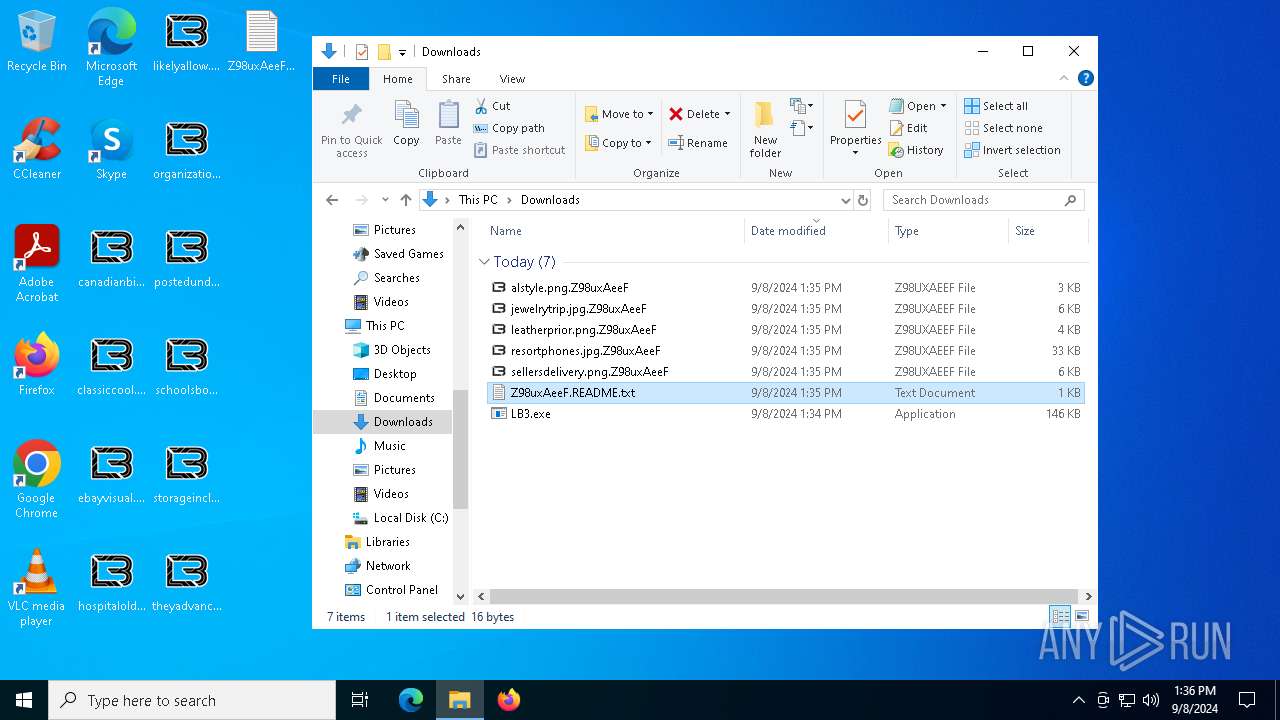
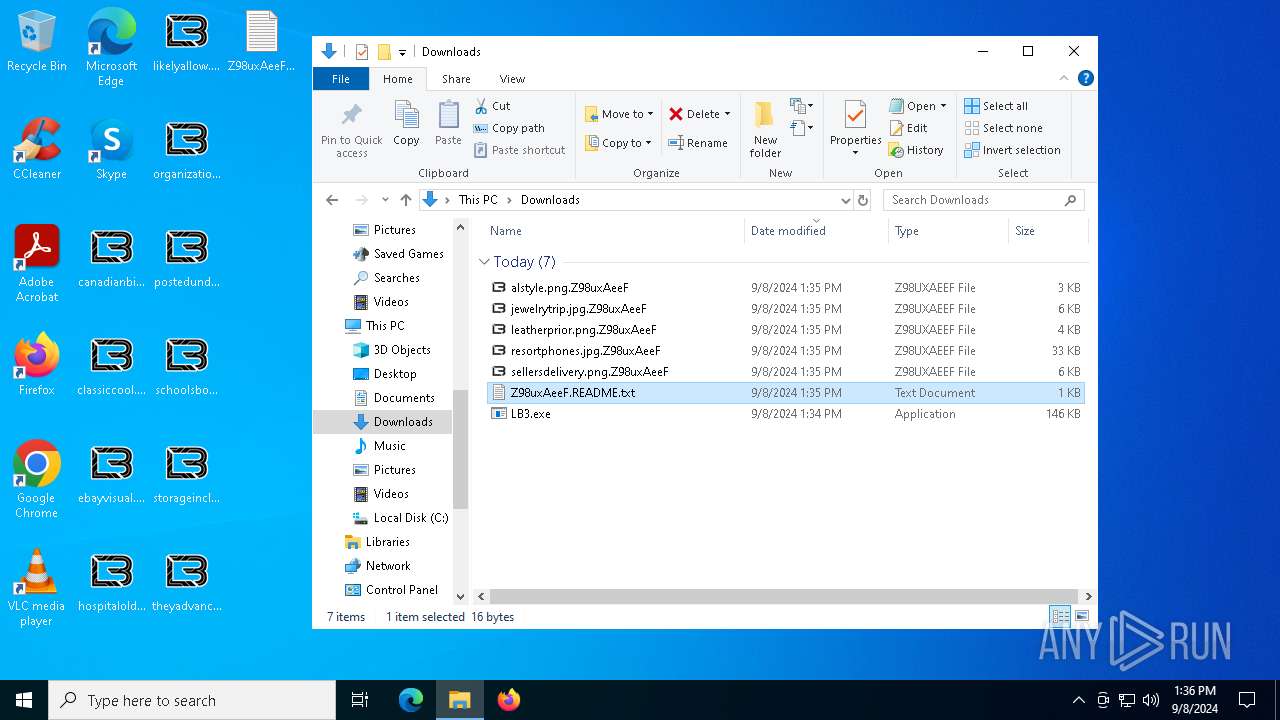
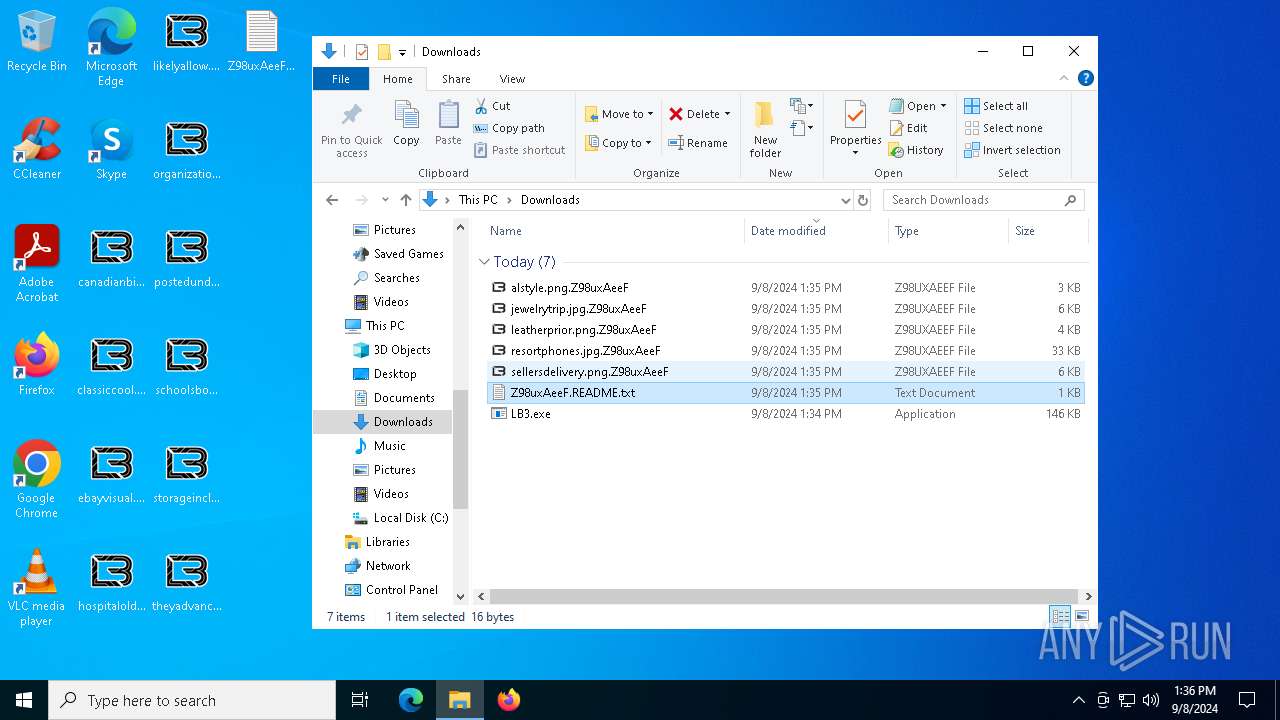
| File name: | LB3.exe |
| Full analysis: | https://app.any.run/tasks/b61e3558-7db4-4a93-86a0-84afcada0ba0 |
| Verdict: | Malicious activity |
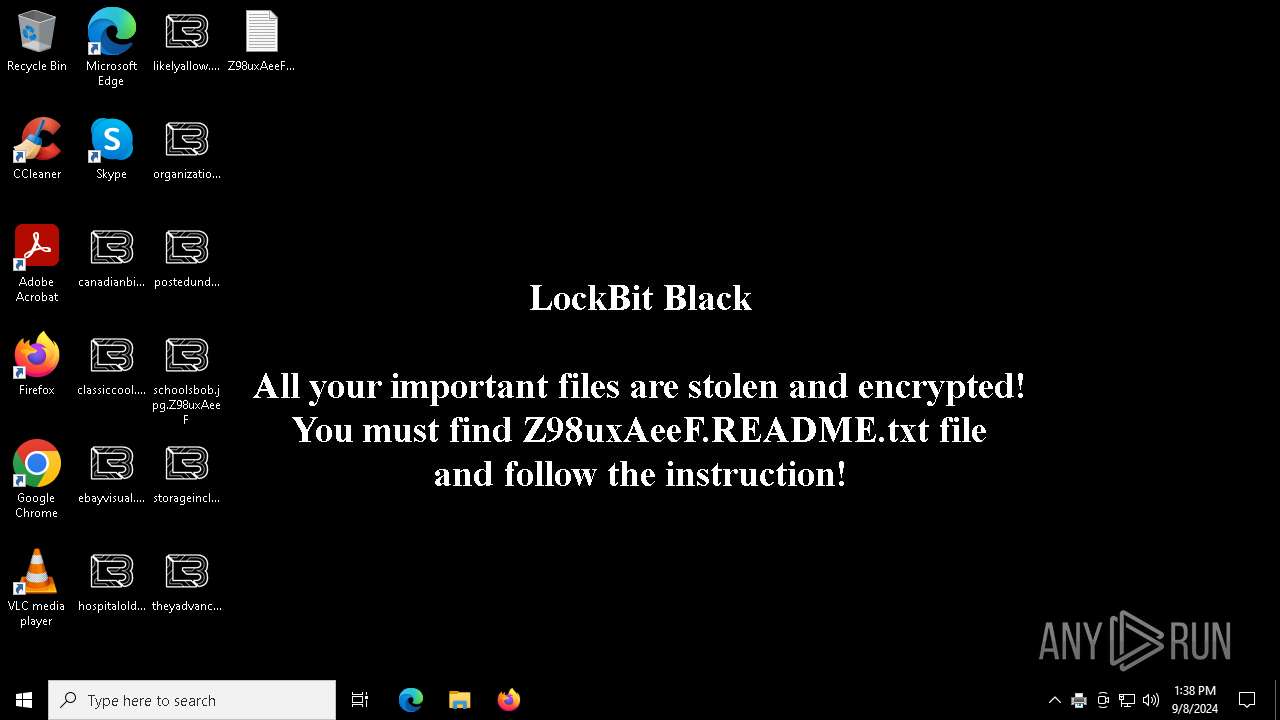
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | September 08, 2024, 13:34:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 71A38904E74D4898B95CBF0456ACE724 |
| SHA1: | 0A35FA7E0FF2037AB12583F383D2E780EF9B5BAD |
| SHA256: | EFADA03FDD8B164AE98ADB62F3B7DA000631D7492213B130F94F7FEBF75578E9 |
| SSDEEP: | 3072:hmhXodguLLDzaJ/A7z7zT73vX/iLKcvkZI1oFiJzFaB:tfza6z7z/6KEzy0zFa |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 6128)
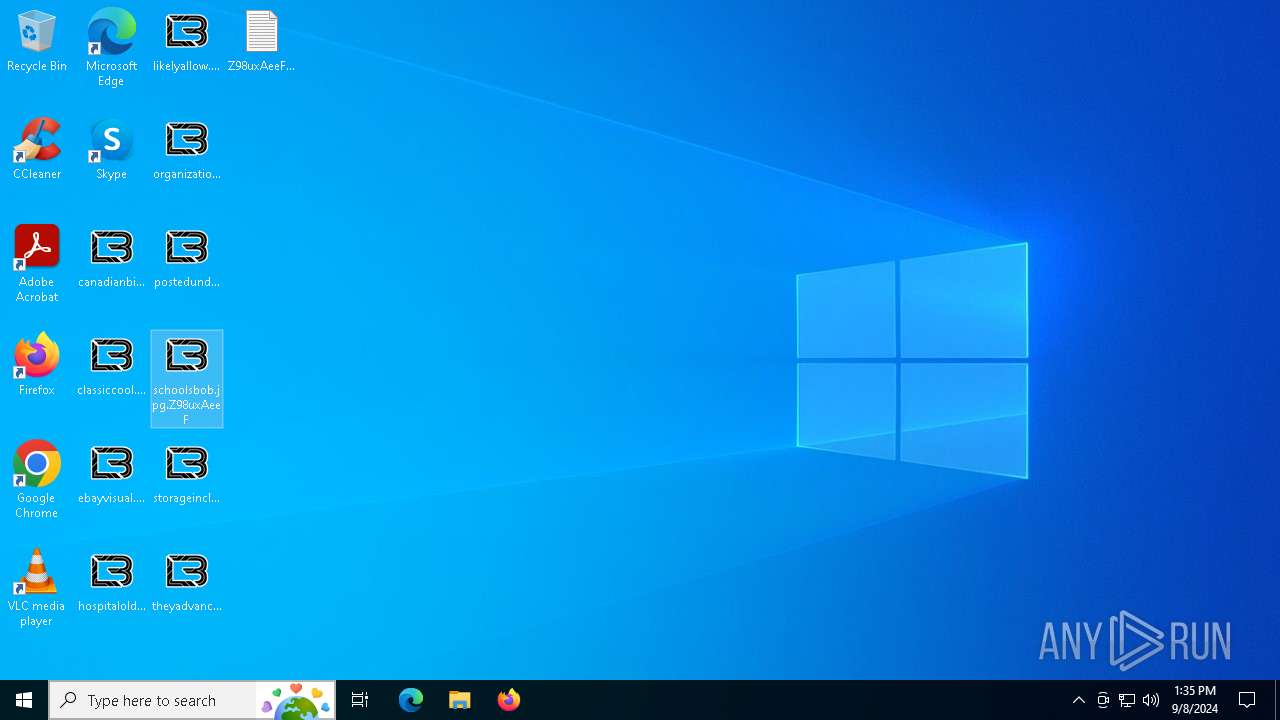
Renames files like ransomware
- LB3.exe (PID: 2584)
Actions looks like stealing of personal data
- LB3.exe (PID: 2584)
Steals credentials from Web Browsers
- LB3.exe (PID: 2584)
[YARA] LockBit is detected
- LB3.exe (PID: 2584)
Scans artifacts that could help determine the target
- ONENOTE.EXE (PID: 2876)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- LB3.exe (PID: 2584)
Changes the desktop background image
- LB3.exe (PID: 2584)
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 2876)
Reads security settings of Internet Explorer
- ONENOTE.EXE (PID: 2876)
Executable content was dropped or overwritten
- LB3.exe (PID: 2584)
Reads the date of Windows installation
- ONENOTE.EXE (PID: 2876)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 2876)
INFO
Checks supported languages
- LB3.exe (PID: 5532)
- LB3.exe (PID: 2584)
- ONENOTE.EXE (PID: 2876)
Reads the computer name
- LB3.exe (PID: 5532)
- LB3.exe (PID: 2584)
- ONENOTE.EXE (PID: 2876)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 6128)
- notepad.exe (PID: 5048)
- splwow64.exe (PID: 6660)
- printfilterpipelinesvc.exe (PID: 6888)
- notepad.exe (PID: 6700)
The process uses the downloaded file
- dllhost.exe (PID: 6128)
Reads the machine GUID from the registry
- LB3.exe (PID: 5532)
- LB3.exe (PID: 2584)
- ONENOTE.EXE (PID: 2876)
Creates files in the program directory
- LB3.exe (PID: 2584)
Creates files or folders in the user directory
- LB3.exe (PID: 2584)
- printfilterpipelinesvc.exe (PID: 6888)
- ONENOTE.EXE (PID: 2876)
Create files in a temporary directory
- LB3.exe (PID: 2584)
- ONENOTE.EXE (PID: 2876)
Manual execution by a user
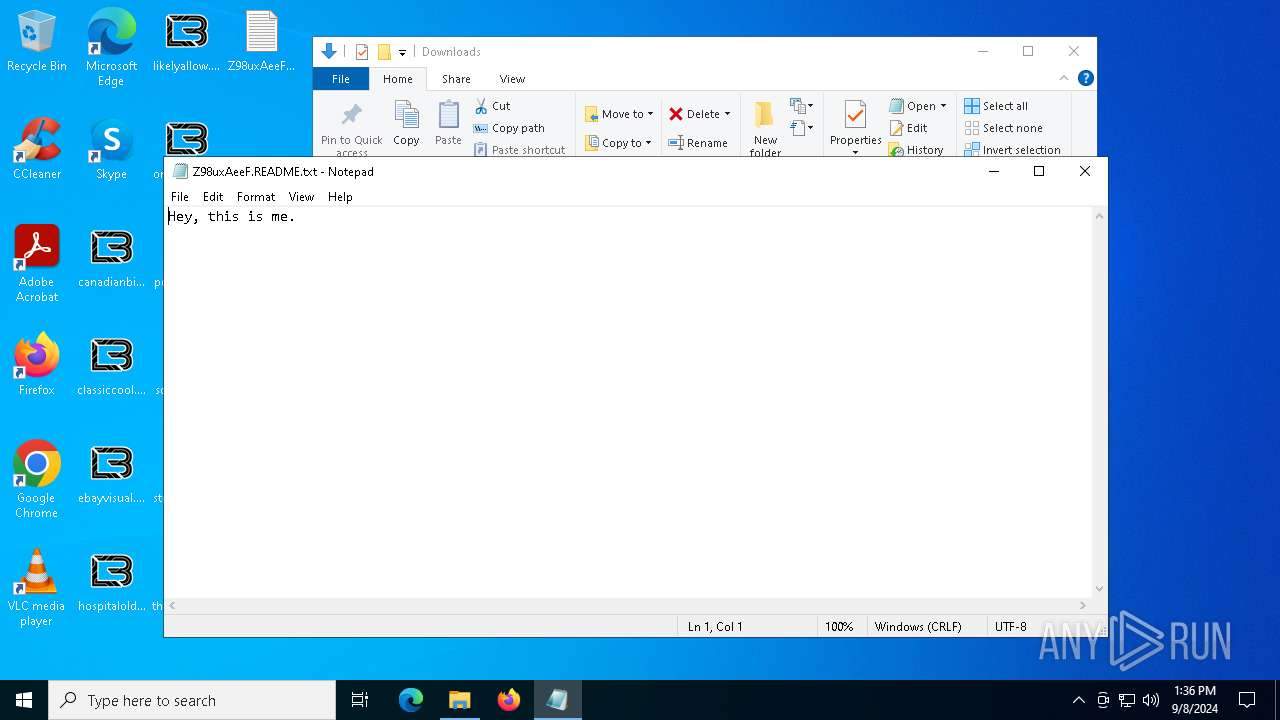
- notepad.exe (PID: 5048)
- notepad.exe (PID: 6700)
Sends debugging messages
- splwow64.exe (PID: 6660)
- ONENOTE.EXE (PID: 2876)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 2876)
Reads Environment values
- ONENOTE.EXE (PID: 2876)
Checks proxy server information
- ONENOTE.EXE (PID: 2876)
Reads product name
- ONENOTE.EXE (PID: 2876)
Reads CPU info
- ONENOTE.EXE (PID: 2876)
Reads the software policy settings
- ONENOTE.EXE (PID: 2876)
Process checks computer location settings
- ONENOTE.EXE (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:13 23:30:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.12 |
| CodeSize: | 99328 |
| InitializedDataSize: | 50688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1946f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2584 | "C:\Users\admin\Downloads\LB3.exe" | C:\Users\admin\Downloads\LB3.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2876 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\{6D5C68FB-7849-4896-B3F9-9FCE600FCEF5}.xps" 133702762711460000 | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
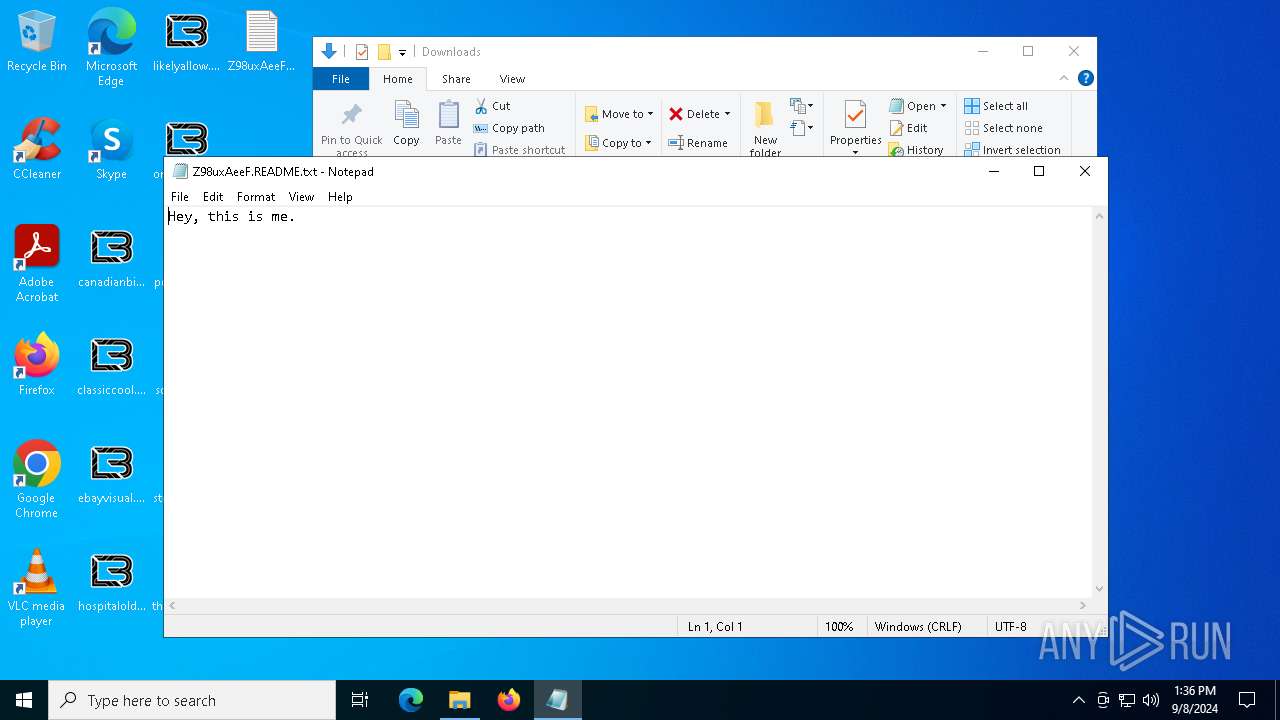
| 5048 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\Z98uxAeeF.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5532 | "C:\Users\admin\Downloads\LB3.exe" | C:\Users\admin\Downloads\LB3.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6128 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | C:\WINDOWS\splwow64.exe 12288 | C:\Windows\splwow64.exe | LB3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6700 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\Z98uxAeeF.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6888 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 418
Read events
9 903
Write events
2 493
Delete events
22
Modification events
| (PID) Process: | (6128) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\AirSpaceChannel |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\AirSpaceChannel |
| Operation: | write | Name: | ChannelAccess |
Value: O:BAG:SYD:(A;;0x1;;;SY)(A;;0x5;;;BA)(A;;0x1;;;LA) | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\AMSI/Debug |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\AMSI/Debug |
| Operation: | write | Name: | ChannelAccess |
Value: O:BAG:SYD:(A;;0x1;;;SY)(A;;0x5;;;BA)(A;;0x1;;;LA) | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\AMSI/Operational |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\AMSI/Operational |
| Operation: | write | Name: | ChannelAccess |
Value: O:BAG:SYD:(A;;0x1;;;SY)(A;;0x5;;;BA)(A;;0x1;;;LA) | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Analytic |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Analytic |
| Operation: | write | Name: | ChannelAccess |
Value: O:BAG:SYD:(A;;0x1;;;SY)(A;;0x5;;;BA)(A;;0x1;;;LA) | |||
| (PID) Process: | (2584) LB3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\DirectShowFilterGraph |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
6
Suspicious files
1 953
Text files
2 109
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\EEEEEEEEEEE | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\DDDDDDDDDDD | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\KKKKKKKKKKK | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\JJJJJJJJJJJ | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\MMMMMMMMMMM | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\LLLLLLLLLLL | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\NNNNNNNNNNN | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\ProgramData\Z98uxAeeF.ico | image | |
MD5:88D9337C4C9CFE2D9AFF8A2C718EC76B | SHA256:95E059EF72686460884B9AEA5C292C22917F75D56FE737D43BE440F82034F438 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\AAAAAAAAAAA | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
| 2584 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | binary | |
MD5:61EEC0C6E08E2A609E919CAD10DDCD6D | SHA256:5EE882F1CDA51A82843745C5C3FAEEFC767033167F533727A674C81D76559F05 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
44
DNS requests
10
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6020 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6020 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5336 | SearchApp.exe | 52.182.143.211:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
splwow64.exe | Invalid parameter passed to C runtime function.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|