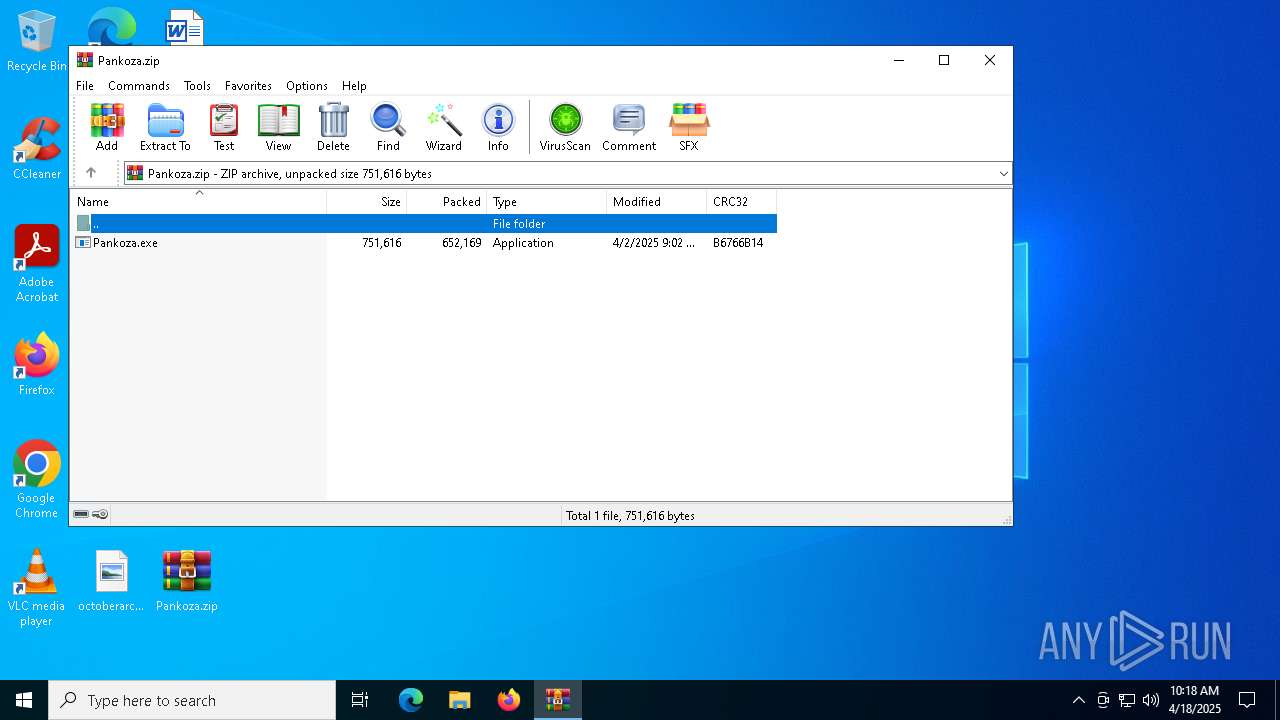
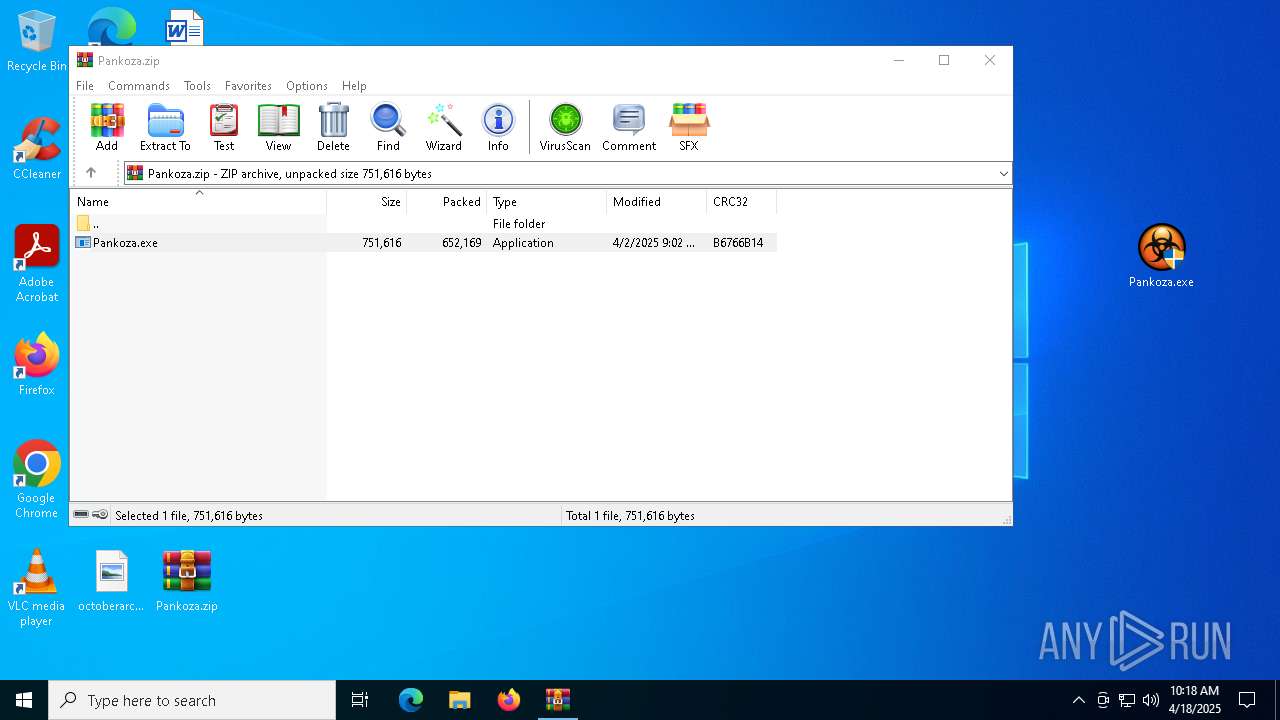
| File name: | Pankoza.zip |
| Full analysis: | https://app.any.run/tasks/e390b973-fdde-44ba-a0b2-d1b0940469a3 |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 10:18:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 00391DFF5CF35340E062271FBA74212D |
| SHA1: | 41024AC93CD2BB8D60E8EC77BA846BC02D08E705 |
| SHA256: | F035262F0B84364BB851ECCD24B0B3C0DB54CD4512096D59E03D1A7C2DADA3F9 |
| SSDEEP: | 24576:D8E11HSRbGhkxFaCQxP5lqHxQjLYc3A1C5/pmAVNIPcbhEQIDdHWfFX443WX0uWo:D8E11HSRbGhkxFaCQxP5lqHxQjLYc3Ax |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1088)
SUSPICIOUS
Executable content was dropped or overwritten
- Pankoza.exe (PID: 6676)
Reads security settings of Internet Explorer
- Pankoza.exe (PID: 6676)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5260)
Runs WScript without displaying logo
- wscript.exe (PID: 5260)
The process executes VB scripts
- Pankoza.exe (PID: 6676)
Executing commands from ".cmd" file
- wscript.exe (PID: 5260)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5260)
The executable file from the user directory is run by the CMD process
- MBRTrash.exe (PID: 6960)
- 1.exe (PID: 4724)
- 2.exe (PID: 2904)
- 3.exe (PID: 5280)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- MBRTrash.exe (PID: 6960)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6080)
There is functionality for taking screenshot (YARA)
- 3.exe (PID: 5280)
- 1.exe (PID: 4724)
- 2.exe (PID: 2904)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1088)
The sample compiled with english language support
- WinRAR.exe (PID: 1088)
Checks supported languages
- Pankoza.exe (PID: 6676)
- MBRTrash.exe (PID: 6960)
- 3.exe (PID: 5280)
- 2.exe (PID: 2904)
- identity_helper.exe (PID: 5232)
- 1.exe (PID: 4724)
Reads the computer name
- Pankoza.exe (PID: 6676)
- identity_helper.exe (PID: 5232)
Manual execution by a user
- Pankoza.exe (PID: 6676)
- Pankoza.exe (PID: 6652)
- msedge.exe (PID: 5756)
Create files in a temporary directory
- Pankoza.exe (PID: 6676)
Process checks computer location settings
- Pankoza.exe (PID: 6676)
Reads security settings of Internet Explorer
- wscript.exe (PID: 5260)
Application launched itself
- msedge.exe (PID: 5756)
- msedge.exe (PID: 7868)
- msedge.exe (PID: 812)
Reads Environment values
- identity_helper.exe (PID: 5232)
Reads the software policy settings
- slui.exe (PID: 6728)
- slui.exe (PID: 7460)
Checks proxy server information
- slui.exe (PID: 7460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:02 21:02:30 |
| ZipCRC: | 0xb6766b14 |
| ZipCompressedSize: | 652169 |
| ZipUncompressedSize: | 751616 |
| ZipFileName: | Pankoza.exe |
Total processes
191
Monitored processes
58
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
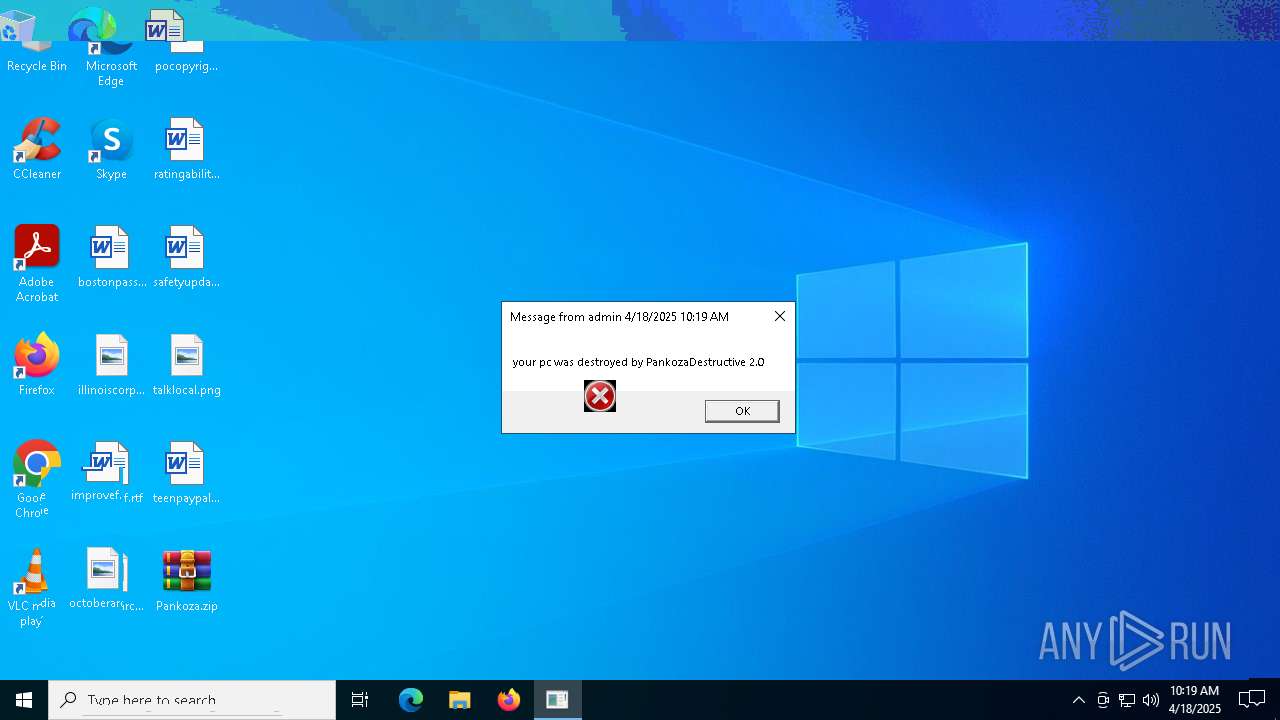
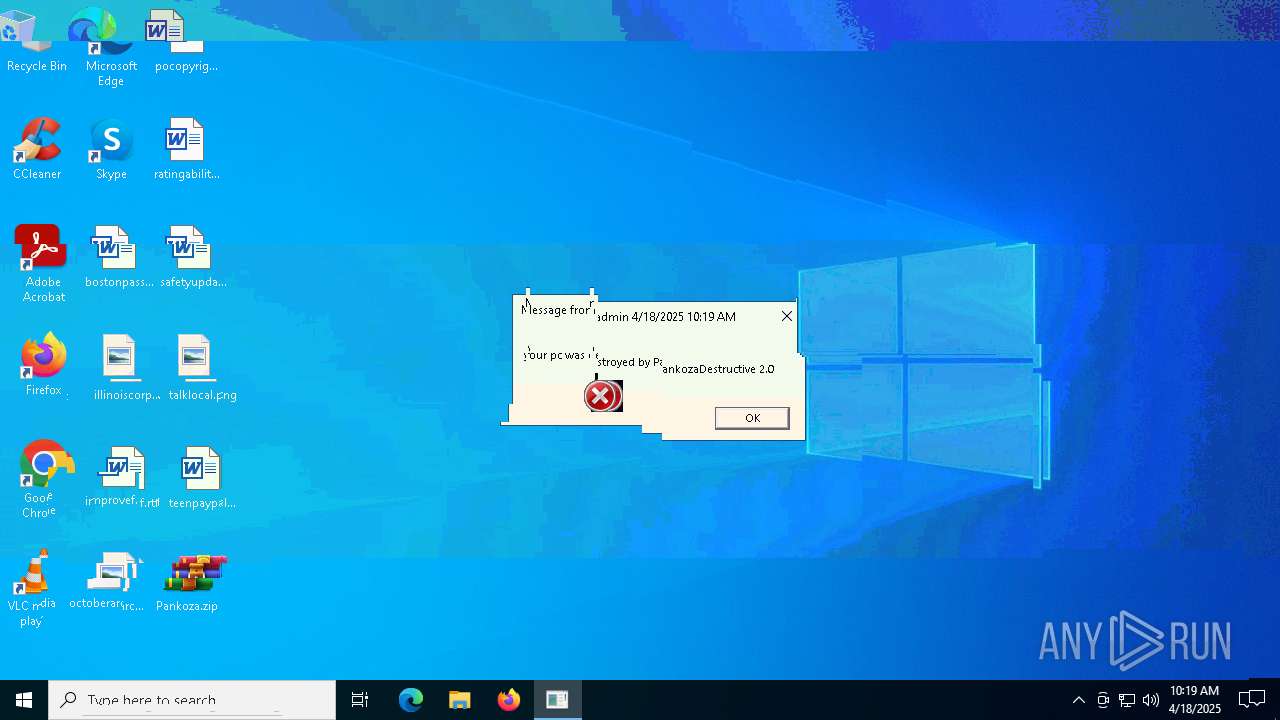
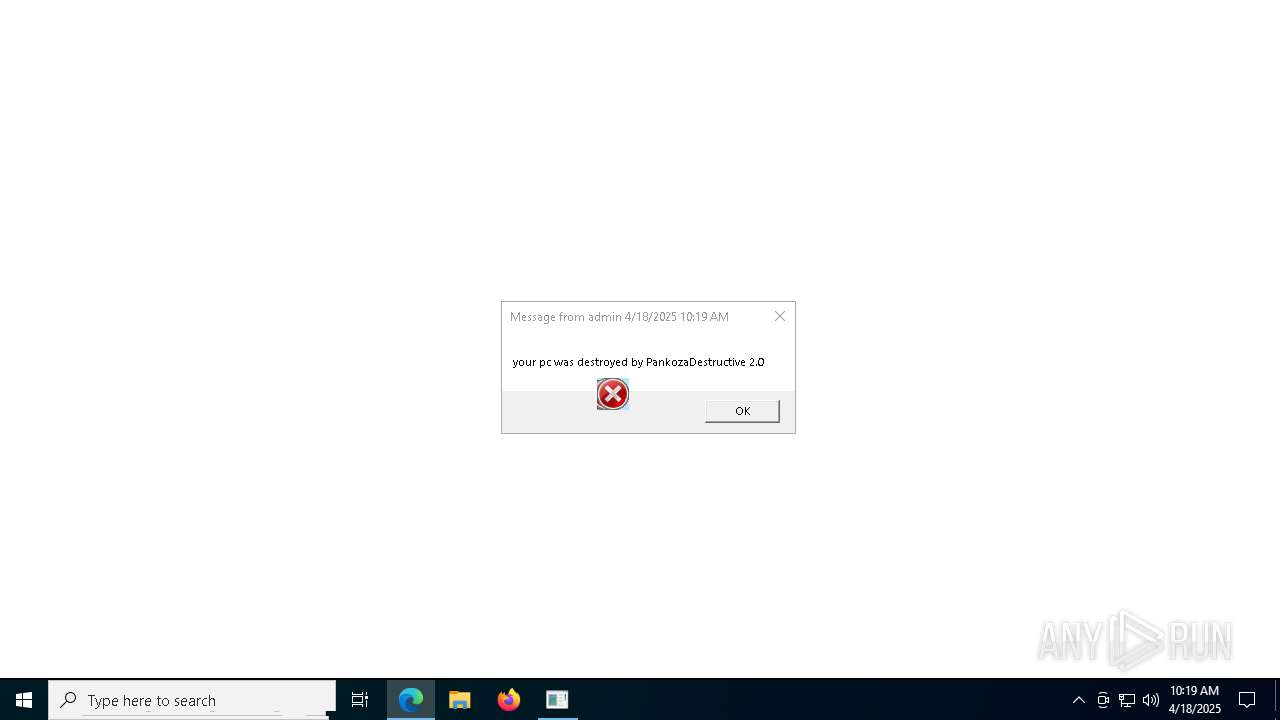
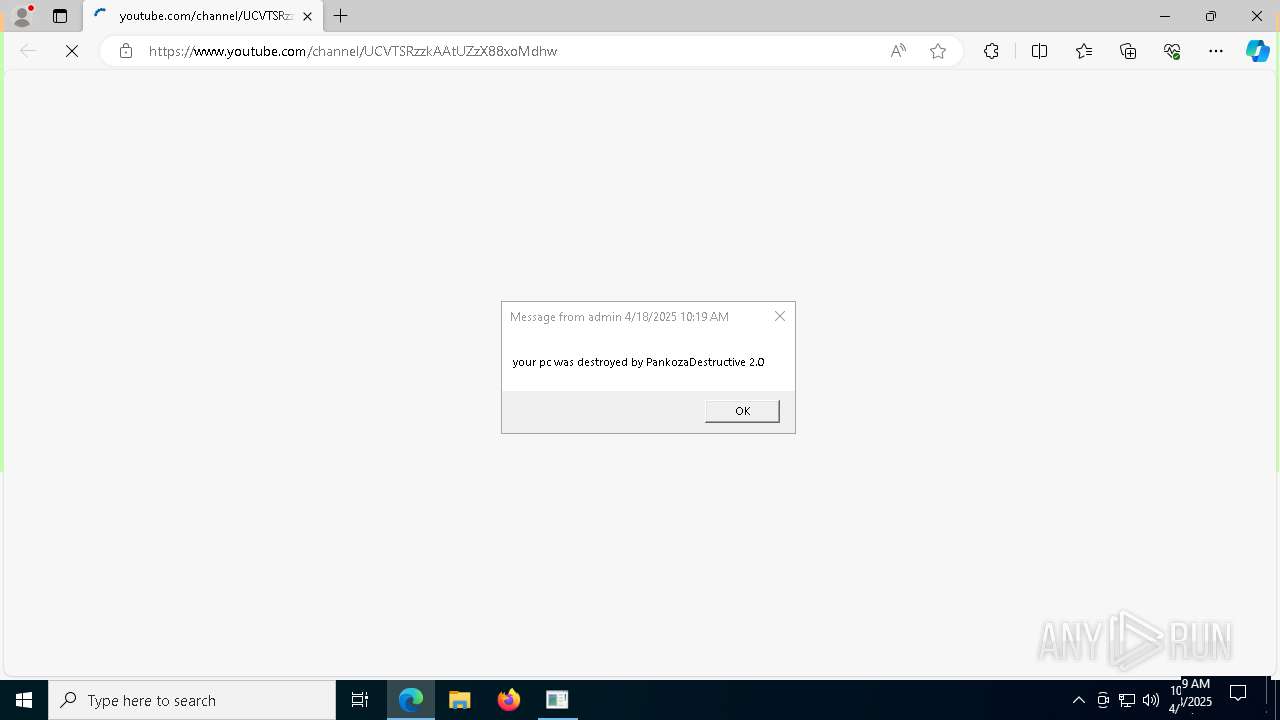
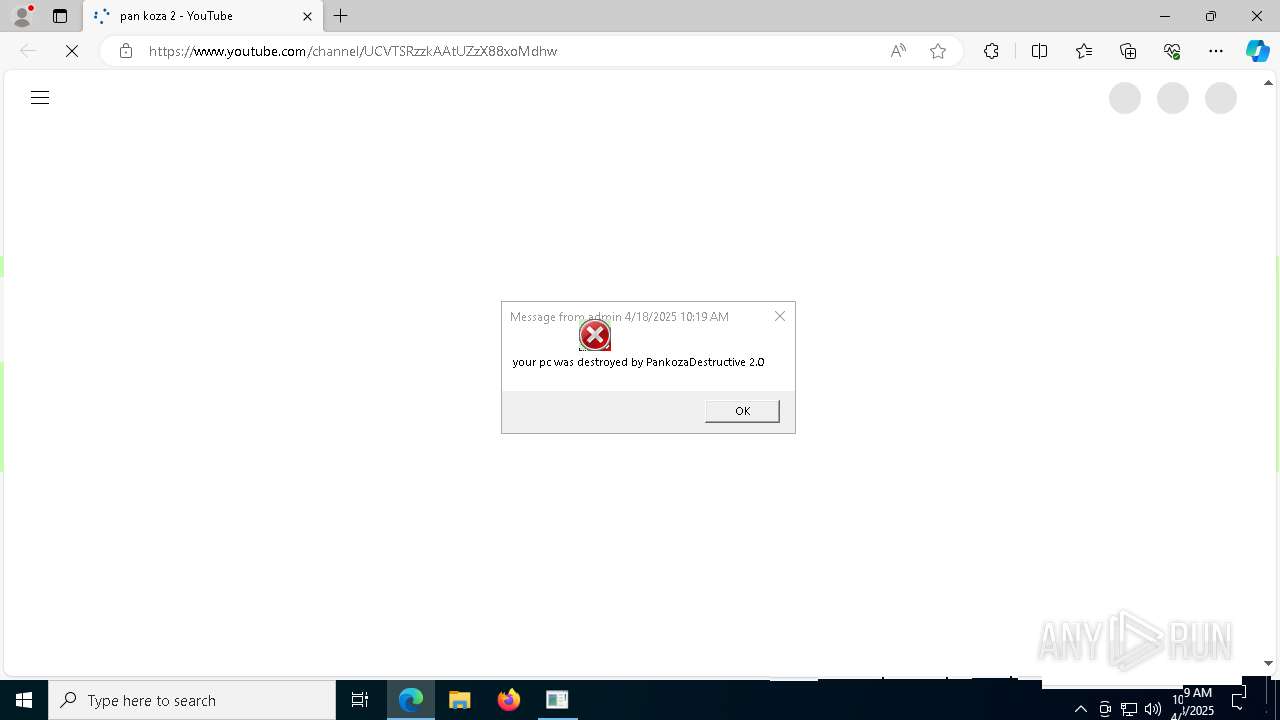
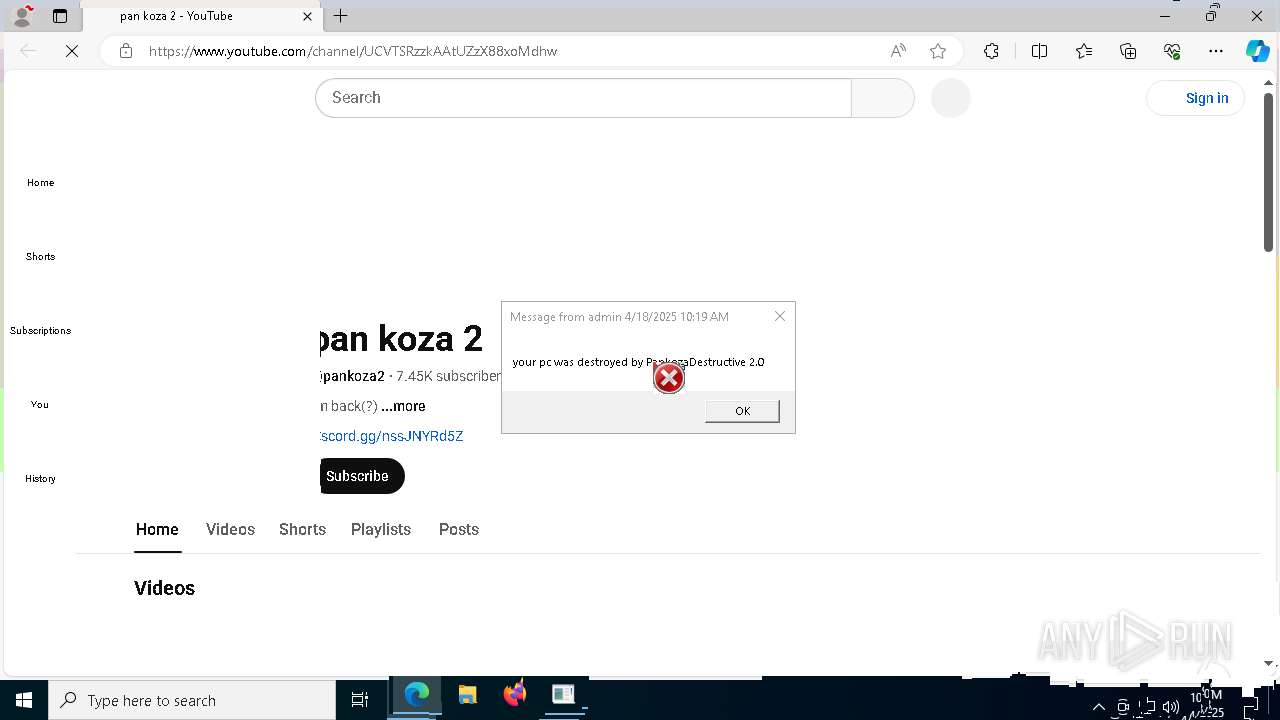
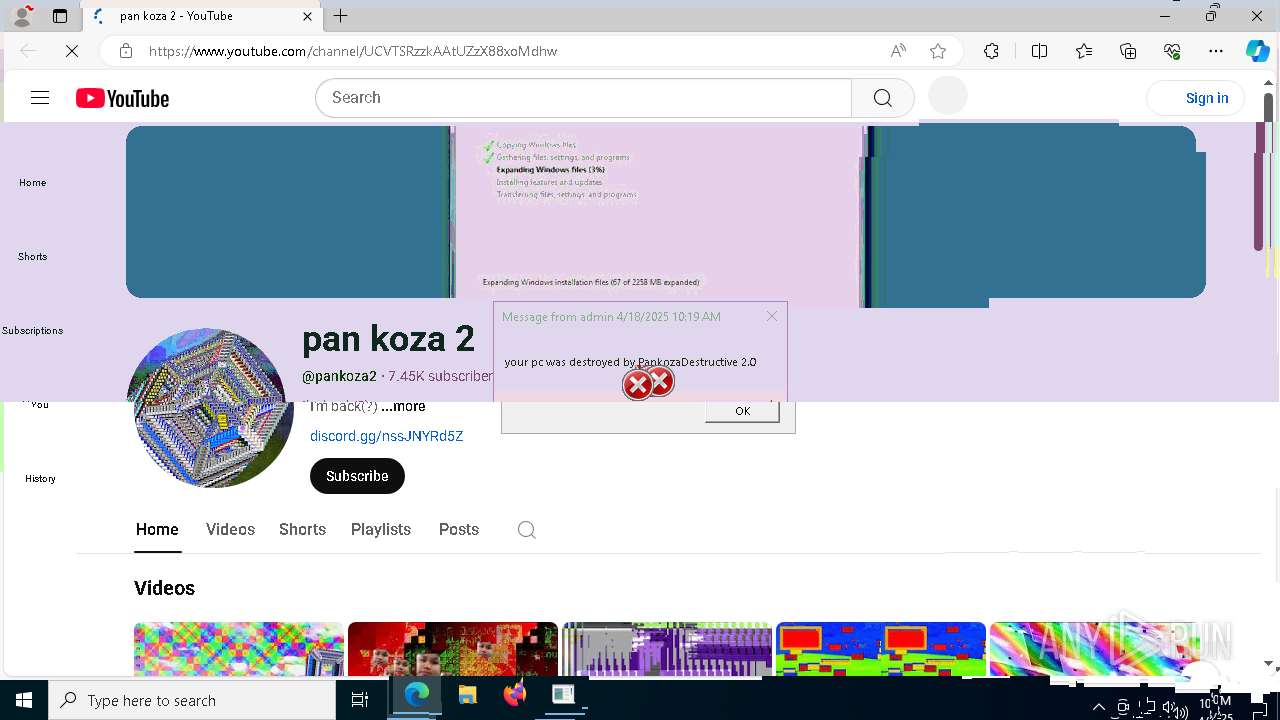
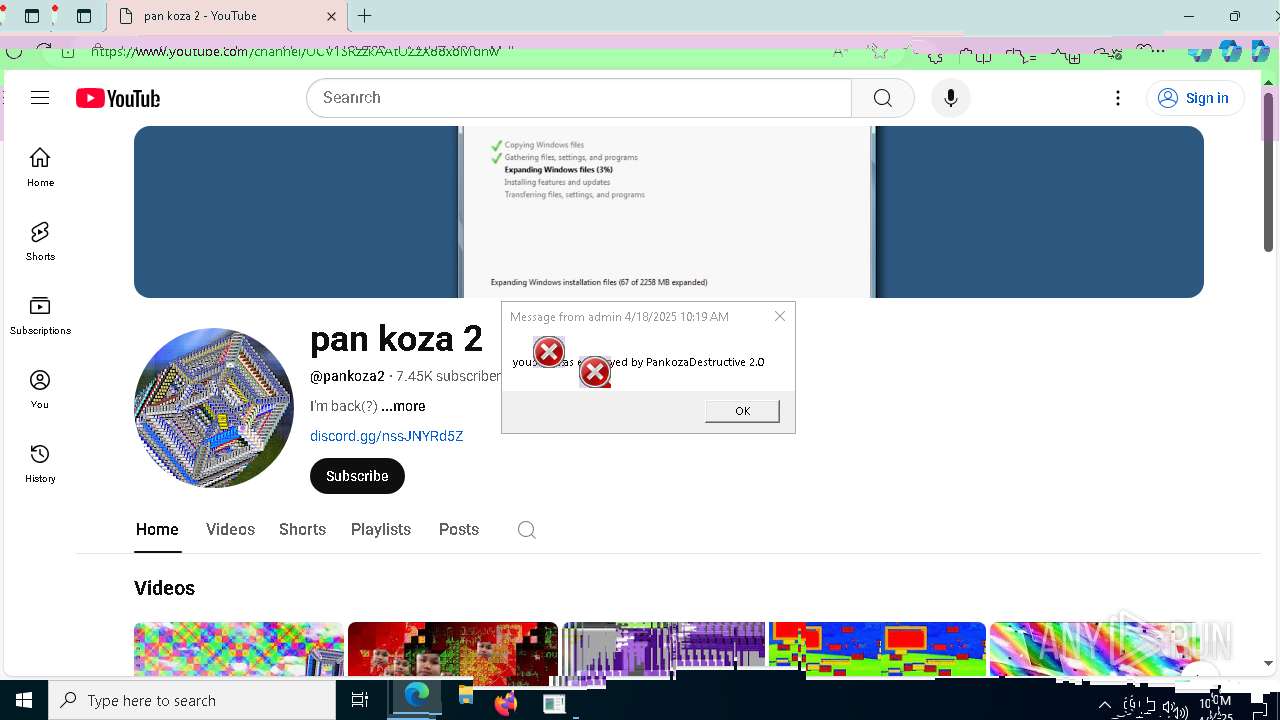
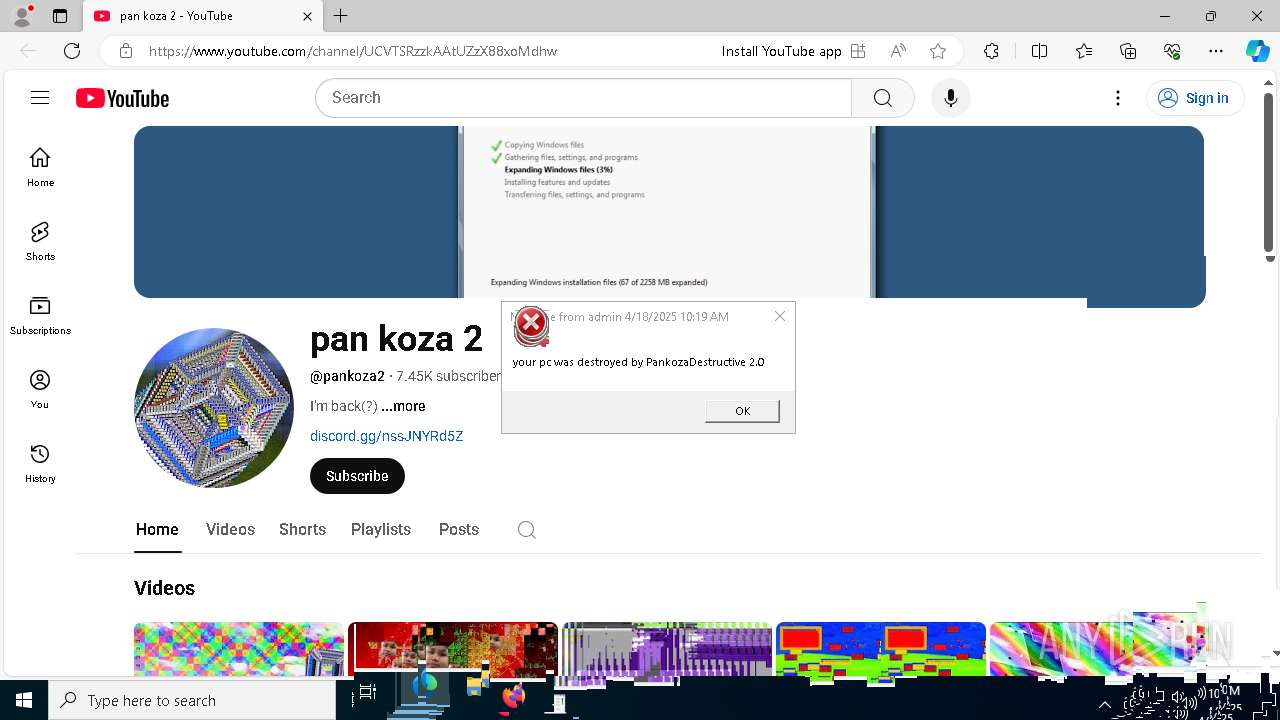
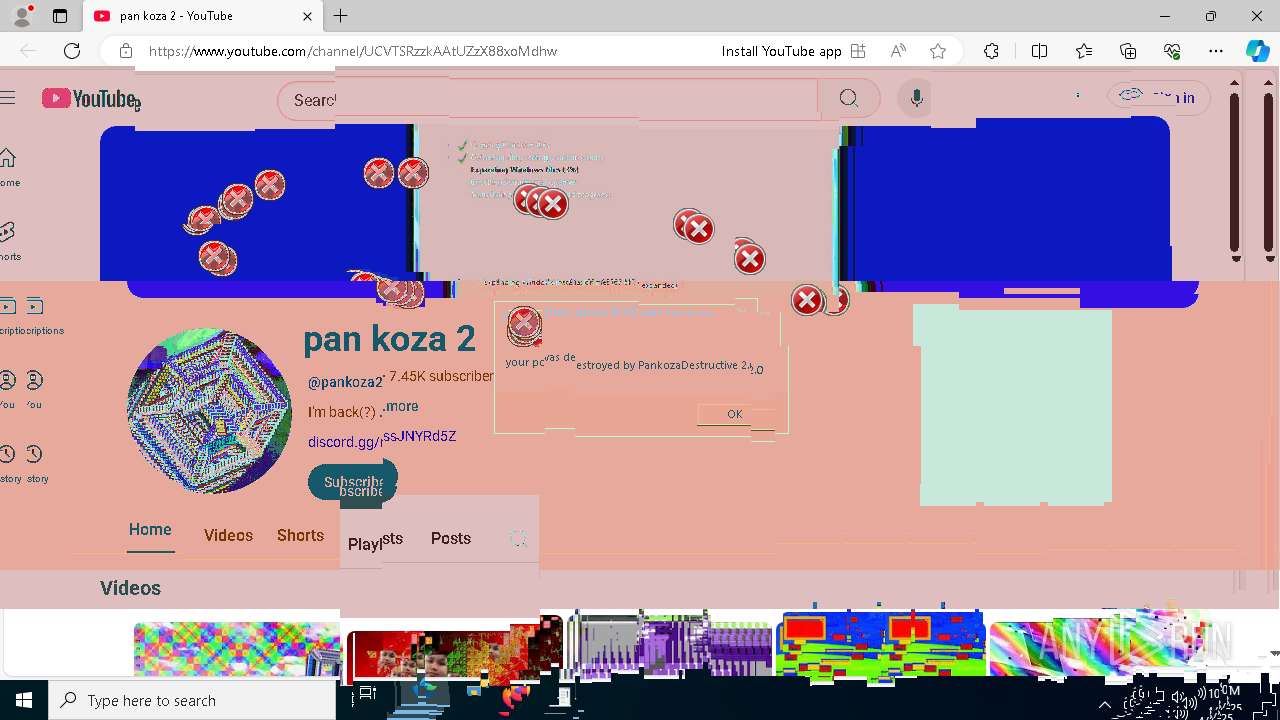
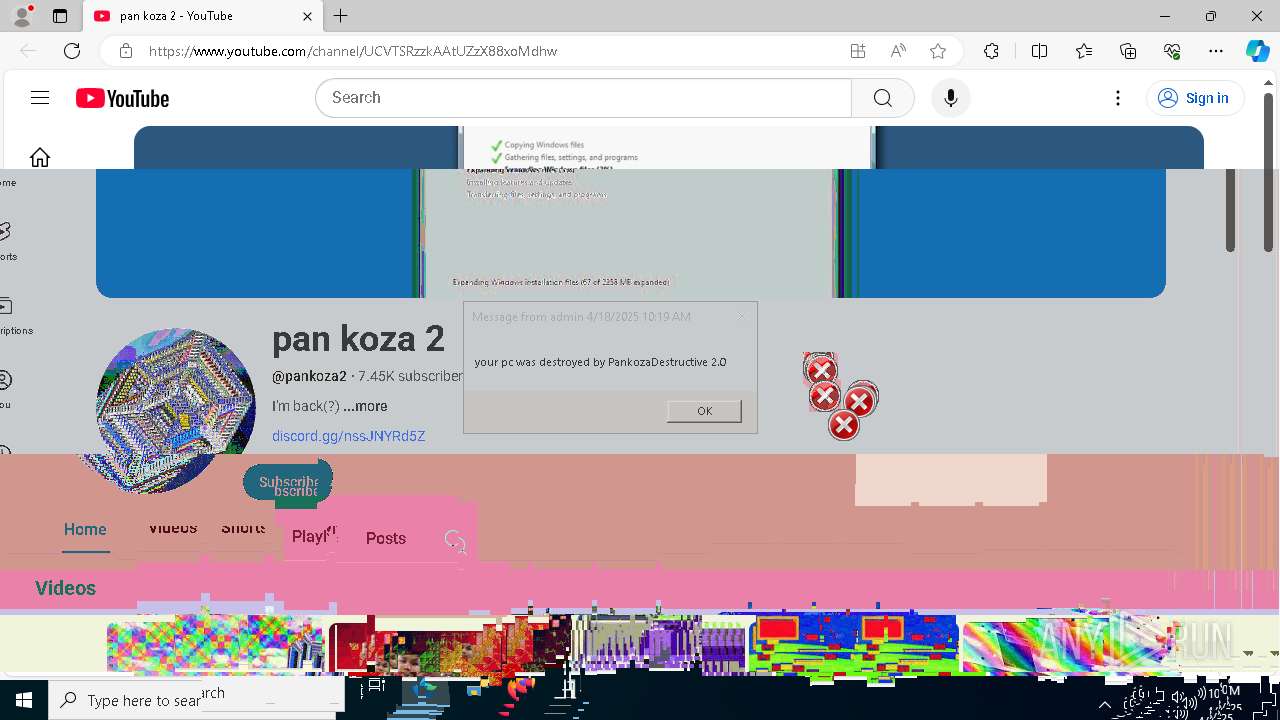
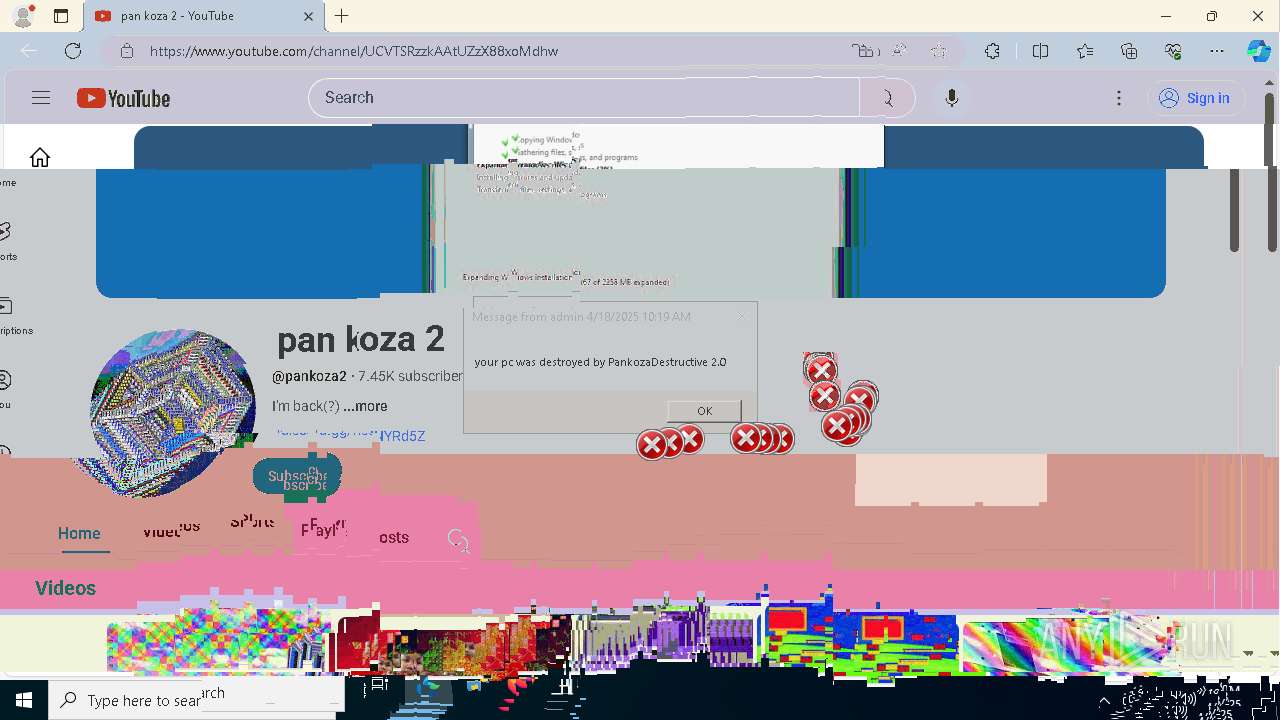
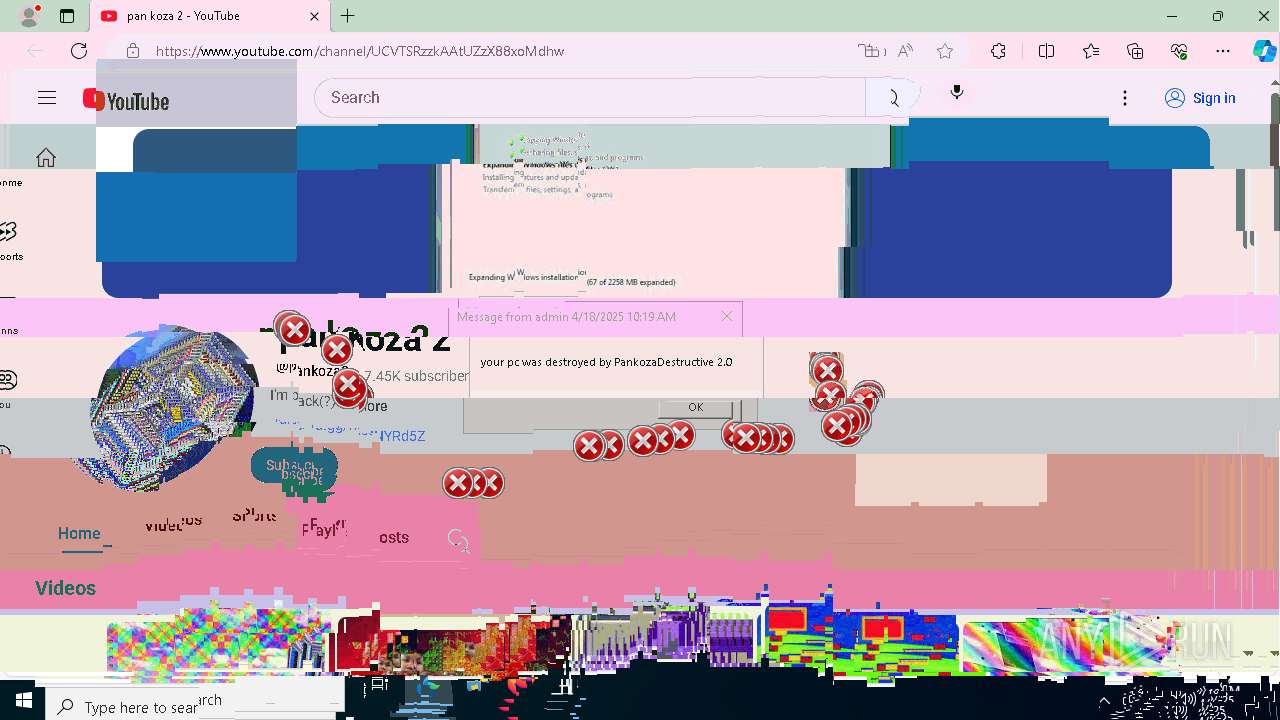
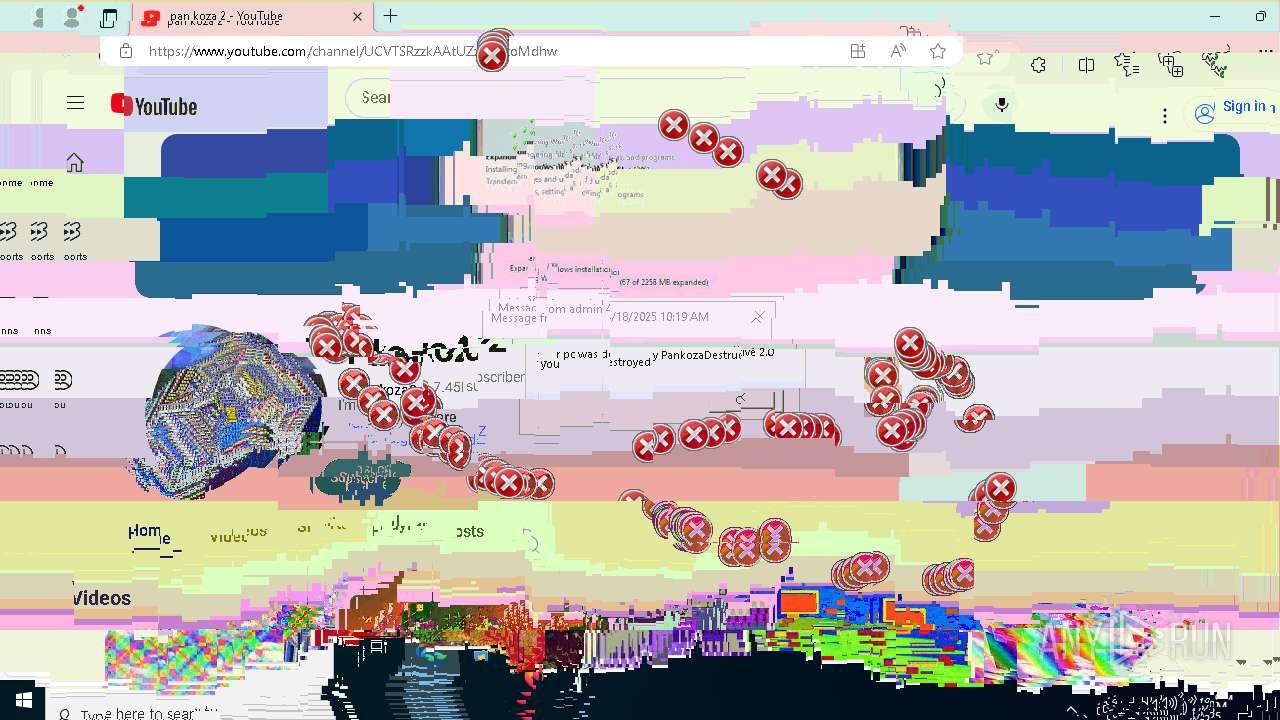
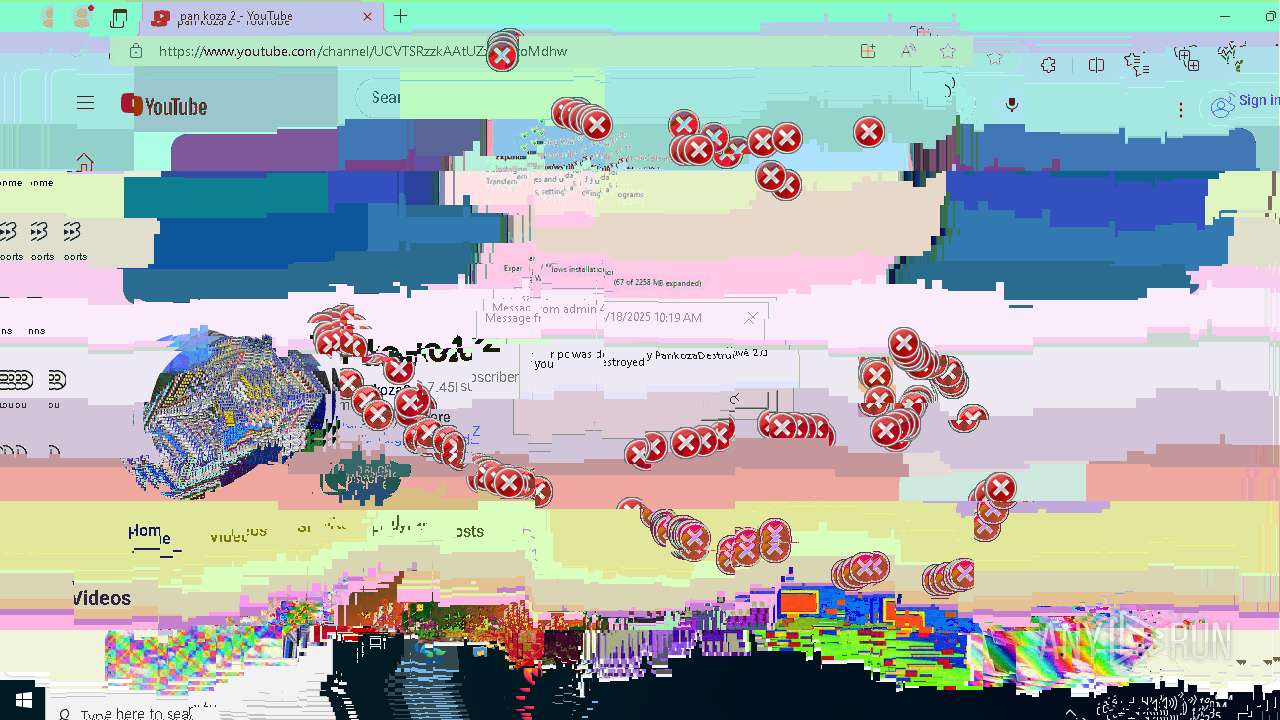
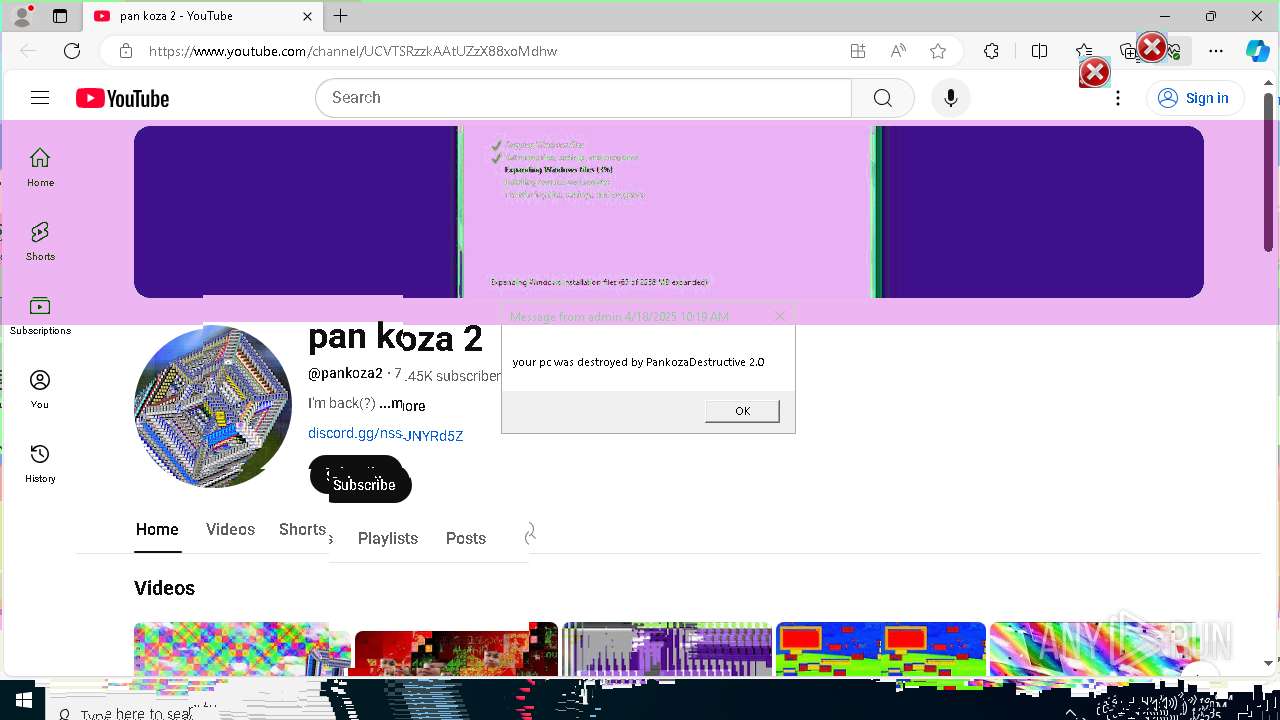
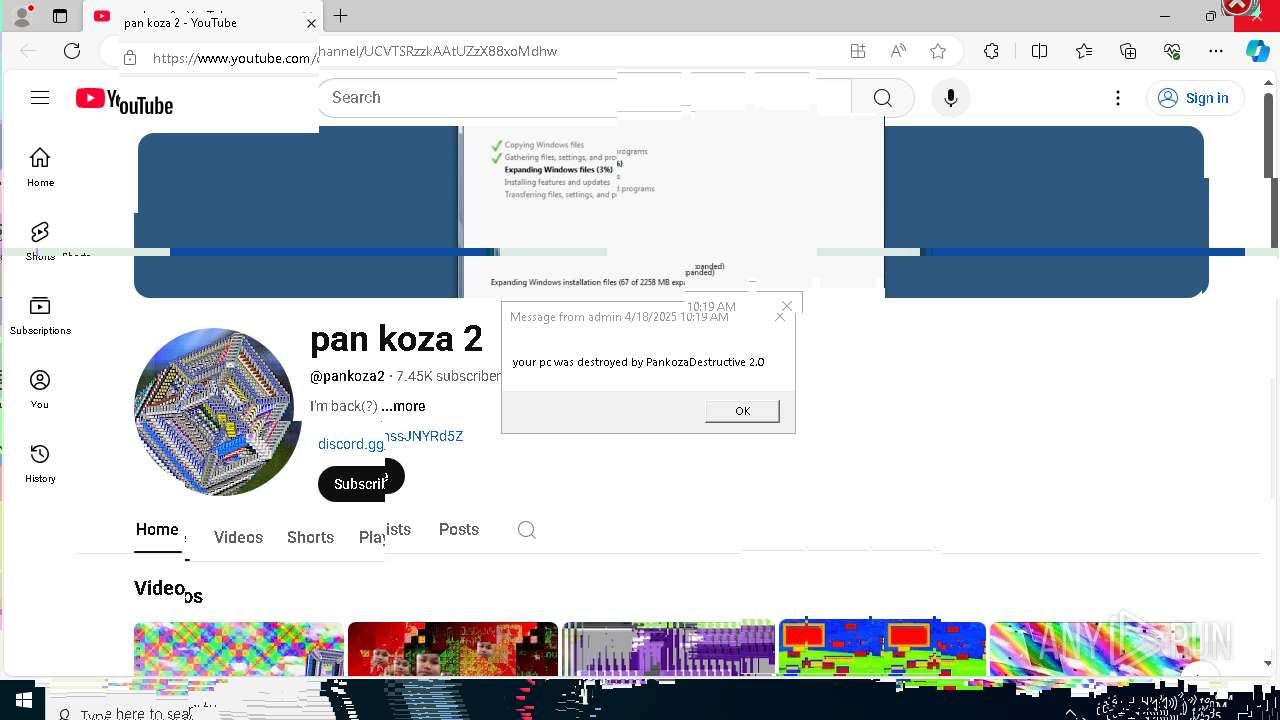
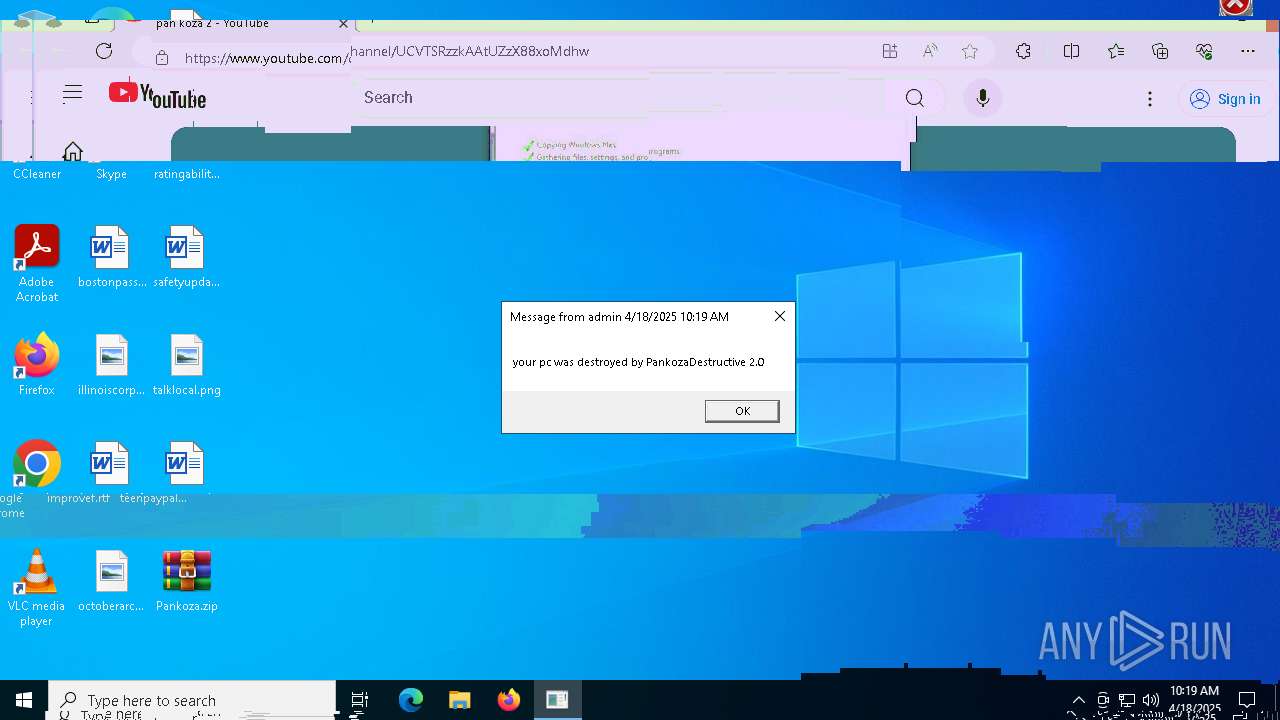
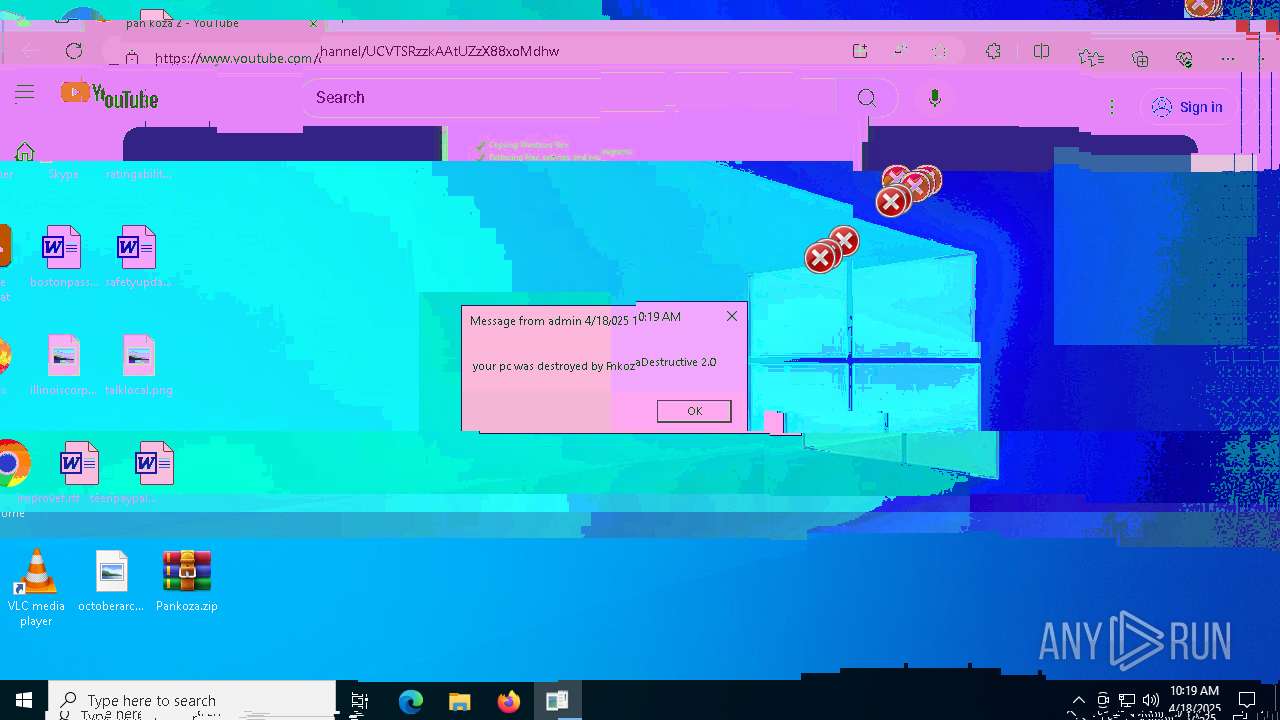
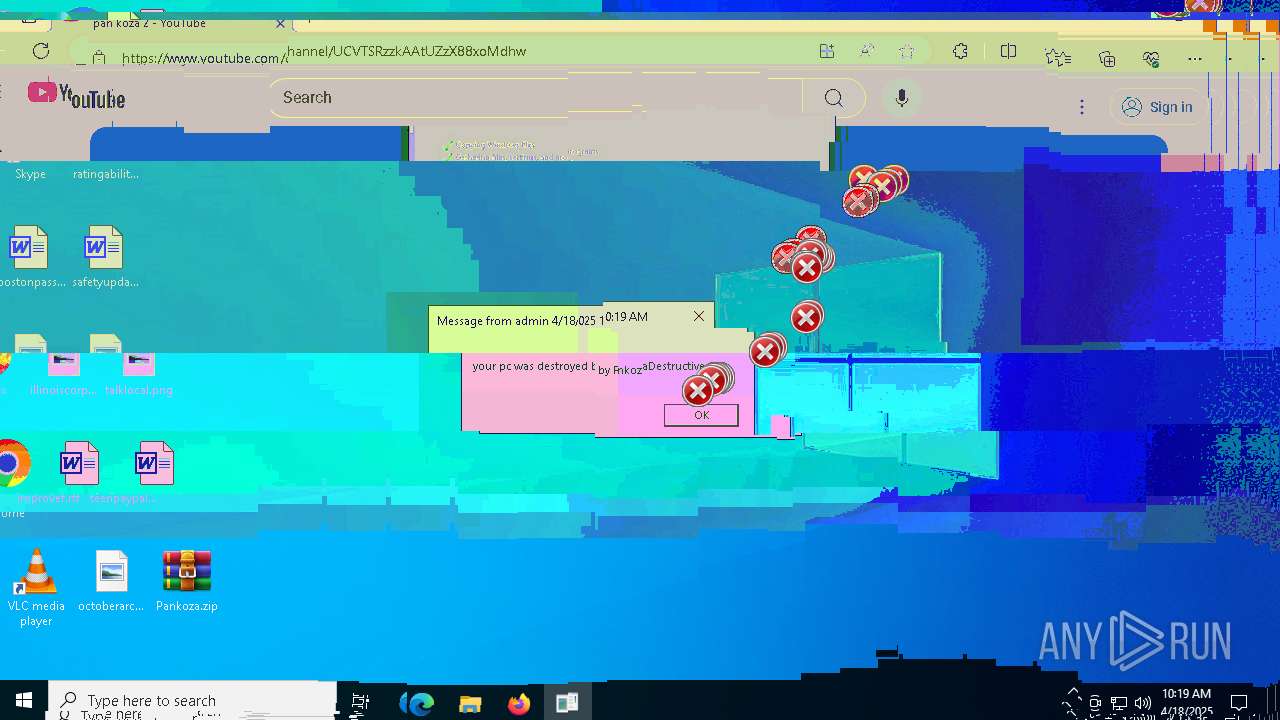
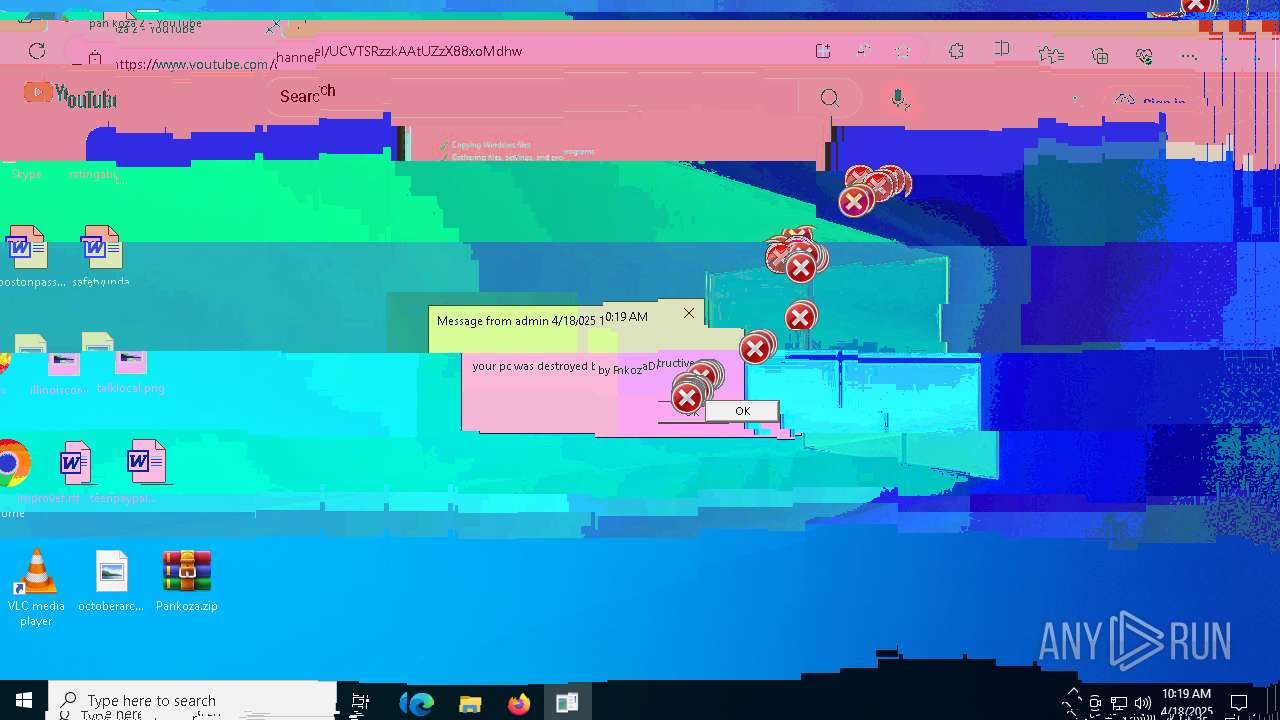
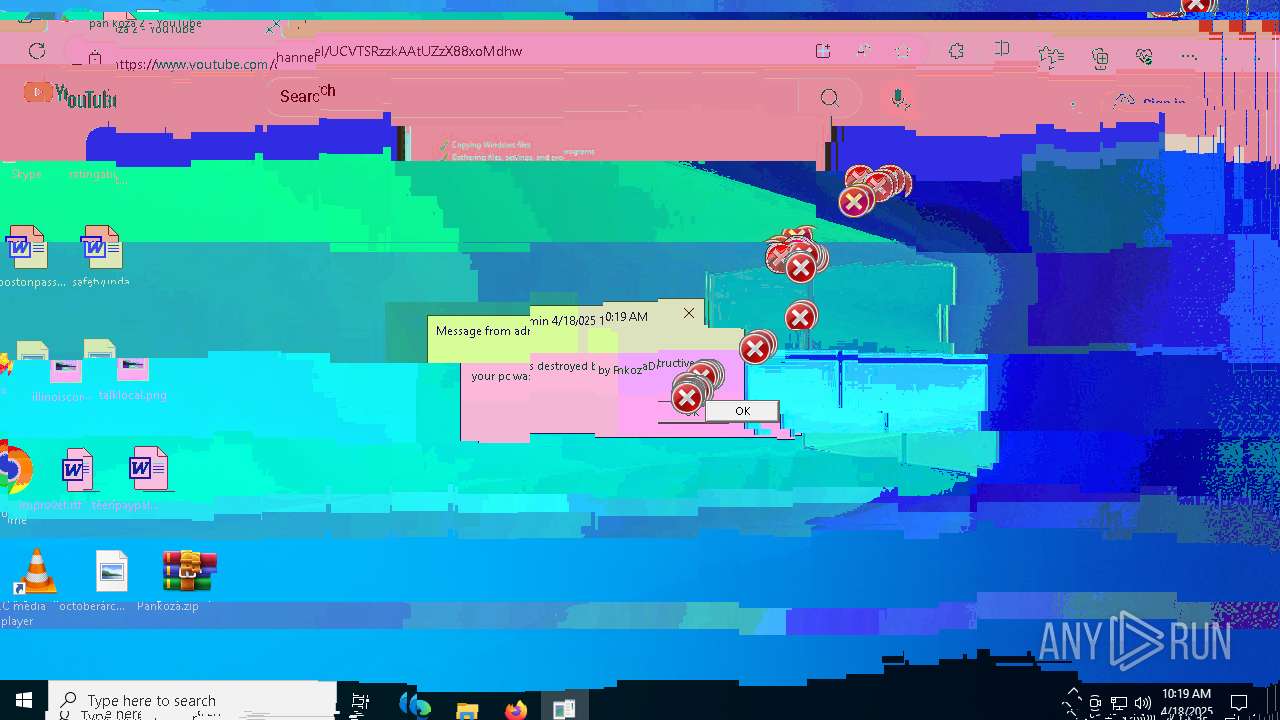
| 720 | msg * your pc was destroyed by PankozaDestructive 2.0 | C:\Windows\System32\msg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Message Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.youtube.com/channel/UCVTSRzzkAAtUZzX88xoMdhw | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Pankoza.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2468 --field-trial-handle=2472,i,16492432668006514681,890391865365220427,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3680 --field-trial-handle=2564,i,13141155854162238196,4939153869520142261,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2904 | 2.exe | C:\Users\admin\AppData\Local\Temp\504F.tmp\2.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4320 --field-trial-handle=2564,i,13141155854162238196,4939153869520142261,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4304 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3972 --field-trial-handle=2340,i,17830201249021199252,6995253923725345221,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
55 557
Read events
10 282
Write events
57
Delete events
45 218
Modification events
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Pankoza.zip | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (1088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
10
Suspicious files
334
Text files
73
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6960 | MBRTrash.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 1088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1088.32476\Pankoza.exe | executable | |
MD5:B172B2BCEBD8E4797CEAF0503C5840AE | SHA256:86B279800D7AA3025B59391F4F8BAB2039C41258D0DAF3D85365B0C3DDF05065 | |||
| 6676 | Pankoza.exe | C:\Users\admin\AppData\Local\Temp\504F.tmp\1.cpp | text | |
MD5:B4AAF10572F37E91A1DAE1C9786E56C1 | SHA256:C99577D427C7991E75A6FDDB22321E7E3BD6A2F447C3AD4CC209F9A1D4F291BA | |||
| 812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:1E9E15EF6E531C4557100F20C9C76F01 | SHA256:46CB063CC268B69B172660F166C4394D5B4EDD802388B3EC16766DEBDB9F86C3 | |||
| 6676 | Pankoza.exe | C:\Users\admin\AppData\Local\Temp\504F.tmp\2.cpp | text | |
MD5:FA001A30E87539715637CCCC809377D5 | SHA256:C70657B504E13B9922B8B12BB20F89A3596234A55D53697BD6B99A05940B7E39 | |||
| 6676 | Pankoza.exe | C:\Users\admin\AppData\Local\Temp\504F.tmp\2.exe | executable | |
MD5:84A2C1994A66F68EA0DE1CA54F2DAF8D | SHA256:A3F537D75FE7BEE34EF70C0997C4DD003F1B463D6CCB5FCDB996A78A41F851D5 | |||
| 5756 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF116f22.TMP | — | |
MD5:— | SHA256:— | |||
| 5756 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:C7E2197BAE099B13BBB3ADEB1433487D | SHA256:3460EEAF45D581DD43A6E4E17AF8102DDAFF5AEAA88B10099527CF85211629E9 | |||
| 812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:A5BD4DF1AD628397C182AC432EF032C2 | SHA256:E5A17D9866C3844E37CFE4F40E10109E9F9C889214BE31391308C2C3BA31BE8F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
91
DNS requests
108
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.17.251.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.210.252.238:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4408 | SIHClient.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4408 | SIHClient.exe | GET | 200 | 2.21.189.233:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.17.251.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 4.207.247.137:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.147.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |