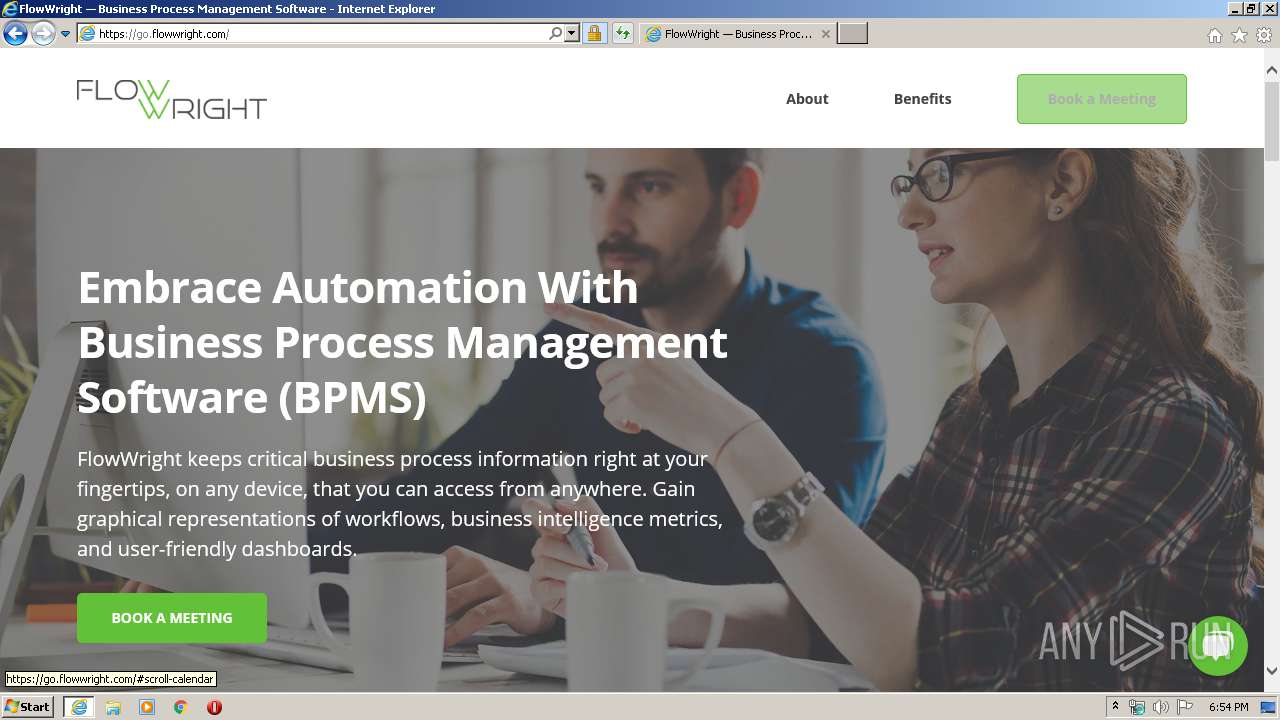
| URL: | https://t.sidekickopen80.com/s1t/c/5/f18dQhb0S7lM8dDMPbW2n0x6l2B9nMJN7t5XWPfhMynW2zq3QM7fctTTW56dQpB9dRjcT102?te=W3R5hFj4cm2zwW3P4yCY3ZZpyfW49M8js4fdHZS348S2&si=8000000002408326&pi=ce91cf627561a433a3df953392ddf779 |
| Full analysis: | https://app.any.run/tasks/fb3f9264-7dc7-4f42-9dd3-54d74058c689 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 18:53:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A810F72C288C720D81D6695CD828EE7A |
| SHA1: | 50A5AACB4F88D9BCFBEAD920839C960070928A1F |
| SHA256: | EF7BAE427C07B35D61611C252F2C8AC6AA9ABB4289C94DB667C0F91532C28466 |
| SSDEEP: | 6:25YputADq23/0vhzh5MGsicimDcsXCGeDF3zK:2upum3/0vhzh2Gb3rGeDhK |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 3000)
Reads Internet Cache Settings
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 3000)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2620)
Reads internet explorer settings
- iexplore.exe (PID: 2620)
Creates files in the user directory
- iexplore.exe (PID: 2620)
Reads settings of System Certificates
- iexplore.exe (PID: 2620)
- iexplore.exe (PID: 3000)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3000)
Changes settings of System certificates
- iexplore.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2620 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3000 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Internet Explorer\iexplore.exe" https://t.sidekickopen80.com/s1t/c/5/f18dQhb0S7lM8dDMPbW2n0x6l2B9nMJN7t5XWPfhMynW2zq3QM7fctTTW56dQpB9dRjcT102?te=W3R5hFj4cm2zwW3P4yCY3ZZpyfW49M8js4fdHZS348S2&si=8000000002408326&pi=ce91cf627561a433a3df953392ddf779 | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
7 174
Read events
1 486
Write events
3 849
Delete events
1 839
Modification events
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1190484382 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796008 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
128
Text files
111
Unknown types
74
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2620 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7C6C.tmp | — | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7C6D.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\FL6PF4LG.txt | — | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6AF4EE75E3A4ABA658C0087EB9A0BB5B_41F6E9BEA3BF3EA170E2716F884CDA93 | der | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PGXAICWX.txt | text | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9EC3B71635F8BA3FC68DE181A104A0EF_F6C39EF89D8A3A72327D8412589658B2 | der | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\WQ37RWQU.txt | text | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:— | SHA256:— | |||
| 2620 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\IACLBX40.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
132
DNS requests
55
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2620 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 312 b | whitelisted |
2620 | iexplore.exe | GET | 200 | 13.35.254.192:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2620 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 312 b | whitelisted |
2620 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2620 | iexplore.exe | GET | 200 | 2.16.186.35:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2620 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2620 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgTady6BaSsA6lHemXkbVBO8pw%3D%3D | unknown | der | 527 b | whitelisted |
2620 | iexplore.exe | GET | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDhKaVxWCYaNQgAAAAALC5%2B | US | der | 472 b | whitelisted |
2620 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQDsUdLxyDpZXHr8qC0JE3XU | US | der | 280 b | whitelisted |
2620 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCHiXrffKxDLI | US | der | 1.73 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2620 | iexplore.exe | 104.16.228.74:443 | t.sidekickopen80.com | Cloudflare Inc | US | shared |
2620 | iexplore.exe | 151.139.128.14:80 | ocsp.trust-provider.com | Highwinds Network Group, Inc. | US | suspicious |
2620 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2620 | iexplore.exe | 104.16.249.5:443 | eventtracking.hubspot.com | Cloudflare Inc | US | shared |
3000 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2620 | iexplore.exe | 54.93.101.66:443 | go.flowwright.com | Amazon.com, Inc. | DE | malicious |
2620 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2620 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2620 | iexplore.exe | 13.35.253.25:443 | builder-assets.unbounce.com | — | US | suspicious |
2620 | iexplore.exe | 172.217.23.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t.sidekickopen80.com |
| whitelisted |
ocsp.trust-provider.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |
eventtracking.hubspot.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.flowwright.com |
| malicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |