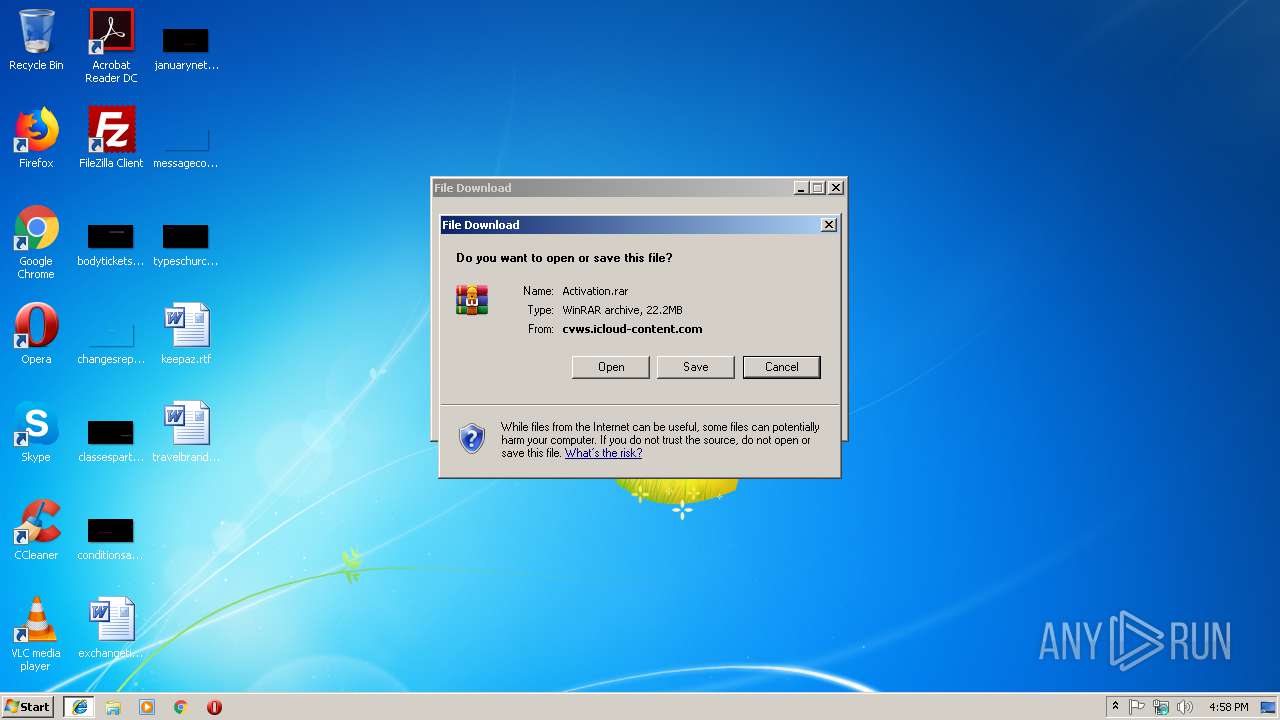
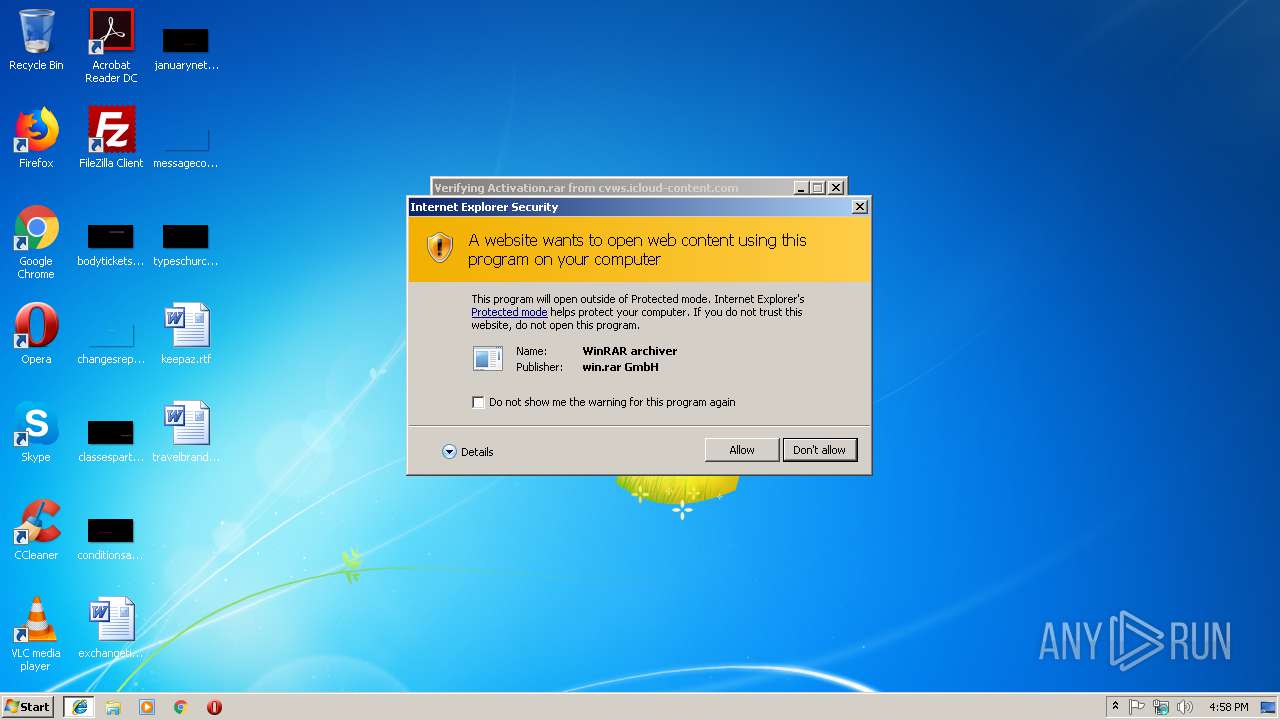
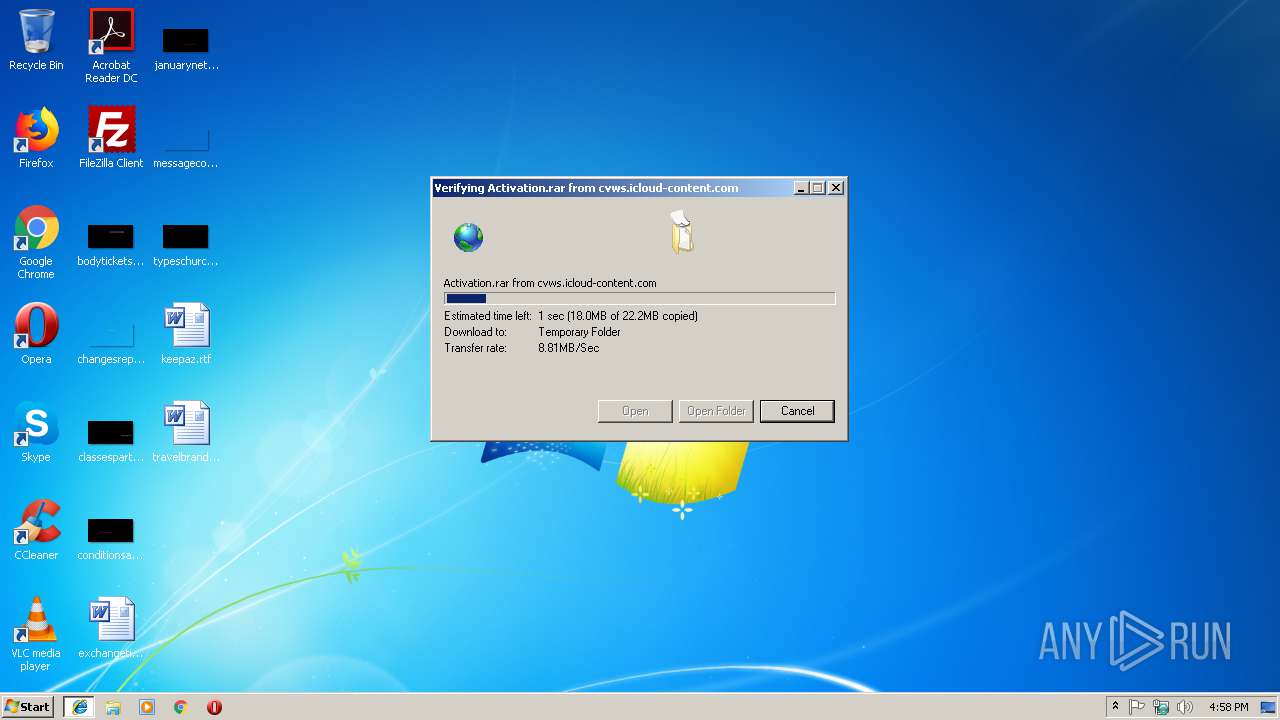
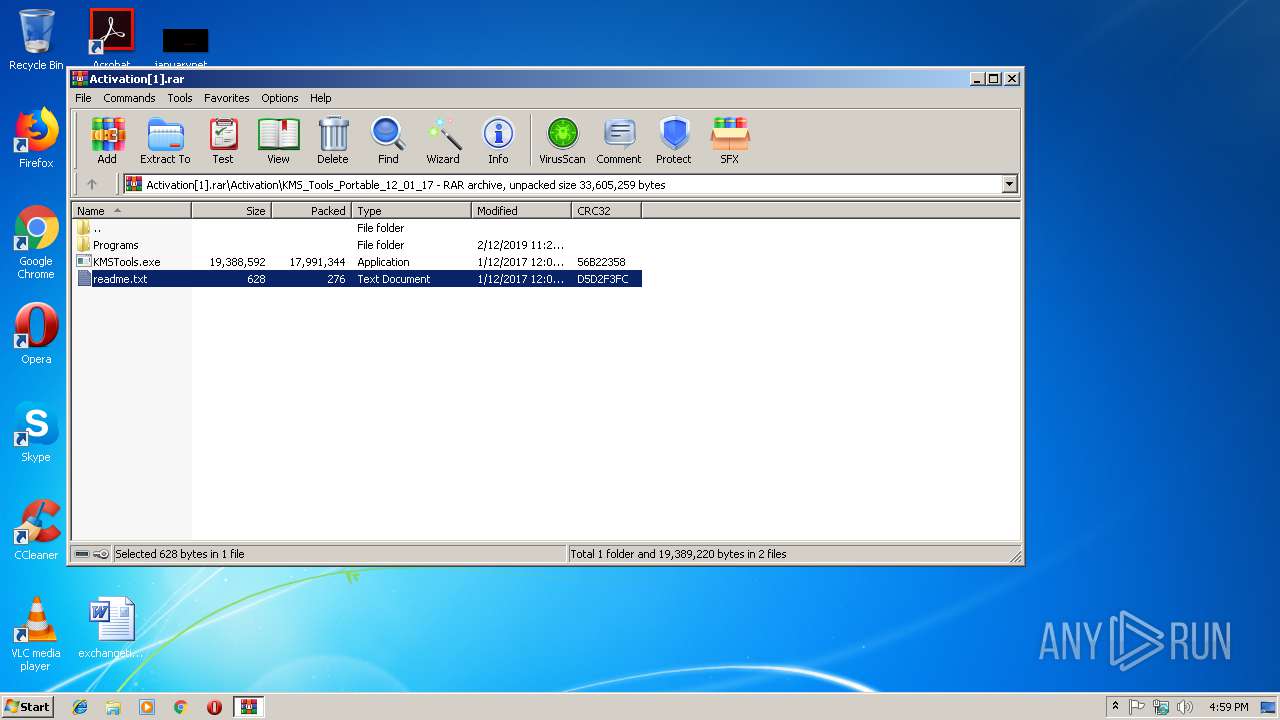
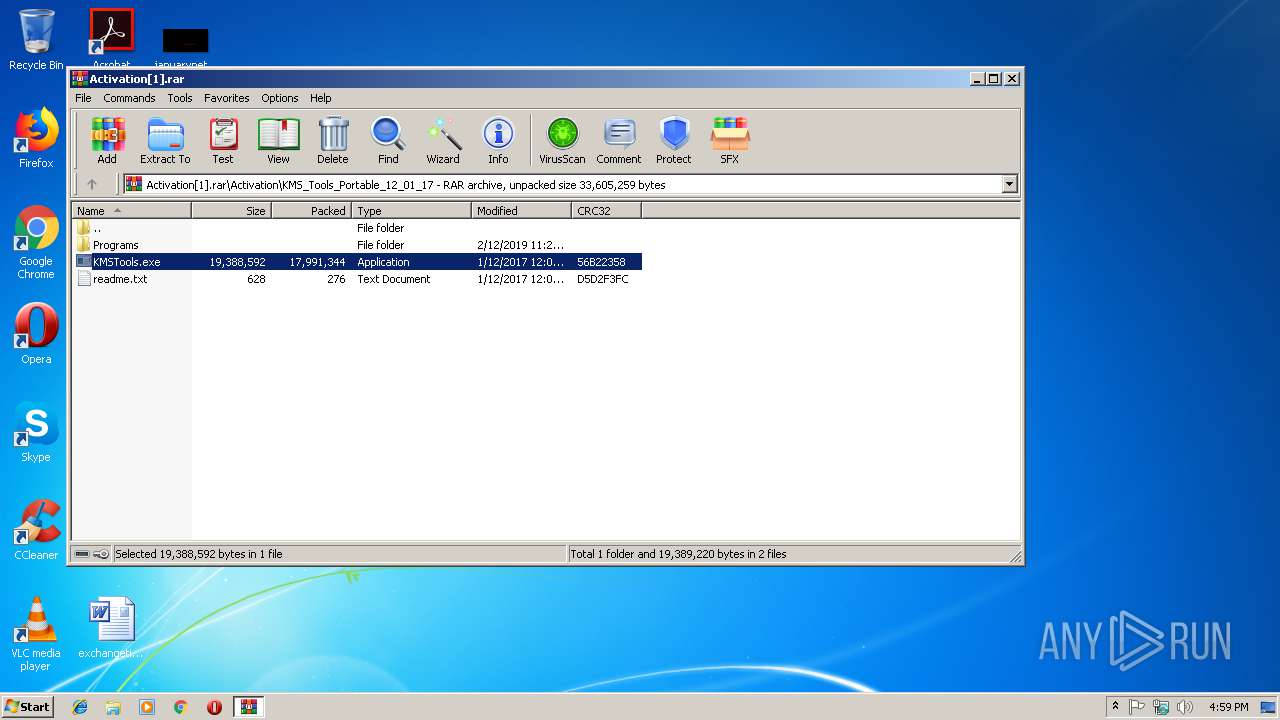
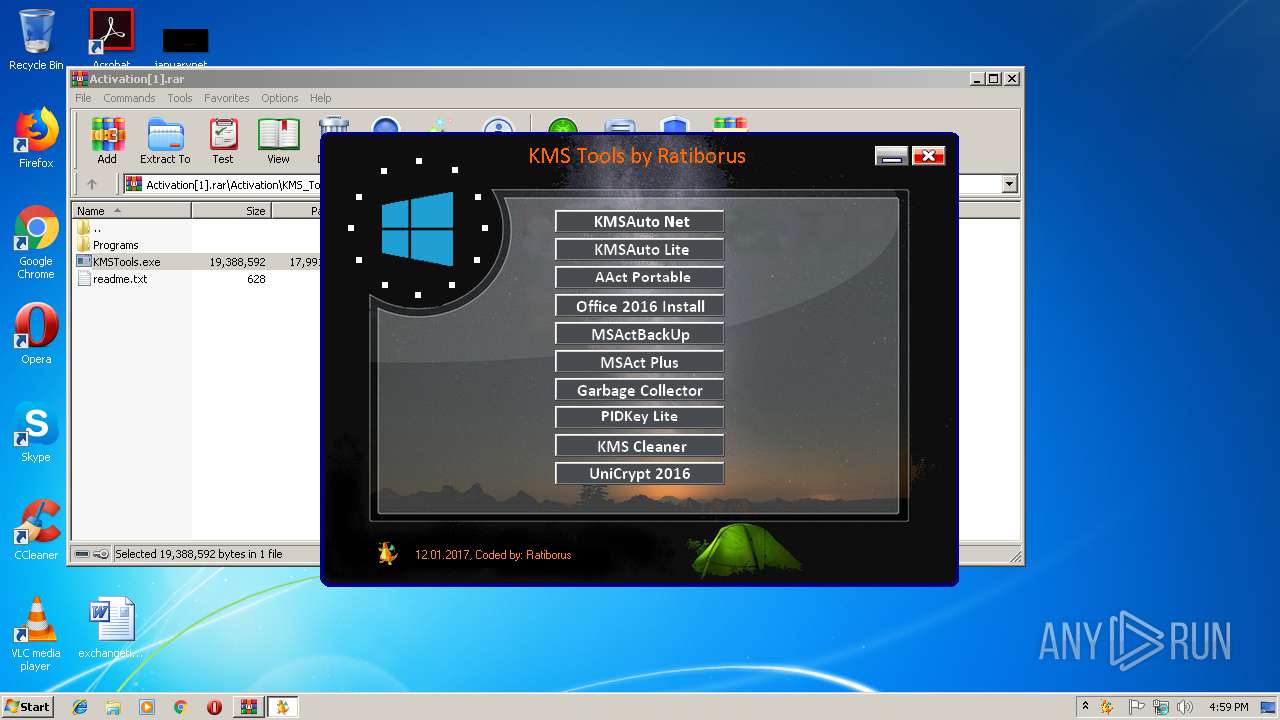
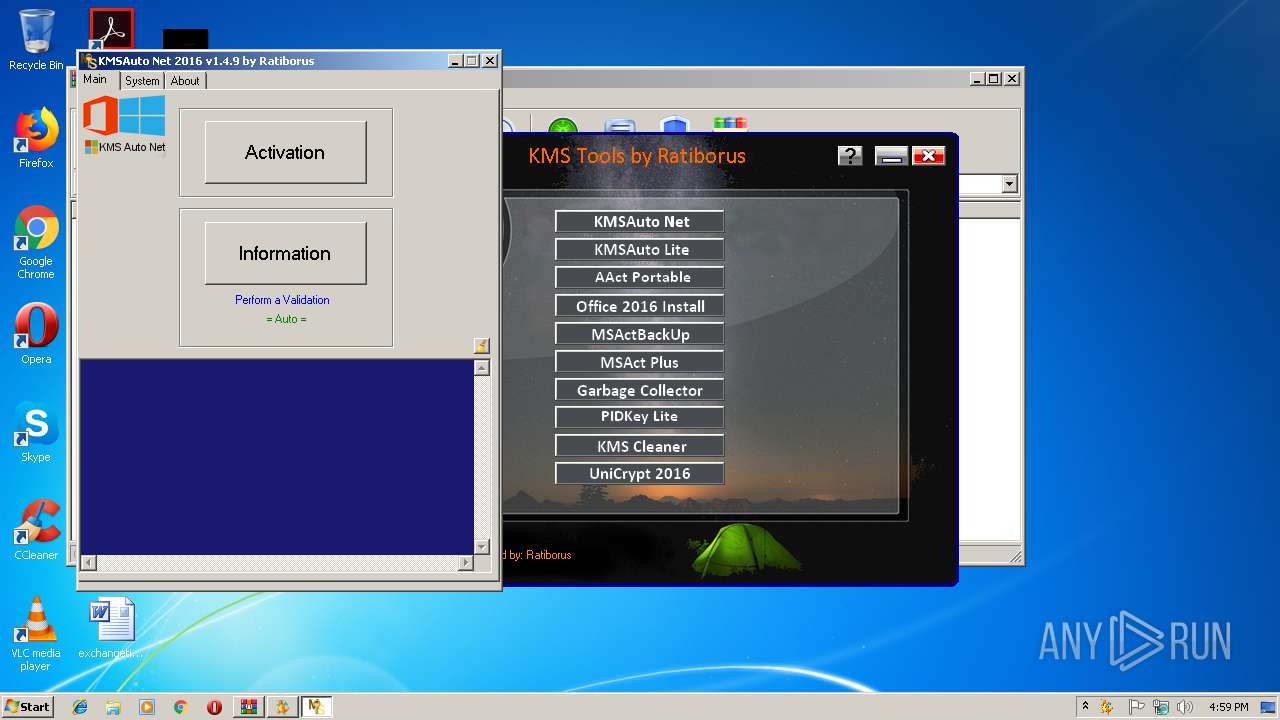
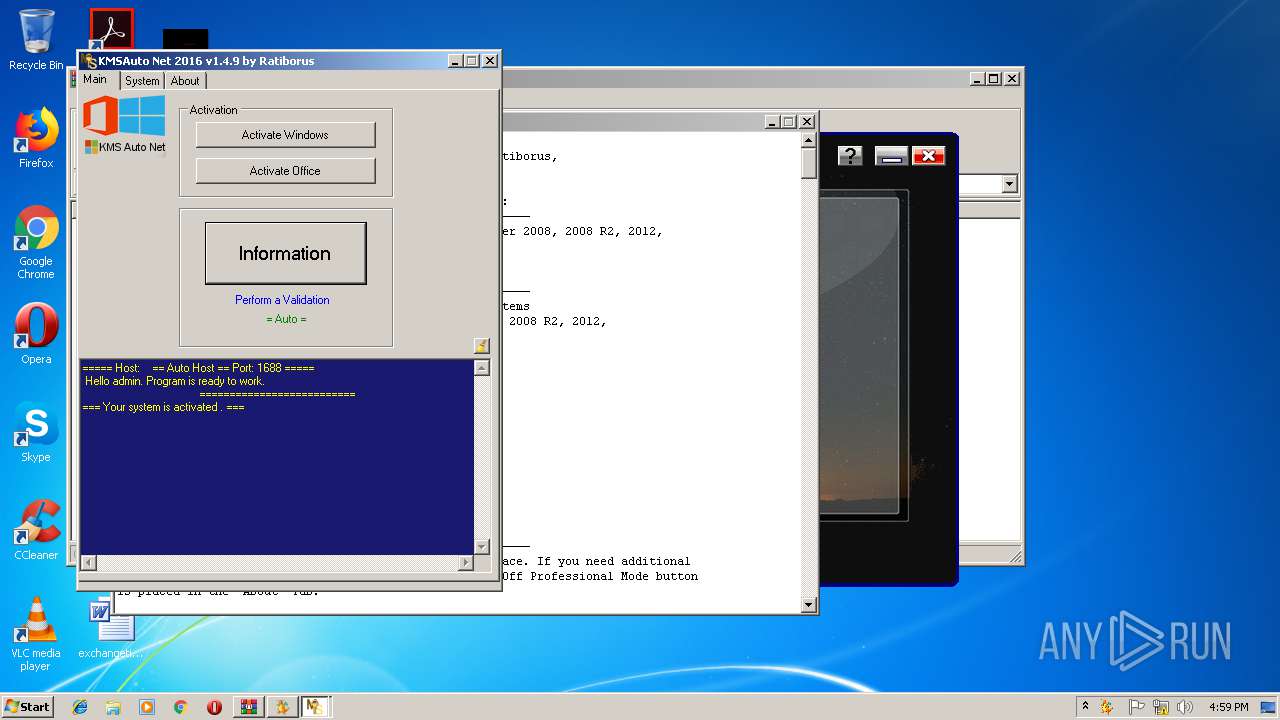
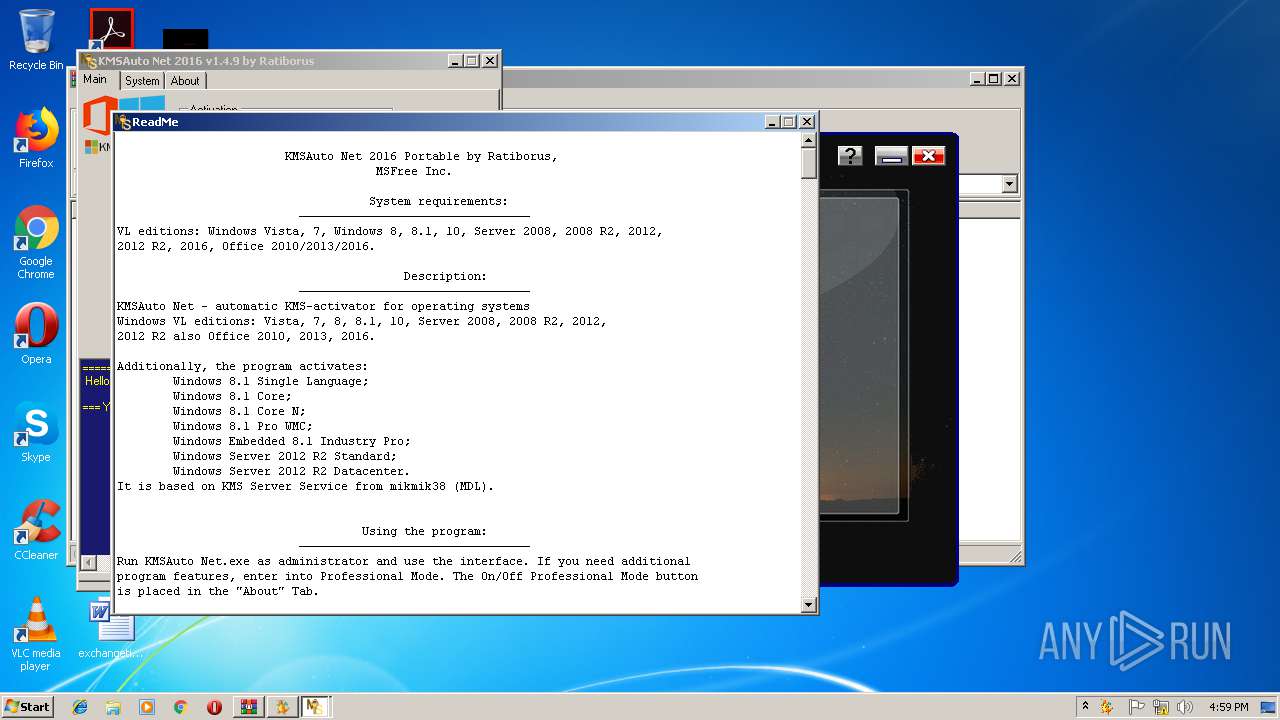
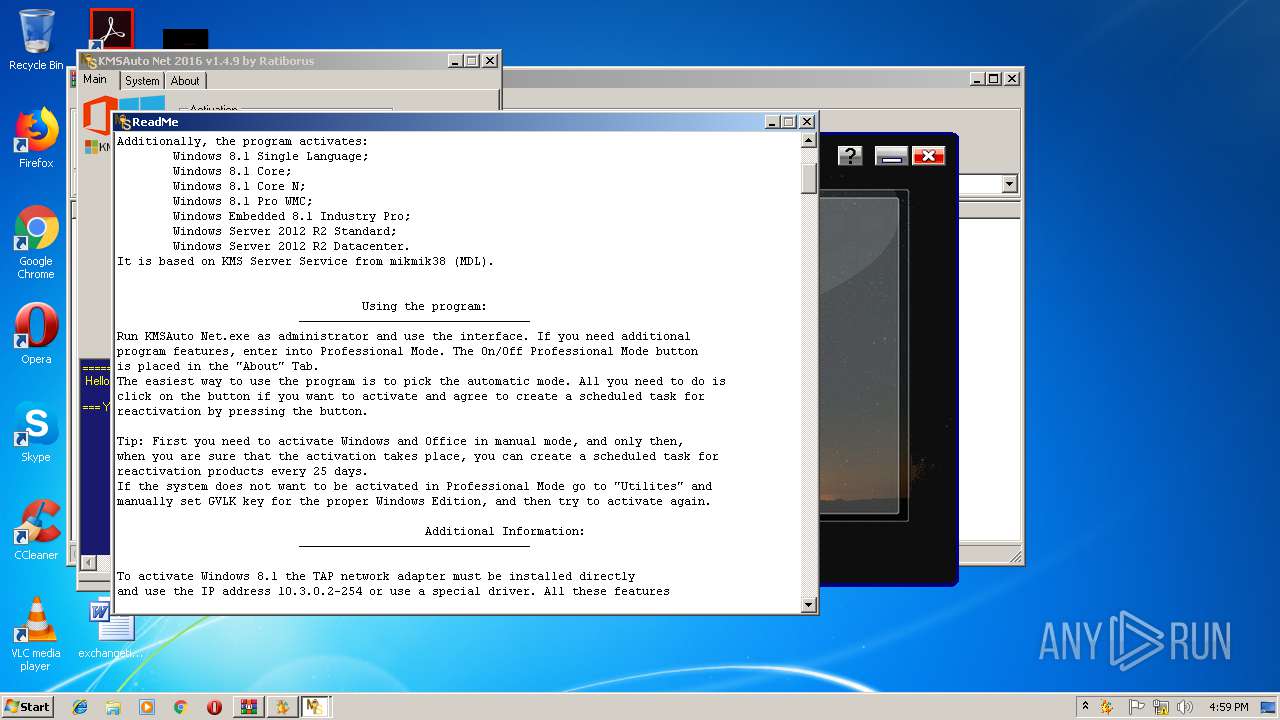
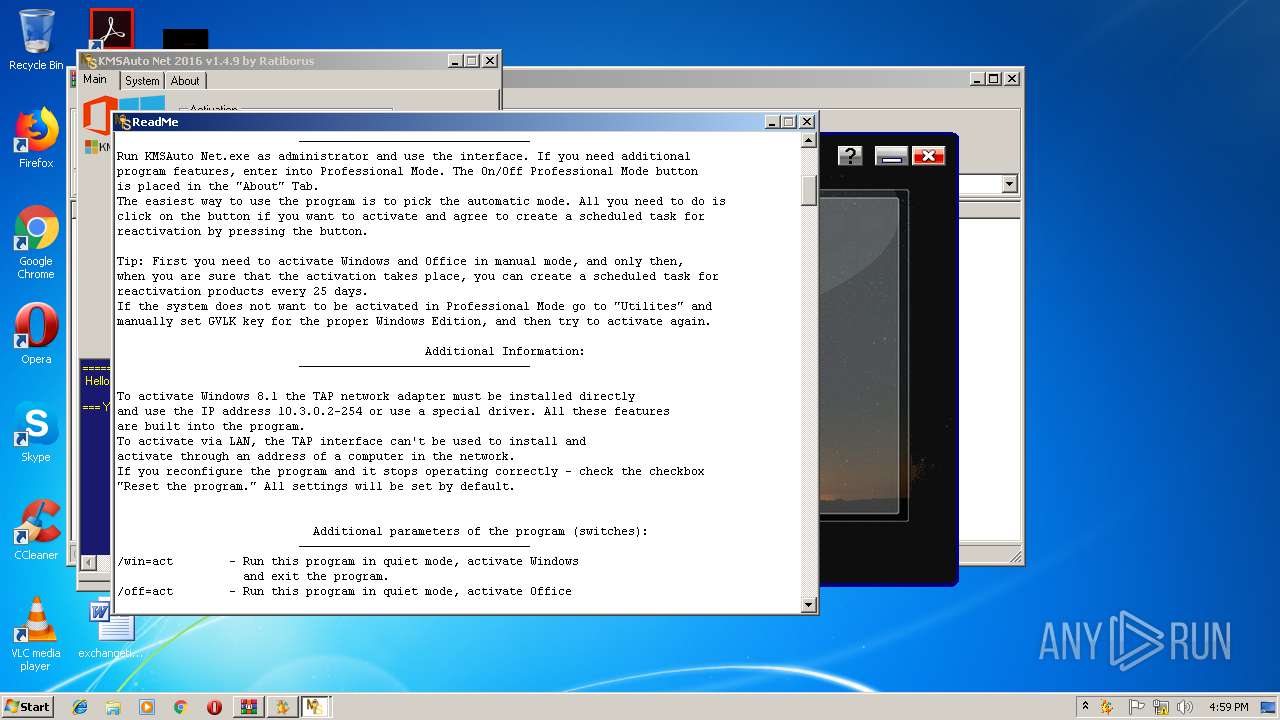
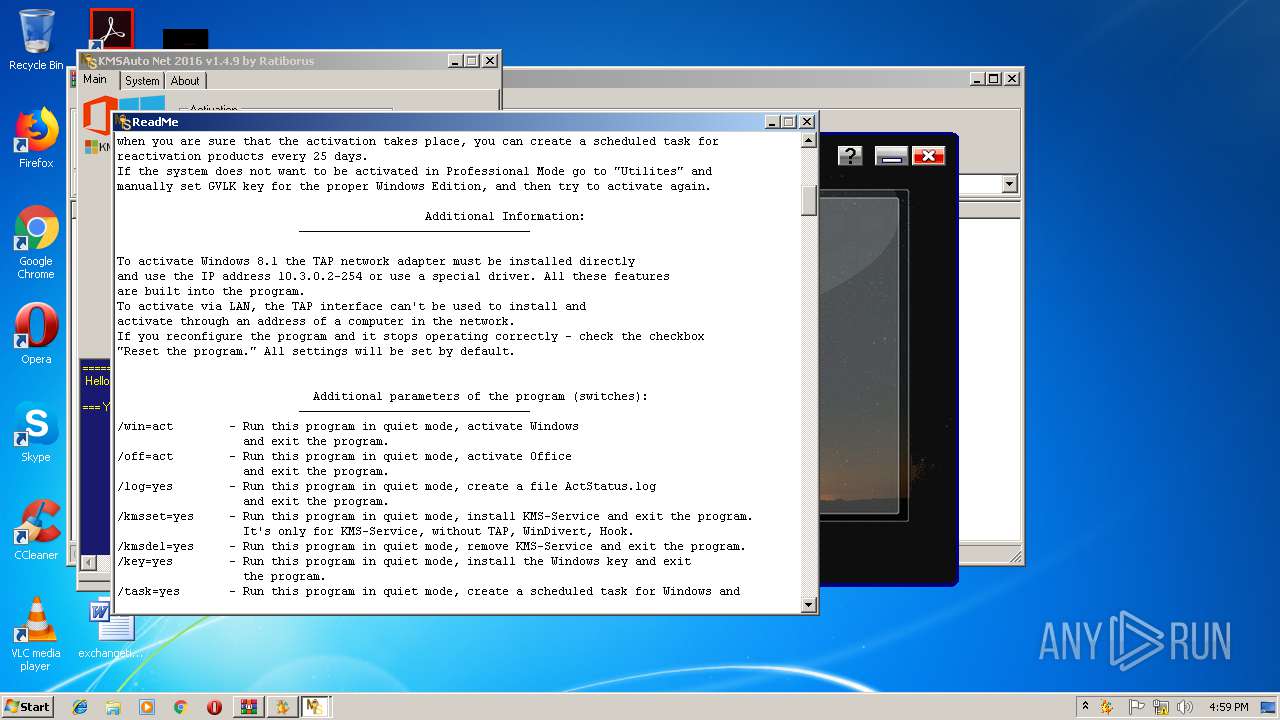
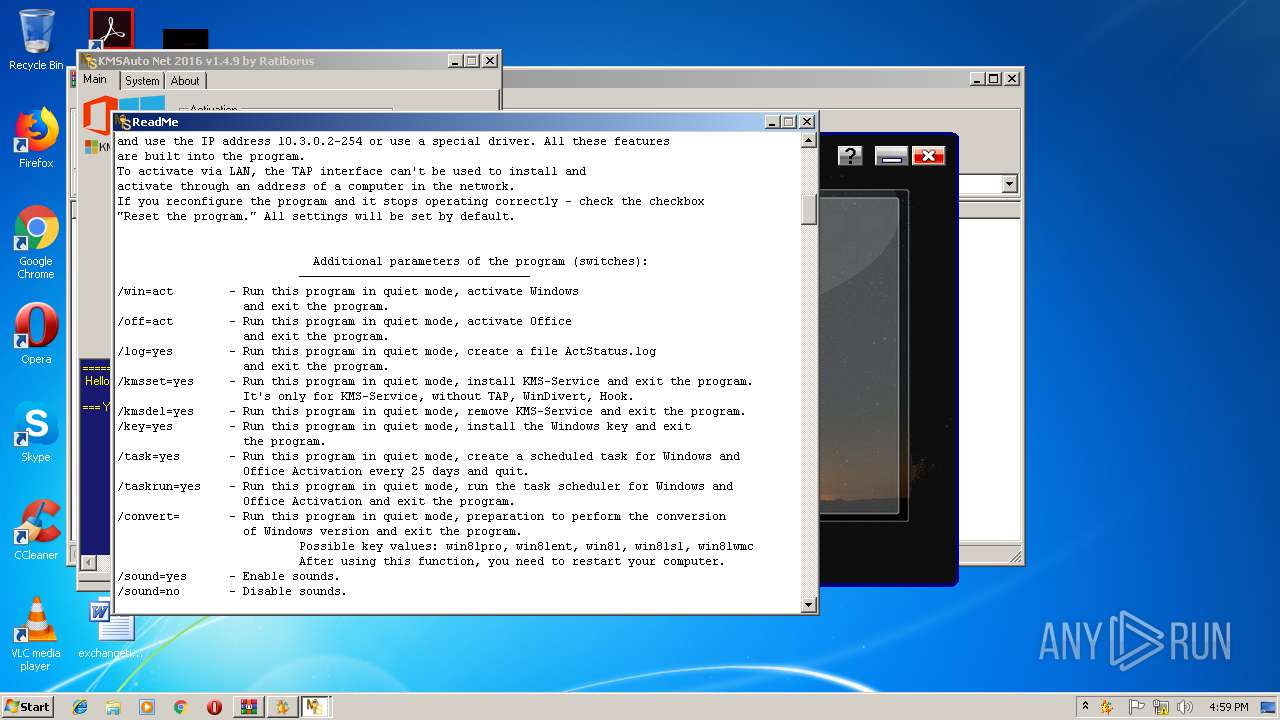
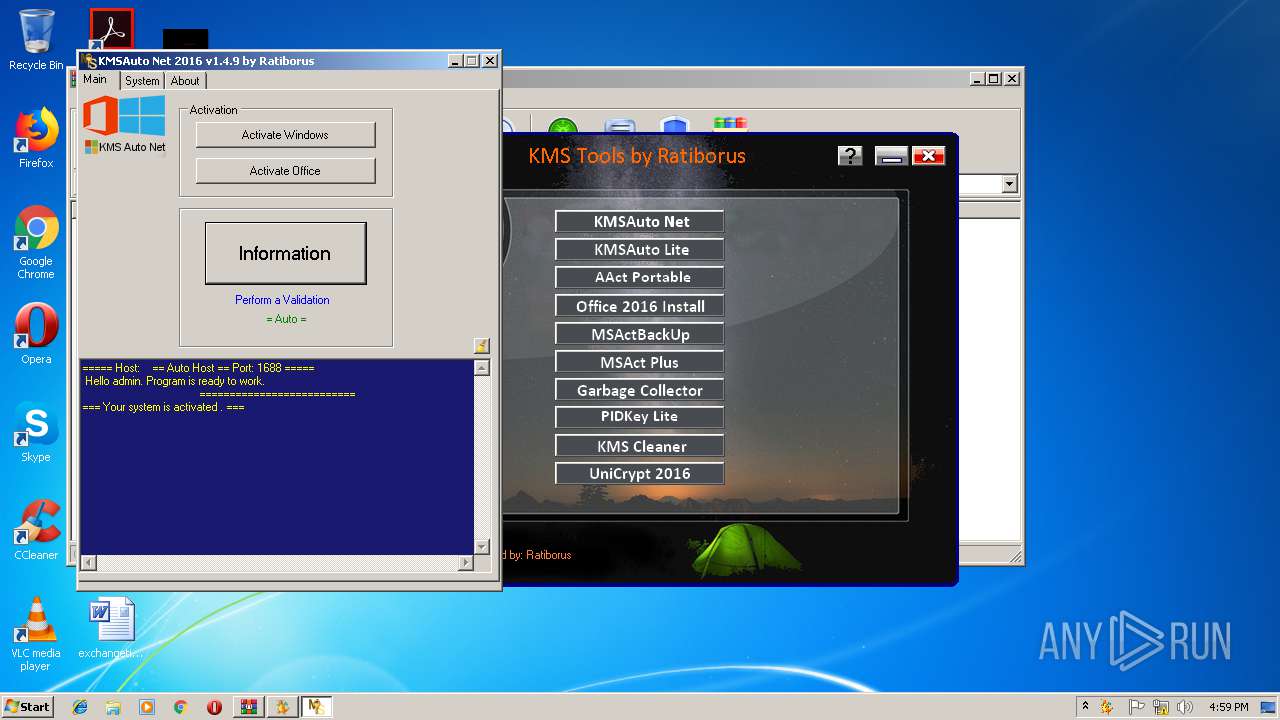
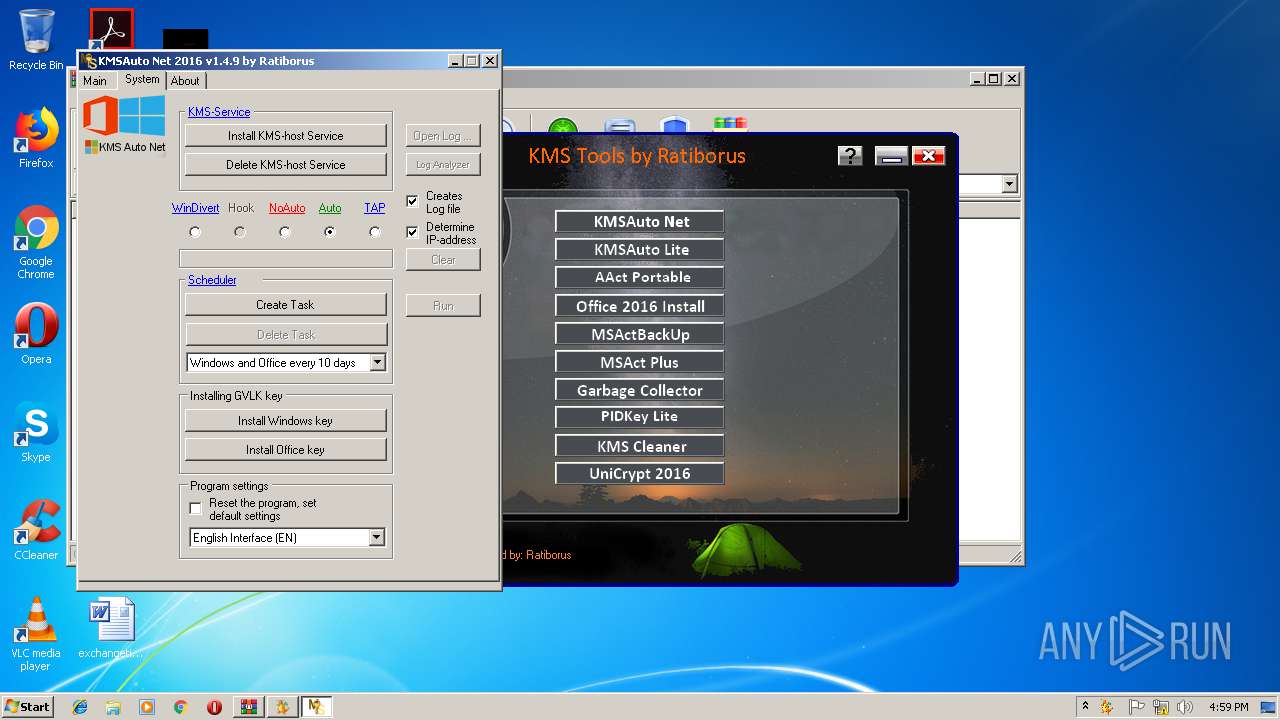
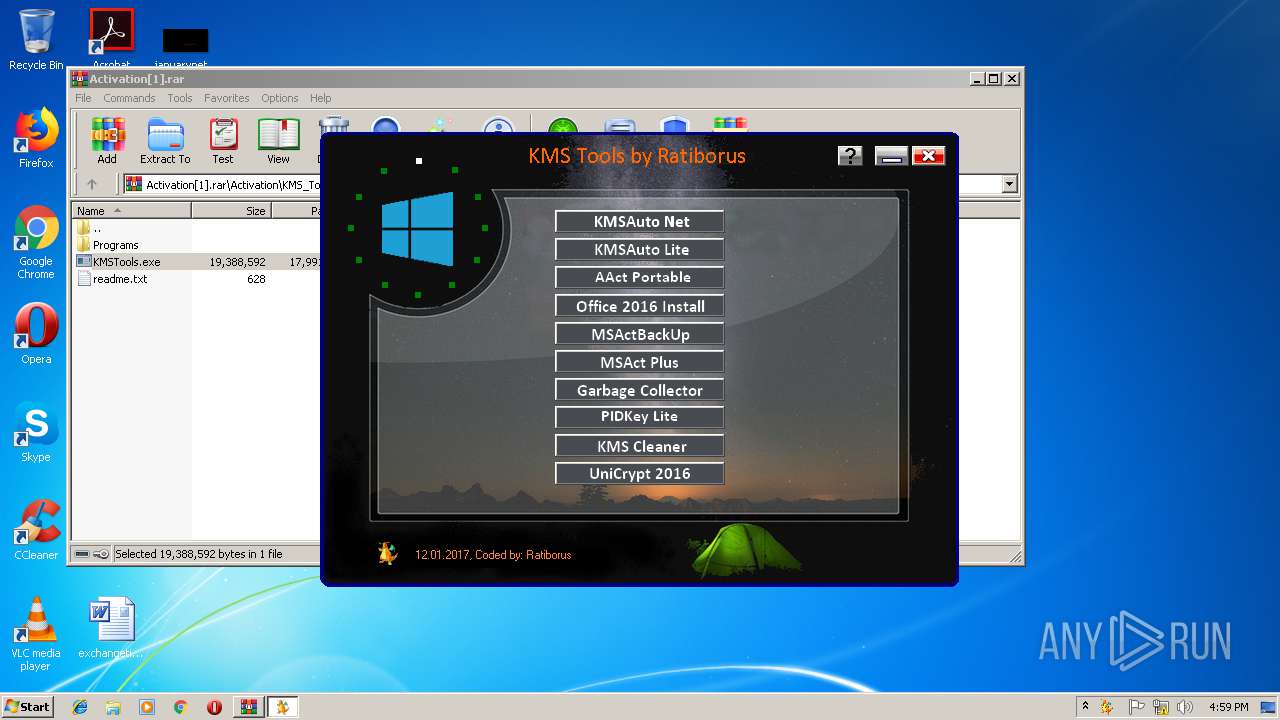
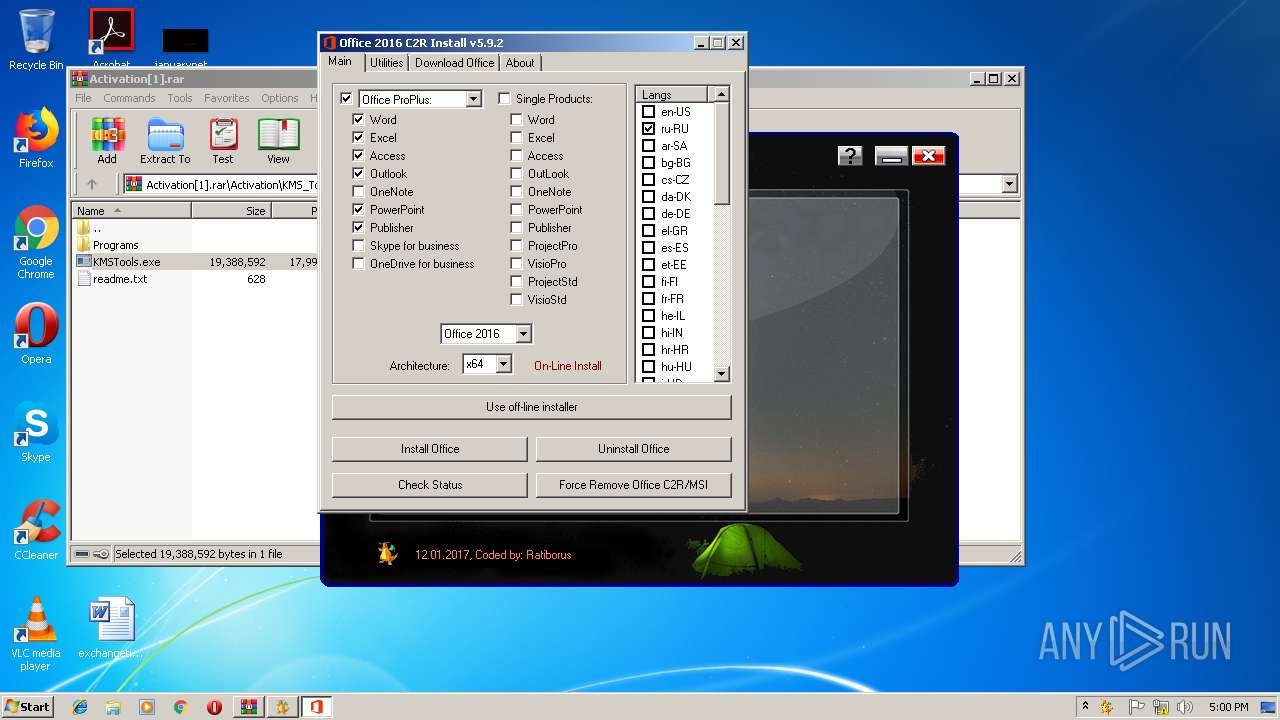
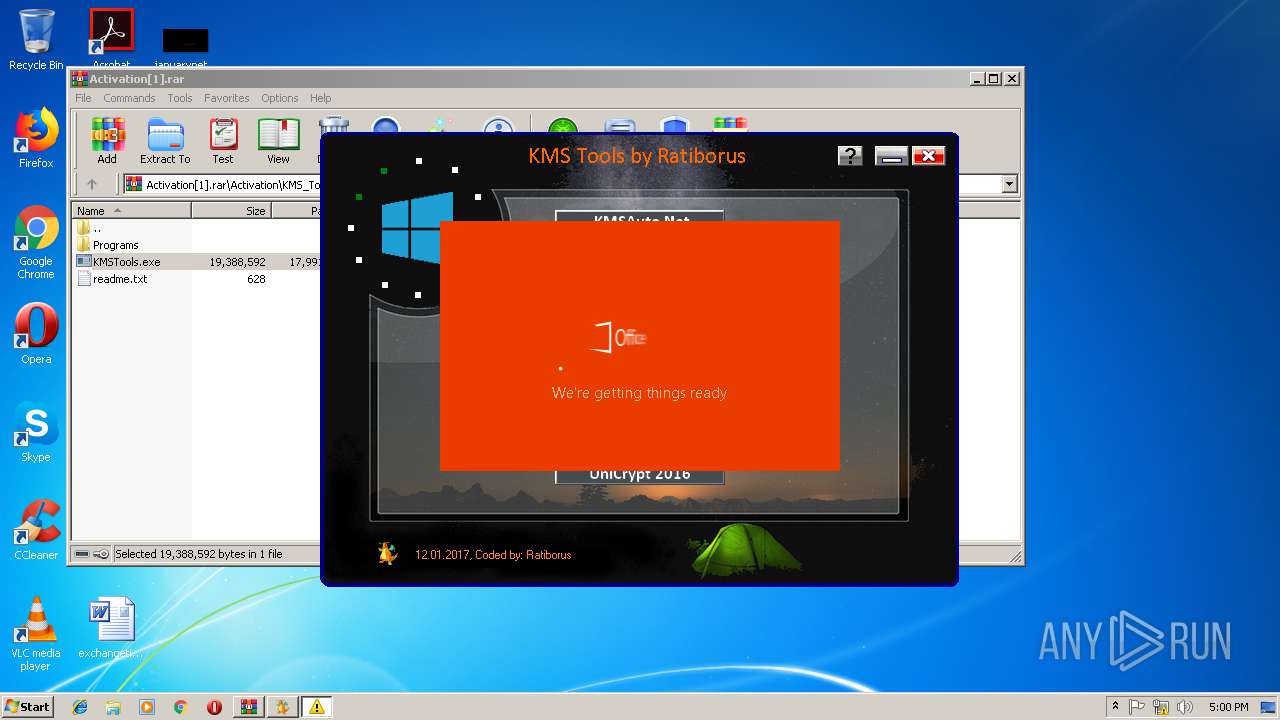
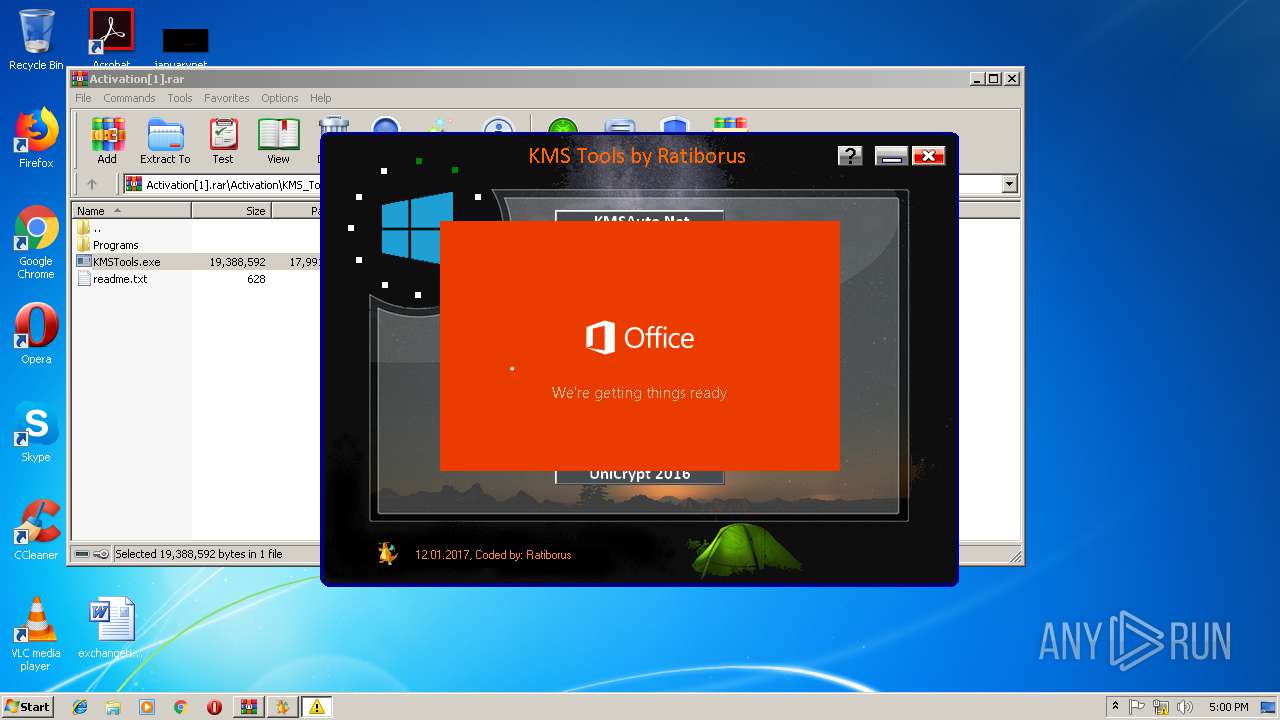
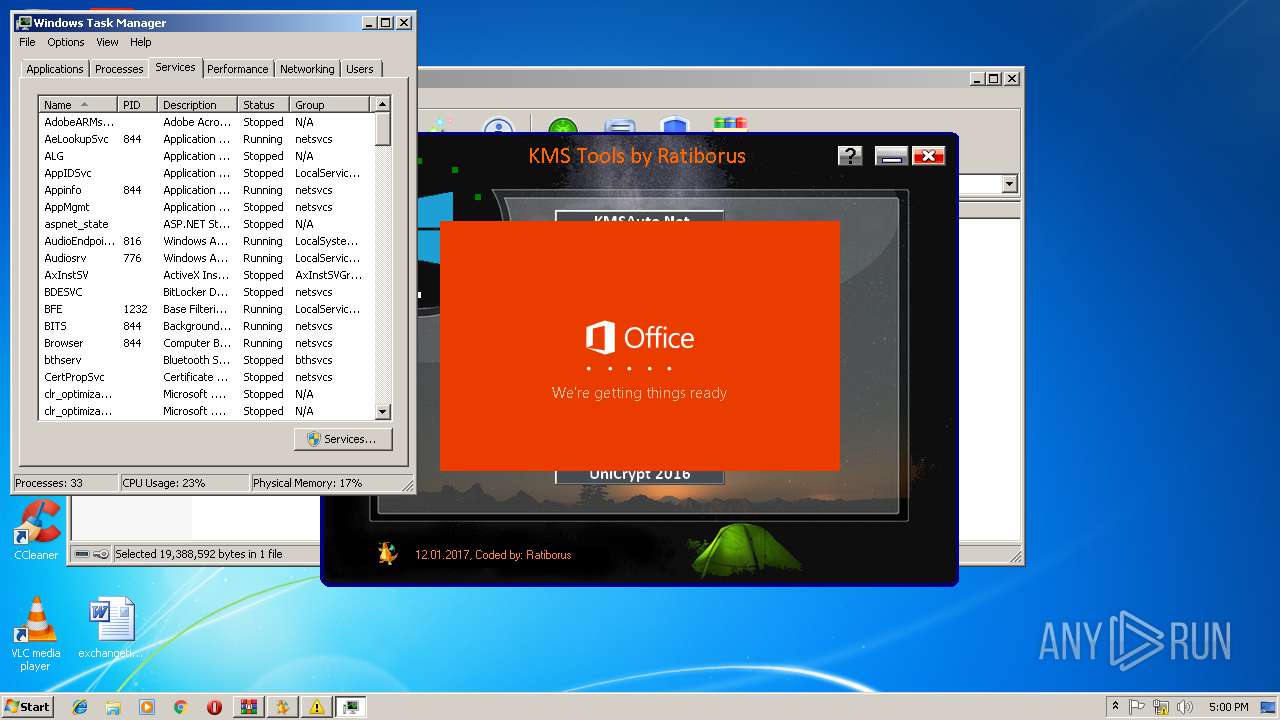
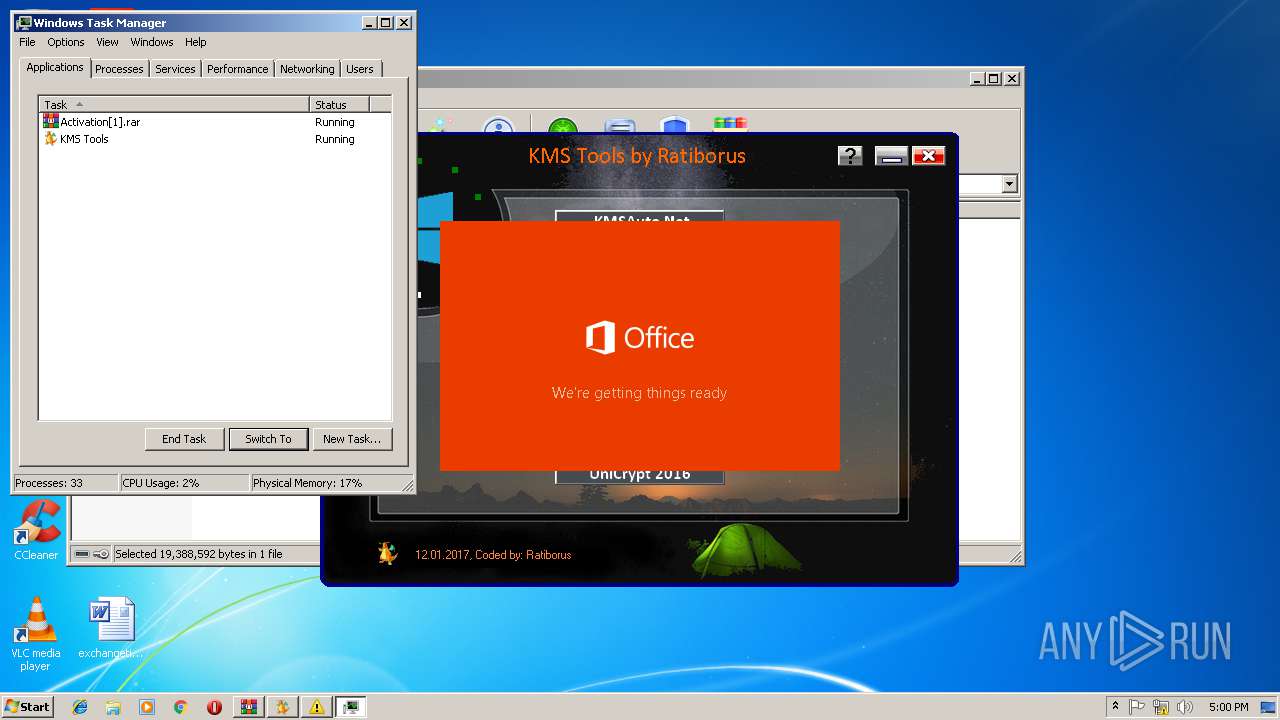
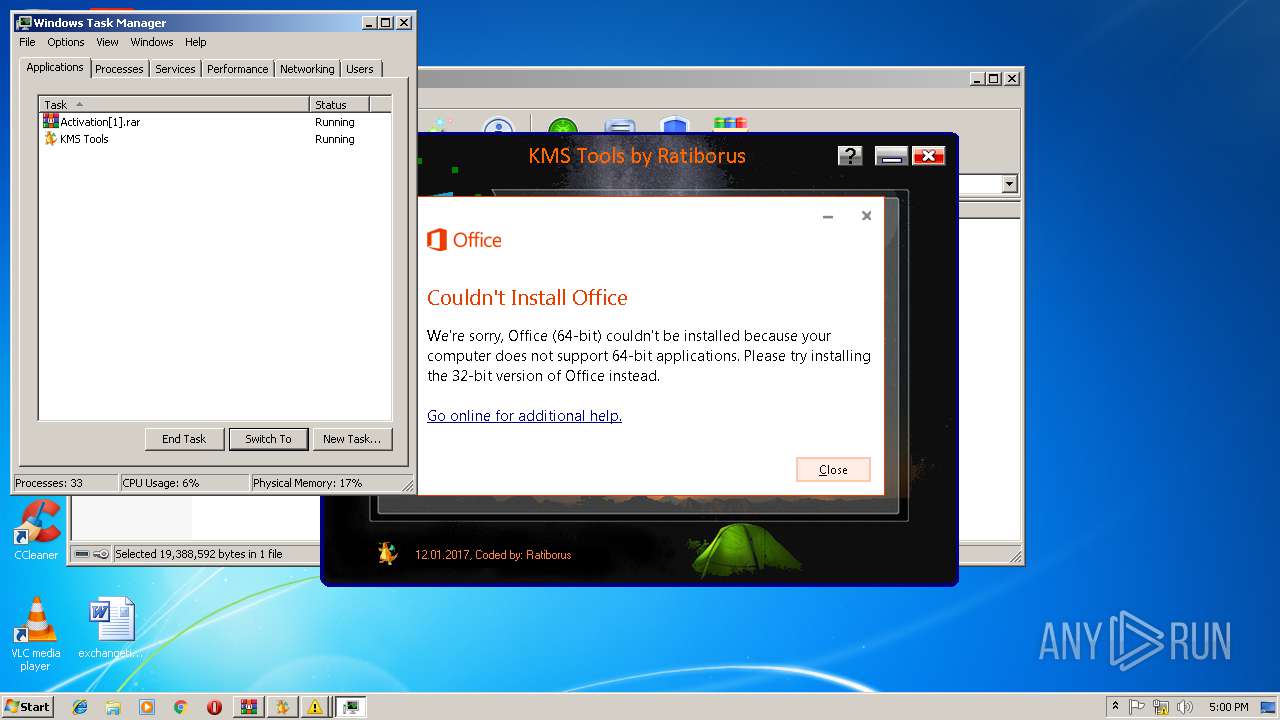
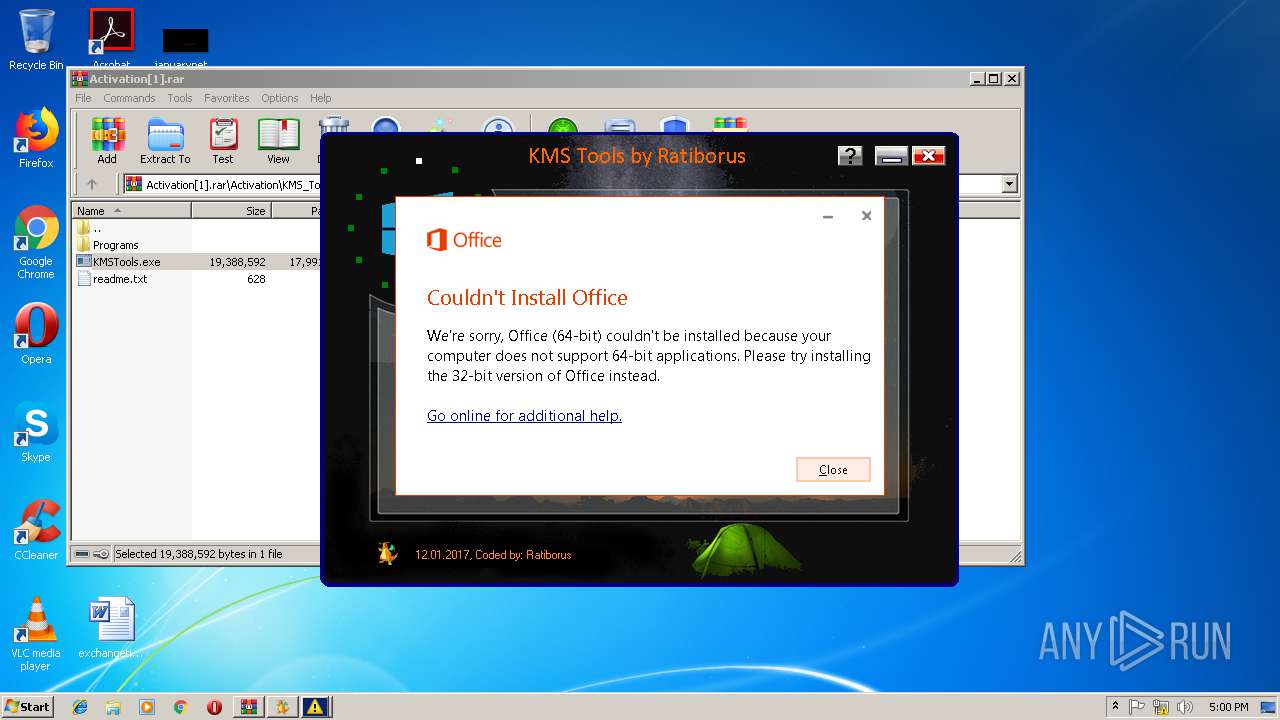
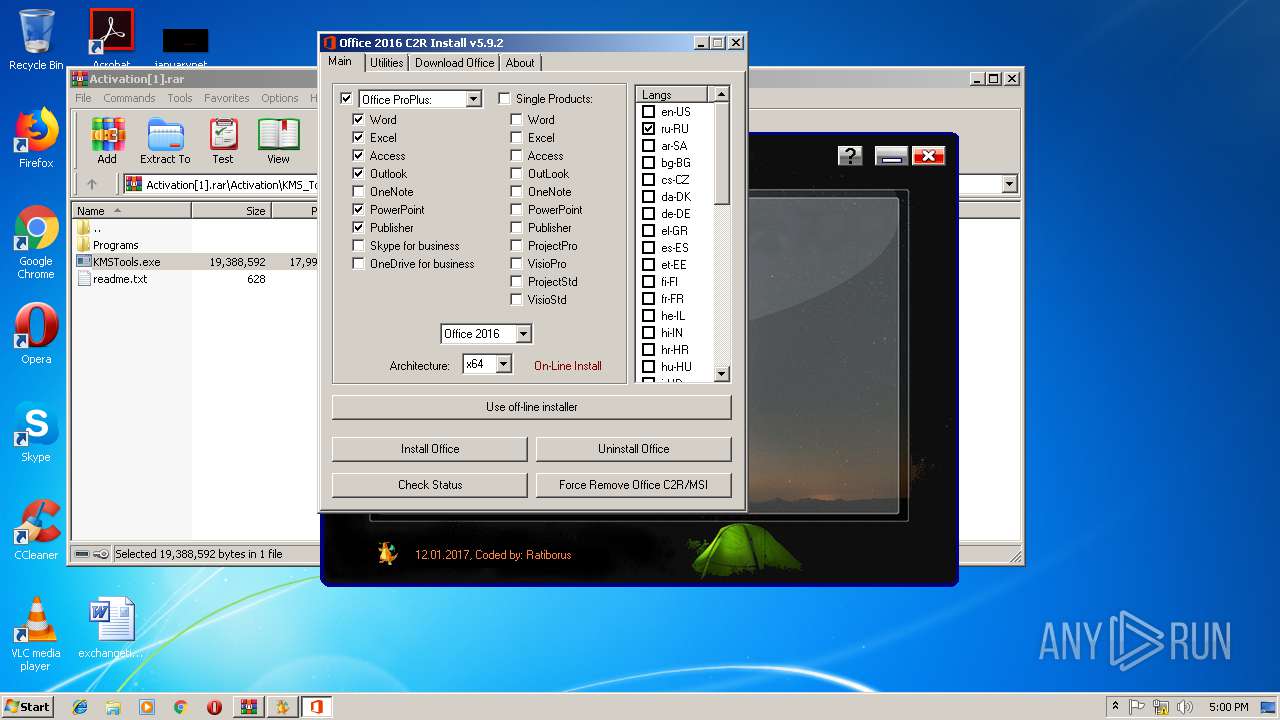
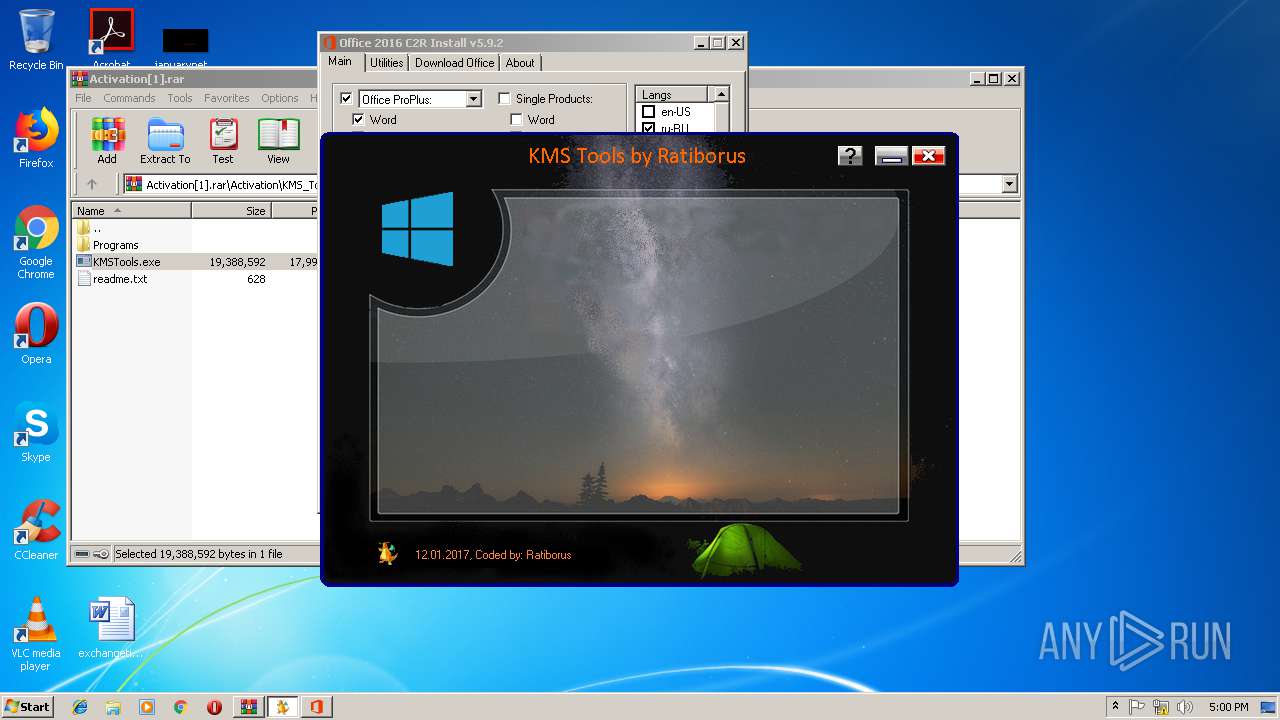
| URL: | https://cvws.icloud-content.com/B/AfeBSE-GgYLDj4PDy0XnTLYnq7kpASxyNhh_9O3eHPrOxnyveZOyWBWS/Activation.rar?o=AhNO4YijyPJmT4G0zYK7SimY4IlmLdgKzhm8xFK7k6ft&v=1&x=3&a=B5tuMM_rnope_7NCIqrHrXwZLI3dAxXRSQEACAHIAP93A0fWA1UoSQ&e=1552563153&k=A8Y0xpQkkjBQPYKhErBdmQ&fl=&r=3b93e0be-4de9-49e1-ae77-3c985f4653a6-1&ckc=com.apple.largeattachment&ckz=Apple-Webmail&y=1&p=34&s=-gjjIrjVBRMwfe3ZZne9xSnTnGQ&teh=1 |
| Full analysis: | https://app.any.run/tasks/1a791528-010a-4ac1-bc85-e10228451a30 |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2019, 16:58:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1BF3A62F2C5CAABA01393471CFD30C79 |
| SHA1: | FABB97789AEBF49E0C159642F772B6D058745193 |
| SHA256: | F013710493F1CD88A9989E971C7375FD014EA8FAE3637036AC7AD1F0A8F221AC |
| SSDEEP: | 12:20RG2mbUXfvBdgUWqkUQVfUMQN/mDMLYN:2IGlbUX3/fzSVcMW/mQLA |
MALICIOUS
Application was dropped or rewritten from another process
- fver.exe (PID: 3568)
- fver.exe (PID: 2068)
- KMSTools.exe (PID: 3728)
- KMSTools.exe (PID: 2460)
- 7zaxxx.exe (PID: 3816)
- KMSAuto Net.exe (PID: 2980)
- OInstall.exe (PID: 3616)
- Setup16.exe (PID: 3364)
- 7zaxxx.exe (PID: 1936)
- GarbageCollector.exe (PID: 3252)
- 7zaxxx.exe (PID: 3720)
- 7zaxxx.exe (PID: 3652)
- KMSCleaner.exe (PID: 1420)
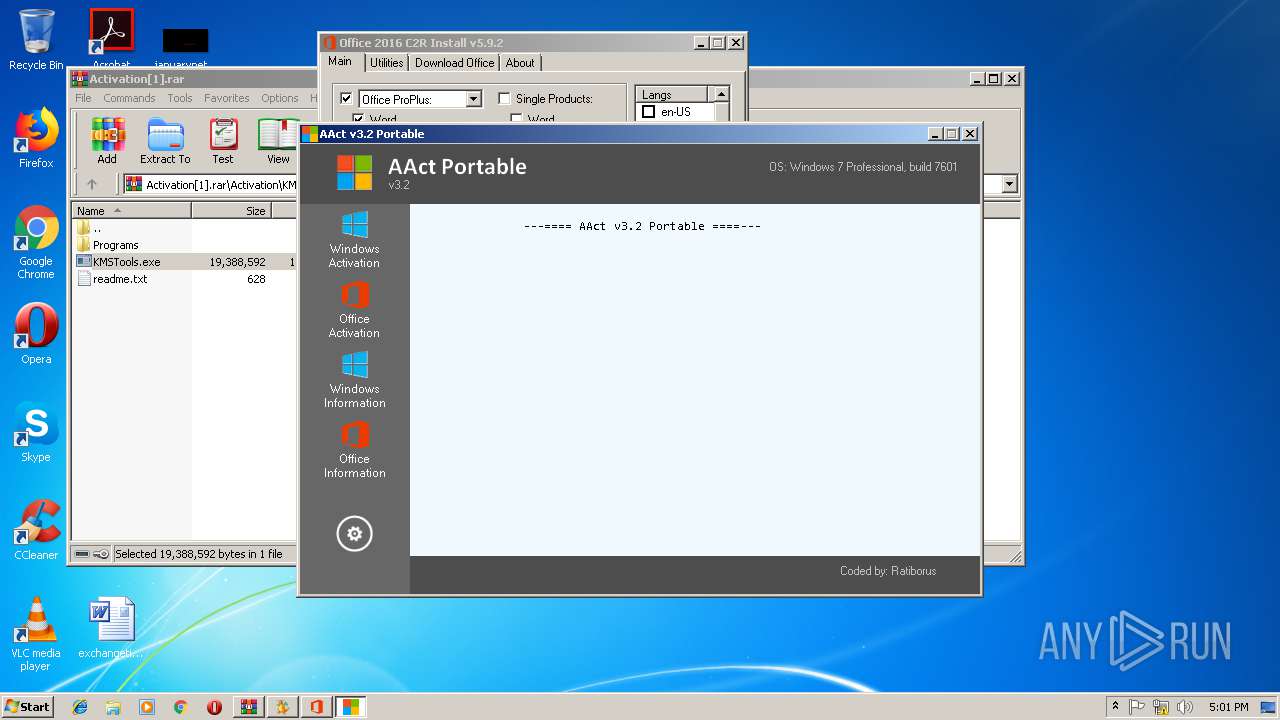
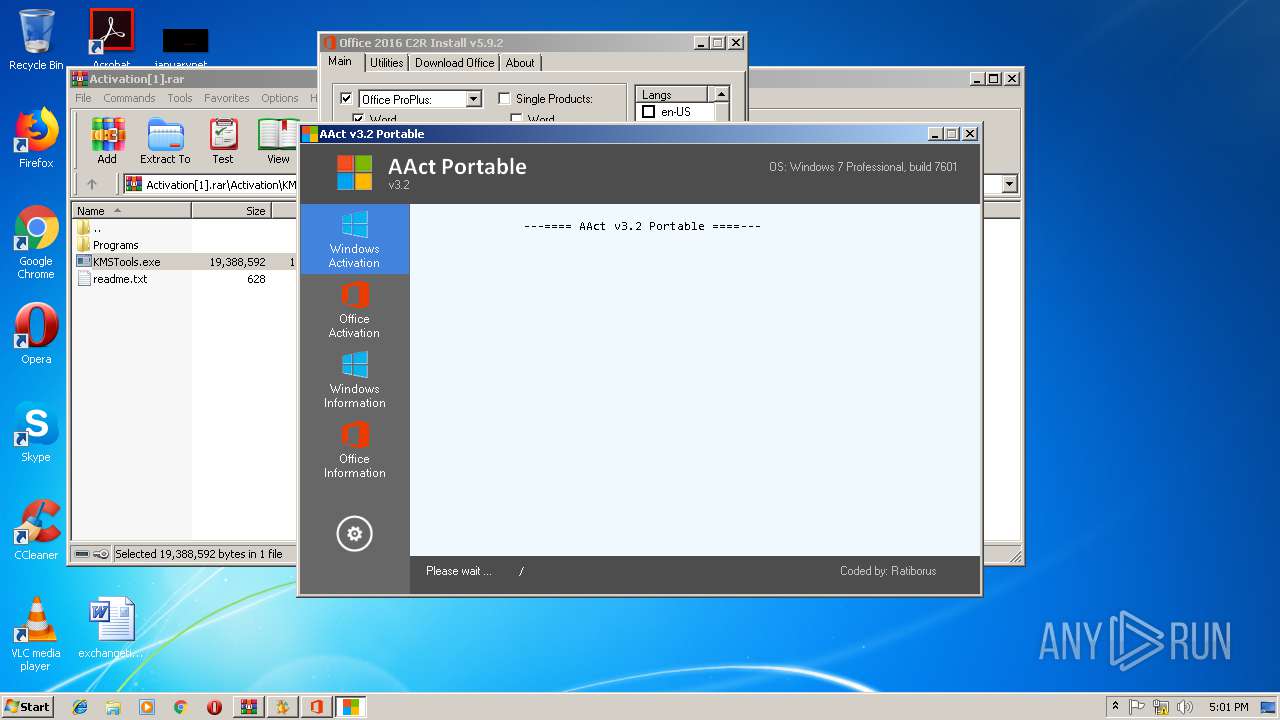
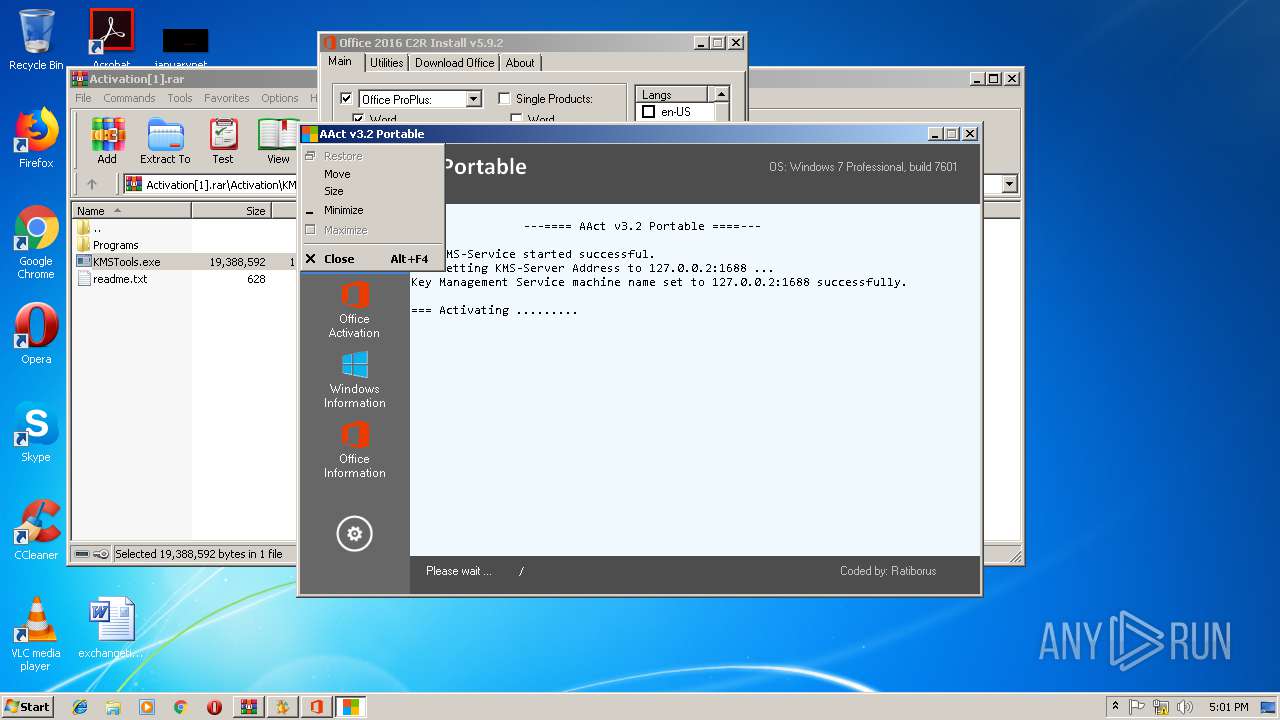
- AAct.exe (PID: 3104)
- aact.dll (PID: 3524)
Loads dropped or rewritten executable
- iexplore.exe (PID: 3336)
- AAct.exe (PID: 3104)
- conhost.exe (PID: 3368)
Changes settings of System certificates
- Setup16.exe (PID: 3364)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3884)
- KMSTools.exe (PID: 2460)
- 7zaxxx.exe (PID: 3816)
- OInstall.exe (PID: 3616)
- 7zaxxx.exe (PID: 1936)
- 7zaxxx.exe (PID: 3720)
- 7zaxxx.exe (PID: 3652)
- AAct.exe (PID: 3104)
Starts CMD.EXE for commands execution
- KMSTools.exe (PID: 2460)
- KMSAuto Net.exe (PID: 2980)
- OInstall.exe (PID: 3616)
- AAct.exe (PID: 3104)
Reads Environment values
- KMSAuto Net.exe (PID: 2980)
Reads internet explorer settings
- KMSAuto Net.exe (PID: 2980)
- GarbageCollector.exe (PID: 3252)
Adds / modifies Windows certificates
- Setup16.exe (PID: 3364)
Changes IE settings (feature browser emulation)
- GarbageCollector.exe (PID: 3252)
Creates files in the user directory
- GarbageCollector.exe (PID: 3252)
Executes scripts
- cmd.exe (PID: 2184)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 2776)
- cmd.exe (PID: 3576)
- cmd.exe (PID: 2812)
- cmd.exe (PID: 4056)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1820)
- cmd.exe (PID: 2592)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 3668)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 3732)
Uses REG.EXE to modify Windows registry
- AAct.exe (PID: 3104)
Starts application with an unusual extension
- AAct.exe (PID: 3104)
INFO
Changes settings of System certificates
- iexplore.exe (PID: 2996)
Reads Internet Cache Settings
- iexplore.exe (PID: 3336)
Changes internet zones settings
- iexplore.exe (PID: 2996)
Application launched itself
- iexplore.exe (PID: 2996)
Reads settings of System Certificates
- iexplore.exe (PID: 2996)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
120
Monitored processes
56
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | Netsh.exe Advfirewall Firewall delete rule name=AAct_IN_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.16080\Activation\KMS_Tools_Portable_12_01_17\Programs\KMSCleaner v1.5 Portable\KMSCleaner.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.16080\Activation\KMS_Tools_Portable_12_01_17\Programs\KMSCleaner v1.5 Portable\KMSCleaner.exe | — | KMSTools.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1524 | Netsh.exe Advfirewall Firewall delete rule name=AAct_OUT_Port_KMS protocol=TCP | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1576 | cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /ckms | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1820 | "C:\Windows\System32\cmd.exe" /c Netsh.exe Advfirewall Firewall delete rule name=AAct_IN_Port_KMS protocol=TCP | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1936 | "C:\Users\admin\AppData\Local\Temp\7zaxxx.exe" x data.pak -pkmstools -y -bsp1 -o"C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.16080\Activation\KMS_Tools_Portable_12_01_17\Programs" "Garbage Collector"* | C:\Users\admin\AppData\Local\Temp\7zaxxx.exe | KMSTools.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
| 2068 | "C:\Users\admin\AppData\Local\Temp\fver.exe" /D /A "C:\Users\admin\AppData\Local\Temp\Rar$EXa3884.16080\Activation\KMS_Tools_Portable_12_01_17\Programs\Office 2013-2016 C2R Install v5.9.2\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\fver.exe | — | KMSTools.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2080 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /act-type 0 | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2184 | "C:\Windows\System32\cmd.exe" /c cscript.exe C:\Windows\System32\slmgr.vbs //NoLogo /upk XXXXX | C:\Windows\System32\cmd.exe | — | AAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2344 | C:\Windows\System32\cmd.exe /D /c del /F /Q "kmsauto.ini" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 929
Read events
1 520
Write events
403
Delete events
6
Modification events
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {19906C5B-3B7A-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2996) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307020004001C0010003A002A003703 | |||
Executable files
15
Suspicious files
10
Text files
48
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2996 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8BFA.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8BFB.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8C2B.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8C2C.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8D27.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8D28.tmp | — | |
MD5:— | SHA256:— | |||
| 2996 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF03ED0698473E99BE.TMP | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\Activation[1].rar | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
10
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3364 | Setup16.exe | HEAD | 301 | 2.18.68.82:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/MRO.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | HEAD | 200 | 2.16.186.83:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/MRO.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | GET | 301 | 2.18.68.82:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/MRO.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | GET | — | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
3364 | Setup16.exe | HEAD | 301 | 2.18.68.82:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.11231.20174.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | GET | 301 | 2.18.68.82:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.11231.20174.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | GET | 200 | 2.16.186.83:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/MRO.cab | unknown | compressed | 16.0 Kb | whitelisted |
3364 | Setup16.exe | HEAD | 301 | 2.18.68.82:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/MRO-E.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | GET | 301 | 2.18.68.82:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/MRO-E.cab | unknown | — | — | whitelisted |
3364 | Setup16.exe | HEAD | 200 | 2.16.186.83:80 | http://officecdn.microsoft.com.edgesuite.net/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v64_16.0.11231.20174.cab | unknown | compressed | 16.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3336 | iexplore.exe | 17.248.146.12:443 | cvws.icloud-content.com | Apple Inc. | US | unknown |
2996 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3336 | iexplore.exe | 2.16.186.81:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3364 | Setup16.exe | 2.16.186.83:80 | officecdn.microsoft.com.edgesuite.net | Akamai International B.V. | — | whitelisted |
3364 | Setup16.exe | 2.18.68.82:80 | officecdn.microsoft.com | Akamai International B.V. | — | whitelisted |
3364 | Setup16.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
3252 | GarbageCollector.exe | 89.111.162.36:80 | img15.nnm.me | Jsc ru-center | RU | unknown |
2732 | wmiprvse.exe | 92.122.18.115:80 | go.microsoft.com | Akamai Technologies, Inc. | GB | whitelisted |
2732 | wmiprvse.exe | 65.52.98.231:443 | activation.sls.microsoft.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cvws.icloud-content.com |
| suspicious |
www.bing.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
officecdn.microsoft.com.edgesuite.net |
| whitelisted |
crl.microsoft.com |
| whitelisted |
img15.nnm.me |
| unknown |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |