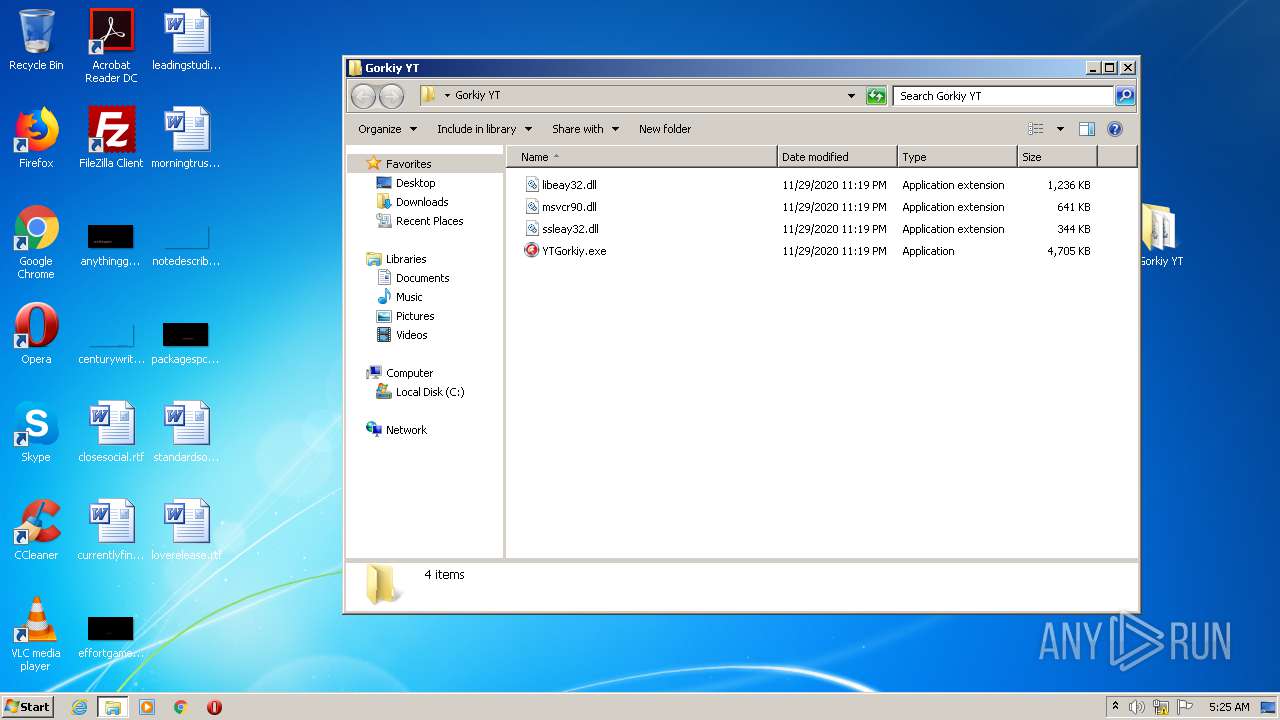
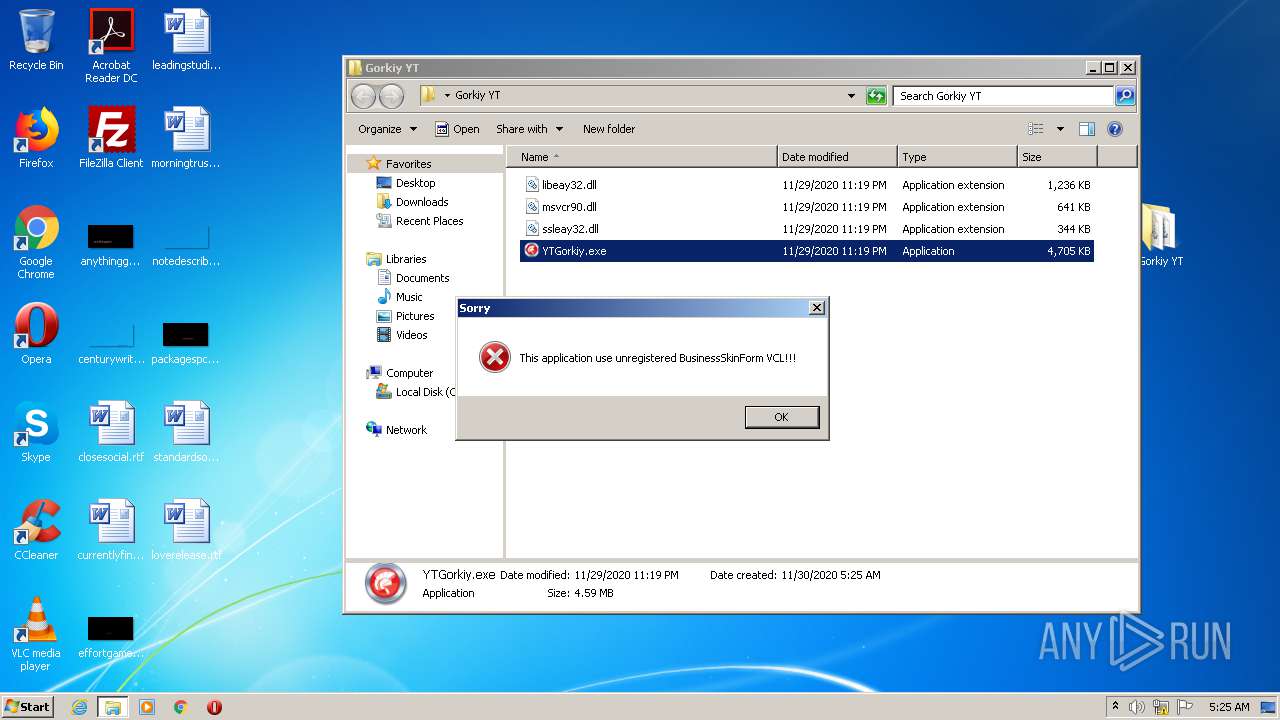
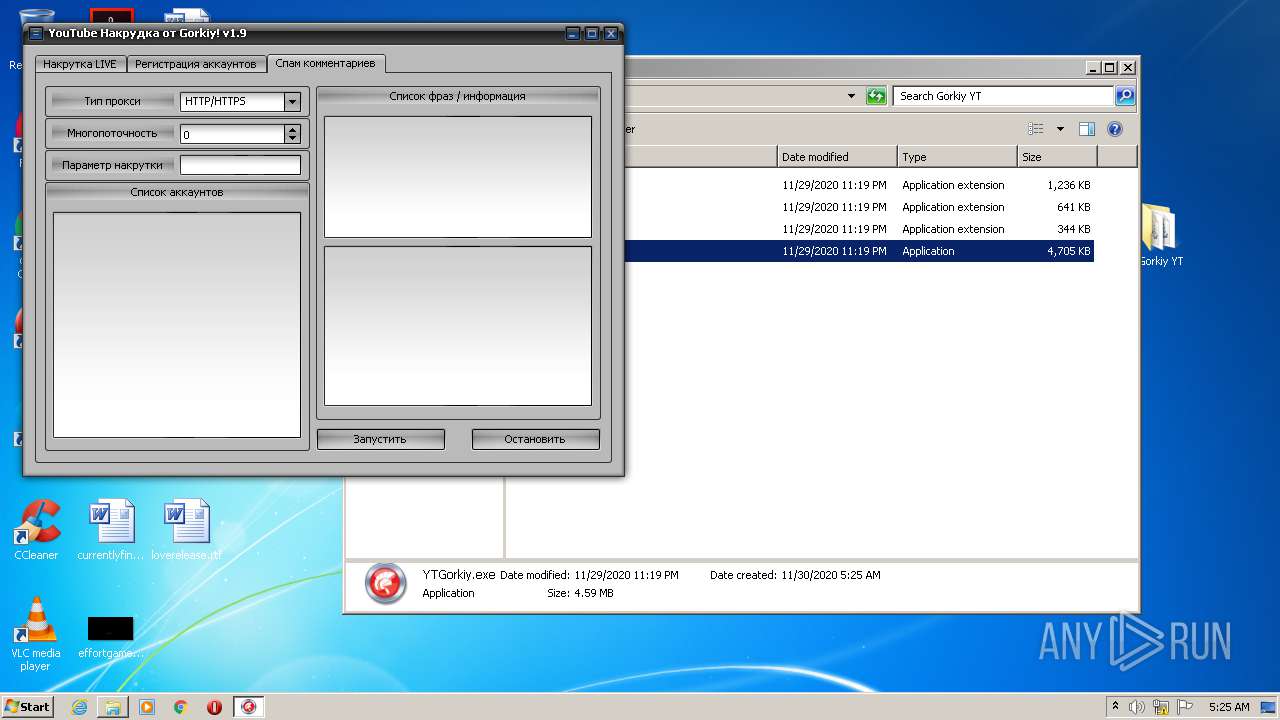
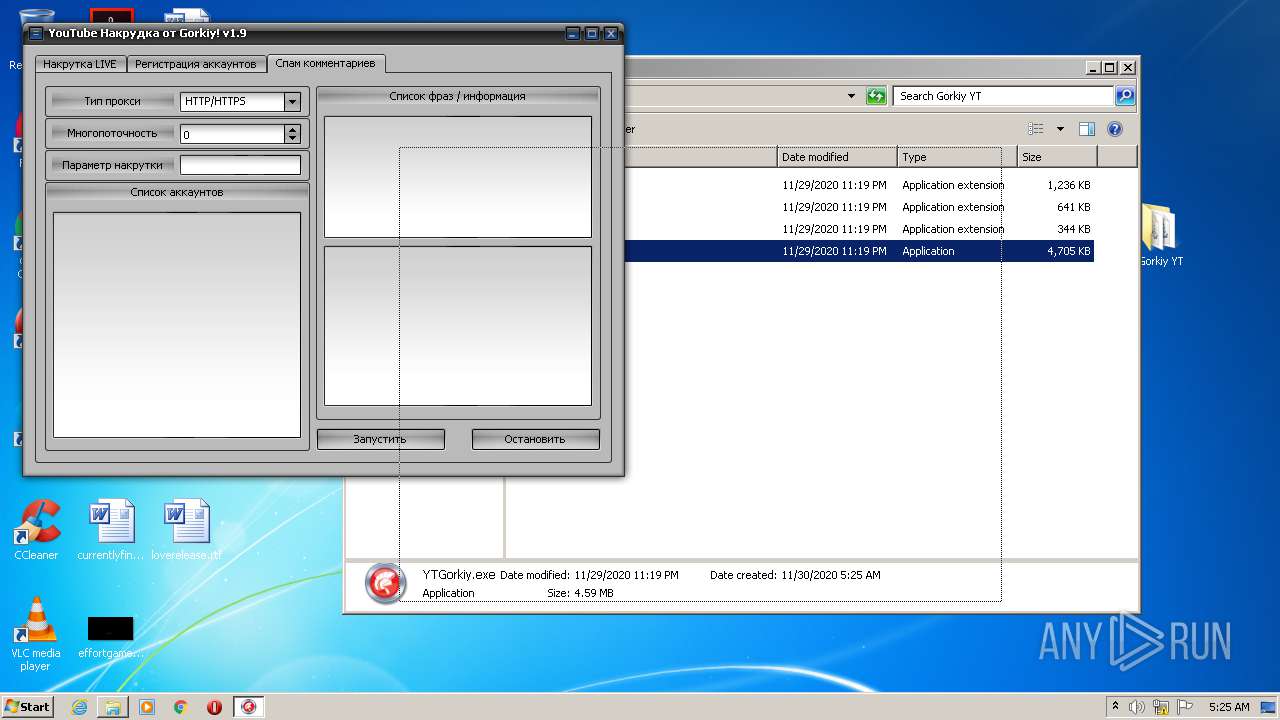
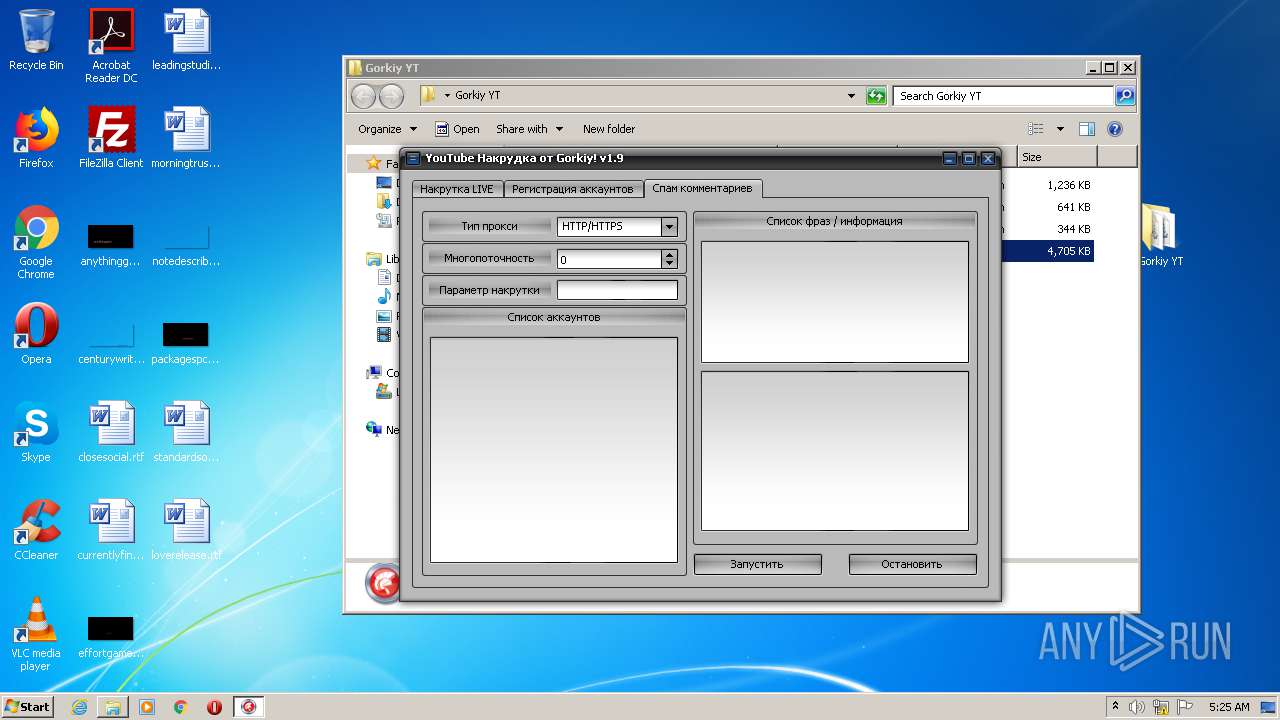
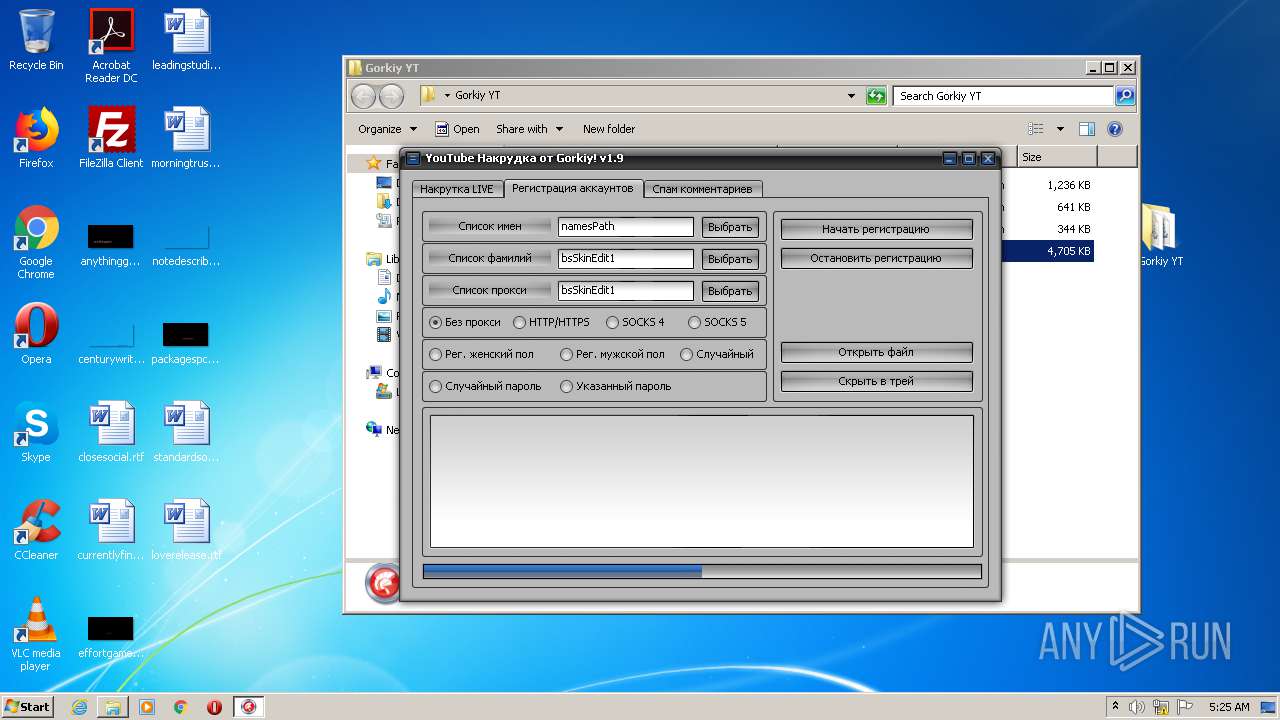
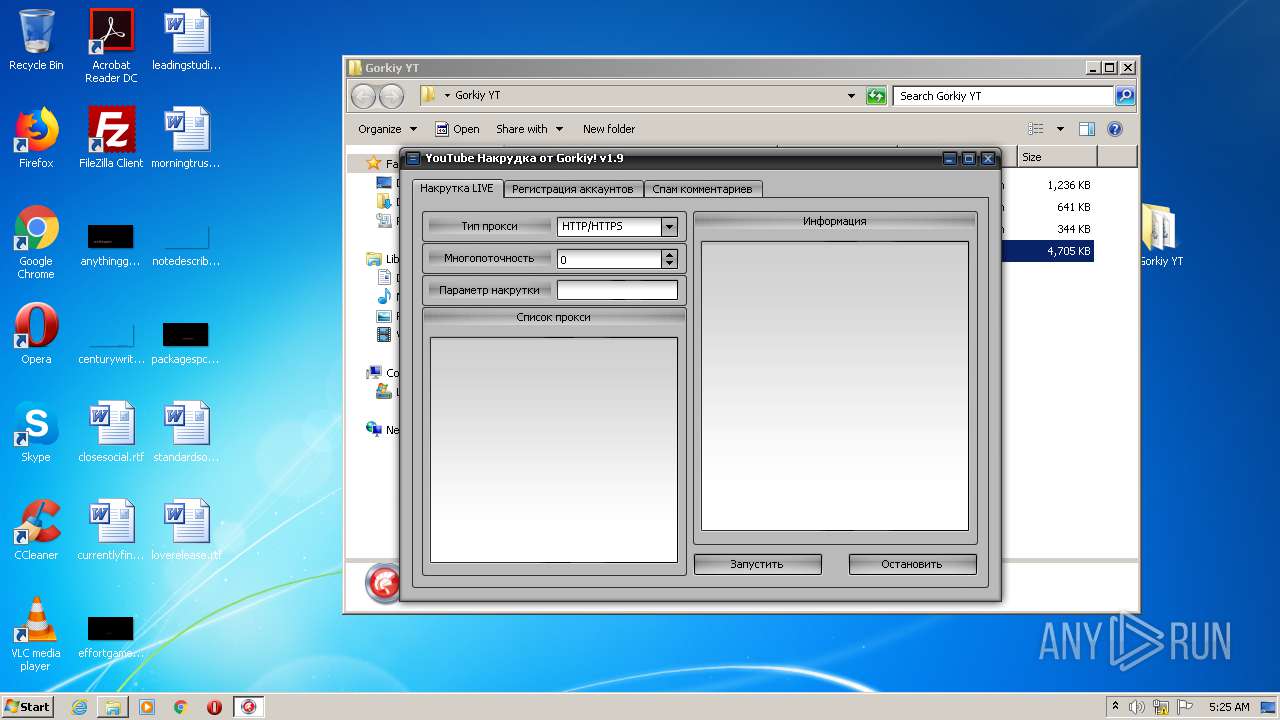
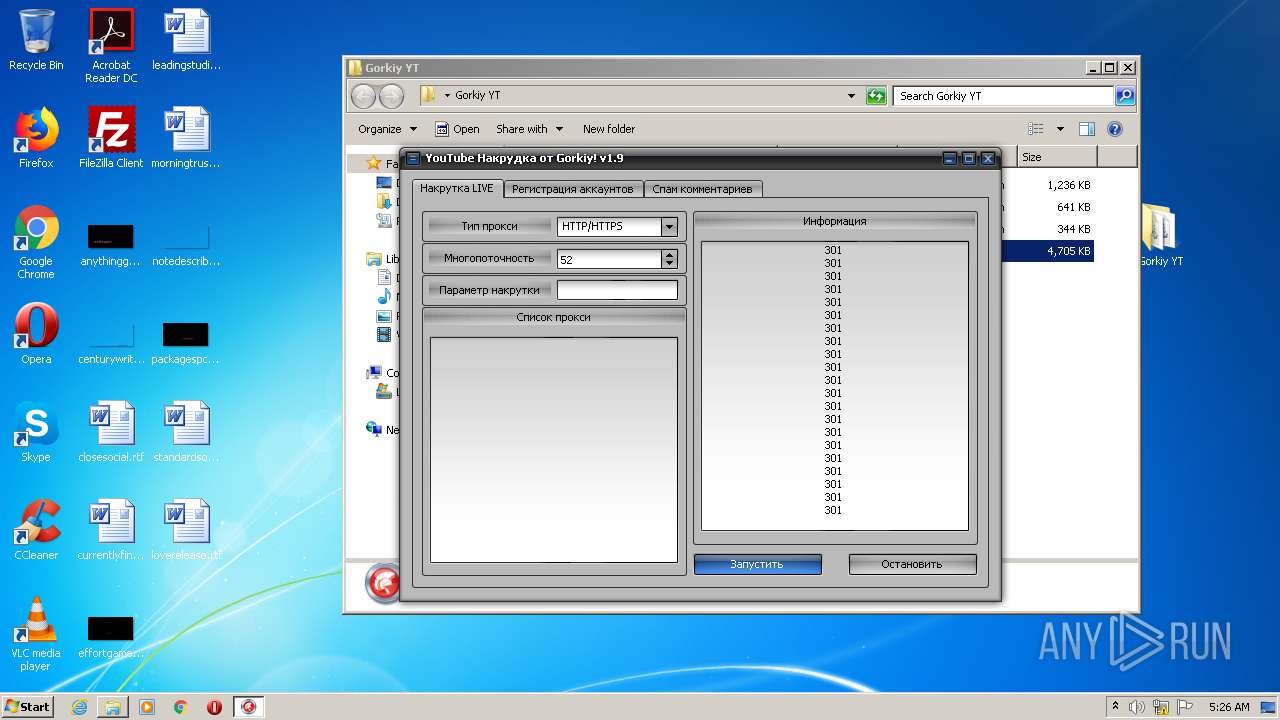
| File name: | Gorkiy YT.zip |
| Full analysis: | https://app.any.run/tasks/c6234b01-7698-4b9a-84e2-639af7879b18 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 05:24:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C647834C68D079DD0A9F599D037F9705 |
| SHA1: | 3388B2905F79CB50D2DB12BCE94891902C80A2DF |
| SHA256: | EF24B6B677142955E0FCA3CD3E21577B3EF5F44439F95D2894CB94EB102953F9 |
| SSDEEP: | 49152:QmxHkOdRry2VBPxSndfQtViS72uY0VHk1kNIohLKzckFkP5Ji0dEiRk7l:Qmxx/gCVlgUmkGrxvGkh |
MALICIOUS
Application was dropped or rewritten from another process
- YTGorkiy.exe (PID: 2396)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3164)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2460)
Drops a file with too old compile date
- WinRAR.exe (PID: 2460)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2460)
INFO
Manual execution by user
- YTGorkiy.exe (PID: 2396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:11:30 14:23:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Gorkiy YT/ |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2396 | "C:\Users\admin\Desktop\Gorkiy YT\YTGorkiy.exe" | C:\Users\admin\Desktop\Gorkiy YT\YTGorkiy.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2460 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Gorkiy YT.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3164 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
794
Read events
775
Write events
19
Delete events
0
Modification events
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Gorkiy YT.zip | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2460.25410\Gorkiy YT\YTGorkiy.exe | executable | |
MD5:— | SHA256:— | |||
| 2460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2460.25410\Gorkiy YT\ssleay32.dll | executable | |
MD5:— | SHA256:— | |||
| 2460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2460.25410\Gorkiy YT\msvcr90.dll | executable | |
MD5:E7D91D008FE76423962B91C43C88E4EB | SHA256:ED0170D3DE86DA33E02BFA1605EEC8FF6010583481B1C530843867C1939D2185 | |||
| 2460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2460.25410\Gorkiy YT\libeay32.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
104
DNS requests
13
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2396 | YTGorkiy.exe | 142.250.8.190:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 142.250.8.93:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 64.233.171.136:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 172.217.195.190:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 74.125.198.136:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 172.217.195.91:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 172.217.195.93:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 108.177.103.136:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 172.253.58.91:443 | www.youtube.com | Google Inc. | US | unknown |
2396 | YTGorkiy.exe | 74.125.198.91:443 | www.youtube.com | Google Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
s.youtube.com |
| whitelisted |