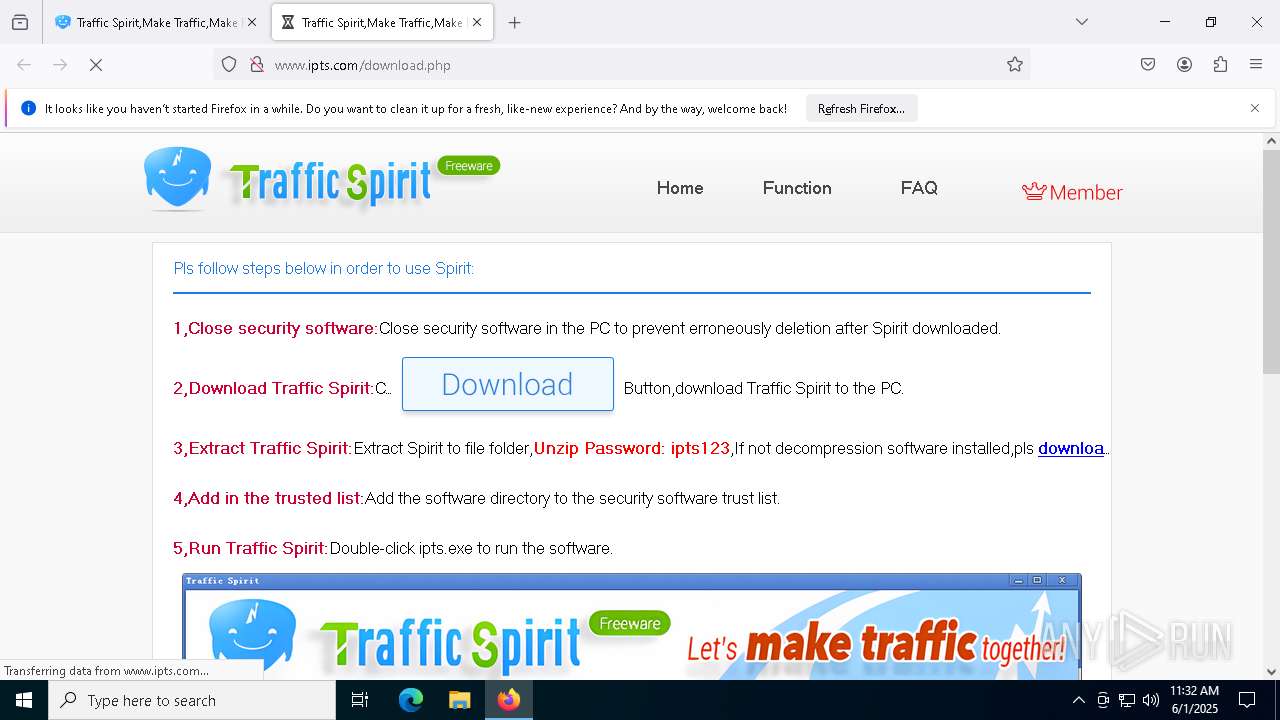
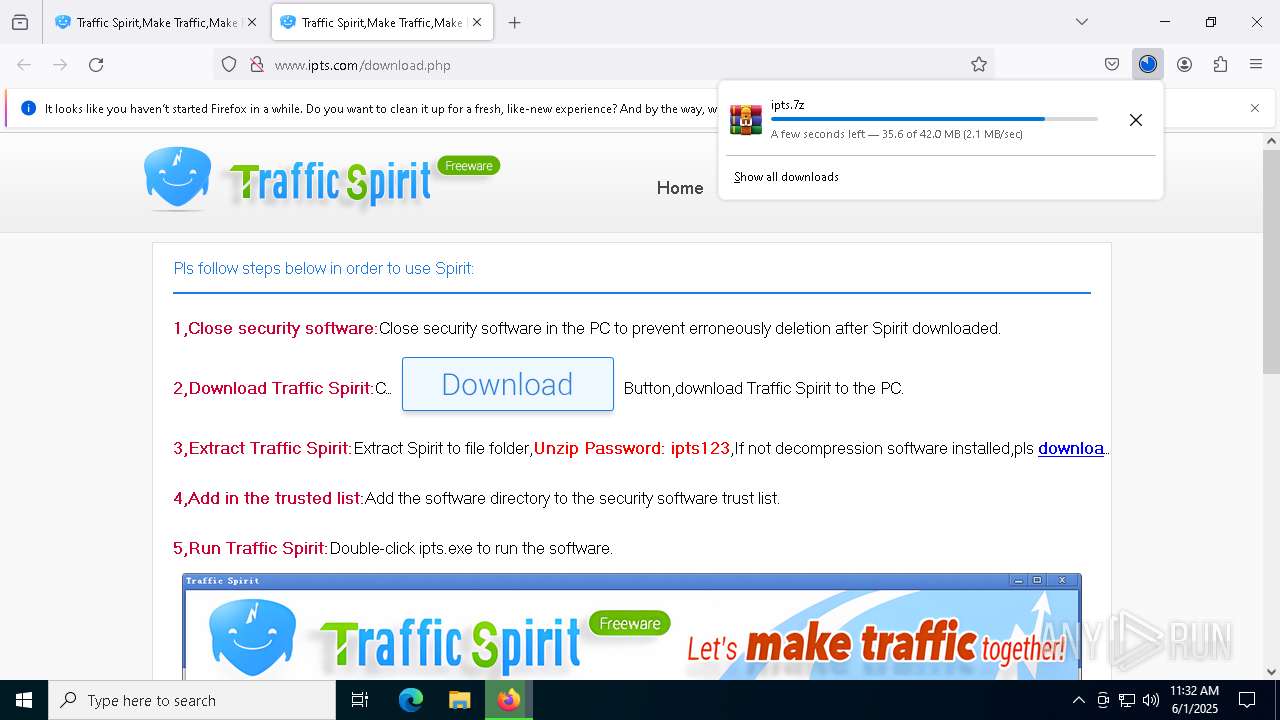
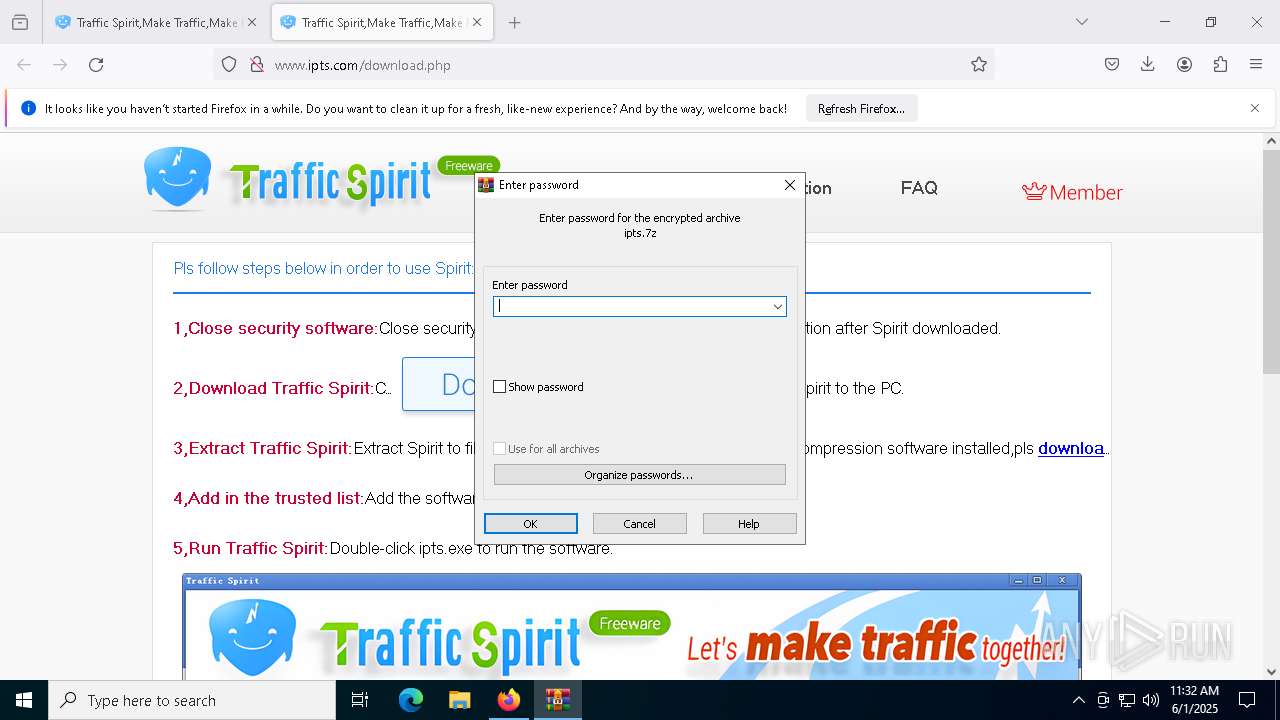
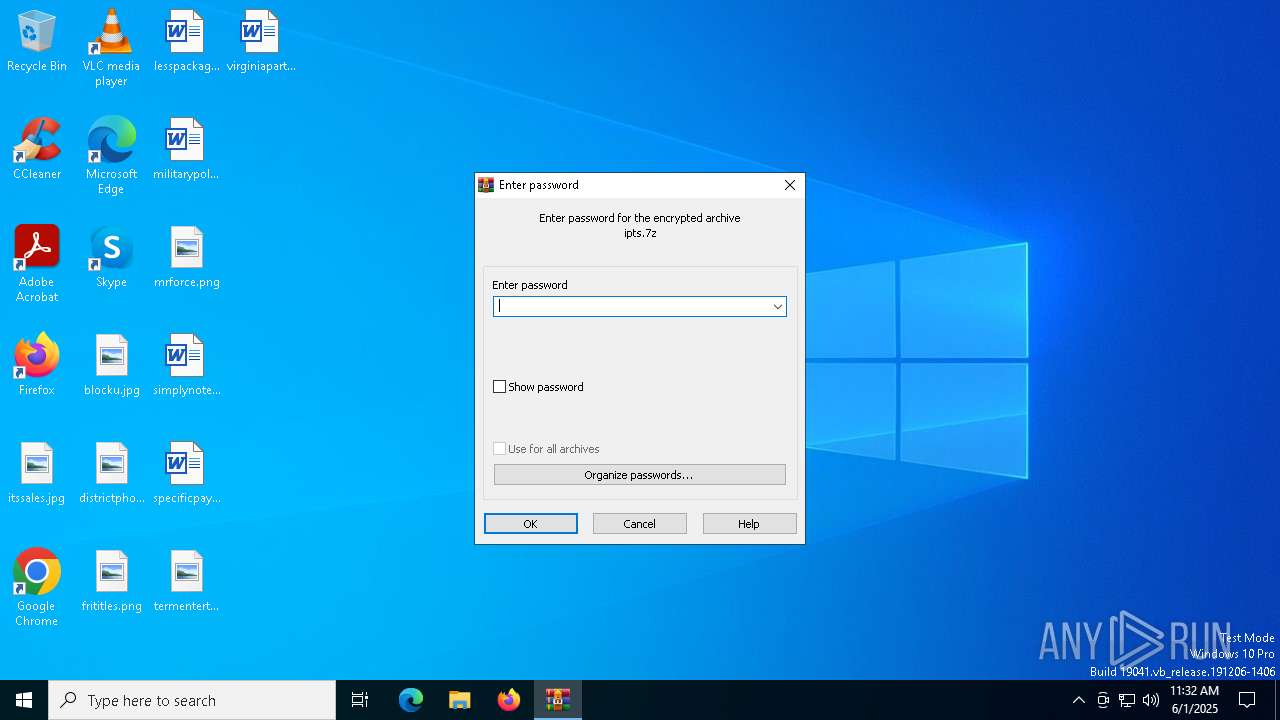
| URL: | http://www.ipts.com/ |
| Full analysis: | https://app.any.run/tasks/7c80265c-77aa-426b-b1a8-8eef9912e827 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | June 01, 2025, 11:32:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0E72A6EA889827BFA1E618E6B46AE8FD |
| SHA1: | DF9A6D6D6DB1EB6581A57E3598DCA830110093E4 |
| SHA256: | EF87EDB74ACAFBFF0B327D864081CC7EC133497FA174A957AC53453EA58FF7C9 |
| SSDEEP: | 3:N1KJS4rLdIKn:Cc4rLd3 |
MALICIOUS
Changes the autorun value in the registry
- ipts.exe (PID: 8000)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 6824)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6824)
Application launched itself
- ipts.exe (PID: 8000)
- ipts.exe (PID: 8136)
Process requests binary or script from the Internet
- ipts.exe (PID: 4996)
- ipts.exe (PID: 5736)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ipts.exe (PID: 5736)
There is functionality for taking screenshot (YARA)
- ipts.exe (PID: 8000)
- ipts.exe (PID: 8092)
Reads security settings of Internet Explorer
- ipts.exe (PID: 8136)
Block-list domains
- ipts.exe (PID: 5736)
INFO
Application launched itself
- firefox.exe (PID: 6740)
- firefox.exe (PID: 7812)
Launch of the file from Downloads directory
- firefox.exe (PID: 6740)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6824)
Manual execution by a user
- WinRAR.exe (PID: 6824)
- ipts.exe (PID: 8000)
Reads the computer name
- ipts.exe (PID: 8000)
- ipts.exe (PID: 4996)
- ipts.exe (PID: 8136)
- ipts.exe (PID: 8092)
- ipts.exe (PID: 5736)
- ipts.exe (PID: 7388)
- ipts.exe (PID: 5216)
- ipts.exe (PID: 7500)
Checks supported languages
- ipts.exe (PID: 8000)
- ipts.exe (PID: 4996)
- ipts.exe (PID: 3828)
- ipts.exe (PID: 4336)
- ipts.exe (PID: 7444)
- ipts.exe (PID: 8092)
- ipts.exe (PID: 5736)
- ipts.exe (PID: 7544)
- ipts.exe (PID: 8136)
- ipts.exe (PID: 5056)
- ipts.exe (PID: 4728)
- ipts.exe (PID: 7184)
- ipts.exe (PID: 776)
- ipts.exe (PID: 5776)
- ipts.exe (PID: 3140)
- ipts.exe (PID: 7908)
- ipts.exe (PID: 5548)
- ipts.exe (PID: 7804)
- ipts.exe (PID: 7388)
- ipts.exe (PID: 8080)
- ipts.exe (PID: 7484)
- ipts.exe (PID: 760)
- ipts.exe (PID: 2108)
- ipts.exe (PID: 4784)
- ipts.exe (PID: 5216)
- ipts.exe (PID: 7560)
- ipts.exe (PID: 6644)
- ipts.exe (PID: 2780)
- ipts.exe (PID: 2340)
- ipts.exe (PID: 5072)
- ipts.exe (PID: 8024)
- ipts.exe (PID: 7500)
- ipts.exe (PID: 6800)
- ipts.exe (PID: 7744)
- ipts.exe (PID: 7580)
- ipts.exe (PID: 7820)
- ipts.exe (PID: 3332)
- ipts.exe (PID: 2652)
The sample compiled with english language support
- WinRAR.exe (PID: 6824)
Launch of the file from Registry key
- ipts.exe (PID: 8000)
Reads CPU info
- ipts.exe (PID: 8000)
Reads the machine GUID from the registry
- ipts.exe (PID: 8000)
- ipts.exe (PID: 8136)
- ipts.exe (PID: 7500)
Process checks computer location settings
- ipts.exe (PID: 4336)
- ipts.exe (PID: 8000)
- ipts.exe (PID: 7544)
- ipts.exe (PID: 8136)
- ipts.exe (PID: 5056)
- ipts.exe (PID: 776)
- ipts.exe (PID: 4728)
- ipts.exe (PID: 7908)
- ipts.exe (PID: 7184)
- ipts.exe (PID: 5776)
- ipts.exe (PID: 5548)
- ipts.exe (PID: 3140)
- ipts.exe (PID: 7804)
- ipts.exe (PID: 7484)
- ipts.exe (PID: 8080)
- ipts.exe (PID: 760)
- ipts.exe (PID: 4784)
- ipts.exe (PID: 2108)
- ipts.exe (PID: 7560)
- ipts.exe (PID: 2780)
- ipts.exe (PID: 6644)
- ipts.exe (PID: 5072)
- ipts.exe (PID: 8024)
- ipts.exe (PID: 2340)
- ipts.exe (PID: 7580)
- ipts.exe (PID: 6800)
- ipts.exe (PID: 7744)
- ipts.exe (PID: 7820)
- ipts.exe (PID: 3332)
- ipts.exe (PID: 2652)
Create files in a temporary directory
- ipts.exe (PID: 8136)
- ipts.exe (PID: 4996)
- ipts.exe (PID: 8000)
Reads the software policy settings
- slui.exe (PID: 7012)
- slui.exe (PID: 7376)
Checks proxy server information
- slui.exe (PID: 7376)
Creates files or folders in the user directory
- ipts.exe (PID: 7500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
194
Monitored processes
68
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
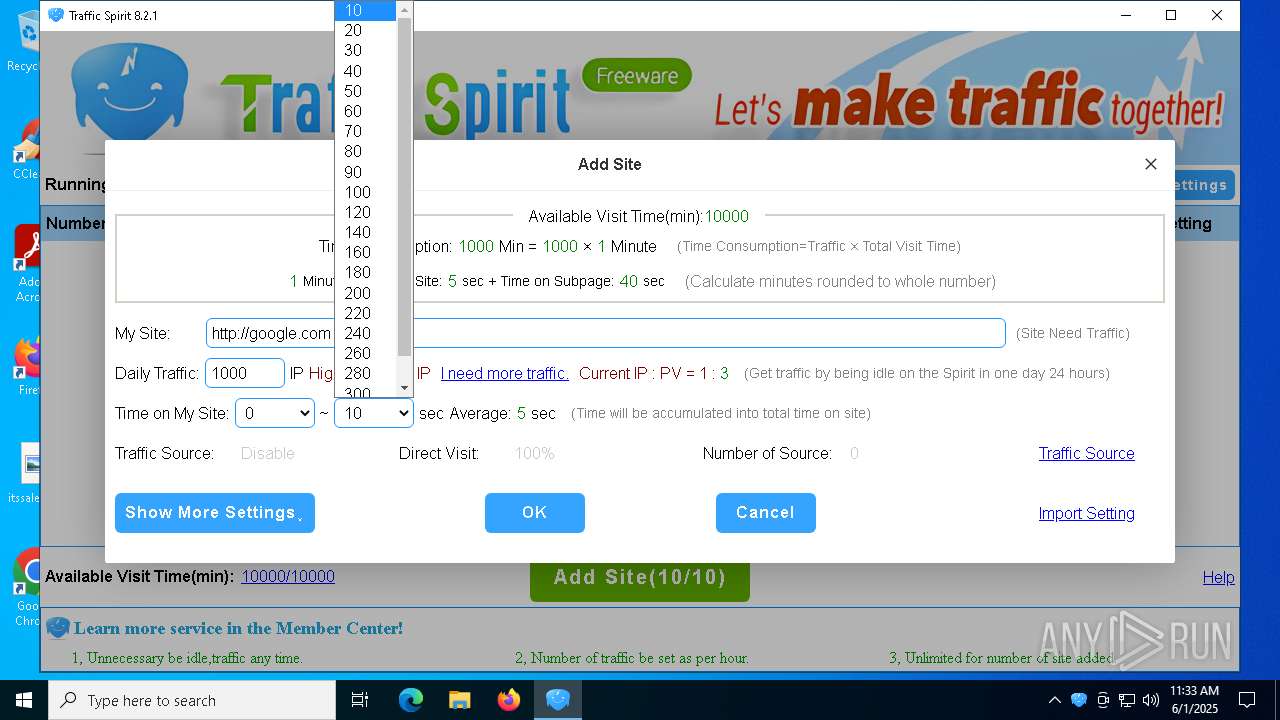
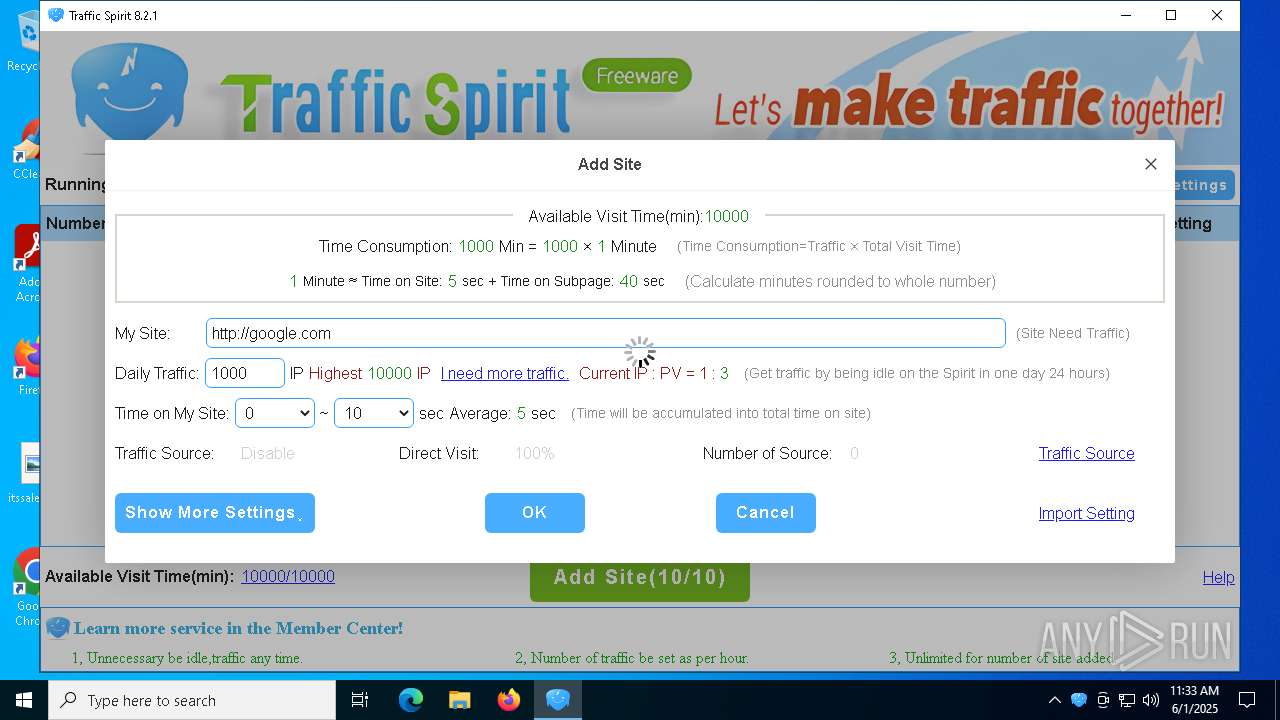
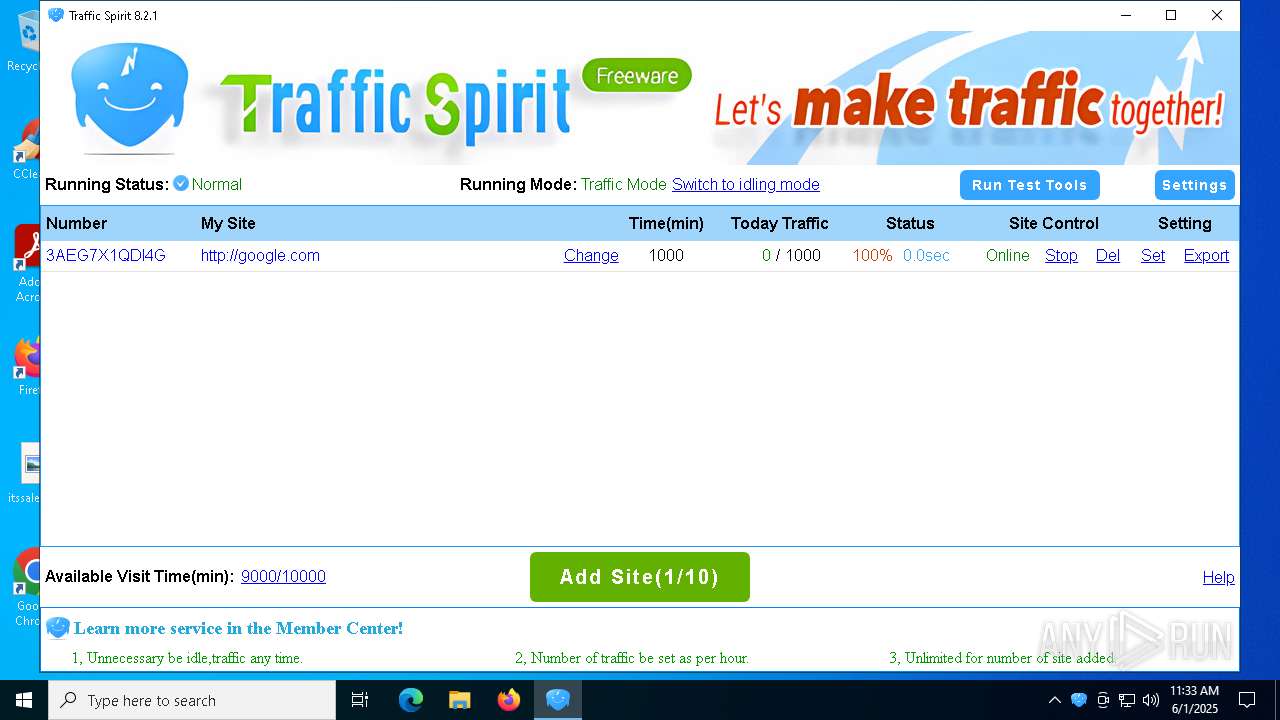
| 448 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=38 --mojo-platform-channel-handle=2992 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.12.28.45 Modules
| |||||||||||||||
| 760 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=4304 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.12.28.45 Modules
| |||||||||||||||
| 776 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=3272 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.12.28.45 Modules
| |||||||||||||||
| 832 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --mojo-platform-channel-handle=4776 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Version: 2023.12.28.45 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=46 --mojo-platform-channel-handle=5004 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.12.28.45 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4276 -childID 2 -isForBrowser -prefsHandle 4268 -prefMapHandle 4264 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1268 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7622d3f9-b1a5-42ff-837d-5eac6e340329} 6740 "\\.\pipe\gecko-crash-server-pipe.6740" 2261c1dd850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1276 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2168 -parentBuildID 20240213221259 -prefsHandle 2160 -prefMapHandle 2148 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {28a9cf6b-b874-4135-a701-9818378931d6} 6740 "\\.\pipe\gecko-crash-server-pipe.6740" 22606f80f10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=3152 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.12.28.45 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Users\admin\Desktop\ipts.exe" --type=renderer --ub-type=urltask --image-replacement --disable-databases --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --mojo-platform-channel-handle=4776 --field-trial-handle=1560,i,15285572966555549200,8480376650128010593,131072 /prefetch:1 | C:\Users\admin\Desktop\ipts.exe | — | ipts.exe | |||||||||||
User: admin Company: Spiritsoft(www.ipts.com) Integrity Level: LOW Description: Traffic Spirit(http://www.ipts.com) Exit code: 0 Version: 2023.12.28.45 Modules
| |||||||||||||||
Total events
20 204
Read events
20 181
Write events
23
Delete events
0
Modification events
| (PID) Process: | (6740) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\ipts.7z | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
218
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6740 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:22DA36CA5BA1D055ADE237F52DC825A7 | SHA256:7438A5D5298BFA0ABAB51E6B35EAC0F26B830BCEFBDBEB5F07721DBA34F89E0D | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:036FFBEDFCA10E0B90C23FE8E3585FE8 | SHA256:B24AAED66AE8DF29CE5634B1CCCAD637BD3D7E9745C2421E9DF34E816C738D2A | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:D0D36E6CCAB6716E7B0B484AEC6A0D10 | SHA256:51CC2BD8BB43532E6E70FFD639A53527749FFEFAB2F2AE87A78A9FE55ABB796F | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:EC5A105065210091C1C00742B07B288C | SHA256:3C9443149790401EC056C208B0B14856D94E6B120BFC7F8A2AD4736A3663D41B | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:7C26361B925B58E3BC4430A6D4743D60 | SHA256:9469C77F443182EAC0026A4EBCD1EBE04E6790560CE88563CFC646A96CC3A78D | |||
| 6740 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:C09FF302D57C404B61E6A89B0B9F36E7 | SHA256:6A5B4F82595799346D0E501FE6CC8629E0FD6ED27B74D0E6CB5073DDB2E3C40B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
477
TCP/UDP connections
1 153
DNS requests
651
Threats
74
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6740 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6740 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6740 | firefox.exe | POST | 200 | 2.22.242.121:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6740 | firefox.exe | POST | 200 | 2.22.242.225:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6740 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
6740 | firefox.exe | POST | 200 | 2.22.242.225:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6740 | firefox.exe | GET | 200 | 47.88.10.215:80 | http://www.ipts.com/ | unknown | — | — | unknown |
6740 | firefox.exe | POST | 200 | 2.22.242.121:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7868 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6740 | firefox.exe | 47.88.10.215:80 | www.ipts.com | Alibaba US Technology Co., Ltd. | US | suspicious |
6740 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
6740 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6740 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.ipts.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
2196 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (t .co) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
5736 | ipts.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M1 |