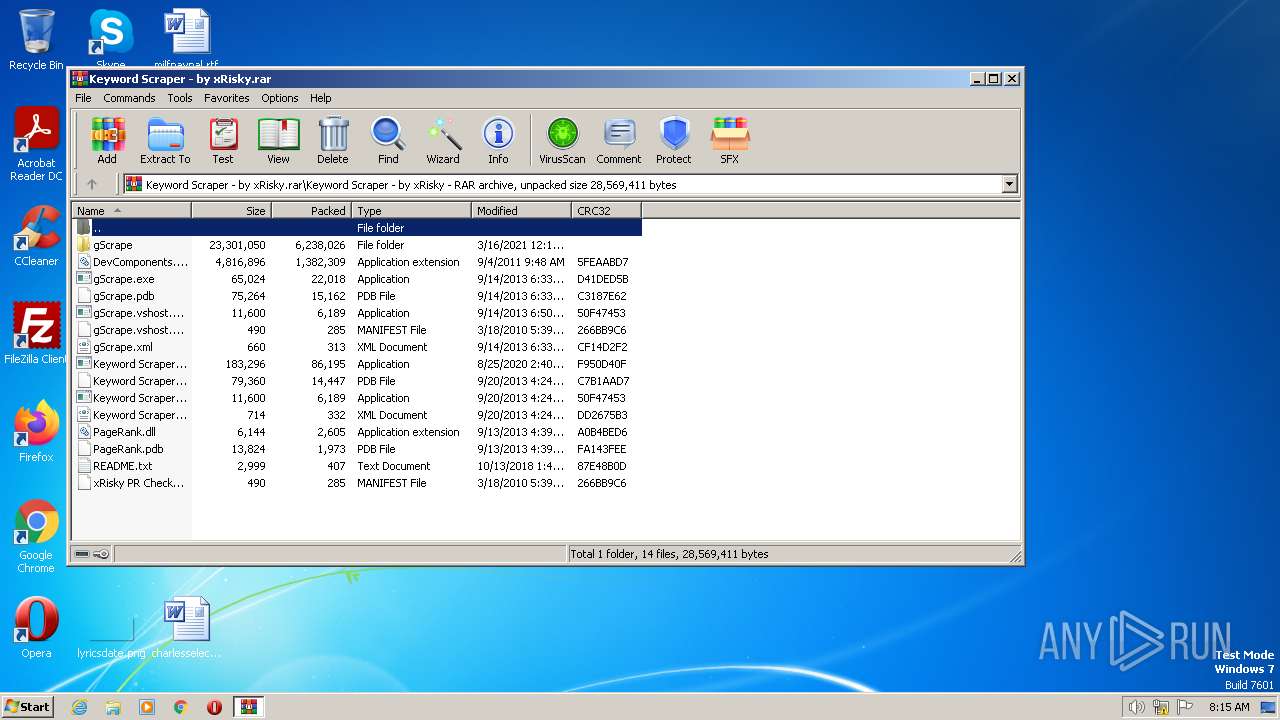
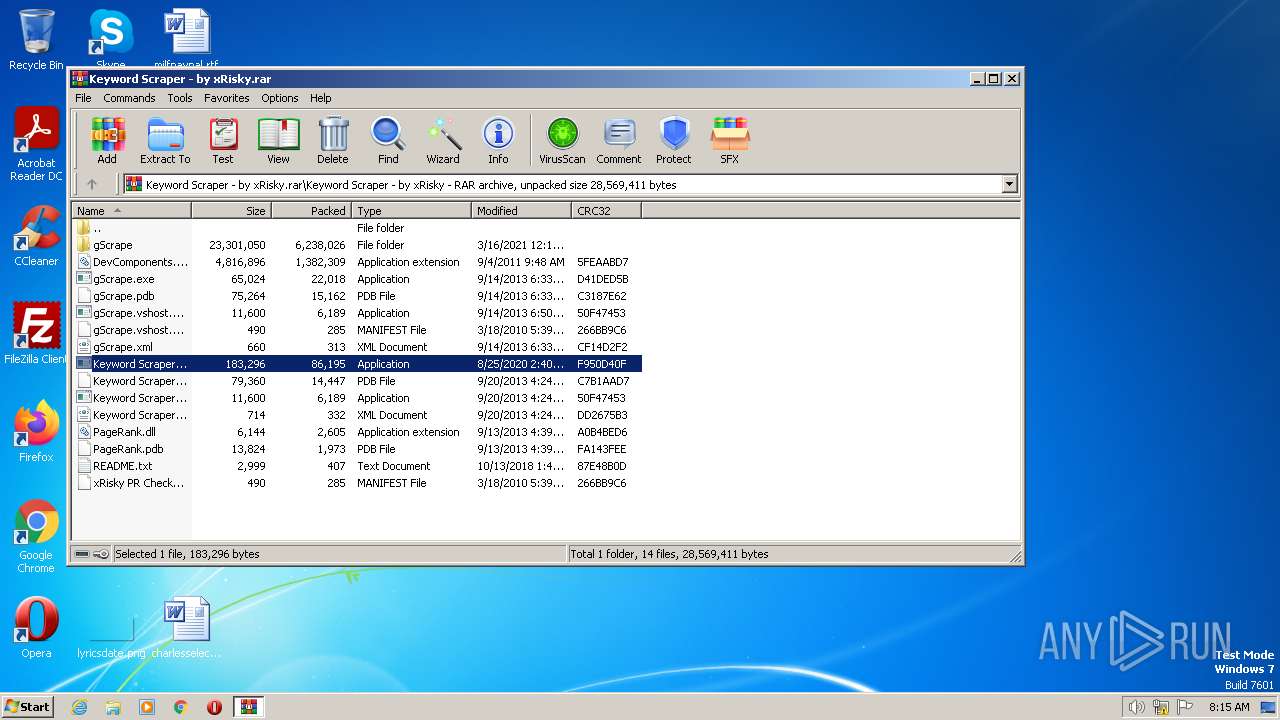
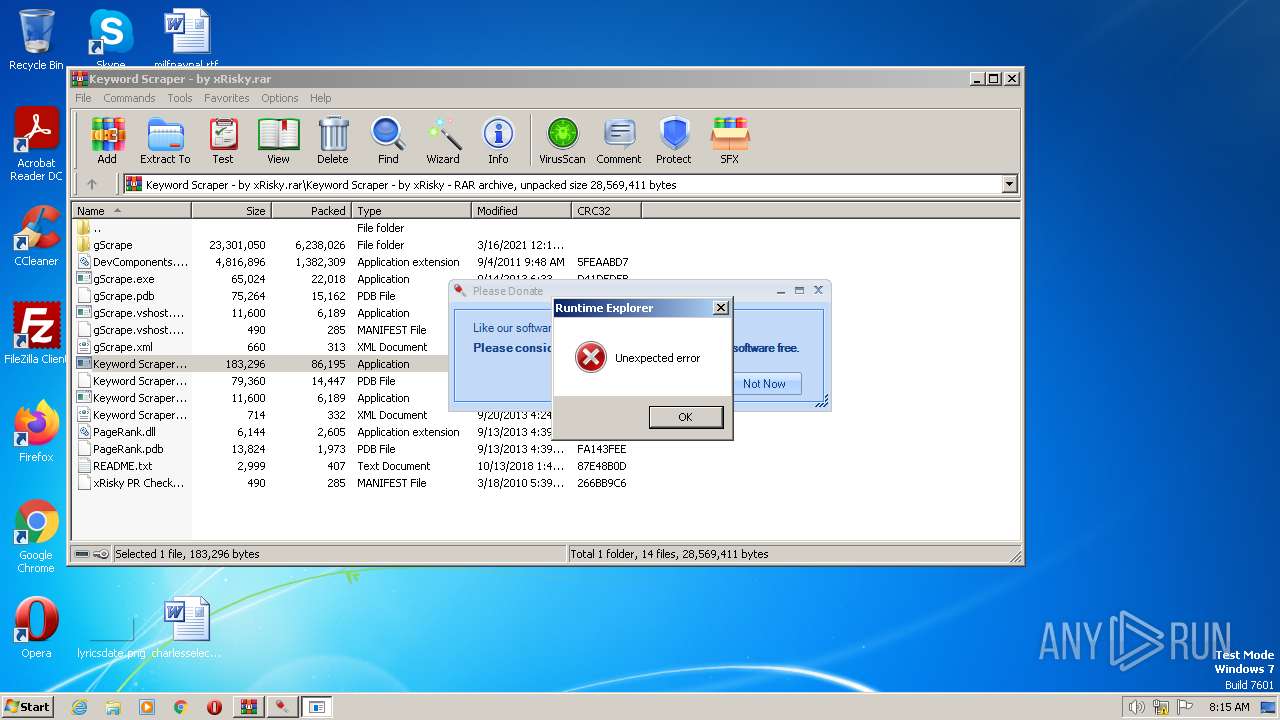
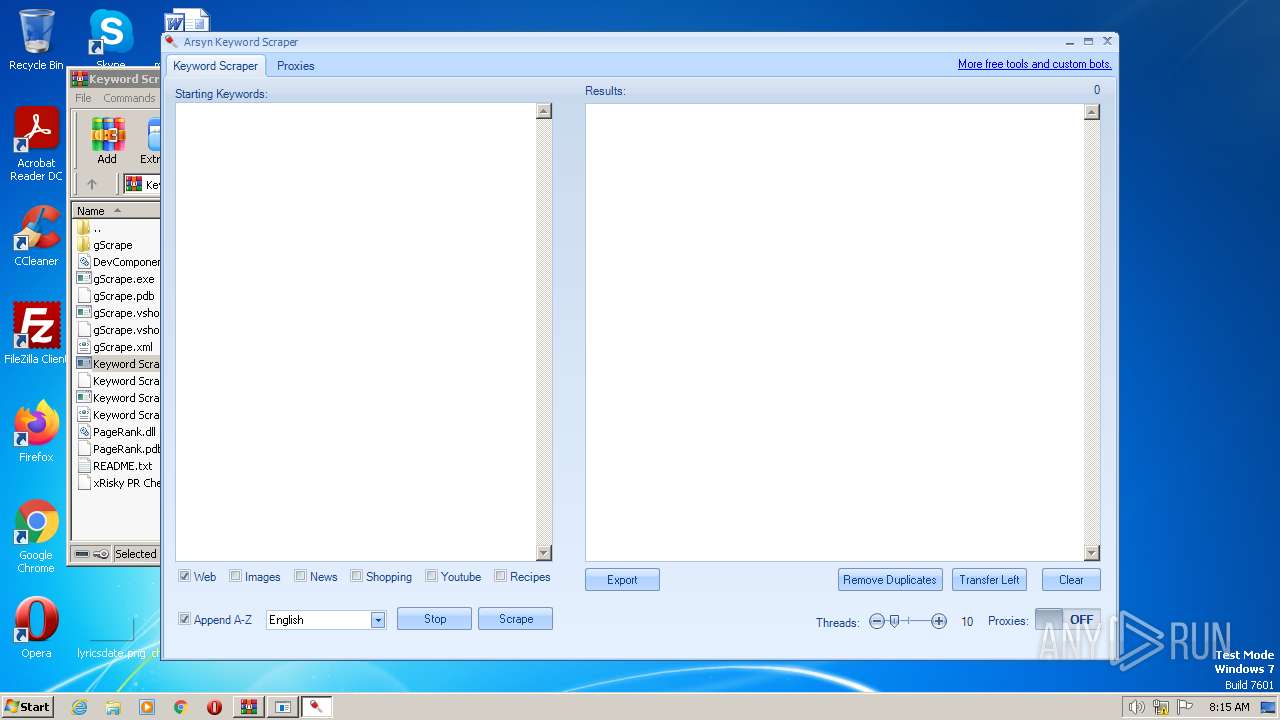
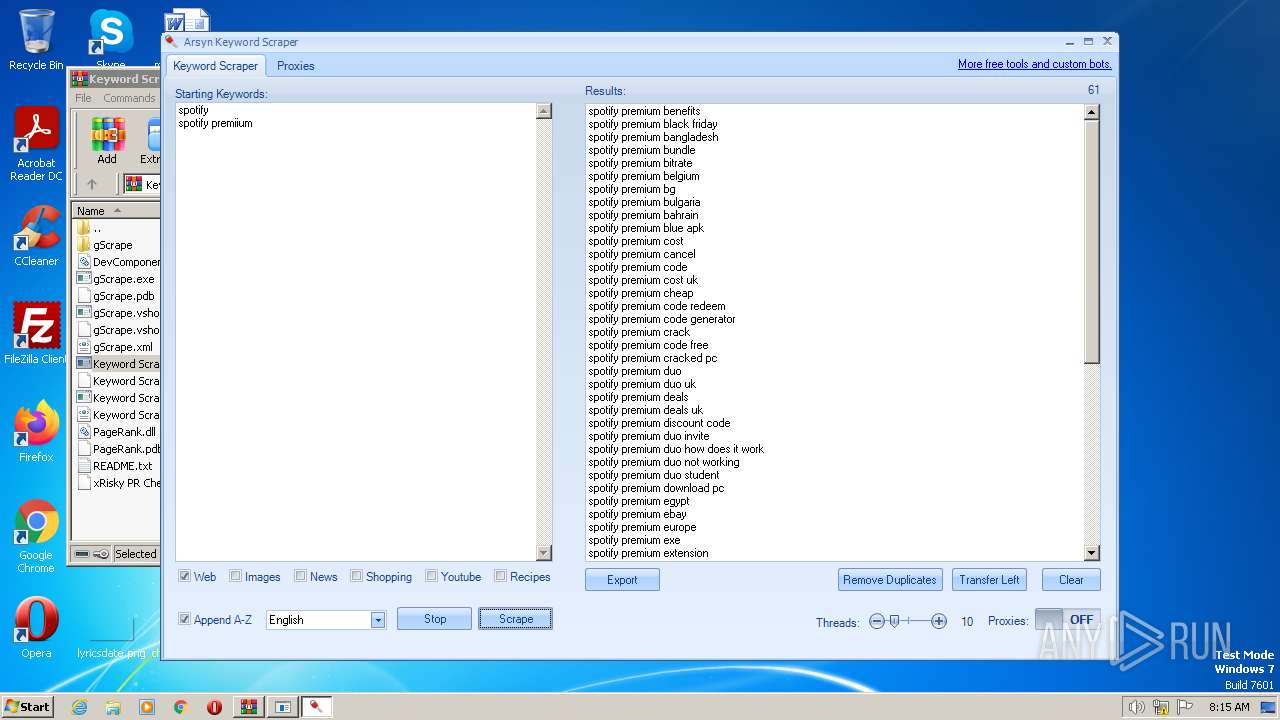
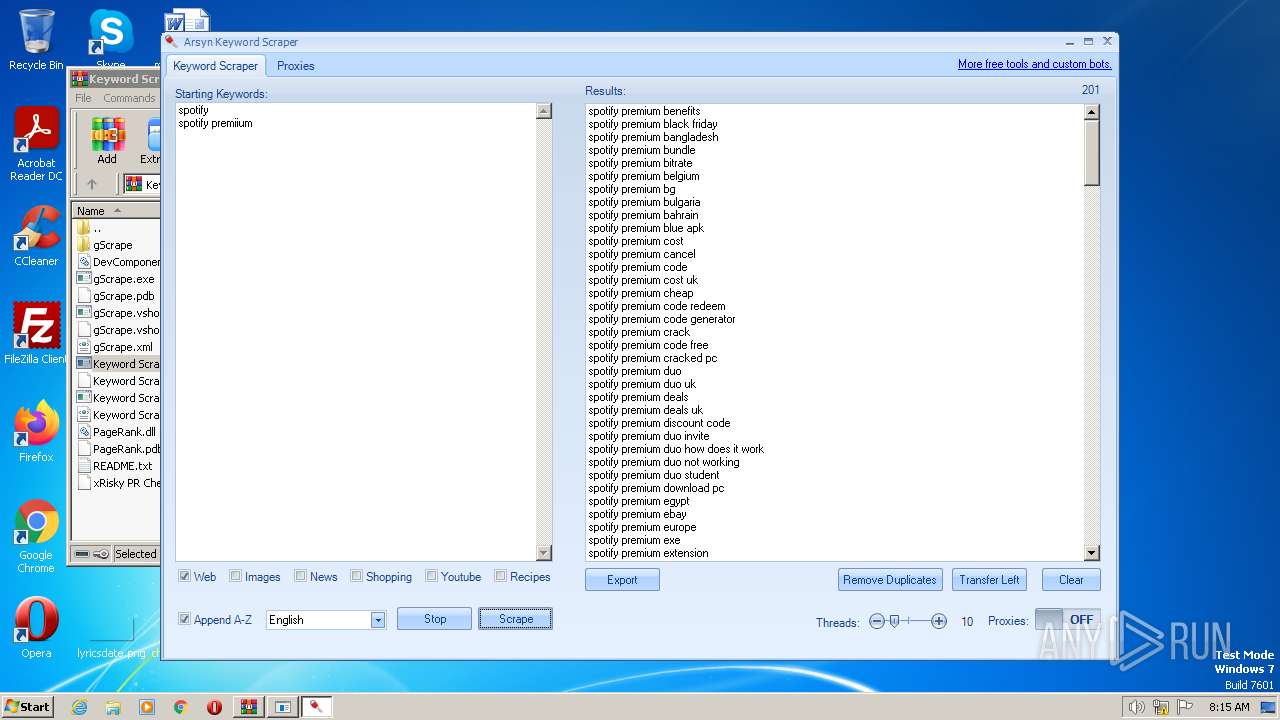
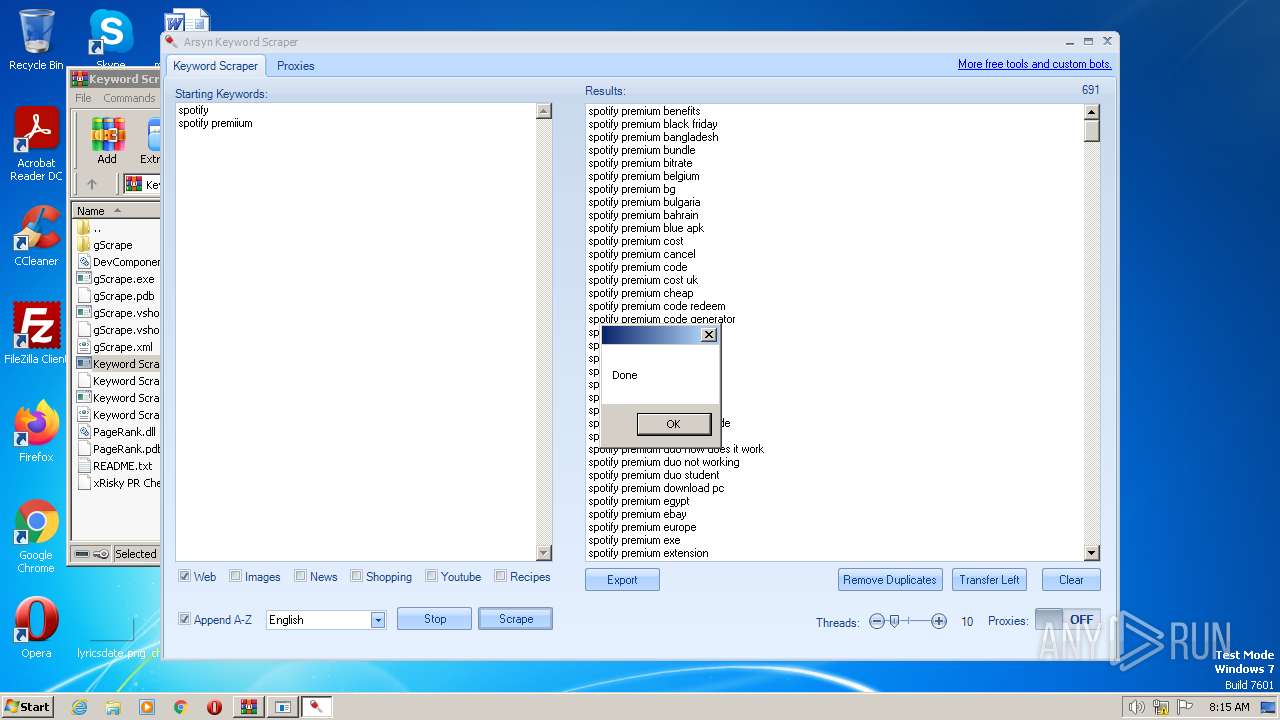
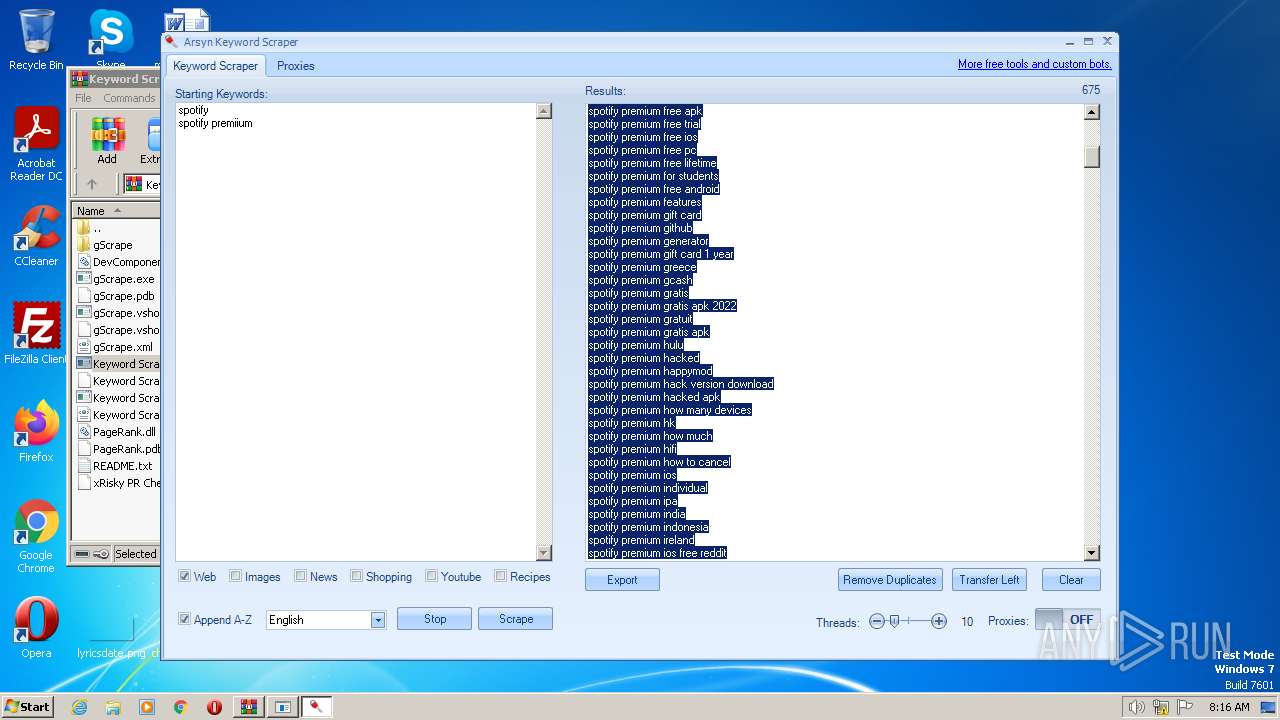
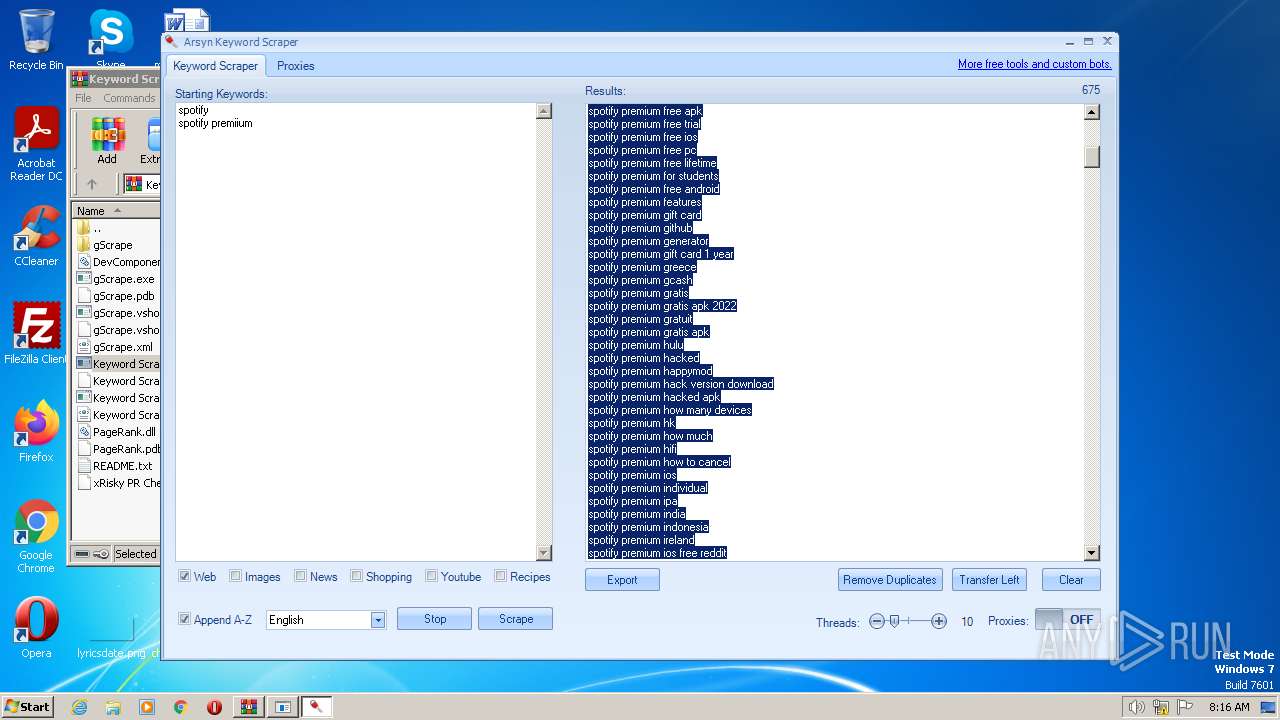
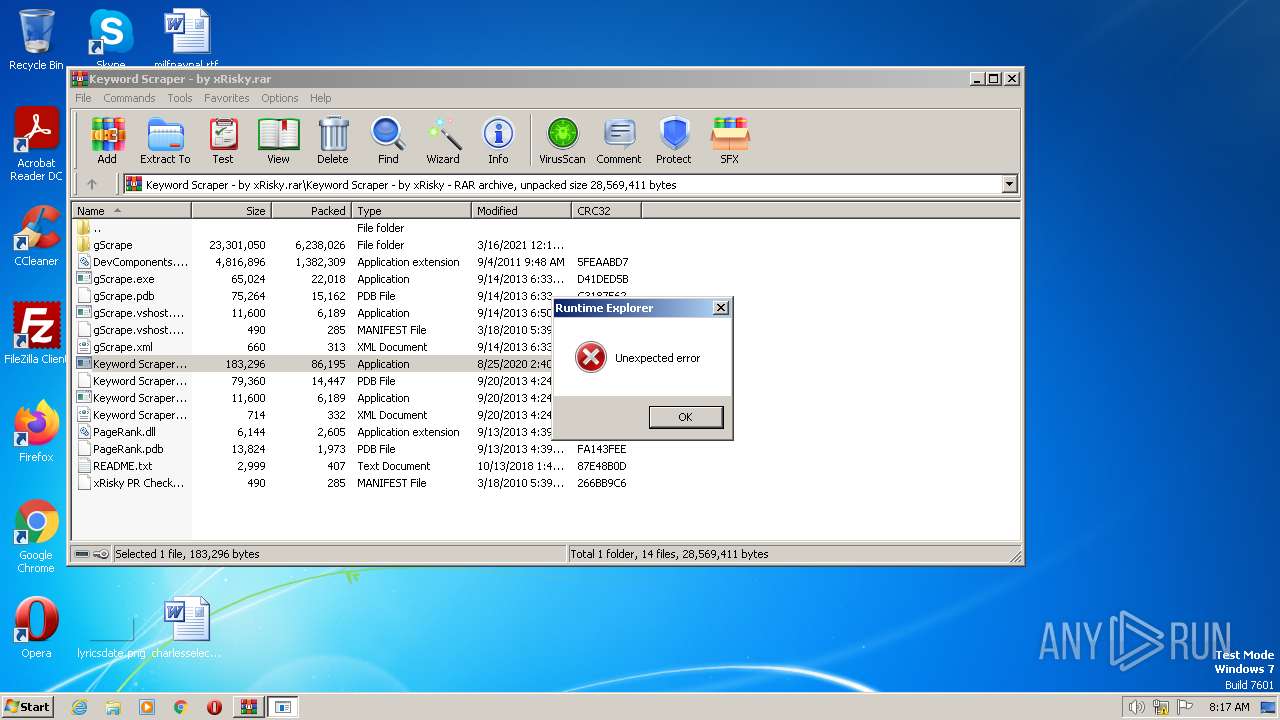
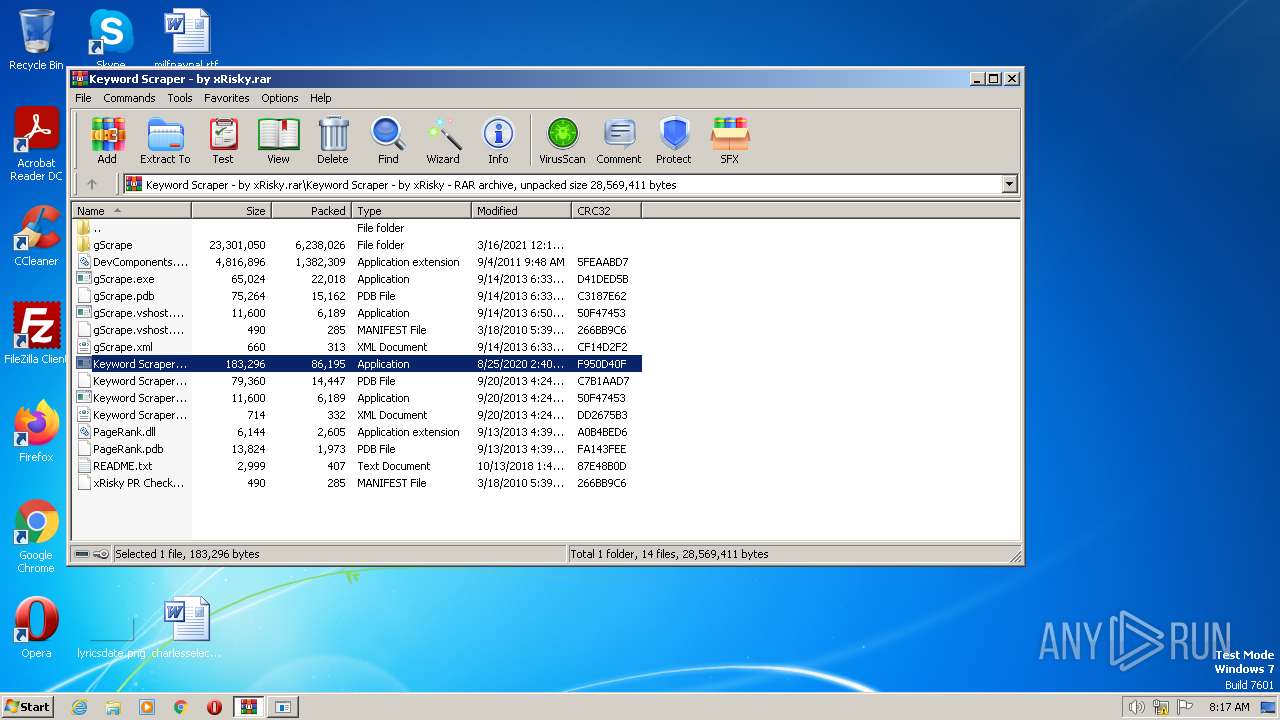
| File name: | Keyword Scraper - by xRisky.rar |
| Full analysis: | https://app.any.run/tasks/006af97f-be37-42c2-83bd-0d0abc4b15f3 |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2023, 07:14:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 832AA1F6C3AD0BA9231CDB6D6D953F6D |
| SHA1: | 58E660D541B542CA3293FC27273F62E90003901A |
| SHA256: | EF5A9F70E6479173CCF4C4067709F95D79B3E9D3BEF0E60382F071591F748AEB |
| SSDEEP: | 196608:OtSDpjNFNcum0tSDpi93sU923HYChrn8YgvFYHr:fjNL+43sUs34CF8vvGHr |
MALICIOUS
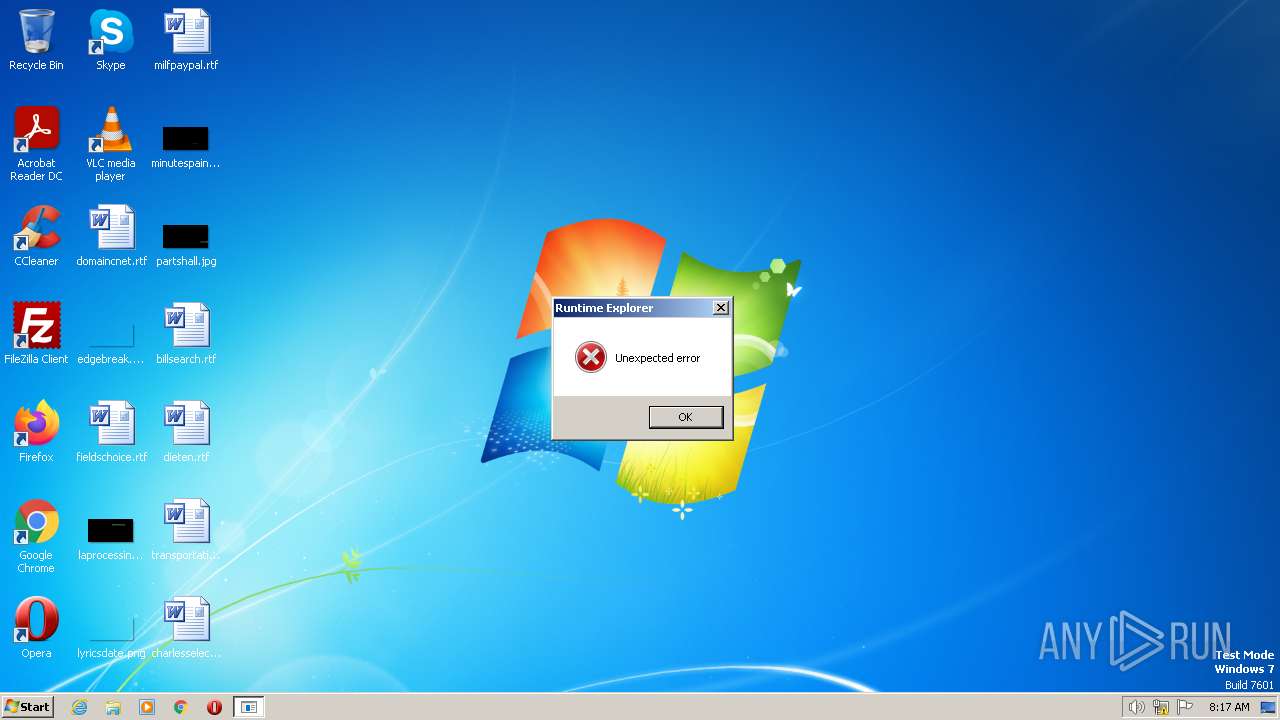
Loads dropped or rewritten executable
- Launcher.exe (PID: 2220)
- Scraper.exe (PID: 3976)
Application was dropped or rewritten from another process
- Scraper.exe (PID: 3976)
- Keyword Scraper v1.exe (PID: 3444)
- Launcher.exe (PID: 2220)
- Runtime Explorer.exe (PID: 2936)
- Secure System Shell.exe (PID: 3732)
- Windows Services.exe (PID: 1828)
- Runtime Explorer.exe (PID: 3496)
- Runtime Explorer.exe (PID: 3744)
- Runtime Explorer.exe (PID: 3328)
Adds path to the Windows Defender exclusion list
- Launcher.exe (PID: 2220)
Create files in the Startup directory
- Launcher.exe (PID: 2220)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4060)
- Launcher.exe (PID: 2220)
Reads the Internet Settings
- Keyword Scraper v1.exe (PID: 3444)
- Launcher.exe (PID: 2220)
- powershell.exe (PID: 3072)
- Windows Services.exe (PID: 1828)
- Scraper.exe (PID: 3976)
Script adds exclusion path to Windows Defender
- Launcher.exe (PID: 2220)
Starts POWERSHELL.EXE for commands execution
- Launcher.exe (PID: 2220)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3072)
Executable content was dropped or overwritten
- Launcher.exe (PID: 2220)
Reads Internet Explorer settings
- Scraper.exe (PID: 3976)
INFO
Checks supported languages
- Keyword Scraper v1.exe (PID: 3444)
- Launcher.exe (PID: 2220)
- Scraper.exe (PID: 3976)
- Secure System Shell.exe (PID: 3732)
- Windows Services.exe (PID: 1828)
- Runtime Explorer.exe (PID: 2936)
- Runtime Explorer.exe (PID: 3496)
- Runtime Explorer.exe (PID: 3744)
- Runtime Explorer.exe (PID: 3328)
Reads the computer name
- Launcher.exe (PID: 2220)
- Keyword Scraper v1.exe (PID: 3444)
- Windows Services.exe (PID: 1828)
- Secure System Shell.exe (PID: 3732)
- Scraper.exe (PID: 3976)
The process checks LSA protection
- Launcher.exe (PID: 2220)
- Keyword Scraper v1.exe (PID: 3444)
- Scraper.exe (PID: 3976)
- Windows Services.exe (PID: 1828)
- Runtime Explorer.exe (PID: 2936)
- Runtime Explorer.exe (PID: 3496)
- Runtime Explorer.exe (PID: 3744)
- Runtime Explorer.exe (PID: 3328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4060)
Reads the machine GUID from the registry
- Launcher.exe (PID: 2220)
- Scraper.exe (PID: 3976)
- Runtime Explorer.exe (PID: 2936)
- Runtime Explorer.exe (PID: 3496)
- Runtime Explorer.exe (PID: 3744)
- Runtime Explorer.exe (PID: 3328)
Creates files or folders in the user directory
- Launcher.exe (PID: 2220)
Create files in a temporary directory
- Runtime Explorer.exe (PID: 2936)
- Runtime Explorer.exe (PID: 3496)
- Runtime Explorer.exe (PID: 3744)
- Runtime Explorer.exe (PID: 3328)
Reads Environment values
- Scraper.exe (PID: 3976)
Manual execution by a user
- chrome.exe (PID: 3624)
Application launched itself
- chrome.exe (PID: 3624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
84
Monitored processes
38
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1408 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2676 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2988 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1968 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2968 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3792 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2292 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1828 | "C:\Windows\IMF\Windows Services.exe" {Arguments If Needed} | C:\Windows\IMF\Windows Services.exe | — | Launcher.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1844 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --field-trial-handle=1032,1226719744569892035,11375226025914254008,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=2992 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
27 149
Read events
26 821
Write events
322
Delete events
6
Modification events
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4060) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
28
Suspicious files
164
Text files
108
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
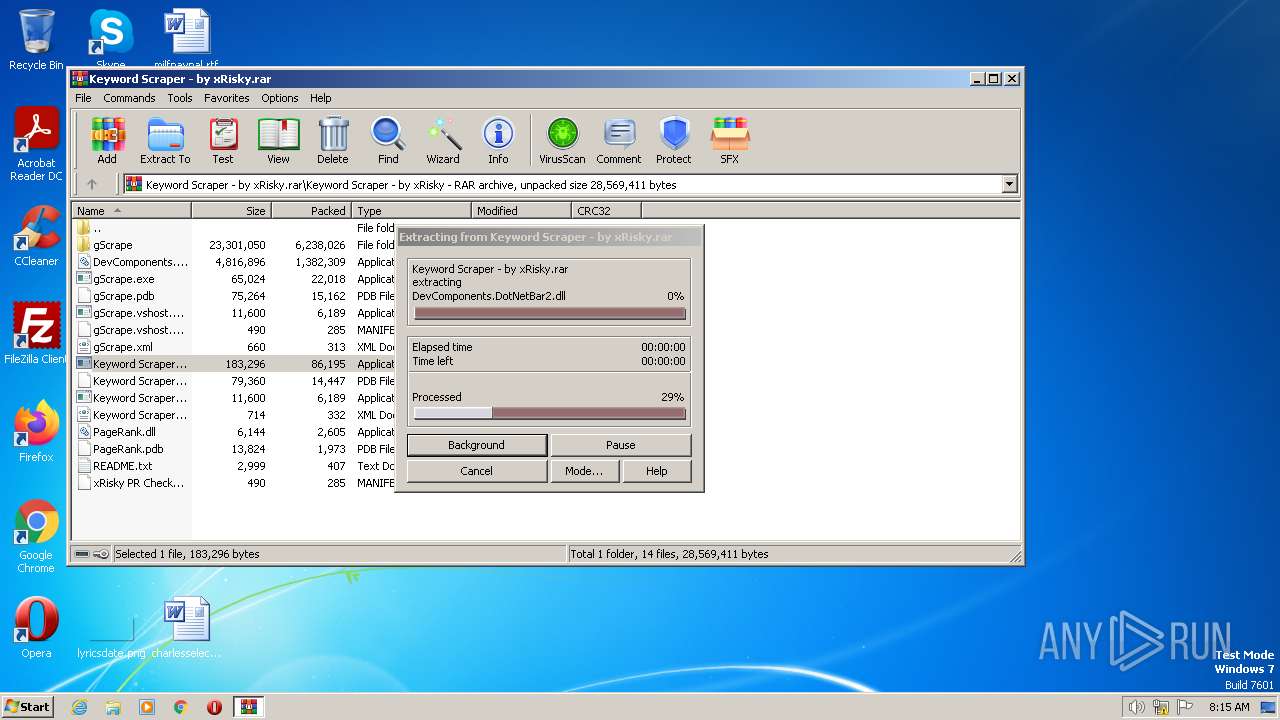
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\DevComponents.DotNetBar2.dll | executable | |
MD5:D068CE38F5F9CAED1E63FFB1169EDE92 | SHA256:08C17E74BE6CEEE14634C12BCEE4985490620C2C39986D2EFC367CC86F3339C7 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\bcastdvr.proxy.dll | executable | |
MD5:EB1E9D853B3A71F8DB7DE8A1EE04A757 | SHA256:610AB0B7BEE791A97E1EBB78A71897ADCDAD3E1DB53598A1E1FBA0B3CAE624C3 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\gScrape.pdb | binary | |
MD5:7C7A79CCA57F887A259ED60F8F69C2C8 | SHA256:D523F3EB0C47EBDE7743AE30E2ACEA92151BD1472DCA7407F4BE525E6B6798A2 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\dsregtask.dll | executable | |
MD5:A19DC8EB9BC666E09318BB14752FBBAE | SHA256:77162AD33EE59E96882E02EBAE14CE3A214A687E9E62FF1F93128702B5315C8D | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\d3dx9_27.dll | executable | |
MD5:852EDC778A7A50077694F84D8E601234 | SHA256:A70D571CD675C97C9EEB4A234DBA1D667FFB54EC3BB14DEFB36B3E2F605AE257 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\gScrape.xml | xml | |
MD5:B3087EAAC02A097B9D630145DD25E206 | SHA256:F76BEA9D648CDC50DD1F504F22BEF61A53E8CF03C5255CEE81A50386D4AF7858 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\Keyword Scraper.pdb | pdb | |
MD5:FDDB0FD6E8710CCE14AA559A8BD431D4 | SHA256:AAACE21EA0E8CD94ADC9AACCFE5B8201EB9642FF15FC598DF5D7B6B75869276C | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\gScrape.exe | executable | |
MD5:4A93F404B4D93301D5D29B49148F1C4A | SHA256:AD9A8548ED89FE552F3042D0E666F91A977A263BC1D110C541BA3184AA62866F | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\gScrape.vshost.exe | executable | |
MD5:02BE6D33B1EDBC61C79882D3F556BD8A | SHA256:4C9F9B9DE2FFEEA9CCC6524D05EA5B78A14C1642CECC189FE40E7A57A6C294B3 | |||
| 4060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4060.39589\Keyword Scraper - by xRisky\gScrape\Launcher.exe | executable | |
MD5:C6D4C881112022EB30725978ECD7C6EC | SHA256:0D87B9B141A592711C52E7409EC64DE3AB296CDDC890BE761D9AF57CEA381B32 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
65
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20F | US | xml | 910 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20L | US | xml | 928 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20J | US | xml | 920 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=spotify%20A | US | xml | 818 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20K | US | xml | 884 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20D | US | xml | 924 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20C | US | xml | 897 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20G | US | xml | 911 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20I | US | xml | 904 b | whitelisted |
3976 | Scraper.exe | GET | 200 | 142.250.185.206:80 | http://suggestqueries.google.com/complete/search?output=toolbar&hl=en&q=%0Aspotify%20premiium%20M | US | xml | 960 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3624 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3216 | chrome.exe | 142.250.185.141:443 | accounts.google.com | GOOGLE | US | whitelisted |
3976 | Scraper.exe | 142.250.185.206:80 | suggestqueries.google.com | GOOGLE | US | whitelisted |
3216 | chrome.exe | 142.250.184.193:443 | lh5.googleusercontent.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | chrome.exe | 142.250.186.46:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
3216 | chrome.exe | 142.250.185.193:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
3216 | chrome.exe | 172.217.16.206:443 | clients2.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
suggestqueries.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |