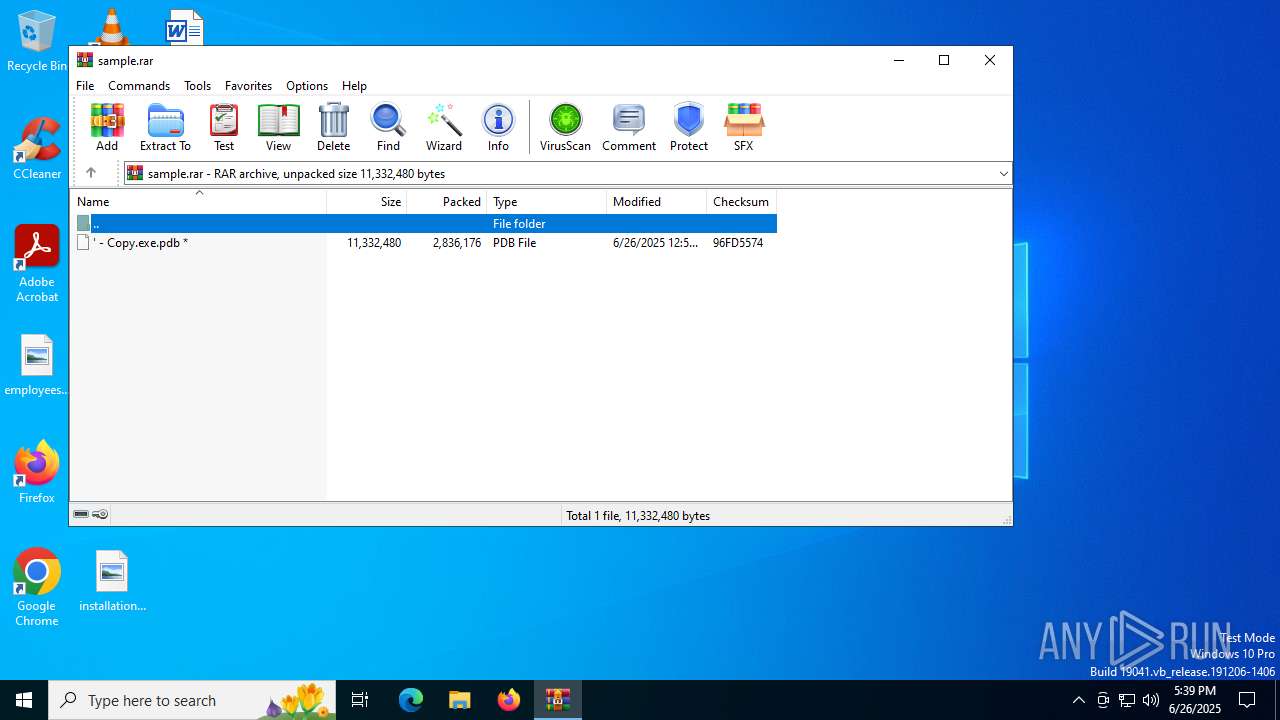
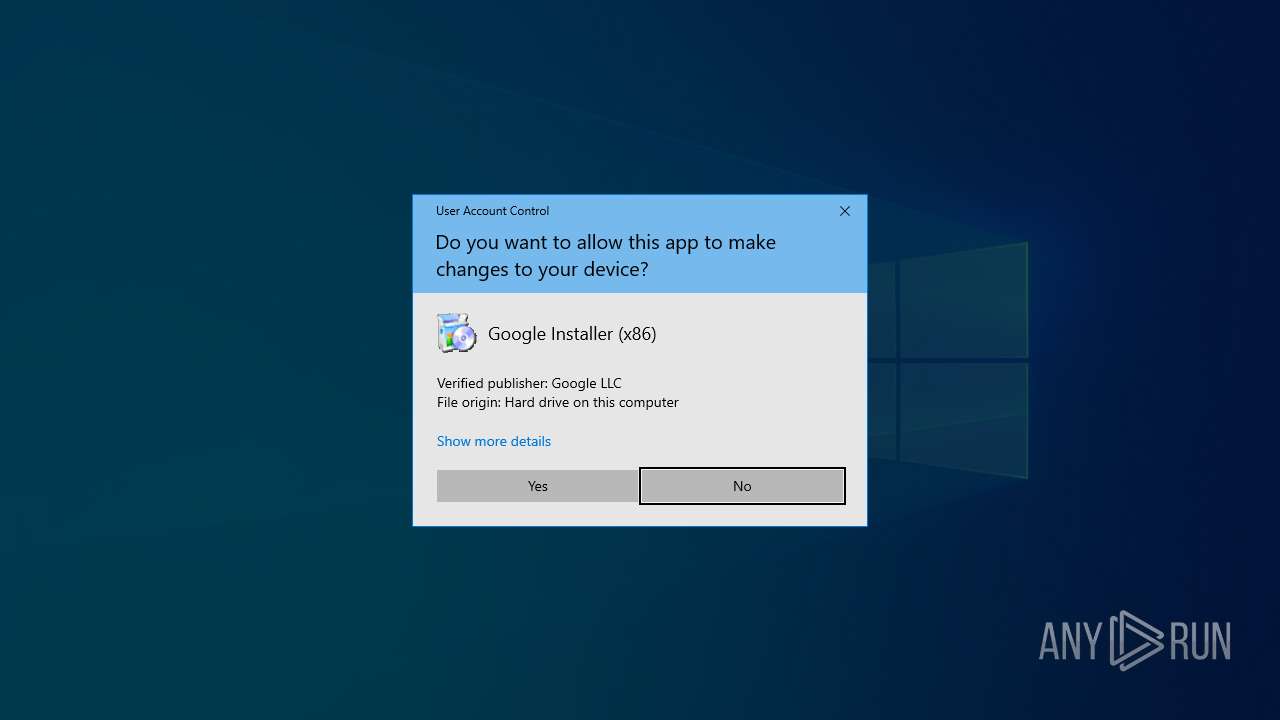
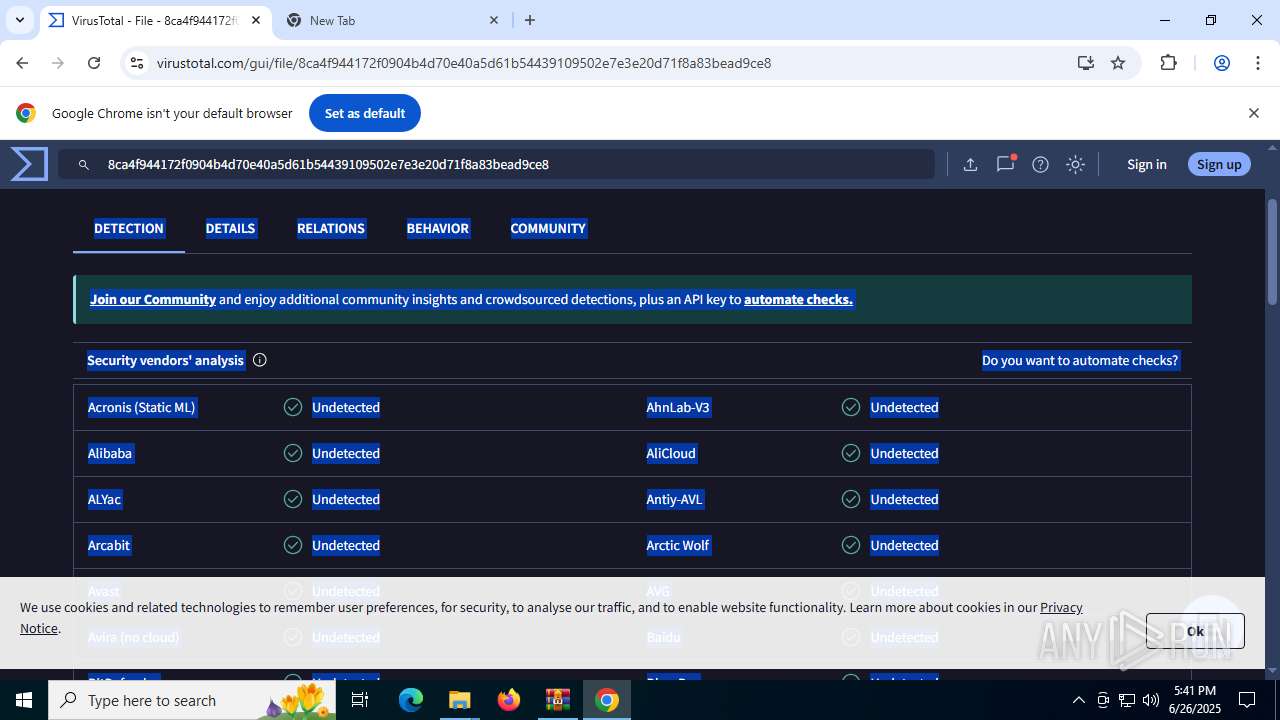
| File name: | sample.rar |
| Full analysis: | https://app.any.run/tasks/e033928c-2441-4555-a2e9-0c106b4dbc55 |
| Verdict: | Malicious activity |
| Analysis date: | June 26, 2025, 17:39:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 123107B0D88F3367F3F0F2B89D251F84 |
| SHA1: | DBADEB52C4E9D28F1B39213C7375D03F5289CDA6 |
| SHA256: | EFAEF9DCADAEDE1736BFF6D7C4101F1630BF7860322FA6FBC3CF2E1A5AA24EAA |
| SSDEEP: | 98304:6Fd7ekLdbjFE4uO7TjtC9aDPgHBUkPv3u1xlsZaYRahTmFcLkDRfbPqfr2foJ29Q:lkKcIKC9o5 |
MALICIOUS
Changes the autorun value in the registry
- setup.exe (PID: 7752)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 4772)
- updater.exe (PID: 2140)
- updater.exe (PID: 2160)
- setup.exe (PID: 7752)
- 137.0.7151.122_chrome_installer_uncompressed.exe (PID: 3864)
Reads security settings of Internet Explorer
- ' - Copy.exe (PID: 6380)
- updater.exe (PID: 2140)
Application launched itself
- ' - Copy.exe (PID: 6380)
- updater.exe (PID: 2140)
- updater.exe (PID: 2648)
- updater.exe (PID: 2160)
- setup.exe (PID: 7752)
- setup.exe (PID: 7880)
- updater.exe (PID: 7312)
- updater.exe (PID: 2448)
Executes as Windows Service
- updater.exe (PID: 2160)
- updater.exe (PID: 2648)
- updater.exe (PID: 7312)
- updater.exe (PID: 2448)
Creates file in the systems drive root
- explorer.exe (PID: 4772)
Searches for installed software
- setup.exe (PID: 7752)
Creates a software uninstall entry
- setup.exe (PID: 7752)
INFO
Manual execution by a user
- ' - Copy.exe (PID: 6380)
- firefox.exe (PID: 4748)
- chrome.exe (PID: 7984)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2356)
- chrome.exe (PID: 1324)
Checks supported languages
- ' - Copy.exe (PID: 6380)
- ' - Copy.exe (PID: 4844)
- updater.exe (PID: 2220)
- updater.exe (PID: 2140)
- updater.exe (PID: 2160)
- updater.exe (PID: 3720)
- updater.exe (PID: 2648)
- updater.exe (PID: 7116)
- 137.0.7151.122_chrome_installer_uncompressed.exe (PID: 3864)
- setup.exe (PID: 7780)
- setup.exe (PID: 7880)
- setup.exe (PID: 7900)
- setup.exe (PID: 7752)
- elevation_service.exe (PID: 7540)
- updater.exe (PID: 6980)
- updater.exe (PID: 7312)
- updater.exe (PID: 2448)
- updater.exe (PID: 1128)
Reads the computer name
- ' - Copy.exe (PID: 6380)
- ' - Copy.exe (PID: 4844)
- updater.exe (PID: 2140)
- updater.exe (PID: 2160)
- updater.exe (PID: 2648)
- setup.exe (PID: 7752)
- setup.exe (PID: 7880)
- 137.0.7151.122_chrome_installer_uncompressed.exe (PID: 3864)
- elevation_service.exe (PID: 7540)
- updater.exe (PID: 7312)
- updater.exe (PID: 2448)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
Process checks computer location settings
- ' - Copy.exe (PID: 6380)
Create files in a temporary directory
- ' - Copy.exe (PID: 4844)
- updater.exe (PID: 2140)
Creates files in the program directory
- updater.exe (PID: 2220)
- updater.exe (PID: 2140)
- updater.exe (PID: 2160)
- updater.exe (PID: 2648)
- setup.exe (PID: 7752)
- setup.exe (PID: 7880)
- updater.exe (PID: 7312)
Process checks whether UAC notifications are on
- updater.exe (PID: 2140)
- updater.exe (PID: 2160)
- updater.exe (PID: 2648)
- updater.exe (PID: 7312)
- updater.exe (PID: 2448)
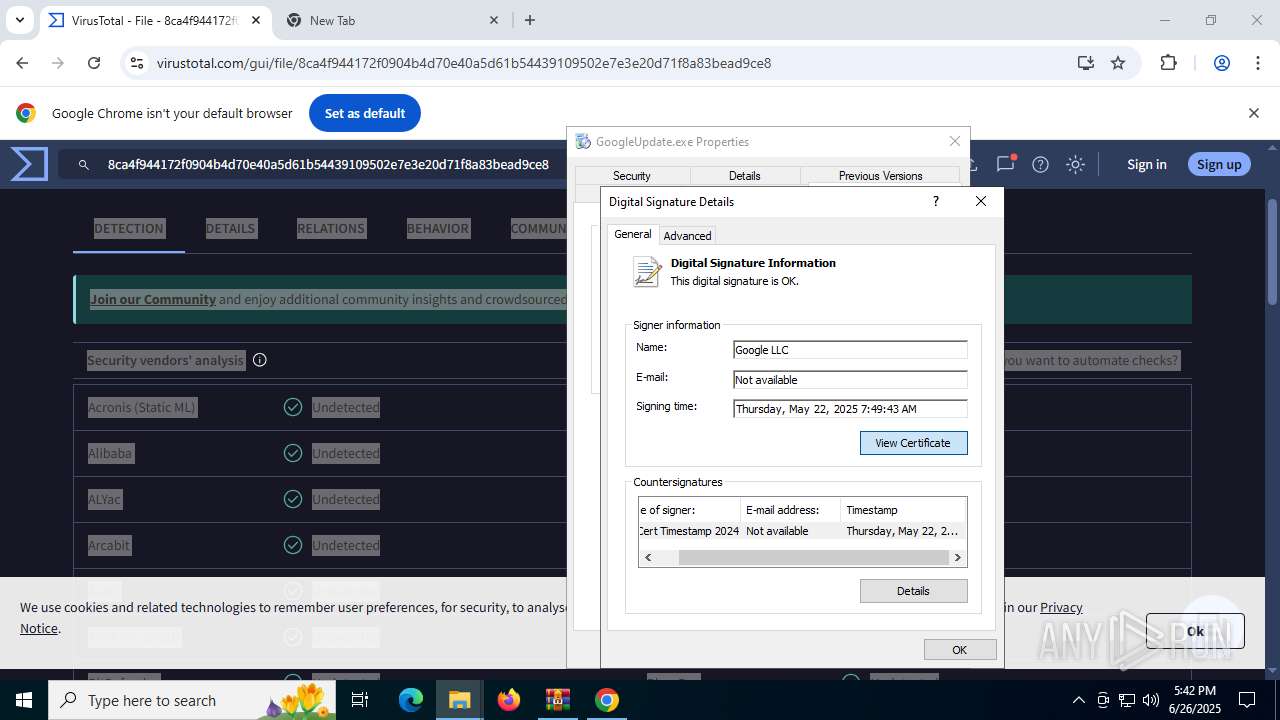
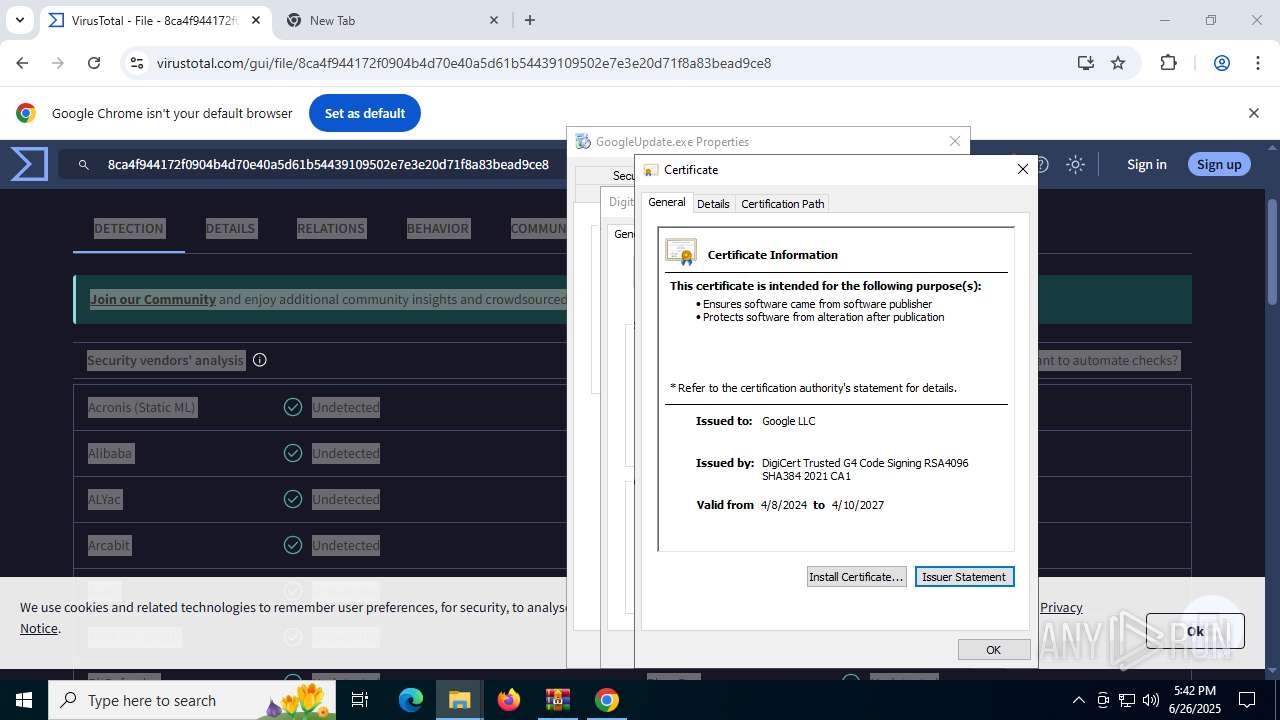
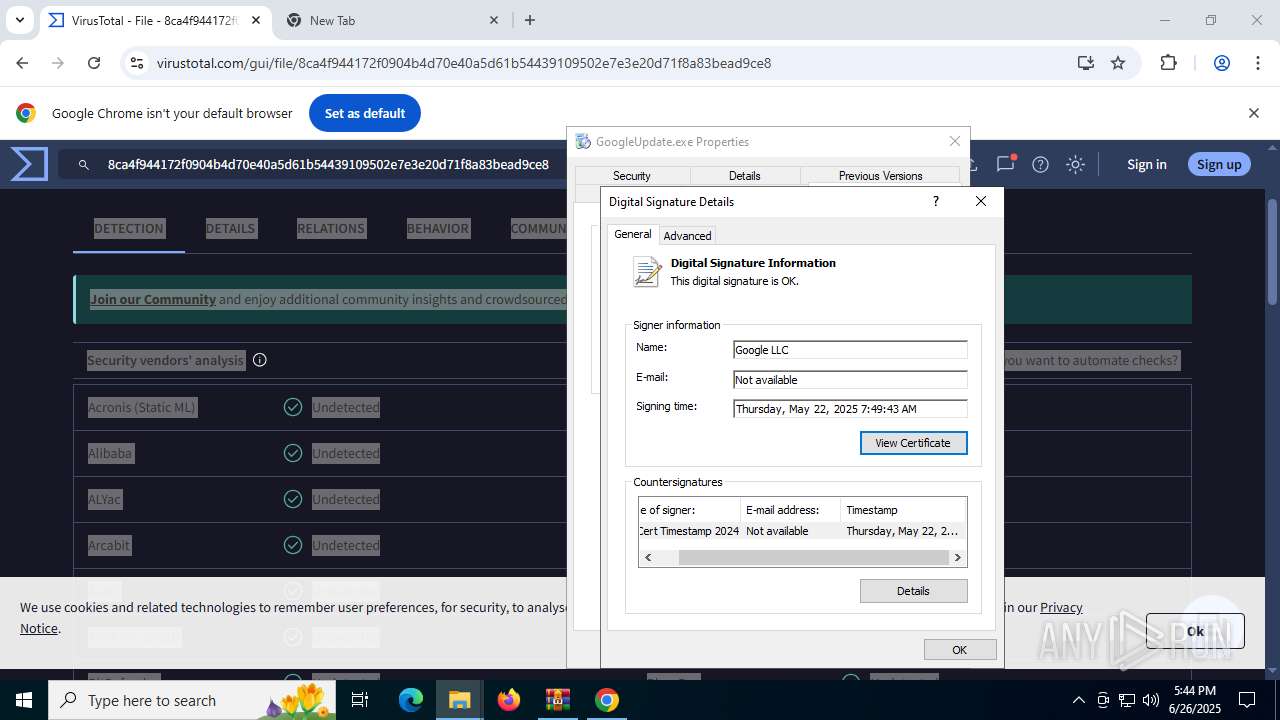
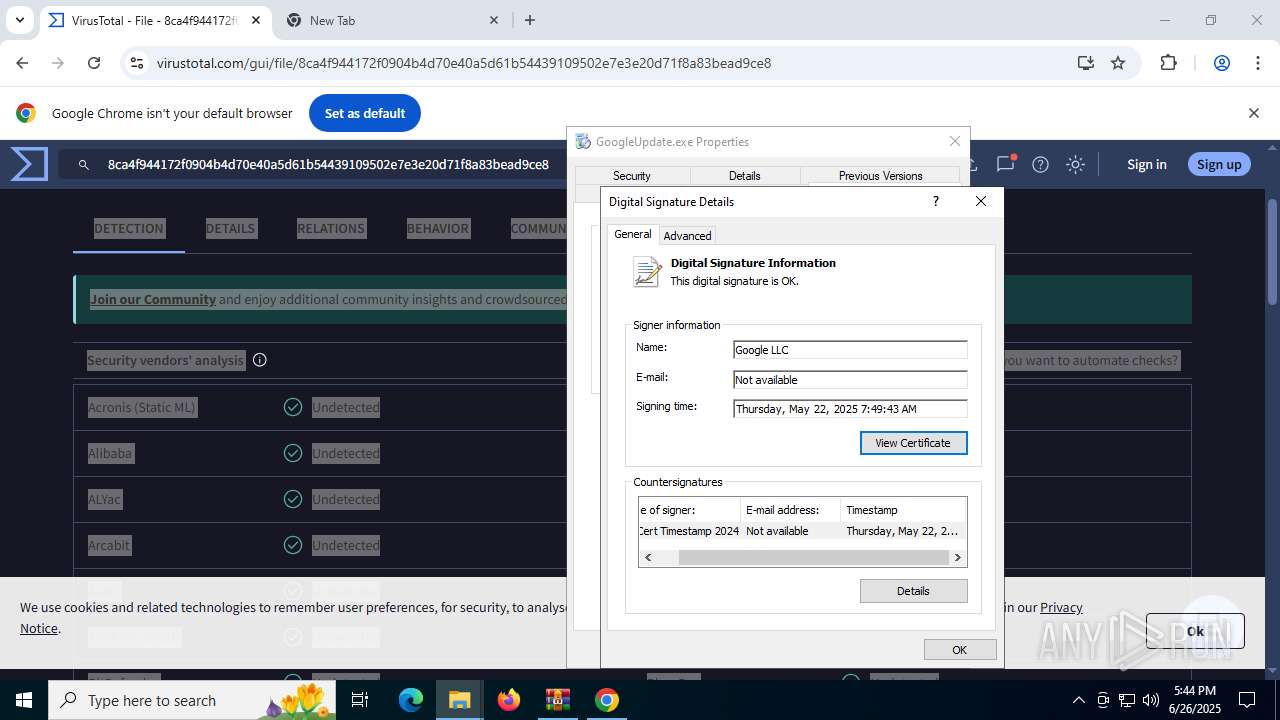
The sample compiled with english language support
- updater.exe (PID: 2140)
- WinRAR.exe (PID: 2356)
- updater.exe (PID: 2160)
- 137.0.7151.122_chrome_installer_uncompressed.exe (PID: 3864)
- setup.exe (PID: 7752)
- chrome.exe (PID: 1324)
Checks proxy server information
- updater.exe (PID: 2140)
- explorer.exe (PID: 4772)
- slui.exe (PID: 1300)
Reads the machine GUID from the registry
- updater.exe (PID: 2140)
Reads the software policy settings
- updater.exe (PID: 2648)
- updater.exe (PID: 2140)
- explorer.exe (PID: 4772)
- updater.exe (PID: 7312)
- updater.exe (PID: 2448)
- slui.exe (PID: 1300)
Creates files or folders in the user directory
- updater.exe (PID: 2140)
- explorer.exe (PID: 4772)
Application launched itself
- firefox.exe (PID: 4748)
- firefox.exe (PID: 1636)
- chrome.exe (PID: 7984)
Launching a file from a Registry key
- setup.exe (PID: 7752)
Reads Microsoft Office registry keys
- firefox.exe (PID: 1636)
Executes as Windows Service
- elevation_service.exe (PID: 7540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 2836176 |
| UncompressedSize: | 11332480 |
| OperatingSystem: | Win32 |
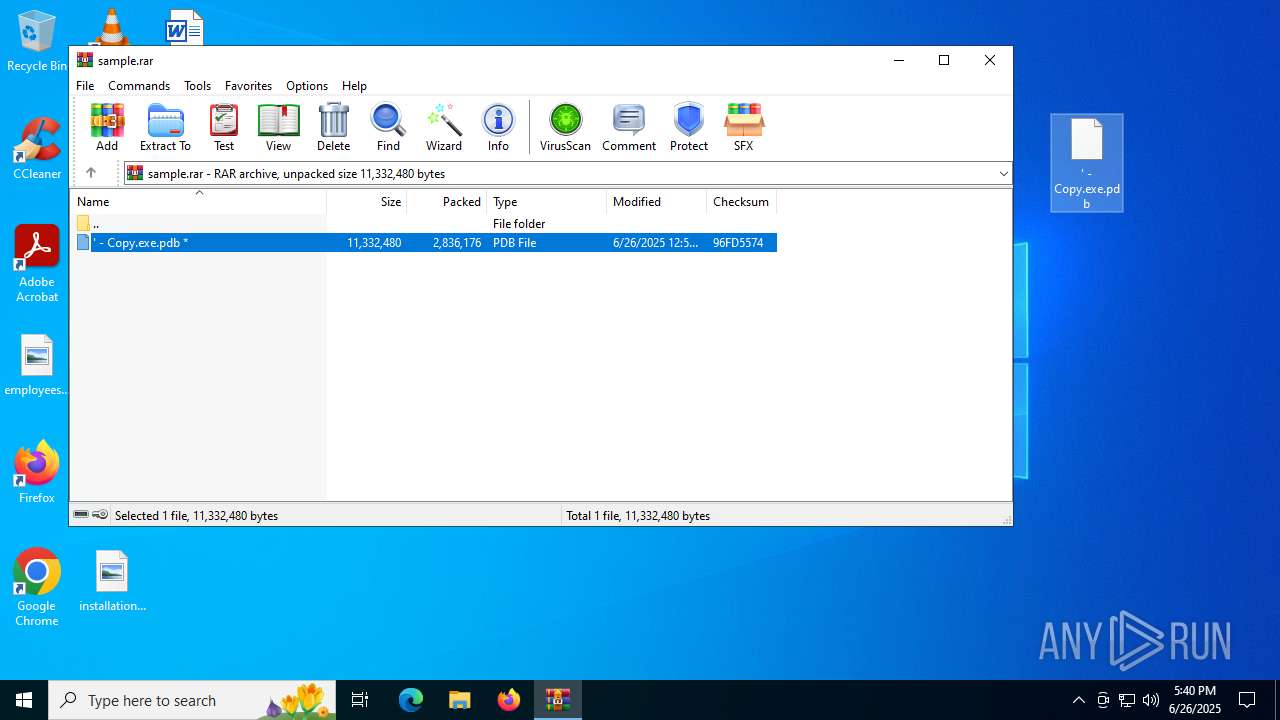
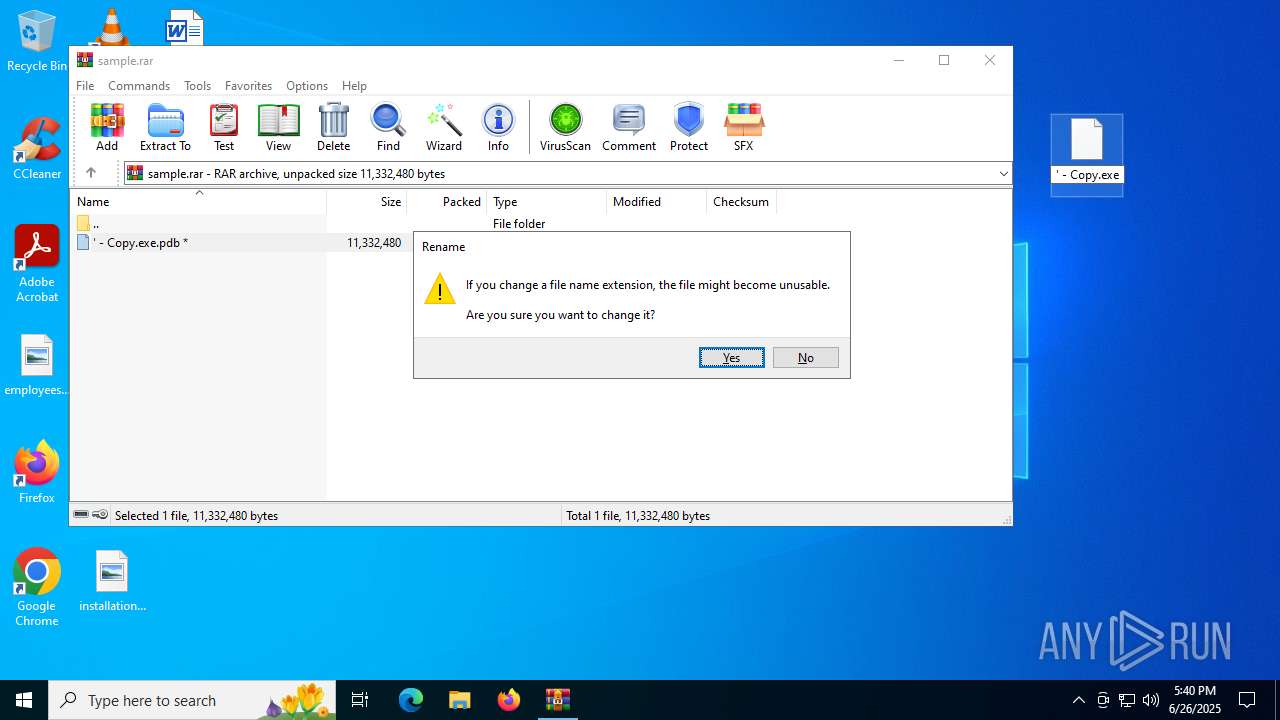
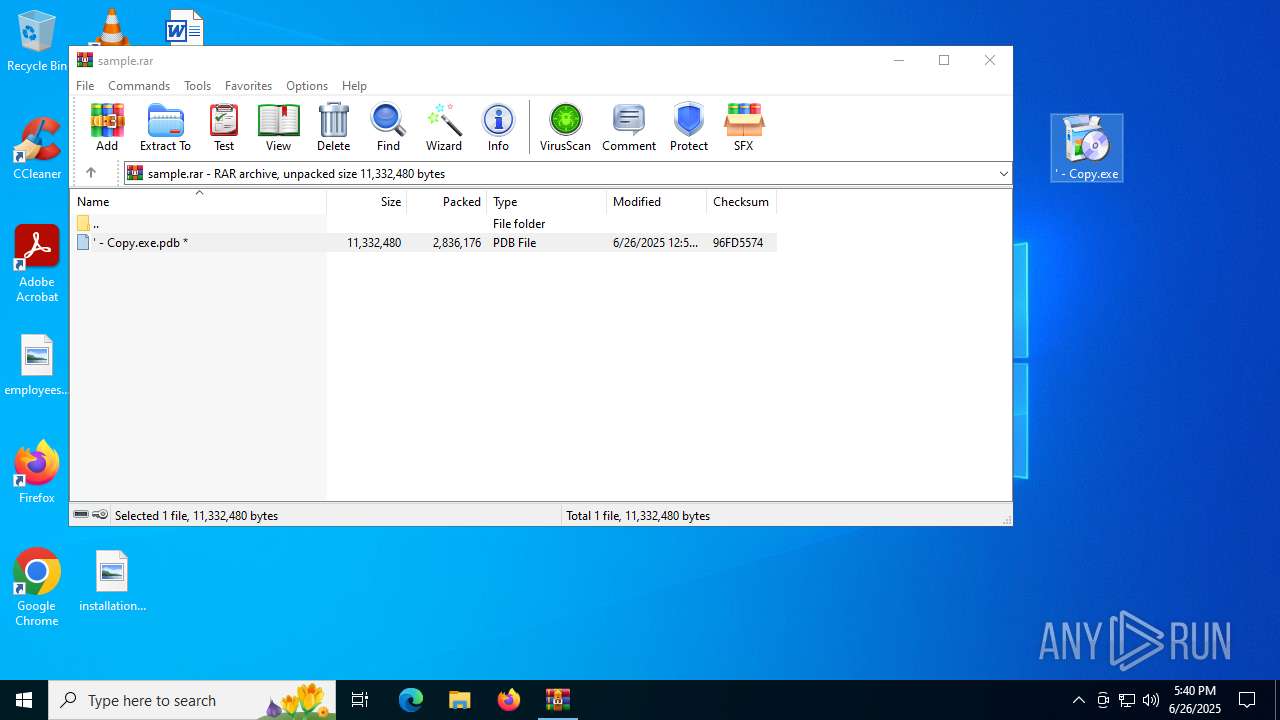
| ArchivedFileName: | ' - Copy.exe.pdb |
Total processes
233
Monitored processes
88
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --force-high-res-timeticks=disabled --field-trial-handle=2128,i,15232146416694535826,12516637542136090889,262144 --variations-seed-version --mojo-platform-channel-handle=6384 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 137.0.7151.122 Modules
| |||||||||||||||
| 1128 | "C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=138.0.7194.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x14c29c0,0x14c29cc,0x14c29d8 | C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater (x86) Version: 138.0.7194.0 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 2168 -prefsLen 36520 -prefMapHandle 2172 -prefMapSize 272997 -ipcHandle 2212 -initialChannelId {364798d2-1215-46d3-afaa-be13cafc6481} -parentPid 1636 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1636" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 2 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1300 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=2128,i,15232146416694535826,12516637542136090889,262144 --variations-seed-version --mojo-platform-channel-handle=4008 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 137.0.7151.122 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --force-high-res-timeticks=disabled --gpu-preferences=UAAAAAAAAADoAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2128,i,15232146416694535826,12516637542136090889,262144 --variations-seed-version --mojo-platform-channel-handle=3748 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 137.0.7151.122 Modules
| |||||||||||||||
| 1532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=2128,i,15232146416694535826,12516637542136090889,262144 --variations-seed-version --mojo-platform-channel-handle=6944 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 137.0.7151.122 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --force-high-res-timeticks=disabled --field-trial-handle=2128,i,15232146416694535826,12516637542136090889,262144 --variations-seed-version --mojo-platform-channel-handle=6760 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 137.0.7151.122 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --force-high-res-timeticks=disabled --field-trial-handle=2128,i,15232146416694535826,12516637542136090889,262144 --variations-seed-version --mojo-platform-channel-handle=4020 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 137.0.7151.122 Modules
| |||||||||||||||
Total events
65 530
Read events
65 081
Write events
400
Delete events
49
Modification events
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sample.rar | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040302 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
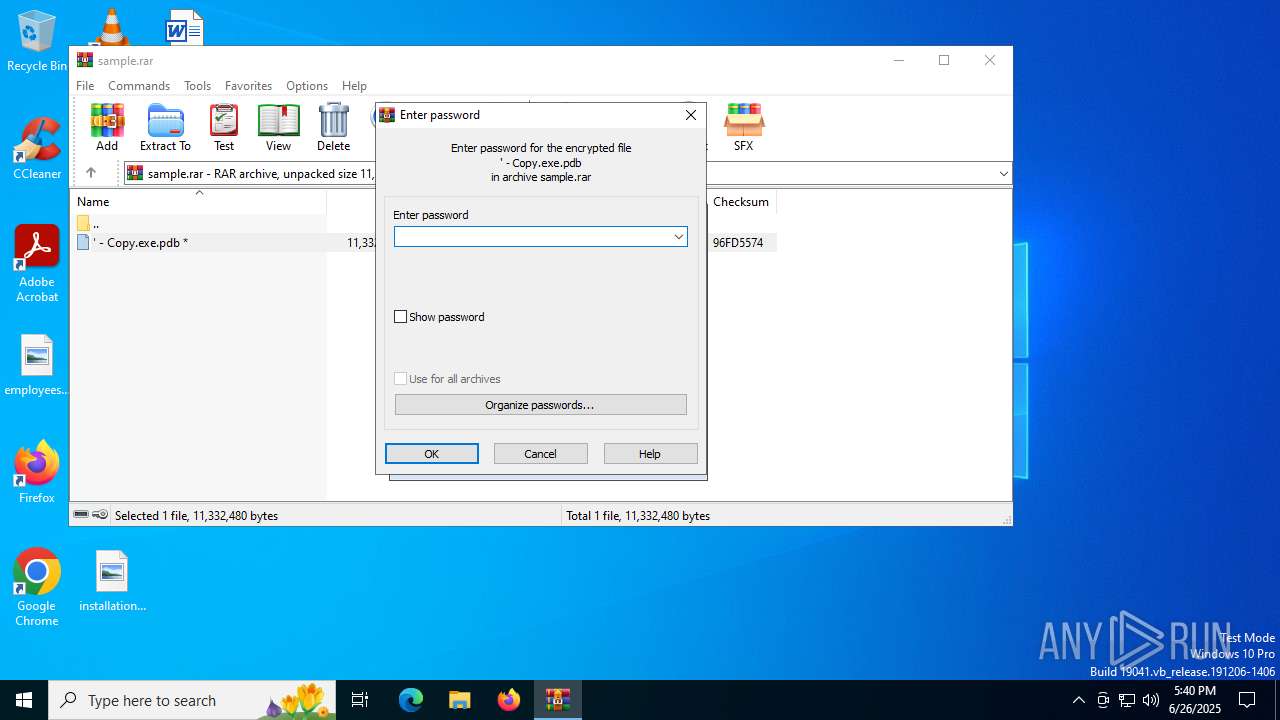
| (PID) Process: | (2356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
12
Suspicious files
376
Text files
93
Unknown types
109
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4844 | ' - Copy.exe | C:\Users\admin\AppData\Local\Temp\Google4844_1819723725\UPDATER.PACKED.7Z | — | |
MD5:— | SHA256:— | |||
| 2140 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\prefs.json~RF17bad4.TMP | binary | |
MD5:6A7C22B00ADBF302C1F53F51AF1AB2F6 | SHA256:BFD4268EDA9AB3F0E8D8D2ED0884BD28C0B34546332B36E54EBD30ACF45053FF | |||
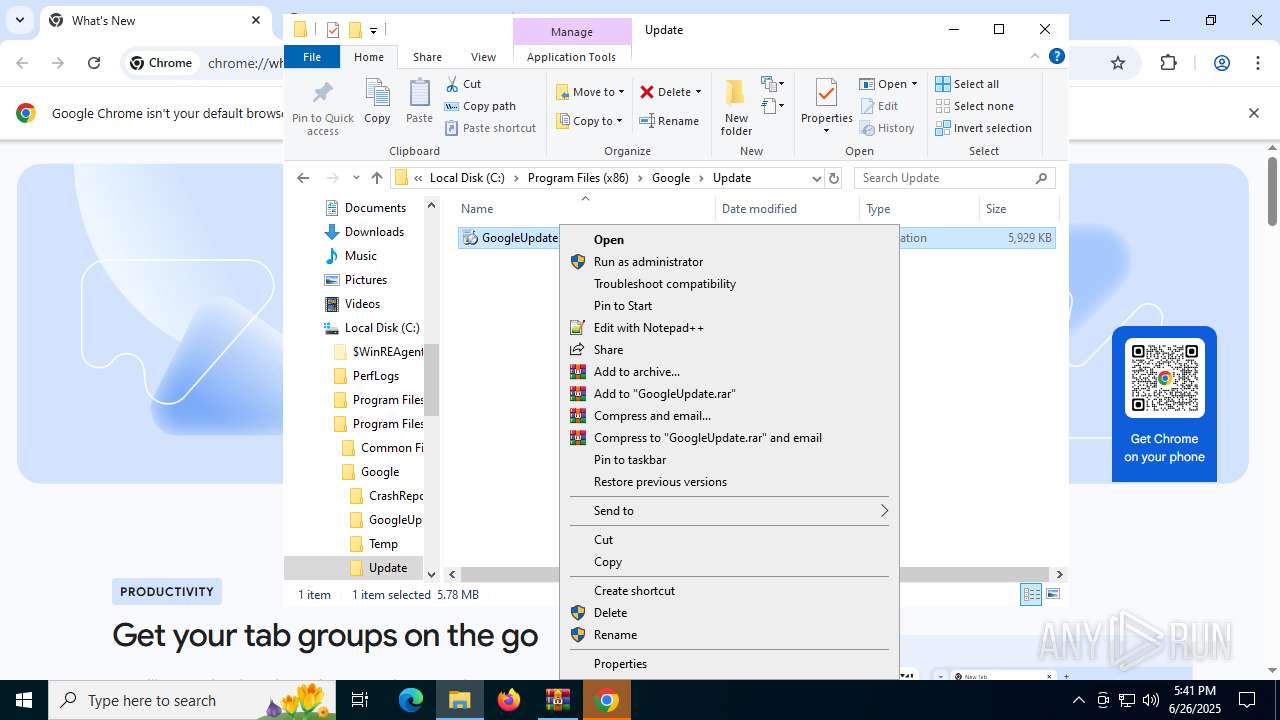
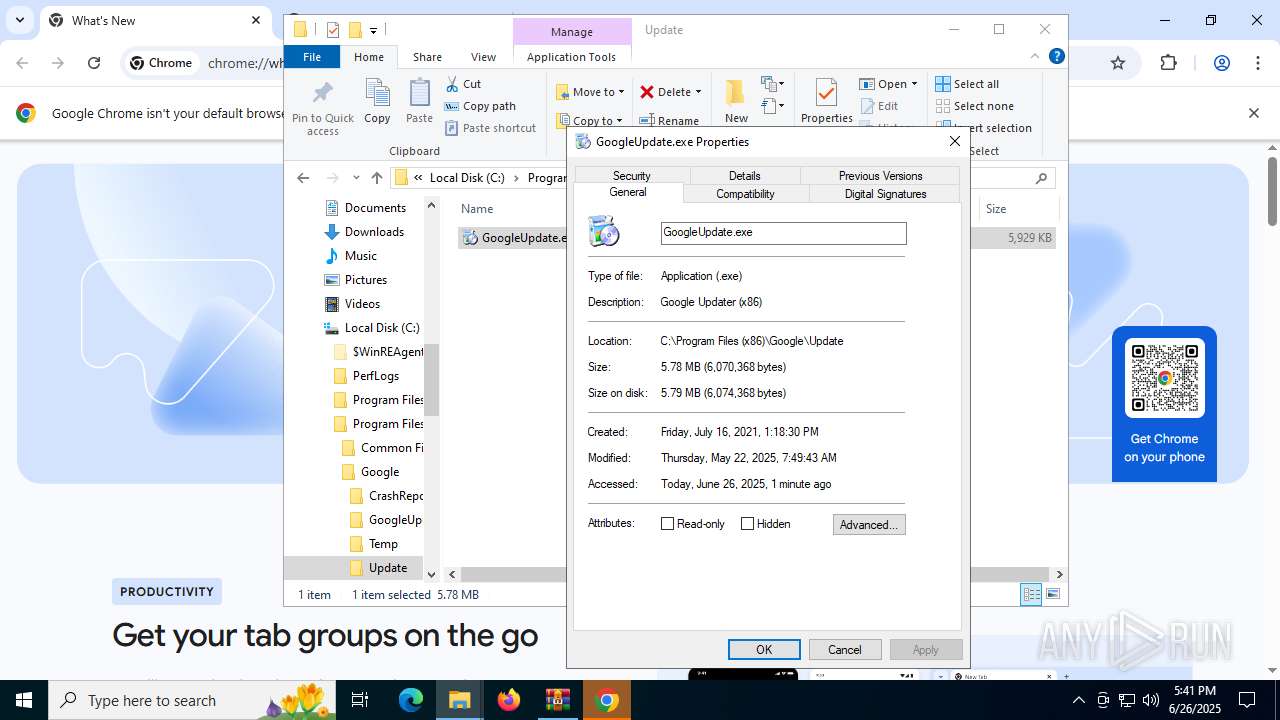
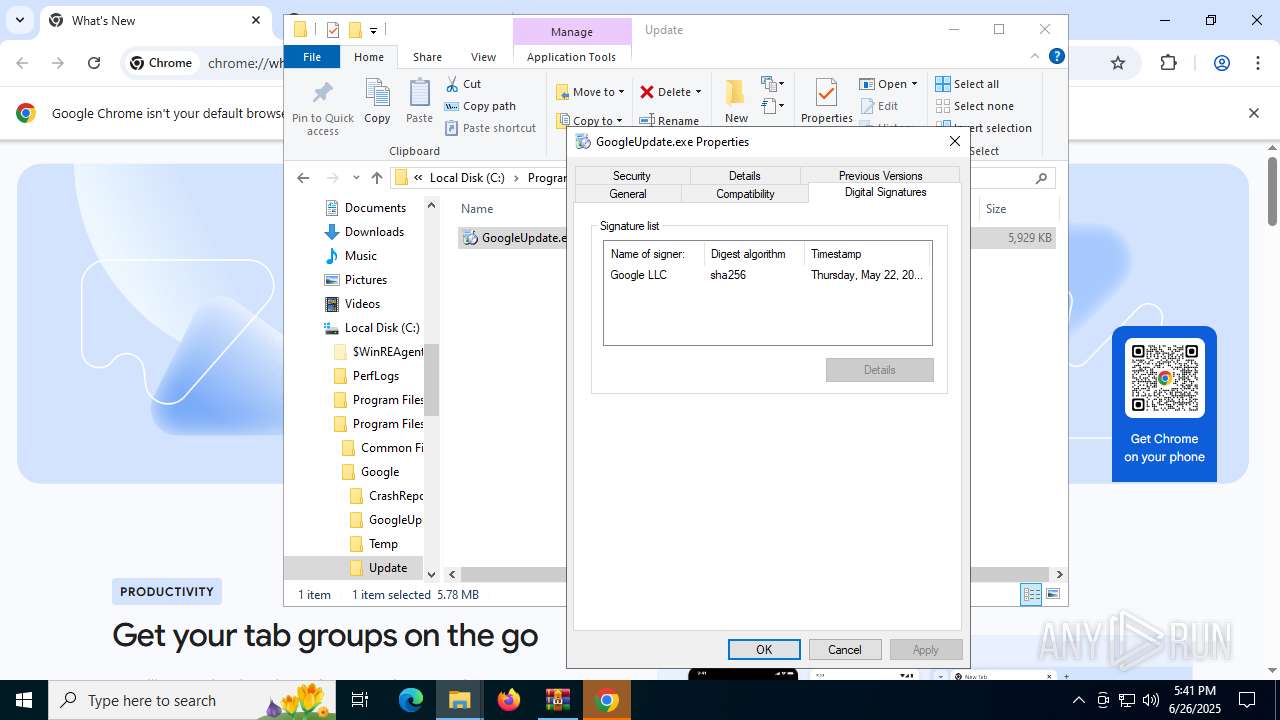
| 2160 | updater.exe | C:\Windows\SystemTemp\Google2160_1560032759\scoped_dir2160_1894158227\GoogleUpdate.exe | executable | |
MD5:FC6BEC2FD20110CF75394784819949D6 | SHA256:323C097DEFB278F09A20AACA7B05AEA20A1C859414CCA9CAEA263FA5A627A1AE | |||
| 2140 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\prefs.json | binary | |
MD5:4D8DF8FA0D5BE0C431DB342041019C34 | SHA256:D9CF12B4F14BD5ABB0B6C967A3DFE3293FEBF1FF251E7ACECBEDB6801CF52E5C | |||
| 2356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2356.41647\' - Copy.exe.pdb | executable | |
MD5:45EEE234B18AA02B846985C8FD1596B3 | SHA256:A0D60908E1669D2143A7A76BB96B206681A01898B854163F66C73091ABD2B8E2 | |||
| 2160 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\prefs.json | binary | |
MD5:AA2D0C0C72BB528CF4168EA91C1C9A56 | SHA256:E03E9D262CA3B7D19E37C3A69C7D8B46BD3F5542AA555A17D864071C28257B2C | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 2160 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\138.0.7194.0\0da45efb-4b77-46ca-bc1d-62b4b3fb59f9.tmp | binary | |
MD5:AA2D0C0C72BB528CF4168EA91C1C9A56 | SHA256:E03E9D262CA3B7D19E37C3A69C7D8B46BD3F5542AA555A17D864071C28257B2C | |||
| 2160 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\1b9c789d-b665-469b-a7ba-b50d2bb83974.tmp | binary | |
MD5:F0781A6FC9768A7A4C093D8514634CD5 | SHA256:0125BDA47A5EF97E186C40B34C36627F2CB994B9B3C6928E56B7293659C5C337 | |||
| 2648 | updater.exe | C:\Windows\SystemTemp\chrome_url_fetcher_2648_619398876\c4224f740d60158195c46c98246d44e48b91d1641a26890314fce7dd28b28d58 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
139
DNS requests
190
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2524 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6892 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2140 | updater.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2140 | updater.exe | GET | 200 | 142.250.185.67:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQCebGtkb2cNegm%2FGwwoZmjS | unknown | — | — | whitelisted |
6892 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2648 | updater.exe | GET | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/%7B8a69d345-d564-463c-aff1-a69d9e530f96%7D/c4224f740d60158195c46c98246d44e48b91d1641a26890314fce7dd28b28d58 | unknown | — | — | whitelisted |
2140 | updater.exe | GET | 200 | 142.250.185.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1636 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4860 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2524 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2524 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6892 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
6348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6348 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
chrome.exe | I0000 00:00:1750959668.118640 4040 voice_transcription.cc:58] Registering VoiceTranscriptionCapability
|