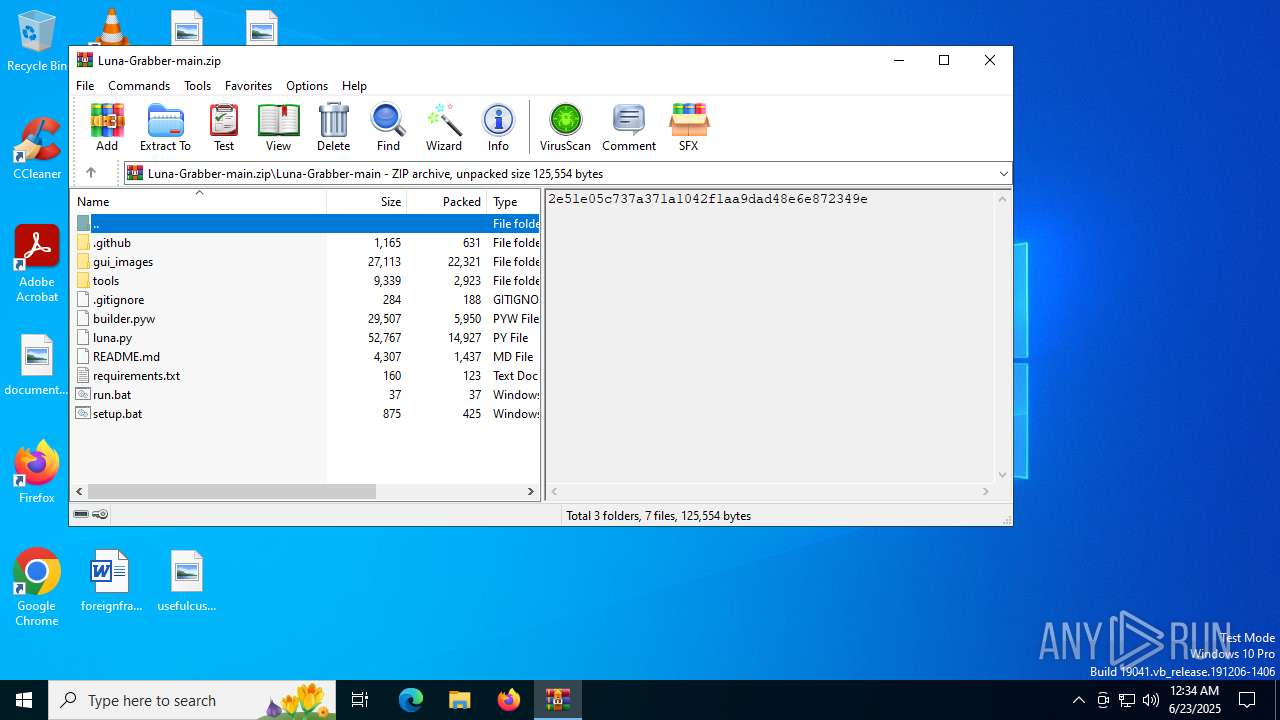
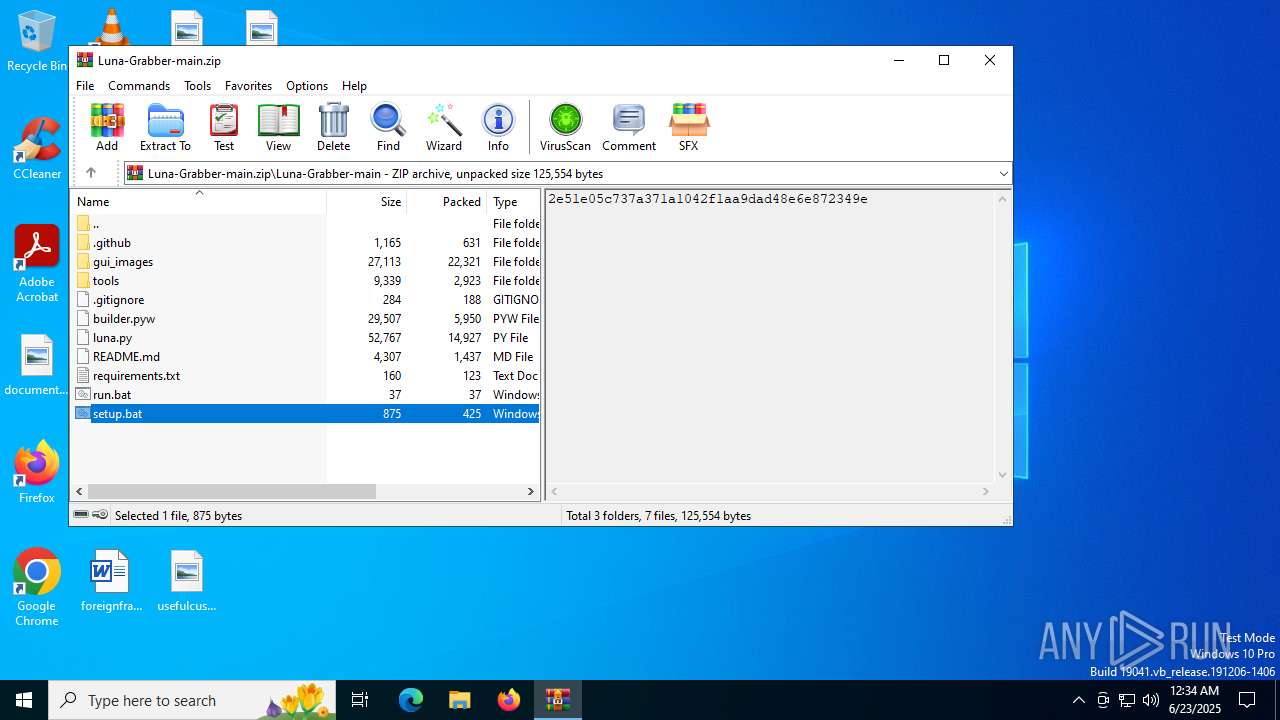
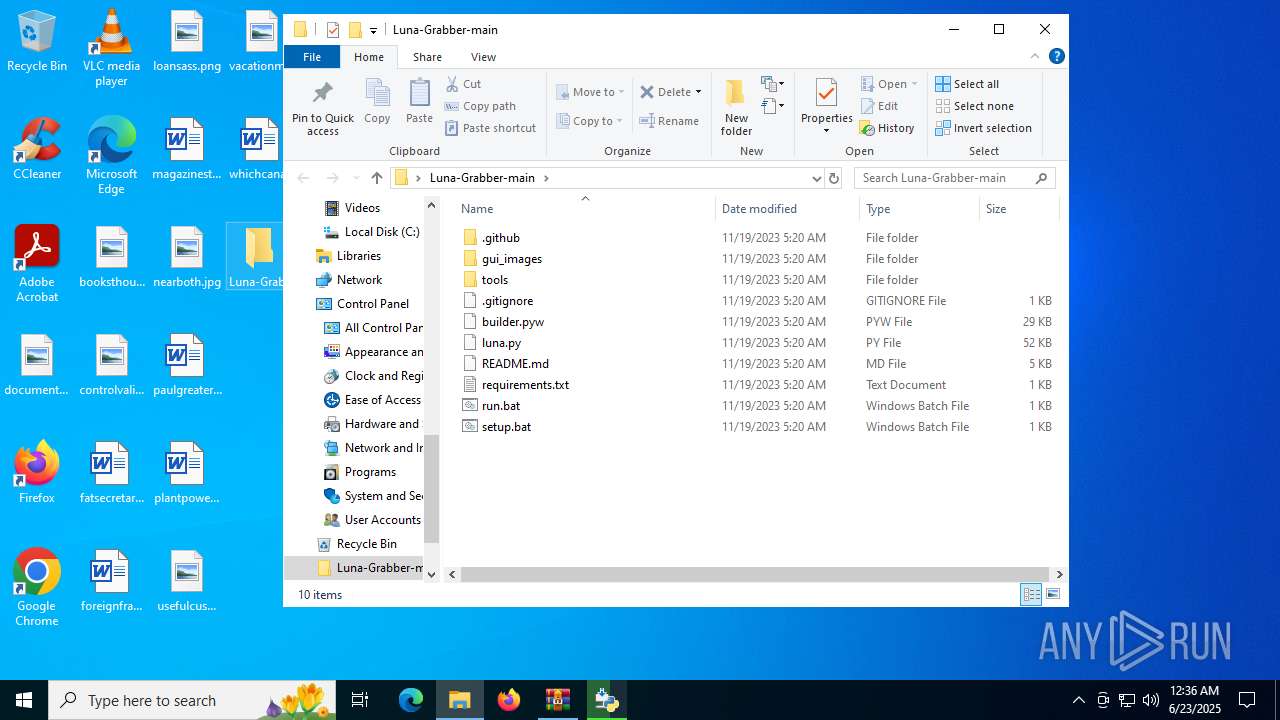
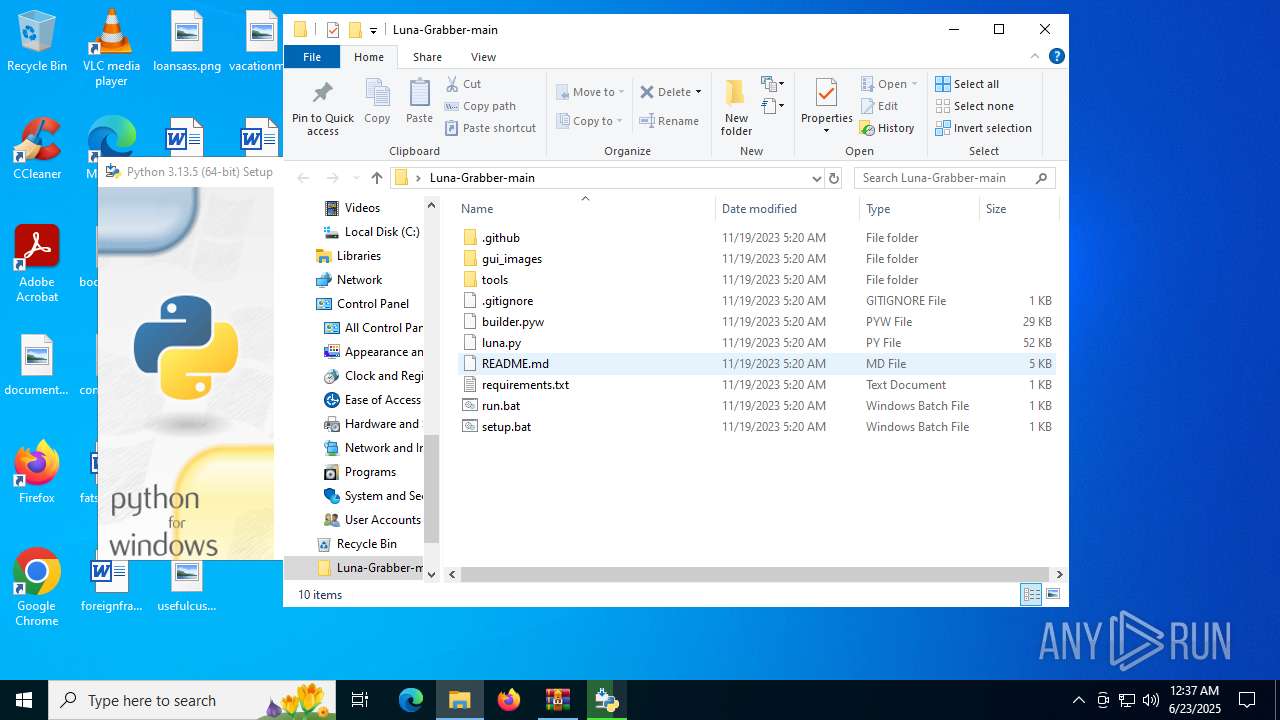
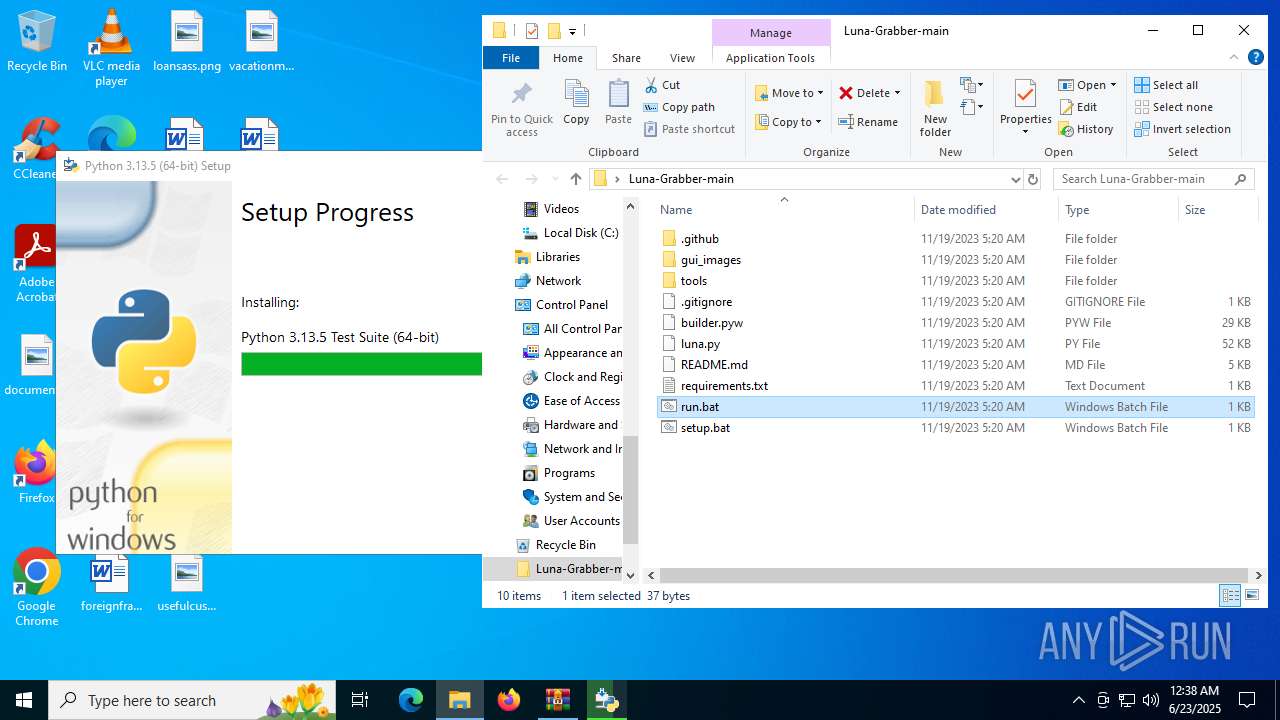
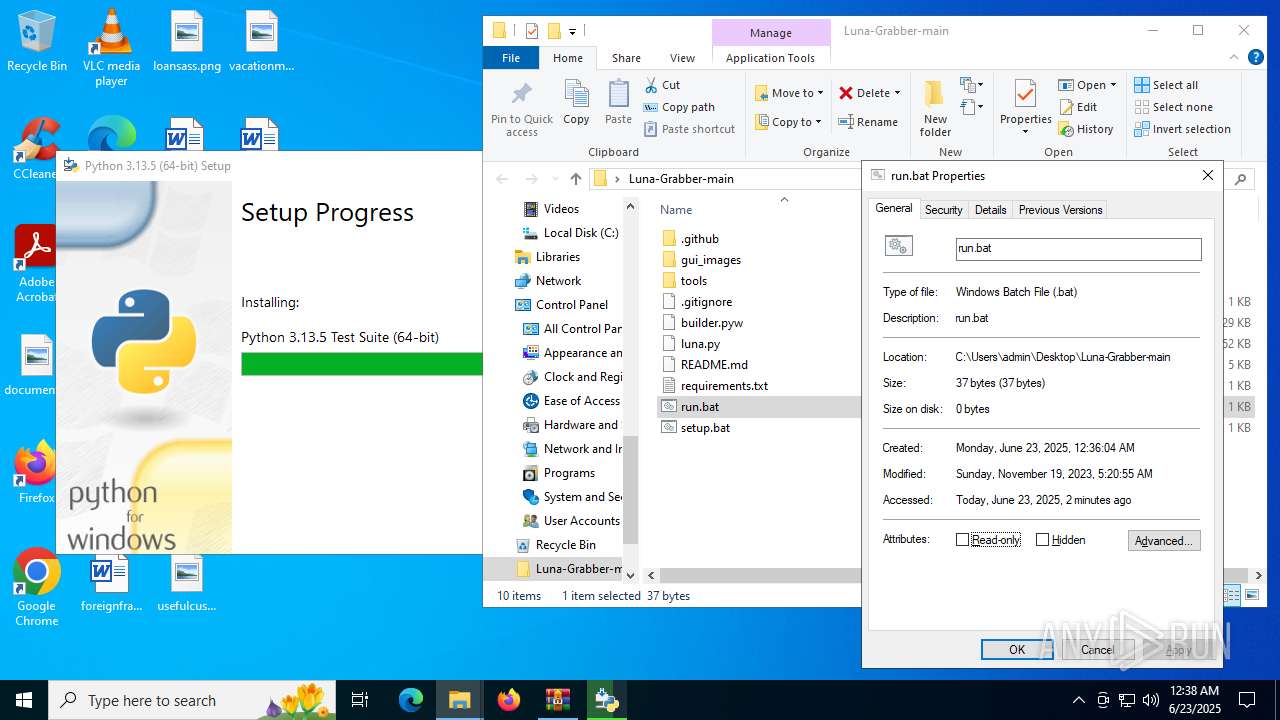
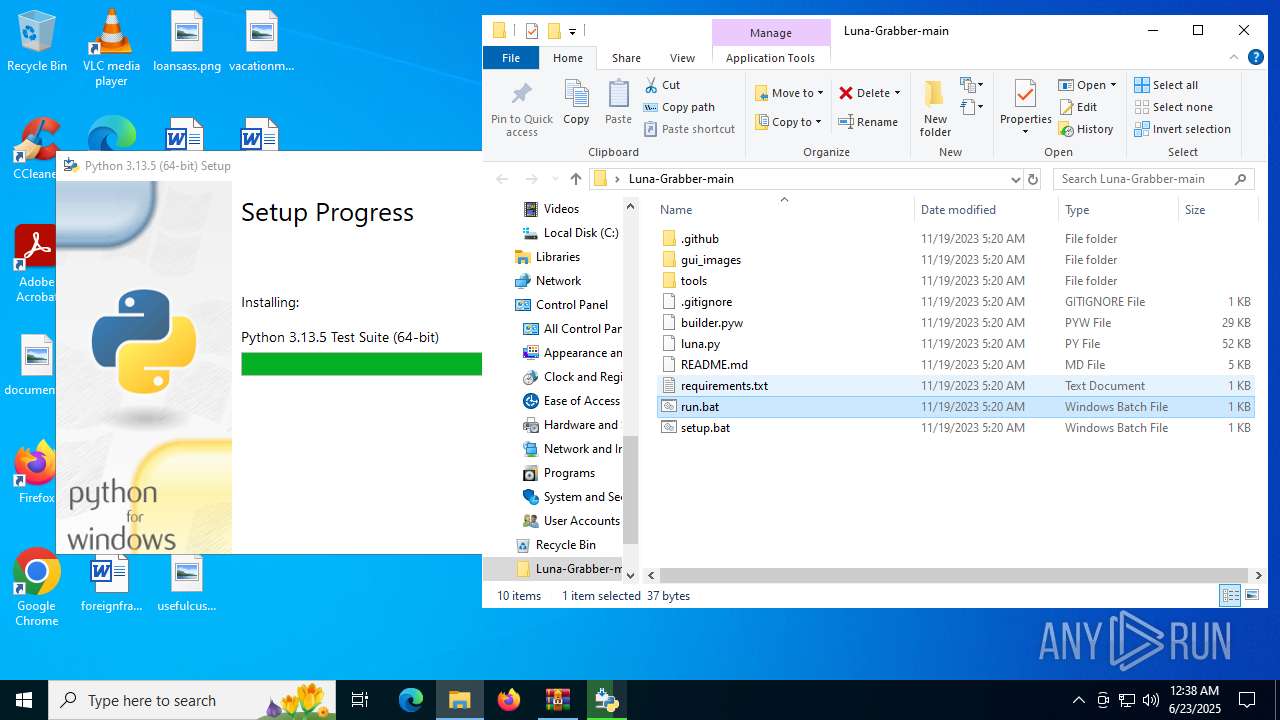
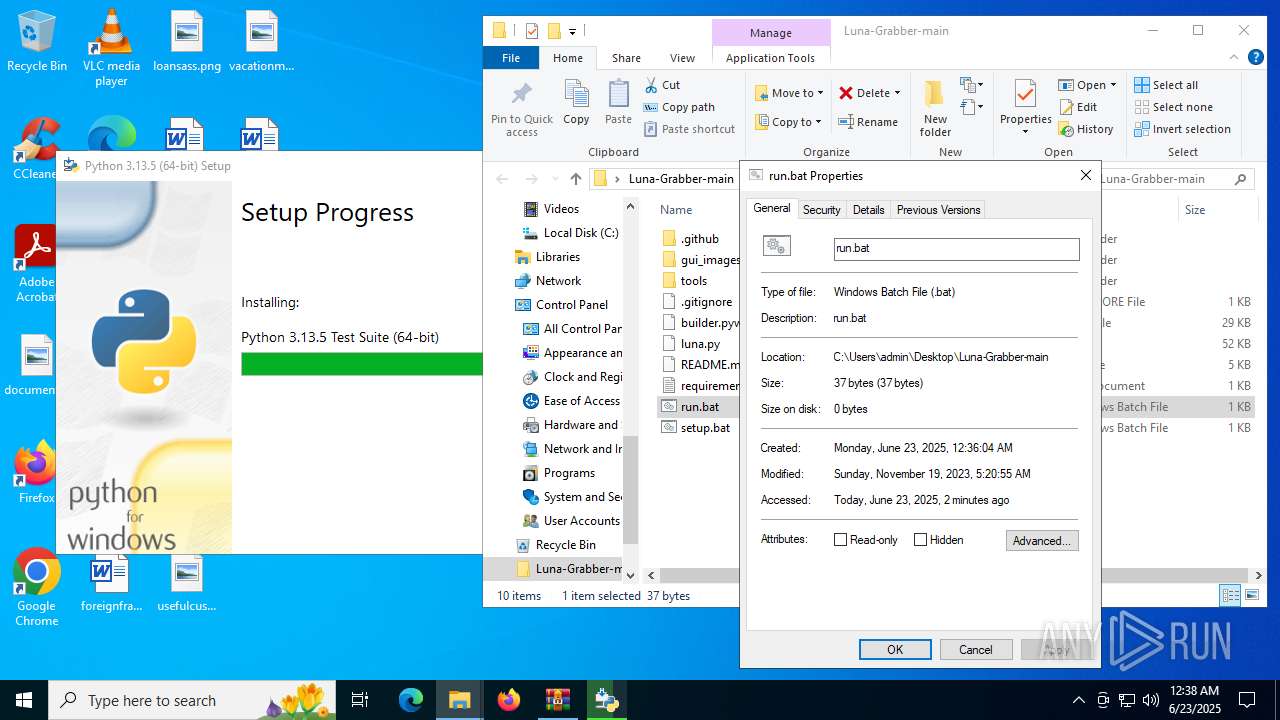
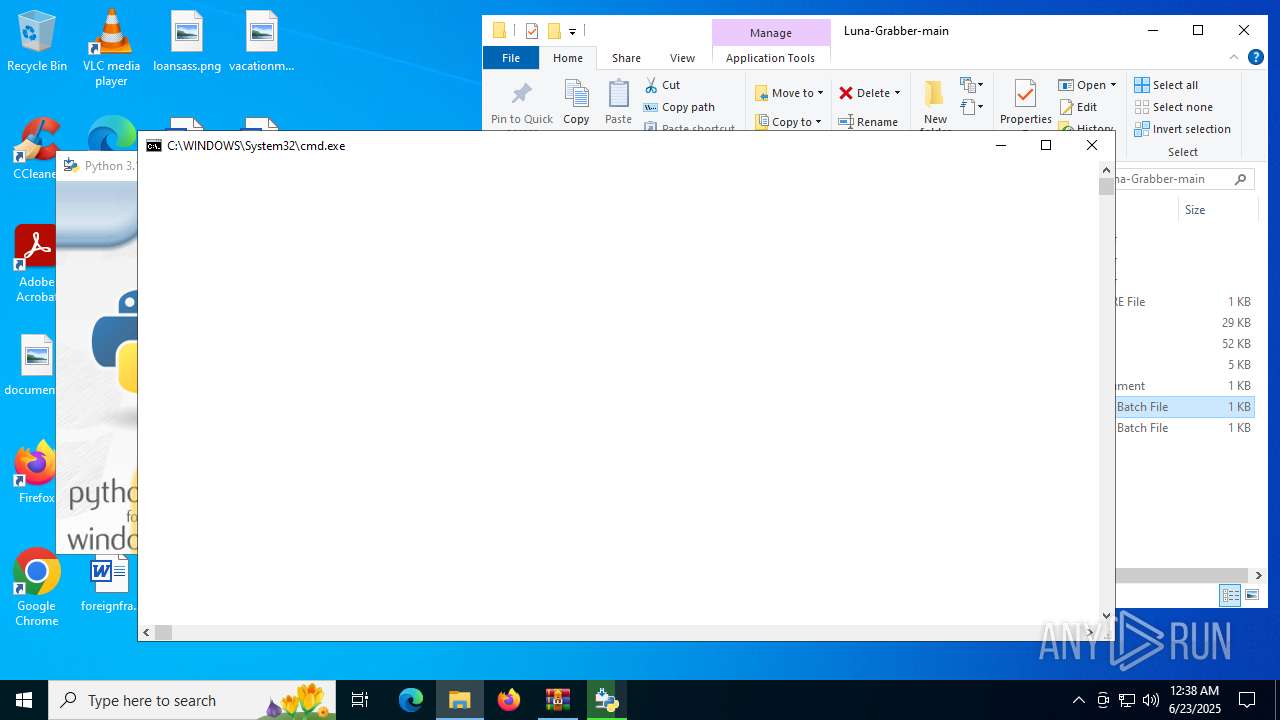
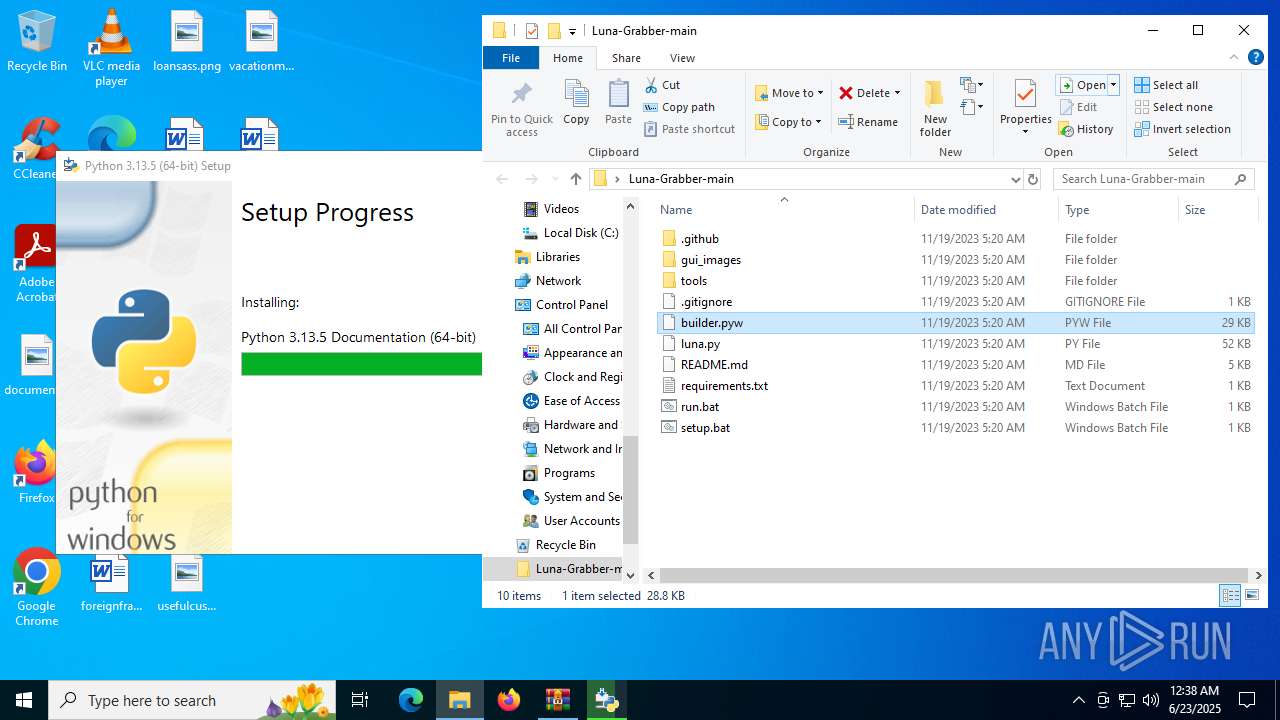
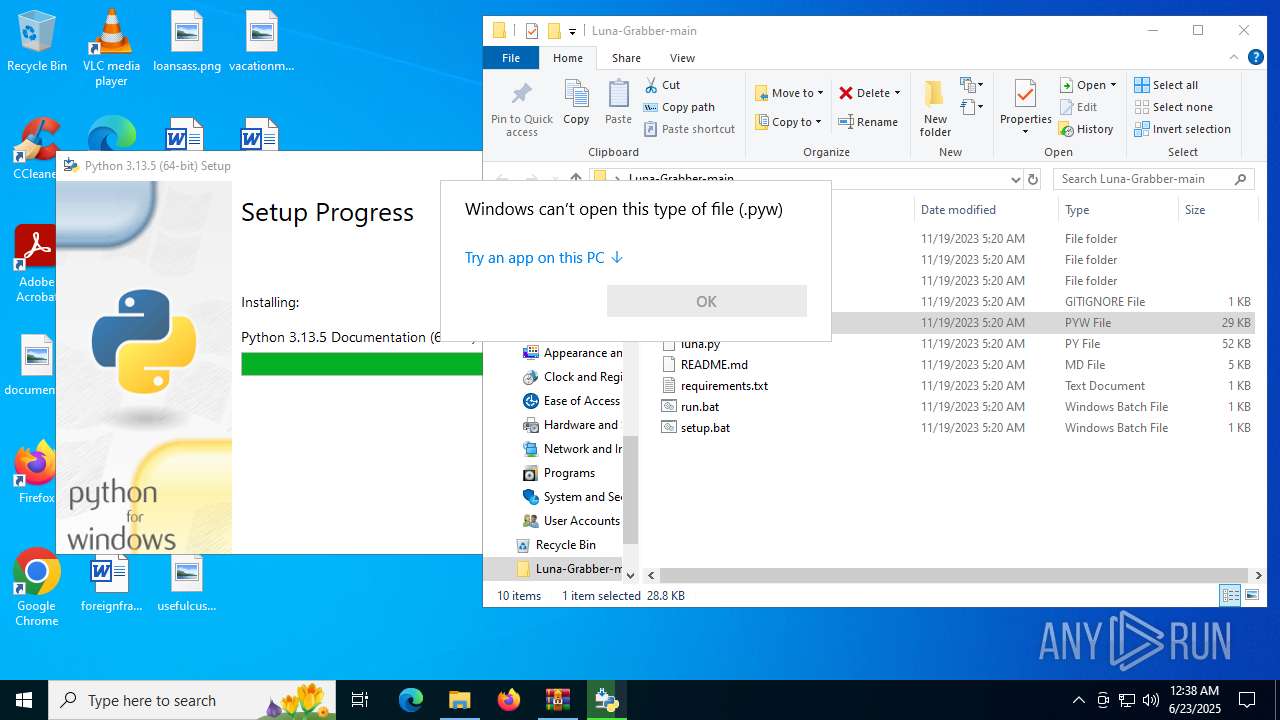
| File name: | Luna-Grabber-main.zip |
| Full analysis: | https://app.any.run/tasks/6acb2ee0-5b13-478f-95bc-a01723872cc8 |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2025, 00:34:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | F3342A6859DAA490327E041DB20AB632 |
| SHA1: | 2D31981CBD85CD8024B9D6C3D570781CC68EADBD |
| SHA256: | EFD91060235FFF7A51867562C35E4B897224EE793D42097EFFD08E5489CB0786 |
| SSDEEP: | 768:+cvm2KYSb02UGtE6yXApdiYrYsZ6o72zL/z7qbFMVRbnifGqTCbm5vE1QDQWz:+cvBFGvywAYrRgz7GFMVdni/xxWQDJ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4216)
Changes the autorun value in the registry
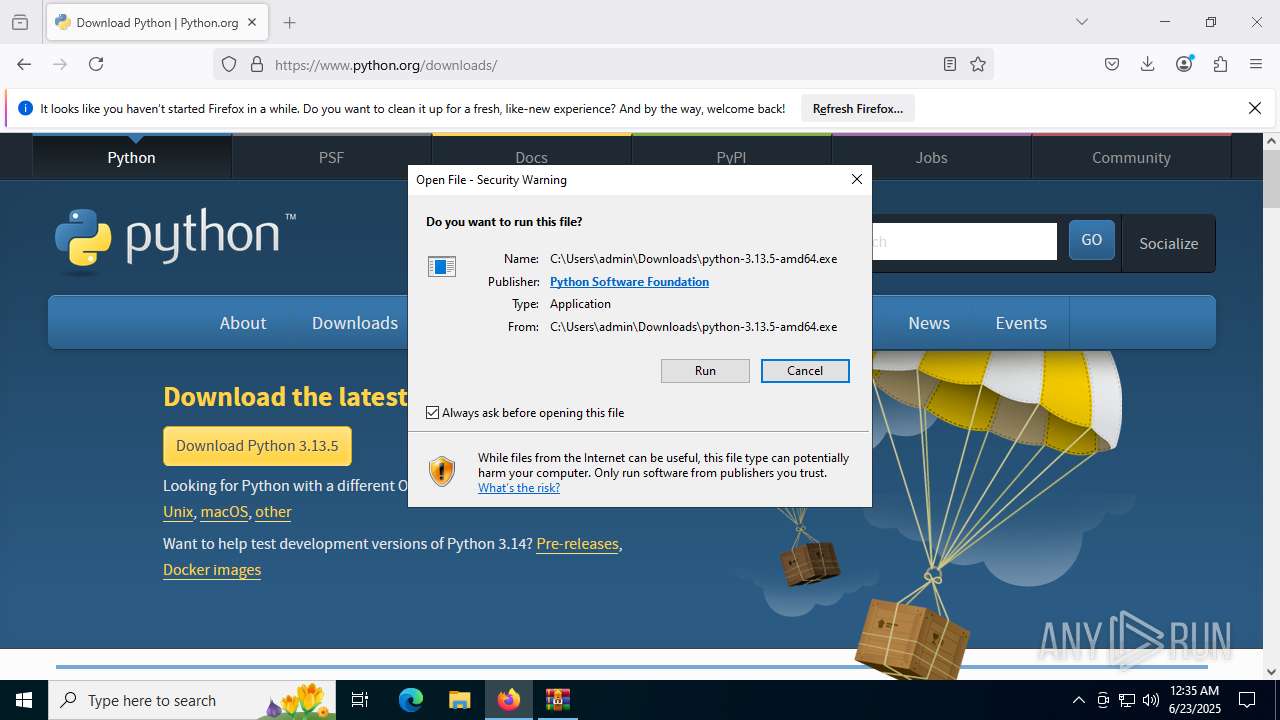
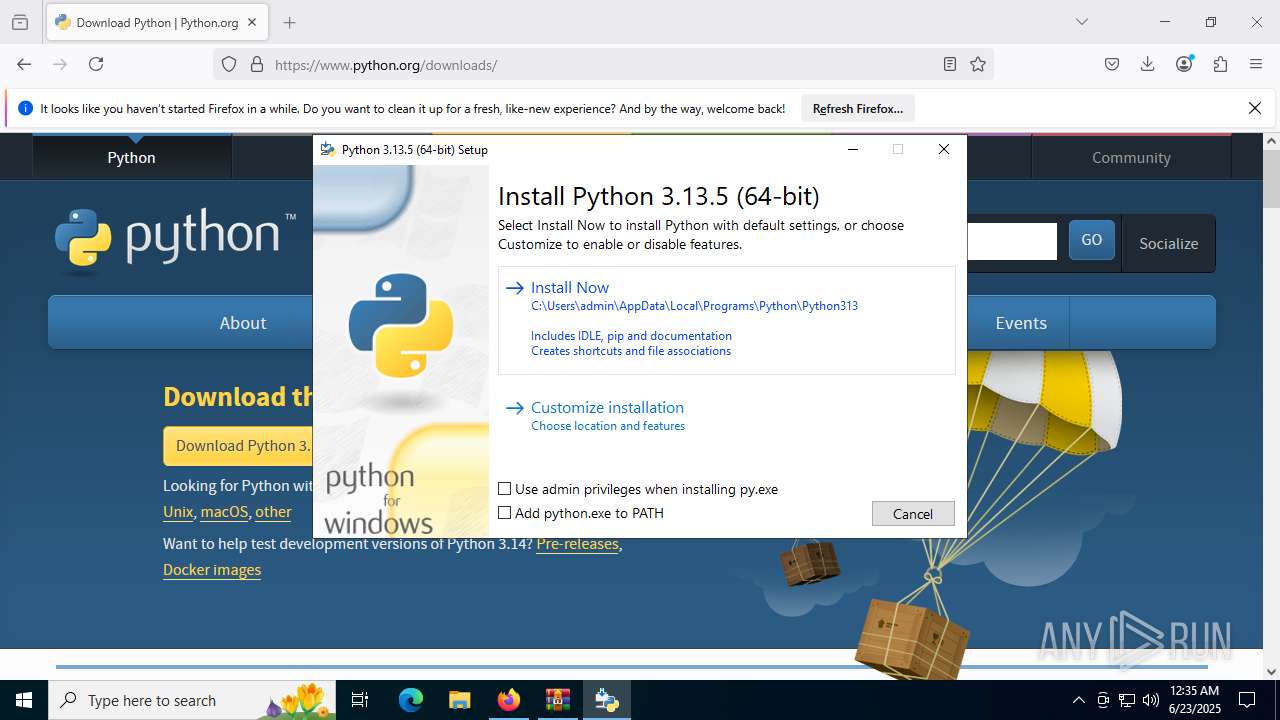
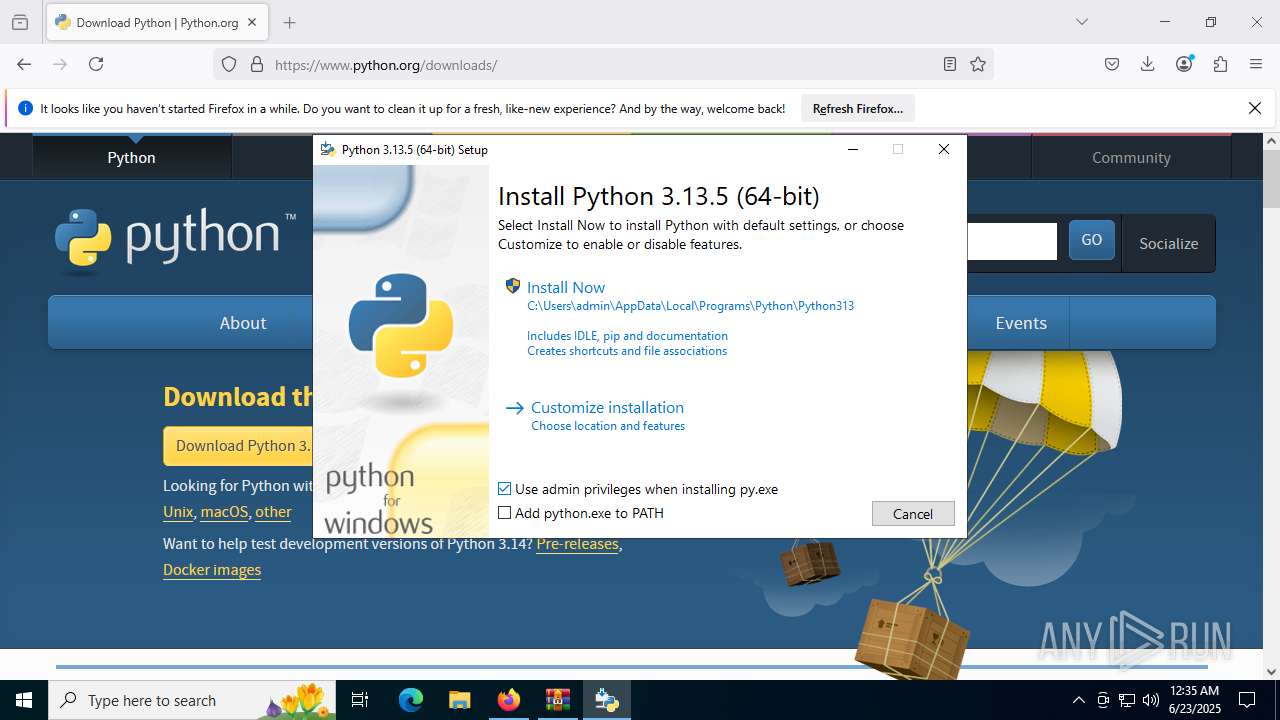
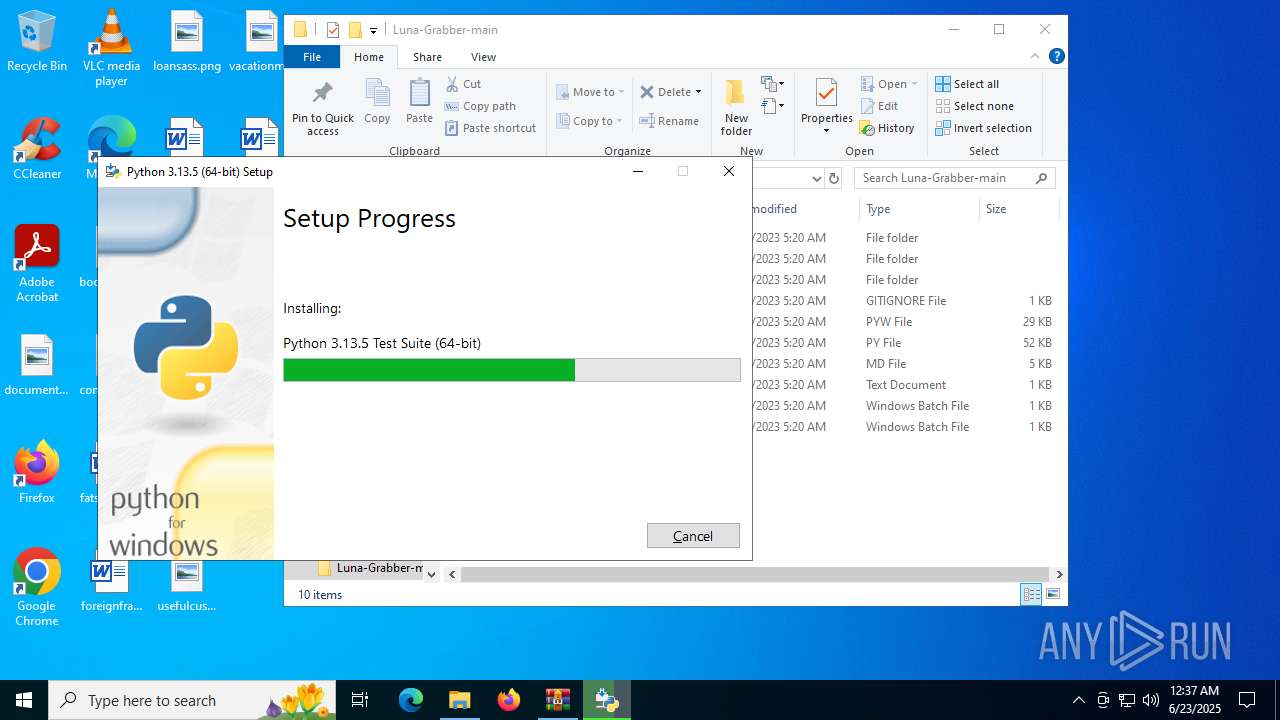
- python-3.13.5-amd64.exe (PID: 7664)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4216)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4216)
- python-3.13.5-amd64.exe (PID: 7664)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4216)
Executable content was dropped or overwritten
- python-3.13.5-amd64.exe (PID: 7640)
- python-3.13.5-amd64.exe (PID: 7664)
- python-3.13.5-amd64.exe (PID: 7960)
Searches for installed software
- python-3.13.5-amd64.exe (PID: 7664)
- dllhost.exe (PID: 8052)
Starts itself from another location
- python-3.13.5-amd64.exe (PID: 7664)
Executes as Windows Service
- VSSVC.exe (PID: 7296)
Process drops legitimate windows executable
- python-3.13.5-amd64.exe (PID: 7664)
- msiexec.exe (PID: 7412)
Creates a software uninstall entry
- python-3.13.5-amd64.exe (PID: 7664)
The process drops C-runtime libraries
- python-3.13.5-amd64.exe (PID: 7664)
- msiexec.exe (PID: 7412)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7412)
There is functionality for taking screenshot (YARA)
- python-3.13.5-amd64.exe (PID: 7664)
Process drops python dynamic module
- msiexec.exe (PID: 7412)
INFO
Application launched itself
- firefox.exe (PID: 4860)
- firefox.exe (PID: 3668)
- firefox.exe (PID: 2792)
- firefox.exe (PID: 6256)
Reads Microsoft Office registry keys
- firefox.exe (PID: 3668)
- firefox.exe (PID: 6256)
- OpenWith.exe (PID: 4828)
- OpenWith.exe (PID: 3644)
Launching a file from the Downloads directory
- firefox.exe (PID: 3668)
Manual execution by a user
- firefox.exe (PID: 4860)
- cmd.exe (PID: 7048)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 2040)
- firefox.exe (PID: 2792)
Executable content was dropped or overwritten
- firefox.exe (PID: 3668)
- msiexec.exe (PID: 7412)
Checks supported languages
- python-3.13.5-amd64.exe (PID: 7640)
- python-3.13.5-amd64.exe (PID: 7664)
- python-3.13.5-amd64.exe (PID: 7960)
- msiexec.exe (PID: 7412)
The sample compiled with english language support
- python-3.13.5-amd64.exe (PID: 7640)
- python-3.13.5-amd64.exe (PID: 7664)
- firefox.exe (PID: 3668)
- msiexec.exe (PID: 7412)
Reads the computer name
- python-3.13.5-amd64.exe (PID: 7664)
- python-3.13.5-amd64.exe (PID: 7960)
- msiexec.exe (PID: 7412)
Create files in a temporary directory
- python-3.13.5-amd64.exe (PID: 7640)
- python-3.13.5-amd64.exe (PID: 7664)
Process checks computer location settings
- python-3.13.5-amd64.exe (PID: 7664)
Creates files or folders in the user directory
- python-3.13.5-amd64.exe (PID: 7664)
- msiexec.exe (PID: 7412)
Manages system restore points
- SrTasks.exe (PID: 7200)
Launching a file from a Registry key
- python-3.13.5-amd64.exe (PID: 7664)
Reads the machine GUID from the registry
- python-3.13.5-amd64.exe (PID: 7664)
- python-3.13.5-amd64.exe (PID: 7960)
- msiexec.exe (PID: 7412)
Creates files in the program directory
- python-3.13.5-amd64.exe (PID: 7960)
Reads the software policy settings
- msiexec.exe (PID: 7412)
- slui.exe (PID: 7524)
Creates a software uninstall entry
- msiexec.exe (PID: 7412)
Checks proxy server information
- slui.exe (PID: 7524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:11:18 21:20:54 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Luna-Grabber-main/ |
Total processes
204
Monitored processes
52
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4776 -prefsLen 39120 -prefMapHandle 4756 -prefMapSize 273053 -jsInitHandle 4760 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 4728 -initialChannelId {dbfc416e-dbde-4e5f-b943-7c0ff3df664a} -parentPid 6256 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6256" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 7 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Luna-Grabber-main\run.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 3332 -prefsLen 36996 -prefMapHandle 3336 -prefMapSize 272997 -ipcHandle 3344 -initialChannelId {b5fd10ed-8e34-43da-bf18-b9111bbbdfff} -parentPid 3668 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3668" -appDir "C:\Program Files\Mozilla Firefox\browser" - 4 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 136.0 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5032 -prefsLen 39068 -prefMapHandle 5036 -prefMapSize 272997 -jsInitHandle 5040 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5048 -initialChannelId {80a58230-ad45-4862-aeaa-060e3d06727a} -parentPid 3668 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3668" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 8 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 3372 -prefsLen 37058 -prefMapHandle 3376 -prefMapSize 273053 -ipcHandle 3380 -initialChannelId {ed0a179a-d122-49e1-92a8-5992e58b6011} -parentPid 6256 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6256" -appDir "C:\Program Files\Mozilla Firefox\browser" - 4 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 136.0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5224 -prefsLen 39120 -prefMapHandle 5228 -prefMapSize 273053 -jsInitHandle 5232 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 4924 -initialChannelId {54cafa6c-1413-42fd-9e88-73ca77bfe365} -parentPid 6256 -crashReporter "\\.\pipe\gecko-crash-server-pipe.6256" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 8 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 3092 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 320
Read events
62 914
Write events
5 321
Delete events
85
Modification events
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Luna-Grabber-main.zip | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4216) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3668) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3668) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
88
Suspicious files
611
Text files
3 323
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:1D171451E94C1F8270F045ACC378B89E | SHA256:CA3F4863A1B087C1415621C667EC112A5563DBD4C81BD9B3A62BD67335344FEE | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4216 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4216.19868\setup.bat | text | |
MD5:EAD06886429F30C957D5C0ABEFC5E697 | SHA256:050A503DAACE1BC5D438BCC7F9A45D5B21828F74880AF100AE2B0293AF2F6401 | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:3134ED3F12E4F4F8643DB90043B0FD7B | SHA256:26E4F122034D7A03F6DA0E707799B09CBEEBDAF8D7A3133A1F7BD894AC72EEA1 | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:60C7BC55E67F7809EA3E676699B04486 | SHA256:4C17E9CCC742C84E21B054E4969EEC00E4DB43CE439E44B52DD5CEAA22ACC88D | |||
| 3668 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
163
DNS requests
210
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2288 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3668 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3668 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
3668 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
3668 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
3668 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
3668 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
3668 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
3668 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3956 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2288 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2288 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |