BDCFC5E3F9B2E7C7A22 | SHA256:99D490C2BDEF5115F306A595964663540370141F65A25C5052352155F2603F68 | |||
| 3492 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3176\New | image | |
MD5:C23CBF002D82192481B61ED7EC0890F4 | SHA256:4F92E804A11453382EBFF7FB0958879BAE88FE3366306911DEC9D811CD306EED | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3176\tabback | image | |
MD5:4C3DDA35E23D44E273D82F7F4C38470A | SHA256:E728F79439E07DF1AFBCF03E8788FA0B8B08CF459DB31FC8568BC511BF799537 | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3176\banner | image | |
MD5:CE1143E3563DE4E200BA7F4953B3807B | SHA256:A5EEFACA044B04460A1CED5FEC2229545EDF85F01E1D6673E6E14D06B3108C2D | |||
| 3176 | KMS_VL_ALL_AIO.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3176\insticon | image | |
MD5:66C842AF0B4FC1C918F531D2E1087B82 | SHA256:48278165490487EE414BE65E20501B19A65EDAF1B6F473EB7D8C55023175EC88 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report