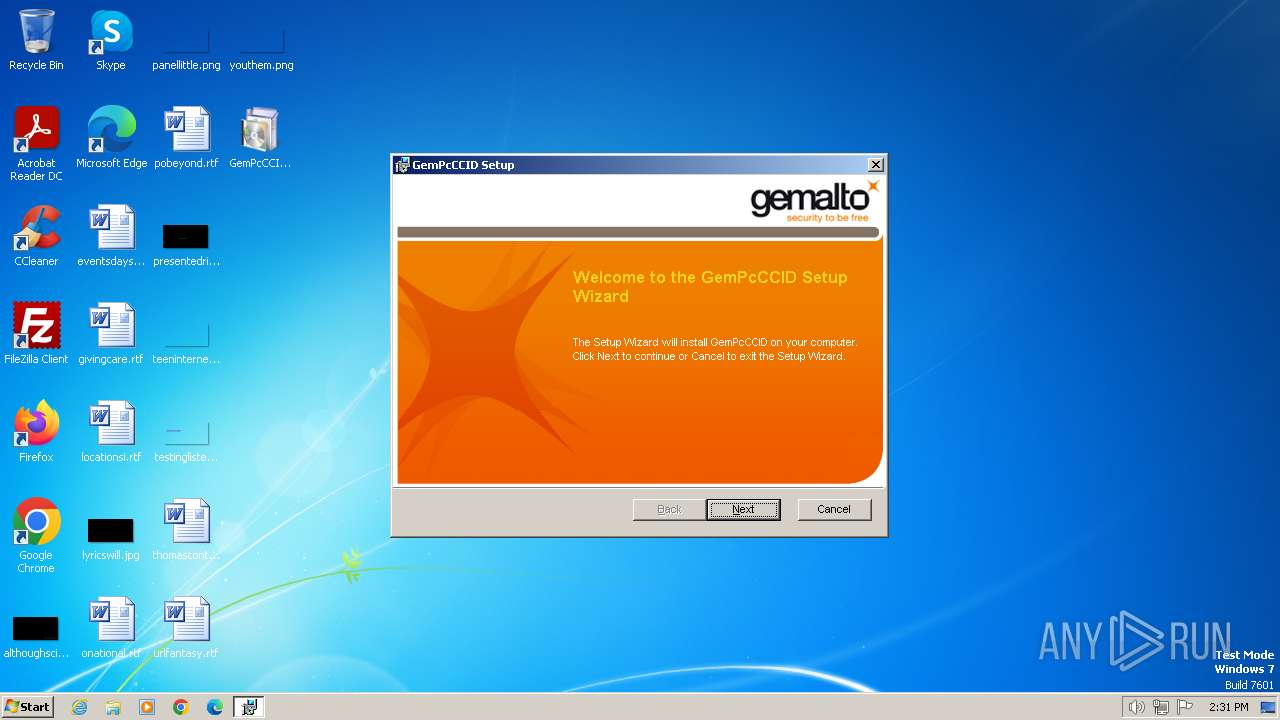
| File name: | GemPcCCID.exe |
| Full analysis: | https://app.any.run/tasks/0fa33af2-4a70-4501-9cdd-dcb3a04b7b88 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2023, 14:31:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6398B8EEFE43C672A73F35865E0A2732 |
| SHA1: | D99BD2E7ABE96688B1A2C15A26C23E79EDD028CF |
| SHA256: | EED01D9A250D5E8D8B5A305C2A1C2430A866A7FA136C6D024DF1F6359FA4401E |
| SSDEEP: | 98304:8n2J6xU3Jo6+YI5MEyvNQtE1AebyhnpWlB0V+l25s5xyAD7c+WRX6bVeIxh9iED8:+EQOA |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 664)
SUSPICIOUS
Reads the Internet Settings
- GemaltoInstallerSelectionApp.exe (PID: 2040)
Checks Windows Trust Settings
- msiexec.exe (PID: 1604)
- drvinst.exe (PID: 664)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 1604)
- msiexec.exe (PID: 2432)
- drvinst.exe (PID: 664)
Creates files in the driver directory
- drvinst.exe (PID: 664)
INFO
Drops the executable file immediately after the start
- GemPcCCID.exe (PID: 2120)
- msiexec.exe (PID: 1604)
- msiexec.exe (PID: 2432)
- drvinst.exe (PID: 664)
Process drops legitimate windows executable
- GemPcCCID.exe (PID: 2120)
- msiexec.exe (PID: 1604)
Create files in a temporary directory
- GemPcCCID.exe (PID: 2120)
- GemaltoInstallerSelectionApp.exe (PID: 2040)
- msiexec.exe (PID: 1604)
- msiexec.exe (PID: 2432)
Checks supported languages
- GemPcCCID.exe (PID: 2120)
- GemaltoInstallerSelectionApp.exe (PID: 2040)
- msiexec.exe (PID: 1604)
- drvinst.exe (PID: 664)
- msiexec.exe (PID: 2432)
- msiexec.exe (PID: 452)
Reads Environment values
- GemaltoInstallerSelectionApp.exe (PID: 2040)
Reads the machine GUID from the registry
- GemaltoInstallerSelectionApp.exe (PID: 2040)
- msiexec.exe (PID: 1604)
- msiexec.exe (PID: 2432)
- drvinst.exe (PID: 664)
- msiexec.exe (PID: 452)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 548)
Executes as Windows Service
- VSSVC.exe (PID: 1264)
Reads the computer name
- msiexec.exe (PID: 1604)
- GemaltoInstallerSelectionApp.exe (PID: 2040)
- msiexec.exe (PID: 2432)
- drvinst.exe (PID: 664)
- msiexec.exe (PID: 452)
Reads product name
- GemaltoInstallerSelectionApp.exe (PID: 2040)
Application launched itself
- msiexec.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (86.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
| .exe | | | Generic Win/DOS Executable (0.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:10:14 07:50:27+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 26112 |
| InitializedDataSize: | 2139136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x67cc |
| OSVersion: | 6.3 |
| ImageVersion: | 6.3 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.9600.16428 |
| ProductVersionNumber: | 11.0.9600.16428 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.9600.16428 (winblue_gdr.131013-1700) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.9600.16428 |
Total processes
44
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | C:\Windows\system32\MsiExec.exe -Embedding A4B759DF9915A4F54203B6430512EE1B | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Gemalto Installer\GemPcCCID_en-US_32.msi" | C:\Windows\System32\msiexec.exe | — | GemaltoInstallerSelectionApp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{2eb4bbd9-3530-2c95-287a-ae709b889a2c}\gemccid.inf" "0" "63d3e4633" "00000558" "WinSta0\Default" "00000550" "208" "C:\Program Files\Gemalto\ReaderTools\Installer\GemPcCCID" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemaltoInstallerSelectionApp.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemaltoInstallerSelectionApp.exe | — | GemPcCCID.exe | |||||||||||
User: admin Company: Gemalto 7.21 Integrity Level: MEDIUM Description: WindowsFormsApplication1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\Desktop\GemPcCCID.exe" | C:\Users\admin\Desktop\GemPcCCID.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2432 | C:\Windows\system32\MsiExec.exe -Embedding DD515392FC22527D27F31CA875A98C29 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
12 540
Read events
12 447
Write events
80
Delete events
13
Modification events
| (PID) Process: | (2040) GemaltoInstallerSelectionApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) GemaltoInstallerSelectionApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) GemaltoInstallerSelectionApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) GemaltoInstallerSelectionApp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (548) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1604) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1604) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1604) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 73 | |||
| (PID) Process: | (1604) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008543C5D72FB0D90164030000840D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1604) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
23
Suspicious files
27
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1604 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemPcCCID_en-us_32.msi | executable | |
MD5:E448AFFAF1F32B319FF78C04C9B949C7 | SHA256:161D3CE9F9FDF0C6AD359C9074D42DED9141176EB0E9E61F829E6F9313FF6839 | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemaltoInstallerSelectionApp.exe | executable | |
MD5:2BCA230997CD0C68633F3321E8D0D16F | SHA256:669A2457E22566AA691175DB69F36AC9B91ABF35163D27EA41C22068F8D0E6B8 | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemPcCCID_en-us_64.msi | executable | |
MD5:3A39A404CB240FE0292E379DB55BF069 | SHA256:EB145597455520B8A73302819D93A964782851429FBE9234EDD13465445A9FD8 | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemPcCCID_nl-NL_32.msi | executable | |
MD5:12937B3E728F7EB585E2C5D736A9365B | SHA256:40582A6D77158A6B6BB50A613299293A5736407049005C95FD34D11809AAD4F5 | |||
| 1604 | msiexec.exe | C:\Program Files\Gemalto\ReaderTools\Installer\GemPcCCID\gemccid.cat | cat | |
MD5:C3CD219380A6BE669552E520C2F11781 | SHA256:9B9B938F41F7F3D710B6E06C8462CEBA3A4EEF4941A81C502EF74EE66F6F60A8 | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemPcCCID_ja-jp_64.msi | executable | |
MD5:069DE1CCB5EC69C6A9B067C4038FDB8E | SHA256:D21F0692ECC588D4C6AB7F2741D8734A964AFBF433FF4D4B7D8D837B3899EE6C | |||
| 1604 | msiexec.exe | C:\Windows\Installer\MSI3FB4.tmp | binary | |
MD5:ED38764DACECA39C5D740735330809ED | SHA256:61587E4BDCF6A1E6D2D256893DEADBB9E0773C794AC201CF00B893E4930E2B34 | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemPcCCID_sk-sk_32.msi | executable | |
MD5:9130F0184C2F88DE1BE45D9AAAD2D693 | SHA256:4E91722A6A748E0B910ABB8846CEEC2E3A496EEC809B1A7387162C36854FF23D | |||
| 2120 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\GemPcCCID_fr-fr_32.msi | executable | |
MD5:E043B466842EB82DC2C3717B2AFC630E | SHA256:4C3EF16C0F2C9349E3CE958AC3E9A69CED63A401D2EB89A64A23D8C7E3263E9F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |