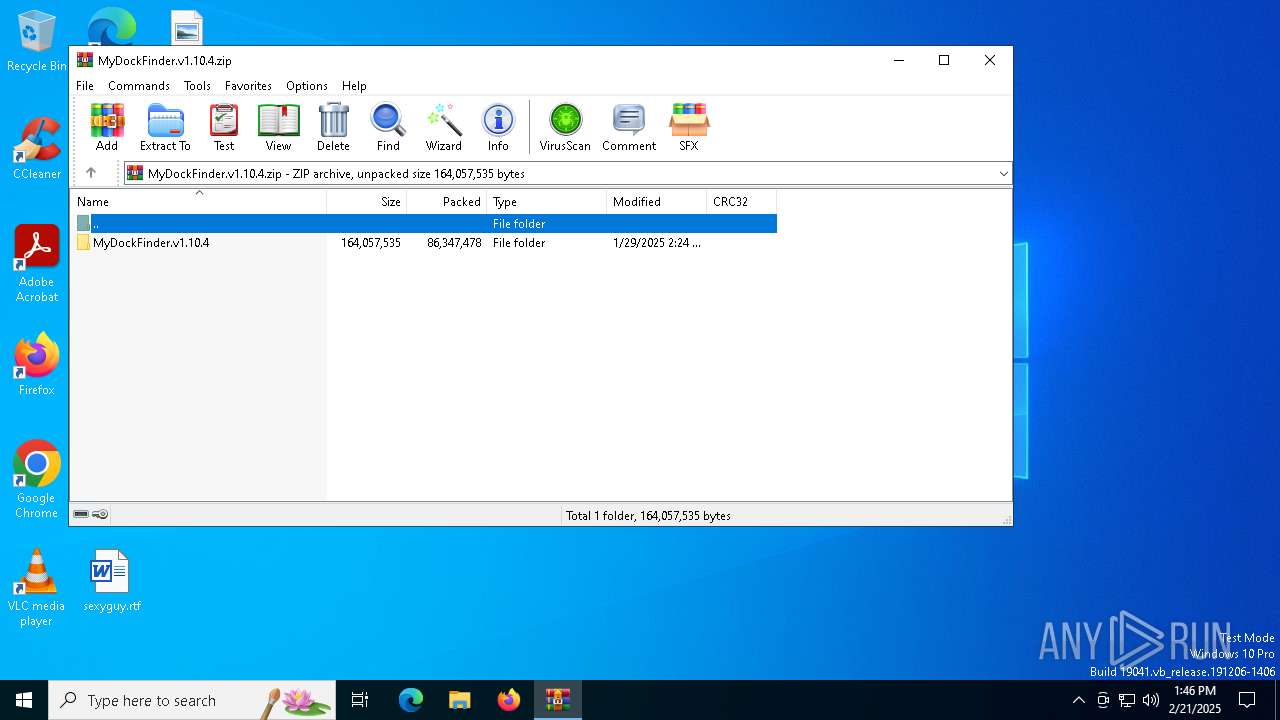
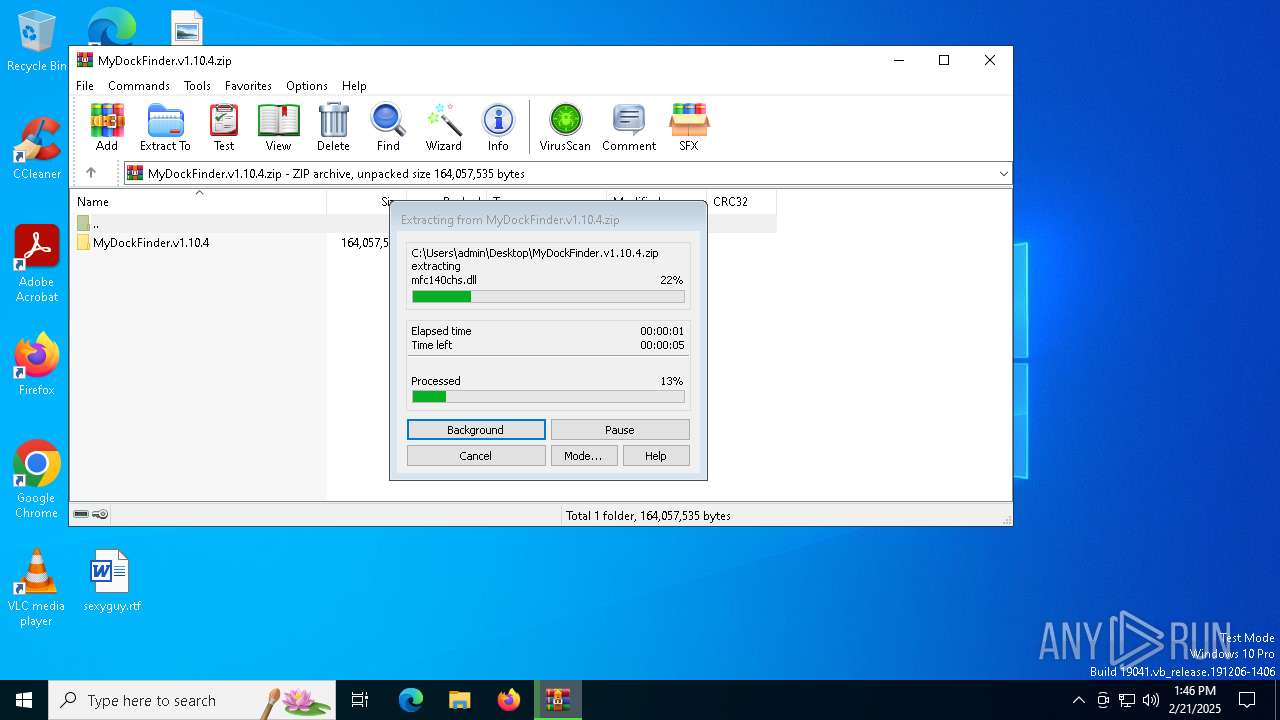
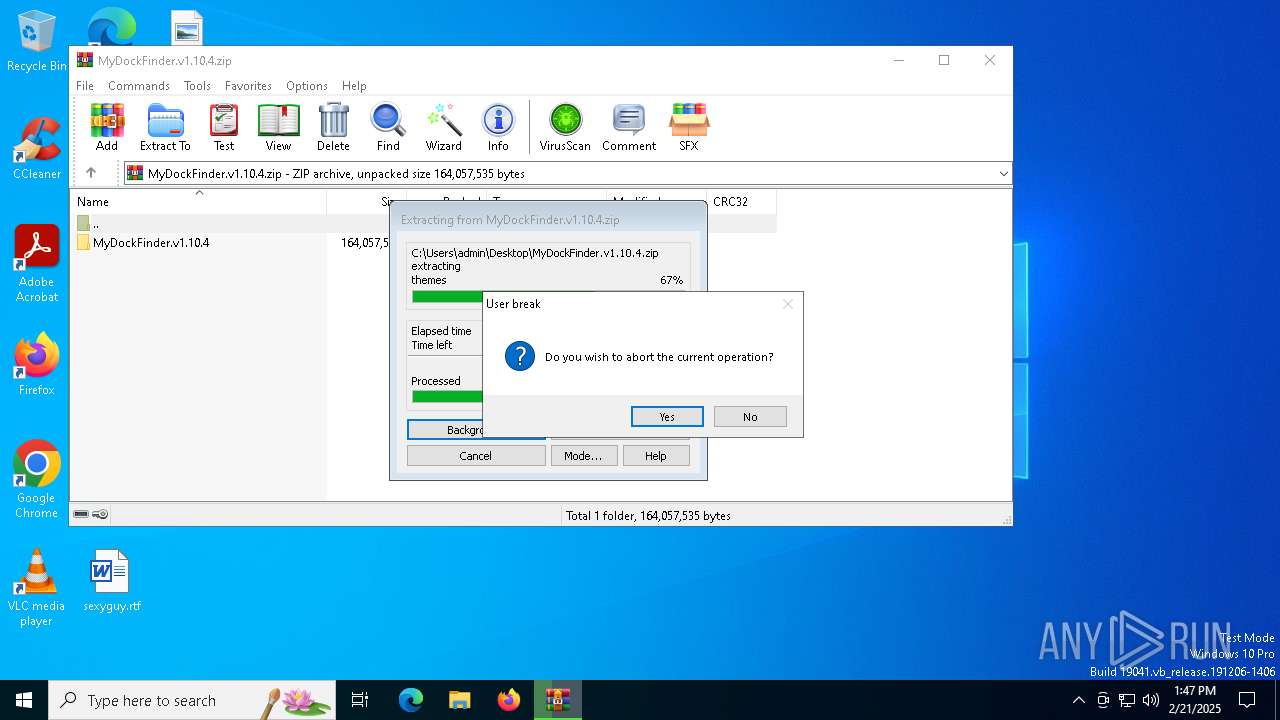
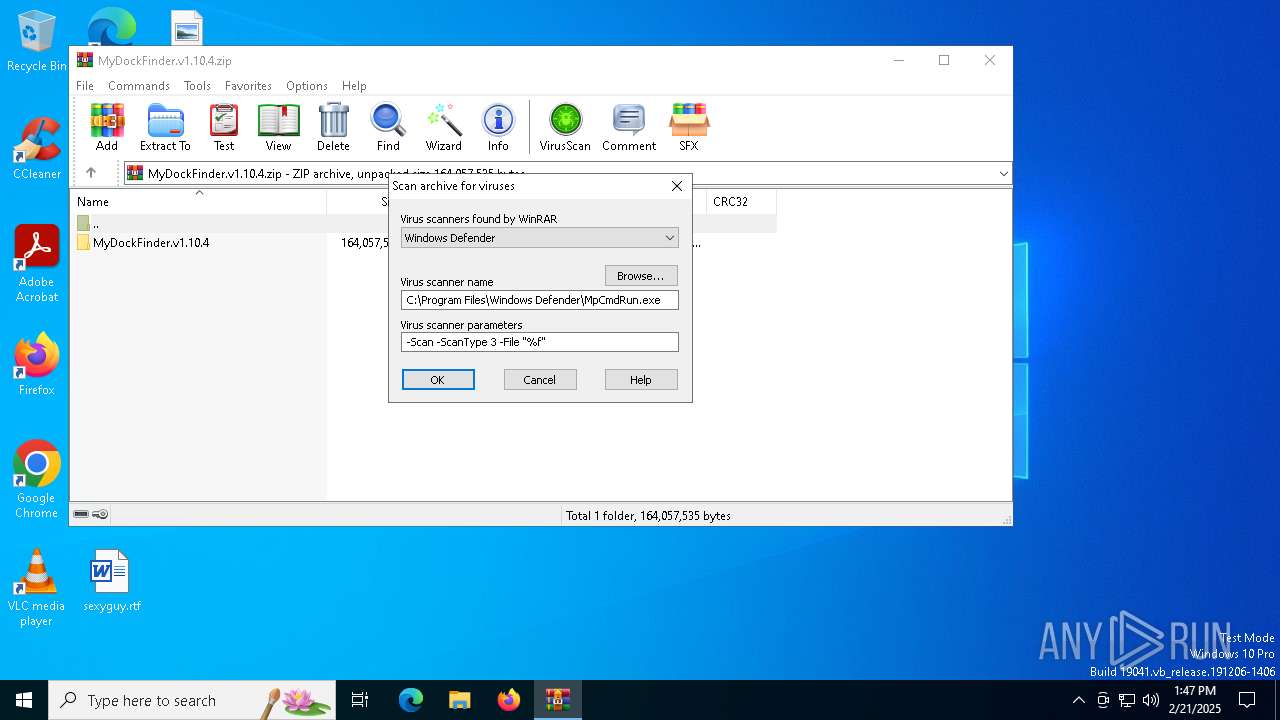
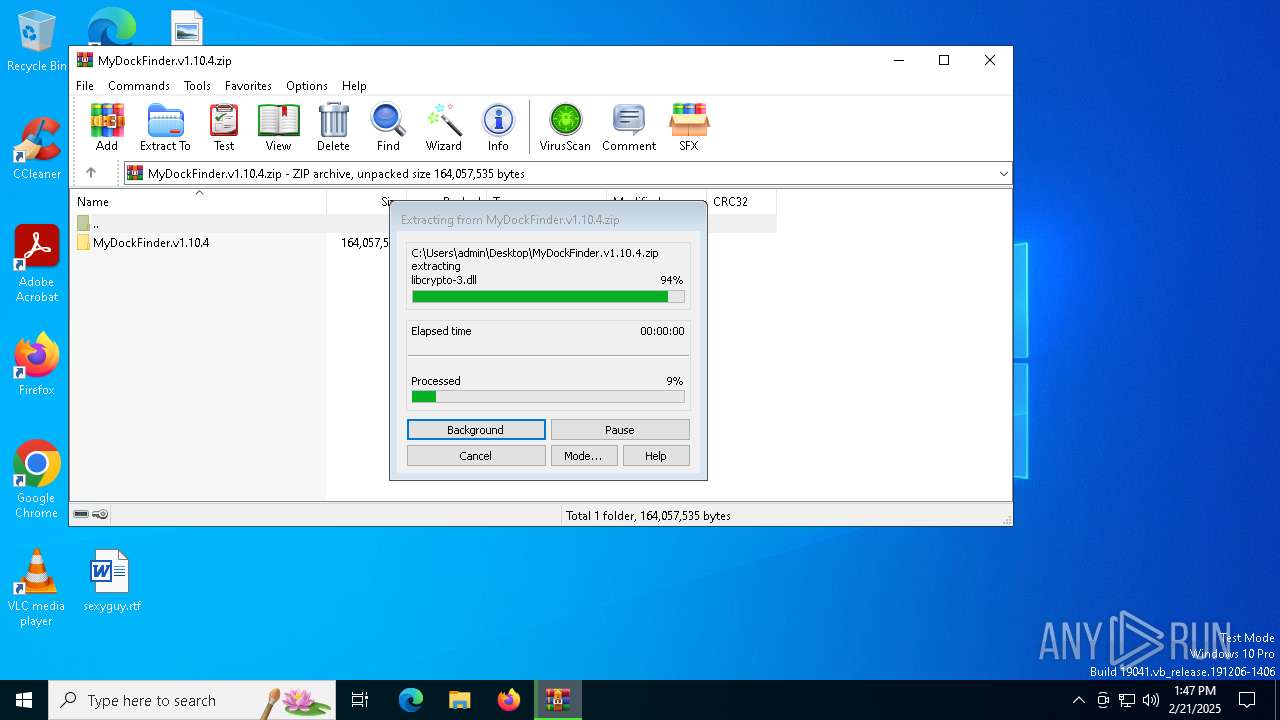
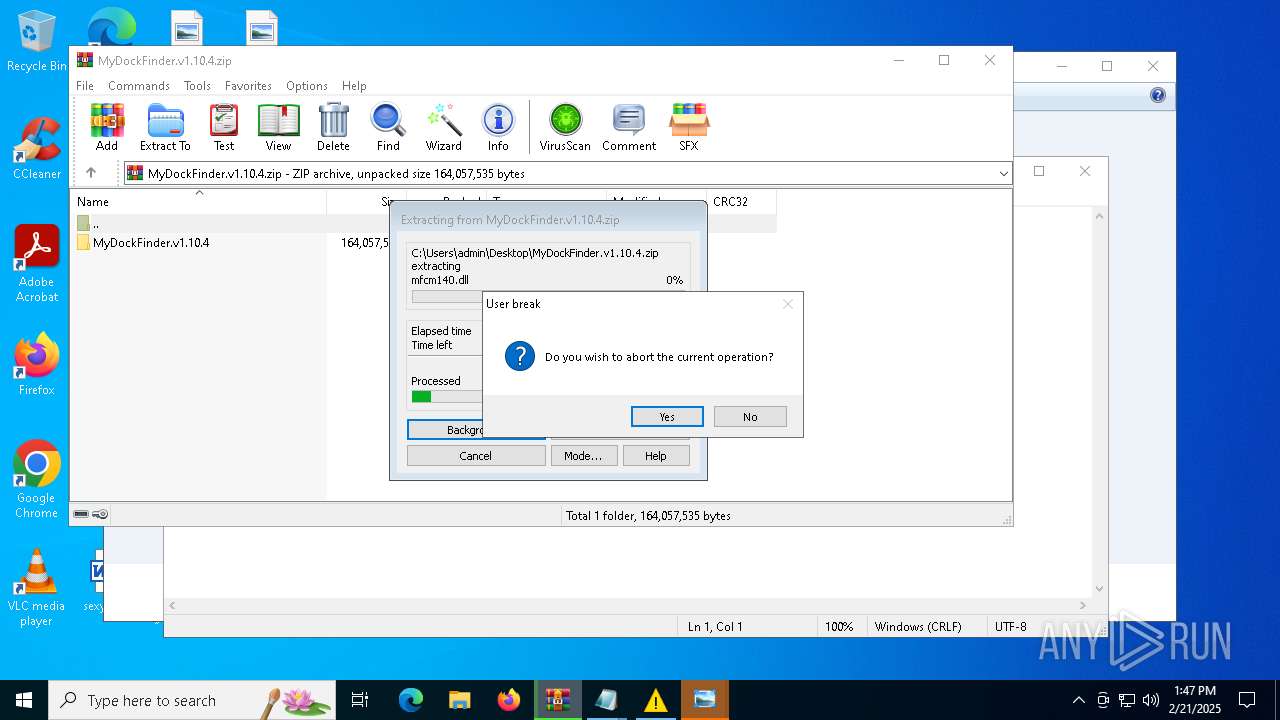
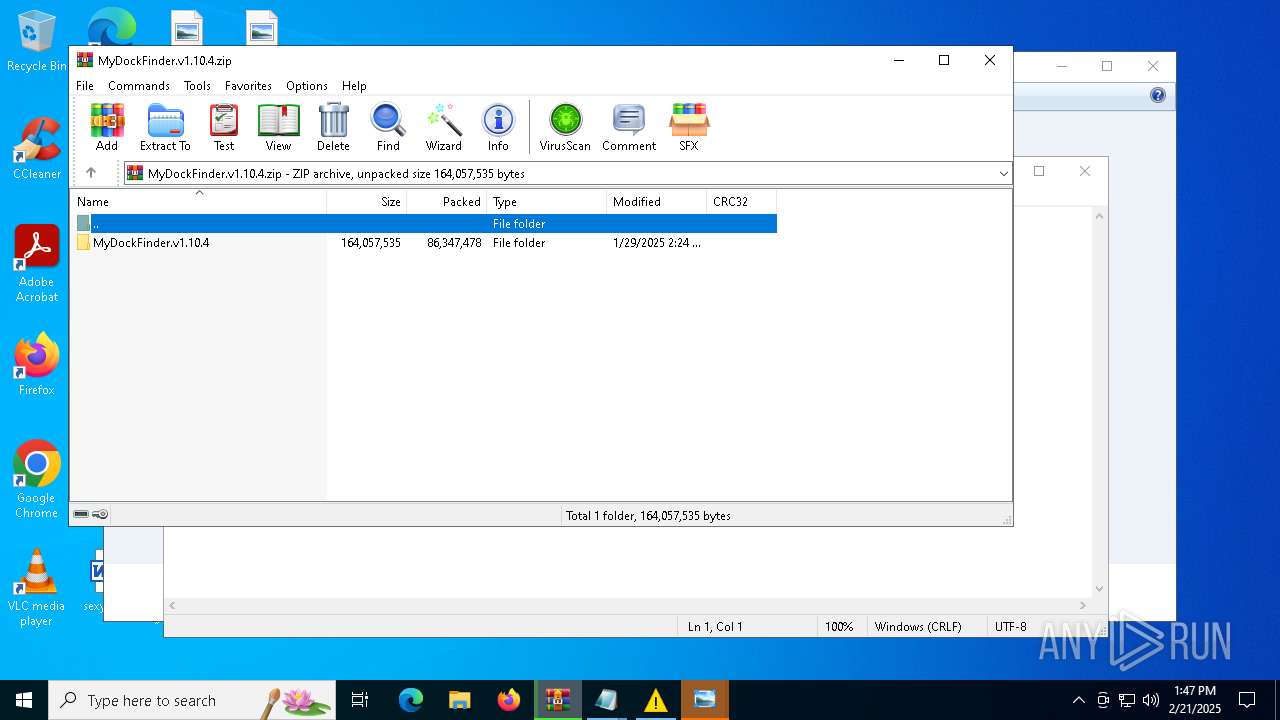
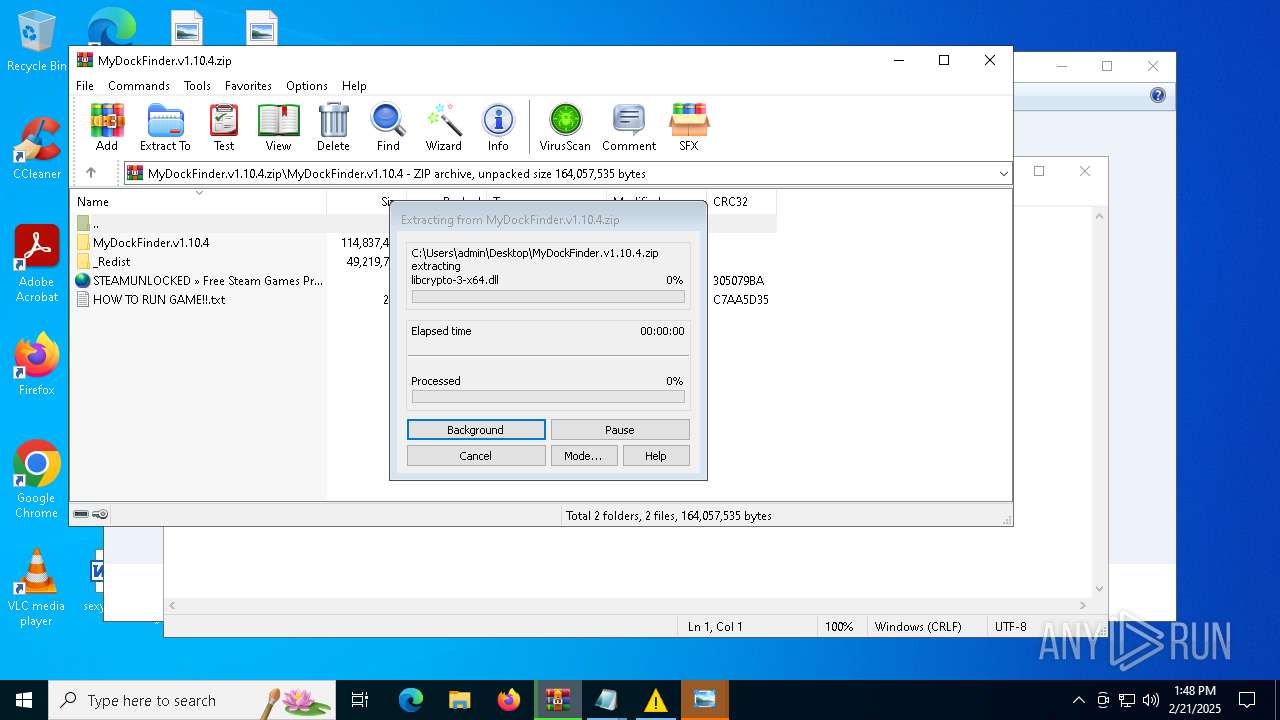
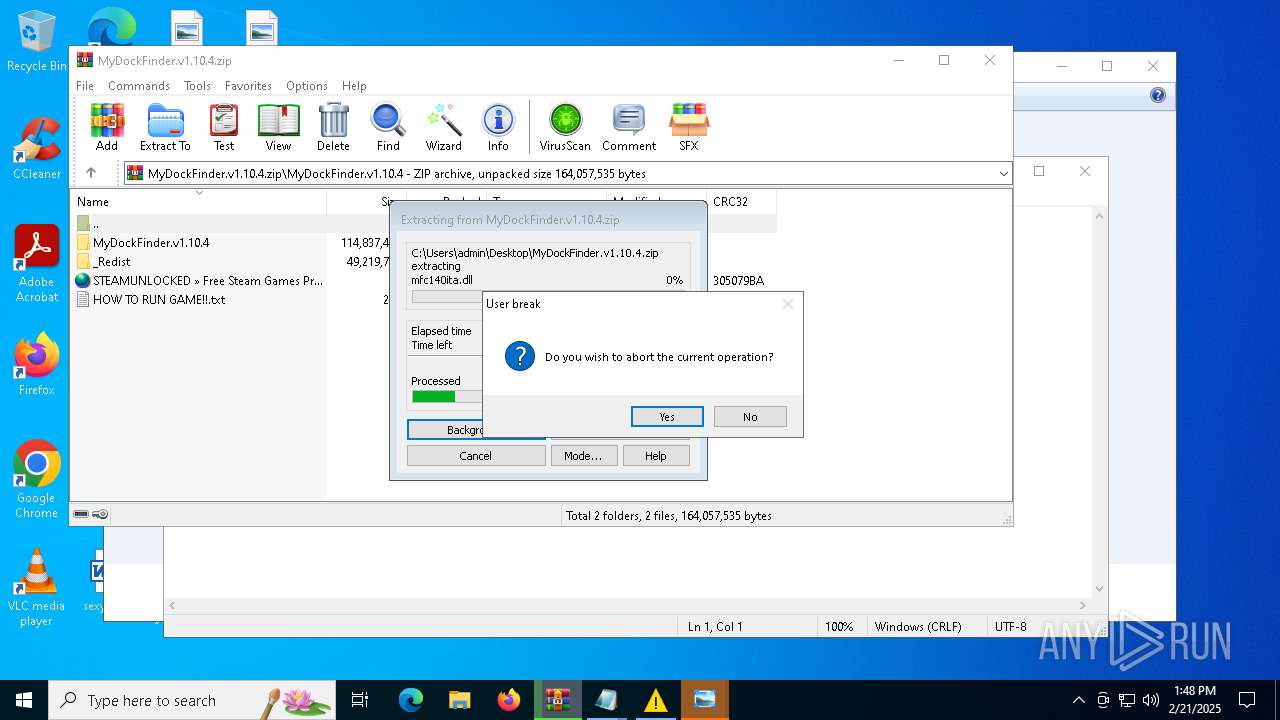
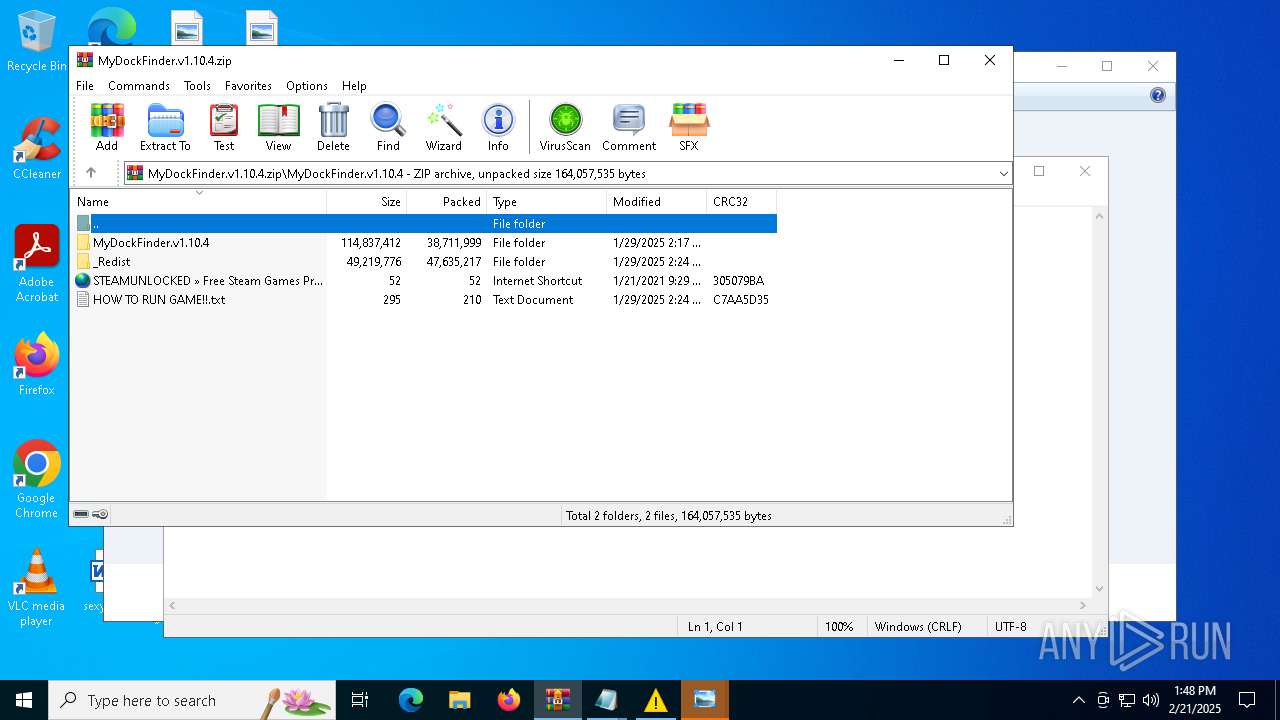
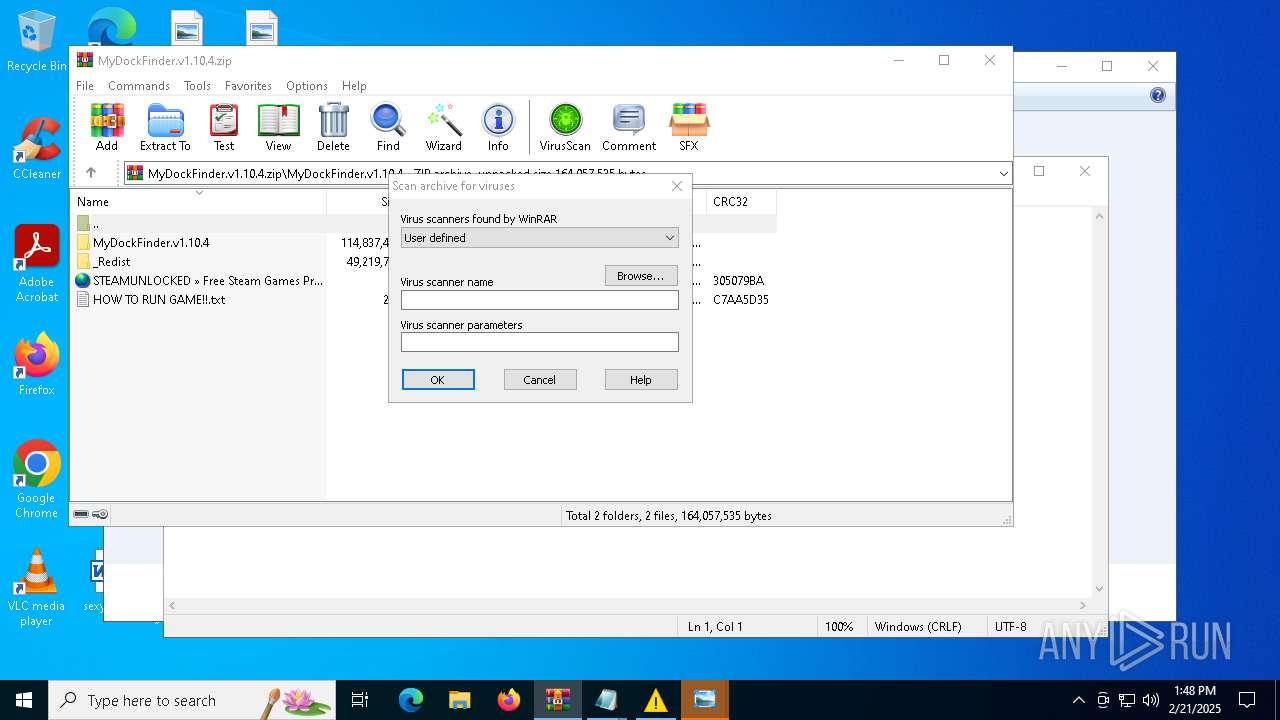
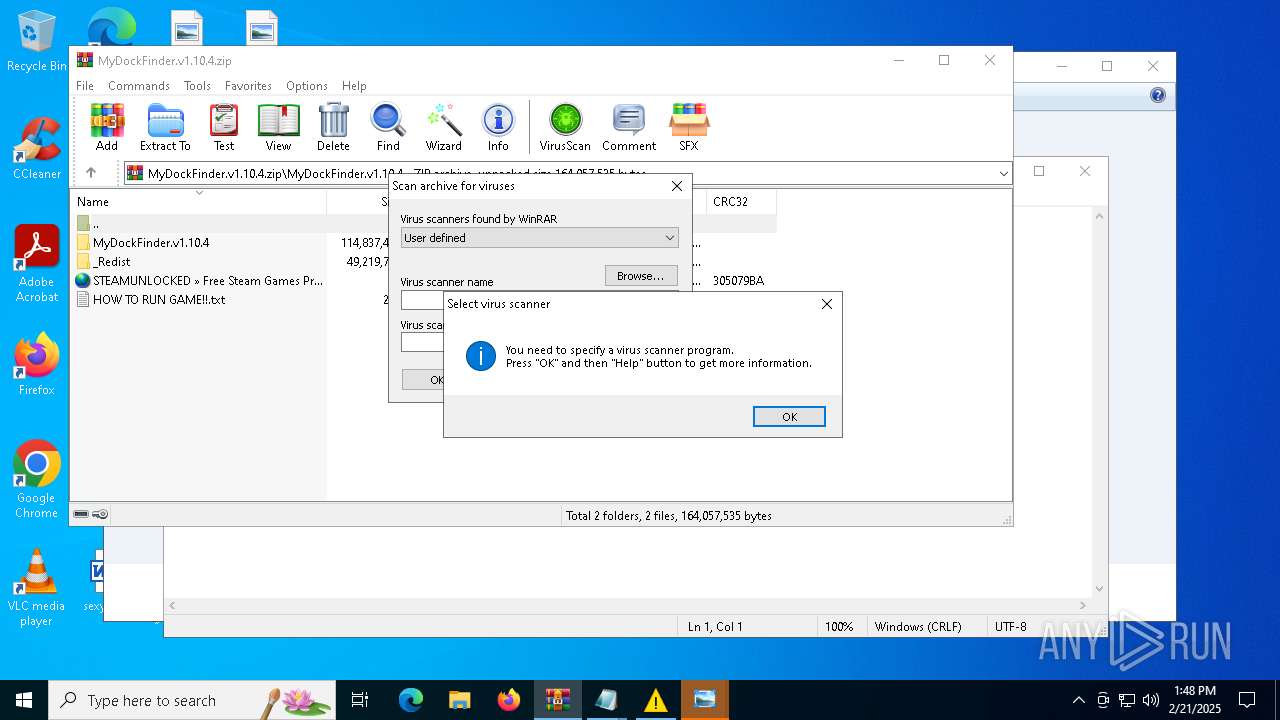
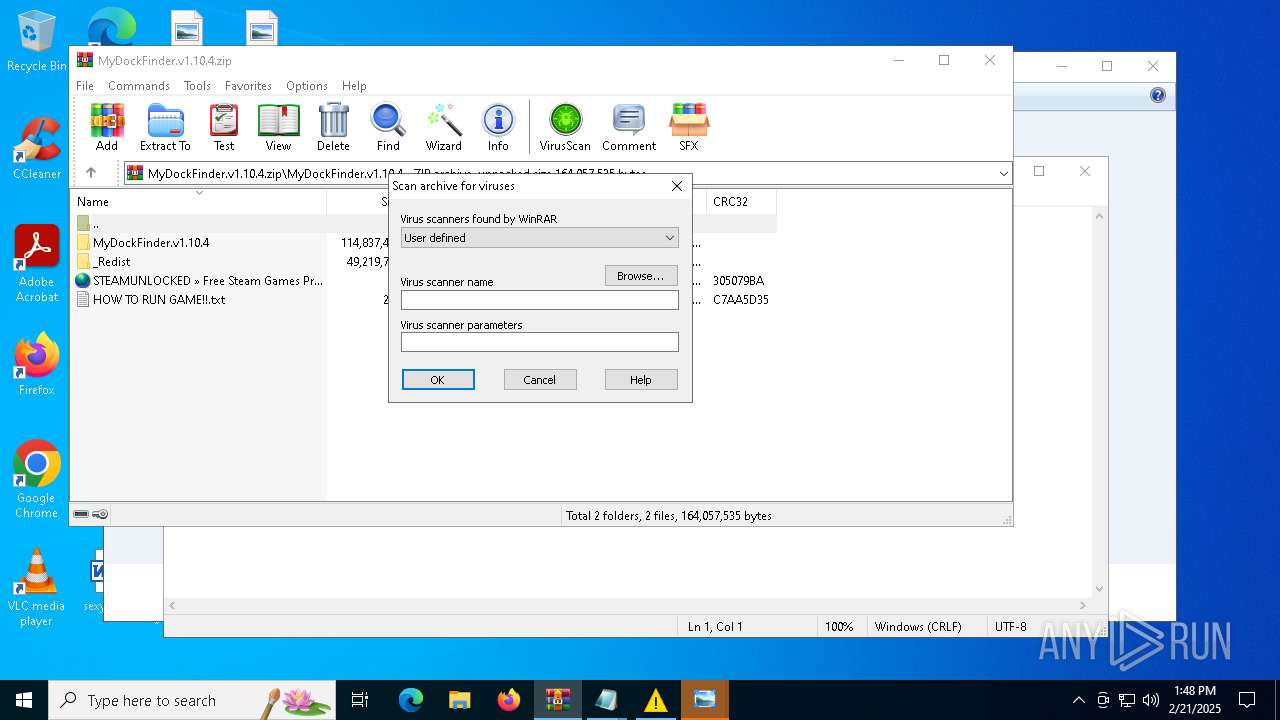
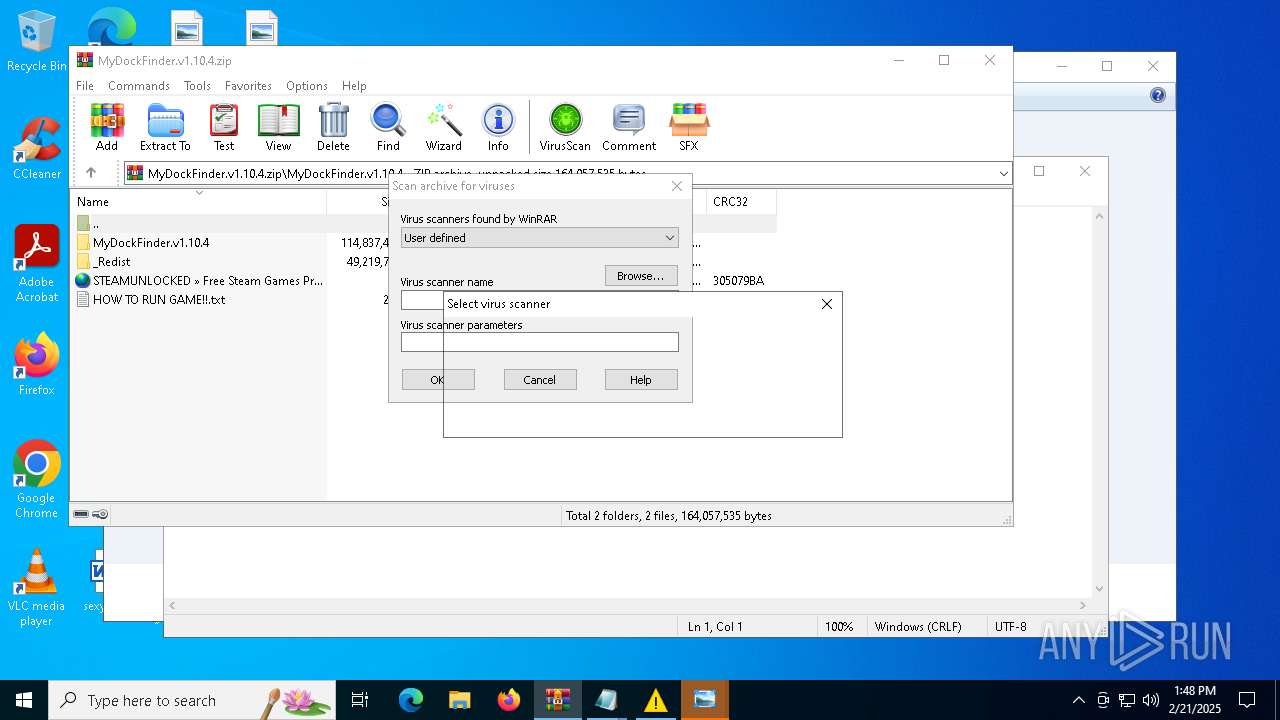
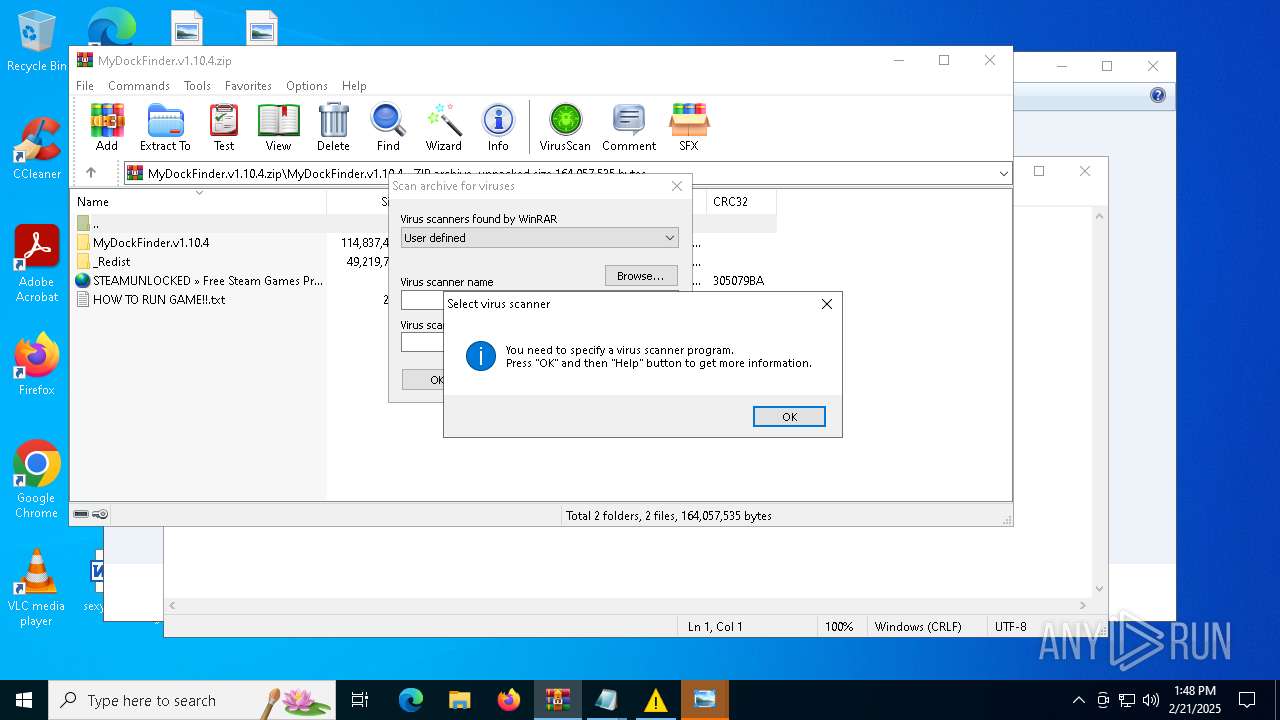
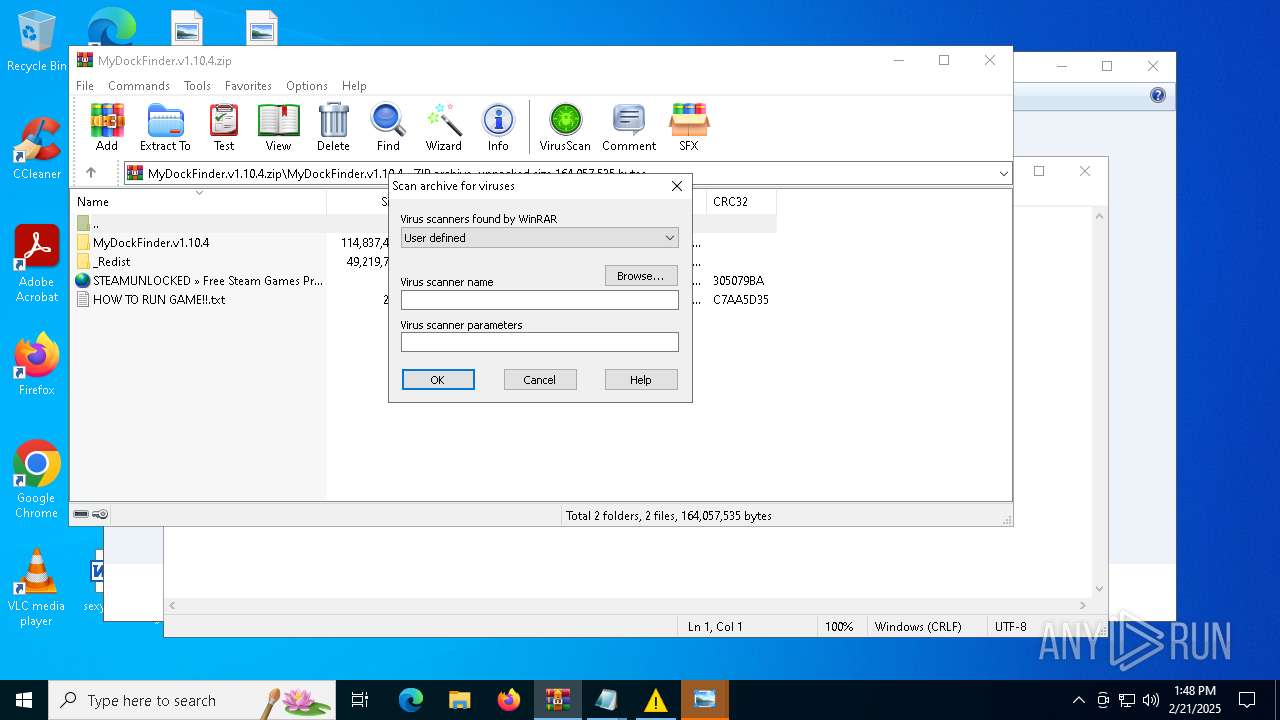
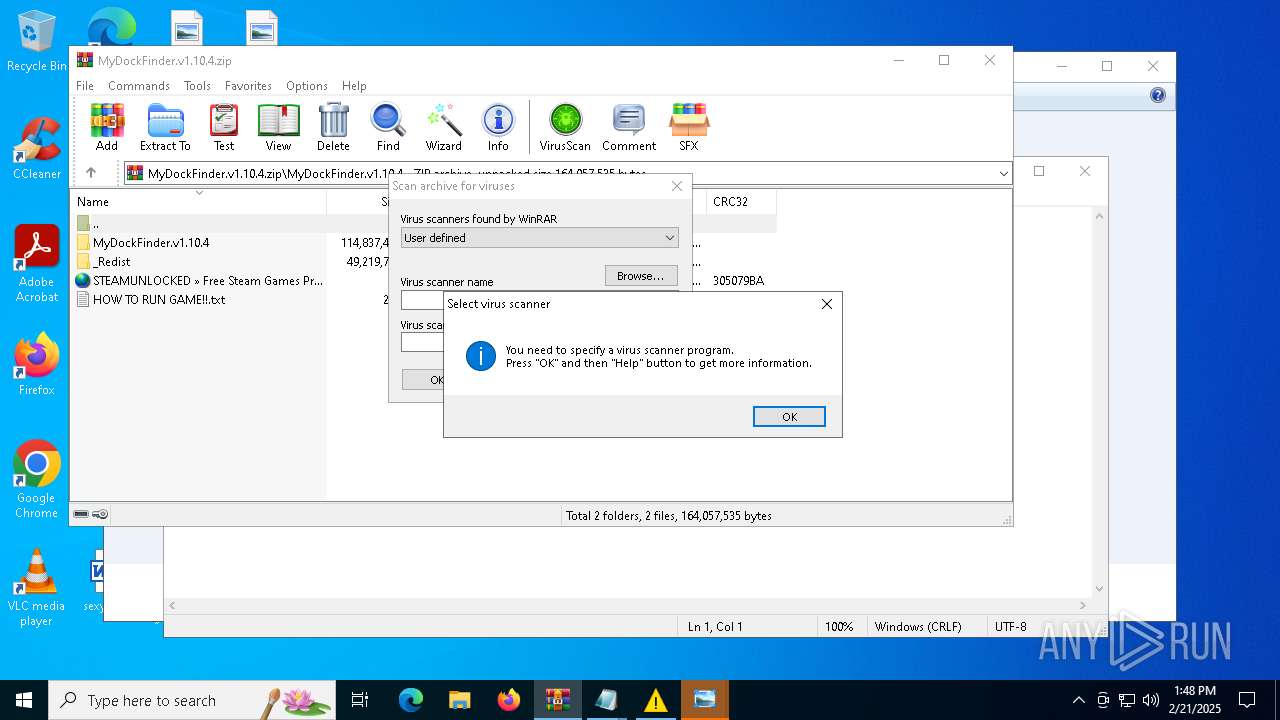
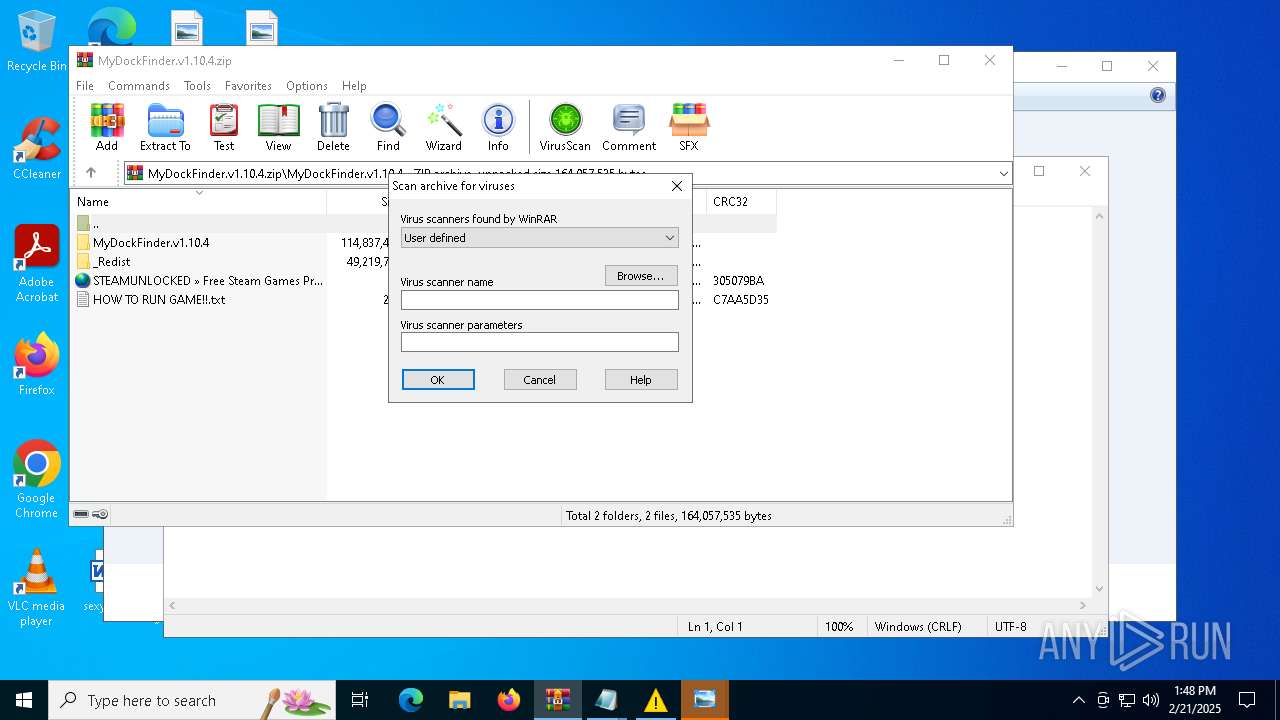
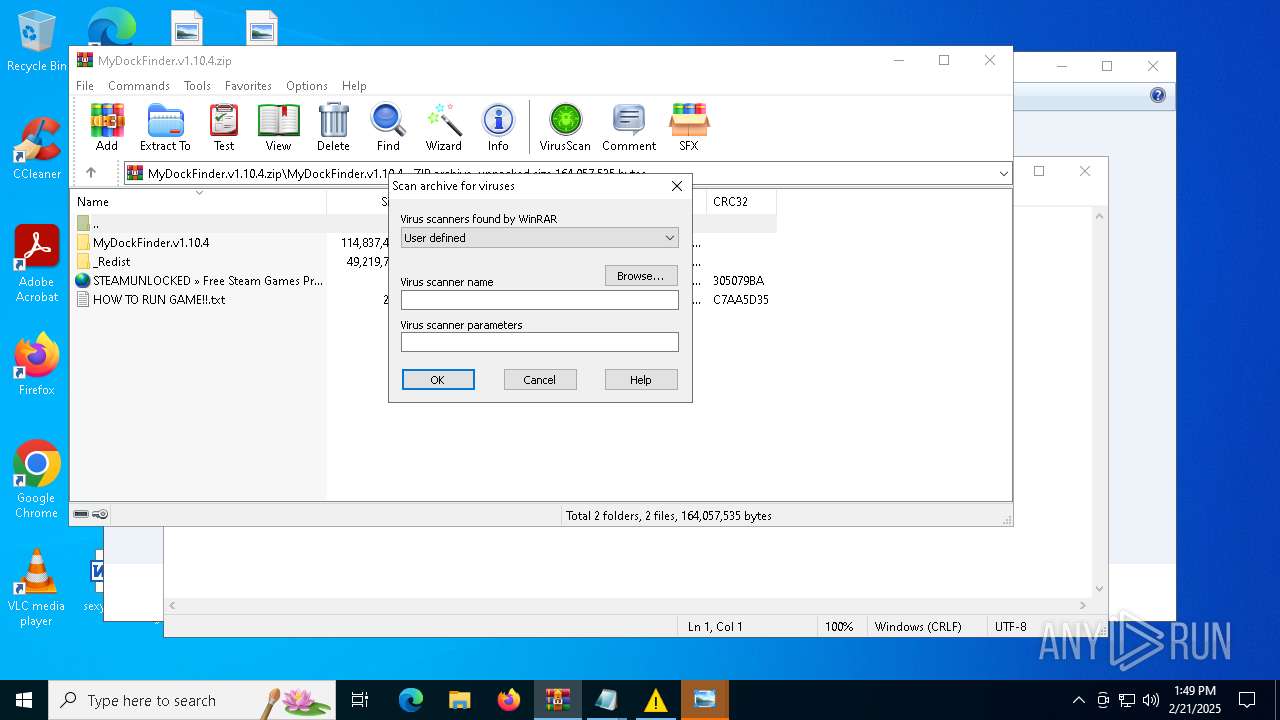
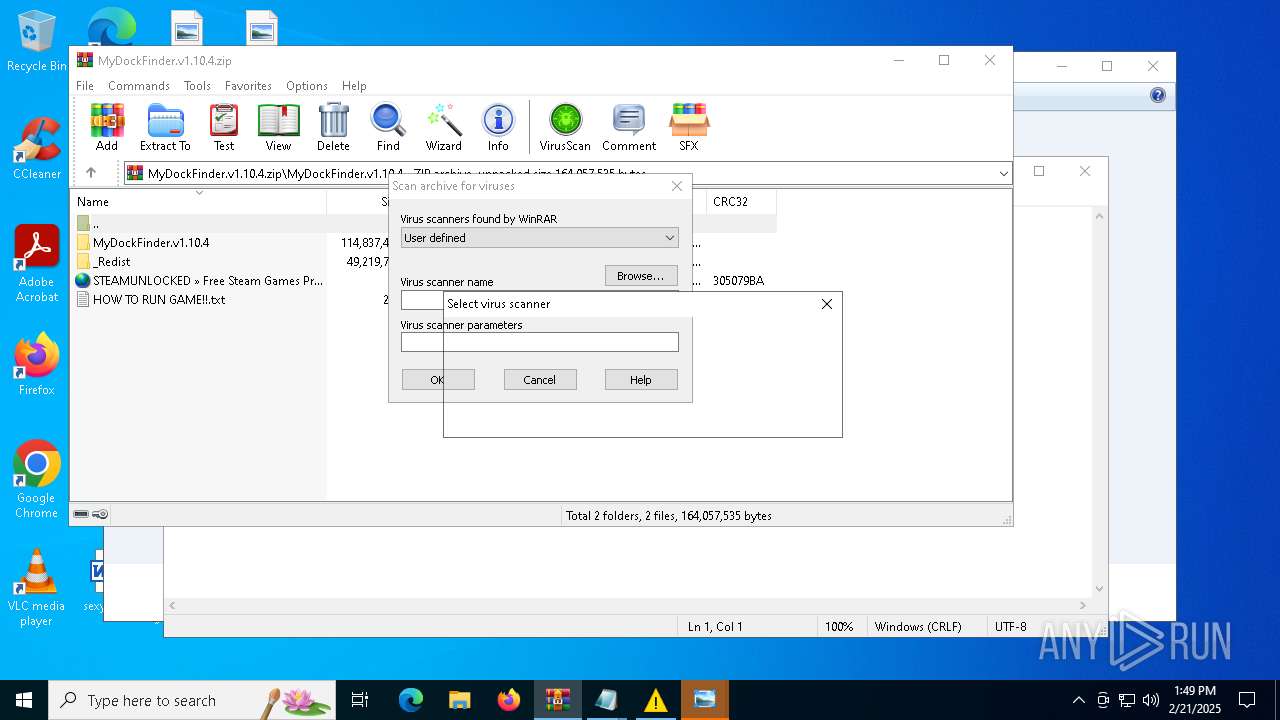
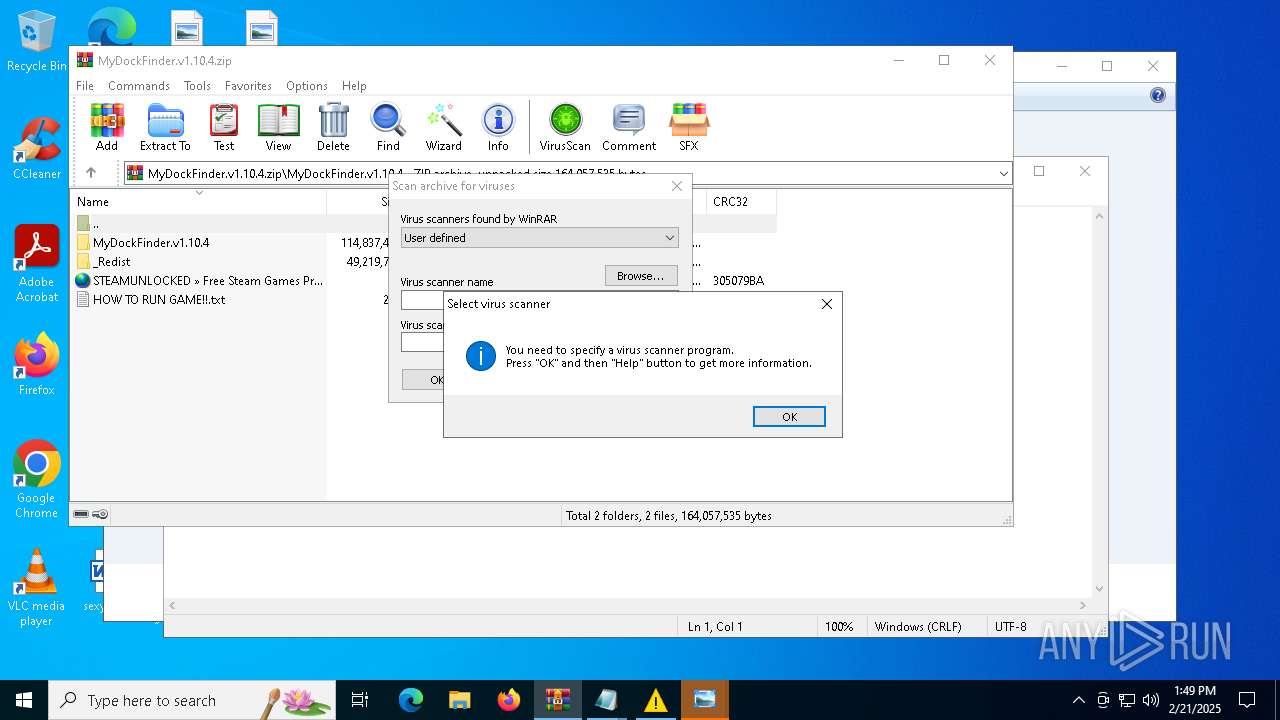
| File name: | MyDockFinder.v1.10.4.zip |
| Full analysis: | https://app.any.run/tasks/ad17a342-f05b-4c72-8b12-3e10419fed51 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2025, 13:46:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | AB38EB6EF2CEC6CE70B18F2476BD7DD3 |
| SHA1: | 1909EB5AF6446251FE473C83843E0DD8018F5C48 |
| SHA256: | EF2FDC3CFEF1ECEA02274849E9CC2219A23932836A0E55F057E5A7C677716683 |
| SSDEEP: | 786432:dMbwNwzEEct0qudhqudBqCjJR4qTO9QldqOD2:WbgjE7dzdBqAJR4qTO9QTrD2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4764)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4764)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 3688)
- rundll32.exe (PID: 3076)
- rundll32.exe (PID: 3364)
- rundll32.exe (PID: 5496)
- rundll32.exe (PID: 2076)
- rundll32.exe (PID: 4536)
- rundll32.exe (PID: 4160)
- notepad.exe (PID: 1200)
The sample compiled with english language support
- WinRAR.exe (PID: 4764)
Manual execution by a user
- rundll32.exe (PID: 3076)
- notepad.exe (PID: 3688)
- rundll32.exe (PID: 4536)
- rundll32.exe (PID: 3364)
- rundll32.exe (PID: 5496)
- rundll32.exe (PID: 2076)
- rundll32.exe (PID: 4160)
- notepad.exe (PID: 1200)
Local mutex for internet shortcut management
- rundll32.exe (PID: 3076)
- rundll32.exe (PID: 3364)
- rundll32.exe (PID: 4536)
- rundll32.exe (PID: 2076)
- rundll32.exe (PID: 5496)
- rundll32.exe (PID: 4160)
- WinRAR.exe (PID: 4764)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:29 06:24:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | MyDockFinder.v1.10.4/ |
Total processes
117
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\config.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\18.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | "C:\WINDOWS\system32\rundll32.exe" "C:\WINDOWS\system32\ieframe.dll",OpenURL %l | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\16.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
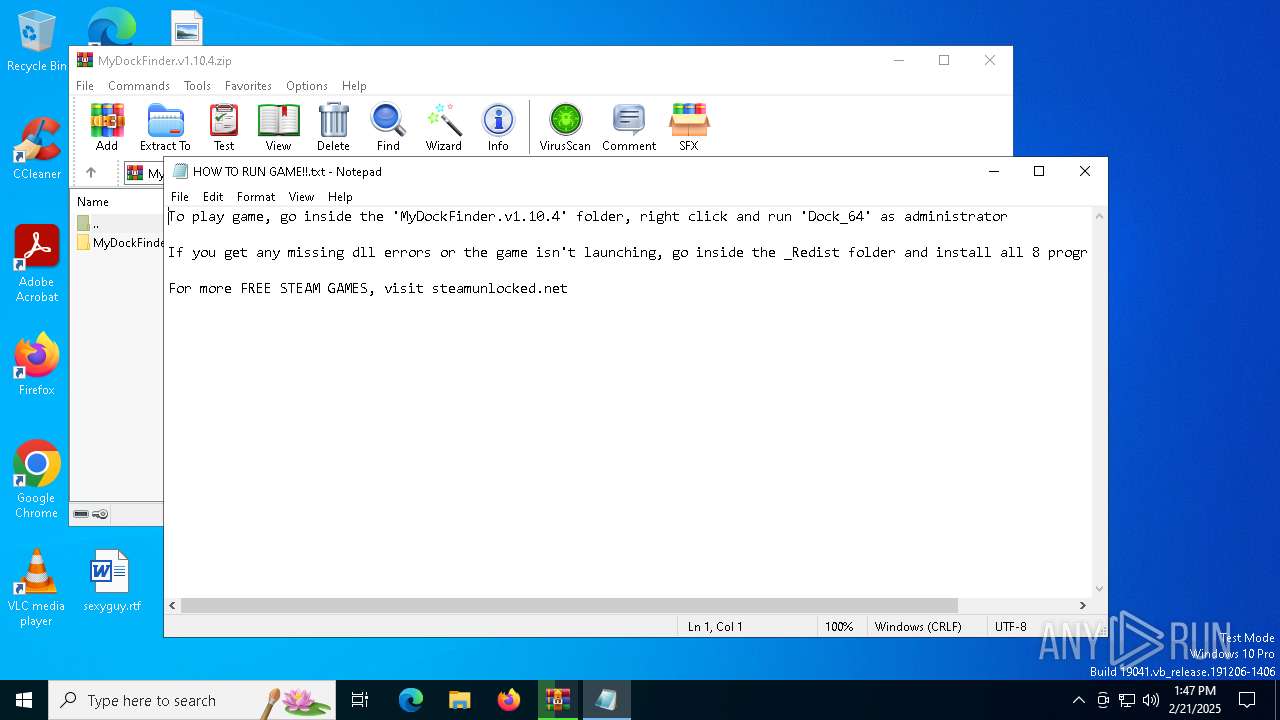
| 3688 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\HOW TO RUN GAME!!.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4160 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\28.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4536 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\13n.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4764 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\MyDockFinder.v1.10.4.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5496 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\minute.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 944
Read events
4 915
Write events
29
Delete events
0
Modification events
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MyDockFinder.v1.10.4.zip | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
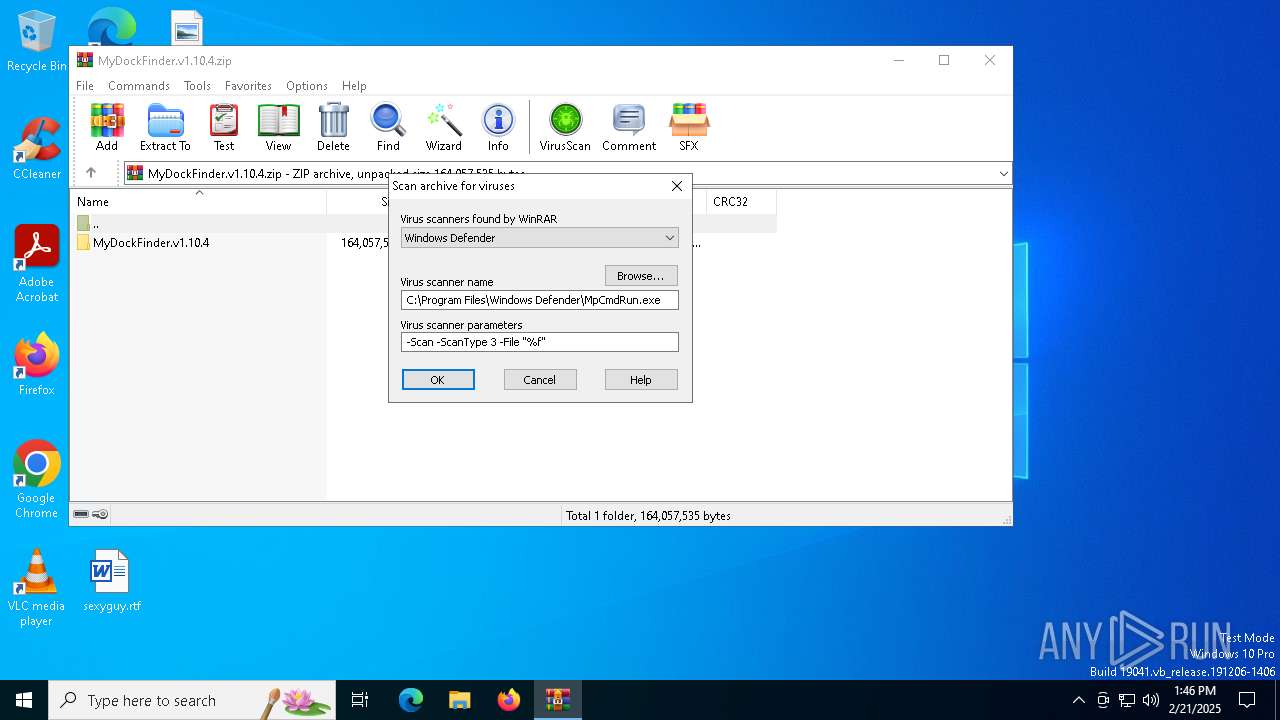
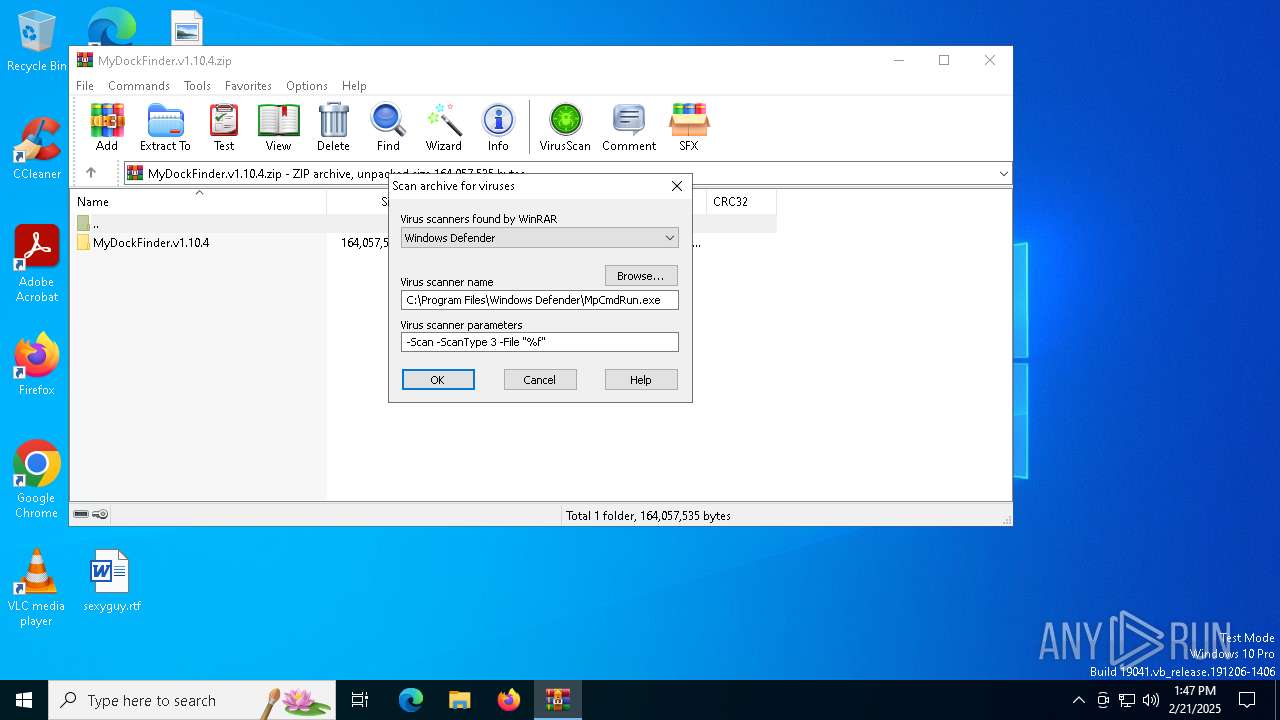
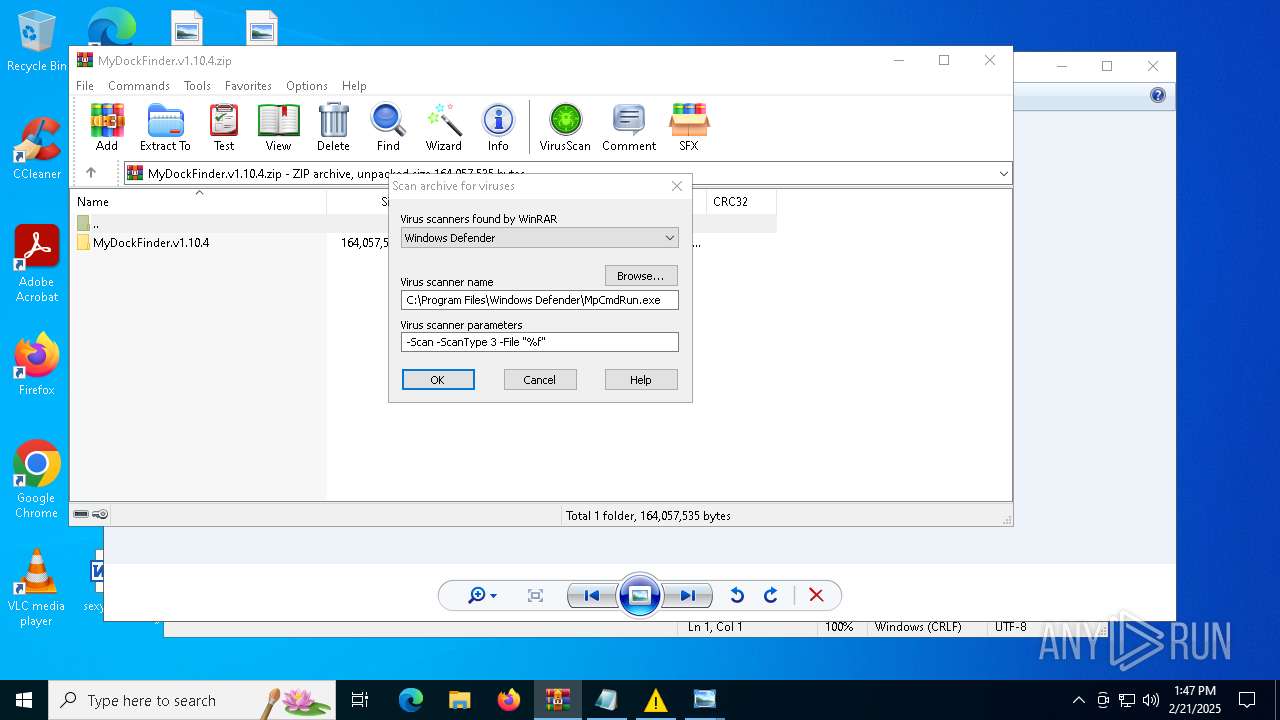
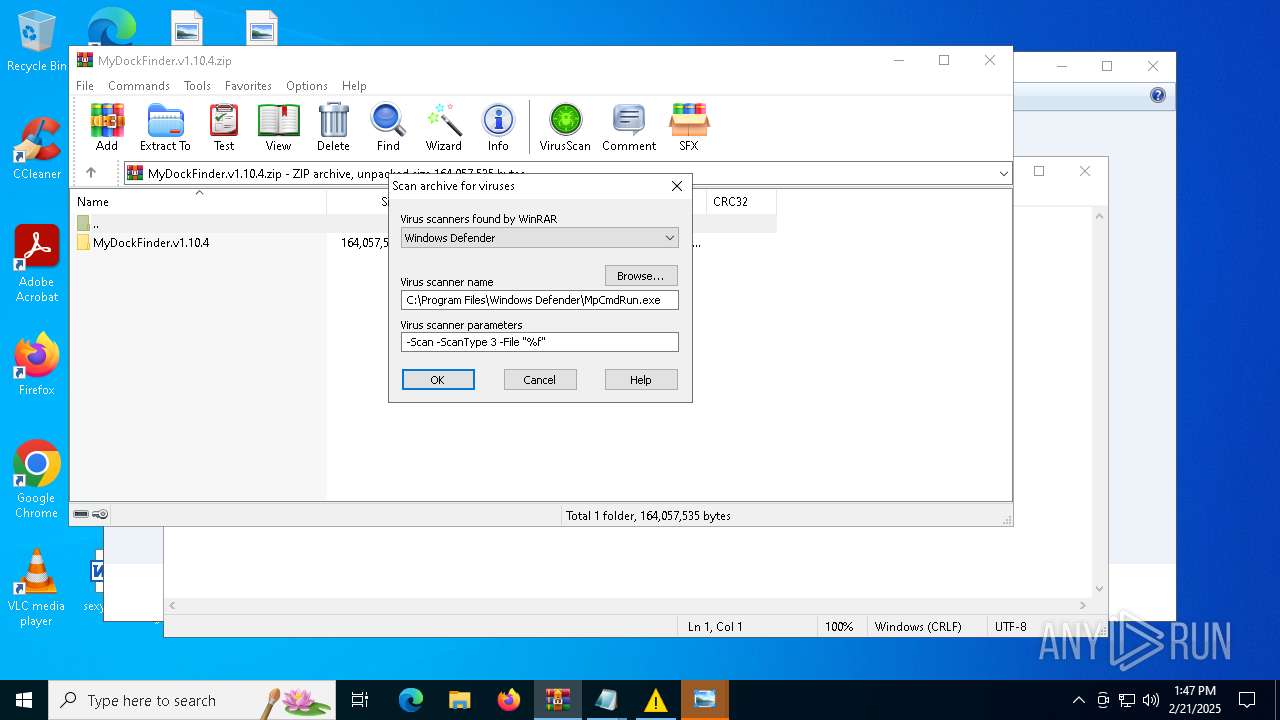
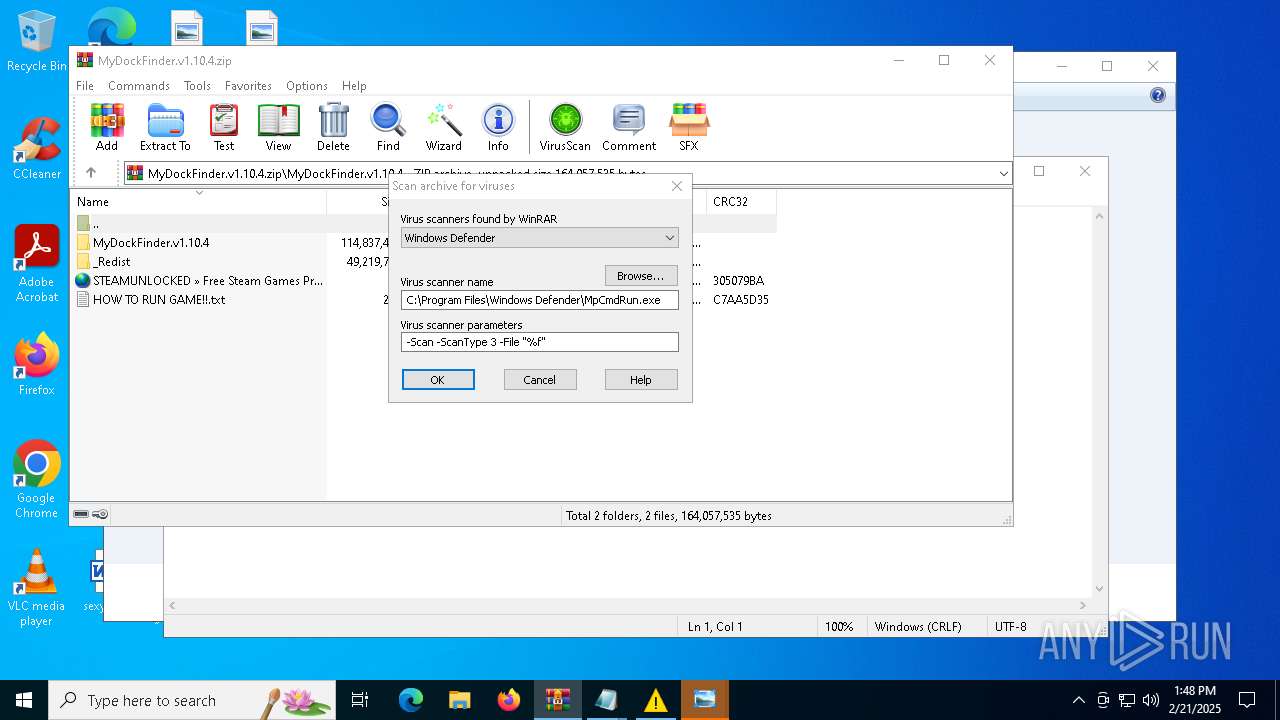
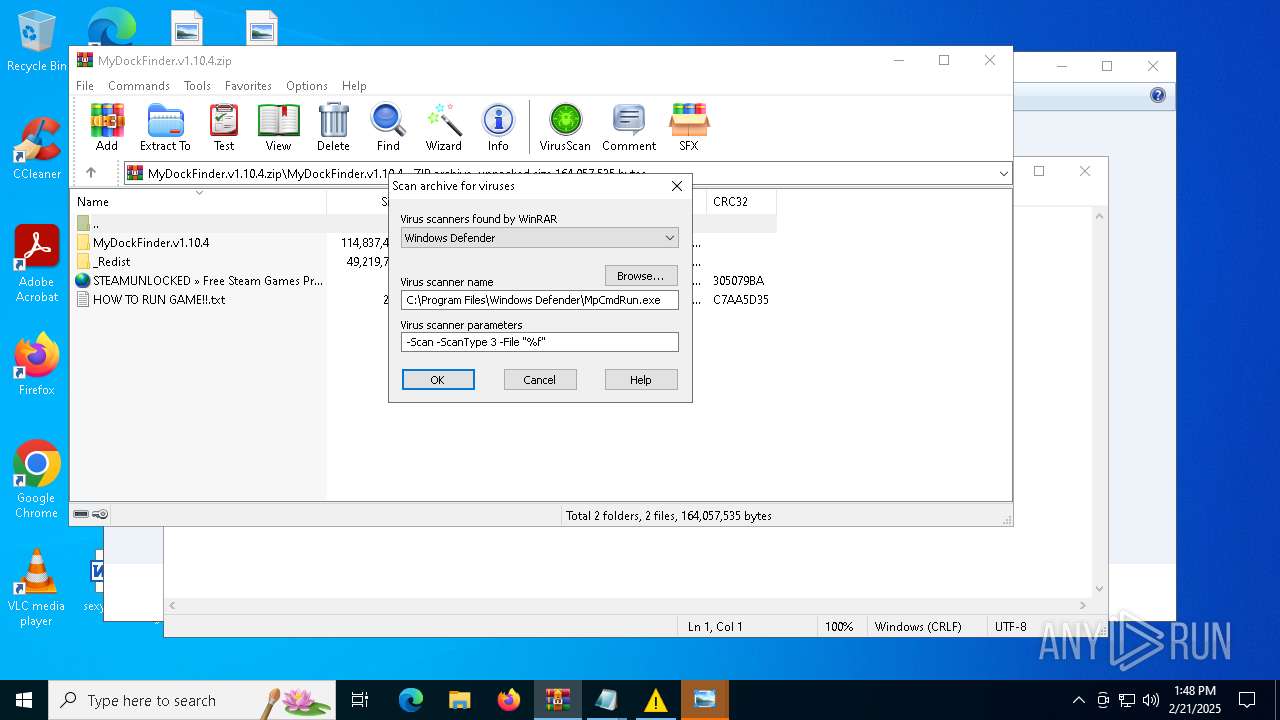
| (PID) Process: | (4764) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (4536) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
258
Suspicious files
61
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\concrt140_app.dll | executable | |
MD5:443AE6A3D863C77844F2431FA49508F5 | SHA256:A9C93A08A3B599AC2CCC448C3F09195EBF74A5D5D7DBD501EFAF82E3956CE5E4 | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\libcurl.dll | executable | |
MD5:E90C74F6C8C3262F8CFEC5AD63711141 | SHA256:6C49C8CF8816417E669488145C8808E596DD9FA72F074CE198475EE734EB2EC6 | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\libssl-3-x64.dll | executable | |
MD5:4F8505F01597C0BE84983A6F8D4CEAA8 | SHA256:90A230EBF5AB250527670F01871CA1AA0EC81557F1B1179E868A9623DF0BC69D | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\msvcp140_2.dll | executable | |
MD5:DDC38BB34DE28E1F42B6DEA9770D4D65 | SHA256:89E2E9A163165E20C540F9ADEA081E927DDFE4A556547B0F45F11586D4CCE165 | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\concrt140.dll | executable | |
MD5:8FC1C2F2EBB7E46DF30ECD772622B0BC | SHA256:E2E4609C569C69F7B1686F6D0E81CE62187AC5DF05E0247954500053B3C3DE3F | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\Microsoft.Graphics.Canvas.dll | executable | |
MD5:4FA3917224642623174DCF7F081D9AE3 | SHA256:532358E45807395426DD70D46DBAFA28B58CCE23A740AE8A4C8915C1BEF4D3CA | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\msvcp140_atomic_wait.dll | executable | |
MD5:333727166AF151E95B05CB54550342CD | SHA256:FBF41E4B53F51BBF73FEE37B6120103FEA6B7D5AE29916F8EF50C50CFDEDEEAD | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\msvcp140_atomic_wait_app.dll | executable | |
MD5:7E3A3D7E996F8C3E0C40A6F5F7CCC8CF | SHA256:FA0B47C78415052B6ADE31DBCA25C36F3AFCBF56C31CEC9B0380434085335808 | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\msvcp140.dll | executable | |
MD5:CFDF6EAF5328FECBDEC268B7F9E21F3A | SHA256:9057D39B36B6C7D054865EE2BF9CDE7A490FE3B01EC4E82514687E24F576269F | |||
| 4764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4764.42780\MyDockFinder.v1.10.4.zip\MyDockFinder.v1.10.4\MyDockFinder.v1.10.4\dll\x64\msvcp140_1_app.dll | executable | |
MD5:17DE759913138D59757CE32CC8F2DCC6 | SHA256:F7664C1CECC9C98B5D472D95CC0EA0015EE0B2F7E1D739B9447023304B61A8F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
16
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5156 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5156 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 2.16.204.156:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5156 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5156 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |