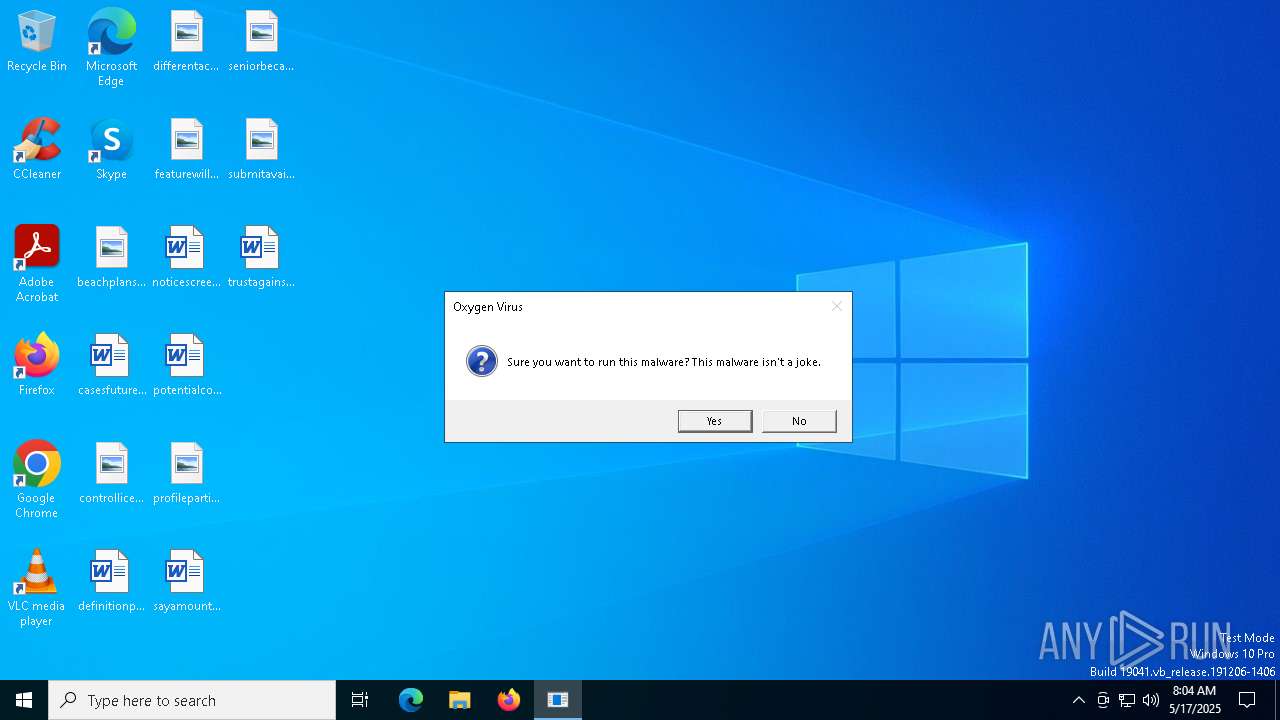
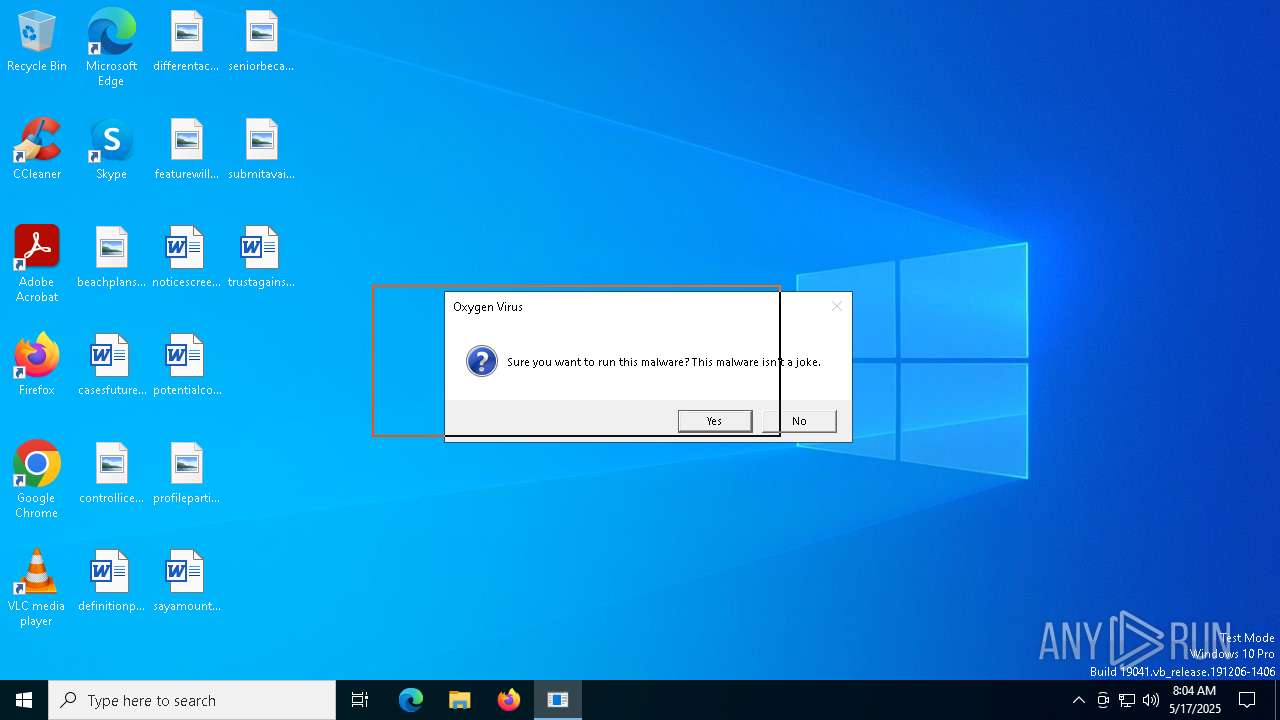
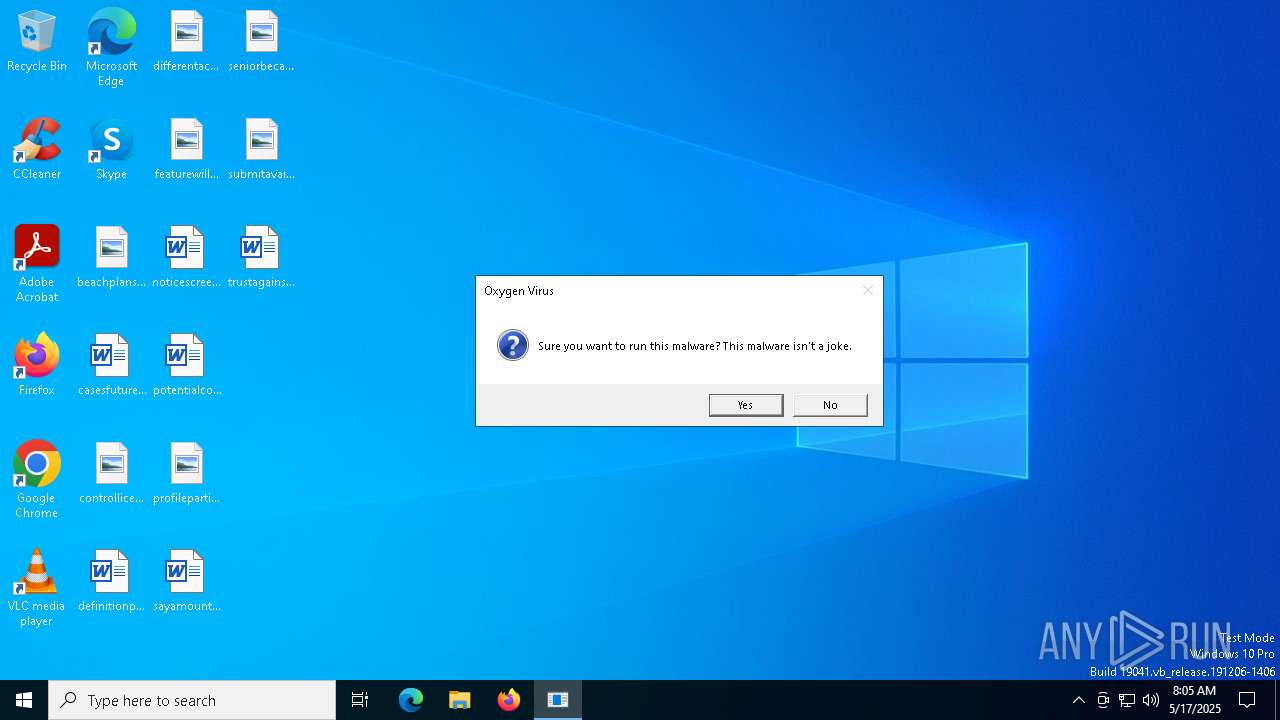
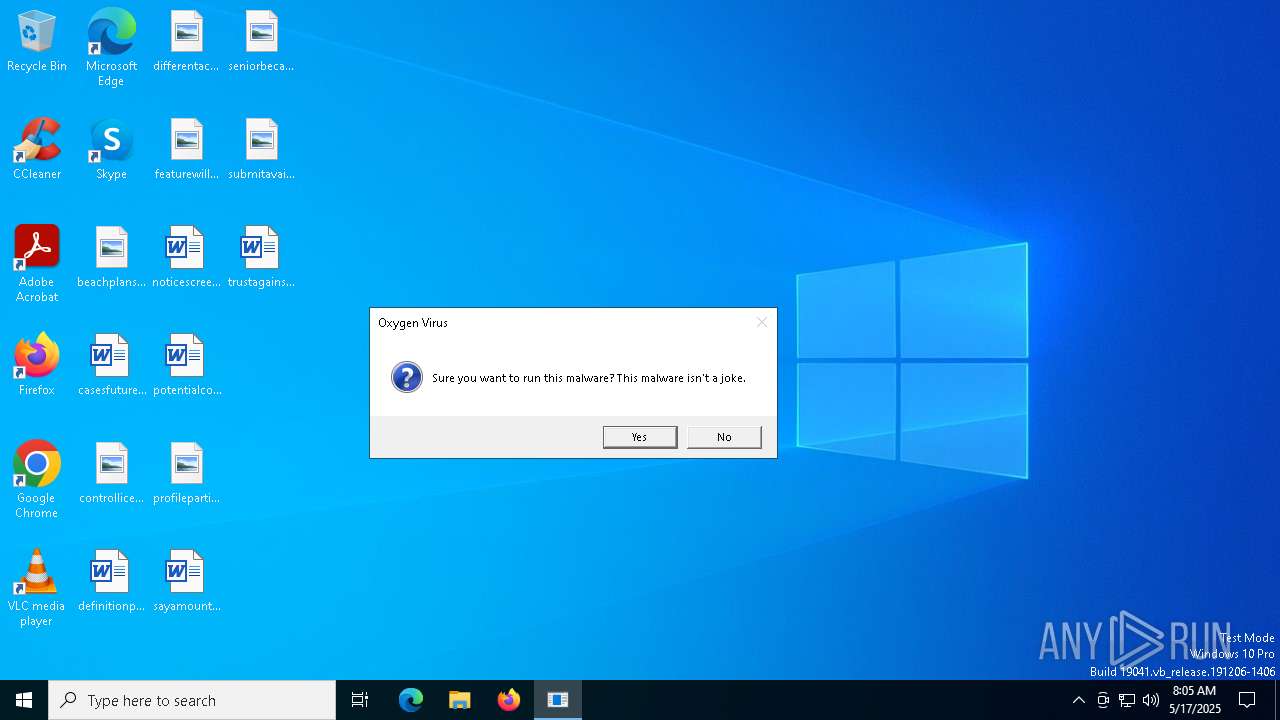
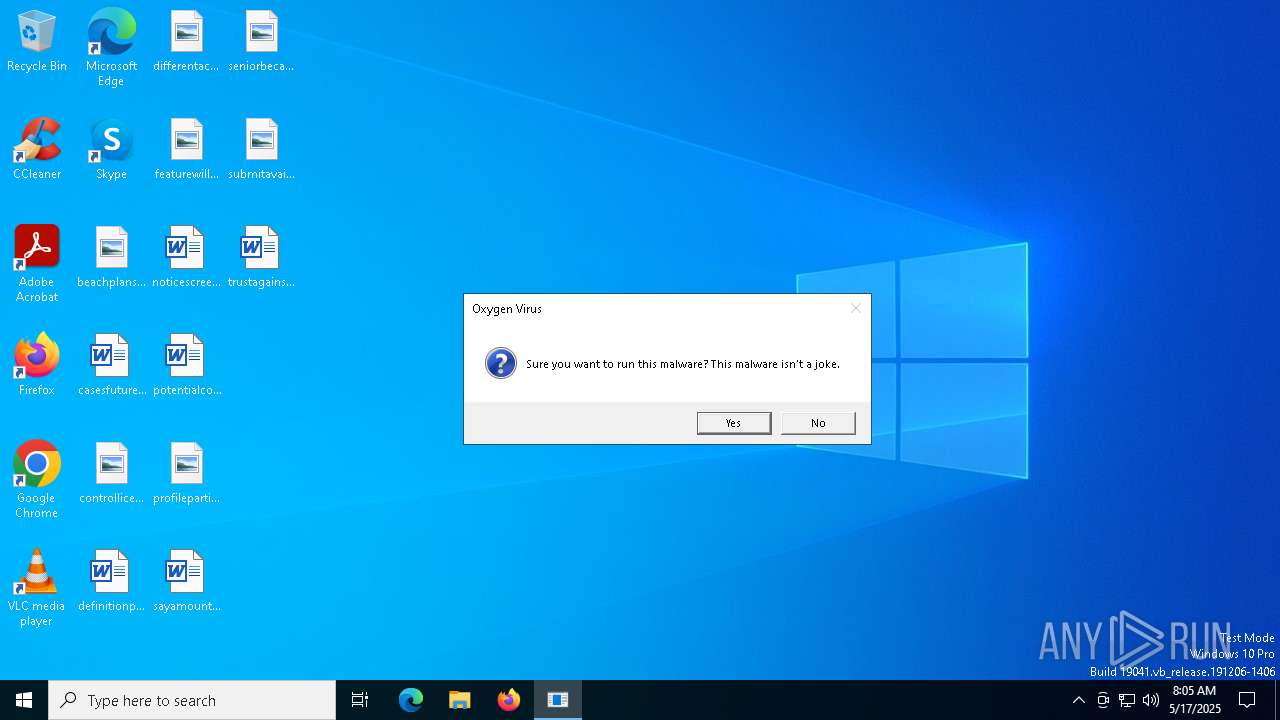
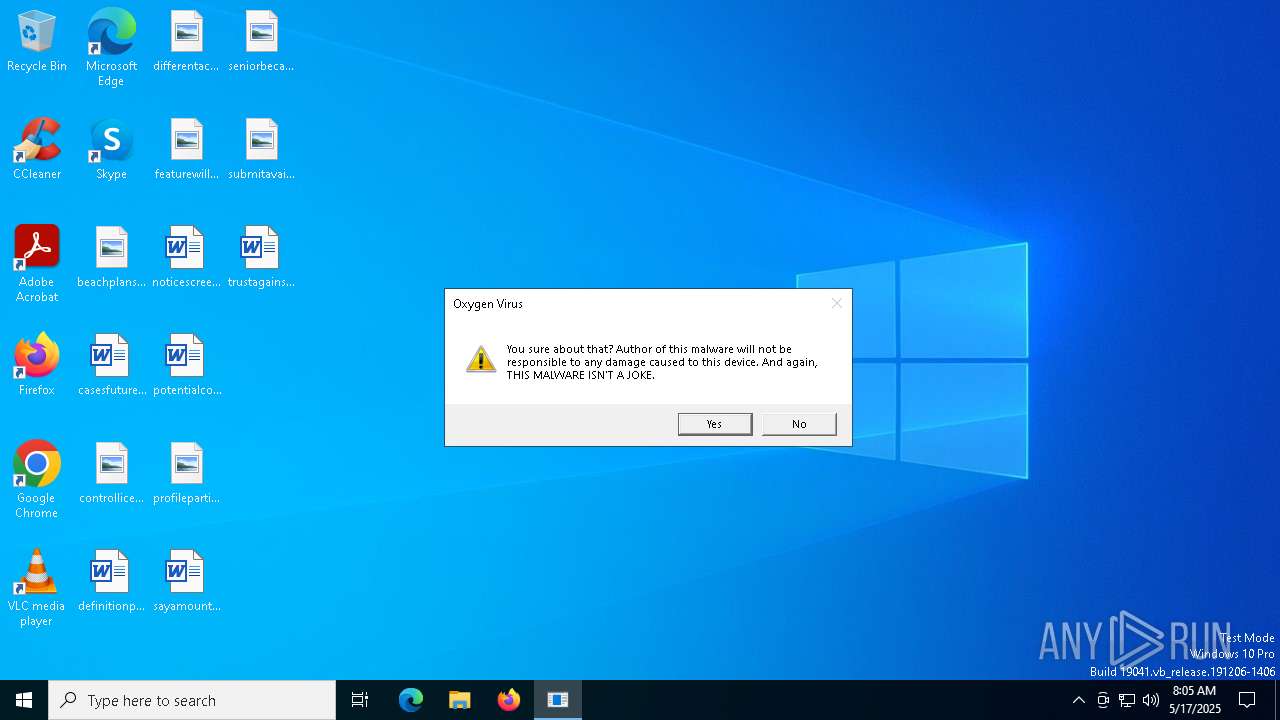
| File name: | Oxygen Virus.exe |
| Full analysis: | https://app.any.run/tasks/997d8fce-5966-46ff-a376-95b4b0a6a2c4 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 08:04:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 2F879BBC5B7D5265EB378431BC116C03 |
| SHA1: | DED230B4927E562A9DA7F6070D1AAF9B78C3F515 |
| SHA256: | EFAEF808012437A7B58DA354868B9A233CF9E295CB9CD64045EB1F068E236B04 |
| SSDEEP: | 6144:1ErozMdcYpo8zGVorBkhcrZNjshMX+VQkxf/4JNzIKDE:1Eroz8cYpolGrBkhcrZdshMX+vxnYzIp |
MALICIOUS
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 8056)
Disables the Command Prompt (cmd)
- Oxygen Virus.exe (PID: 7972)
Disables task manager
- Oxygen Virus.exe (PID: 7972)
SUSPICIOUS
Executable content was dropped or overwritten
- Oxygen Virus.exe (PID: 7424)
Reads the date of Windows installation
- Oxygen Virus.exe (PID: 7424)
- StartMenuExperienceHost.exe (PID: 1184)
Reads security settings of Internet Explorer
- Oxygen Virus.exe (PID: 7424)
- StartMenuExperienceHost.exe (PID: 1184)
Starts itself from another location
- Oxygen Virus.exe (PID: 7424)
Starts CMD.EXE for commands execution
- Oxygen Virus.exe (PID: 7972)
INFO
Checks supported languages
- Oxygen Virus.exe (PID: 7424)
- Oxygen Virus.exe (PID: 7972)
- TextInputHost.exe (PID: 6872)
- StartMenuExperienceHost.exe (PID: 1184)
- SearchApp.exe (PID: 728)
Reads the computer name
- Oxygen Virus.exe (PID: 7424)
- TextInputHost.exe (PID: 6872)
- StartMenuExperienceHost.exe (PID: 1184)
- SearchApp.exe (PID: 728)
- Oxygen Virus.exe (PID: 7972)
Process checks computer location settings
- Oxygen Virus.exe (PID: 7424)
- StartMenuExperienceHost.exe (PID: 1184)
- SearchApp.exe (PID: 728)
Reads the software policy settings
- SearchApp.exe (PID: 728)
Checks proxy server information
- SearchApp.exe (PID: 728)
Reads Environment values
- SearchApp.exe (PID: 728)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:17 08:04:19+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 157696 |
| InitializedDataSize: | 104960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9470 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
148
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6872 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 7308 | "C:\Users\admin\AppData\Local\Temp\Oxygen Virus.exe" | C:\Users\admin\AppData\Local\Temp\Oxygen Virus.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7424 | "C:\Users\admin\AppData\Local\Temp\Oxygen Virus.exe" | C:\Users\admin\AppData\Local\Temp\Oxygen Virus.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Oxygen Virus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7496 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7528 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7972 | "C:\WINDOWS\system32\Oxygen Virus.exe" --moved | C:\Windows\System32\Oxygen Virus.exe | — | Oxygen Virus.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 055
Read events
8 957
Write events
97
Delete events
1
Modification events
| (PID) Process: | (1184) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{aa3449e9-3a7d-3621-a5d7-da5c9b44c698}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 010000008AF1716F02C7DB01 | |||
| (PID) Process: | (728) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (1184) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (1184) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_AppUsageData |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (1184) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_TargetedContentTiles |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (1184) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{aa3449e9-3a7d-3621-a5d7-da5c9b44c698}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 000000002611A46F02C7DB01 | |||
| (PID) Process: | (1184) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\CloudStore\Store\Cache\DefaultAccount\$de${c6a388c9-afd3-47e2-a46b-29cb43ad4323}$start.tilegrid$windows.data.curatedtilecollection.tilecollection\Current |
| Operation: | write | Name: | Data |
Value: 02000000ECC8AA6F02C7DB0100000000434201000A0A00D0140CCA3200CB8C0A0212267B00410039003400310034003200440039002D0032003100350030002D0034003600380037002D0038003600390033002D003100450036003200320036003500390039003900430031007D000012267B00390033004600380044003900390046002D0036003500300041002D0034003100330035002D0038004200340043002D003200460046004100410041003300450046004600340039007D0000E22C01010000 | |||
| (PID) Process: | (728) SearchApp.exe | Key: | \REGISTRY\A\{f935c7a7-5e62-603c-70f1-ac53ae4b8ee6}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000F4A9C06F02C7DB01 | |||
| (PID) Process: | (728) SearchApp.exe | Key: | \REGISTRY\A\{f935c7a7-5e62-603c-70f1-ac53ae4b8ee6}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 0000F4A9C06F02C7DB01 | |||
| (PID) Process: | (728) SearchApp.exe | Key: | \REGISTRY\A\{f935c7a7-5e62-603c-70f1-ac53ae4b8ee6}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 0000F4A9C06F02C7DB01 | |||
Executable files
1
Suspicious files
45
Text files
1 080
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\w7tED3SztwP1 | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\fcZfXHfA7WQW | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\U1DvrtjbV5pU | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\WH3yjXHgwFls | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\M0Vd82zgqD4z | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\bYpk738z0Zjl | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\LLObn6U1wGxF | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\ORryxdXrcsDn | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\qzHv3whT6ux7 | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
| 7972 | Oxygen Virus.exe | C:\Users\admin\Desktop\VQn8f8WEe2hC | text | |
MD5:1DC0CDA9AFD5F3E09C2835CF245EB83F | SHA256:C75D0F58F707789FAF1217151478EE946BF09714FBC8D8DB3CBEEFE71CA5D541 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
28
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
728 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7968 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7968 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |