| File name: | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b |
| Full analysis: | https://app.any.run/tasks/5e7377c5-303f-49fd-baa1-95c36c8d981f |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2025, 00:29:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 78627054F0DD401024493FC0C4A2067E |
| SHA1: | AAC22D91C3115D739DADD2F777F6FEF0FA21BCD6 |
| SHA256: | EFE31D3A135025BC8F8F5951A1FBACE3586389F5B98F55DDEAF8C74C9D3D504B |
| SSDEEP: | 98304:Y/QMcyl7Ic5llxp3eh9D1lej9O6+GNHOsnHeeHs+H9/pZvOU3kGY2QK35YbX0MBd:mghGdKtGoE0Kw65/K |
MALICIOUS
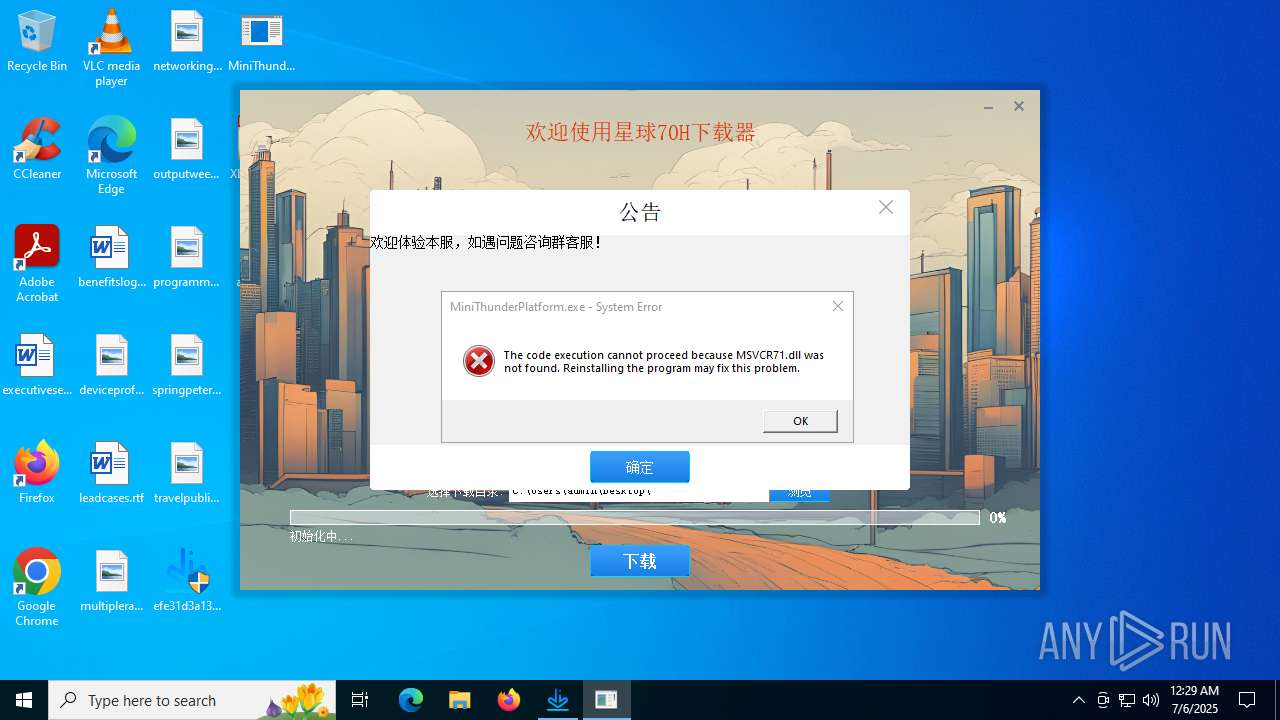
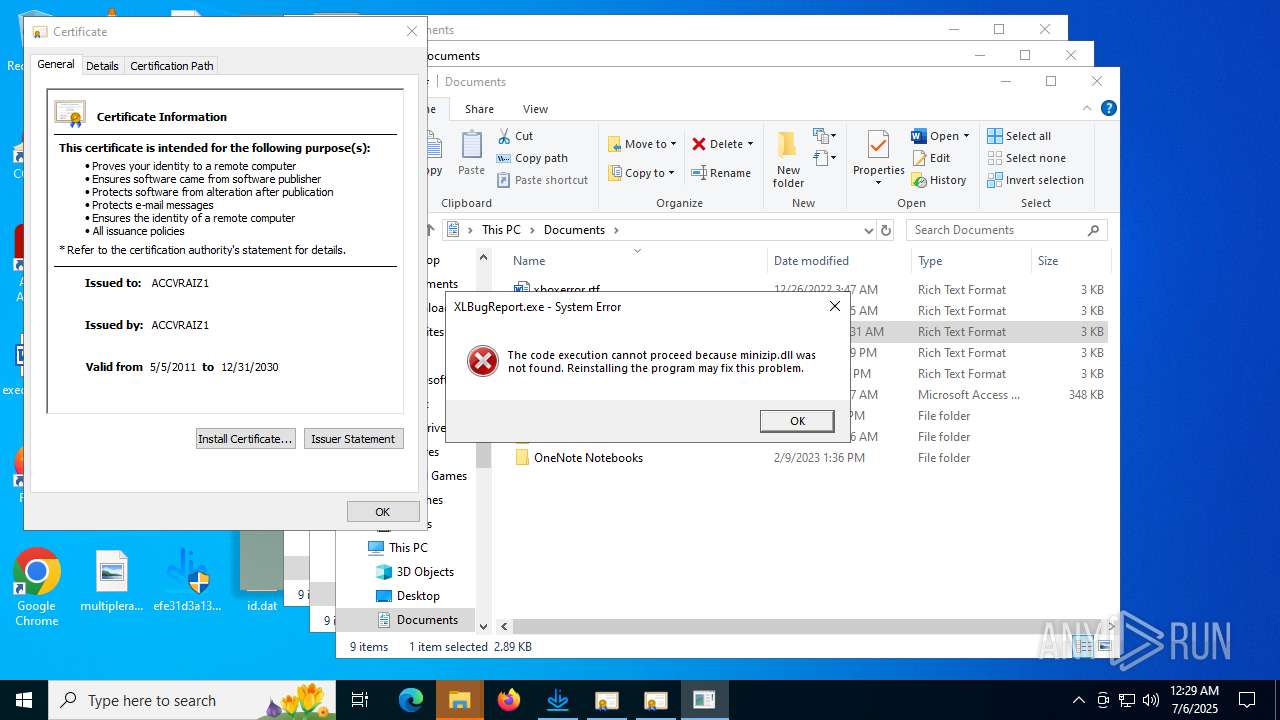
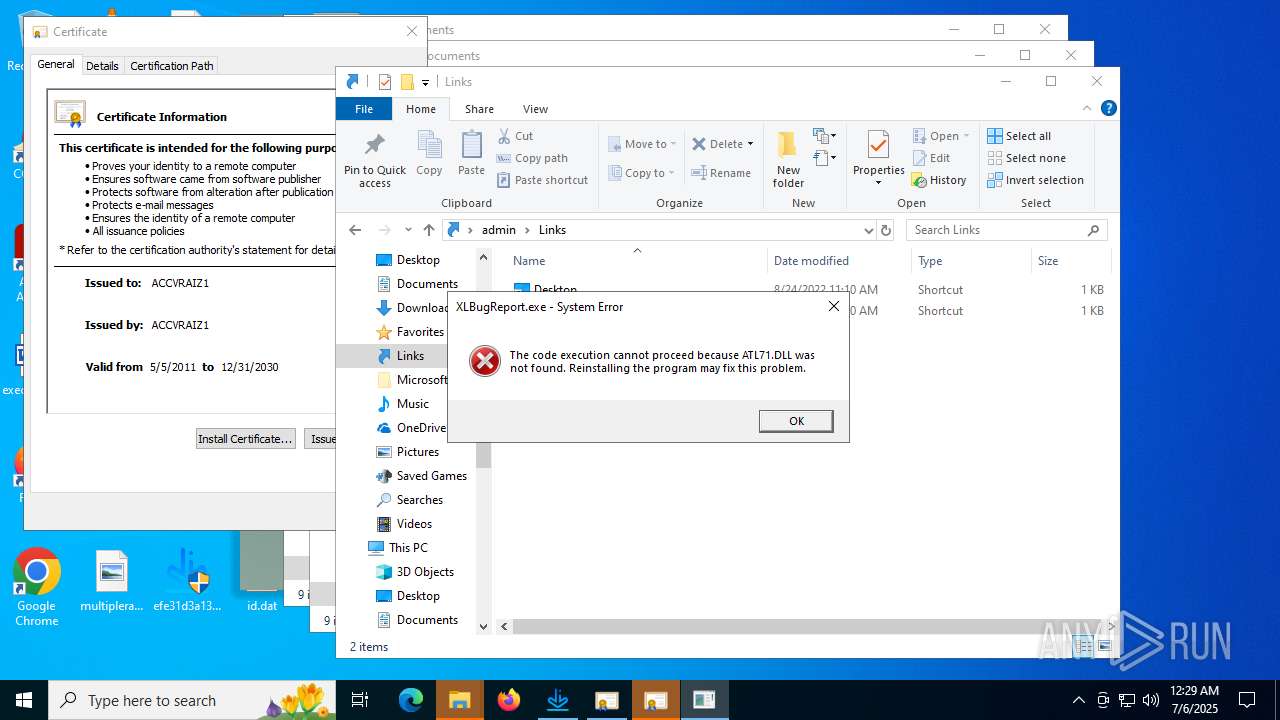
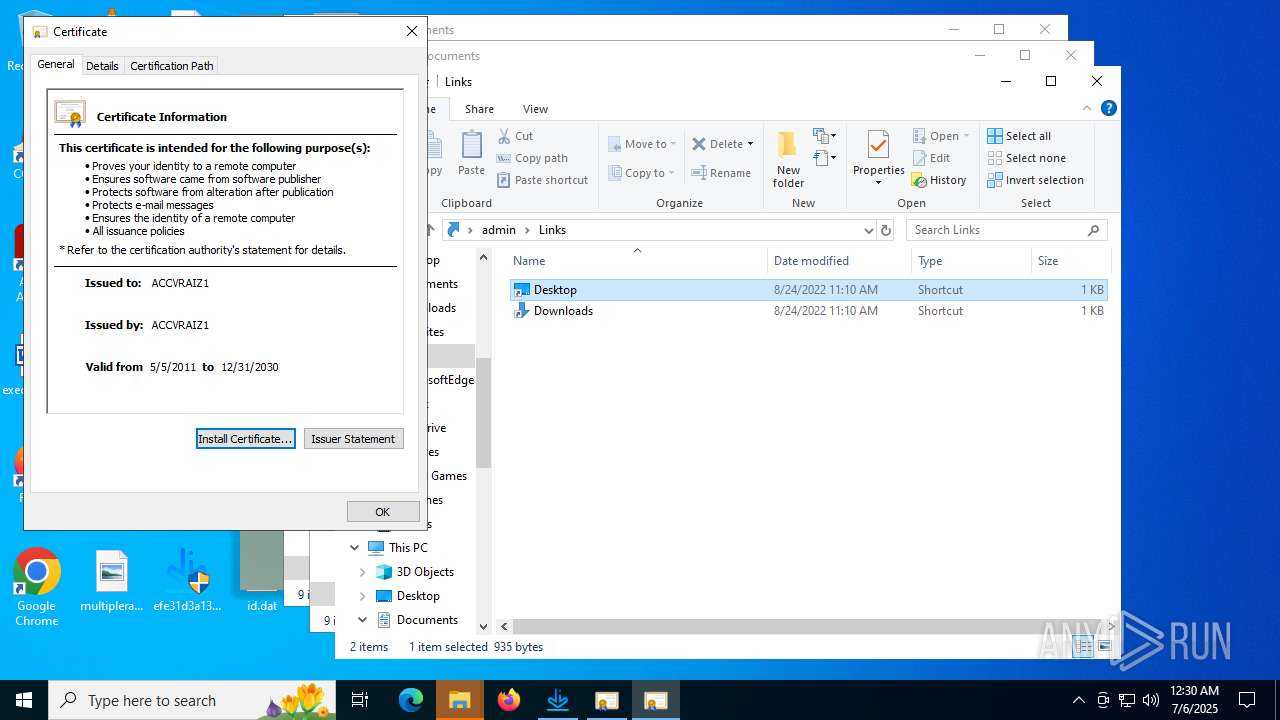
Executing a file with an untrusted certificate
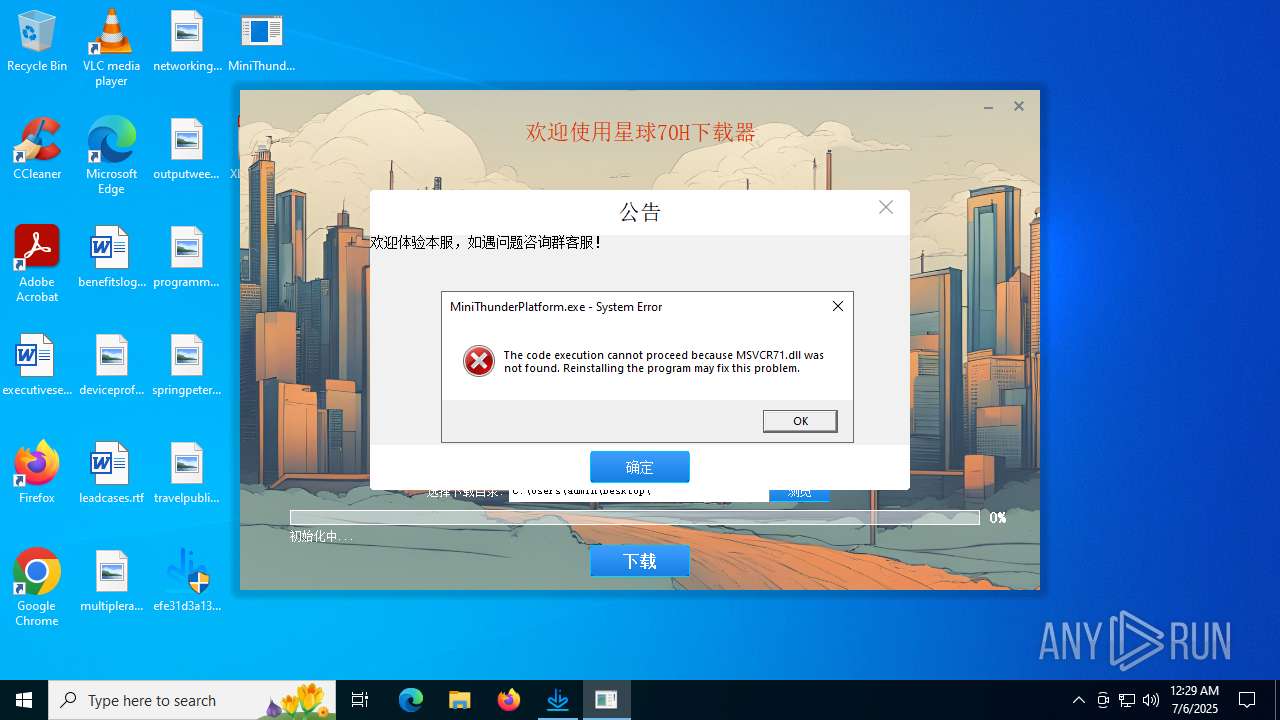
- MiniThunderPlatform.exe (PID: 5424)
- XLBugReport.exe (PID: 3608)
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
SUSPICIOUS
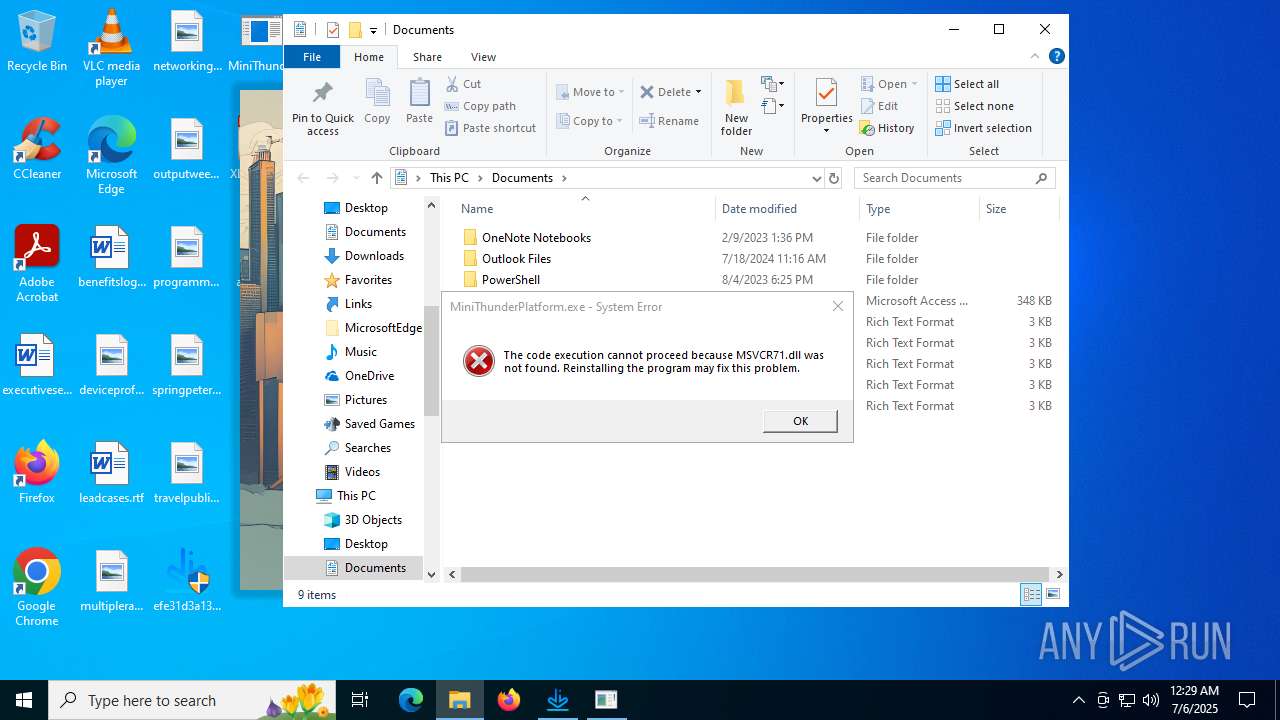
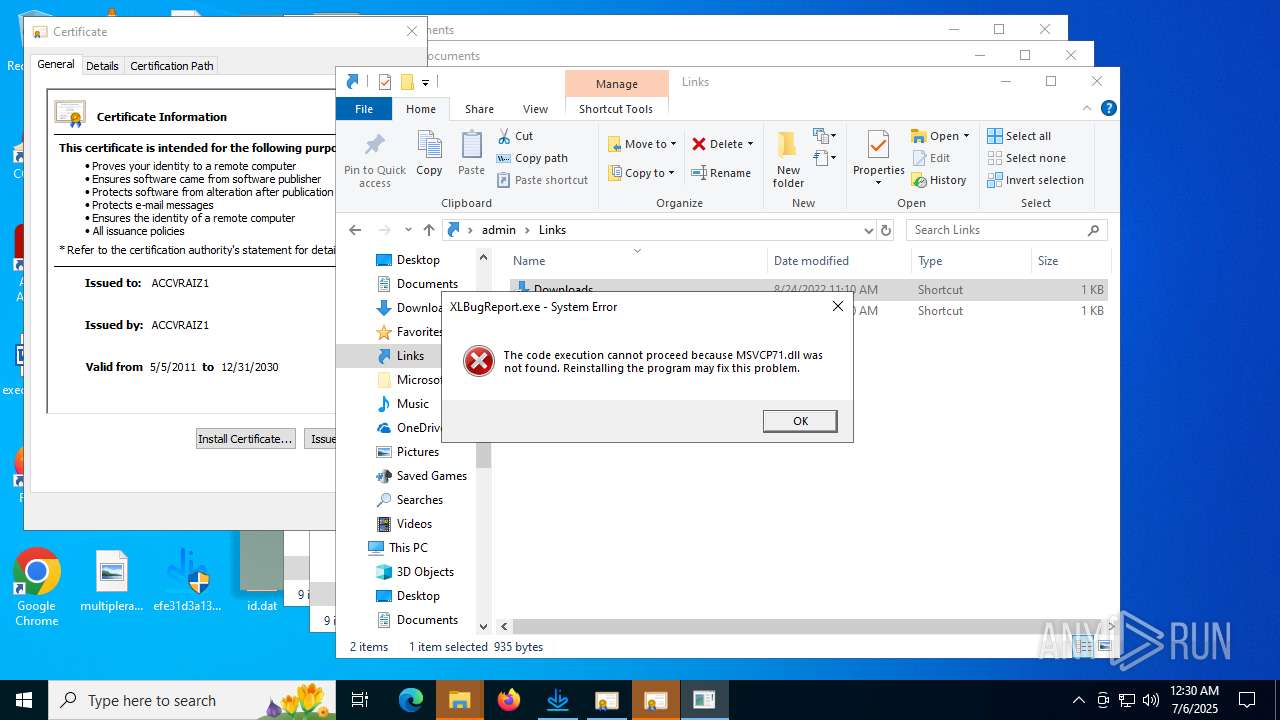
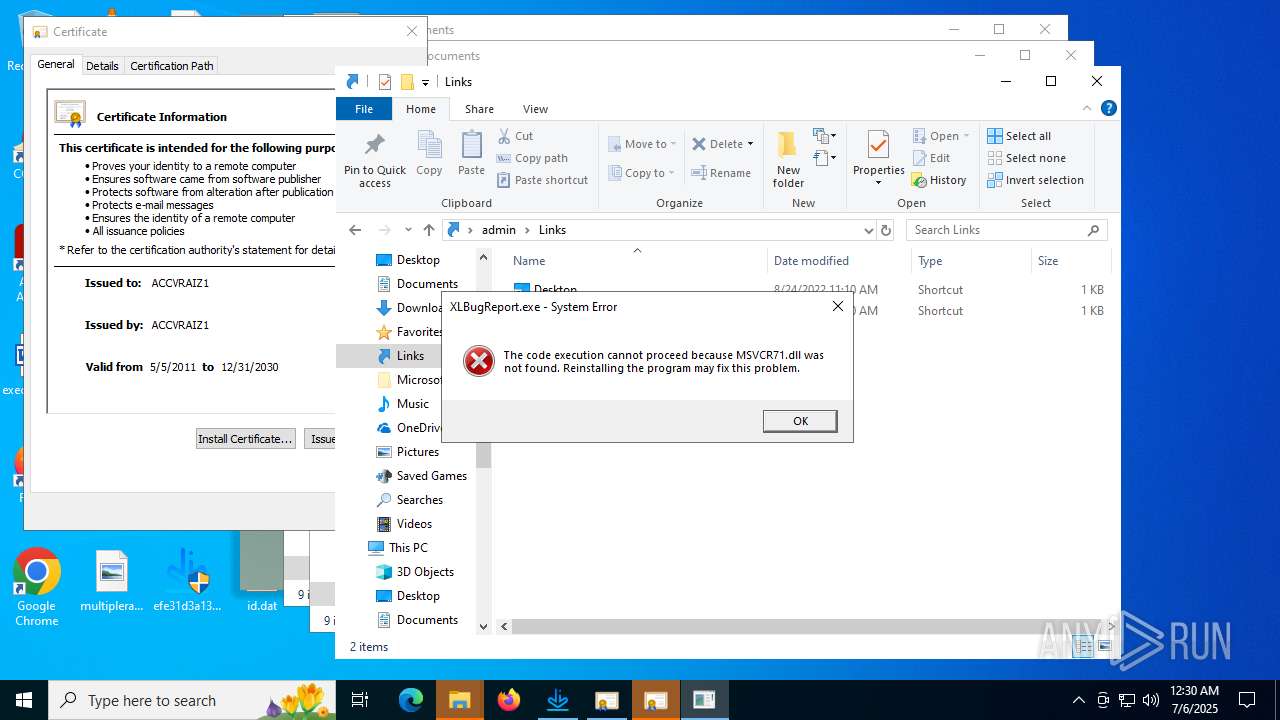
The process drops C-runtime libraries
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Drops 7-zip archiver for unpacking
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
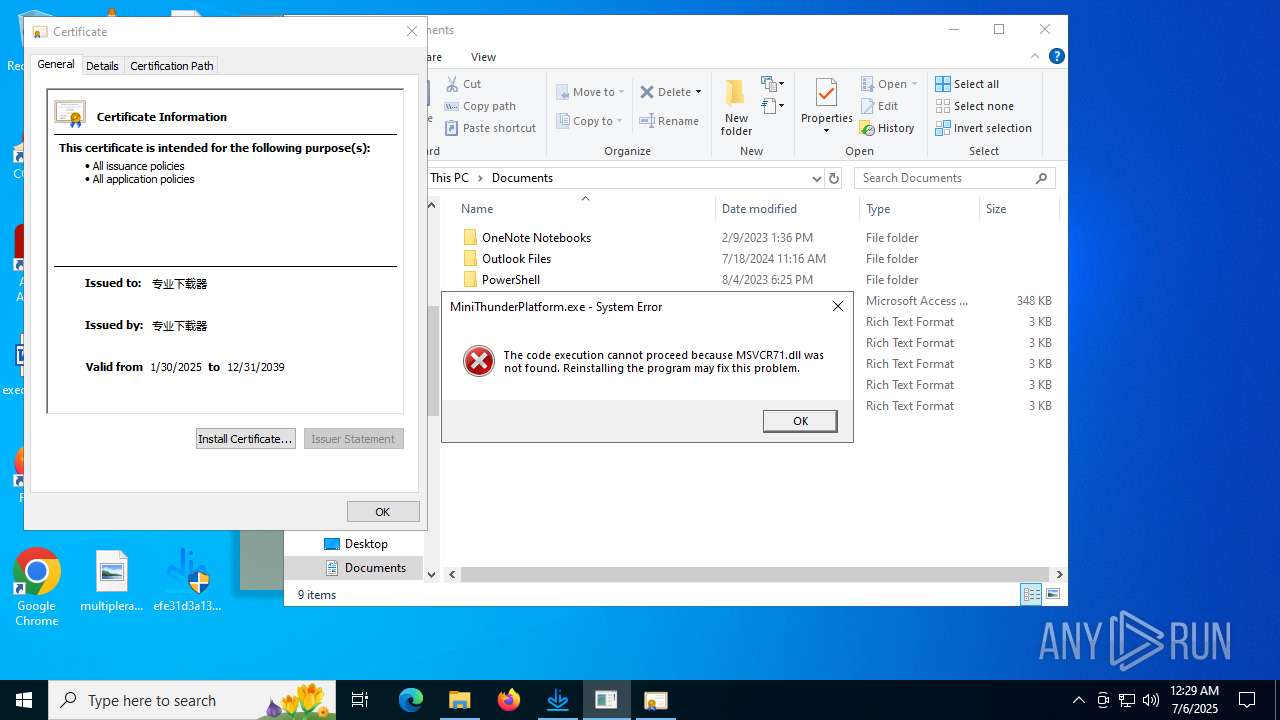
Adds/modifies Windows certificates
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
There is functionality for taking screenshot (YARA)
- XLBugReport.exe (PID: 3608)
Process drops legitimate windows executable
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Executable content was dropped or overwritten
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
INFO
The sample compiled with chinese language support
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Checks supported languages
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Reads the computer name
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Manual execution by a user
- XLBugReport.exe (PID: 3608)
- rundll32.exe (PID: 4080)
- rundll32.exe (PID: 5620)
- MiniThunderPlatform.exe (PID: 5424)
UPX packer has been detected
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Reads the software policy settings
- rundll32.exe (PID: 5620)
- rundll32.exe (PID: 4080)
- slui.exe (PID: 2716)
The sample compiled with english language support
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 5620)
- rundll32.exe (PID: 4080)
Checks proxy server information
- slui.exe (PID: 2716)
Creates files or folders in the user directory
- efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe (PID: 4380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (43.7) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (42.8) |
| .exe | | | Win32 Executable (generic) (7.1) |
| .exe | | | Generic Win/DOS Executable (3.1) |
| .exe | | | DOS Executable Generic (3.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:06:16 02:22:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 9334784 |
| InitializedDataSize: | 32768 |
| UninitializedDataSize: | 10735616 |
| EntryPoint: | 0x1324030 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileDescription: | 专业版Ver0.1.5 (731191) |
| FileVersion: | 1.0.0.1 |
| InternalName: | ConsoleA.exe |
| LegalCopyright: | Copyright (C) 2024 |
| OriginalFileName: | Pro |
| ProductName: | Downloader |
| ProductVersion: | 1.0.0.1 |
Total processes
140
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2128 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\Desktop\efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe" | C:\Users\admin\Desktop\efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 专业版Ver0.1.5 (731191) Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\Desktop\XLBugReport.exe" | C:\Users\admin\Desktop\XLBugReport.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 迅雷错误报告 Exit code: 3221225781 Version: 2, 2, 0, 12 Modules
| |||||||||||||||
| 4080 | "C:\WINDOWS\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Users\admin\Desktop\1.crt | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | "C:\Users\admin\Desktop\efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe" | C:\Users\admin\Desktop\efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 专业版Ver0.1.5 (731191) Version: 1.0.0.1 Modules
| |||||||||||||||
| 5424 | "C:\Users\admin\Desktop\MiniThunderPlatform.exe" | C:\Users\admin\Desktop\MiniThunderPlatform.exe | — | explorer.exe | |||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: MEDIUM Description: 迅雷云加速开放平台 Exit code: 3221225781 Version: 3.2.1.36 Modules
| |||||||||||||||
| 5620 | "C:\WINDOWS\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Users\admin\Desktop\I.cer | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 413
Read events
13 411
Write events
1
Delete events
1
Modification events
| (PID) Process: | (4380) efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | CC1C64DFEE39E07D053AC69522B1089D1C39749D |
Value: | |||
| (PID) Process: | (4380) efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\CC1C64DFEE39E07D053AC69522B1089D1C39749D |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000CC1C64DFEE39E07D053AC69522B1089D1C39749D2000000001000000FA020000308202F6308201E2A00302010202103F5BA01C60CBF1B2447D05F57975A021300906052B0E03021D050030153113301106035504031E0A4E134E1A4E0B8F7D5668301E170D3235303133303134343632375A170D3339313233313233353935395A30153113301106035504031E0A4E134E1A4E0B8F7D566830820122300D06092A864886F70D01010105000382010F003082010A0282010100D873B5208726FBF05B8CB6FD97393716300F9A4B787C20A516C4FE3A5A287947DD7FC65D5E7BF00D8864083D659A693CD0FB04159B7885846CECB46F7C743F2EB5880475E747C65548E3CAE7E823C7B856C640FE7C6AFAC6DDBD9B4CF5B25A27F414861C215093E0712A4E390FB59BAB81EDD129C9CEFAA183B4D0ABD6249B100095898E9F5D06990B58AED0C543A8F569B609FE99FD15288C702DF556F4C6BAF3AC4AF8E2732ADD63FE0B63EF02C4D640760A7C9F3D2CAC1E41451DD763494F26F5F2718F5E716D5F3FBC0A49E000A78516713450C44176DB44E373E344B4EFAFCE7496D9F0CE13F08499A2199A2778ECC0B7B85AA7A7AB54249D5C1BE2286D0203010001A34A304830460603551D01043F303D8010E1479FA279483823D8A9575BFE1C6863A11730153113301106035504031E0A4E134E1A4E0B8F7D566882103F5BA01C60CBF1B2447D05F57975A021300906052B0E03021D05000382010100BF07FE18F3E099C052A73A4F86AFD745E43206FB9FE76CC5352187DA37E43B6BAC4C5D1B721117B27EA27DF7E6C6F940A55163E5986EE1DCC44B02298D87C858CBFAF21B95A63FDB83C6A739AD2E575D03EE1DD1D661291ABDE70D8772133E19060FE179096997E71A6A338A403D31742AC998E251D4C5CF8C28D11D12440E85068EE8C811F07674AC3F1DE44382A00C91ECF3F16BE450CCC54CF9FC0E0E6B28DDD73D7FF3DB801BF1DC998757F0D8E13A35959BE0B85EC65CC357F124560016707703FC435F697471D189AEA5EE6F4F29F5CB7DCBDD16465C563EB9BDF442878DE1966419DD7BBE8A6FBE003A34DC25FF48E660CD698E94E1DA49FB4D0493FE | |||
Executable files
13
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\aria2.conf | text | |
MD5:C048DDD7E003849AE9DF1C5F5FCDA3AE | SHA256:30D9ABDBCB13554237A754A9679F29A8CEB7ECE575DF93A742F41F3E03E2F026 | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\dht6.dat | binary | |
MD5:E6EB369112210FD480587C81B65C6CFF | SHA256:63739D9E7F68106DAC0FDBAE5EECF5B02DDE21F1148A190356930D757CC6FC99 | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\dht.dat | binary | |
MD5:EB4B365F5FD4E6D01D1A485576685DE3 | SHA256:BACEAEE42B56A80161A3B0837208287321BDF4809D5AC1474DF4C44DAA6102CA | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Temp.zip | compressed | |
MD5:DACCB8279E7C774459CEB7A29029F8D6 | SHA256:FAA149503FD0FE0A8E3C936BFB511FE4A9435CDFF9DCBCEE1CE17AE6505AC257 | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\download\id.dat | text | |
MD5:2F1032A6C4978F87AAEF968AE9EA72CF | SHA256:EE56B138E5369281511528510ED6E94317A88EA26E4469BC60F562938013068E | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\download\atl71.dll | executable | |
MD5:79CB6457C81ADA9EB7F2087CE799AAA7 | SHA256:A68E1297FAE2BCF854B47FFA444F490353028DE1FA2CA713B6CF6CC5AA22B88A | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\download\MiniThunderPlatform.exe | executable | |
MD5:9F1D3DFAC55080C712C0281FB2EEEB47 | SHA256:A5622E2BF46CC2EC90C4DCA70372F051BFB5BF55DA3788B5DFCA9429529D285B | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\download\dl_peer_id.dll | executable | |
MD5:DBA9A19752B52943A0850A7E19AC600A | SHA256:69A5E2A51094DC8F30788D63243B12A0EB2759A3F3C3A159B85FD422FC00AC26 | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\download\msvcr71.dll | executable | |
MD5:CA2F560921B7B8BE1CF555A5A18D54C3 | SHA256:C4D4339DF314A27FF75A38967B7569D9962337B8D4CD4B0DB3ABA5FF72B2BFBB | |||
| 4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | C:\Users\admin\AppData\Roaming\Downloader_Por\download\msvcp71.dll | executable | |
MD5:A94DC60A90EFD7A35C36D971E3EE7470 | SHA256:6C483CBE349863C7DCF6F8CB7334E7D28C299E7D5AA063297EA2F62352F6BDD9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
20
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5172 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | POST | 200 | 1.56.98.184:80 | http://aria2c.vip/vc/SelectListOne.php | unknown | — | — | unknown |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5172 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5172 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5172 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4380 | efe31d3a135025bc8f8f5951a1fbace3586389f5b98f55ddeaf8c74c9d3d504b.exe | 1.56.98.184:80 | aria2c.vip | CHINA UNICOM China169 Backbone | CN | unknown |
5944 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
aria2c.vip |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |