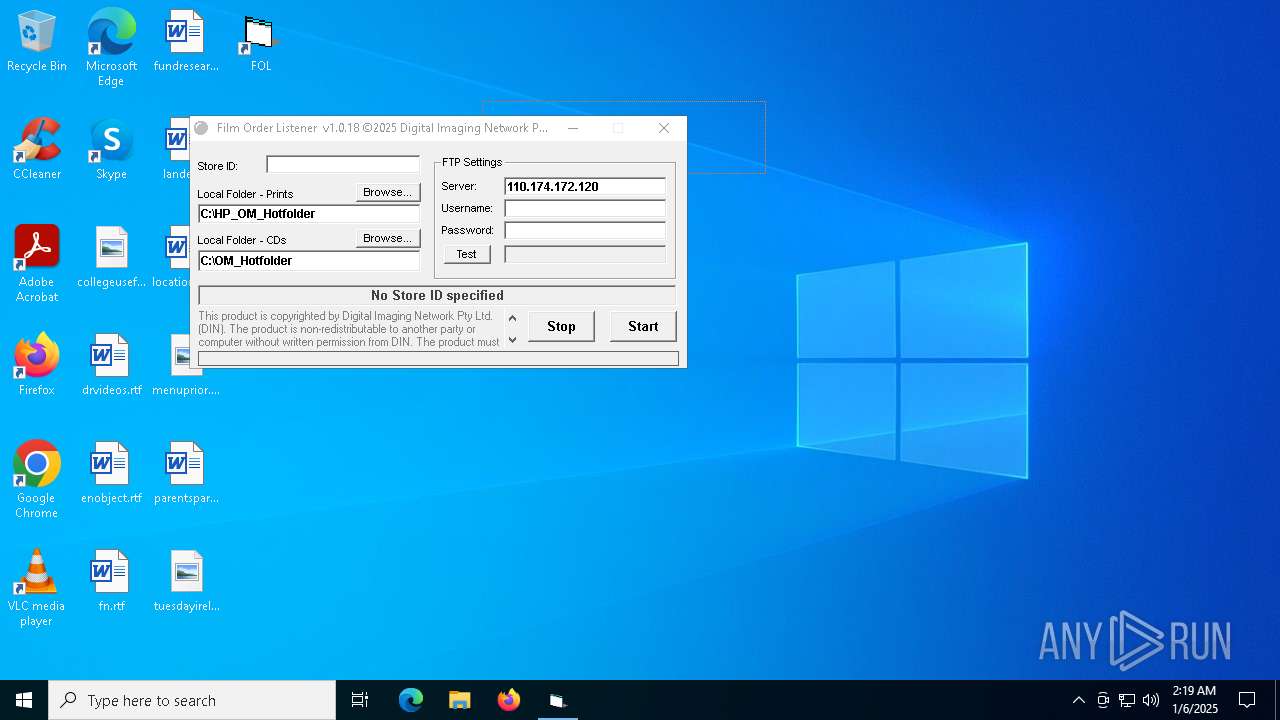
| File name: | FOL Installer Generic.exe |
| Full analysis: | https://app.any.run/tasks/ac972c0a-c9da-4ca1-9d56-5c3994d0505d |
| Verdict: | Malicious activity |
| Analysis date: | January 06, 2025, 02:19:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | C086D610C109F2AB434F8009C8ED72B7 |
| SHA1: | 26A928326529DB0ADDEEF91BF47988FCA63DD5BF |
| SHA256: | F02943431FE518574017A65B8800E8C1BF73A6B3DE012AC0C38319202B43C4CA |
| SSDEEP: | 98304:09EtxjHkj5AjZi/o7wSF+zZJqrWTdYZeu00MBzcj1EPuq8tzdlqlY8nuj+O5hw/o:DPVh0V89R |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- FOL Installer Generic.exe (PID: 6820)
Changes the autorun value in the registry
- FOL.exe (PID: 2092)
SUSPICIOUS
Executable content was dropped or overwritten
- FOL Installer Generic.exe (PID: 6820)
Reads security settings of Internet Explorer
- FOL Installer Generic.exe (PID: 6820)
Searches for installed software
- FOL Installer Generic.exe (PID: 6820)
Process drops legitimate windows executable
- FOL Installer Generic.exe (PID: 6820)
Creates a software uninstall entry
- FOL Installer Generic.exe (PID: 6820)
Starts application with an unusual extension
- FOL Installer Generic.exe (PID: 6820)
Creates/Modifies COM task schedule object
- GLJ5BD0.tmp (PID: 1344)
- GLJ5BD0.tmp (PID: 1864)
- GLJ5BD0.tmp (PID: 6340)
- GLJ5BD0.tmp (PID: 1616)
- GLJ5BD0.tmp (PID: 4516)
- GLJ5BD0.tmp (PID: 1512)
- GLJ5BD0.tmp (PID: 2928)
- GLJ5BD0.tmp (PID: 5788)
- GLJ5BD0.tmp (PID: 836)
- GLJ5BD0.tmp (PID: 4076)
- GLJ5BD0.tmp (PID: 5544)
- GLJ5BD0.tmp (PID: 5588)
- GLJ5BD0.tmp (PID: 4144)
- GLJ5BD0.tmp (PID: 5728)
- GLJ5BD0.tmp (PID: 4548)
- GLJ5BD0.tmp (PID: 4764)
- GLJ5BD0.tmp (PID: 5536)
- GLJ5BD0.tmp (PID: 5236)
- GLJ5BD0.tmp (PID: 5244)
- GLJ5BD0.tmp (PID: 5604)
- GLJ5BD0.tmp (PID: 520)
- GLJ5BD0.tmp (PID: 6716)
- GLJ5BD0.tmp (PID: 5920)
- GLJ5BD0.tmp (PID: 6816)
- GLJ5BD0.tmp (PID: 3488)
- GLJ5BD0.tmp (PID: 6336)
- GLJ5BD0.tmp (PID: 6736)
- GLJ5BD0.tmp (PID: 6536)
- GLJ5BD0.tmp (PID: 3172)
- GLJ5BD0.tmp (PID: 6312)
- GLJ5BD0.tmp (PID: 6368)
- GLJ5BD0.tmp (PID: 6884)
- GLJ5BD0.tmp (PID: 6976)
INFO
Checks supported languages
- FOL Installer Generic.exe (PID: 6820)
- GLJ5BD0.tmp (PID: 1804)
- GLJ5BD0.tmp (PID: 3564)
- GLJ5BD0.tmp (PID: 1344)
- GLJ5BD0.tmp (PID: 5300)
- GLJ5BD0.tmp (PID: 4516)
- GLJ5BD0.tmp (PID: 6340)
- GLJ5BD0.tmp (PID: 1616)
- GLJ5BD0.tmp (PID: 1512)
- GLJ5BD0.tmp (PID: 5588)
- GLJ5BD0.tmp (PID: 1864)
- GLJ5BD0.tmp (PID: 2928)
- GLJ5BD0.tmp (PID: 5788)
- GLJ5BD0.tmp (PID: 3128)
- GLJ5BD0.tmp (PID: 4076)
- GLJ5BD0.tmp (PID: 836)
- GLJ5BD0.tmp (PID: 5544)
- GLJ5BD0.tmp (PID: 4520)
- GLJ5BD0.tmp (PID: 5728)
- GLJ5BD0.tmp (PID: 4548)
- GLJ5BD0.tmp (PID: 4764)
- GLJ5BD0.tmp (PID: 5536)
- GLJ5BD0.tmp (PID: 5920)
- GLJ5BD0.tmp (PID: 4144)
- GLJ5BD0.tmp (PID: 5236)
- GLJ5BD0.tmp (PID: 5604)
- GLJ5BD0.tmp (PID: 6716)
- GLJ5BD0.tmp (PID: 5244)
- GLJ5BD0.tmp (PID: 520)
- GLJ5BD0.tmp (PID: 3488)
- GLJ5BD0.tmp (PID: 6816)
- GLJ5BD0.tmp (PID: 6336)
- GLJ5BD0.tmp (PID: 6736)
- GLJ5BD0.tmp (PID: 6536)
- GLJ5BD0.tmp (PID: 3172)
- GLJ5BD0.tmp (PID: 6312)
- GLJ5BD0.tmp (PID: 6368)
- GLJ5BD0.tmp (PID: 6884)
- GLJ5BD0.tmp (PID: 6308)
- FOL.exe (PID: 2092)
- GLJ5BD0.tmp (PID: 6976)
The sample compiled with english language support
- FOL Installer Generic.exe (PID: 6820)
Process checks computer location settings
- FOL Installer Generic.exe (PID: 6820)
The process uses the downloaded file
- FOL Installer Generic.exe (PID: 6820)
Reads the computer name
- FOL Installer Generic.exe (PID: 6820)
- GLJ5BD0.tmp (PID: 1344)
- GLJ5BD0.tmp (PID: 6340)
- GLJ5BD0.tmp (PID: 1864)
- GLJ5BD0.tmp (PID: 4516)
- GLJ5BD0.tmp (PID: 1616)
- GLJ5BD0.tmp (PID: 1512)
- GLJ5BD0.tmp (PID: 5588)
- GLJ5BD0.tmp (PID: 4076)
- GLJ5BD0.tmp (PID: 3128)
- GLJ5BD0.tmp (PID: 5788)
- GLJ5BD0.tmp (PID: 5544)
- GLJ5BD0.tmp (PID: 836)
- GLJ5BD0.tmp (PID: 4520)
- GLJ5BD0.tmp (PID: 2928)
- GLJ5BD0.tmp (PID: 4144)
- GLJ5BD0.tmp (PID: 5728)
- GLJ5BD0.tmp (PID: 4548)
- GLJ5BD0.tmp (PID: 4764)
- GLJ5BD0.tmp (PID: 5536)
- GLJ5BD0.tmp (PID: 5236)
- GLJ5BD0.tmp (PID: 5604)
- GLJ5BD0.tmp (PID: 5244)
- GLJ5BD0.tmp (PID: 520)
- GLJ5BD0.tmp (PID: 3488)
- GLJ5BD0.tmp (PID: 5920)
- GLJ5BD0.tmp (PID: 6716)
- GLJ5BD0.tmp (PID: 6736)
- GLJ5BD0.tmp (PID: 6816)
- GLJ5BD0.tmp (PID: 6336)
- GLJ5BD0.tmp (PID: 3172)
- GLJ5BD0.tmp (PID: 6312)
- GLJ5BD0.tmp (PID: 6368)
- GLJ5BD0.tmp (PID: 6976)
- GLJ5BD0.tmp (PID: 6884)
- FOL.exe (PID: 2092)
Creates files in the program directory
- FOL Installer Generic.exe (PID: 6820)
Create files in a temporary directory
- FOL Installer Generic.exe (PID: 6820)
- FOL.exe (PID: 2092)
Creates files or folders in the user directory
- FOL Installer Generic.exe (PID: 6820)
- FOL.exe (PID: 2092)
Reads mouse settings
- GLJ5BD0.tmp (PID: 1864)
- GLJ5BD0.tmp (PID: 4144)
- GLJ5BD0.tmp (PID: 5728)
- FOL.exe (PID: 2092)
Manual execution by a user
- FOL.exe (PID: 2092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:08:17 15:25:48+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, Removable run from swap |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8704 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21af |
| OSVersion: | 4 |
| ImageVersion: | 4 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Microsoft |
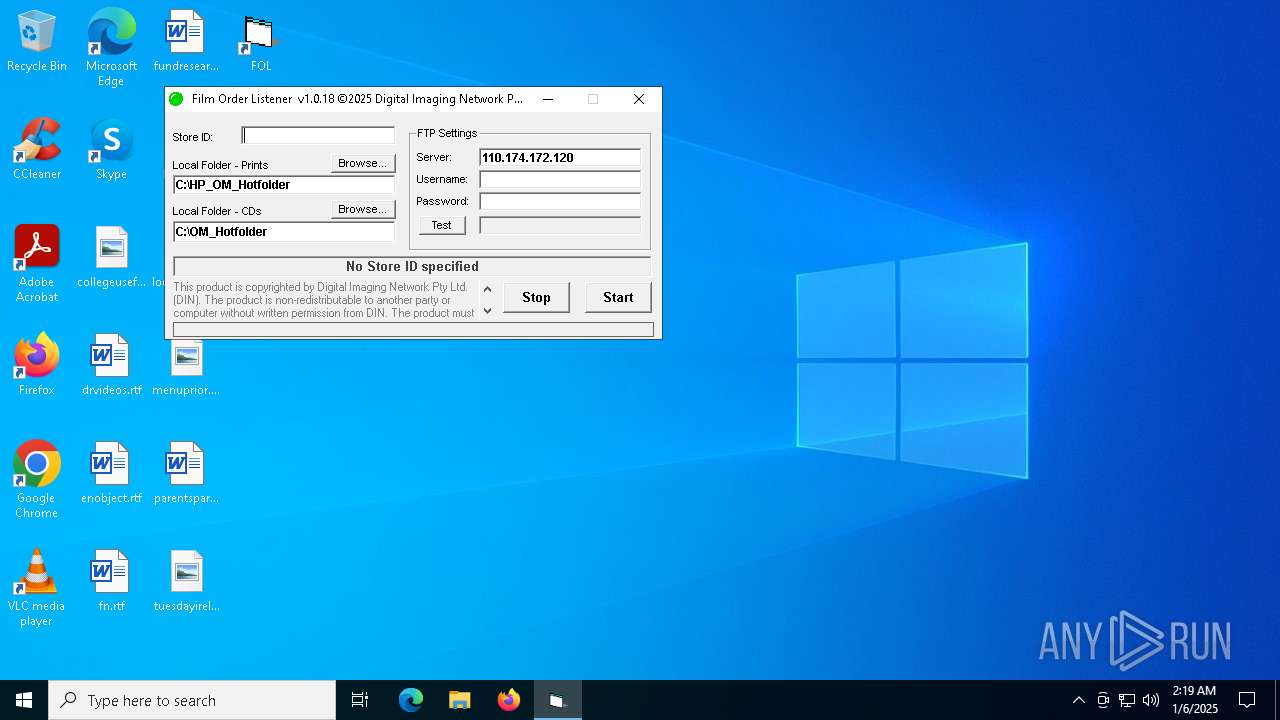
| FileDescription: | FilmOrderListener Installer |
| FileVersion: | - |
| LegalCopyright: | Microsoft |
Total processes
172
Monitored processes
43
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\MSINET.OCX | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 836 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\MSBIND.DLL | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\msvbvm60.dll | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\comctl32.ocx | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1616 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\comct332.ocx | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1804 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\oleaut32.dll | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1864 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\MSCOMCTL.OCX | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2092 | "C:\Program Files (x86)\FilmOrderListener\FOL.exe" | C:\Program Files (x86)\FilmOrderListener\FOL.exe | explorer.exe | ||||||||||||
User: admin Company: Blackburn Software Consultants Pty Ltd Integrity Level: MEDIUM Version: 1.00.0018 Modules
| |||||||||||||||
| 2928 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\DBADAPT.DLL | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp" C:\Windows\System32\DBGRID32.OCX | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | — | FOL Installer Generic.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 140
Read events
2 933
Write events
811
Delete events
396
Modification events
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\oleaut32.dll |
Value: 2 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\asycfilt.dll |
Value: 2 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\stdole2.tlb |
Value: 2 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\COMDLG32.OCX |
Value: 1 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\olepro32.dll |
Value: 2 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\msvbvm60.dll |
Value: 2 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\comcat.dll |
Value: 2 | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\FilmOrderListener Installer |
| Operation: | write | Name: | DisplayName |
Value: FilmOrderListener Installer | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\FilmOrderListener Installer |
| Operation: | write | Name: | UninstallString |
Value: C:\PROGRA~2\FILMOR~1\UNWISE.EXE C:\PROGRA~2\FILMOR~1\INSTALL.LOG | |||
| (PID) Process: | (6820) FOL Installer Generic.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\MSCOMCTL.OCX |
Value: 1 | |||
Executable files
159
Suspicious files
1
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6820 | FOL Installer Generic.exe | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | executable | |
MD5:B9B41E50D612E00BF3A49A6405B89D74 | SHA256:50E7A30E1825FAB93B94B698C2C6D2CC1787B094C6CEE53EEED5C497F77443C9 | |||
| 6820 | FOL Installer Generic.exe | C:\Users\admin\AppData\Local\Temp\GLJ5BD0.tmp | executable | |
MD5:6F608D264503796BEBD7CD66B687BE92 | SHA256:49833D2820AFB1D7409DFBD916480F2CDF5787D2E2D94166725BEB9064922D5D | |||
| 6820 | FOL Installer Generic.exe | C:\Users\admin\AppData\Local\Temp\GLC5BB0.tmp | executable | |
MD5:0D0E4CE1220016D57F9FEEC2F0DFA300 | SHA256:38F6640F2322878C7F2EEFCD5E0D517BFE00C9466664AE79AD7866985EB824AC | |||
| 6820 | FOL Installer Generic.exe | C:\Windows\SysWOW64\~GLH0005.TMP | executable | |
MD5:8D4E57DC2A426CA2FB79BC1900F7B544 | SHA256:E043C59C66BA2DC549BF5AC104C70279EC05931D531DE2971458EAB91871F7B6 | |||
| 6820 | FOL Installer Generic.exe | C:\Windows\SysWOW64\~GLH0008.TMP | executable | |
MD5:F70459191C9B65156FFD7930BA6DA13B | SHA256:7329EEB23D21FE0FE64BF9B8D7E166240C9149E2363B2647174A566899242EE7 | |||
| 6820 | FOL Installer Generic.exe | C:\Windows\SysWOW64\~GLH000a.TMP | executable | |
MD5:169D623C2C604E17E9517F08AE9D16EB | SHA256:9D0698998FECAD750A8B155D1FBD32471DB1569973A225C15369F411C17E7EC1 | |||
| 6820 | FOL Installer Generic.exe | C:\Windows\SysWOW64\MSCOMCTL.OCX | executable | |
MD5:F70459191C9B65156FFD7930BA6DA13B | SHA256:7329EEB23D21FE0FE64BF9B8D7E166240C9149E2363B2647174A566899242EE7 | |||
| 6820 | FOL Installer Generic.exe | C:\Windows\SysWOW64\COMDLG32.OCX | executable | |
MD5:169D623C2C604E17E9517F08AE9D16EB | SHA256:9D0698998FECAD750A8B155D1FBD32471DB1569973A225C15369F411C17E7EC1 | |||
| 6820 | FOL Installer Generic.exe | C:\Windows\SysWOW64\~GLH000b.TMP | executable | |
MD5:169D623C2C604E17E9517F08AE9D16EB | SHA256:9D0698998FECAD750A8B155D1FBD32471DB1569973A225C15369F411C17E7EC1 | |||
| 6820 | FOL Installer Generic.exe | C:\Program Files (x86)\FilmOrderListener\~GLH000c.TMP | executable | |
MD5:443E13846997C537E8F5ED61130AB705 | SHA256:49EF36BD01B8EBF38C7B807A5FB44CBAF47C9D4EFA883B01C41494C61AE4A2E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
372 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
372 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6464 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4328 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2096 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |